Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 7 and April 14. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
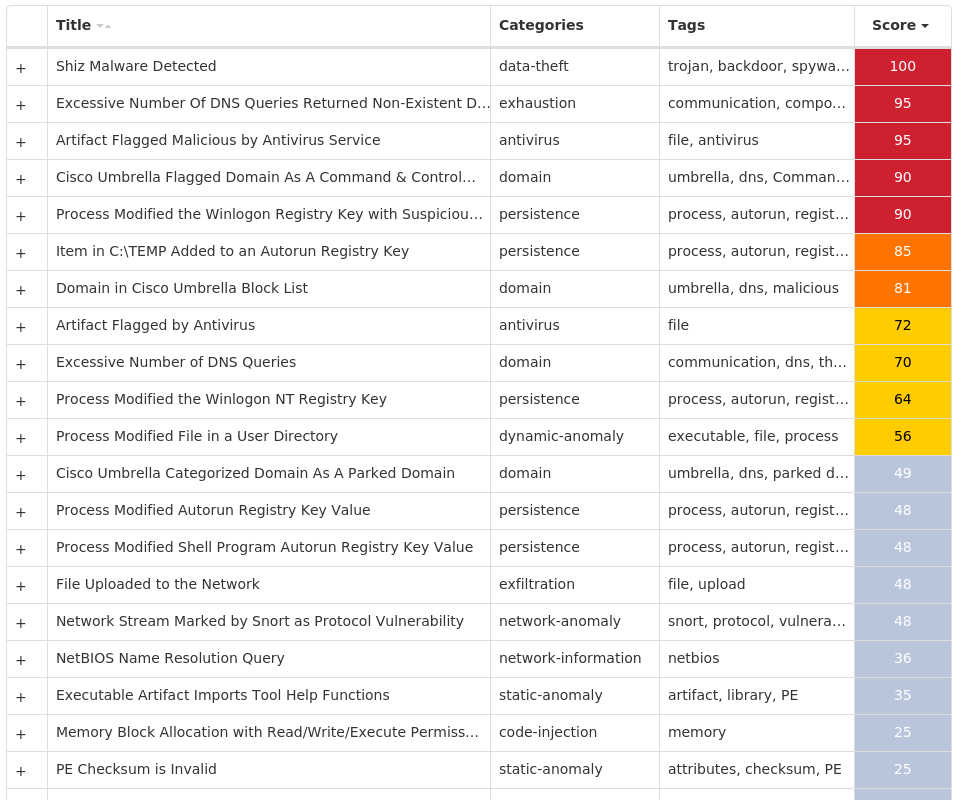
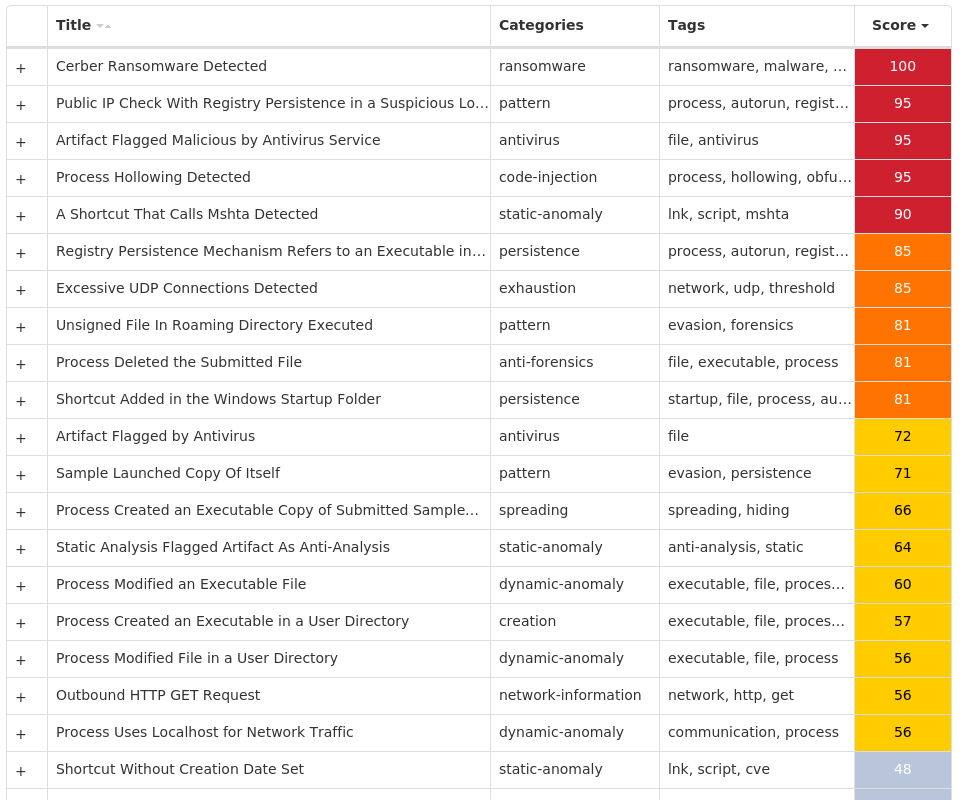
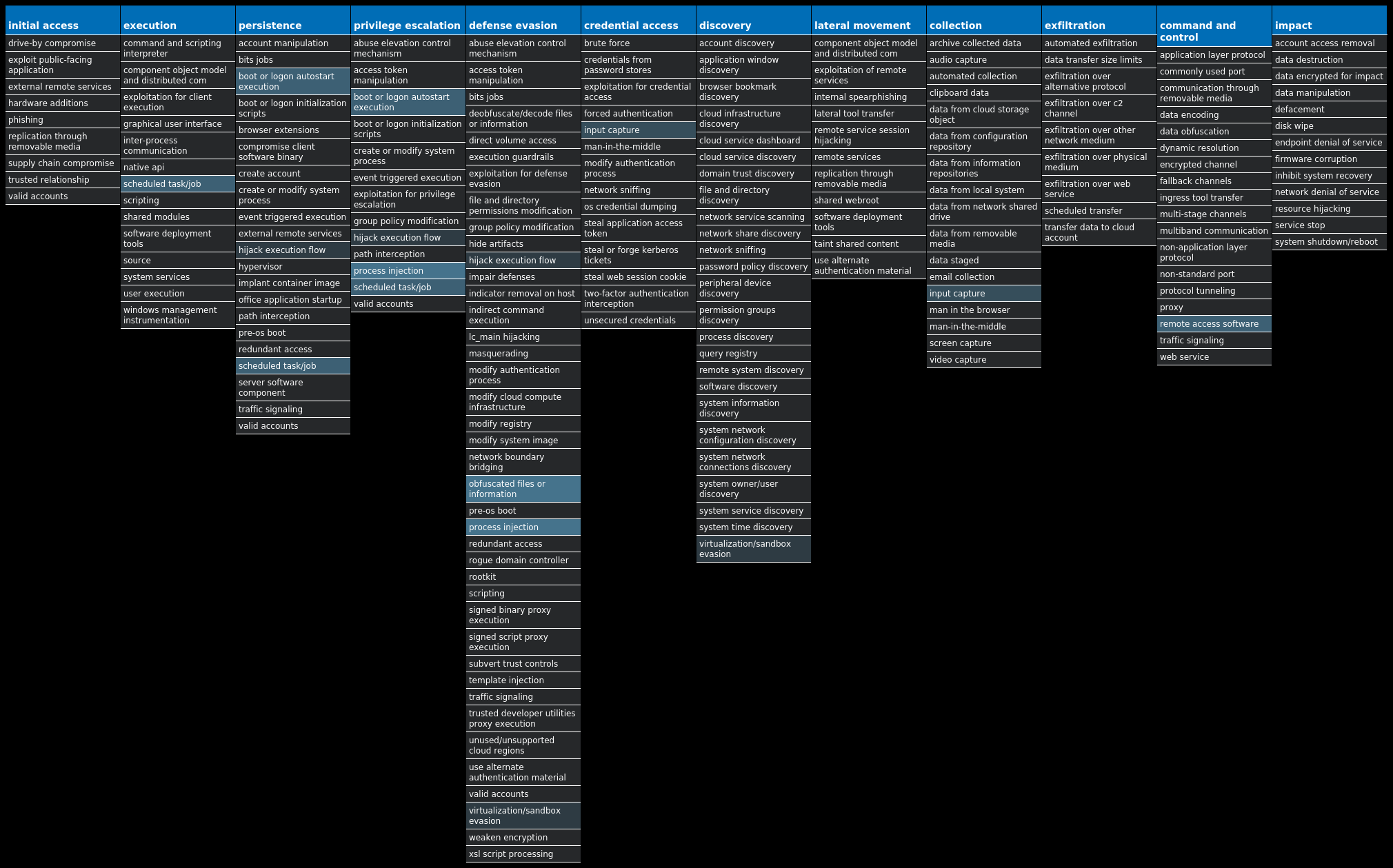
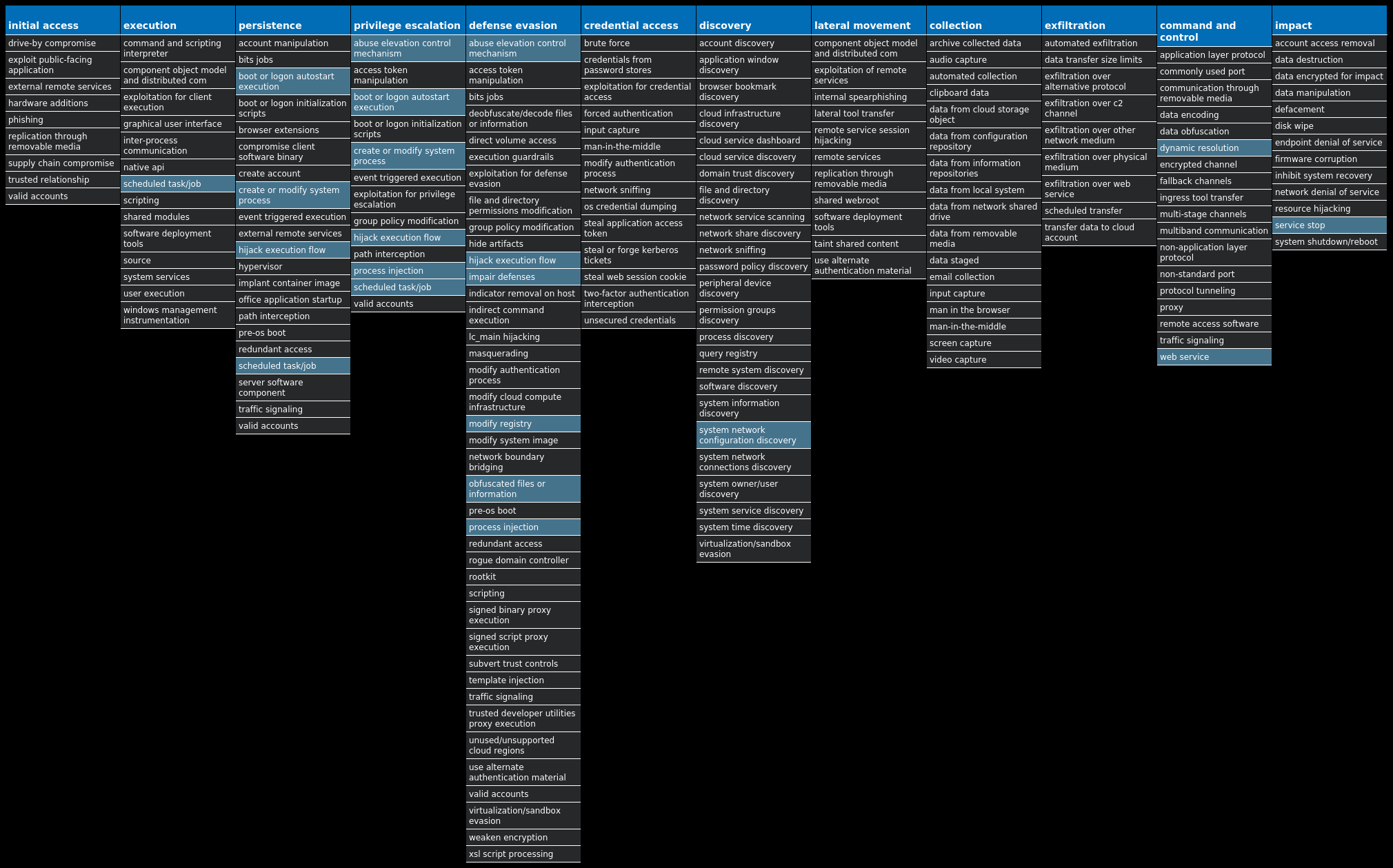
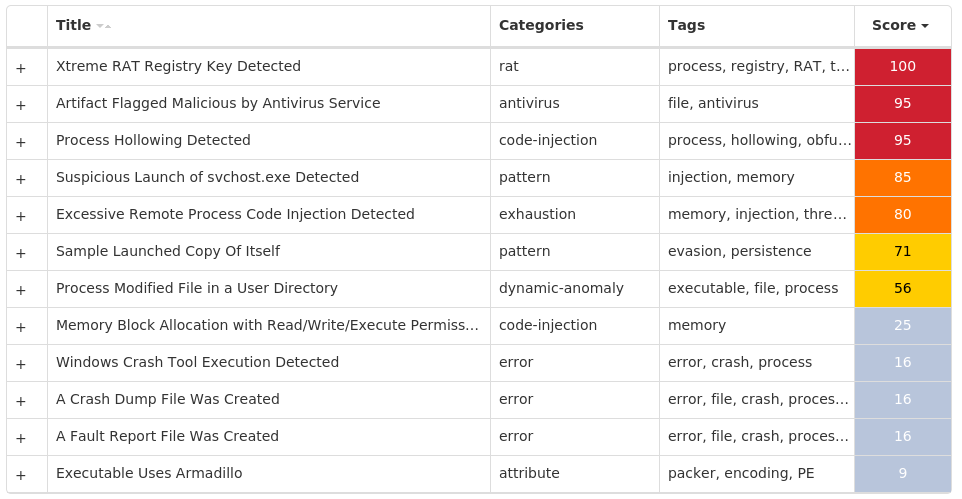
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.Shiz-9995579-0 Dropper Shiz is a remote access trojan that allows an attacker to access an infected machine to harvest sensitive information. It is commonly spread via droppers or by visiting a malicious site. Win.Ransomware.Cerber-9995641-0 Ransomware Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns, other file extensions are used. Win.Virus.Xpiro-9995713-1 Virus Expiro is a known file infector and information-stealer that hinders analysis with anti-debugging and anti-analysis tricks. Win.Dropper.DarkComet-9995915-1 Dropper DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. Capabilities of this malware include the ability to download files from a user's machine, send back usernames and passwords from the infected systems, and mechanisms for persistence and hiding. Win.Dropper.Dridex-9995967-0 Dropper Dridex is a well-known banking trojan that steals credentials and other sensitive information from an infected machine. Win.Dropper.Kuluoz-9996010-0 Dropper Kuluoz, sometimes known as "Asprox," is a modular remote access trojan that is also known to download and execute follow-on malware, such as fake antivirus software. Kuluoz is often delivered via spam emails pretending to be shipment delivery notifications or flight booking confirmations. Win.Virus.Ramnit-9996725-0 Virus Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It also has the ability to steal browser cookies and attempts to hide from popular antivirus software. Win.Dropper.XtremeRAT-9996042-0 Dropper XtremeRAT is a remote access trojan active since 2010 that allows the attacker to eavesdrop on users and modify the running system. The source code for XtremeRAT, written in Delphi, was leaked online and has since been used by similar RATs. Win.Dropper.TinyBanker-9996101-1 Dropper TinyBanker, also known as Zusy or Tinba, is a trojan that uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe." When the user accesses a banking website, it displays a form to trick the user into submitting personal information.
Threat Breakdown Win.Dropper.Shiz-9995579-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT Value Name: 67497551a 26 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: 98b68e3c 26 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: userinit 26 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: System 26 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: load 26 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: run 26 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: userinit 26
Mutexes Occurrences Global\674972E3a26 Global\MicrosoftSysenterGate726 internal_wutex_0x000004b426 internal_wutex_0x0000043c26 internal_wutex_0x000004dc26 internal_wutex_0x<random, matching [0-9a-f]{8}>26
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 85[.]94[.]194[.]16926 13[.]107[.]21[.]20015
Domain Names contacted by malware. Does not indicate maliciousness Occurrences fobyqyhezem[.]eu26 gacucuhumeg[.]eu26 maxilumiriz[.]eu26 jelojujopen[.]eu26 qekafuqafit[.]eu26 ryhyruqeliz[.]eu26 kejepujajeg[.]eu26 tufibiqunit[.]eu26 lygumujycen[.]eu26 xudoxijiwef[.]eu26 pupoliqotul[.]eu26 citahikodab[.]eu26 direfiwahur[.]eu26 vowypikelaf[.]eu26 foqurowyxul[.]eu26 nomimokubab[.]eu26 ganovowuqur[.]eu26 mavaxokitad[.]eu26 jecekorosuk[.]eu26 qexeholagav[.]eu26 cilicofahev[.]eu26 vojajofyced[.]eu26 dikolobeliw[.]eu26 fogefobunik[.]eu26 gadurabotiw[.]eu26
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\<random, matching [A-F0-9]{1,4}>.tmp26
File Hashes 068d644b9b7235586167057d266c5a1a91ae65c815e6ebf8c507a302f62dc3cf08956248ac031ddec7e91d369383005a3e28658e5f7df2e96608ec48db3500220e8064493dd2bdcbdbca2fe6b3b24cb2bd8ca1a986f3af91b41ef3799c8506ba102364dee6af1ee0fd51b1c6334ffc9b98ac09ee5a4f7944479983f023f7ec7f11fdf3b279e74b1edb4113ed0c915a0036d58c8daa0c35e01bd9b2e459a2dacb13b48d20f75458f89fb5ffd17c78aab1da965b3adacb5a4d180e5f13742af38f17c5296cbfe5d684c62ca1e5e42f88dcfe808f0279e28cb474ce5e12a7949ffc1b553ace2cb8a8f52e85cd1426c88b0935875bffed100e3ab85964f08beb87a51f6808ef75efc5f9dd8ceefbe64419d3aee9227ea9acb284847083e1e6b4bab921c687d07078f7074d72c92d6f71090175c44c2ab5984c5e02c65ef2658835fb2fd3d2a3389db1d81cc060004780951dd342aa732c040f3bbb3d1c712845ecb733315dd18879cc9df6e3846c8bf6c14c3e62be2df8b019bcb03a9d81e082b5c635e96b87fc6cf18df36cc81484646847ca82595a8bdeb9edc416114005dfcc7a3e78983f6aebe750f0d6c68a271e181a4fab42a3ac7ee03175978efb31deab8746479e0841295c9aecdbd689c77ea0f6ffe8dde9f711fe8a489efb3ccebec85f46f717eb75a5f0759731fda1837e33f42e05c61ae5684d0b8b1c444395cd94b447e0e6e0e50be3647896c3348295a39704df29f410014c511cb473d9c3ae793d4c7efbbc7df32938f5f78f86a4b0d06585fdc1cff20fed1cf16339815f8e7fd055b3ebe3ffab9d6444b3fc421dc805ead41354d24f3cd78ec54b78550cc5779e56975c17ab0b602e247ddce9d0240e0e5b7578b457f9b4c29fb6b574c65c104a56e291a38441d33e987f87d1fe9e14a3d0ed6c9a8ce5d657bdb2a34faf0483c05f57e49fbe9a4f7c1c3a6dfc26a4157b4c353ac6dcee708a6a52588ebeee66906041b3299179a15c0fa9d22b4a7f2d8d83e9796e580e635e99eae097f0c2ace2659a73a75a0c3e83f51812ed3b0d68ca7bc36404b89dc4417ec56cb5f9857ea166415be060a7fdedd814b1ec50b69bfdecbfd4c692335e3dd1eecc4de60b219d
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
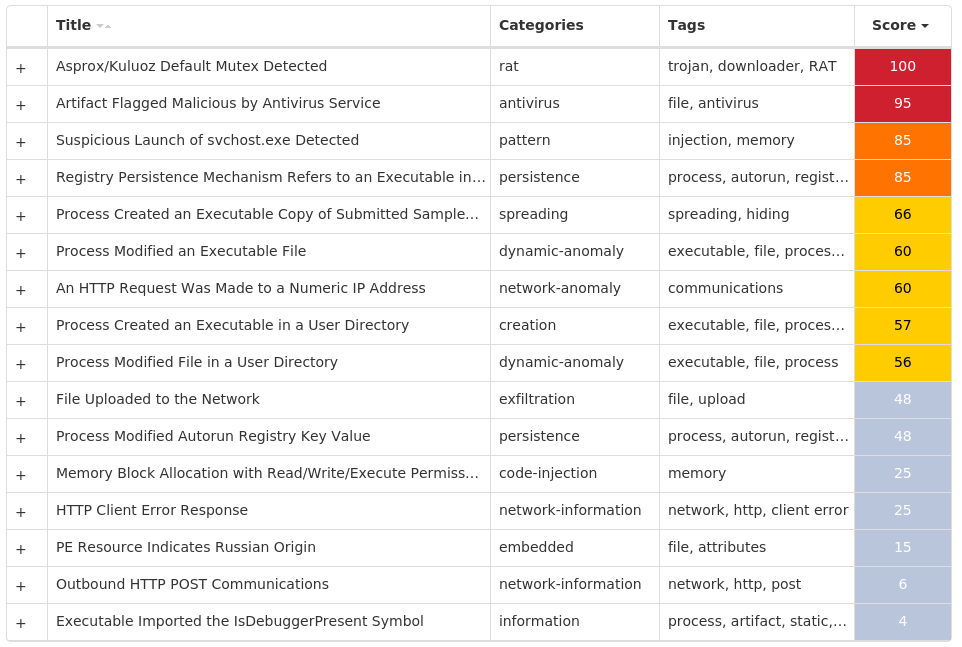
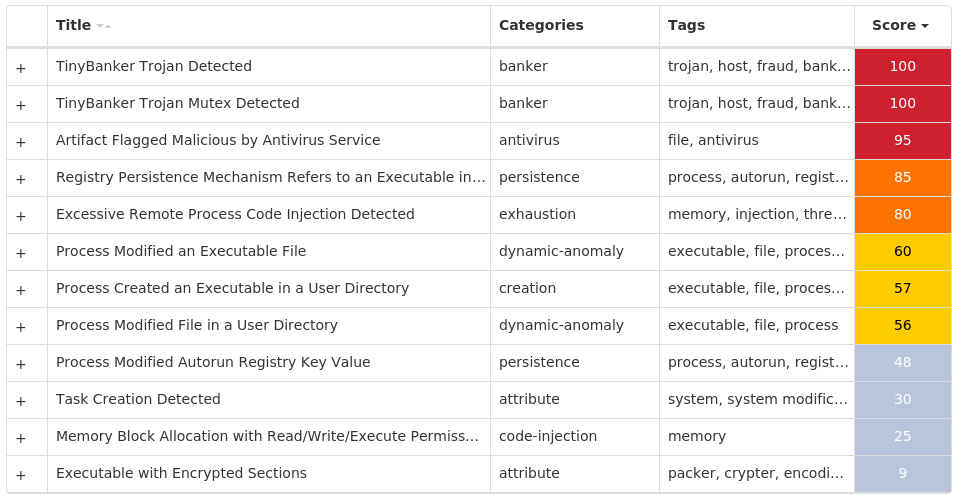
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.Cerber-9995641-0 Indicators of Compromise IOCs collected from dynamic analysis of 73 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER Value Name: Run 72 <HKCU>\SOFTWARE\MICROSOFT\COMMAND PROCESSOR Value Name: AutoRun 72 <HKCU>\PRINTERS\DEFAULTS\{21A3D5EE-E123-244A-98A1-8E36C26EFF6D}72 <HKCU>\PRINTERS\DEFAULTS72 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: mshta 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: mshta 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: perfmon 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: perfmon 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: sbunattend 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: sbunattend 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: osk 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: osk 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: poqexec 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: poqexec 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: iscsicli 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: iscsicli 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: xwizard 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: xwizard 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: mfpmp 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: mfpmp 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: verifier 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: verifier 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: unlodctr 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: unlodctr 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: bootcfg 1
Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}72 Global\44716b81-d4e0-11ed-9660-00151783c8e11
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 208[.]95[.]112[.]172 31[.]184[.]234[.]0/2372
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ip-api[.]com72
Files and or directories created Occurrences %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}72 %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\Component_0071 %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\Component_0171 %APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\perfmon.lnk3 %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\perfmon.exe3 %System32%\Tasks\mshta3 %APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\mshta.lnk3 %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\mshta.exe3 %System32%\Tasks\perfmon3 %APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\sbunattend.lnk2 %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\sbunattend.exe2 %APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\xwizard.lnk2 %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\xwizard.exe2 %APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\poqexec.lnk2 %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\poqexec.exe2 %System32%\Tasks\poqexec2 %APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\osk.lnk2 %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\osk.exe2 %APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\verifier.lnk2 %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\verifier.exe2 %APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\unlodctr.lnk2 %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\unlodctr.exe2 %APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp\iscsicli.lnk2 %APPDATA%\{6F885251-E36F-0FE6-9629-63208157D7A2}\iscsicli.exe2 %System32%\Tasks\osk2
*See JSON for more IOCs
File Hashes 03ccbaf5889b4588c9e903539df86ece3c1276234e3fbc0f6e2e56c67e4665820c253e5a56c27246b349ef1d9088c39ed16d2c44461b36666600e419122ffdb60c6aeaab949862cf4ccdb0f13d461e34e3b25988da44715f2c1085c5782dd9b8170e9a207c61dcaf7f88b6ad5fbc1c3b5a4c93fb8ef05381430172cd420f985517265f3b9cc835fd0e15ab2702129f1cb430a9ef1364d80230a0b3c8c19b7d8c1b5bde97078fab60340410ddd0582e87367a0bf49e632e02987858686cac75803094e5d17240c02fc0559c2be545ae01f5db65b0db932f6a09a9369643eaf516309610bec03f343cf9579e8c9b6244b39722c55faca931f2954cf53f8c0c23bd3715ea8c6137eb072a3f05bbadb53a4ec3decf072a3a73f34691e5c03afea9163e0e0b0adb20c703ab08d01e74302a374137fbab1b47bd4de1066cc89dc057d23ef1c20f49367cc81a6b4e54e250fb4e87e8143f8920c5e4b594593aefd819ff4129794742f87337e025ca3a2065ae0cebe8c582d428bafd31fd99a5f4b0ba77420b53d1d1c1bd5e81c30c9ac05bdc2d8965a17a1fc569d6591b7ffa1ca0125744eb59ba7d2f70da2444c0817a3edac7d644c6a1bd41f354032e227205cb8c984655e151c7cb73cc5d27bef4d1062c2448bd57b3a01d32b0669ebc36a197df384b427a3342938b2b4da751151dd1b9a28e1bc9c9bee65796604020319d8e6f0550a97a57d26a458586b21050e67fa266ccfa7af504af375d0d2f45ed001bdfba515cef52848bcd79a4debe6d7a0d3d88cdb7e6305aa41efc5bd0d6db9f42c5cb5419843ff86a28858a3e9c3484c0113e96f6354f086a3345af018dc110cb63605e0f1397a28195463e0e444321b06681af1d4efe453607bac0bfd12426872dc86336b9ef15163faa704166351bbc31bbc9af111f6b674c76bd90777ec5bdacdc64c477b43c8bb2809df4ce86e8831a40ced61f6f59d2eceb058353d2fa6ea27e665b897b6dc9a0049400c44d640eacc3487223d0bdf55d72a8cc14f1bfbc38b0677feac61e3728846e09deeeb4f6adb4fb0ba209a16baad683faedd1940db4266989058fd659095de56f66b4399d58b919ceb66a93d1a9fd2db79efac8741280
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Virus.Xpiro-9995713-1 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER Value Name: HideSCAHealth 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32 Value Name: Type 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64 Value Name: Type 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32 Value Name: Type 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32 Value Name: Start 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64 Value Name: Type 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64 Value Name: Start 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IEETWCOLLECTORSERVICE Value Name: Type 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IEETWCOLLECTORSERVICE Value Name: Start 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE Value Name: Type 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE Value Name: Start 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE Value Name: Type 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE Value Name: Start 25 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\SYSTEM Value Name: EnableSmartScreen 25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC\S-1-5-21-2580483871-590521980-3826313501-50025 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC\S-1-5-21-2580483871-590521980-3826313501-500 Value Name: EnableNotifications 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32 Value Name: Start 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64 Value Name: Start 25 <HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE Value Name: AccumulatedWaitIdleTime 25 <HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\LISTENEDSTATE Value Name: RootstoreDirty 25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE Value Name: AccumulatedWaitIdleTime 25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\LISTENEDSTATE Value Name: RootstoreDirty 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Type 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Start 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER Value Name: Type 24
Mutexes Occurrences kkq-vx_mtx6225 kkq-vx_mtx6325 kkq-vx_mtx6425 kkq-vx_mtx6525 kkq-vx_mtx6625 kkq-vx_mtx6725 kkq-vx_mtx6825 kkq-vx_mtx6925 kkq-vx_mtx7025 kkq-vx_mtx7125 kkq-vx_mtx7225 kkq-vx_mtx7325 kkq-vx_mtx7425 kkq-vx_mtx7525 kkq-vx_mtx7625 kkq-vx_mtx7725 kkq-vx_mtx7825 kkq-vx_mtx7925 kkq-vx_mtx8025 kkq-vx_mtx8125 kkq-vx_mtx8225 kkq-vx_mtx8325 kkq-vx_mtx8425 kkq-vx_mtx8525 kkq-vx_mtx8625
*See JSON for more IOCs
Files and or directories created Occurrences %CommonProgramFiles%\Microsoft Shared\OfficeSoftwareProtectionPlatform\OSPPSVC.EXE25 %CommonProgramFiles(x86)%\microsoft shared\Source Engine\OSE.EXE25 %ProgramFiles(x86)%\Microsoft Office\Office14\GROOVE.EXE25 %ProgramFiles(x86)%\Mozilla Maintenance Service\maintenanceservice.exe25 %SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe25 %SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe25 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe25 %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe25 %System32%\FXSSVC.exe25 %System32%\alg.exe25 %System32%\dllhost.exe25 %System32%\ieetwcollector.exe25 %System32%\msdtc.exe25 %System32%\msiexec.exe25 %SystemRoot%\ehome\ehrecvr.exe25 %SystemRoot%\ehome\ehsched.exe25 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.log25 %SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngen_service.log25 %SystemRoot%\SysWOW64\dllhost.exe25 %SystemRoot%\SysWOW64\msiexec.exe25 %SystemRoot%\SysWOW64\svchost.exe25 %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngen_service.log25 %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngenservicelock.dat25 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.lock25 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngenservicelock.dat25
*See JSON for more IOCs
File Hashes 1a51dc7078bc904e289c30ee08b08e76710ec97dbff37b62a906378cd942b9631cfa1f8ace93ede66537d196e5558e1fc53861a1a61119690a8acd88aa2439c721d2473fd376c4718b76af1448b23e37ce6fd620ca459cb8d2d53ff00777da102b6586a202142083f24f7d02e9221264ac5b8688b183acdbeea8c487c13aec2c42e3b53e9277585630c2cf6e39b1f8b23804ef1f50979e5b9fbd96f97397d7ae47c31bb54c72a8c4ccc728b8d35f38d7ecb8a4c01ae6573c98ae8707c5b314b647fd1c6e279fb90f0e340d734ef2fe8ace00166a7998fa81b931d92c5b074fa549aa3434734f91b628a66ef8448d2951068ad918784597688c8837b2a03460d45511281e4402ecdd8c066ab381fe65f6599a259cf4540d47a9224b15646af59f5639f56d060317a8f143b190502c0d465a437cc0bb4cb8bfa258d79da7e01df45b49c7075057543f34083c628c330a59d77b781ee651adc13feed34d3fc902015c8c5b1078c861b6150fcb5546bd824dcf49339282e82fb3a0c057435bf304d0697d8910027b9cd392fd984af2b735caf4a2f45a509dd36d3a5af4a33ce6c5b370b6c7364e53cd0b98d61533a888f6fcaf31de035da2acfef5bb970207bacae67c0051fb95cb0b9660ec9fdcb5b415af43f131118f28400c14c6a7900753e25e8609ec20c4d8f7bb60cc954e271f5d4edb896e81993d4232bda55c348a78e4588c900ac34d876e4f74a9dd6f29e4bd96f1983c4bc97157f66ab067beeb4f9ef58cff77e8d9569bcb2e7982a8333b82bc5d4d54afbf744160d3aaeb2df531539a90115759a4a2985e9758ef12a7afb13768c0c12b08a7ec45f458f4490d3e579e915ec7c041668bd324b0d659ee512bd7232c69c2b07fab357a21feba3f38235b9477240aba143cf98a870a3acb2e2bc5dd455dc5b95824e5b9bd82af38f75a0b9ae8abc868b383b0d495cdd19d00836ba49ef61a84afe1f1569516c96de52cb1a9e3a4fe2a6da2363b055f938b1fba4a2ca4b2b666e6df5105681f197f65190aad063e5ab6632483233b7a0950b82d5625a89da913c49b36d587875d38b5653cafa140696090b8d85b6d0604dc9288c18ebd8aa8d8a969a7e2a080837b254d0f
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
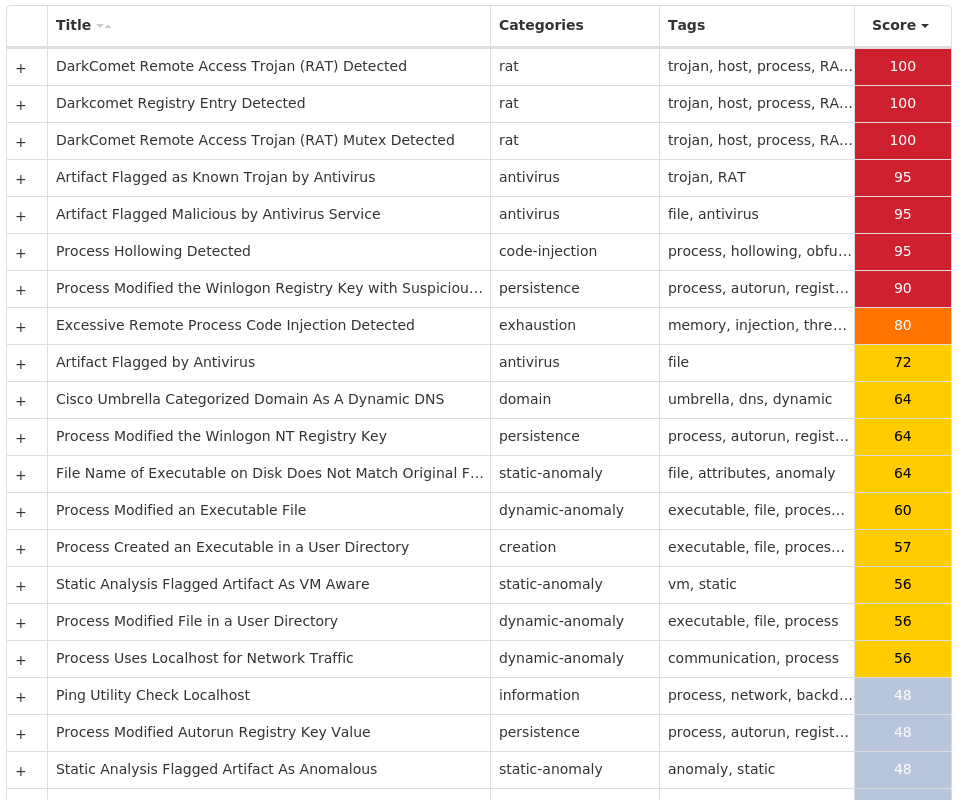
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.DarkComet-9995915-1 Indicators of Compromise IOCs collected from dynamic analysis of 33 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 31 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: wextract_cleanup0 23 <HKCU>\SOFTWARE\DC3_FEXEC15 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: UserInit 10 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: winupdater 9 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusDisableNotify 3 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: svchost 2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: wextract_cleanup1 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN2 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: EnableFirewall 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: DisableTaskMgr 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DisableNotifications 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLUA 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UpdatesDisableNotify 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CURRENTVERSION\EXPLORERN Value Name: NoControlPanel 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: DisableRegistryTools 1 <HKU>\S-1-5-21-2580483871-590521980-3826313501-5001 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: MicroUpdate 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CURRENTVERSION1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CURRENTVERSION\EXPLORERN1 <HKCU>\SOFTWARE\XENOCODE1 <HKCU>\SOFTWARE\XENOCODE\SANDBOXCACHE1 <HKCU>\SOFTWARE\XENOCODE\SANDBOXCACHE\31044DB31
Mutexes Occurrences DC_MUTEX-<random, matching [A-Z0-9]{7}>15 _xvm_mtx_file_0xE13E63127 _xvm_mtx_other_0xE13E63127 _xvm_mtx_reg_0xE13E63127 __xnospawnvm_0x7985 __xnospawnvm_0x7884 __xnospawnvm_0x77c4 __xnospawnvm_0x71c4 __xnospawnvm_0x7dc4 _xvm_mtx_file_0x213E27571 _xvm_mtx_file_0xF6CFE0931 _xvm_mtx_file_0xCBE2DE5A1 _xvm_mtx_other_0x213E27571 _xvm_mtx_reg_0x213E27571 _xvm_mtx_other_0xF6CFE0931 _xvm_mtx_reg_0xF6CFE0931 _xvm_mtx_other_0xCBE2DE5A1 _xvm_mtx_reg_0xCBE2DE5A1 _xvm_mtx_file_0x6F9EE3E51 _xvm_mtx_other_0x6F9EE3E51 _xvm_mtx_reg_0x6F9EE3E51 _xvm_mtx_other_0x7D909FF31 _xvm_mtx_reg_0x7D909FF31 _xvm_mtx_file_0x521319441 _xvm_mtx_other_0x521319441
*See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 199[.]59[.]243[.]2232 78[.]159[.]131[.]801
Domain Names contacted by malware. Does not indicate maliciousness Occurrences backtrack[.]xtreemhost[.]com2 superprova95[.]zapto[.]org1 qwe[.]no-ip[.]info1 redesert[.]no-ip[.]biz1 darkcomet1[.]no-ip[.]org1 serhat[.]no-ip[.]org1 knightrider988[.]no-ip[.]org1
Files and or directories created Occurrences \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode31 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox31 %TEMP%\IXP000.TMP\calc.exe16 %SystemRoot%\SysWOW64\Windupdt8 %SystemRoot%\SysWOW64\Windupdt\winupdate.exe8 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Native7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Native\STUBEXE7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Native\STUBEXE\@APPDATALOCAL@7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Native\STUBEXE\@APPDATALOCAL@\Temp7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Native\STUBEXE\@APPDATALOCAL@\Temp\IXP000.TMP7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Native\STUBEXE\@APPDATALOCAL@\Temp\IXP000.TMP\NOVO.exe7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Native\STUBEXE\@APPDATALOCAL@\Temp\IXP000.TMP\calc.exe7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Virtual\SXS7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Virtual\SXS\Manifests7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Virtual\SXS\Manifests\NOVO1.EXE_0x524163b09cc32d9a640e2bffb45bb10a.1.manifest7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Virtual\SXS\wextract@1.0.0.07 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Virtual\SXS\wextract@1.0.0.0\wextract.manifest7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Virtual\SXS\wextract@1.0.0.0\wextract@1.0.0.0.manifest7 %TEMP%\IXP000.TMP\NOVO.exe7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Native\STUBEXE\@SYSTEM@7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Native\STUBEXE\@SYSTEM@\explorer.exe7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK7 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.17 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.597 \Device\HarddiskVolume2%LOCALAPPDATA%\Xenocode\Sandbox\bet365+HACK\2.0.1.1\2013.11.09T18.59\Virtual7
*See JSON for more IOCs
File Hashes 0359d1cf3daba5ae58bfd91f3daa5ca9741c76ff3e98ac791fd73788968a5c0607bdc9b4214fd0d2cf06fe4807b33999d0f552f43829017e8702b840cee0efe71ce501039d895a1c93354949a64ebb19065d8fa97b8b795bf69b8430dcbdbd761dc2b097f9a1109e651c092db8f6f992502bc10c00e5fdd0da75e785fd06a1772482c6a291c070ebd220398bbe554a4555fd8993db4c41cc9724c565ac9a8ccf30f7a0cbee6aa3255682c58598c4df12382f261f210924a9448137e33f3304243143179bae1d9316d3b50aab447ff56cd3f8b9df5446adc8700020f94726513f4341307cb4081ee188c5a94e4f8a3310c89d9f0d691b81b6c20ad4845e985d884ce6d0c4e2d8473e8f7fe0dd41451cca644b3e81a2ef08a0e9bfcc36686e4a3150d73063c2d44ba34afdc60f8b54da9d9857a65b758e6dbe0859444d5155691253136c30c930686b7f35d356abee730983dd759e2f825f28e7f4e94a0289f00c5814b46b2b36bd83935d62c4fa593a4dfb8577b80f364fb61c77c23e15c2f9c85a3c4ef91c72b9a9b43162d7b10884b4f9e0c581b5632deb30c21fcce6054fd561a950bb0c79804090f97e84e91d6cb675c8aa7103d154de98c2fd72c45b2c7d634baa075ec773ebc348e3b0ee2ca5fedb25177ea6c0398c3c68f97d4939e77668c7461832acb98a438d3cc0bb7f8d2ed797c1050d765f36764273c0f076939d6e71ea65c97ff1f8cb0d827dd7de5e147eb912d436f230cf8c2c53f642e3ba7571d788352230d467d21f9ca65997b5a062c67d391ff62853a0cabfd14d8b8c0f746b14f4dbd7cf8a93b907fbff658a8323b9dbee0d78dcb9a3322f4f255edbd882286164ef22450adc99af0b602aac191005674d7b2d16f301d969b3da7b9e7287f80e9986dab771123910dc3c87b9ed6da9fd56d054802157eb692872960d9a8af88eba55f62e52417586b1d2c855ffeb792915a2f0a6ef28ef893a5ad6f4708b9866f646a4f7f6c651c4dab44f35c4b8e4d2cc9f7b6b82c0bea1cfd7356320900a4b6a0b030aff05841e278da77c4f3980a751a961f3a13dbf7901026d71e690bfc181a8215a0ce11a9bc80d882b058b044e5e79a5d17ca29ee11318f74fa5
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
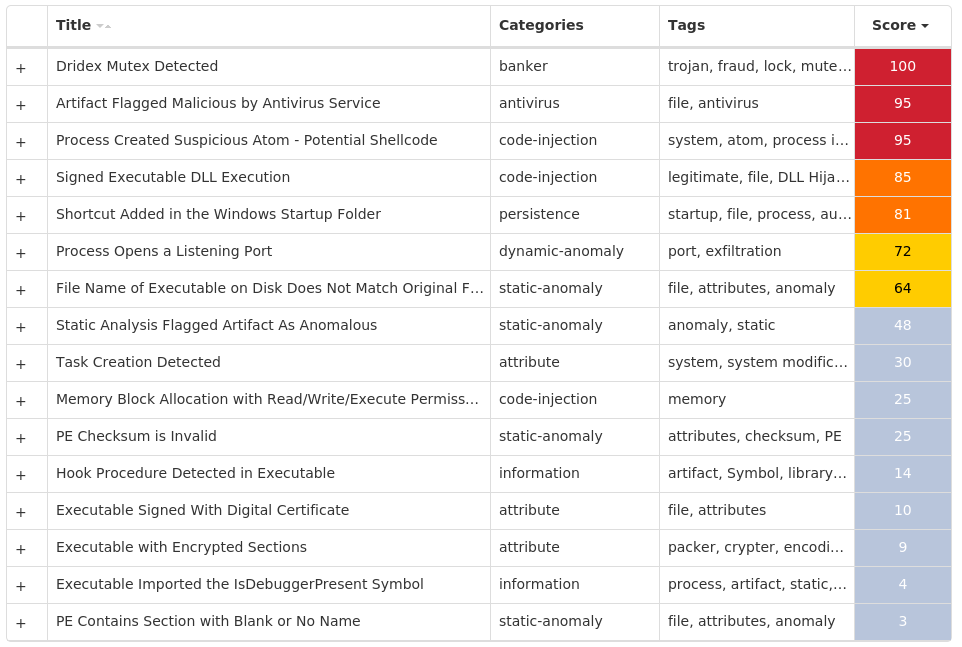
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Dridex-9995967-0 Indicators of Compromise IOCs collected from dynamic analysis of 21 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{690D1BD7-EA98-1004-3AC9-E87553700E95}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{690D1BD7-EA98-1004-3AC9-E87553700E95}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{63FC4996-AFD5-E391-06A7-EFB6E2702561}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{63FC4996-AFD5-E391-06A7-EFB6E2702561}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{10CDDA71-B745-777B-1AF7-51696DB9BB93}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{10CDDA71-B745-777B-1AF7-51696DB9BB93}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{CFD6D5E6-02FB-7433-9261-E8E1B87CAC69}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{CFD6D5E6-02FB-7433-9261-E8E1B87CAC69}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{8BAB5812-9D02-8F14-74B1-BEDE393F8C1F}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{8BAB5812-9D02-8F14-74B1-BEDE393F8C1F}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{10DF83AD-199B-9C18-3FEF-E4ECD6A42F66}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{10DF83AD-199B-9C18-3FEF-E4ECD6A42F66}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{1AD90FE5-CE2F-E8B8-CF09-E0B1912E9542}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{1AD90FE5-CE2F-E8B8-CF09-E0B1912E9542}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{05ED06D6-F422-71CC-26B3-C9964D56F645}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{05ED06D6-F422-71CC-26B3-C9964D56F645}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{98B09642-2764-54AE-3333-D8C6CA536428}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{98B09642-2764-54AE-3333-D8C6CA536428}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{63D99860-AA40-CA79-F681-9DECBEF55447}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{63D99860-AA40-CA79-F681-9DECBEF55447}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{D4B277A3-C25E-BCDE-A054-D41AAC36394B}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{D4B277A3-C25E-BCDE-A054-D41AAC36394B}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{FE9DE6BC-A4CF-8285-E73C-DFE7A08197FE}11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{FE9DE6BC-A4CF-8285-E73C-DFE7A08197FE}\SHELLFOLDER11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{B11CF2E2-C0C2-7860-F12E-428101DCB963}11
Mutexes Occurrences {dbad1190-816b-947c-9b01-53ef739d7edb}21 {24d07012-9955-711c-e323-1079ebcbe1f4}11 {616807e7-60c7-8c80-3741-36d83851a051}11 {66a0c47d-e072-fcc3-ab91-eb5a9f75db13}11 {ccf5ce5e-e149-8d4b-f524-b5f23ab2c424}11
Files and or directories created Occurrences %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c511 %System32%\Tasks\Ryddmbivo10 %APPDATA%\Microsoft\Templates\LiveContent\Managed\Word Document Building Blocks\9u1 %APPDATA%\Media Center Programs\sCUqiQ1 %APPDATA%\Media Center Programs\HQO1 %APPDATA%\Macromedia\Flash Player\#SharedObjects\YXTRFETG\P41 %APPDATA%\Media Center Programs\MZ1 %APPDATA%\Adobe\Flash Player\AssetCache\241W6oAXo1 %APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\FBQqsDe1 %APPDATA%\Microsoft\Templates\LiveContent\Managed\SmartArt Graphics\1033\D83KuAjg3e61 %APPDATA%\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\pGS1 %APPDATA%\Microsoft\Windows\Recent\AutomaticDestinations\jWe3JvN1
File Hashes 046da66560472fa27ee440ad8848d4d5ba5fa5d4534d259e4b075b246459d15c123e0ab5c374db93fbb217db44ae7d5607c85c3f1b15ffb15f167bf047e829132a5d500bdee9f6e137e6276deeb8d6a72285df949ac1955b7dbfe1716ef180e9344bff5395c6f9a211cb71d860b375a2b198dddbb2fe32d68e44ac6c3253903856c3227e3308d299b95b8ca9b7929bf971a7f3db2a670ccaceb1c2340f168dce5f128da8b7deae29b301ffd710242e13130e9dc8020d5789070f1a66f48e799760065bfb14cfd680b5da509a3f464b3b101a9b62475f1197a02504491b56a8017cd473aa5b11f8cc4af2918e4521f137de198202cf72858a53e7fbbe493389948a0d4edd1bb511982d369e333f94dec04b2b0d1f78df10375dfd37bdafeb018b8db547a8527970a8775240828bacd753e5abaf413dc88065a4342e224c4cc975975afec6e6f596bb9436acc4cbad48a4d6fb199aa277333d23aa144ea6dc606c99e54f6b23efe5743ac489f039db890502ba7124084a786fb6cf7689a11a04999a3f0ac74dcfb5302554ffcf5db221664db00cc9bb8c3f6bfe6332d71dd73a569d392b285381b6a199617e09752f65c51d2b9dd7527c040e91ab5e3089893124a533d9e4e322325e6106498a053f7b53db0ecb8f1159477f7377b6160543d379a7fbf5018438537c5271612847de9d2e5e98664e025882093d8f35aa27229651d3ea351dc31b73a2f5ca3100b24f20a504ca0be7516598af09586e56d675cda3dbe0720b69f0b0692718a588be2f51380592ce968b6ac719ca3e836ddb400f4de5dfddbbc2fcc7dab0d8ea0bf0cfc8b6866b324e96b9438e9cfada79f57e9243eb97387e1cfd33b25d51b9318fbc6b67e381d91872890d46482b6943061be777ec32a982e4ccd1c155cd482799c17dd3f46dd48b43138503d70da00ec8d33a86
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Kuluoz-9996010-0 Indicators of Compromise IOCs collected from dynamic analysis of 82 samples Registry Keys Occurrences <HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'>82 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ovbbsfvk 1 <HKCU>\SOFTWARE\GJTFROFQ Value Name: cbsfpkrb 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: pssgkcqi 1 <HKCU>\SOFTWARE\JEMHQXXX Value Name: druccwlb 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ktrevmew 1 <HKCU>\SOFTWARE\PAIBDTJC Value Name: fsucsfhg 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bnemqfsa 1 <HKCU>\SOFTWARE\UHCQPKMX Value Name: amnjftbr 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: obsmbqbq 1 <HKCU>\SOFTWARE\FUNMLNOS Value Name: ccxamicb 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: qribaabm 1 <HKCU>\SOFTWARE\UVXHKNHM Value Name: utmukwxs 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: mmfrqhhs 1 <HKCU>\SOFTWARE\WHTNMNNO Value Name: kgpkwloh 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: stdrvpjs 1 <HKCU>\SOFTWARE\HLNQWSCE Value Name: rhigfktc 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: tsmmaued 1 <HKCU>\SOFTWARE\RPMOEQJV Value Name: krvhkxaw 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: jftcloae 1 <HKCU>\SOFTWARE\PFHJKKOK Value Name: vdkdftsj 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: cjaodbtr 1 <HKCU>\SOFTWARE\WKCBLJHG Value Name: idalivxm 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: saxixejb 1 <HKCU>\SOFTWARE\JTESAUDU Value Name: fddrpvdc 1
Mutexes Occurrences aaAdministrator82 abAdministrator82
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 178[.]33[.]8[.]16273 109[.]123[.]107[.]3272 74[.]208[.]65[.]13868 5[.]56[.]58[.]11864 217[.]106[.]239[.]25060 185[.]66[.]12[.]16560 198[.]199[.]101[.]1353
Files and or directories created Occurrences %LOCALAPPDATA%\<random, matching '[a-z]{8}'>.exe82
File Hashes 006528b78fb28d2ddfccc87846880a7603fed406c01ba9ac65a14b9fe4e4b1d40943e0d40826ee3196fd233f8d966155ff30d3ffc51ae7ba6d4151bdf75e9aa30aeac3cdca10f5fb66feb262f1896057d8808d5f6d6a2dc90d3432c40272f89c0b3901dbbff512ce2e5cea95adcdb41c02198a245b9d069f360552a04047c8ad0b870d2bab64958c2832a666ec088dea48bf46c91cdf42697d9614560b0d99ac0d14687696bb27d291b16761fdb9ebc03682d94e68ef8fe8d630150d3c2f03821075ad4fefa9732af3b1dd3584f4fd7bb93570392ffae76cd0dcceecb4cadbf5118440d0f8026af9287eadf3cde228043874a679a9b5df83359babc896490e5d13ed48260d638b74bac1c441b7e87cb10b3acf8a2ad1f0e60e7a7a63b6fcf528161adf6735ee7a63f5821cb261a3b1efa41c0b55e632e9628b9eb592cfaf377f1b9ac924caf478022b30f94c3c41b58036f751a600584880ef9cdcbfaed98afa1d2bb0bdadbc9dd4f0d09230db34ca476bc4e5e22ea7986e4acfd71deb08974b1decbdeb950f5051d498b5a611d00e2b8e5f19b2e2e4e28b249571a43b134fc1222e551ca310dc3d5d41acef826322a9a628fcb060cb43a6533c085101b91570247ab56ba6d2a0d2eee182f5975d03ddb1cd0775a8f5335906947353de554ba22817e589af495e5e394b082a39c7e28c7944347e43cd877aada6c5fd6f0259a82a805406bbd00bd590bccf45bb2b2a0b6e757aed1b80045b235628507d3e120a2cf3341cf3b834c8d06b841f18154789f64c3135f0f37d79a7b4631bdbb9a03131e6d9921e63a73a3c982bac40a19b98ada2cb25238ed3583e08ace72c9d248533e20e9fc75a3b18de84c9b57d7668f0d23b278e0f90ec965d21da8624f1c75d37089d441711839ac2a447ecf720c84cb932f6f41e9a35c5ec17f488360a2a463bd3cca628c72f4dda4d800e36a840a26aa11c7896ebc0c5b11bcdcc6a4e4c163becfc9252d28c2ae6383c6286efcdd83931e3203a52aff820718651684554704012d3bf788dc8e58534a97798b812caf5259db4010e43778f79b156c0526aa743abc407dd8ef1585d37b850247cbdc3ed5c31aae5b90b29ba533ba18187dcb0
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
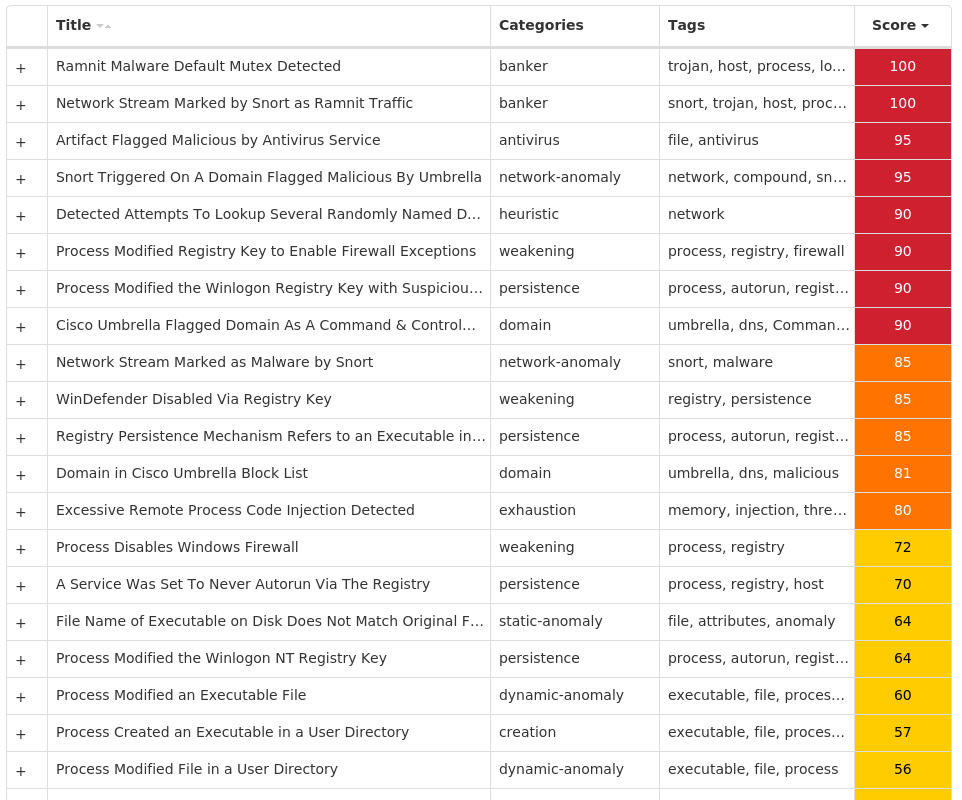
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Virus.Ramnit-9996725-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusOverride 15 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusDisableNotify 15 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallDisableNotify 15 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallOverride 15 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UpdatesDisableNotify 15 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UacDisableNotify 15 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLUA 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: EnableFirewall 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DoNotAllowExceptions 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DisableNotifications 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC Value Name: Start 15 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION Value Name: jfghdug_ooetvtgk 15 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: JudCsgdy 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 15 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Defender 15 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: Userinit 15 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: Userinit 15 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{10072CEC-8CC1-11D1-986E-00A0C955B42E}15 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{10072CEC-8CC1-11D1-986E-00A0C955B42E}\PROGID15 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{10072CEC-8CC1-11D1-986E-00A0C955B42E}\VERSIONINDEPENDENTPROGID15 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{10072CEC-8CC1-11D1-986E-00A0C955B42E}\PROGRAMMABLE15 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{10072CEC-8CC1-11D1-986E-00A0C955B42E}\INPROCSERVER3215 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{10072CEC-8CC1-11D1-986E-00A0C955B42E}\COMPONENT CATEGORIES15
Mutexes Occurrences {7930D12C-1D38-EB63-89CF-4C8161B79ED4}15 {79345B6A-421F-2958-EA08-07396ADB9E27}15
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 46[.]165[.]254[.]20114 72[.]26[.]218[.]7014 195[.]201[.]179[.]20714 208[.]100[.]26[.]24514 104[.]247[.]81[.]5014 206[.]191[.]152[.]5814 72[.]251[.]233[.]24514 142[.]250[.]65[.]17414 104[.]247[.]81[.]5414 104[.]155[.]138[.]215 104[.]154[.]244[.]2445 35[.]205[.]61[.]674
Domain Names contacted by malware. Does not indicate maliciousness Occurrences google[.]com14 testetst[.]ru14 mtsoexdphaqliva[.]com14 uulwwmawqjujuuprpp[.]com14 twuybywnrlqcf[.]com14 wcqqjiixqutt[.]com14 ubgjsqkad[.]com14 iihsmkek[.]com14 tlmmcvqvearpxq[.]com14 flkheyxtcedehipox[.]com14 edirhtuawurxlobk[.]com14 tfjcwlxcjoviuvtr[.]com14
Files and or directories created Occurrences %LOCALAPPDATA%\bolpidti15 %LOCALAPPDATA%\bolpidti\judcsgdy.exe15 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\judcsgdy.exe15 \TEMP\w8g8q2315
File Hashes 023667489cef9b0ce5af2a16783c4547ca4cb07177f34eb8f696a9311fcf57ab0911754d2b604000a0894f0de686da528545dca73111ce2ba2384a17f662e0fd0c075593881ed13d0cdb01f54813314b6fa6a6deea7361d065e35365387ce62b0eb742b6fcb54625a90aec571cf3ef2b5eb0ad19b7733c6aa5a3590847e0e91f1611b206305e0ec80061db00c4db19b20e9bc249691f0d35d45e3bde1a9f9bdc65ce48f32ef6e5fb78a07d84d5b0610f4d36267338bbc8d29dea29a89b4fe7476792a7c3ae1d888c0b4ba4fa20dfa9f0a07b395df851746f2bb48b7df49633be7da9a5d98ad3cf7f25a922212f99973442faa0a44a513b0692a1673a4d9e64dd7e0d36ff19dd6e128553d0e84e6190762c2c7e9eb7bb2d5b128031d14a41c3aebcc8e89f485fbcaaac9084a7a13612fb41015f83dd1ca58eecd21b04e5e5cde9bfd9ca4508b5be3c9836de05aa30adbb432edfd00ad63e40a53d4bb0b7264c44c6dfa0af563bbe3b10e0994c9d558e25cb0e00f0b6509de1fefe54243513d617d86bf52733b337fba829388408022b78b0fedfe31002ddc95c189cf1194e7eddf6254bf8efa6a6cf308ed5ed01f3c8a77d280f99a05f28914a3bd399796474edf9f242d29e8a2ac4f3bc88bd806789db635463933e624061a996eafd0f654859
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.XtremeRAT-9996042-0 Indicators of Compromise IOCs collected from dynamic analysis of 34 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 9 <HKCU>\SOFTWARE\XTREMERAT8 <HKCU>\SOFTWARE\XTREMERAT Value Name: Mutex 8 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKLM 7 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKCU 7 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5460C4DF-B266-909E-CB58-E32B79832EB2} Value Name: StubPath 7 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5460C4DF-B266-909E-CB58-E32B79832EB2}7 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: FaviconPath 4 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: Deleted 4 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES Value Name: DefaultScope 4 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}4 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: @explorer.exe,-7001 3 <HKCU>\SOFTWARE\((MUTEX)) Value Name: InstalledServer 2 <HKCU>\SOFTWARE\((MUTEX))2 <HKCU>\SOFTWARE\LG3XWSUBC2 <HKCU>\SOFTWARE\LG3XWSUBC Value Name: InstalledServer 2 <HKCU>\SOFTWARE\LG3XWSUBC Value Name: ServerStarted 2 <HKCU>\SOFTWARE\((MUTEX)) Value Name: ServerStarted 2 <HKCU>\SOFTWARE\--((MUTEX))-- Value Name: ServerName 1 <HKCU>\SOFTWARE\--((MUTEX))--1 <HKCU>\SOFTWARE\YDRYS1 <HKCU>\SOFTWARE\YDRYS Value Name: ServerStarted 1 <HKCU>\SOFTWARE\YDRYS Value Name: InstalledServer 1 <HKCU>\SOFTWARE\--((MUTEX))-- Value Name: ServerStarted 1 <HKCU>\SOFTWARE\472JCD5PAHK2A11
Mutexes Occurrences Global\<random guid>26 XTREMEUPDATE6 --((Mutex))--3 --((Mutex))--PERSIST2 ((Mutex))2 ((Mutex))PERSIST2 ((Mutex))EXIT2 lg3XwSubC2 lg3XwSubCPERSIST2 lg3XwSubCEXIT2 --((Mutex))--EXIT1 MTLr7L9MtcTpsCpM1 ydRYs1 ydRYsPERSIST1 ydRYsEXIT1 Ed3e7ynAP8WK1 472jcD5PaHK2a11 Y26rKQLRp3E1 Ed3e7ynAP8WKPERSIST1 Y26rKQLRp3EPERSIST1 GAFwYEaQ1 GAFwYEaQPERSIST1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]127[.]184[.]494 23[.]202[.]2[.]1054 13[.]107[.]21[.]2001 204[.]95[.]99[.]1091
Domain Names contacted by malware. Does not indicate maliciousness Occurrences go[.]microsoft[.]com4 www[.]bing[.]com4 learn[.]microsoft[.]com4 fons[.]no-ip[.]info2 mda[.]no-ip[.]org1 yoyo86[.]no-ip[.]biz1 raouf-tnt[.]no-ip[.]biz1
Files and or directories created Occurrences %TEMP%\x.html10 %SystemRoot%\InstallDir6 %SystemRoot%\InstallDir\Server.exe4 %APPDATA%\Microsoft\Windows\((Mutex)).cfg2 %APPDATA%\Microsoft\Windows\lg3XwSubC.cfg2 %SystemRoot%\InstallDir\Micro.exe2 %APPDATA%\Microsoft\Windows\lg3XwSubC.dat2 %SystemRoot%\SysWOW64\InstallDir1 %APPDATA%\Microsoft\Windows\--((Mutex))--.dat1 %APPDATA%\Microsoft\Windows\.cfg1 %APPDATA%\Microsoft\Windows\ydRYs.cfg1 %SystemRoot%\SysWOW64\InstallDir\System.exe1 %APPDATA%\Microsoft\Windows\ydRYs.dat1 %APPDATA%\Microsoft\Windows\472jcD5PaHK2a1.dat1 %SystemRoot%\InstallDir21 %SystemRoot%\InstallDir2\Server.exe1
File Hashes 132c72181b8a778376133aa889fcebb5c5a4473d859fe08a47fa5b47aa56dac31d9f624473789656a5401c9e4c1a69f2c8e6cafa7e9444186719d2988651889a1e1b1c83eed0322f7e7676602e3bce5dc6bc283c5931d388322e5b6637bbe9ad1f059d9c92056bd3613c92c4ecca413cd83b9217d5c098d3dc5fff0ab75e2825205d64176dd361806008a7fa2019143c4cb530d33046e8a9e21745a565abd5e4231288d8568c0d3d517b1d8c44b6f68da8d9bb59382e4f02dd8bb8518bead48f251984feea5278328400793066e5ef6ea6da37dde5510fce20b2967c6c53217925352138d86a5759260e222c105a1a6b5a0507da77af90f61712b9409458a8cd2d375c5461cf1e8b328acbb9bf2d24200cbfc3cdab72b6ad7e1ecc21d1f623dd3501684ecc4bee8ac81ff50a9810b8718740d5d3cd5e901d761ad6bdb462a47c45ccdcacb23684fbdaac5bc97f33499c9502c83d90196d0edec69ddb7f60e5c55a1d1559b7c7dd6098f0bf5c384446848748928ea9d894dffa172278a58594e45de044683cfa0784690988e86177360fb75a3df3665f474cf6e74598b3a8517e5f5ada2d424b5b51b15844604bb591bcc590997b26be6a4193837f7d712a7f1661e5012b4acffb042e49a33a469d9017cd8f2dc9501c6f0bd303eb3536eaba976dcb98c07550e7dd9ac5d7adb9b7250b055b260897df1a96c509c6f7d18484c477973bbd8c69532536d12ef04b2a1f01dfd22f7abe3729de519f139f9a56f83c80518969b3419c0030e216c73ed493c550125ce2b00622463bbb74bb56fdf1b9837211fabd2d34904e006e00b08eaf54fd2f4b36417853f84218d46658ae220d8378faa88efcb53205abfad7a2707d4b4832db33db78f26592f91c4147a02a19880d6cf77bad0fb370b4932795c6470499a16532a55ebebacf9b672c71173464a0ca439ed3d0722ef01c887c8b58d2faa0bedce051d45544fbef9be19961f383a196e5354890e9360e0b1885d163aaeb850da8f687980104467d082c64639a32a6eb0d8fe971628d04c2d660ebf54380bc6fa2525572f75e222b836463ec56f1aa2602750800ec6d8f2b31e77f6754bfa697e028bd8769bb49ba4ceddebf3d85
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.TinyBanker-9996101-1 Indicators of Compromise IOCs collected from dynamic analysis of 12 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: DA81EF4C 12
Mutexes Occurrences DA81EF4C12
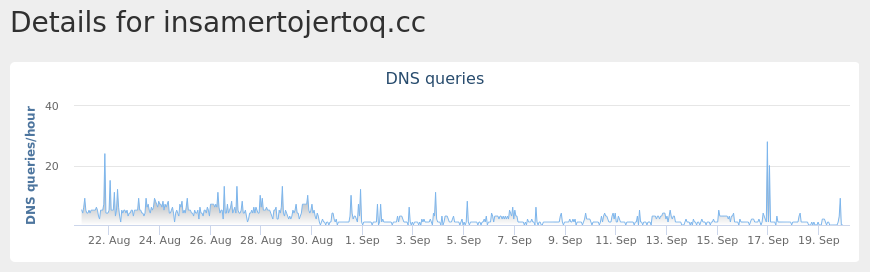
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]google[.]com4 insamertojertoq[.]cc4
Files and or directories created Occurrences %HOMEPATH%\AppData\LocalLow\DA81EF4C12 %APPDATA%\DA81EF4C12 %APPDATA%\DA81EF4C\bin.exe12
File Hashes 04b2c67a6cf8f2e636fcaf527ca0521044ba4515b4eddaf197d39c754b00d73804eade6496885d483398f72945aa81cb5dc2d06cc1c33c7d10f93a37bd6e5b9c1654bf09b2b92e846968199c088c77e3f1ee27d10b8f637cf4403a40544ba9d14c122eef70ee516c9d4a20ebe5193097fe368efdf98ffa83ca0c31b629c25b865f0a35567959443f7829921cdecb2074e256dd6278fd9e23eccc3143098c7d2569a50411cd516669a169ac67660176bec242a6ef9bdf65c8cbaa2b2b8c09e5766c0011015815d10317fb49e14f3d19035e36f960bc536e2190c063003ad415a2924679e979e6d335fd216cd053c823d6a79ca2723483fc3db2a2b61a9417c0a1b11bf65aaafb001c41302ce9b1922099ceb3bb468fa27fe3fe470ad09cf515cfbbbe2b6336209e71a102e57fb22e4cb7f28a3ea74122f8260869becf1fb36ec4cff1b9c7195661422d1357cca73e56d924983f17f9d3b95ba2c44612a53e4aedf431fa85df46d0f3bce71d7623a9b6eaa8417b41fd39dd7297136ed8eb47b05c
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics Umbrella MITRE ATT&CK