Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 14 and April 21. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
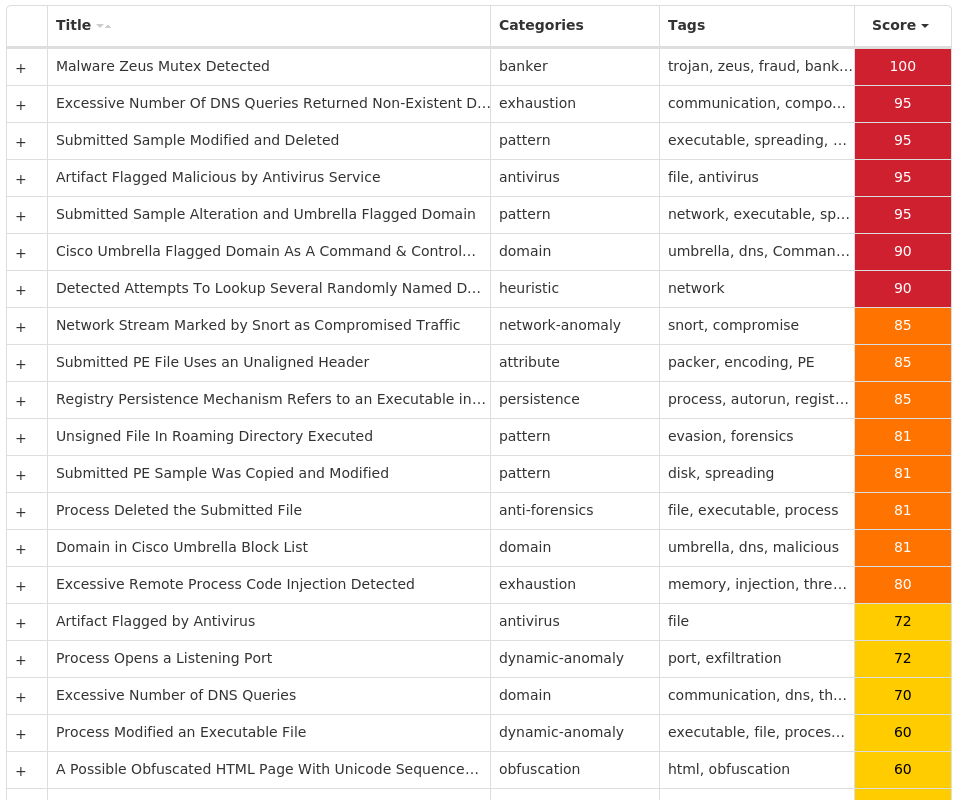
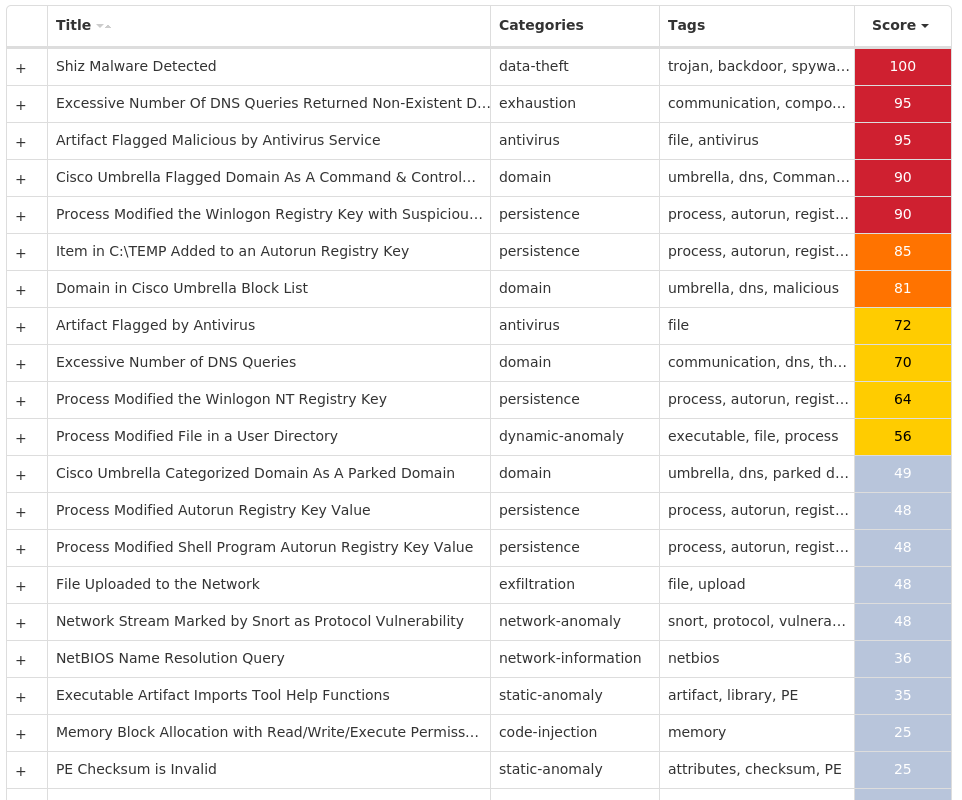
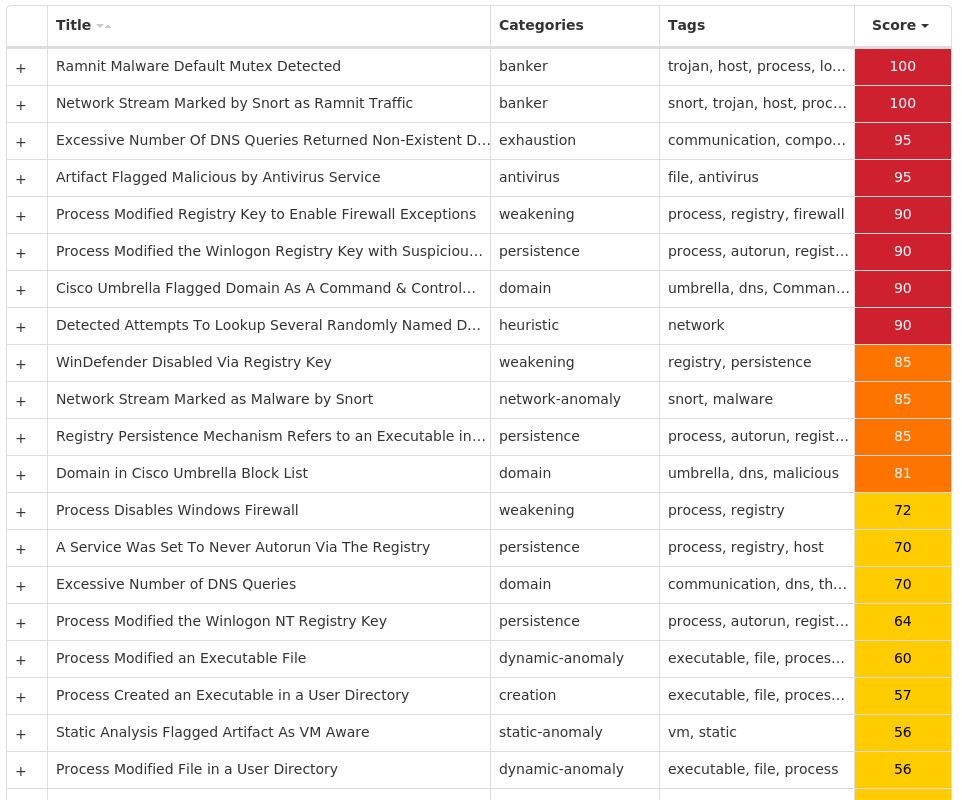
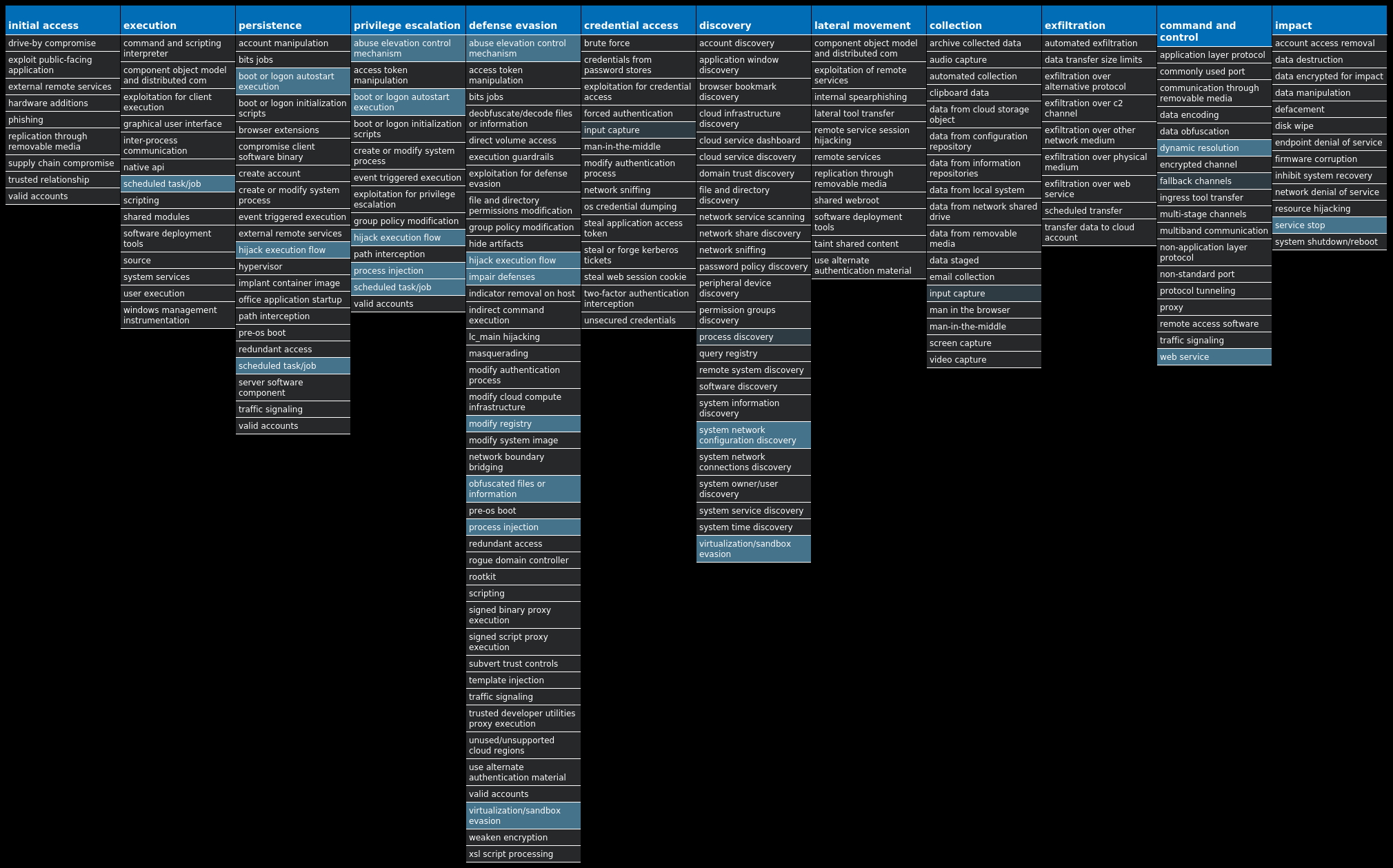
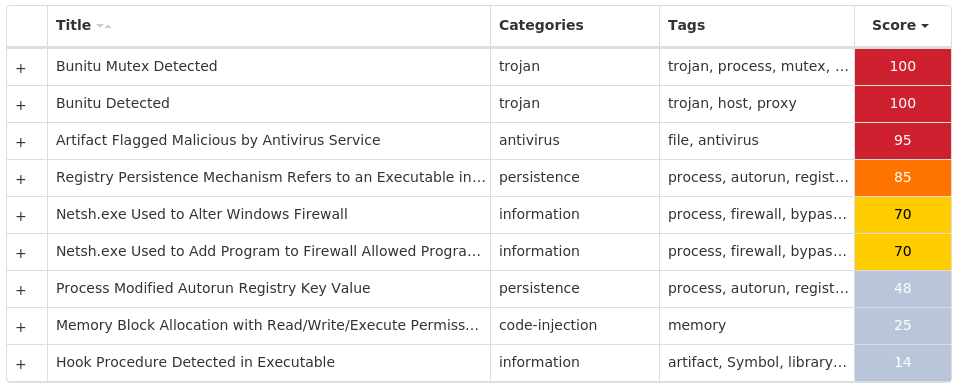
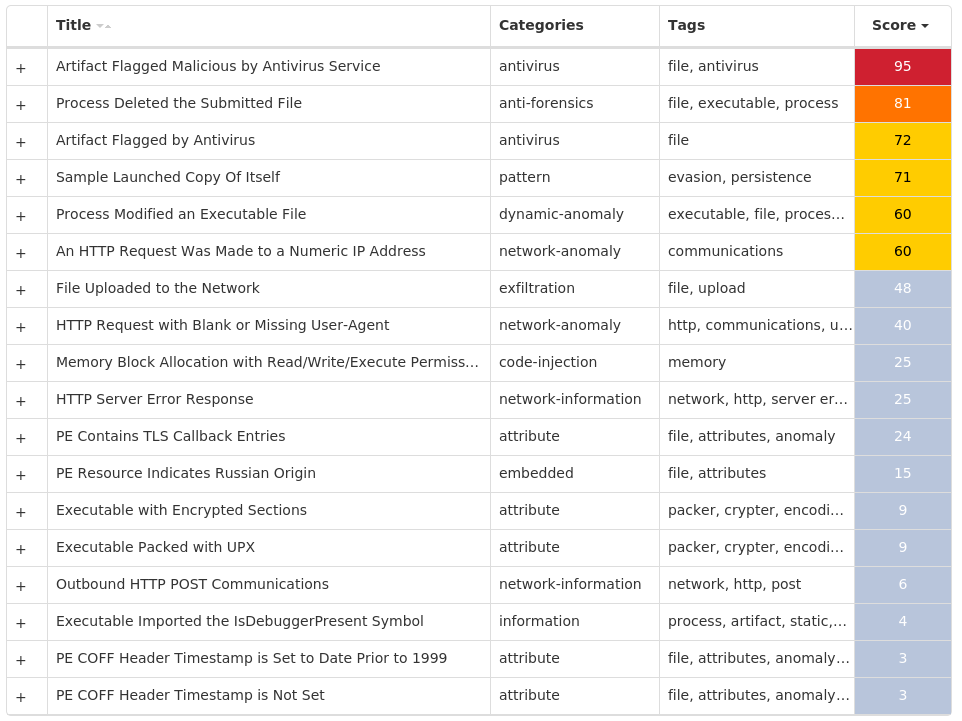
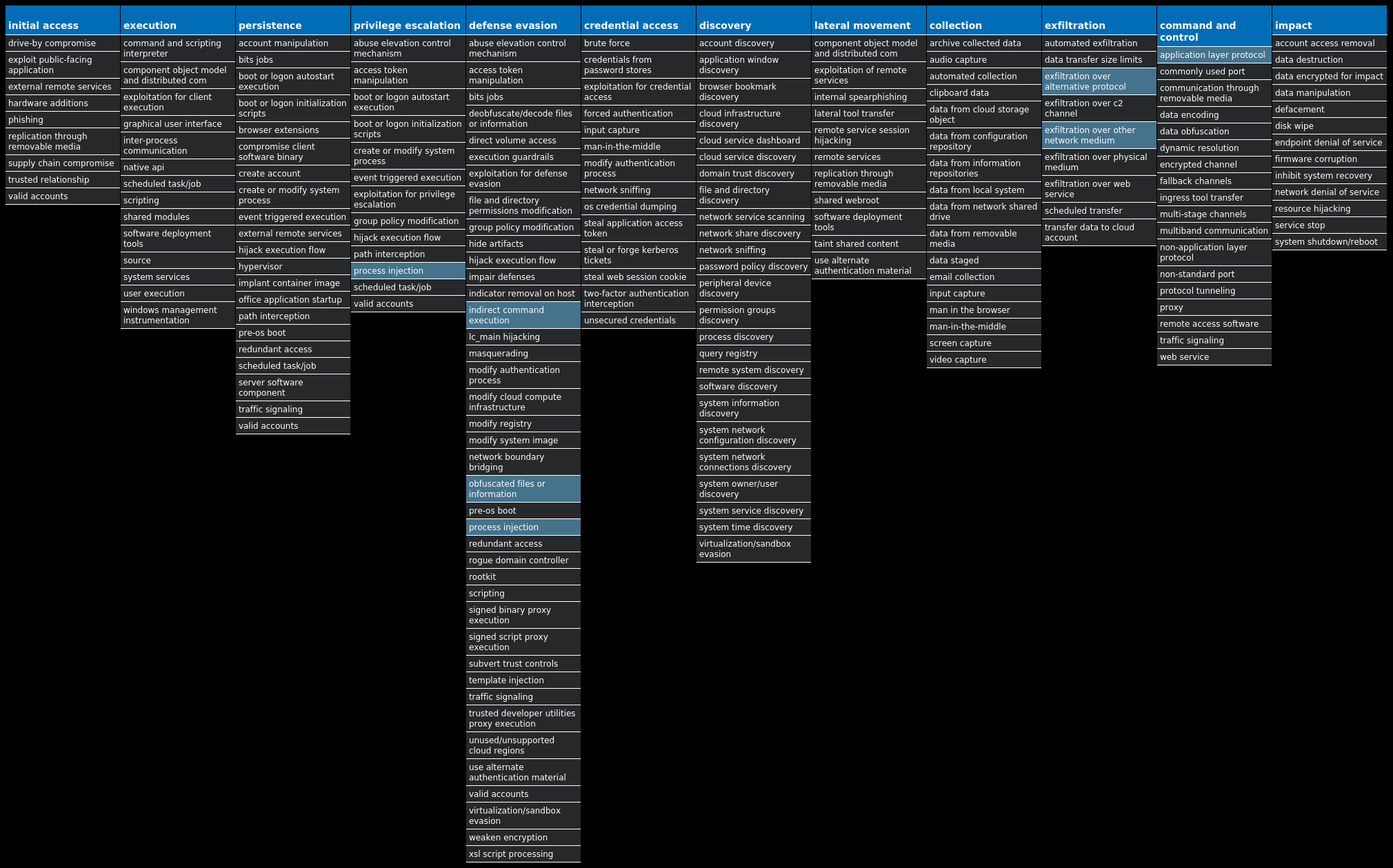
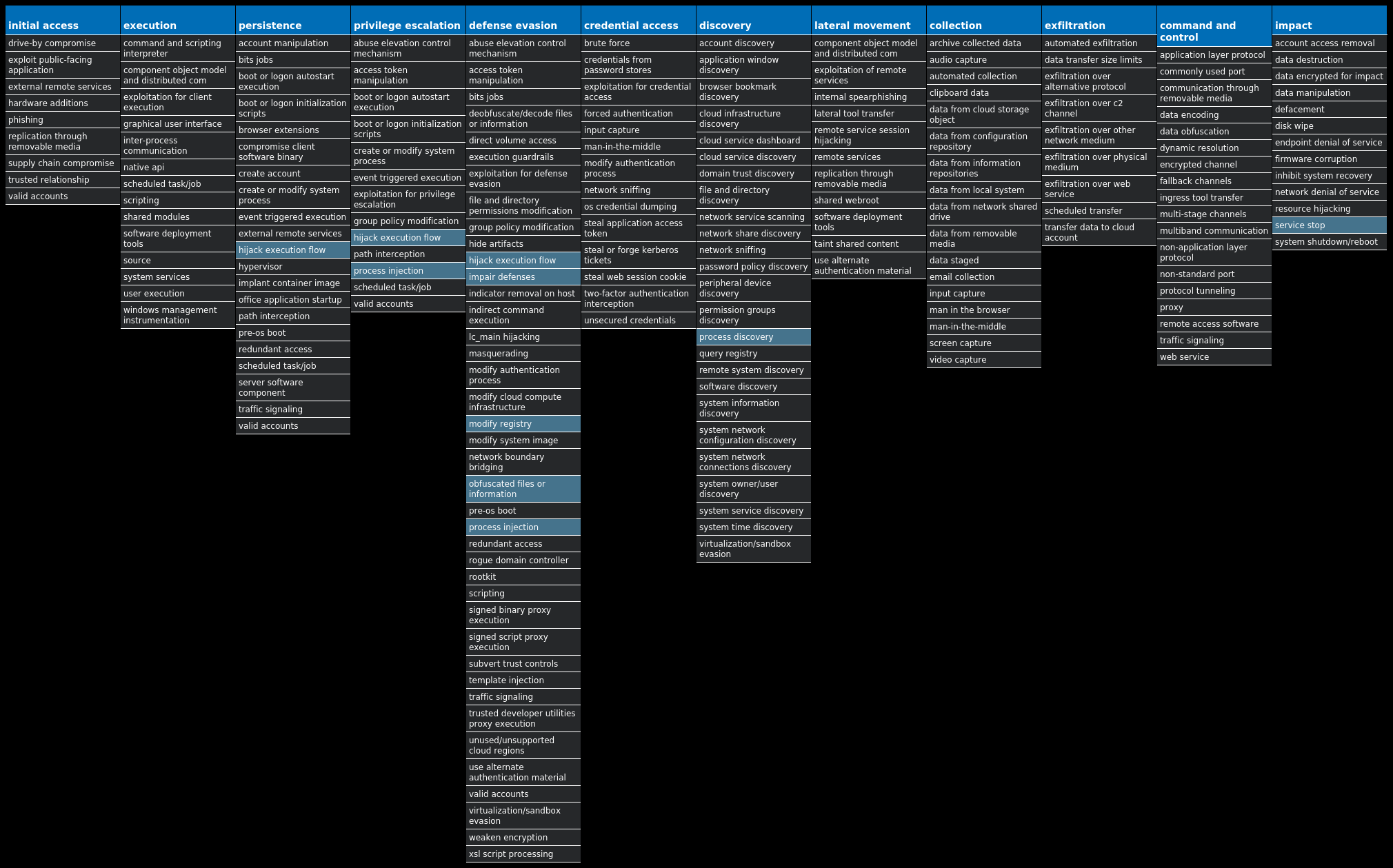
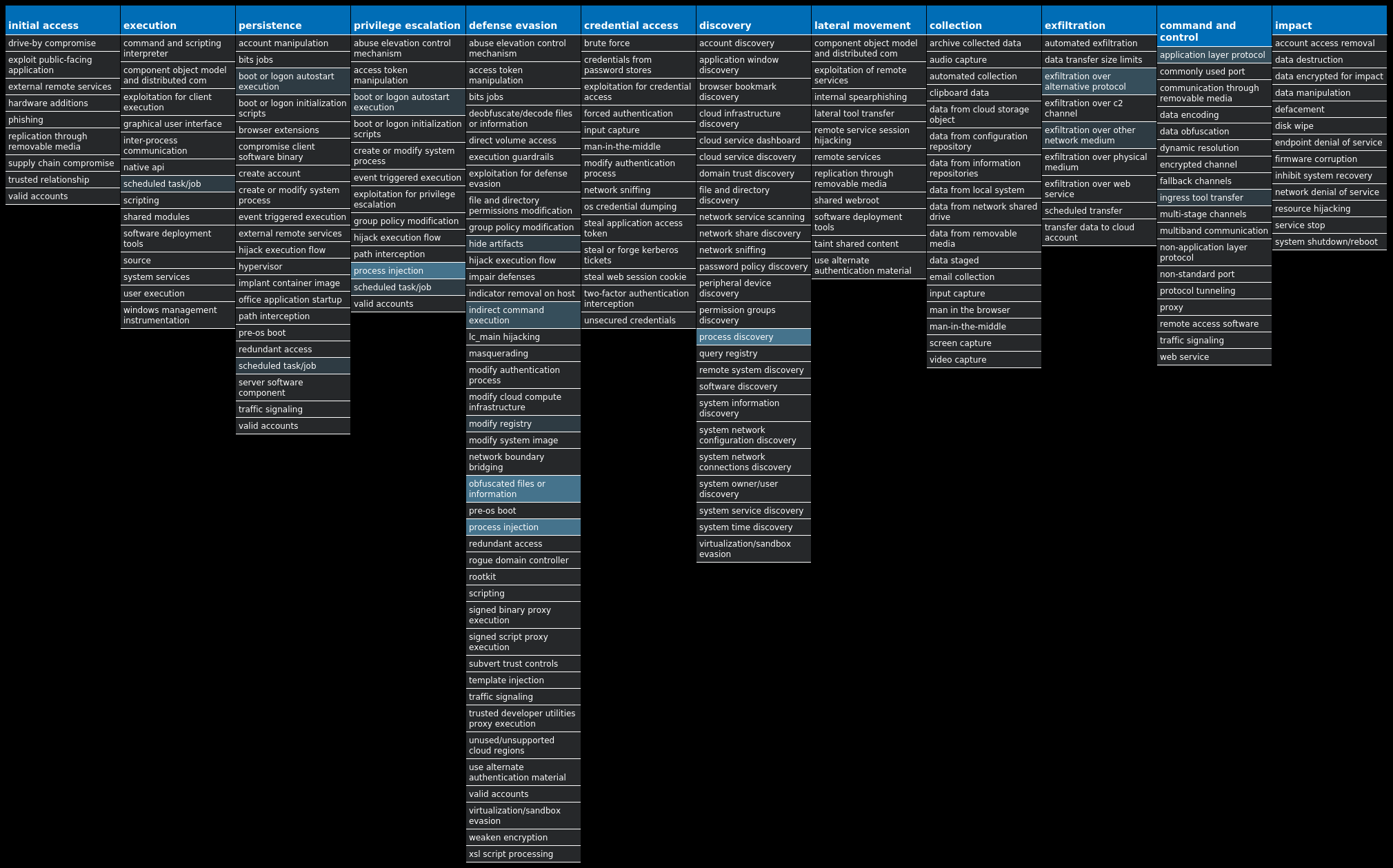
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.Zeus-9997235-0 Dropper Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing. Win.Dropper.Shiz-9997181-0 Dropper Shiz is a remote access trojan that allows an attacker to access an infected machine in order to harvest sensitive information. It is commonly spread via droppers or by visiting a malicious site. Win.Virus.Ramnit-9997053-0 Virus Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It also can steal browser cookies and attempts to hide from popular antivirus software. Win.Dropper.Bunitu-9997037-0 Dropper Bunitu is malware that establishes a persistent foothold on an infected machine and then turns it into a proxy for criminal VPN services. Win.Trojan.Vobfus-9997065-0 Trojan Vobfus is a worm that copies itself to external drives and attempts to gain automatic code execution via autorun.inf files. It also modifies the registry so that it will launch when the system is booted. Once installed, it attempts to download follow-on malware from its command and control (C2) servers. Win.Dropper.DarkKomet-9998118-0 Dropper DarkKomet is a freeware remote access trojan released by an independent software developer. It provides the expected functionalities of a trojan, such as keylogging, webcam access, microphone access, remote desktop, URL download and program execution. Win.Ransomware.TeslaCrypt-9998112-0 Ransomware TeslaCrypt is a well-known ransomware family that encrypts a user's files and demands a Bitcoin payment in exchange for a file decryption service. A flaw in the encryption algorithm was discovered that allowed files to be decrypted without paying the ransomware, and eventually, the malware developers released the master key allowing all encrypted files to be recovered easily. Win.Dropper.Ryuk-9998099-0 Dropper Ryuk is ransomware known for targeting large organizations and asking for rather large ransom payments to recover the encrypted files. The infection has been associated with emails that contain malicious attachments that first deliver Emotet, which is used to deliver modular payloads such as Ryuk. Ryuk encrypts a user's files using AES-256 + RSA2048 encryption algorithms. Win.Dropper.Tofsee-9998087-0 Dropper Tofsee is multi-purpose malware that features multiple modules to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency and more. Infected systems become part of the Tofsee spam botnet and send large volumes of spam messages to infect additional systems and increase the size of the botnet under the operator's control.
Threat Breakdown Win.Dropper.Zeus-9997235-0 Indicators of Compromise IOCs collected from dynamic analysis of 19 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: {2EC645E8-BA31-AD44-55BA-04D54CAC27C8} 9 <HKCU>\Software\Microsoft\<random, matching '[A-Z][a-z]{3,11}'>9 \MICROSOFT\WINDOWS\CURRENTVERSION\RUN1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\XMLPROVI1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\XMLPROVI Value Name: EnableFileTracing 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\XMLPROVI Value Name: EnableConsoleTracing 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\XMLPROVI Value Name: FileTracingMask 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\XMLPROVI Value Name: ConsoleTracingMask 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\XMLPROVI Value Name: MaxFileSize 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\XMLPROVI Value Name: FileDirectory 1 <HKCU>\SOFTWARE\MICROSOFT\ITDOO Value Name: jei6ha 1 <HKCU>\SOFTWARE\MICROSOFT\ITDOO Value Name: 2363bdic 1 <HKCU>\SOFTWARE\MICROSOFT\XUXO Value Name: 20ij6d32 1 <HKCU>\SOFTWARE\MICROSOFT\XUXO Value Name: f82b704 1 <HKCU>\SOFTWARE\MICROSOFT\ITDOO Value Name: 4b91d34 1 <HKCU>\SOFTWARE\MICROSOFT\XUXO Value Name: 1h72e0hc 1 <HKCU>\SOFTWARE\MICROSOFT\NAYRU Value Name: a3572fh 1 <HKCU>\SOFTWARE\MICROSOFT\NAYRU Value Name: 1dc39c87 1 <HKCU>\SOFTWARE\MICROSOFT\NAYRU Value Name: deieaab 1 <HKCU>\SOFTWARE\MICROSOFT\UXYCIB Value Name: 134i55g1 1 <HKCU>\SOFTWARE\MICROSOFT\UXYCIB Value Name: 36dbj54b 1 <HKCU>\SOFTWARE\MICROSOFT\YWUN Value Name: 18ifc40i 1 <HKCU>\SOFTWARE\MICROSOFT\YWUN Value Name: 2cbcb7fc 1 <HKCU>\SOFTWARE\MICROSOFT\UXYCIB Value Name: j89hi4f 1 <HKCU>\SOFTWARE\MICROSOFT\YWUN Value Name: 1ce82898 1
Mutexes Occurrences Global\{C30C6CF2-932B-408E-55BA-04D54CAC27C8}9 Global\{73DE6ED9-9100-F05C-55BA-04D54CAC27C8}9 Global\{A9348FD8-7001-2AB6-55BA-04D54CAC27C8}9 Global\{A9348FDF-7006-2AB6-55BA-04D54CAC27C8}9 Local\{C8D239CA-C613-4B50-55BA-04D54CAC27C8}9 Local\{C8D239CB-C612-4B50-55BA-04D54CAC27C8}9 GLOBAL\{<random GUID>}9 Local\{<random GUID>}9
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 194[.]94[.]127[.]989 69[.]39[.]74[.]69 24[.]120[.]165[.]589 108[.]211[.]64[.]469 184[.]156[.]76[.]1589 155[.]212[.]138[.]699 142[.]176[.]125[.]2039 99[.]68[.]30[.]829 96[.]57[.]35[.]1099 71[.]42[.]56[.]2539 94[.]67[.]185[.]1889 199[.]243[.]220[.]2189 64[.]219[.]121[.]1899 87[.]203[.]112[.]1749 85[.]9[.]95[.]2059 151[.]49[.]166[.]2069 99[.]95[.]152[.]2269 50[.]72[.]177[.]249 66[.]117[.]77[.]1349 142[.]250[.]176[.]1968 13[.]107[.]21[.]2001 142[.]250[.]80[.]41
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]google[.]com9 www[.]bing[.]com6 augqwshaypbydxjnhacugqqgbumvf[.]ru2 lreurwknkfwcmfwgscpkzcmdefypcy[.]com2 twonmtauydnwxbmzkbsgxktjf[.]info2 eqojlqstdeaionpvaigqdmypsvsyt[.]org2 cqfyyvzamxgmhamfxobetxnr[.]biz2 yirkqgytovhonwydeqsoqst[.]com2 lnsouqsusztaofgeukxjffyh[.]ru2 uowomfpnbipvolovjvsdmfqhsg[.]com2 dmcmxtdmfqfqbeijzhnvjffylmz[.]net2 rcvwscythudbipnpnobvokzfebinrmf[.]biz2 iblmbdabelugdajziguxxw[.]info2 mjfedmhfutpztdhaqlxmvxwmz[.]com2 dtgrwuscefqzpvhubonbgyg[.]ru2 lnssgkjlxwdulhicyqgushe[.]com2 hizmnqcgqgeykrlrcauaemblib[.]biz2 tdskkbweageifhpwthiemeqt[.]org2 diwtoymnmyxsxrgaqkdal[.]net2 fydetkrvwxgibmxytugpbbetd[.]com2 cetoxhsphljhuayrkvpbdy[.]biz2 xmbgykaidyhunvvvxodyy[.]com2 qkcmfelbnzlganjmfzhirouw[.]ru2 xwugqrgvxnfwcjrsvcbuxseifp[.]com2 ifillfjraywgsgscmscknplp[.]net2
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\tmp<random, matching '[0-9a-z]{8}'>.bat9 %APPDATA%\<random, matching '[a-z0-9]{3,7}'>9 %HOMEPATH%\AppData\LocalLow\<random, matching '[a-z]{4,6}.[a-z]{3}'>9 %APPDATA%\<random, matching '[A-Z][a-z]{3,5}\[a-z]{4,6}'>.exe9
File Hashes 22f805038c3cf048156fdb1232bb8cee4bd46ab32af79d733bba311fc4b61e94250c240a2a8fc8c12f4a93d56c1926ff4f898a4970bc15a11a39eb50d1fc58ce323a57e10f9a124a22314c6137a9b5553f09537f79218c791534ca1ede0aa62b34804aacde53e35cdd4385943d77c879d0f0e58b62ce3429d59d610ba1b883ba421c7692476fd1a7bac73115b1c081c56b20be1bb191d3e228f40bc888de06c8559322ef31c95e8d2498bfeb17ea4c59f207bc6dc2750b76f9aec259afd8e1c86041834d9b3ced19bfc7bd2ed783082c3dafb0f19e4b67541efa0a01c7cfe6a06053302c79b74edbccb9750dea999b799be5e7c409c95bf12322ac83f160897480e3631309c690416b75f24fba4a43040adb7f79569d3bd87940a02e089bc3d1871dfa1ef60d5752755abee6091e67ceaa397ac3accab8a637c16a0bca9e1dc78e22b8f7059b91ae11964886a0f38b7bc743d6a6ca0b7df4975f81552ff0edd6a9692a8a8cf4be472bb45df0265ced1f9f30b23bfbbb9a523df1e64576dbb4e5d03856840b3826ff1dd9add0d5cce68285c9135ea573ed935c3e622968695be3d5e284410ffc8331c5b99940b6f1bc77c0c7d29445de7ad33d625f1ebd63ea08d6134594f22e2a9cff602184ab018753a180f24752393d793586d0ea4c91fce2d846df9dbc6c9d7010e3fd4d2c1cf5ce42adaa24b832d1f1ed7a5604f5f5956dda90e2724c3a78816be07d03baa5344bc7c4e468c3fd14b5af057de9ae4f930edae2db72eb2064f7aec14bf503b279d9a7850804f4f2ee6878c97cd1f6a8f282fc805d6dc870722b1db4c706aa369fdea4c19fc0fa58543e06d4bfe2342aeb1f
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
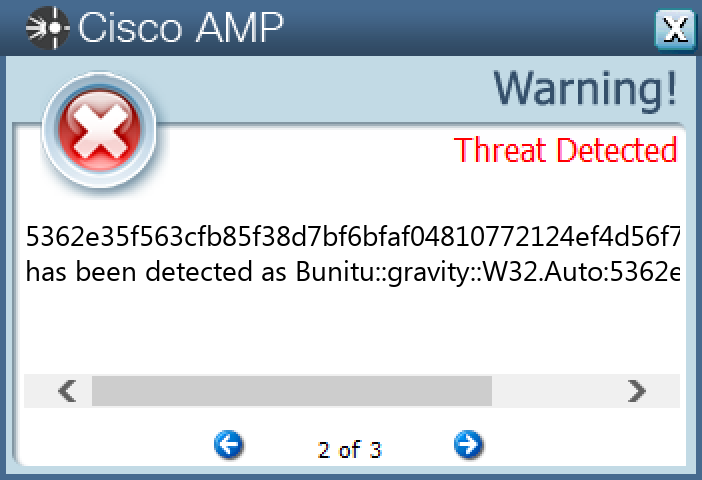
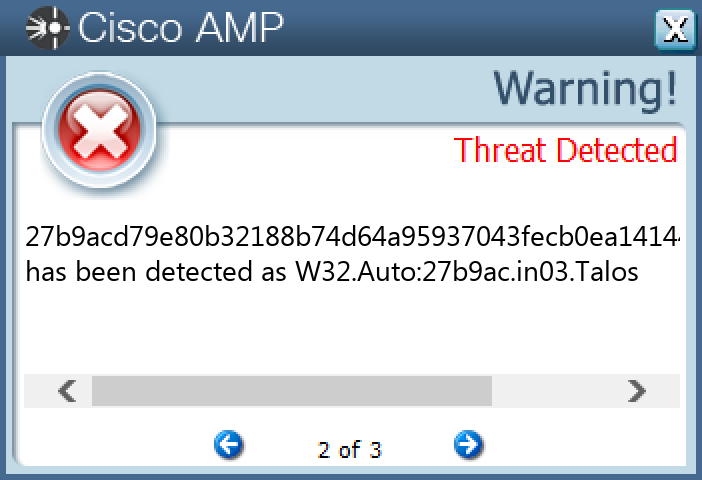
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Shiz-9997181-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT Value Name: 67497551a 15 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: 98b68e3c 15 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: userinit 15 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: System 15 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: load 15 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS Value Name: run 15 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: userinit 15
Mutexes Occurrences Global\674972E3a15 Global\MicrosoftSysenterGate715 internal_wutex_0x000004b415 internal_wutex_0x0000043c15 internal_wutex_0x000004dc15 internal_wutex_0x<random, matching [0-9a-f]{8}>15
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 85[.]94[.]194[.]16915 13[.]107[.]21[.]20010
Domain Names contacted by malware. Does not indicate maliciousness Occurrences qekafuqafit[.]eu15 ryhyruqeliz[.]eu15 kejepujajeg[.]eu15 tufibiqunit[.]eu15 lygumujycen[.]eu15 xudoxijiwef[.]eu15 pupoliqotul[.]eu15 citahikodab[.]eu15 direfiwahur[.]eu15 vowypikelaf[.]eu15 foqurowyxul[.]eu15 nomimokubab[.]eu15 ganovowuqur[.]eu15 mavaxokitad[.]eu15 rylupalyxad[.]eu15 jecekorosuk[.]eu15 lykiwaryvuk[.]eu15 qexeholagav[.]eu15 tujomalumav[.]eu15 vopudetezuq[.]eu15 rycodypycym[.]eu15 cilicofahev[.]eu15 vojajofyced[.]eu15 dikolobeliw[.]eu15 fogefobunik[.]eu15
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\<random, matching [A-F0-9]{1,4}>.tmp15
File Hashes 0315c6bad516fdbca0ec18505aab2fd489f8cae3b1a88480324024e8c0d4dc94032ce1ee56f2fbf5edd3598b81b0a8d2b0d763c6be2b2c45b605216ed48ff7b24d65ee2c89ec77eb0154380541883d8f0b0ffb7ed963421757650eccdca3f90354f74995c8ac50adf9e4d6914943c5dee2450012505cac20f3f9b2ffd8848c917d7a3f2f220e48278e1996c2b8c1df759c5fbc5c420709b16ce352c9a5d5ce657efb62037a6458aded75c10bd1b48dc6c93efed5e9311ff778f5ab3332f476d3849d628ae1ff1e2be87ff7b9a7d5c0561d3a4108b89fecd6450c6080a0621a6986a5d335eabd578d0eabb186e910e9909e4b0e1875c56d8f7ebc879d8f8f36a5a8b8e9d1707759a6d198a2936d0a70f2ee39cd885c5277825981032dc11d8997b1057720ef4c01ad319f0ee782790b2a4cea3ffc1abb5e7a7bc2062d734150c5b2dc0b7dbe88b8e45abc085b9c5ae9779b2ce1de6ddc8ae38377f4c878bd7c78b68fee6ee5495b079fe6dc4347290937c9754728f489cdab49cd5fd417177d24ce3a9e9d184c355a9157a234e9a4ee1c4891d0f93bfb1c9b3455ebf3acf2fb7ccec3dcaa3e9eeec33f29aaa4d3a949ffe34c5e9e688cd997ef344d554ca40de7dae231c71c6fa7ee7eb4adcf91a194167e04c6a2ec2534925021e22e70c4a2f7
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
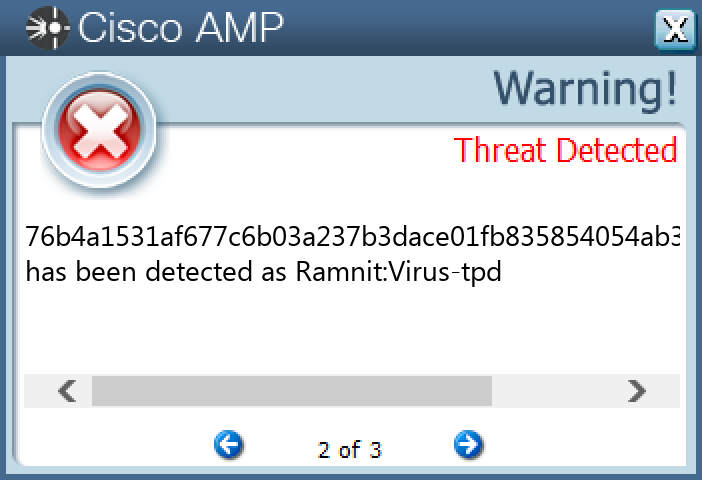
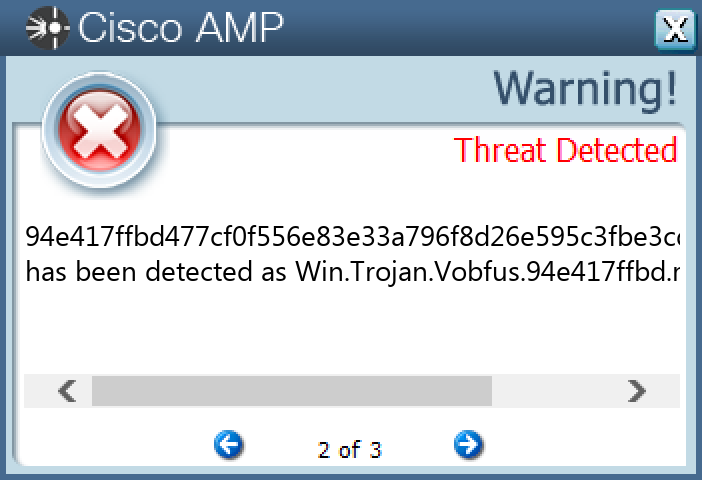
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Virus.Ramnit-9997053-0 Indicators of Compromise IOCs collected from dynamic analysis of 11 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusOverride 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusDisableNotify 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallDisableNotify 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallOverride 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UpdatesDisableNotify 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UacDisableNotify 11 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLUA 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: EnableFirewall 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DoNotAllowExceptions 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DisableNotifications 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC Value Name: Start 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION Value Name: jfghdug_ooetvtgk 11 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: JudCsgdy 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Defender 11 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: Userinit 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: Userinit 11
Mutexes Occurrences {7930D12C-1D38-EB63-89CF-4C8161B79ED4}11 {79345B6A-421F-2958-EA08-07396ADB9E27}11
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 142[.]250[.]65[.]17411 195[.]201[.]179[.]2079 208[.]100[.]26[.]2459 35[.]205[.]61[.]679 72[.]26[.]218[.]708 206[.]191[.]152[.]588 46[.]165[.]254[.]2017 104[.]247[.]81[.]507 72[.]251[.]233[.]2457 104[.]247[.]81[.]547 46[.]165[.]220[.]1451 217[.]20[.]116[.]1401 173[.]231[.]184[.]1221 199[.]21[.]76[.]771 64[.]225[.]91[.]731
Domain Names contacted by malware. Does not indicate maliciousness Occurrences google[.]com11 testetst[.]ru9 mtsoexdphaqliva[.]com7 uulwwmawqjujuuprpp[.]com7 twuybywnrlqcf[.]com7 wcqqjiixqutt[.]com7 ubgjsqkad[.]com7 iihsmkek[.]com7 tlmmcvqvearpxq[.]com7 flkheyxtcedehipox[.]com7 edirhtuawurxlobk[.]com7 tfjcwlxcjoviuvtr[.]com7 otdwndjgsva[.]com1 pldatiuumyt[.]com1 prgmrqjhwu[.]com1 qcskrkqk[.]com1 qihksfkx[.]com1 retnjlfw[.]com1 rgiqbupr[.]com1 riayppnnk[.]com1 ryonuefbyx[.]com1 tcxkbjutij[.]com1 tfjmhkaluy[.]com1 tmergqcjkde[.]com1 ubnlwvgc[.]com1
*See JSON for more IOCs
Files and or directories created Occurrences %LOCALAPPDATA%\bolpidti11 %LOCALAPPDATA%\bolpidti\judcsgdy.exe11 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\judcsgdy.exe11 \TEMP\0OwAGLh4 \TEMP\eWGQvZDz52 \TEMP\Mx0nJh32 \TEMP\emf1 \TEMP\Z9PJGNNd1 \TEMP\9CqjBXH3x1 \TEMP\yvQIHJ1P61
File Hashes 09055a88d6d26119fe3f4ac9dc6141758707d29728a052aae24c2f5420e63e3f10f7326ddfa4efba4045522b6a302759ce6676b7a010a7ecc35a6564d007c34513b7c8e7f6c8b6093ca1a841736a150ca39509f97f65e4df0fa4e2574007994631d3c7955e6b2f749d894826b843158ba8e9889ad2e2851f8224fdb3f7c9cd744221ef633be6b47753cf0c965059d09dacb3fc9a69eaf0a43dbbc2e03b01972c76b4a1531af677c6b03a237b3dace01fb835854054ab3d0637043982d66478367979e85e99f98ef2ea9c410af8f9e359c4113c4bc1c35f40c07392dd51d7264186bb8476332fdf2c10a02ec25cb0491fcae4b2dc7eb61e6d952f5796ecd5614a8c50868d349f8307464281a9c4251cdf2da1d43667b3a4b7a9830f0e977ce1e4a9641f14c64ceaa70082151666b33aad9660977aaa0b7210a629f4b96545835ac6c21d555e9c8cc03c53ee928bd02f0f9377b40e793c98e3ff992fd36a6de804
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Bunitu-9997037-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: wotrwl 25
Mutexes Occurrences 3G1S91V5ZA5fB56W25 8AZB70HDFK0WOZIZ25 ATYNKAJP30Z9AQ25 CBKZiOPASRHKL25 China183909925 China415003925 D1JozWrldD25 FMPsDSCV0l25 Hk4kKLL0ZAF8a25 I0N8129AZR1A25 IwS0100399325 JKLSXX1ZA1QRLER25 KDOWEtRVAB25 MLIXNJ9AEGPSE25 MLIXNJAEGPSE25 N800HANOI25 NHO9AZB7HDK0WAZMM25 NMOZAQcxzER25 NNDRIOZ893325 OMXBJSJ3WA1ZIN25 P79zA00FfF325 PCV5ATULCN25 PJOQT7WD1SAOM25 PSHZ73VLLOAFB25 Tropic81933125
*See JSON for more IOCs
File Hashes 1e8c8dc9d8471c37b7d172e98836d43ca1cad640bea9710ad42783193238359029104433bc9580b8fb971b3b019b31c0429aee6050c94a90388e4c48f31fe0ed354a9603439b1fcba8799f009b3040d36e8072bf7e8d2e5376848ae18e7dcfdf385067c9b15cfbded1fd47997391091921cb96a398b7e47b874148cf0af699de39deff67e6c183bb569f45ad738c61eeb7a5d7aab3d850abd885e58537ee45a44c885b7c936b126e4191c0e7264f65014c521946dccd3315f938cd1dca8ca8315362e35f563cfb85f38d7bf6bfaf04810772124ef4d56f74fd9a554cc276c20455648717057380c395778366acd4a98efc6a594f733ac18124b2a61e781a4bf156968c3025f683ca81913291deb3cacf3ff523a61d2fec4527c703b3b00a9ce058ba452d597c415e579f225bc1428a8f0c99d445c7ef78e484a4366cf822759a726156ada6455930904ffffa4c38757c9e9cc0095916da2d40446cb4b21eba1b7ab47a878fd2d3898ae3fe38dd84bd3959ecd258b84e604d0be70d723a49e03a7c65efbf7293ebf6d60def451efe602b2dfb7690b8bbc379816e501ad9dd46f88456aaf9e6697b7be7941999be838c4ec383ffd6d5978052eedb82141c443a74978fd92bbcaa778f752019816338069efb20192e475cb5a83c7518c91033ade0ab2e6ef15f736f1e035f88720ab374804d55506943f4cf6032c375466121d534b537e19ff297db2a78c3685d311af30ace164b8a8cc2cf947d7b6e02e3ffd452c67c529a843613d911b51eb8624a5f04218386a6260b3afcaba2a8024aa88e72c87e212e2c8f571dd88c669e2a2a5943d9dbc239445d306a0aef59d73e190bd1c9595ba7c81fa90a74e3d5fa081d7489b55765f79a3c3ab19ba84005c69b220ccbd820f37217290b31053e53ca39472959dc8d871795b78a5fd6d55ac9eb3c21d07f119b7549e5766cd9e3e3adae00100320d79422e715c178bd6d67b7f67f3dd2276dbeb2db82ec2a7331e046a28b99bd350b2a1c81079e660c5fe06597e32ce071fcc9aa94dce40c99f86f6683246c12783b0d4194cf0e1adbbe0ad7a5f19ee8bb3349d54cfc58fe72d7c995ba631bd65ff4134ecc266a92bfedad57441970
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Vobfus-9997065-0 Indicators of Compromise IOCs collected from dynamic analysis of 14 samples Mutexes Occurrences HHUdgyTYTdgysgdYYFDTSFDTghvh14 HDHUAbdYYdysgYAYAGYDSgydssyY14 KodjUGydtfTDFRbjNJUFRTdreRRd14
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 69[.]50[.]208[.]1714 91[.]193[.]194[.]4314
Files and or directories created Occurrences %ProgramData%\gHf24500nEkMf24500\gHf24500nEkMf245001 %ProgramData%\fBl06509fHaFi06509\fBl06509fHaFi065091 %ProgramData%\fFc01831iNpBg01831\fFc01831iNpBg018311 %ProgramData%\gHf24500nEkMf24500\gHf24500nEkMf24500.exe1 \TEMP\69fe340067c452a8c1099d895047587c83557ab7525d56e8713c71b1a2b378ff1 %ProgramData%\cKd06511fFeLh06511\cKd06511fFeLh065111 %ProgramData%\fBl06509fHaFi06509\fBl06509fHaFi06509.exe1 \TEMP\1d2f39b5f58de40788b3f9e78e637c0824c4b6fc0f32f0703099cf7ff1b4dd5f1 %ProgramData%\fFc01831iNpBg01831\fFc01831iNpBg01831.exe1 \TEMP\ec9626d0df54277f6706a6b3d799ec1326b7083bb48990bf39e242be0dd529031 %ProgramData%\fIl01819hIoLc01819\fIl01819hIoLc018191 %ProgramData%\fHd24500bPkOh24500\fHd24500bPkOh245001 %ProgramData%\gDb06504iEkOd06504\gDb06504iEkOd065041 %ProgramData%\cKd06511fFeLh06511\cKd06511fFeLh06511.exe1 \TEMP\2ebd16a264a25cca519a446d7c01816535f8f29d405e2023182b40e910faa50a1 %ProgramData%\gPf01814mElFk01814\gPf01814mElFk018141 %ProgramData%\lDg01803cJoMl01803\lDg01803cJoMl018031 %ProgramData%\fHd24500bPkOh24500\fHd24500bPkOh24500.exe1 %ProgramData%\gDb06504iEkOd06504\gDb06504iEkOd06504.exe1 \TEMP\830c02fa1f60800beb319565de95727caa89e778b2a571547d834c80167cec9e1 %ProgramData%\ePo01828jEjJh01828\ePo01828jEjJh018281 \TEMP\0c68ade090284789059722d8fadd314cb034b93a90a18498fdc3fbc65726ce0d1 %ProgramData%\fIl01819hIoLc018191 %ProgramData%\gPd01804pOmHn01804\gPd01804pOmHn018041 %ProgramData%\fIl01819hIoLc01819\fIl01819hIoLc01819.exe1
*See JSON for more IOCs
File Hashes 0c68ade090284789059722d8fadd314cb034b93a90a18498fdc3fbc65726ce0d1d2f39b5f58de40788b3f9e78e637c0824c4b6fc0f32f0703099cf7ff1b4dd5f2ebd16a264a25cca519a446d7c01816535f8f29d405e2023182b40e910faa50a48bfb384e68cf665c724722e37bb61aa1039e22ac978fdc6d507b0a46c38b67d56339ae292b244e84f53ad957174ab5767c54a70e2394be666bee52f1d686568603dcbd333df7de2d23c28f677900f7e5c4299fcc6da96ade60b92b5731c5fd9697a5de897b686f9729a41baff2034f35fd37851baa57914792ae0c3df20396269fe340067c452a8c1099d895047587c83557ab7525d56e8713c71b1a2b378ff6a535c1797c0f36ba2ed2ca0ff87bc512a6ef4bc2341ffafb20b05397c7c3df77c423c22cbedf35cdcf0a9b987de1f43575d1592a6e0c25bd6bbce0b0964dd20830c02fa1f60800beb319565de95727caa89e778b2a571547d834c80167cec9e94e417ffbd477cf0f556e83e33a796f8d26e595c3fbe3cd7f0d250b37fea27bf99d2da258a7c890307c6be6a0c082bae5922cbc866a3285522ca22a66d9a3935ec9626d0df54277f6706a6b3d799ec1326b7083bb48990bf39e242be0dd52903
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
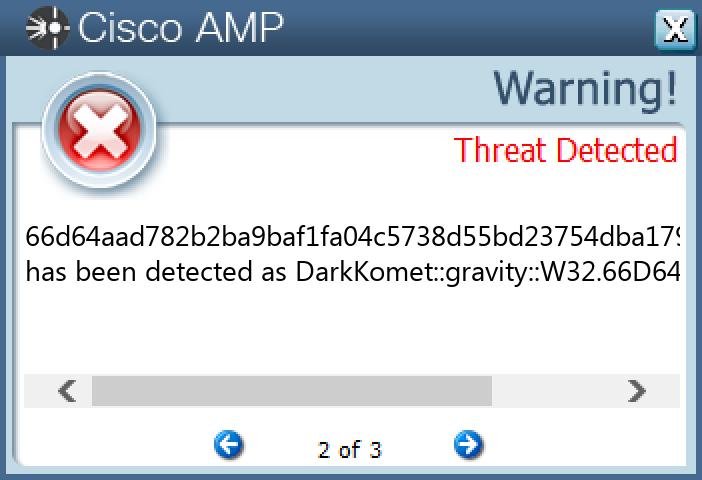
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.DarkKomet-9998118-0 Indicators of Compromise IOCs collected from dynamic analysis of 23 samples Registry Keys Occurrences <HKCU>\SOFTWARE\DC3_FEXEC23 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: kb2456.exe 23
Mutexes Occurrences DC_MUTEX-13F3AYC23
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 162[.]125[.]4[.]1523
Domain Names contacted by malware. Does not indicate maliciousness Occurrences dl[.]dropbox[.]com23 zoukiny[.]no-ip[.]biz23
Files and or directories created Occurrences %APPDATA%\dclogs23 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp23 %TEMP%\tmpBD03.tmp.exe3 %TEMP%\temp_GujQurApmI2 %TEMP%\temp_GujQurApmI\svchost.exe2 %TEMP%\temp_AoPXtxyscR2 %TEMP%\temp_AoPXtxyscR\svchost.exe2 %TEMP%\tmpC06C.tmp.exe2 %TEMP%\temp_MhOpOytNAS\svchost.exe1 %TEMP%\tmpBF9C.tmp.exe1 %TEMP%\temp_dgFaHSHFIP\svchost.exe1 %TEMP%\tmpBAF0.tmp.exe1 %TEMP%\temp_XbxDBxrtQM\svchost.exe1 %TEMP%\temp_hYMuQAMQTy\svchost.exe1 %TEMP%\tmpBF44.tmp.exe1 %TEMP%\temp_AChkJWUFGO\svchost.exe1 %TEMP%\tmpC28E.tmp.exe1 %TEMP%\temp_ktuFuZaySw\svchost.exe1 %TEMP%\tmpCC7D.tmp.exe1 %TEMP%\temp_jTWgKpaNic\svchost.exe1 %TEMP%\tmpC453.tmp.exe1 %TEMP%\temp_gwLGQvZjwn\svchost.exe1 %TEMP%\tmpFFFB.tmp.exe1 %TEMP%\temp_gFRVVtvPLv\svchost.exe1 %TEMP%\tmpC0BA.tmp.exe1
*See JSON for more IOCs
File Hashes 0405c695532cdfadb49cd6e5dc0175e2740a6b34df032e0d6370ac57781bc0b9099393350020fa9d643c1fd02dd8e0c8e2c9090ff5d4ff96a807b03cc927dae60b9d53d8392c6af28951737704765fb1a7c75a849633ef4e4a1d7b7be861f6d71ba1034f63585a98afac1b985f866ec53e66ba500c8a7e499521e47e66e7867e276e6b279f8cf83b531fcee7fe2f770f1814b5d63ba25aa407bf1676698d09c72d67a134e9a81d3f55017c4c3e395e90194d6ad6cf2d24b6f567f9df0729f55e2ed27da0b1a0cf9949aba612b54427c7d104e1fe44c98e363b3cef43289d792437c13c62990a05a6105024b075eb672723a0838eadec043618b4222ca15520b53fe6cb53ea8f0a35f828fc1e87ad9cf6a27081695ef9b709fb3367c2e8c21e82506a3537c3afbb25783fe817f230595b3c7369eaf737ee84475a6ed1d5c5c5ec66d64aad782b2ba9baf1fa04c5738d55bd23754dba179b7c01fe15837ee6b6b7781529034cef2a9316fb18187611f911d2d6463f56636e7d6393045a88302614786be271e7f3f8249203417bd8547b42e3dceb9440e228d844a78c85f2dc78228534b61a4f0c0dc39da45ddf6a874edfbaf0ea9ab36c58f470ae3e062f81c6b288789c72981be3e3f57b31771ab73ad52089f65a8b5f0544d3ae5ed9e8b14f6e889b3fe85d94c61276540ea86de2de983c7d7357eaf394717e0705cd365a307f8f12b7340c8cc0c6c7c3c3f6ed64a3f8850fa035d1f811dc4255b128ab00d4c5a7b80aea4110f98e399e64abb923dee60f70650041593358297542c33f6b8a8eb83385710b54918cdb2814e555c0b6189a2c5ba46bc2cb0a435b5b8f5a5b51cbb837289b0f42bdfbe726dfafbae51a0b5cb5af21a3a2859bedaea7ab770d2482ca67b7e760c2d09004928da6736f4784cc05899ea7ae4bf19deb16d4fee047ced24f72779958896980e074e15cc9abb88daa041c13123525db3d6ee33be32b81ffe2607eec8bda28fc38b19bbef00cfcd572f3335b3773c4df758526243f128b
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
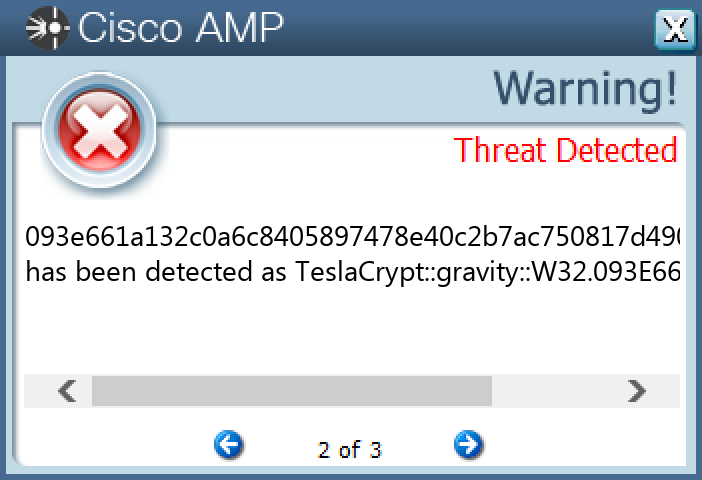
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.TeslaCrypt-9998112-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLinkedConnections 14 <HKCU>\SOFTWARE\ZSYS14 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.CHECK.0 Value Name: CheckSetting 14 <HKCU>\SOFTWARE\ZSYS Value Name: ID 14 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hgjuy78gfh 14 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hgjuy78gfh 14 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'>14 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'> Value Name: data 14 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}4 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: FaviconPath 3 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A} Value Name: Deleted 3 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES Value Name: DefaultScope 3 EXT\STATS\{B4F3A835-0E21-4959-BA22-42B3008E02FF}\IEXPLORE1
Mutexes Occurrences 7845621432412414 Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!16613a87
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 34[.]160[.]111[.]14514 192[.]190[.]221[.]4914 160[.]153[.]47[.]13714 13[.]107[.]21[.]2002
Domain Names contacted by malware. Does not indicate maliciousness Occurrences myexternalip[.]com14 ceremonyofficiants[.]com14 vinvish[.]com14 mugegorcuk[.]com14 sistemaslye[.]com14 w3dot[.]info14 www[.]ceremonyofficiants[.]com14 www[.]bing[.]com3
Files and or directories created Occurrences \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I08BO8F.xlsx14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I11KHR4.doc14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I5QKHLN.doc14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I62TWBD.ppt14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I6FZORX.doc14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IABMX83.pdf14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IAJ2Y6R.pdf14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IALGTCS.xlsx14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IGTBBSA.accdb14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IH49RPF.ppt14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IH71GGR.ppt14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IJKODPH.pdf14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IJP965K.accdb14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IKY5R3M.pdf14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IMYCSIT.pdf14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$ISLP722.doc14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IXLC77A.pdf14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IXUL2U1.doc14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IYSR1FU.ppt14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$IZ2GMJW.XLSX14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R08BO8F.xlsx14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R11KHR4.doc14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R5QKHLN.doc14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R62TWBD.ppt14 \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$R6FZORX.doc14
*See JSON for more IOCs
File Hashes 04299f4d006c5d6b18d192bf71e98527db0fe462ab8e0ee9cfcf62798b5a8789093e661a132c0a6c8405897478e40c2b7ac750817d490b6eec3bdab109bef3911b0b39804d7a92ee2a7e4cfef28766666a2082a01961e78bfa79805ccadd65622401f788baf9df6bce1556b147f7fbb3b8f5f244f60405dd0d1e0be3d1fe191e25c1c67de6ead9c4efd8372caccfbba80cc77667dd9b172e5535b1c7a7b81a5e297bcef62a1b88a614615e7fd022d8b1243874b2d4d0ac639d167b53464919c8331b989a3f98d026d7e285b40904a118699d7391efc2d2ef16c6ee81e1c378f33a912d051d4544720511d30e65d627a974cacfa14635dd4688016ebb17fc160b5602c335943bf9835a9c9048e56c554e7ceed17f1e4d39332ac020a6517c44547c609b5066a69eb0b9d0a7fc7273e54773837d4342381751370f9a2dda51dc588b7e0fab0d039591a911e0cdbe07d357b8749873e9318cf07a0a02b376118d269b01cc5b9bcc1322756605c9a24a0b2b6a02f23df0341e154f650df3d7db9be8cab15a34c5c4c4560d5d3db982e1ec7de1b966670844e01287901e99c44109c7d6fdf4d481ae45dd717cd8ee5877d89879da34ced6f5dc6e9ab9d1eb1d13a1ebf5a609839ae2e0049a6beb793d8d0dbb4446da0fd0759458a2350a3b18bb0513
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Ryuk-9998099-0 Indicators of Compromise IOCs collected from dynamic analysis of 113 samples Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER Value Name: DisableAntiSpyware 113 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoRebootWithLoggedOnUsers 113 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoUpdate 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableBehaviorMonitoring 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableOnAccessProtection 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableScanOnRealtimeEnable 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableIOAVProtection 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE113 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES113 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES Value Name: TamperProtection 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableRealtimeMonitoring 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AUOptions 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AutoInstallMinorUpdates 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS Value Name: DisableNotifications 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: UseWUServer 113 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE Value Name: DoNotConnectToWindowsUpdateInternetLocations 113
File Hashes 0390005afca1f2f7e33031e4ac953e14e95e55b94afd52da3d850e90de51c354091d997ff229e66719e5bcf97b8980319e05e60b0394c2a34bc85dccbc581459092d82556a175015901e6c6de282c229a6c640b8894a1f1a8a18c9f0a89ed5080bd516c3539b63861cfbd4f1e426fb3e730decbb6bcff277985dd089b54115a90de1f935dc67fd7fc2e2fa0ad1b0ef00eca8c2a2dc98b490fff780966ad2ff510fc309bf0975249ee326fa02ff42af98905a75196dd05b8c4a5486824595c444104ff588961235ac1821fb19ec37b97b1f10152df6bacc6eaee753cffd728ac3106e693d6e17ba6794229b51eac9fbb0427d519c78222f60ff0299b756f0032911dc839bd58d033a064eb141a13d652362e82eabef0de5b346356892465050f9146f2fe3666461792937352ae4b6c0aae08739303b51012590dccd414223854c196815e0f72628a844d96180ba5ea4078f5b22ed50f5dda26760ddfc46e911f21a1a9b0dd57527293d6339aba16a6ac361dc5dab82ae998a749879371dc846a01cf11cac6db3b0900035a9b2a7d64fa7d28f50c28df011d837f65f464ca21f111d418d41da0aedc492f4ecf9d2afa04843383631dcaae8e817cc29f0517e2e341e56a709b410822bf642d5588a152714463b59e4de02fc6b6cc7097d27d9155721291524362d2c79137220e8ec83453c32e618279c91e496807f43cab9c1383a22d7dec928486dc68cfc61616d0290627a2cd2e846baa2789e1b03fdcfd4feb427b9acd79e80b32188b74d64a95937043fecb0ea14144fff52482d5a0012d8fc2c585895513e08080cd201355e54d464ab2349134ea7e7e54aaac48db482039f2ccd2456e9621155cbafb6dc9ab85123a7ceced9ae99d109caa9d706bde4e4732ce74fcaa5b3c915b3f96ba9105072fc79ccddb10e60bfaf7a00237877ce2c592d6f0a6f0f06a35a6dc7015b67a0315ad7ed3492ed9d551dd334272ad8fb5c1e2d79b9ab8d8d5c0f1453990725f42c0f145330fe9d6e3427ae9d8cb027f27411333d5cae1bb6acaf590715c02495e8b05eee6c7ebe792c4ba2f340e2c5bf57bb36c33413bf489c22e8fa4829de29d70c7c26fd947a480e3f537fef92f303f4d2
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Tofsee-9998087-0 Indicators of Compromise IOCs collected from dynamic analysis of 22 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\USER SHELL FOLDERS Value Name: Startup 3
Mutexes Occurrences Global\<random guid>9 006700e5a2ab05704bbb0c589b88924d3
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 193[.]201[.]9[.]2403 176[.]124[.]192[.]332
Domain Names contacted by malware. Does not indicate maliciousness Occurrences jeffmorales[.]top2
Files and or directories created Occurrences %APPDATA%\006700e5a2ab053 %APPDATA%\006700e5a2ab05\clip64.dll3 %APPDATA%\006700e5a2ab05\cred64.dll3 %System32%\Tasks\oneetx.exe3 %TEMP%\cb7ae701b33 %TEMP%\cb7ae701b3\oneetx.exe3
File Hashes 16e52c8523bcb28eb990690cc2f1d44873ece0424a0e6a311ef5120d7dae0bd729dc138ff8b2d1300e7fb8c9d48a49b5635ef4eba48fed6fe96ccaea4633860e3a689a258a19a24f4299bd7822b18bedb4d92c7ead8aee33f4bee2471658a7a93c65de52ad093abbb73aae163e3c239069799b0a802418e169de9017dca5ac3856411c5e607385b436a305d2676486db9a832e6981c352938a7bafb538d6772556d914e4c6976ee5d5f74f94f05dea55601fc330dd1e38c2111357283323708c5b49c4564077cbcf7d35179eb46b0bee981fc9777c170f6691849d216024f7f95bca3d8d72005f97db62233c7330cd85656e2f63479f2dbf25b7655030f057a96301cce6e78b8011004d1068928196b9d49e642b58942f980cb2e55a2daef08b669dd95b76e6c32a2ffbb11b4ff767168c6b553f08b04a61e03ad5aef1099cd4703c5b3add9ec20996eb89d8abdfa5f48fb19fa5f04a2847fb1a6dde5e6e0b7a8107254004ae76a6fcdc0255c5d72fde37d81280f3c08faab3f584823bd8e1eb8127bc9f82467eca7c5d2360ebd6d4e275d341a1a254da42e088e78b24ad26558a1f7f831260dfbd1262710452167503867274f7b59593ac569dd8b96eeef72594c1d8052e1f14ebaa26ae41e2b1567ef86e98b126a06c290dd5086f22d50160a3faa51328023afdf40456a901c58a4e977c2337341c6ff0b7dd0bbbaca578dead50da96cb67488a5aa59c830e0f70df5621e698b52737367bd70e6107ea6283c38b39dfada9a664e0adea4030de3e4f4c2b289902cddf7549b2f1737a7eb9aec81d4186d8d7a69c5635b0d3eee3b165c35e56921f0de5bcbec8725b7892d55de406e7f6be7cf008d1952ae1a8882f9e3adca5974dd6d57049c5f8b508958498efccc1f4d10fc8260295ab2593396cdd1ddaf3a90254d94107e4fe8c90c6f2c6f3431d4b0fad8c5e39dd887362217cbaaf7abfa3db413013350ac0378ceebe32
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK