Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 15 and April 22. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
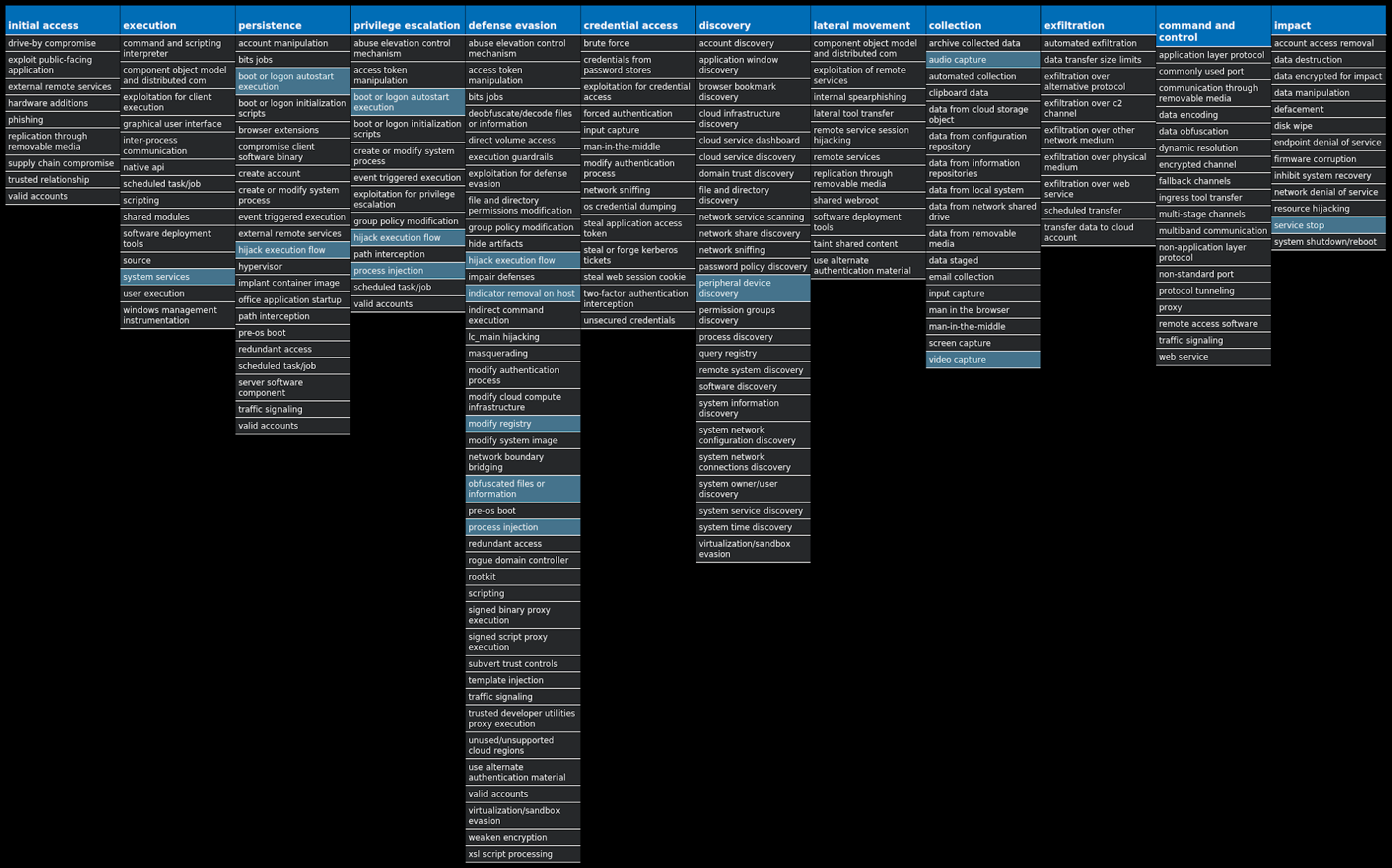
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name
Type
Description
Win.Packed.Razy-9944943-0
Packed
Razy is oftentimes a generic detection name for a Windows trojan. It collects sensitive information from the infected host and encrypts the data, eventually sending it to a command and control (C2) server. Information collected may include screenshots. The samples modify auto-execute functionality by setting and creating a value in the registry for persistence.
Win.Trojan.Zegost-9944345-0
Trojan
Zegost is a remote access trojan designed to provide an attacker with complete control over an infected system. Capabilities include monitoring keystrokes, collecting video footage from the webcam, and uploading/executing follow-on malware. Zegost appears to be derived from Gh0stRAT, which is a well-known remote access trojan that had its source code leaked, thus significantly lowering the barrier to entry for actors looking to modify and reuse the code in new attacks.
Win.Dropper.Formbook-9944286-0
Dropper
Formbook is an information stealer that attempts to collect sensitive information from an infected machine by logging keystrokes, stealing saved web browser credentials, and monitoring information copied to the clipboard.
Win.Ransomware.Cerber-9944814-0
Ransomware
Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware replaces files with encrypted versions and adds the file extension ".cerber," although in more recent campaigns, other file extensions are used.
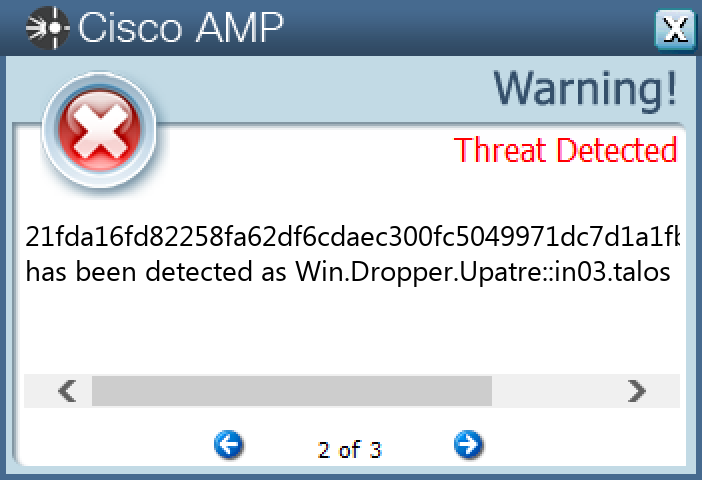
Win.Dropper.Upatre-9944336-0
Dropper
Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware.
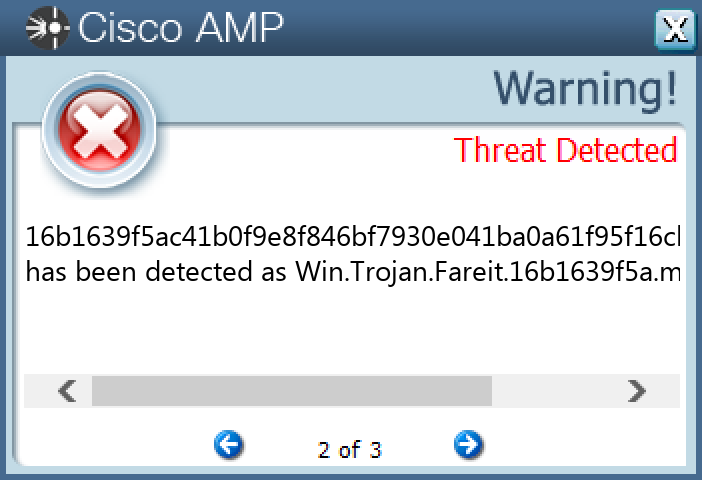
Win.Trojan.Fareit-9944778-0
Trojan
The Fareit trojan is primarily an information stealer with functionality to download and install other malware.
Win.Trojan.Zbot-9944779-0
Trojan
Zbot, also known as Zeus, is a trojan that steals information, such as banking credentials, using methods such as key-logging and form-grabbing.
Win.Downloader.Banload-9944679-0
Downloader
Banload is a banking trojan believed to be developed by Brazilian cybercriminals and is used primarily to infect machines in Latin America. One notable aspect of Banload is its use of custom kernel drivers to evade detection.
Win.Trojan.Miner-9944721-0
Trojan
This malware installs and executes cryptocurrency mining software.
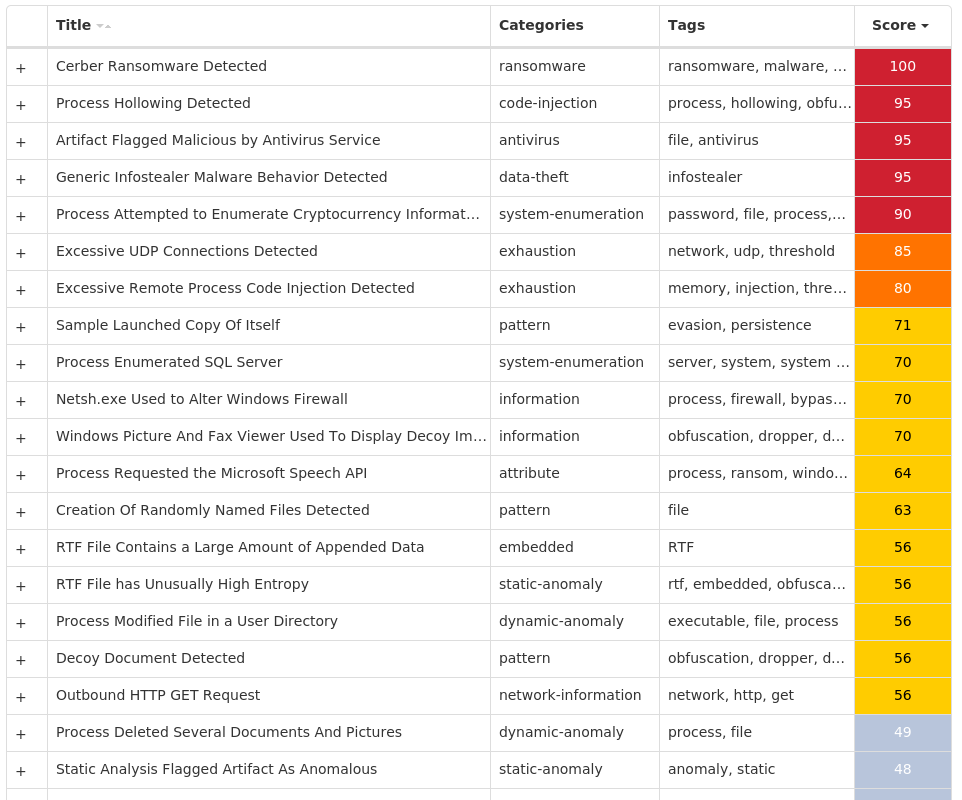
Threat Breakdown Win.Packed.Razy-9944943-0 Indicators of Compromise IOCs collected from dynamic analysis of 28 samples
Registry Keys
Occurrences
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR DATA\LINKAGE Value Name: Export 25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET CLR NETWORKING\LINKAGE Value Name: Export 25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET DATA PROVIDER FOR ORACLE\LINKAGE Value Name: Export 25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\.NET DATA PROVIDER FOR SQLSERVER\LINKAGE Value Name: Export 25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\CRYPTOGRAPHY\AUTOENROLLMENT 25
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: PlexService 25
Mutexes
Occurrences
65845562146GZ2325
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
corporation[.]warzonedns[.]com25
Files and or directories created
Occurrences
%APPDATA%\PlexService25
%APPDATA%\PlexService\PlexMedia.bat25
%APPDATA%\PlexService\PlexMedia.exe25
File Hashes 068a3ee10b9c9ebd6f0313a641f448b6014cd8e7ec0f22152a10a236ed4c6b45
07aa79f924445e867ab77d769a490040776dfd2eab89e22825a89313179676db
0da129e88db6b27bed612cf8ee035bfa40848be932e41eb45da313700960253d
11c22f9c2fe94f8ff90361bbb9a96fe4c3f4da98b67cbf0724d2f9947b0b04a2
177ef73bc608d6b91b393a7cd6610e4747b669df93b953a96f81673609a4c034
1a82aed6c9c1869ff98da8abbaec637607eb29689ac6098d94b4be1319af7f07
1cb5a0ecb44c5f89bbb17f1562cc17525aca13451c344eba4c2ca9dc088073c5
2361ca96e659eed25263dc63407a802ee5d07c0c3e99ab7a1ad2a14875588213
269f5257b774289201d71efaa27bc67437111ebf7f452b5a8a29cc8bbbb4d219
27558fb9c0137fc15536c4f3cea9d010b7bffb14780d016916be1d5a50c617ab
28c38ebb8c671e1b48a82c01a4b85ef262954609530d39998be47cbd0c9648ea
2b2151e143c123febba7c443f23fc726a0f0da0be5669a5ed85c99695737a304
2d3e189b1e137a2f6cd70fef2fb91ea2dcf92ffa8f4669f8df0cabd5ecbb4d48
359b98632577507b103da0d4ff145e4db7d3a5d2dda2ca37c7d262e5bbd348b9
3ee21210560ea2fd7d2fcf2b2447836b8bc4074b7231fb896852650e76d78eaf
4345df8337a451f9f93fbca70c995a4010445361376013beedce950c0a714f0f
45ea008f432728955aaf2178889bac21866970208bd2c91f325b33c87394e957
4d0c3453d16c5b6889f1f2d60e13c685fd931589040840c9a19ead43496cca2f
4fcc1bdef68f2c8faff38761a5c9ca160c9cebd942b00ac920f605119771774c
4fd51fa019a71b648a167935479589cfc99d4071753d47c03fad0e27438b50cd
52986ada0835e3680df5f8bd84a87f6197d4897f4b941e0f3d67e9d0bd304bd2
529c7a90435d28b1bfaa712ff010c80e953ba94963166b83a5999c36540f93b1
5a58119f1e8bcbba381184c41e00d8d8f333ffec921996ca8641fc2e27335432
5af088d7e60b29f97097f6b9591f8e1f0de6fc009ac050715e5908f1d68e5642
5bbc4e75654fd2172777fdd99ccd355b75f3ca24d53773a37e5147c05793a1f0*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
✓
WSA
✓
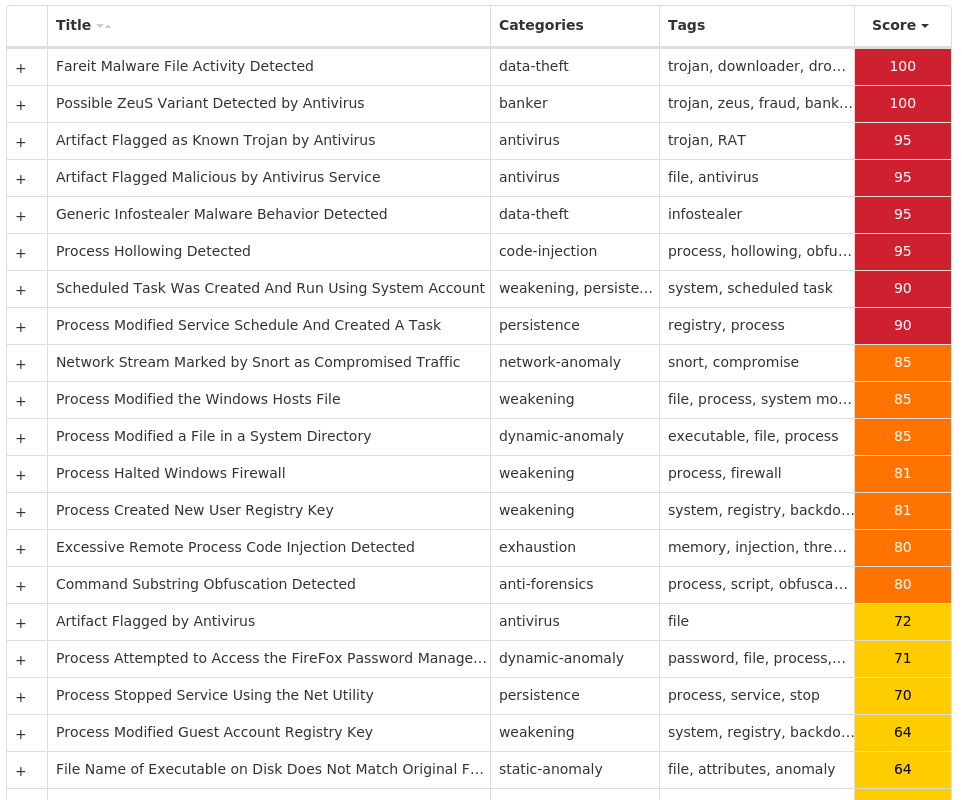
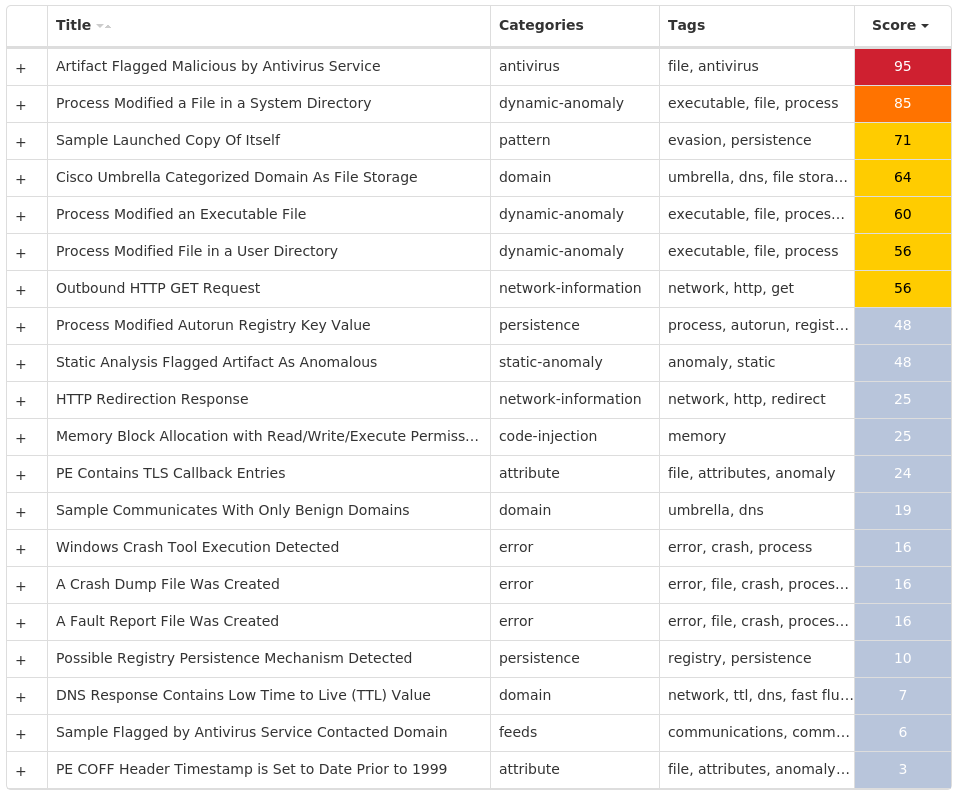
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Zegost-9944345-0 Indicators of Compromise IOCs collected from dynamic analysis of 69 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 40
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY Value Name: Start 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY Value Name: ImagePath 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY Value Name: WOW64 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY Value Name: ObjectName 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY Value Name: Type 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY Value Name: Description 39
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\ACTIVEMOVIE\DEVENUM Value Name: Version 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY\PARAMETERS Value Name: Module 39
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\COMFASTUSERSWITCHINGCOMPATIBILITY70 Value Name: Description 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY Value Name: dElEtEflAG 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY Value Name: ErrorControl 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY Value Name: FailureActions 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY\PARAMETERS 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY 39
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\ACTIVEMOVIE 39
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\ACTIVEMOVIE\DEVENUM 39
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\COMFASTUSERSWITCHINGCOMPATIBILITY70 39
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FASTUSERSWITCHINGCOMPATIBILITY Value Name: DisplayName 39
<HKLM>\SOFTWARE\WOW6432NODE\DFBQWKFXSB Value Name: servicemaiN 1
<HKLM>\SOFTWARE\WOW6432NODE\DFBQWKFXSB Value Name: serviceDlL 1
<HKLM>\SOFTWARE\WOW6432NODE\DFBQWKFXSB Value Name: module 1
<HKLM>\SOFTWARE\WOW6432NODE\EIHPHWCOYY 1
<HKLM>\SOFTWARE\WOW6432NODE\EIHPHWCOYY Value Name: servicemaiN 1
<HKLM>\SOFTWARE\WOW6432NODE\EIHPHWCOYY Value Name: serviceDlL 1
Mutexes
Occurrences
eed3bd3a-a1ad-4e99-987b-d7cb3fcfa7f0 - S-1-5-1839
Global\b-1759044459_2012j39
Global\1708c5a1-bc93-11ec-b5f8-00501e3ae7b61
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
149[.]28[.]39[.]15139
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
wpad[.]example[.]org65
conf[.]f[.]qh-lb[.]com64
computer[.]example[.]org62
conf[.]f[.]360[.]cn39
gbwd[.]hmjxjn[.]com39
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com17
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com15
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com13
www[.]msftncsi[.]com2
Files and or directories created
Occurrences
%ProgramFiles(x86)%\StormII39
%ProgramFiles(x86)%\StormII\%SESSIONNAME%39
\<random, matching [a-z]{7,15}>16
%SystemRoot%\SysWOW64\yynodukngm13
\fhytubgidr9
\filycpdkcx8
%SystemRoot%\SysWOW64\yqyvuripsr8
%SystemRoot%\SysWOW64\yhbilxnlsh7
\ecxbwdgcos6
\fohnepjmxs6
\fekkxwhilf5
%SystemRoot%\SysWOW64\bjlmdboddh4
%SystemRoot%\SysWOW64\aovbtseiyb3
%SystemRoot%\SysWOW64\yppbtbpjgd2
%SystemRoot%\SysWOW64\apxlyqidlt2
%SystemRoot%\SysWOW64\awjtcvggmw2
\Users\user\glejtcydml2
\Users\user\glejtcydml:Zone.Identifier2
\Users\user\jorcsjcinh2
\Users\user\jorcsjcinh:Zone.Identifier2
\Users\user\kgdivufblf2
\Users\user\kgdivufblf:Zone.Identifier2
%SystemRoot%\SysWOW64\rwrnswjdvg2
%TEMP%\whjsbbernj.dat1
%TEMP%\njqxjkqphs.dat1
*See JSON for more IOCs
File Hashes 01a779215e4d35a10112cb8511546d44e0ed09c0c07c45d27e0c0f3a5e3ce7f1
02efc66bb4e3c2e14c7df7644325d215be41d8139eed12dd3404658ca9fd592d
03850eeb28ebd672968037eee12058034ac4707dc769e29bea413ee35be15113
03a5bdd18cd5d305d392d0d5bf787324346a20cc81b683d43a7152228777be78
04cd27985d8905443484714589cb011d64cdaa1c467f244caa6f733711ab1621
05926960be90a69d40fdfc8bb5f5e233f6c2e43e6028e12686661d49a9a07e10
06b1d0824f83abed6afcdab337e8156e5e12a476dfa1e76d677eafbe9175465d
06c1bf196994fe4bea82eee9061f5508e2f411ac0dbad4d49ac7db385d18437f
0a8d8b590dc5cb8a0cc884d0cef4f106ca17878c4993e21aebe8df248a6e8650
0b007efb88401921742899a5c84ff4f95f053ebca9a46c2aa5b9be35b673a25b
0cc9dfe2b1f34b1405342acd769b1a1ccc10c4d16444fafb64c9a554bc99bf51
0ed7be8f938f1b9ed8f3861bfc8a24ea8103722f763e7157bd07e0e7b5f41c19
10065fde00c728c2f86ce3c493f7e11e07c5d2bd01d78bc50bcc27451aad6e16
10ad4201ab0a8b4e589a82eb39a1a8e73a21fa4b6949eae413d441814996a955
10d35b4f9dd7a30670571fefa5c2c2fef60dd054298088a1500b895283f4cf15
12178037648d75f2b2f2b67688f6cc51e77b65d7aceaa19d6466f3c4131adc36
13a79e861c07a43f98cd35778f8f7fa47e1b64d563f5016e80f42c509a0732f1
1a268b0e9a12ed6c09f147d10f0bcedf62b8b14c82655531ca735a5d49c208e2
1accbd29e0fb5138f228f62a9c10f55e9874d892f31aa641439729cde677f64c
1be6a64b5e232705b749c748781fa81a77c0cdeffe07f9a3c2312f5978711020
1bfd059ea01d76f84215eacc82353acabe378ce6193cb7dfca12db4149902a93
1c32f32213127fbfca688437c0b01d47933810ad6566ef01d90352fbf3888b1a
1c768561ec97f8dc6b16704f7020916af8134976b9264e254b36a3d7a6e180b9
1d15bdca32984afc083a36b7a9dc177ca73b28fd2edfe91a52b8118698e7880e
1d95e4141a47e8eb1b8516fd1701e38832124f16011a696d503a23ad185f24db*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Indicators of Compromise IOCs collected from dynamic analysis of 17 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 15
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\INTELLIFORMS\STORAGE2 1
<HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX 1
<HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX\20.0.1 (EN-US)\MAIN 1
<HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA THUNDERBIRD 1
<HKCU>\SOFTWARE\IUYHG-CNQUL6 1
<HKCU>\SOFTWARE\IUYHG-CNQUL6 Value Name: licence 1
<HKCU>\SOFTWARE\IUYHG-CNQUL6 Value Name: exepath 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Iwywbzy 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Jsdpjwg 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Pahykku 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Cjiqhgy 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Wzjjgma 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Weypqbt 1
<HKCU>\SOFTWARE\2022-10TNV5 1
<HKCU>\SOFTWARE\2022-10TNV5 Value Name: exepath 1
<HKCU>\SOFTWARE\2022-10TNV5 Value Name: licence 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Zezpbsi 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Xadwsvm 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Jpgsqas 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Gkngpli 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Hogsygo 1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HTNTCTG0DHU 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Gsvozuj 1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Cnjhrkv 1
Mutexes
Occurrences
8-3503835SZBFHHZ1
Remcos_Mutex_Inj1
O094-12BWX2JKxyZ1
3L8B461U70EZ33HE1
-5ORC052W9B28YHZ1
J10M58T8AHVYX-ED1
935809RVSYB2Hy4z1
O4220SB6GX4E0K0K1
iuyhg-CNQUL61
16L80R97WADJxxY41
JL8QNOB8WV4WJx8Y1
S-1-5-21-2580483-90815907346551
9M2P0PD01AVUFDyZ1
2022-10TNV51
68636P16AXAVHY9J1
0N11726CWTU6H25B1
0P9O879VFA8vVx9K1
112A172-TSDG0BHZ1
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
34[.]102[.]136[.]1805
23[.]227[.]38[.]745
13[.]107[.]42[.]134
13[.]107[.]43[.]133
198[.]54[.]117[.]2182
198[.]54[.]117[.]2102
198[.]54[.]117[.]216/312
37[.]123[.]118[.]1502
15[.]197[.]142[.]1732
142[.]251[.]41[.]192
52[.]228[.]36[.]2282
13[.]104[.]158[.]1802
112[.]213[.]124[.]701
172[.]67[.]215[.]2461
216[.]218[.]206[.]401
104[.]164[.]133[.]1801
74[.]208[.]236[.]1501
52[.]20[.]218[.]921
104[.]21[.]32[.]1281
13[.]104[.]158[.]1771
103[.]147[.]185[.]1001
44[.]194[.]24[.]1671
142[.]251[.]40[.]2111
38[.]63[.]50[.]681
217[.]21[.]190[.]1391
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
onedrive[.]live[.]com9
www[.]hbsckj[.]net1
www[.]awp[.]email1
www[.]amelntl[.]net1
www[.]fabio[.]tools1
www[.]hdlypx[.]com1
www[.]lshdkj[.]com1
www[.]theeastendvoice[.]com1
www[.]cgbbqllc[.]com1
www[.]supraforward[.]com1
www[.]dynwa[.]com1
www[.]stronyinternetower[.]com1
www[.]carfik[.]com1
www[.]5151vip25[.]com1
www[.]aestheticpls[.]com1
www[.]bucariito[.]com1
www[.]jakubkokoszka[.]net1
www[.]positiontrader[.]club1
www[.]fujistrek[.]quest1
www[.]amazonbrickandmortarretail[.]net1
www[.]ideastax[.]com1
www[.]nbsze0[.]com1
www[.]beylikduzuhatunlar[.]com1
www[.]sauqenta[.]com1
www[.]cherrythechickenandfriends[.]com1
*See JSON for more IOCs
Files and or directories created
Occurrences
%ProgramFiles%\Microsoft DN17
%PUBLIC%\Libraries\Cdex.bat7
%PUBLIC%\Libraries\Null7
%APPDATA%\juhg\uhyg.dat1
%PUBLIC%\Libraries\Iwywbzy.exe1
%PUBLIC%\Libraries\yzbwywI.url1
%PUBLIC%\Libraries\Jsdpjwg.exe1
%PUBLIC%\Libraries\JsdpjwgO.bat1
%PUBLIC%\Libraries\Jsdpjwgt.bat1
%PUBLIC%\Libraries\gwjpdsJ.url1
%PUBLIC%\Libraries\Pahykku.exe1
%PUBLIC%\Libraries\PahykkuO.bat1
%PUBLIC%\Libraries\Pahykkut.bat1
%PUBLIC%\Libraries\ukkyhaP.url1
%PUBLIC%\Libraries\Cjiqhgy.exe1
%PUBLIC%\Libraries\yghqijC.url1
%PUBLIC%\Libraries\Wzjjgma.exe1
%PUBLIC%\Libraries\WzjjgmaO.bat1
%PUBLIC%\Libraries\Wzjjgmat.bat1
%PUBLIC%\Libraries\amgjjzW.url1
%PUBLIC%\Libraries\Weypqbt.exe1
%PUBLIC%\Libraries\WeypqbtO.bat1
%PUBLIC%\Libraries\Weypqbtt.bat1
%PUBLIC%\Libraries\tbqpyeW.url1
%PUBLIC%\Libraries\Zezpbsi.exe1
*See JSON for more IOCs
File Hashes 0740e382a0c41661aefbd38aa819fa21bc2c14a2cffc6209b361d07dae5cee3d
11a49d25cf098a273e94cfd206a62cec5ce647e946d2e696db28bddbb05b42ce
13362eb5bba08696533b5e3196ca0700ace9291e8f5a969c3c1b83d4d0e4667c
1e35356036799e52aa7c40c2cf4aa8975eadd9fb71446ea2626b1b2a5b31efcd
26b24f28b0173c020071085d65b260207d5856a8a93c1c1acce7d5cca5e8835f
4365d53513b910bfea66669db212ec18f2ba9ab2cf461d140fe42a61b8f0e7e2
47bbde8a83ef8df67fc61f9bf6df87802e31fa8d3a15cc8efe9e3ad1ebcc6fa6
70eb3857b235b6374a891d8d2136506b52e660ed1339921b913af29a0be6e9dc
713114d1dcb9d12994f1cfcb7cc765283cff3f2242ee57cdf15e849e15213a0b
7d60a35b972f1d9341f85029bb2d31244a0075a291507fcf5337f73002fa7e2d
a3a2d9a377922a592c46004c66ae748433c1874396168c575a26f744f05b6bf7
bc40f738486b53814c364435be4e8ef8ec4ac584e47360aac29d0d73f12c0037
bd09b7f6ad0ca7e7c74eee9ecab5fd3de92f24529c708370710161847d0861be
cb3764453fec3d5302500cc885406c7d905cb3bf50197a84ad9be459d45dde88
dd1e3e11bf3a43ebd5f3c8b877baf458481dd917edca070a98f8b3bfe0d6589c
e5a2e93403f1a6df948697530112dd27440a6b0abce3c9b63eaf64dd6dad17bc
f43ec67b5158f58273a216cbc49003c55b8f0e6316a3390823348924e38507beCoverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
✓
WSA
✓
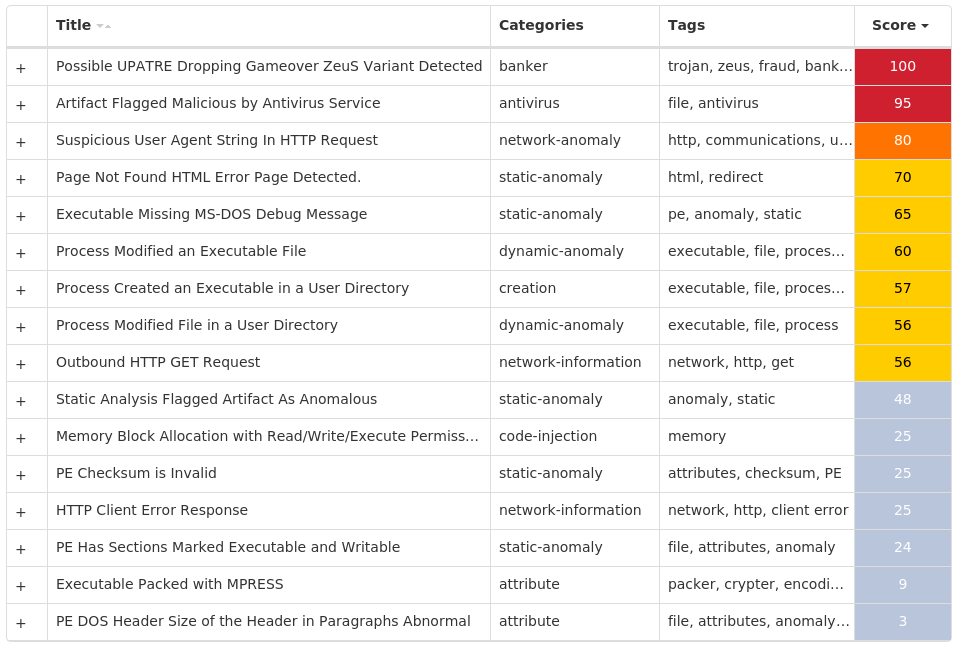
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.Cerber-9944814-0 Indicators of Compromise IOCs collected from dynamic analysis of 31 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 22
Mutexes
Occurrences
shell.{381828AA-8B28-3374-1B67-35680555C5EF}21
Global\<random guid>5
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
178[.]128[.]255[.]17921
149[.]202[.]122[.]0/2721
149[.]202[.]64[.]0/2720
149[.]202[.]248[.]0/2220
104[.]20[.]20[.]2519
104[.]20[.]21[.]2517
172[.]67[.]2[.]885
20[.]189[.]173[.]212
172[.]66[.]41[.]181
20[.]189[.]173[.]221
104[.]208[.]16[.]941
209[.]126[.]118[.]1241
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
wpad[.]example[.]org27
computer[.]example[.]org26
api[.]blockcypher[.]com21
bitaps[.]com21
btc[.]blockr[.]io21
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com9
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com7
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com7
clientconfig[.]passport[.]net4
onedsblobprdwus16[.]westus[.]cloudapp[.]azure[.]com2
chain[.]so1
onedsblobprdwus17[.]westus[.]cloudapp[.]azure[.]com1
onedsblobprdcus16[.]centralus[.]cloudapp[.]azure[.]com1
acvqxi[.]com1
aotcye[.]com1
Files and or directories created
Occurrences
<dir>\_READ_THIS_FILE_<random, matching [A-F0-9]{4,8}>_.hta24
<dir>\_READ_THIS_FILE_<random, matching [A-F0-9]{4,8}>_.txt24
<dir>\_READ_THIS_FILE_<random, matching [A-F0-9]{4,8}>_.jpeg24
%TEMP%\d19ab98921
%TEMP%\d19ab989\4710.tmp21
%TEMP%\d19ab989\a35f.tmp21
%LOCALAPPDATA%\Microsoft\Office\Groove1\System\CSMIPC.dat21
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp21
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.bmp21
\Users\user\AppData\Local\Microsoft\Office\15.0\OfficeFileCache\CentralTable.accdb20
\Users\user\Documents\Documents\resume.docx20
\Users\user\Documents\Documents\resume.pdf20
\Users\user\Documents\Documents\resume.rtf20
\Users\user\Documents\Documents\resume.x.odt20
\Users\user\Documents\Presentations\Presentation 1.ppt20
\Users\user\Documents\Presentations\Presentation 1.pptx20
\Users\user\Documents\Sheets\budget.5.xls20
\Users\user\Documents\Sheets\budget.xls20
\Users\user\AppData\Local\Temp\24e2b309\1719.tmp20
\Users\user\AppData\Local\Temp\24e2b309\4436.tmp20
\Users\user\Documents\Documents\resume.docm20
\Users\user\Documents\Documents\resume.dot20
\Users\user\Documents\Documents\resume.dotm20
\Users\user\Documents\Documents\resume.dotx20
\Users\user\Documents\Documents\resume.x.xml20
*See JSON for more IOCs
File Hashes 02c6a36e44b292f5b1d22dbb1b4d5a579439d224623ee1b4c0c1caceb2f16f6a
0af669cce769dc7c2b0cff2d574d8ed1ba73f836f4bd5013b048cc09dc4426a6
3458612721f225aeee4b474976070ba1f41b17ab08bde13faa0904a76ebabcff
37d9ce68dc0d2c0ae951587257545f3a8f17af009f44ee7789e3aa91826c4b74
3b986b7fd2eab8063df599dfaa7375831364ffc18b49f7edb32d40414fcea26f
47f4a1e92985bdff3ff06ae9d48ebca9298f92ca28607066178220c5e5dec7ca
6206f6ebaec0109c9dc3e9b0d7ec1ed15e7f0642ccf31757c55494b03f63f1ac
63d19c22386e7659362133968e1f571f11f083b2e78e2dcdd1cf5da98f828224
677bd793beda8cbf84df1785df5896b85eccbb36808bd7fe39b2c573fc6f15f1
7048d8c578dd490328cafce671eec2f324495a58d6b6b4449cd62244bc0c5387
72f18931d8dbd1a2559280d553afd5569f36422895eb771ef748047c0e7e57a3
7d721d0e9e209a8ecb18d3baaf0511570d68db70fe4912d72034acbad09685a1
848fcfd0b1646b3edb4a5e6d0041859296046de57691e2aa7dea1e1acbc01623
8e6fa0449256bf9d7f179425a8120312753f5b95a442c85d161ca375932302fa
965b5af826c43ef4b559bd2a2fca8ca32734a4c667d94e90f31289b45ff80c86
a31839107f0e0ec930ea18fee9dff3672870d736dbbaf6e3ea2c2d0c7b2e5906
a5d0889335c679c1ae374e960004f536923849616bda3c36fd2813c849b179ea
a8b8bd4876cff6c3645da4b4835860d6253311b5156cb3baaf54ad3ee3e2a14a
aa547346a6163b93f2ec8bc3f74fce240adf33134f80677a2e15b6606d9d4adc
b7347d9888c585bc8a05d52d0204fea1ae51cfbe6c76a623c5cc3ed137de276b
c624adbede90ccb4a61ac7125bef7921e5601c3da9770fb5656f0a5d1029e092
d0639e813ab71b125289f92094803b8becf3cc6ce06060e83e74eb58592eba4a
d09c177ad11b37ede495e462a9adc78398e3740039a3e920e894aa84383df01a
d9e034e955db9826506e393ee6c5f80e0f452eb4b5b97f3170934fb7898e5a74
e1a112a64249095ac3093952883f046746633321c169299f452026fb7c239681*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
✓
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Upatre-9944336-0 Indicators of Compromise IOCs collected from dynamic analysis of 36 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 36
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
207[.]148[.]248[.]14336
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
aatextiles[.]com36
Files and or directories created
Occurrences
%TEMP%\budha.exe36
File Hashes 04262ed39b2626755887b938fb5c44f4a2a9288de0c65c465879088a367be5b7
047ff0f102294a029e74efeb7d1dd98053ca149383c77a046b74d264bf15af20
05da23bdbe2177164a50d67116c1b7db07e7ac6845e099e7a6541c4daf8b6e15
06ff0f00379a01129abc56b99b8f987f0c69a9d452c0e60320270a9c9f27d86d
0c82c1967cb5ac458d40e77bab1289b0c5d2c245296adea44ac27b5e1ed9059e
0e96385f9ac256a2c0b1038341f2eeffd598177ad29593ab4217e7dc095e605d
1030688471696927c2bd5db64b144dd9616cf7f568e2c8c5ffa69a3ae75132c1
10cfd9d0c24622a03752f70f257af98d66e7f4b7d155b6ffe2b8089bea6b7f2e
183d65da16b08049bccc46aecc85740b6de9abbf7a2bafca4c4764495cd1f01a
19583d45cc828a423fa50b0a154f07867999bd590356d8e0b5b3fda4aba34ff5
1b286997145c64250498594329291ed3c3a7e8cfd96db445bff4665d63176aaf
1be5f03f9fdcdbf8d76501a533a253a704ac35e70874f0d7b0eb32629f79d6d4
1ef5aba4583f69d1805f1e87f06a618ab66248131cd175e1bfa44e6ff1384786
1f94b3e5761ed84b6b570dfb60c25792336e234eefb9de9d26947e104ed63bc0
2049a23fadf2a6b9a41149a869aec85f72876c57447bf10f150915147f442d2b
21fda16fd82258fa62df6cdaec300fc5049971dc7d1a1fb3b87ad643509088df
26c19de8832bddc868f90c79c0e158ab21b7e9ea24127ca02c4d47e5601076fd
2849b3b3354caf3edd15c5e9601a58e27415a3f68f97f2e1bc064eec73b138da
2890cb7a1776dfc48bc97483ee3c1995b3ec78c1aad85d56d4bd17c7a6c93414
2896670d04bbb1b544318d6d1eea870b89d86fd285a64b4646d747fabe485d8e
2a0c29f8f89cb1e2e564b3f24b445ceba0c1dcb2bfff49c73c3a4b2095a92fd9
2ba5aaca3a299d3908913f7cca086298aaf13bf804c2dd57d7d6129347e5748a
34b2be6f923b8bce54cef690a32fd9cd0e308d0b4facb257a685b9a178df2f16
34fd7f61a3b540af93e847635b120e785296c642d79c96c72817f0fc66b56da2
35a9c3addb60ddae771f4505d2db8768f660c89d122d3464097d9eef33ed0fd5*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
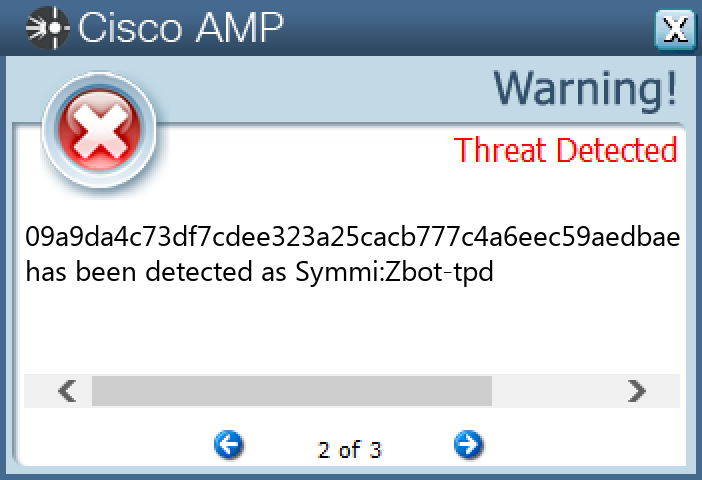
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Fareit-9944778-0 Indicators of Compromise IOCs collected from dynamic analysis of 48 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 48
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SCHEDULE Value Name: NextAtJobId 42
<HKCU>\SOFTWARE\WINRAR 42
<HKCU>\SOFTWARE\WINRAR Value Name: HWID 42
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003E9 Value Name: F 42
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000001F5 Value Name: F 42
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003EC Value Name: F 42
<HKCU>\SOFTWARE\Z 37
<HKCU>\SOFTWARE\Z\RECENT FILE LIST 37
<HKCU>\SOFTWARE\Z\SETTINGS 37
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: shell 1
Mutexes
Occurrences
Global\<random guid>48
8548551544
UACMutexxxxx42
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
20[.]189[.]173[.]222
52[.]182[.]143[.]2121
20[.]42[.]73[.]291
104[.]208[.]16[.]941
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
wpad[.]example[.]org46
computer[.]example[.]org43
vkwoucy[.]pw31
sdideme[.]pw31
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com19
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com14
xirukitu[.]pw11
ckimajuy[.]pw11
rosatip[.]pw11
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com10
clientconfig[.]passport[.]net5
windowsupdatebg[.]s[.]llnwi[.]net3
onedsblobprdwus17[.]westus[.]cloudapp[.]azure[.]com2
onedsblobprdcus15[.]centralus[.]cloudapp[.]azure[.]com1
onedsblobprdeus15[.]eastus[.]cloudapp[.]azure[.]com1
onedsblobprdcus16[.]centralus[.]cloudapp[.]azure[.]com1
zzoygsulaeli[.]com1
qcmldfo[.]com1
micnetwork100[.]com1
xuuvbrhkevi[.]com1
vbtlnzluxcyioi[.]com1
oygsulaeliaa[.]com1
tor-connect-secure[.]com1
fieoarrzfvi[.]com1
network-dnsspace[.]com1
*See JSON for more IOCs
Files and or directories created
Occurrences
%System32%\drivers\etc\hosts42
%System32%\Tasks\At142
%SystemRoot%\Tasks\At1.job42
%System32%\drivers\etc\hosts.sam42
%SystemRoot%\SelfNotepad.exe42
%TEMP%\3718931872
%TEMP%\3718949812
%TEMP%\3718953402
%APPDATA%\skype.dat1
%TEMP%\rhmrszrphk.pre1
%TEMP%\3718950901
%TEMP%\3718922981
%TEMP%\3718957461
%TEMP%\3718929061
%TEMP%\3718946691
%TEMP%\3718940301
%TEMP%\3718939981
%TEMP%\3718941081
%TEMP%\3718934991
%TEMP%\3718935621
%TEMP%\3718928441
%TEMP%\3718960581
%TEMP%\3718944511
%TEMP%\3718957301
%TEMP%\3718961671
*See JSON for more IOCs
File Hashes 020068017f1f40595fc03344e59414b7fc606a6f92ab63b088ac0995eee272b4
0275e077882d97349eeafa966d9d8b24c3b8b821c1d1ba5a94e1a603b9342086
05cb3c02a56b9e88601290a0451fef44d817517cf49e6145f3d5319fe7d07ac2
0a79838e89cc670429ff1aa7db9e20e3f838ff59901129896b292c4c70b12875
1060f9796eeb053c3b7a67edf88ff7b33ce83d92410a58a8aab7f5dbfdc72936
12e605dfd33e68e663a4db6629675a699c661461c3e48aff6d271e257f177d22
13d0eff9f710d256af961d391fcc94f007c029bcf71ad0b0a354aa6908a6c50e
16b1639f5ac41b0f9e8f846bf7930e041ba0a61f95f16cb9a809d791b87d08c6
1aa883b64cf541198a9d13b6846777131cf8938f4997230a0043b82cee0d0585
2ba23e4c7db7aa0de83d5cde1e8aadaa05f105353a02a68eb7ff87e6f0c6265d
31b7439894f33eeafdfa44fa1225d78b9d54f70c8da343605f3c20d6a842efa0
35dd39dfd253e7b40de2ac652547f1158712c71b98ef26d66d24ee6cc9fcc11b
376a2b3de0d6c40f7c48e135add3345070089d5a2921ab78e148a5dbf96b788b
38924cd6ac1cf2e20dd38ec5b84aab8deb1642929899879255feee54b4efcabd
45a3801408c3520f58fba1aa2bd8636448b75022b96b0af1377b930f77807cfd
485cdf46a93e5b37b4aadbf5d8a2589afd9fd6d6398d6ffcf936f71b4fefaba4
493cd1f281f660cfaca59d44f5b542086a9d02b9167e6e4f9d6d339786c1c5ca
4b156532190c11573cc086fbecbccde9e9c16e76053093cab9dc204d060a0f72
5452a932699000c728b8e9c7a0359244ae9edb5bcda26cc242abe86838444058
54fa762e6c6ea2b739b680aae27f232b28c8ac2d98b92aee1ee5c3025a2c7f57
557df8e22c7ca92520bfcef789da472d0fd19da277c7d200b38ce9095d712ad3
57b68e7c4c19ce2db5b5f59ad801b7b2193f1f7dd3f480267c67e8376ec13014
57c8224acd53a9ae45fd6de271552038a13ef8d53eba47416a65505f104b2eca
601a8aed6b10d7f57c3604fdbfb1eabfdc27476dff030a1d20210007155a32d1
62a467a87f61a97f61db6c7ede969fd37c1dcb042456e2c077d77bb92b85277e*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
✓
WSA
✓
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Zbot-9944779-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples
Registry Keys
Occurrences
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\DIRECT3D Value Name: LA 25
<HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS 25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SCHEDULE Value Name: NextAtJobId 25
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 25
<HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\S0 25
<HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\S0\RECENT FILE LIST 25
<HKCU>\SOFTWARE\LOCAL APPWIZARD-GENERATED APPLICATIONS\S0\SETTINGS 25
Mutexes
Occurrences
8548551525
Global\hfdjfodfjd25
Global\dasjfoisajfodsjf25
Global\e2jor3j25
Global\fjoidsfjodfj25
Global\fdsjofidjfoidjfad25
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
94[.]228[.]209[.]13225
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
b48b4b4c879e7211d6a13e26a8a914aaf6c218653840e81d9f[.]0[.]0[.]f3[.]method[.]in25
wpad[.]example[.]org25
6[.]0[.]0[.]609[.]2863923067[.]3163759174[.]0[.]0[.]b48b4b4c879e7211d6a13e26a8a914aaf6c218653840e81d9f[.]method[.]in25
609[.]b48b4b4c879e7211d6a13e26a8a914aaf6c218653840e81d9f[.]ofi[.]method[.]in25
computer[.]example[.]org24
vmss-prod-weu[.]westeurope[.]cloudapp[.]azure[.]com11
vmss-prod-seas[.]southeastasia[.]cloudapp[.]azure[.]com8
vmss-prod-eus[.]eastus[.]cloudapp[.]azure[.]com5
d2c0695a0769ff12288ba69fb11e0af359535884ecab0759bb[.]0[.]0[.]f3[.]method[.]in1
609[.]b87d1bc12f9cb258ada26bc6df5262a3fa055172129bde7cb4[.]ofi[.]method[.]in1
609[.]d2c0695a0769ff12288ba69fb11e0af359535884ecab0759bb[.]ofi[.]method[.]in1
b87d1bc12f9cb258ada26bc6df5262a3fa055172129bde7cb4[.]0[.]0[.]f3[.]method[.]in1
6[.]0[.]0[.]609[.]2902517135[.]125478764[.]0[.]1[.]d2c0695a0769ff12288ba69fb11e0af359535884ecab0759bb[.]method[.]in1
6[.]0[.]0[.]609[.]4275042737[.]1258892621[.]0[.]1[.]b87d1bc12f9cb258ada26bc6df5262a3fa055172129bde7cb4[.]method[.]in1
6[.]0[.]0[.]609[.]1016122232[.]3724806370[.]0[.]1[.]724aa02abdd63fe3c18870a2c1df84cb736adc287b72e33b14[.]method[.]in1
724aa02abdd63fe3c18870a2c1df84cb736adc287b72e33b14[.]0[.]0[.]f3[.]method[.]in1
6[.]0[.]0[.]609[.]3888551047[.]2272603056[.]0[.]1[.]fba5f83ba54c4af2afdaf3541afa94f949f74b3b1e9471ce08[.]method[.]in1
609[.]724aa02abdd63fe3c18870a2c1df84cb736adc287b72e33b14[.]ofi[.]method[.]in1
609[.]fba5f83ba54c4af2afdaf3541afa94f949f74b3b1e9471ce08[.]ofi[.]method[.]in1
fba5f83ba54c4af2afdaf3541afa94f949f74b3b1e9471ce08[.]0[.]0[.]f3[.]method[.]in1
609[.]a6025df4318e42aa7667fd8b0fde432c205df9e59413377709[.]ofi[.]method[.]in1
a6025df4318e42aa7667fd8b0fde432c205df9e59413377709[.]0[.]0[.]f3[.]method[.]in1
6[.]0[.]0[.]609[.]1498414586[.]656237423[.]0[.]1[.]a6025df4318e42aa7667fd8b0fde432c205df9e59413377709[.]method[.]in1
6[.]0[.]0[.]609[.]2635499747[.]3812587964[.]0[.]1[.]28bc88bae72017739b7e58329b29ac5b299cf4b82184cbab4e[.]method[.]in1
609[.]28bc88bae72017739b7e58329b29ac5b299cf4b82184cbab4e[.]ofi[.]method[.]in1
*See JSON for more IOCs
Files and or directories created
Occurrences
%System32%\Tasks\At2525
%System32%\Tasks\At2625
%System32%\Tasks\At2725
%System32%\Tasks\At2825
%System32%\Tasks\At2925
%System32%\Tasks\At3025
%System32%\Tasks\At3125
%System32%\Tasks\At3225
%System32%\Tasks\At3325
%System32%\Tasks\At3425
%System32%\Tasks\At3525
%System32%\Tasks\At3625
%System32%\Tasks\At3725
%System32%\Tasks\At3825
%System32%\Tasks\At3925
%System32%\Tasks\At4025
%System32%\Tasks\At4125
%System32%\Tasks\At4225
%System32%\Tasks\At4325
%System32%\Tasks\At4425
%System32%\Tasks\At4525
%System32%\Tasks\At4625
%System32%\Tasks\At4725
%System32%\Tasks\At4825
%SystemRoot%\Tasks\At25.job25
*See JSON for more IOCs
File Hashes 0300b2675abcbf21db5e97a36f9e091751872dc257e130af98fd4b10bf499696
0510ed5456e4bbce01cceb01666e8ae24ce7c95199273ed4f925f32b4a55cebe
09a9da4c73df7cdee323a25cacb777c4a6eec59aedbae1fac74fe5ead98ab335
0e9c204b0b517578b7b55253ac1f72adcd82300124a4766cdd186f297089d9be
11ab35c7796e53c9791fee0bf9f246c181b9d39a25b8f26362783852e8a2cf70
1496641a7ecebb0d7efbd8f4a15827a2ceac7750dff23f36507c2fa8805df68e
17139ef1297335a774429dddc40ecd8175709f9bb15919c00229668b14e43b66
17468bb72d1fc5ff1ba573433c584de2011981af133cd43d3d0a7b76435b32a6
17ba615707dc3801d4eb6bdcee1a15453f839191f6f9ba1acde5734574ca6ef9
1c45781b83aec8e12a8a367a8d25ed3f2c88212db10ecc8eb107cb09464505ee
23effdda466d05c04851d7c24c5c01d5c70f1b0c788120d6c110c446453caa06
2946646456ed67a37a35a85f55443e52d57d2d469703d000791251d53b0cd58a
29bcecb23328021aa8d549e1b5ebb415c04e3a6387de9b5726b52d616b71ddda
2e43e8419afe37118db8ff571717c01908be71403b709ba714dc18fce139820a
2f2c348a9bd01a8358ef0fad13ec867f285461d6f66ccaef32482390fd2036da
36e3d79fd7995f44c25261101a4145e8c47bd598b935facd58a77432c02796ba
39fe30b10918d57818125a3fd807c925d8435ccb63d53336771bfa2b39aa3b7e
406cc460d6c842650abef0b30d0f0669499d6e7f5ed8fb385bf3277cd69a5ff0
46b5eb754539c4b41fd84f870118aebe36246182b4c303a6d8fac86e71071002
49ef63b7625964ab183603437769e1b7d28b5a3bc837b1863092c6f4781ace5e
4ac817a7b3e74ab9a309a5d81428efe49bee6d650d8e3e59fe8e82574aacd0b9
502673f79ee90568efc721d3fd76bf46bfc242f1bf0db0658c87ad69e28a87e2
5038fe90e18af46f33f1d1f3e2297674efa6f56550feb1590f22012ea797e249
547a8bb06a123e6e2a06ee9d95dac4860d163fdc2ff9ff9a3ca39dda52edefc3
55ae0dc5d942e64b86eb9e6bb2ed648437517f82e51550c1baaab2a9434a937a*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
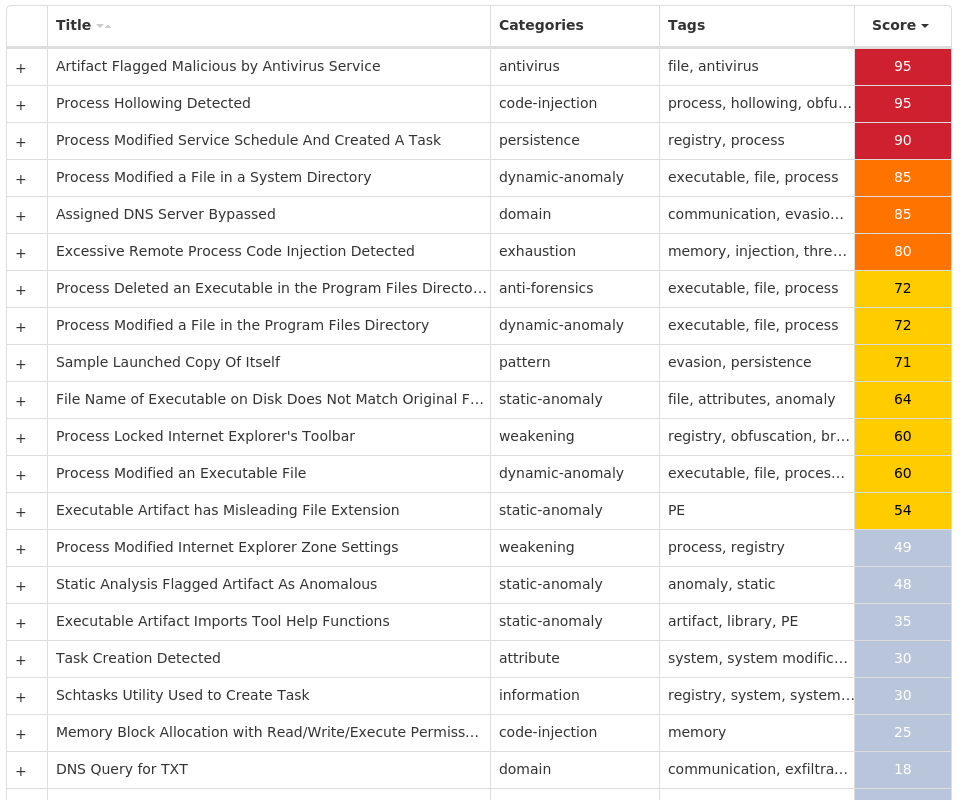
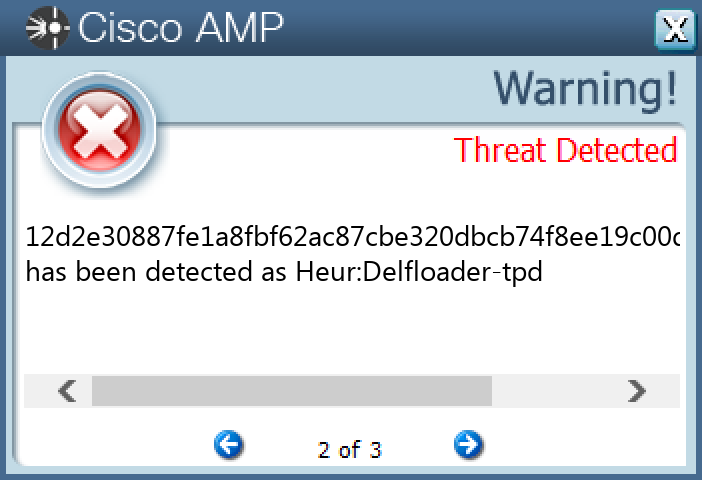
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Downloader.Banload-9944679-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 25
<HKCU>\FRMPRINCIPAL 25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: avgtrail 25
Mutexes
Occurrences
Global\<random guid>25
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
5[.]57[.]226[.]20213
107[.]152[.]27[.]1936
208[.]75[.]230[.]464
174[.]120[.]59[.]1872
174[.]120[.]59[.]1892
107[.]152[.]27[.]2011
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
www[.]argonios[.]webcindario[.]com6
argonios[.]webcindario[.]com6
typgutierres[.]webcindario[.]com6
www[.]reserva2[.]webcindario[.]com6
reserva2[.]webcindario[.]com6
www[.]box[.]net5
www[.]freewebtown[.]com4
www[.]tintalita[.]webcindario[.]com4
tintalita[.]webcindario[.]com4
www[.]lojacfsantos[.]kinghost[.]net3
www[.]tocadobrinquedo[.]com2
www[.]acetato[.]webcindario[.]com2
acetato[.]webcindario[.]com2
79[.]app[.]box[.]com1
vulcano[.]79[.]box[.]net1
users[.]cjb[.]net1
admarq[.]110mb[.]com1
www[.]argonio[.]webcindario[.]com1
argonio[.]webcindario[.]com1
www[.]albumfotos[.]webcindario[.]com1
albumfotos[.]webcindario[.]com1
Files and or directories created
Occurrences
%SystemRoot%\SysWOW64\service25
%SystemRoot%\SysWOW64\service\dhuidjkqwld25
%SystemRoot%\SysWOW64\service\dsanuix.dll13
%SystemRoot%\SysWOW64\service\02b2b1dc960b0b33e4b3c07a0e332f684554198591a46ad0df60ed6c00955fa8.exe1
%SystemRoot%\SysWOW64\service\0195a110d2acd6e1d96898a4c25ece898edc25b4d526db9124097770e32d8959.exe1
%SystemRoot%\SysWOW64\service\0ec3d674ada8eed243db8c33ea67edb6e8a46c21b28d883da2daef6e185d8b94.exe1
%SystemRoot%\SysWOW64\service\364d2ccf7728f575c61dbb223c509a5b159936540c5132081ef31c9167c2c86a.exe1
%SystemRoot%\SysWOW64\service\12d2e30887fe1a8fbf62ac87cbe320dbcb74f8ee19c00da8a29ef4741a857328.exe1
%SystemRoot%\SysWOW64\service\081b5279c8ca45a0265e1741617bc6dab432510d3f4e430eb1050a492b268d19.exe1
%SystemRoot%\SysWOW64\service\39d54ab89b5124062ed0f3a8167a39f2f72171640a098df11253615511b548f9.exe1
%SystemRoot%\SysWOW64\service\0ef657a40ef7b2c4d415552ed15d844dccc18fa8bbcffa40f8a13c0004af33be.exe1
%SystemRoot%\SysWOW64\service\393ca1fc5614e5c8c7d0dfa284eb79b7c8b11e301622e1bd62b11c1037431343.exe1
%SystemRoot%\SysWOW64\service\16036dd9d032db894ffc5370ac8285577426c06ad0467d696390eee81579cf39.exe1
%SystemRoot%\SysWOW64\service\1fb8413c5ed1afb34c9c4e89a3c8f2a15c40af76bb335097971c6fff0676006e.exe1
%SystemRoot%\SysWOW64\service\3ba485f04b12f653c8330c8d86a23460dc6387b8fb32579e147b42848a01be7f.exe1
%SystemRoot%\SysWOW64\service\3293ad6ab0b5a70ea83ac294007d24e9a7813026fcb479248928923e2811f0f3.exe1
%SystemRoot%\SysWOW64\service\3066f7a4f3da2c263181e50a79a3ed232b4a5921ebd3a2317f199ace8136b3db.exe1
%SystemRoot%\SysWOW64\service\0c82f9d452d8fc4306b2f018492581d458e7ce57bd43fdc4838d0d71a4e0ce00.exe1
%SystemRoot%\SysWOW64\service\3c9c1d8bdde803ee4edb4d35676358e366ef8573413a73a7c361d93f3a73dbc1.exe1
%SystemRoot%\SysWOW64\service\38dd0a85b6e84609b98039005a3d7d2ab90c4482163d89bc47cba37a283113a1.exe1
%SystemRoot%\SysWOW64\service\37d4778cee0166402a365e254df3f12c97ed1570b7fbad5b916a9c116bdfd698.exe1
%SystemRoot%\SysWOW64\service\4727015c94da26ef85aaf82cc3f1b5984c4df6e8d4bd01138fbcf6061baed3f3.exe1
%SystemRoot%\SysWOW64\service\1dd30000885dcf04580f7079df62e70cba43d237f566d784dfb2a360690ba05a.exe1
%SystemRoot%\SysWOW64\service\42aecbf7891ed110dc5c80968d658b048865c95b2d5695ebf10141ff0a4aaacf.exe1
%SystemRoot%\SysWOW64\service\5531a05f0ea677a30beade771ec23bdfbb4830577a02794ff55259fbffeb601b.exe1
*See JSON for more IOCs
File Hashes 0195a110d2acd6e1d96898a4c25ece898edc25b4d526db9124097770e32d8959
02b2b1dc960b0b33e4b3c07a0e332f684554198591a46ad0df60ed6c00955fa8
081b5279c8ca45a0265e1741617bc6dab432510d3f4e430eb1050a492b268d19
0c82f9d452d8fc4306b2f018492581d458e7ce57bd43fdc4838d0d71a4e0ce00
0ec3d674ada8eed243db8c33ea67edb6e8a46c21b28d883da2daef6e185d8b94
0ef657a40ef7b2c4d415552ed15d844dccc18fa8bbcffa40f8a13c0004af33be
12d2e30887fe1a8fbf62ac87cbe320dbcb74f8ee19c00da8a29ef4741a857328
16036dd9d032db894ffc5370ac8285577426c06ad0467d696390eee81579cf39
1dd30000885dcf04580f7079df62e70cba43d237f566d784dfb2a360690ba05a
1fb8413c5ed1afb34c9c4e89a3c8f2a15c40af76bb335097971c6fff0676006e
3066f7a4f3da2c263181e50a79a3ed232b4a5921ebd3a2317f199ace8136b3db
3293ad6ab0b5a70ea83ac294007d24e9a7813026fcb479248928923e2811f0f3
364d2ccf7728f575c61dbb223c509a5b159936540c5132081ef31c9167c2c86a
37d4778cee0166402a365e254df3f12c97ed1570b7fbad5b916a9c116bdfd698
38dd0a85b6e84609b98039005a3d7d2ab90c4482163d89bc47cba37a283113a1
393ca1fc5614e5c8c7d0dfa284eb79b7c8b11e301622e1bd62b11c1037431343
39d54ab89b5124062ed0f3a8167a39f2f72171640a098df11253615511b548f9
3ba485f04b12f653c8330c8d86a23460dc6387b8fb32579e147b42848a01be7f
3c9c1d8bdde803ee4edb4d35676358e366ef8573413a73a7c361d93f3a73dbc1
42aecbf7891ed110dc5c80968d658b048865c95b2d5695ebf10141ff0a4aaacf
4727015c94da26ef85aaf82cc3f1b5984c4df6e8d4bd01138fbcf6061baed3f3
4bb943491dd24b5983557d0080c675b0637323425b2f574e94e0e6ab805d3648
4ead99c96ced1cec5987e6492b62d8039f9aef40506af54f8219586138e05528
544d94c4086ebcd4487760974ca3469cb3223ee3bc7a63cef5f5d09416abc041
5531a05f0ea677a30beade771ec23bdfbb4830577a02794ff55259fbffeb601b*See JSON for more IOCs
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
N/A
WSA
N/A
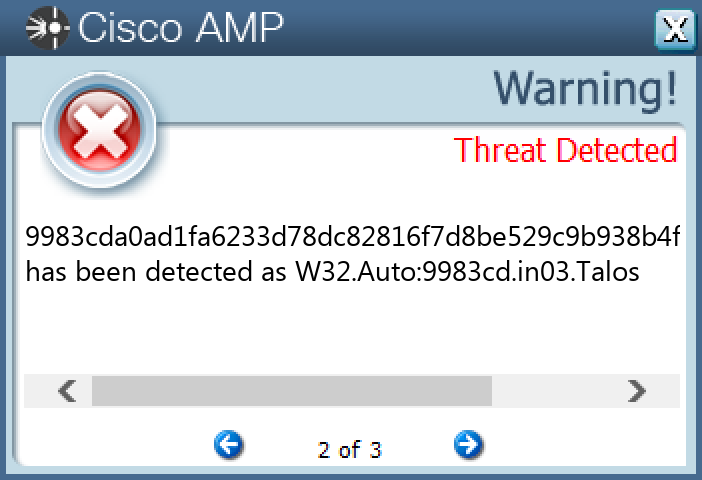
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Miner-9944721-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples
Registry Keys
Occurrences
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159 25
Mutexes
Occurrences
4pC39Ev2yuzFY8izw76DGDJR25
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
185[.]10[.]68[.]22013
185[.]10[.]68[.]12312
91[.]211[.]89[.]296
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
eu[.]minerpool[.]pw25
File Hashes 01b7e86d2925a3f65e7ded5966f21168c98d8eaeaef1757ba5aed24c32b8e024
0781ea60bd2cb928383af1073bebd6925b3f9b7cf3f6c53d2cc1da694be54a36
0ff381624efcc5a744e0cf2100035144111e0c2a5afa47713b896c581b13ee20
1111c6b3695099646f041c52a121b414c51dae804fb42f05e43350d7fdc1c4ff
17cffe2427097eb490ffe945cb02ce60b98ddcbb9f11c0e80b594332b3b58051
44a8f57b1733e94308c4478ef5d390cba0e2b896244ffbb28ebf3d01e4a4a410
4b7b0d7eb009bbf4409b2aeeb5ec7c26bb0ca280467867bc7c7f7a3fcc957967
56852bd8289dd9d56f650cd26c178fe9528bdd113a0a8f4b938113d8cd2e7fd1
5da22ae0744fba1edcc413ce109bc86da84630f55d16fdb57473ac9919859c2e
60f87050b4ba9b84bd7660eccca3b83598d41884cc9f92a4f6be231455539461
612c1f72048e28b9c22063ecc68a0690808d0a4f7d4ec4fce625989919d90e23
6afd0d6b2b5b4c8b161c1fecd394df7fbfe9d4c87709dfed1a515d38f67fc09f
719f44c5fac7dd508419e869750037b2b32e11c236ea6f1bb27f07b0c5313752
7430208ca68090a9c5ab8651c9c878ae00557a89213c447c73dcf2f28343d8bd
822f024a30ed68d42baf3c272ba9aae77e640cdd8803b9610c23f233ea575833
8949dae0e51052d128a99c79b3f99953020d843d1fa12fa9948e7b116d54a8ff
8b9cf6ab5b7364f88e21bd38c9713365d5a84faa2e4fc90c4163967eca29e309
9483e1d2da98a5a32be8a96b0703ee9520444e96c6b7bc7eaaf135d47ab72d2f
9983cda0ad1fa6233d78dc82816f7d8be529c9b938b4f478bb0f3456de42e6e5
9b1357513663adbfbb9f611310c45cc44b2b41f615c52134dab8263494d5dea9
9b3916b40d4fd02c8c47688a80ac12a6addbcbc6dde5c94bdc2aec7c4efea49f
b0ba1a0ff172477273402b048cb37874aa367ab31e4239016c7de95b88d978bb
b9d18413ec0b73f5dea538ee2f8ddcee07b42dd8aa4d4c0146fe9a4439051076
ba84e6e773655a2dc829794c7a77261a1df93b8dd8710ac92fb424895a20dee0
c10ff3c0d078d88aab7f570ed7bb9f63c99990132068d908de2a9ca0de56fcdf*See JSON for more IOCs
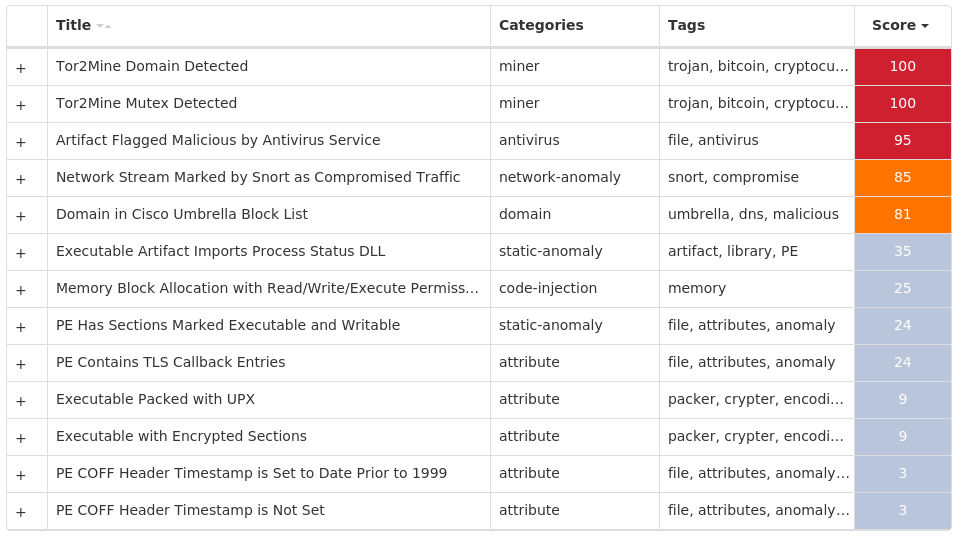
Coverage
Product
Protection
Secure Endpoint
✓
Cloudlock
N/A
CWS
✓
Email Security
✓
Network Security
✓
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
✓
Umbrella
✓
WSA
✓
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK