Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 24 and May 1. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net . here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Malware.Emotet-7682836-0
Malware
Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a wide variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails.
Win.Packed.Dridex-7683649-0
Packed
Dridex is a well-known banking trojan that aims to steal credentials and other sensitive information from an infected machine.
Win.Packed.Nymaim-7683937-0
Packed
Nymaim is malware that can be used to deliver ransomware and other malicious payloads. It uses a domain generation algorithm to generate potential command and control (C2) domains to connect to additional payloads.
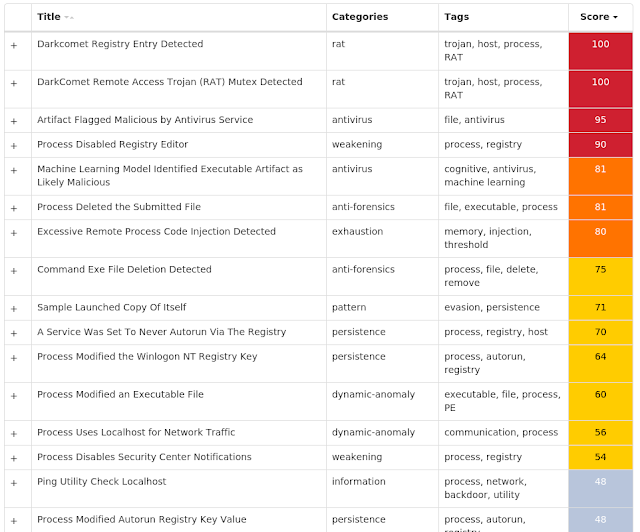
Win.Packed.DarkComet-7684517-0
Packed
DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. Capabilities of this malware include the ability to download files from a user's machine, mechanisms for persistence and hiding, and the ability to send back usernames and passwords from the infected system.
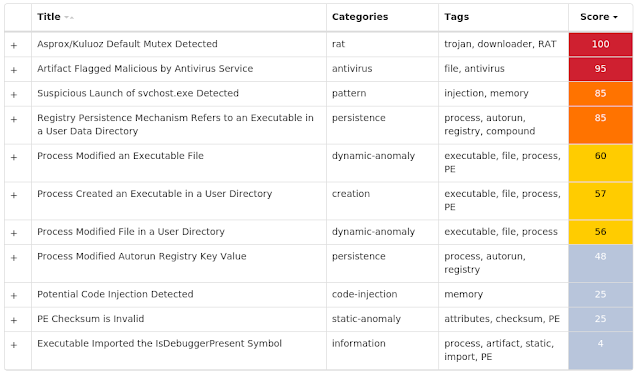
Win.Downloader.Kuluoz-7684621-0
Downloader
Kuluoz, sometimes known as "Asprox," is a modular remote access trojan that is also known to download and execute follow-on malware, such as fake antivirus software. Kuluoz is often delivered via spam emails pretending to be shipment delivery notifications or flight booking confirmations.
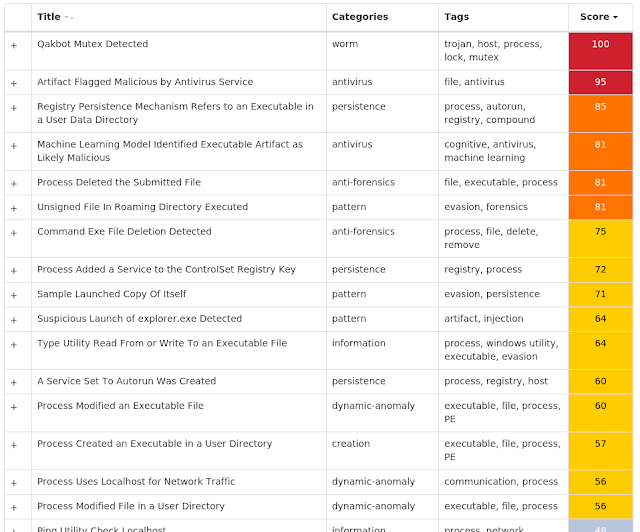
Win.Dropper.Qakbot-7726164-0
Dropper
Qakbot, aka Qbot, has been around since at least 2008. Qbot primarily targets sensitive information like banking credentials but can also steal FTP credentials and spread across a network using SMB.
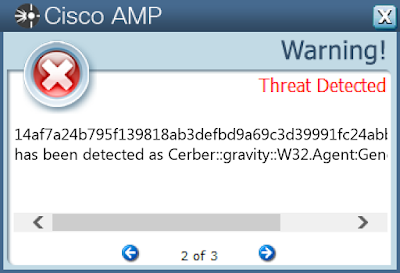
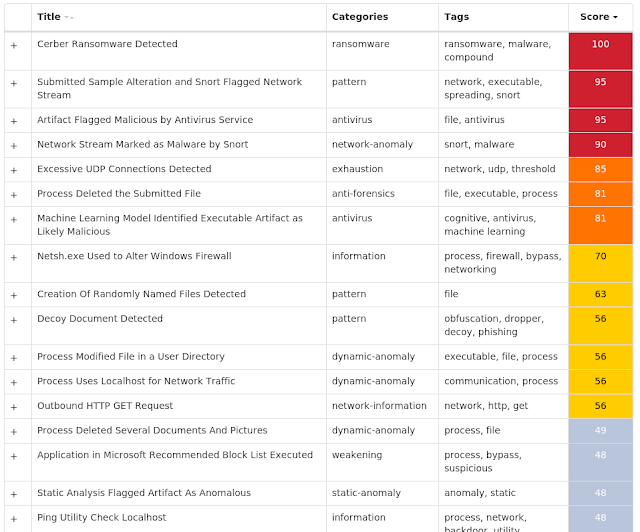
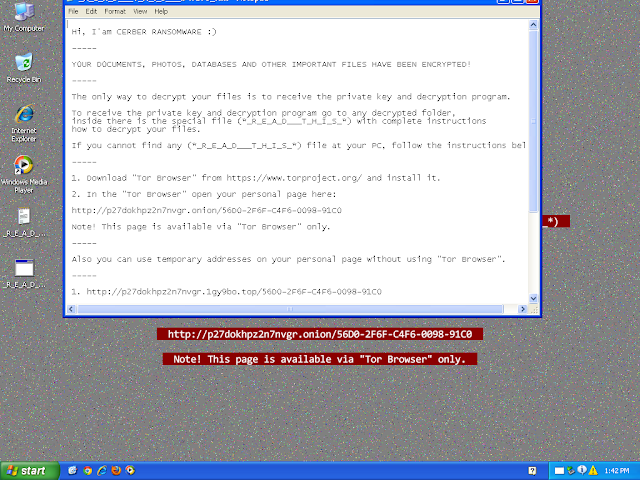
Win.Ransomware.Cerber-7699943-0
Ransomware
Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber." In more recent campaigns, other file extensions are used.
Win.Malware.XtremeRAT-7685153-1
Malware
XtremeRAT is a remote access trojan active since 2010 that allows the attacker eavesdrop on users and modify the running system. The source code for XtremeRAT, written in Delphi, was leaked online and has since been used by similar RATs.
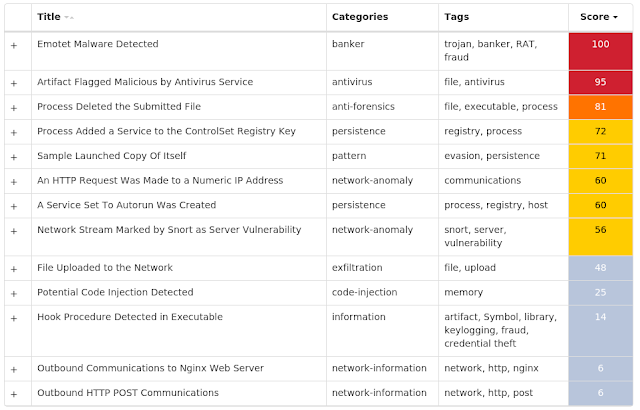
Threat Breakdown Win.Malware.Emotet-7682836-0 Indicators of Compromise IOCs collected from dynamic analysis of 33 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
11
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Type
11
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Start
11
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ErrorControl
11
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ImagePath
11
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: DisplayName
11
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: WOW64
11
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ObjectName
11
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Description
11
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDEST
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDEST
Value Name: Type
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDEST
Value Name: Start
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDEST
Value Name: ErrorControl
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDEST
Value Name: ImagePath
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDEST
Value Name: DisplayName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDEST
Value Name: WOW64
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDEST
Value Name: ObjectName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NLSDATA004B
Value Name: ObjectName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDYCL
Value Name: Type
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDYCL
Value Name: Start
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NLSDATA004B
Value Name: Description
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDYCL
Value Name: ErrorControl
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDYCL
Value Name: ImagePath
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDYCL
Value Name: DisplayName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\KBDYCL
Value Name: WOW64
1
Mutexes Occurrences Global\I98B68E3C
33
Global\M98B68E3C
33
Global\Nx534F51BC
5
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 70[.]48[.]238[.]90
17
103[.]31[.]232[.]93
11
152[.]170[.]196[.]157
11
124[.]150[.]175[.]133
5
152[.]231[.]123[.]2
5
104[.]236[.]52[.]89
4
239[.]255[.]255[.]250
3
103[.]38[.]12[.]139
3
51[.]159[.]23[.]217
1
Files and or directories created Occurrences %TEMP%\<random, matching '[a-f0-9]{3,5}'>_appcompat.txt
30
%TEMP%\<random, matching '[A-F0-9]{4,5}'>.dmp
30
%SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>
8
%SystemRoot%\SysWOW64\KBDEST
2
%SystemRoot%\SysWOW64\winsta
1
%SystemRoot%\SysWOW64\txflog
1
%SystemRoot%\SysWOW64\uniplat
1
%SystemRoot%\SysWOW64\traffic
1
%SystemRoot%\SysWOW64\nddeapi
1
%SystemRoot%\SysWOW64\wshbth
1
%SystemRoot%\SysWOW64\samcli
1
%SystemRoot%\SysWOW64\api-ms-win-core-localregistry-l1-1-0
1
%SystemRoot%\SysWOW64\mssign32
1
%SystemRoot%\SysWOW64\msvcr100
1
%SystemRoot%\SysWOW64\dispex
1
%SystemRoot%\SysWOW64\credwiz
1
%SystemRoot%\SysWOW64\occache
1
%SystemRoot%\SysWOW64\KBDBULG
1
%SystemRoot%\SysWOW64\wbemcomn2
1
%SystemRoot%\SysWOW64\sud
1
%SystemRoot%\SysWOW64\api-ms-win-downlevel-shlwapi-l1-1-0
1
%SystemRoot%\SysWOW64\vcruntime140
1
%SystemRoot%\SysWOW64\olecli32
1
%SystemRoot%\SysWOW64\NlsData004b
1
%SystemRoot%\SysWOW64\KBDYCL
1
*See JSON for more IOCs
File Hashes 0015b8f49dd3e9556abbdca601ec5b8606aa765a3d6f92891af13f2f5c3550c3
0501430e2925788715a0b58d1c62aced338f9939140ffae6caeb36a6042a4252
0a9b9090e79f075f23778ad28a9a531c4b141d7e127c76566c7f5a9f5e3cd234
10329e674b1ab26afbe66d239d586ae20c2b1794505d41c54176ab2d6902a8bc
1723e09aacabd295194e8ffcf50e21cfb73bef6defe35c258c50137a6deb1df4
1a9ac929db33d182b0fadfc253bb84722e7deb4671cb08eabcb640442fba5e6a
2a3b337ed79e479d85efd2e0038cf84ea56810b09853ac3f1196d63409b78af3
40a9b19edd0207c16fa6137aaf327a7ff5a2124f140b4592f3110127123882c5
4f63d65cfafbb0db6606bd8bb411da95fa4249f698826d726b0dddb822bd00fd
5a4d53e7bed6a08f6bd24baa1d67f6455687f813e39bb4d431e3fa489755ff3b
61a0848e33147562bdc08c64c2b10415857f54d75dfe45eee24d5c803c705b55
67c0f03a59645901e47c08518c710b674c7455e35c4483b6d2e2f0ea04f8614a
6fb122a65f8368702bf5933b9699aa0a1bb880fe5e4666aae84cdfbd8e3a1b73
74d66172a3a9bd315c8aecf78d43a7d6d63b48cb15f527eba65f6bf48f4276e6
772a38f28756d2fc4e101f4f50e82e4768dfdc4e13ee19a9515ea45e4819579b
77cc4cb2e7b6e93c984095b863b80799c33bae9184fdd808df61ac9b536cbcbe
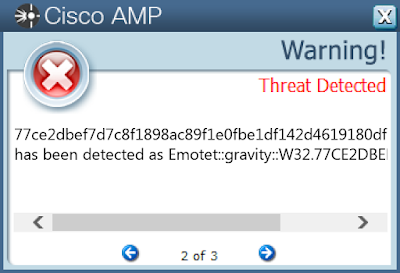
77ce2dbef7d7c8f1898ac89f1e0fbe1df142d4619180df7e923676c8240e85bd
7b0576064e60c67366f0eaceb9c6f23fc1f6654391eb0a170e6e71c5fc2e4808
7d782af49f8fbffb2002ccb221e2e67c57a767b923056cec89c158f731a2b099
7f436c24584b7eb54f50f31e9ee87b61834cc4f4061c68b6e5ee2fe0cb44ade4
804f82d7fa4a69355dc56eaba8a65dc5c09036405d06cdedb2267ed9efc265fa
821d6f372f3891411ebfc81d249b2ee266077098eab7bacc5c910d1364c68a5c
92be7efac03c4da13c572ec7f151d08d8b00cf5095b2100f66d06f506e573ebf
9cf2926b90684826ea6b1f204fb5a01ae2a2a5755cd27e81a26a1a73f9080940
9e24230fbb70ee6b3ca34138057954181baab27efa3ea90058940a1830eb4aef*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
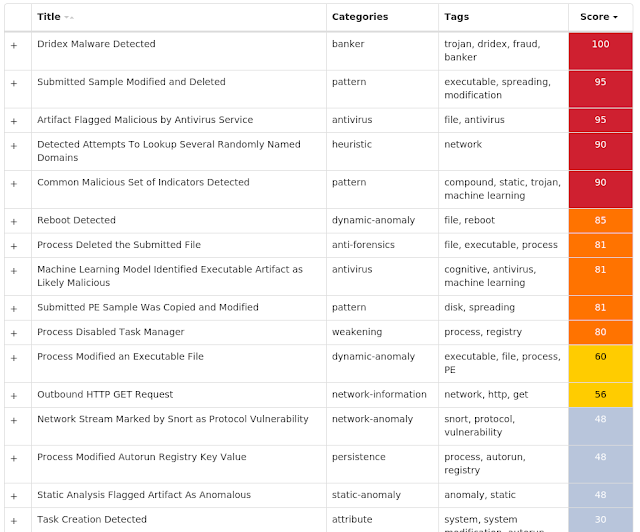
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK Win.Packed.Dridex-7683649-0 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: trkcore
10
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: DisableTaskMgr
10
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.CHECK.0
Value Name: CheckSetting
10
Mutexes Occurrences r2cS9yaSYd
1
931mUsI9mB
1
wjjmYrYQ5u
1
VifTUaJZhe
1
yaBqzAN82z
1
XhlHEmmxjv
1
zAITdaip8g
1
0Cj9jsHPvn
1
XkIMq6AJ51
1
5A3n9KYzR8
1
mrPam9azom
1
8hjP2ozHwz
1
s8BxkAkvLH
1
A9GxWuy80Z
1
Yzw99uDKC7
1
fe9RK4o66F
1
p5osKFiKAZ
1
pGpxuwTjuQ
1
0YLhQsqTTI
1
3UcT1da1ET
1
78m4rDg7R0
1
EX9mEG1KKT
1
ACHJV4Sj4o
1
FKTZNtNekW
1
RTgH5PBYsA
1
*See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 172[.]217[.]7[.]206
10
104[.]23[.]99[.]190
5
104[.]23[.]98[.]190
5
Domain Names contacted by malware. Does not indicate maliciousness Occurrences pastebin[.]com
10
www[.]ec9pbhuc3m[.]com
1
www[.]5jrbsxlfeq[.]com
1
www[.]tofam00uu4[.]com
1
www[.]af7p7ov2or[.]com
1
www[.]niijaaxqsv[.]com
1
www[.]ekq9jeogd8[.]com
1
www[.]muyjze3f71[.]com
1
www[.]wm0vpjbt8q[.]com
1
www[.]oearzzlgot[.]com
1
www[.]xdp1plibv9[.]com
1
www[.]t5th23jprc[.]com
1
www[.]bhagla4me3[.]com
1
www[.]7ty5rlprko[.]com
1
www[.]lg0xzs5na1[.]com
1
www[.]fr9hx7tsa9[.]com
1
www[.]ixknc7rhzu[.]com
1
www[.]dy30znpepv[.]com
1
www[.]jgnrmi7rhg[.]com
1
www[.]lybqeljypd[.]com
1
www[.]949ndbggae[.]com
1
www[.]ezdd7ayykk[.]com
1
www[.]vyi2mjy7wd[.]com
1
www[.]qkvnruupx3[.]com
1
www[.]ryebaopbzg[.]com
1
*See JSON for more IOCs
Files and or directories created Occurrences <malware cwd>\old_<malware exe name> (copy)
10
File Hashes 6246ef32aa403e0206abfc9a3154fe2010f72e7a3ce6c47b9caa2eae1bee8fa5
64495c2955fbc293dc4a96661e36b325d714d50020224ebcc8b2dc2428bf08dc
6fccd50bd4c04ca0e22fa06566873bf0a4df6ed6cc67fcd47eb547343e980287
7522ff8361dc6ce55b81aaa88022fc99cefb9e9227920d0374e922b63d4b28f4
7705808022d90ae37a977d0d3187dcd24f074375068381d52b07bd9e08995071
7cbd11ea5e754e2f3f7f6b48461be3c1493da5eca7ba18c35ec6fb9016a20f7c
a77b5ea9422470b3e9c689301a79b0fb036cacff0f26bbb19fd6936b53be3d64
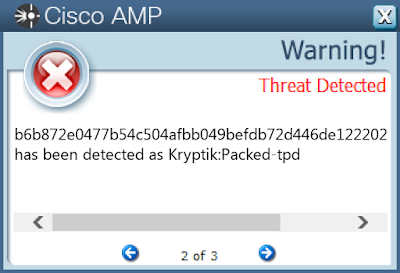
b6b872e0477b54c504afbb049befdb72d446de122202a08a3526b912f941792c
f53fa08e106bbf3496b111b12c21297571234dc021f10840c458c6828b85df66
f696fe55b1e0730b7bc5814a191f27e286e11b31d65b701c5dd54c9da1dc3f74Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK Win.Packed.Nymaim-7683937-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\GOCFK
25
<HKCU>\SOFTWARE\MICROSOFT\GOCFK
Value Name: mbijg
25
Mutexes Occurrences Local\{369514D7-C789-5986-2D19-AB81D1DD3BA1}
25
Local\{D0BDC0D1-57A4-C2CF-6C93-0085B58FFA2A}
25
Local\{F04311D2-A565-19AE-AB73-281BA7FE97B5}
25
Local\{F6F578C7-92FE-B7B1-40CF-049F3710A368}
25
Local\{306BA354-8414-ABA3-77E9-7A7F347C71F4}
25
Local\{F58B5142-BC49-9662-B172-EA3D10CAA47A}
25
Local\{C170B740-57D9-9B0B-7A4E-7D6ABFCDE15D}
25
Local\{74966FCB-4057-0A33-C72F-DA1761B8A937}
25
Local\{457A7A9B-5537-F010-1620-E1BCC38A93D1}
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 66[.]220[.]23[.]114
25
64[.]71[.]188[.]178
25
184[.]105[.]76[.]250
25
Domain Names contacted by malware. Does not indicate maliciousness Occurrences jtmuapq[.]in
25
lmajnkhq[.]pw
25
nhyriuyahve[.]com
25
vdodmwmxvi[.]pw
25
hwzkyadomjg[.]net
25
bcwbeoyp[.]in
25
zlzefe[.]in
25
rscrhvlfkbs[.]in
25
Files and or directories created Occurrences %TEMP%\fro.dfx
25
\Documents and Settings\All Users\pxs\pil.ohu
25
%ProgramData%\ph
25
%ProgramData%\ph\fktiipx.ftf
25
%TEMP%\gocf.ksv
25
%ProgramData%\<random, matching '[a-z0-9]{3,7}'>
25
%APPDATA%\<random, matching '[a-z0-9]{3,7}'>
25
%LOCALAPPDATA%\<random, matching '[a-z0-9]{3,7}'>
25
%ProgramData%\v3rdq
10
%LOCALAPPDATA%\g0tb0x
10
%APPDATA%\9763
10
%TEMP%\bpnb.skg
1
File Hashes 04d1b65b02f9df9a4ab0f11e4a6c22c29beed17f66c6c34a4adda3a0353df23a
0848062314c6c74ac38ed598d05ac1d96d18b992743dae7a9de3dc423283ded5
0b90e3c997823004e571a1769edf902567b2b4faacbd9091245f03e8bdb27307
0bd7490f558b35df99e7170034344354b31e8179a45500d34d0ef8ce9df4feed
1314f7f318afe16c1b70d74f24c3ed894a8153d655a0ca12055eabaa92a947d5
1499fda7a05ed4817f8b3a5ce8ed0abb397ca87f0ec1ccd31f31c50d07e0e5da
27dca594a187cb306d0b1ce4f06ed3bb0c05997d757cc328b9ada3422fa6a17e
2c721ba6a470ac3531137e655172e7c75fb4403626f45dec2361380026abd4bc
2d474abd2adc281a9a3fcf801bbab50372672e78d270e201ac0e5a2d2a91aecc
2eabbe4630643d728457336fc865127896a48ce6e2d6f945125f0bab499fdcae
32958bc88e5e52e5c2eaa8202a8b96895abb0fd6d48b4fadee10fd684480637f
386fae25d2204a1d570a91fb6e630d24358b81316f815caf9af4fea2f7a41bc9
3c3eb520100820348743dd5313e5025112a2915cc17270ba0c9366062d2b397d
44271dea39e672bf7a0d739f1d781a14891b7bc38886baa0fcae2c731c15754e
516713fc196746170b143c6026d3b2891e4d273a453e18943f273f91f379798f
54fd0a34de6e76b65a5b317a6e4fa8c96e4e8e7bcc275436b117cbbae82e8b67
5bc8bdb71d0fb24b1d816bf7ff37e4006f1522864b09b10811eca1da330a9028
6e71d0c582b026a436f36d540397cde3c36fc5d8d4850ca3cb0f909b9c4ac4d8
7264eab700460e94dc1834ea8063b924a4e74f9a94fc04cd2d6797e92d2320b9
82471660d14e638cb1ff2c5f01c264431423a1414fe2f462ef263cd15d1ff932
8331b1912cce040fa2d28ea21a2a5ac9535364232f6cbaeee0638a0ee1f52dc7
8b58b6f3aba2162dc1cac43751937b8cc4f424137b6a19f1ade66ec8c9410d7c
9193dd6596650b6b62939843e1b02c00d18c1ab35e188f95e99e6ae2fe46fef4
96b1db11f0c9deed48f8d8254652448b450cabc64e3a43467294e744b636b023
9853fbd835c993d014fdb0dedfe9da76787290dcfcc81e9e680585c7cf8bffa8*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
WSA
Screenshots of Detection AMP ThreatGrid Umbrella MITRE ATT&CK Win.Packed.DarkComet-7684517-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKCU>\SOFTWARE\DC3_FEXEC
12
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: UserInit
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: MicroUpdate
4
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UpdatesDisableNotify
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: DisableRegistryTools
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: DarkComet RAT
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Default Key
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLUA
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusDisableNotify
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CURRENTVERSION\EXPLORERN
Value Name: NoControlPanel
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: winupdater
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: AGP Manager
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: cftmon
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Startup RegKey Name
1
<HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES\75E0ABB6138512271C04F85FDDDE38E4B7242EFE
Value Name: Blob
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CURRENTVERSION
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CURRENTVERSION\EXPLORERN
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: windows
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Server
1
<HKCU>\SOFTWARE\TESTE
1
<HKCU>\SOFTWARE\TESTE
Value Name: FirstExecution
1
<HKCU>\SOFTWARE\TESTE
Value Name: NewIdentification
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{48B8DGFH-W775-4SJ5-Q0WE-T3340887668K}
1
Mutexes Occurrences DC_MUTEX-<random, matching [A-Z0-9]{7}>
9
<random GUID>
7
DCPERSFWBP
1
_x_X_UPDATE_X_x_
1
_x_X_PASSWORDLIST_X_x_
1
_x_X_BLOCKMOUSE_X_x_
1
Local\https://docs.microsoft.com/
1
***CryptoSuite***_SAIR
1
***CryptoSuite***
1
@NM=GS8@FD@>6S?NHIQM;2F*47KKU5BVZ
1
MFL
1
DCMIN_MUTEX-HPFX0T7
1
Global\{eef9b1ae-b262-4633-aa41-39a8aee8487f}
1
Global\8756fc41-85f5-11ea-a007-00501e3ae7b5
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 1[.]1[.]1[.]1
2
13[.]107[.]21[.]200
1
204[.]79[.]197[.]200
1
172[.]217[.]197[.]155
1
151[.]101[.]0[.]133
1
151[.]101[.]130[.]217
1
152[.]199[.]4[.]33
1
65[.]55[.]44[.]109
1
20[.]36[.]253[.]92
1
151[.]101[.]192[.]133
1
23[.]51[.]186[.]146
1
172[.]217[.]7[.]142
1
52[.]204[.]201[.]207
1
140[.]82[.]112[.]4
1
81[.]225[.]213[.]55
1
72[.]175[.]8[.]209
1
176[.]154[.]76[.]13
1
217[.]121[.]10[.]140
1
88[.]165[.]14[.]214
1
23[.]59[.]221[.]43
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences schema[.]org
1
www[.]google-analytics[.]com
1
stats[.]g[.]doubleclick[.]net
1
github[.]com
1
avatars1[.]githubusercontent[.]com
1
az725175[.]vo[.]msecnd[.]net
1
aka[.]ms
1
avatars3[.]githubusercontent[.]com
1
developercommunity[.]visualstudio[.]com
1
cdn[.]speedcurve[.]com
1
w[.]usabilla[.]com
1
growtopiagems[.]us[.]to
1
nutss21[.]ddns[.]net
1
minemooo[.]mooo[.]com
1
hask000[.]ddns[.]net
1
testr4t[.]ddns[.]net
1
defqon[.]no-ip[.]org
1
pyxelrat[.]myftp[.]org
1
rxttconfia[.]no-ip[.]org
1
Files and or directories created Occurrences %APPDATA%\dclogs
7
%APPDATA%\Imminent
7
%APPDATA%\Imminent\Logs
7
%APPDATA%\Imminent\Logs\23-04-2020
7
%APPDATA%\Imminent\Logs\24-04-2020
6
%TEMP%\MSDCSC\msdcsc.exe
2
%TEMP%\MSDCSC
2
%LOCALAPPDATA%\Default Folder
2
%LOCALAPPDATA%\Default Folder\Server.exe
2
%HOMEPATH%\Local Settings\Application Data\Default Folder\Server.exe
2
%TEMP%\UuU.uUu
1
%TEMP%\XX--XX--XX.txt
1
%TEMP%\XxX.xXx
1
%APPDATA%\logs.dat
1
%System32%\drivers\etc\hosts
1
%APPDATA%\MSDCSC\msdcsc.exe
1
\Windupdt\winupdate.exe
1
%APPDATA%\Imminent\Path.dat
1
%ProgramFiles(x86)%\AGP Manager\agpmgr.exe
1
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat
1
%APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\task.dat
1
%System32%\Tasks\AGP Manager
1
%System32%\Tasks\AGP Manager Task
1
%HOMEPATH%\Documents\MSDCSC\msdcsc.exe
1
%HOMEPATH%\Documents\DCSCMIN\IMDCSC.exe
1
*See JSON for more IOCs
File Hashes 0b735faafe0b163bcbf2cfa89ba3e7a57f8e41b7483d867013449c4b6aa63eba
0e156e7cffd949484758261e8fed0a0b0cfc5eed757603ac5102839a73a9f368
25c4550ad94101ac8c4106a3c4bd0f922aab456be370eddb331d0056d80ccb98
387a94a474fdd1fe37973dfe0126a239699ba216384e5b943beaa4d12b9c44fc
3c60fb77be69e9824eac6503aa8997bb71a148a10aca9d6bffaf2164819a5327
3de72f9f4b8c8f7ce322a462843390768b2cba1ddbe553cfaaae00c689eb46ba
42e460f29c78dd866892386f87505b77ada9b70891ac8212e00c30e75382a329
53f90d6860c61ca7846a4ecddbdc81ac59f8d04005a58079f7577271c9e68866
58792d71faf0f1f865d4f082fac16d78494761d843aa96757e0b2209ebb2868e
5ba0f728f1c40309f2073ec41b006a218860395f4d5569ac52b17f1337c6fcda
65b4482a1dc15cb0ea7f6d939d330b7138c0e60269e5e2a394fe8a142a0bd9a8
6b1ba39b1c059feb656ecbad136366616eb7913d0d97c7ef547572c9b129c15e
6d27b43d82f528580e59846c89a7db8e4dc6628ad55d0cb5fb96f87ede5b1edb
75ecfa713f8c03fd44fbd212059b797cd960588f7269ee952f496d8b01002867
78ad6b940449a36a043060e5b2d93d35c0bf728a7a998a1d70024ed3c9a80bec
7c1e39ee5d822c7a01f7113ea85089963973508ced5cb98ad2e32aef36d4ebcd
8ced8315ed75b2de8dce62056a63843be831cb1dde75945f3a8e0beea59581b7
9833ee64ef4cc0dcb7f86735a61c38d8388843fa2eb158793a27a27d636ab8ab
9ab5fd0a062b1934f6c22dab3a38ac1125b4cc03116a656ecc5867ce48767f39
a5a0efc3d68194458aed571e0aadb94effe597f2640523bc5bcbbfaee5c25f41
b868eae752ec77eb67bbb05f78c3456494373aaaab991595a8a785e6fdeb1ea9
be06f3a809cd0757d0b928fea839afd4ca32d4020bb98f70e3dde26180097280
c1760b233c5925ebd245a854235c5909c63a622279630bd7291bfb6d37130cd4
c32b8fa61c0d97ea37d027d1876f34e9c8938c1daa60588f49ac6083b6d23e61
cb1354690f9933eedbda842028f81745eb4b30eb9913136a1390b04ecf97b6f3*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK Win.Downloader.Kuluoz-7684621-0 Indicators of Compromise IOCs collected from dynamic analysis of 130 samples Registry Keys Occurrences <HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'>
130
<HKCU>\SOFTWARE\KVEVCRPN
Value Name: eoxeibrs
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: cqwmjmoj
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: oqkjbkul
1
<HKCU>\SOFTWARE\FCSRTDQI
Value Name: hxqiiowt
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: tjesahfu
1
<HKCU>\SOFTWARE\VINDGLMI
Value Name: baqldbpr
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: fklxrpch
1
<HKCU>\SOFTWARE\NKRAIPBX
Value Name: rbeejfdr
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: tupwmwhc
1
<HKCU>\SOFTWARE\QLUPIUTR
Value Name: kcedhlpe
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ifnqbivd
1
<HKCU>\SOFTWARE\WUQQNUQI
Value Name: rbprlkga
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: genbjvjd
1
<HKCU>\SOFTWARE\JLXMNDEB
Value Name: roghnhdl
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: kfctlmoo
1
<HKCU>\SOFTWARE\WSPVUKER
Value Name: omavrsga
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: wmlgvopr
1
<HKCU>\SOFTWARE\BSUCGPLT
Value Name: siuifekg
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ntinwikq
1
<HKCU>\SOFTWARE\VSNBDBWG
Value Name: dokanrjo
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: uniaampj
1
<HKCU>\SOFTWARE\VQIEKUDA
Value Name: moobxslo
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: pghlaqnd
1
<HKCU>\SOFTWARE\FDXTGGOX
Value Name: ntjbnvgg
1
Mutexes Occurrences 2GVWNQJz1
130
CCXPO_13_wKSU
130
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 173[.]192[.]72[.]226
94
198[.]0[.]216[.]35
88
113[.]53[.]247[.]147
83
81[.]177[.]22[.]90
83
151[.]3[.]8[.]106
81
91[.]142[.]223[.]136
78
196[.]211[.]170[.]187
78
91[.]121[.]177[.]88
73
76[.]74[.]184[.]127
72
Files and or directories created Occurrences %LOCALAPPDATA%\<random, matching '[a-z]{8}'>.exe
130
%HOMEPATH%\Local Settings\Application Data\hwpcjlqm.exe
1
%HOMEPATH%\Local Settings\Application Data\xofsfqvf.exe
1
%HOMEPATH%\Local Settings\Application Data\kwoisujq.exe
1
%HOMEPATH%\Local Settings\Application Data\pexvaadg.exe
1
%HOMEPATH%\Local Settings\Application Data\hquwwbhh.exe
1
%HOMEPATH%\Local Settings\Application Data\bdogvdqm.exe
1
%HOMEPATH%\Local Settings\Application Data\vkwfijko.exe
1
%HOMEPATH%\Local Settings\Application Data\mnrradhj.exe
1
%HOMEPATH%\Local Settings\Application Data\vkwgrkwq.exe
1
%HOMEPATH%\Local Settings\Application Data\rqteojat.exe
1
%HOMEPATH%\Local Settings\Application Data\xofvdock.exe
1
%HOMEPATH%\Local Settings\Application Data\pnjndgpb.exe
1
%HOMEPATH%\Local Settings\Application Data\rxkqrfeb.exe
1
%HOMEPATH%\Local Settings\Application Data\lpwhbjme.exe
1
%HOMEPATH%\Local Settings\Application Data\wmbhaxqj.exe
1
%HOMEPATH%\Local Settings\Application Data\omnbnvvm.exe
1
%HOMEPATH%\Local Settings\Application Data\hgwlfrew.exe
1
%HOMEPATH%\Local Settings\Application Data\riumolxv.exe
1
%HOMEPATH%\Local Settings\Application Data\ccrridef.exe
1
%HOMEPATH%\Local Settings\Application Data\gqexkxad.exe
1
%HOMEPATH%\Local Settings\Application Data\vqkqhwcx.exe
1
%HOMEPATH%\Local Settings\Application Data\dtkmfljp.exe
1
%HOMEPATH%\Local Settings\Application Data\dtsqmdtx.exe
1
%HOMEPATH%\Local Settings\Application Data\fcitkmec.exe
1
*See JSON for more IOCs
File Hashes 000e901c6da4baec48f43026148f4a4fff543935548ab65e373589f00e0d60ac
0947060cfdf400caabb5c38b95a2ddf18022c068980adf9589d8b3e24b8f930a
0c600818bf33cd0db69e8a0d95d5306ad1275838cb7725b766e39f4037ba85fc
0c89c3d3b87282820bd8c8ce23534b621c716814e5fe1e84f5332a55a1cdf8c0
0cc466185eec91b61d5bad3eab7074c6154a3a8ef191a566b5544d01face0f29
0ea7692c58aa869bf1e1a1d959274a26ecbd937858ad99389c2f126223e377f8
0f142fc20767209db77363ecb4477a26fda0fe4357ded001bfb80869a99d042a
1010414d9a14196ff13af4972eac28e8857d4effc518e7185c2f825c735d29f9
12143da996d21c7a54a09b018049aae70aa7936748e4c8bca9e1ef6473f3c224
13ab908d1c57dc9dd16df162216ccc828702f6fee1f8a52bde0def63059bb799
16ca550176d867db56add27591bb337f21928fdd730ae2b9e1421ca7c93bd8cf
18728830651c252d694fd244b32069978981fa4e8cd6a3d01518eb57eac3ff9b
19ec2bf9148978bc545b5cc4de8fee81dab697b4e6ac348356a863585a3ff49d
1af13bdf961b00d3897196e913f7a8fda04553ede0f3d5cf14c349a3d62e99ac
1d053a0ffd16bf81e04d22b28a87d4a4b7fd6739603d19c555d0b9792d37b021
1d8e6d0edcbdd625e65617be152d12d9423a1f96f0e3bd55e3645ac9f12fde96
255730a4b2d4a1b93ed45581d0cd90bfdf7637c53e9242f55a746b41c5793ef8
2865c34e2066f4c0bc455c2fdcdcce57ccb321bb45ce86670923211c7839dcf4
28d5b0303431b5bb5bcaf89a9147e80bdf13d70a78f2442b8699f6e775176ebe
28def12539ef716b2513a56b30825cd1ed4a2c0f7518673a39326e1ae1a8dff8
292c097b4be846017d64115272befa689bc1f3d406e4c20a0fbbca138333613a
2a202677d2c116700150455934ae798f6f380496fc7e494375628e3f9e3d6898
31180a1d86f0a03ddc78ad1bc50dda2378e4359e79fdd9dfa35579b32ac62e52
35436998d4174730e485b6b83fbabac62b031264dab619a1f5ec66215a110a76
359b6985beefe22aae9d15e2c5d9ee05ce4162d563603c5cd26f841ce8daa369*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK Win.Dropper.Qakbot-7726164-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\AVKAXOQ
Value Name: Type
19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AVKAXOQ
Value Name: Start
19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AVKAXOQ
Value Name: ErrorControl
19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AVKAXOQ
Value Name: ImagePath
19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AVKAXOQ
Value Name: DisplayName
19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AVKAXOQ
Value Name: DependOnService
19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AVKAXOQ
Value Name: DependOnGroup
19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AVKAXOQ
Value Name: WOW64
19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AVKAXOQ
Value Name: ObjectName
19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AVKAXOQ
19
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AQEJPWSX
Value Name: Type
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AQEJPWSX
Value Name: Start
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AQEJPWSX
Value Name: ErrorControl
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AQEJPWSX
Value Name: ImagePath
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AQEJPWSX
Value Name: DisplayName
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AQEJPWSX
Value Name: DependOnService
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AQEJPWSX
Value Name: DependOnGroup
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AQEJPWSX
Value Name: WOW64
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AQEJPWSX
Value Name: ObjectName
7
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AQEJPWSX
7
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: nafs
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: uqhd
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: vkxpdsd
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: sxuwptqb
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: gyame
1
Mutexes Occurrences llzeou
26
<random, matching [a-fA-F0-9]{10}>
25
<random, matching [a-zA-Z0-9]{5,9}>
25
Global\amztgg
19
amztgga
19
Global\eqfik
7
eqfika
7
<32 random hex characters>
7
Global\uesljahq
2
Global\pabunoq
2
Global\akiot
1
Global\zaedan
1
Global\imyuiwlg
1
Global\pitkso
1
Global\ybyswmes
1
Global\iaayeekk
1
Global\vogeg
1
Global\imzdodo
1
Global\ishzq
1
Global\vjoge
1
Global\xpvyyl
1
f28e24912d37bfd7b81afdcb8079fd29Ð÷L Administra
1
Global\wyrcaqd
1
Global\hqxrysov
1
Global\epyaiaia
1
*See JSON for more IOCs
Files and or directories created Occurrences %APPDATA%\Microsoft\Amztggm
19
%APPDATA%\Microsoft\Amztggm\amztg.dll
19
%APPDATA%\Microsoft\Amztggm\amztgg.exe
19
%TEMP%\~amztgg.tmp
19
%APPDATA%\Microsoft\Eqfikq\eqfi.dll
7
%APPDATA%\Microsoft\Eqfikq
7
%APPDATA%\Microsoft\Eqfikq\eqfik.exe
7
%TEMP%\~eqfik.tmp
7
%APPDATA%\Microsoft\Pabunoqa\pabuno.dll
2
%APPDATA%\Microsoft\Pabunoqa\pabunoq.exe
2
%APPDATA%\Microsoft\Uesljahqe\uesljah.dll
2
%APPDATA%\Microsoft\Uesljahqe\uesljahq.exe
2
%APPDATA%\Microsoft\Imyuiwlgm\imyuiwlg.exe
1
%APPDATA%\Microsoft\Pitksoi\pitks.dll
1
%APPDATA%\Microsoft\Pitksoi\pitkso.exe
1
%APPDATA%\Microsoft\Iaayeekka\iaayeek.dll
1
%APPDATA%\Microsoft\Iaayeekka\iaayeekk.exe
1
%APPDATA%\Microsoft\Imzdodom\imzdod.dll
1
%APPDATA%\Microsoft\Imzdodom\imzdodo.exe
1
%APPDATA%\Microsoft\Vogego\voge.dll
1
%APPDATA%\Microsoft\Vogego\vogeg.exe
1
%APPDATA%\Microsoft\Ybyswmesb\ybyswme.dll
1
%APPDATA%\Microsoft\Ybyswmesb\ybyswmes.exe
1
%APPDATA%\Microsoft\Ishzqs\ishz.dll
1
%APPDATA%\Microsoft\Ishzqs\ishzq.exe
1
*See JSON for more IOCs
File Hashes 0035286d2a15565f04dafad9f9c962e647ed1f35a637a42a60724a165ea696c1
070349109365a2cc9ac66ffe3abab024ac962c527c7de043d4b9c785e408af41
08e9009545c6734ee1a22acd34536df2bf139d69e011a2ff7d50bc758c72b4c5
094822654bc5270d9bee04766ff3a374eca403fc48206b4e0f87a78017b836f4
09af9d8f27f111a02bc102a28360d4a19ea7b0f0c6a2339e5cb5d9b80e5fba9a
09ee7246eb6db6fca0d2a83afb536d3d7766dc5e697bca576ef290b981546e3e
100c2b868de3d4cb419a43b1a0308f6d50b8ab6bbacfb1d399bacb08b5cddd3f
140ee794676c3e8e8977e51804a4acc1c26665c702cd4837950f6f3358f0c07c
15803e553626933033ceb8ebd5f5dd20e8f97fdcf6f3ed19fba971ea2d4ec09b
174bb146df227b403f1184cc887f3bc3209864f0810cf0e9d355163a14d4de5e
17e09c8774ce1060c99a69fd8331b662aebe8470ad818f8f3ce58a4bc1478d4b
1c16e1c550fb5edb91174f4568d59d2174980bb3567643e290cfba3638cd9275
1cd12ce6570e0e6048dd1c2fe3eae56d2751c3ab60d252a818145c19070f520b
1d8161e41b050503a1c407a397d83264da618439a085db7917bfae695f573442
1fe70f8fcd0d4aa563009cbe96abd9ba45cd259ae540d910e81159ace294562f
20322be8bba2b0260bb49759e298ac3c150609535b6f0c6d6706e8efbed164e9
205a6e0321633133395d55a7a21c8756308dbc43a7175916693afcf338e017cd
20ed1b1f7d0cbafbbda0ba199273202fda7deb285bf3484b8d6dc765739ad90b
22d0b589887fe42608fd42b7b5b4aad8b38d97758f4c28f1e7fb40e0c940013b
24431fadaa150200c48d437ce84f9901a78cb1c2e871037f4caccae4a31abdc4
25a376c596dc821bb9c2abedbacfd22f12230032f7576a50f1b78a704297bb3d
2772742210c6140fd538b368ccdc5b9d109cd402f7dd4fa0267a4ae8cca9587e
2d6a151f5d2d246ed708a92d794a95a4c259781b65e6c83acbaf0c5823a30f55
305a5a4d3c28f131cfada56706f8c70e85265e2f5d89a78699c3f89941efeb25
30f6c71d8035b3603f146f091d0afc01298776e70b66c5509dce5fb86179c4d2*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK Win.Ransomware.Cerber-7699943-0 Indicators of Compromise IOCs collected from dynamic analysis of 185 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
185
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
Value Name: PendingFileRenameOperations
185
<HKCR>\LOCAL SETTINGS\MUICACHE\\52C64B7E
Value Name: LanguageList
1
Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}
185
shell.{<random GUID>}
34
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 178[.]33[.]158[.]0/27
185
178[.]33[.]159[.]0/27
185
178[.]33[.]160[.]0/25
185
178[.]128[.]255[.]179
142
104[.]20[.]20[.]251
89
104[.]24[.]104[.]254
74
104[.]24[.]105[.]254
68
104[.]20[.]21[.]251
27
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]blockcypher[.]com
185
bitaps[.]com
142
chain[.]so
142
btc[.]blockr[.]io
142
hjhqmbxyinislkkt[.]1j9r76[.]top
43
Files and or directories created Occurrences %TEMP%\d19ab989
185
%TEMP%\d19ab989\4710.tmp
185
%TEMP%\d19ab989\a35f.tmp
185
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp
185
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.bmp
185
<dir>\_R_E_A_D___T_H_I_S___<random, matching '[A-F0-9]{4,8}'>_.txt
185
<dir>\_R_E_A_D___T_H_I_S___<random, matching '[A-F0-9]{4,8}'>_.hta
185
<dir>\<random, matching [A-Z0-9\-]{10}.[A-F0-9]{4}> (copy)
34
File Hashes 00ff48f6639d622ed89cee9f2e1aaea567dbd8d4bf12a7e4327c35380f94eb5f
0161ef6d3384e75a506b076ac7295b756a18b27855584b988e25a5f7a72579c0
01781767835618ecc5f2fb528fa8383d413235fb9922ecfc57bbbb77794b6cff
03429f5b6b0b19e815cc2c130e870bea8f2e763a72b4b0f8dcd152712c475923
03db909b35430debea115c5e8450ee0c4ee2db79cd0d9fd2ef2f61fb5408ac79
05bcd1582750db610b6f2e27b170887c8bec3751a1baa70a80fa6da6f4f5ee5e
06455ac6d07d35a22f67cc08ad8f5c45b60d2f14e054e630131ffac7aebbba4d
0794f49d36f3b13ff00604c858f977fbf0c7e0fa680209cad31a79ed8fb8c2d8
08d463d3534373c83c089d018b407621da1a508408c4ed0a243b4bf5601993d1
0a98e6bec51b7f7db37c94dea5cf3fcfb0da70855a328e090c89dda260bc7844
0adbbb464f02cabf1319e98f3e8f3092926dafbf4daab5d466604f3fa45f33c8
0b49c47f7a18c805fb37386d9ad9e9e390b50e5d6e9f199b95f19795026bf12a
0dc2e38832f18cfa2aeaf13abb2d640985f249192c1b72a0b8514ae58c2f6e32
10385f979b902e71b32605a6b673ef668e90b34799af018955aabe71a131662d
116a4eec66acff2e11c7827698f9edbbf9e0c47564a1278050eb77975c55be89
11726b17f749bb3c7b9fd30c120c9443c6381b5011f825c98c3f580c94930930
126bb42be6c0a5fa2d53b6e7f7623d2e54c40c999b5d12d66eef27b77244ca88
14af7a24b795f139818ab3defbd9a69c3d39991fc24abb595480e8c4ed168bc6
14efd50092e56558854d29d8d89668dc177d79d42b091a35df6bb828e86ec608
165875634f7728d42084dbb491e0c1ac56e2cd5c8aa0191348a6b5045d73c84b
185d66d675b2eacf57a1d5f8682061aebd9b7746a492b2fa7d11e7daeffefebc
1c17bd0f208b6585ecd68f4709c36e0f02b9de18a24a24ecece159f69852e203
1c7c8e8875c6869a0f141fd4c47d28bdc34a8e776d2f1aec69d852ce975f1128
1fd6753fe98f4c6c3659bb3665c5f6143529cf60725103f75a0b1934971e6a75
1fef0ab2f6d9eed47b94a8f76e9fa6057e36527d05e831e4fa1b11501ef2b267*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP ThreatGrid Malware MITRE ATT&CK Win.Malware.XtremeRAT-7685153-1 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKU>\S-1-5-21-2580483871-590521980-3826313501-500
Value Name: di
15
<HKCU>\ENVIRONMENT
Value Name: SEE_MASK_NOZONECHECKS
15
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: ParseAutoexec
15
<HKCU>\SOFTWARE\4ED9E6A300F8A49940285E2397655B25
15
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 4ed9e6a300f8a49940285e2397655b25
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 4ed9e6a300f8a49940285e2397655b25
15
<HKCU>\SOFTWARE\4ED9E6A300F8A49940285E2397655B25
Value Name: [kl]
15
<HKCU>\SOFTWARE\YSY@WZ+$V
11
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{MQF8HSLV-26W0-LG28-17P3-07TVKC8674EJ}
11
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: HKLM
11
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: HKCU
11
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{MQF8HSLV-26W0-LG28-17P3-07TVKC8674EJ}
Value Name: StubPath
11
<HKCU>\SOFTWARE\YSY@WZ+$V
Value Name: InstalledServer
11
<HKCU>\SOFTWARE\YSY@WZ+$V
Value Name: ServerStarted
11
Mutexes Occurrences 4ed9e6a300f8a49940285e2397655b25
15
XTREMEUPDATE
11
YSy@Wz+$V
11
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 94[.]73[.]36[.]254
11
Domain Names contacted by malware. Does not indicate maliciousness Occurrences bozokwebrat[.]no-ip[.]org
15
xtremewebrat[.]no-ip[.]biz
11
Files and or directories created Occurrences %SystemRoot%\temp\FolderName
25
%SystemRoot%\temp\explorer .exe
25
%TEMP%\tmp.exe
23
%TEMP%\dlhost.exe
15
%SystemRoot%\InstallDir
11
%APPDATA%\Microsoft\Windows\YSy@Wz+$V.cfg
11
%APPDATA%\Microsoft\Windows\YSy@Wz+$V.dat
11
%SystemRoot%\InstallDir\dlhost.exe
11
%APPDATA%\tmp.exe
3
%TEMP%\FolderName
1
%TEMP%\explorer .exe
1
File Hashes 05a09daf8160219a4a80403199ab37b22e6f54d55c668b3f635fd4476d0a8a59
090415c9ced7989e8c9ad65a131773616e6c91766a25750b03c8acaebb805e7d
0f3f453aeea499a8d86a3e72f35de2dc77715a4de23677e6bc17dfd456a62f35
2cc336e8966508db5ee2b10299bf87350b0201f7c4ab366f29567bd5e814e9da
2ff1a7ff2ba03de1d8a191fd33050b30c909c16c7eeabc21edb3bfbeb3510a3c
36504a9d21183f2b22661c5e782b5edf0b892104ac8100e676b9e7835c99d9aa
376c87460f9471b170ef68eaf2acfa43f1e084544c1a4ffa68a4f1a7de7a5e3d
39468dabb6cc656914369c4e7d29ecc7c4c7912763559458e15e09ddb1453794
3df86b0291dc758d9c1dbcbd92483e8115d58e163ded45ae0e023707a10987c5
489ec1726eede1c448a39a26cebb3c2c3ecce3663b608e660155c2082b10a1f6
5a195c810773e384e286a3d1cf6128431df79605e66801f960b874886ee26ed3
5d848cc23da9d068bac6503cf0f7367a543857434c2e52801e49d310eccd49ad
5dbd4a496a111211e57e7a0ed7b59baee0238fc3bad953e977505aa9ac13b622
629e45a9c909b08db3a55fb3a0b97ebc3666cc1dd2f15fd5ad41d2a449b543e5
684f30b2f6e0d3573f7c942e15a6657a7cc22f6a48e94999e0e32bf69c68493e
6986e642888d4be2ce1962d2fc510ded8b5e2e2b7b3030c799ddb7337adaa5e8
6ff6b2f5e91ec8d1b01efe3f974db2f857670e25d060c4d3ede1c0b8a9bfeff7
7b8234eb73eca0870cce0b01f61fa18ee7416622fe8707249d82a06a83a3eb55
92c29bca69bfdc69219e8caab4e8ad102edca1cf0aba1325027a6563449c9cf1
962814862ed445cdb8df6e35a59b6d4c7d85e0c5ed1d169b99c4e92a17363fe1
9d301e413dcab7642620735a680b80b5d083524cd4f374595e10270561f54a82
a2ec2fec47ed81a86fbb125be52ebb476ee85442959ce8b663583d25df5ae38e
a97bccc9d90b387c85b5823c9762eb159069ff09a72e88b41e519d3aa4324fb0
aa99e1a54cd01f4244aa0d5bdd1970927a0911e7885f23a2846f7cd7e38d1a9f
bfea435f85b14c96f9b9b2c7e70eb5f55c3cdddb0ebaf647283398ef461e86f5*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK Exploit Prevention Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. Dealply adware detected - (5832)
DealPly is adware, which claims to improve your online shopping experience. It is often bundled into other legitimate installers and is difficult to uninstall. It creates pop-up advertisements and injects advertisements on webpages. Adware has also been known to download and install malware.
Excessively long PowerShell command detected - (4689)
A PowerShell command with a very long command line argument that may indicate an obfuscated script has been detected. PowerShell is an extensible Windows scripting language present on all versions of Windows. Malware authors use PowerShell in an attempt to evade security software or other monitoring that is not tuned to detect PowerShell based threats.
CVE-2019-0708 detected - (2172)
An attempt to exploit CVE-2019-0708 has been detected. The vulnerability, dubbed BlueKeep, is a heap memory corruption which can be triggered by sending a specially crafted Remote Desktop Protocol (RDP) request. Since this vulnerability can be triggered without authentication and allows remote code execution, it can be used by worms to spread automatically without human interaction.
Process hollowing detected - (885)
Process hollowing is a technique used by some programs to avoid static analysis. In typical usage, a process is started and its obfuscated or encrypted contents are unpacked into memory. The parent then manually sets up the first stages of launching a child process, but before launching it, the memory is cleared and filled in with the memory from the parent instead.
Kovter injection detected - (92)
A process was injected into, most likely by an existing Kovter infection. Kovter is a click fraud Trojan that can also act as an information stealer. Kovter is also file-less malware meaning the malicious DLL is stored inside Windows registry and injected directly into memory using PowerShell. It can detect and report the usage of monitoring software such as wireshark and sandboxes to its C2. It spreads through malicious advertising and spam campaigns.
Gamarue malware detected - (49)
Gamarue is a family of malware that can download files and steal information from an infected system. Worm variants of the Gamarue family may spread by infecting USB drives or portable hard disks that have been plugged into a compromised system.
Installcore adware detected - (44)
Install core is an installer which bundles legitimate applications with offers for additional third-party applications that may be unwanted. The unwanted applications are often adware that display advertising in the form of popups or by injecting into browsers and adding or altering advertisements on webpages. Adware is known to sometimes download and install malware.
Special Search Offer adware - (30)
Special Search Offer adware displays unwanted advertising in the form of popups or by injecting into browsers and altering advertisements on webpages. Adware has also been known to download and install malware.
IcedID malware detected - (23)
IcedID is a banking Trojan. It uses both web browser injection and browser redirection to steal banking and/or other financial credentials and data. The features and sophistication of IcedID demonstrate the malware author's knowledge and technical skill for this kind of fraud, and suggest the authors have previous experience creating banking Trojans. IcedID has been observed being installed by Emotet or Ursnif. Systems infected with IcedID should also be scanned for additional
malware infections.
Corebot malware detected - (12)
Corebot is a Trojan with many capabilities found in other prominent families. It features a plugin system to enable it to load a variety of features from the C&C server at any time. Known plugins include RAT capabilities such as taking desktop screenshots, as well as being able to intercept and modify browser communications and steal data, especially data related to banking.