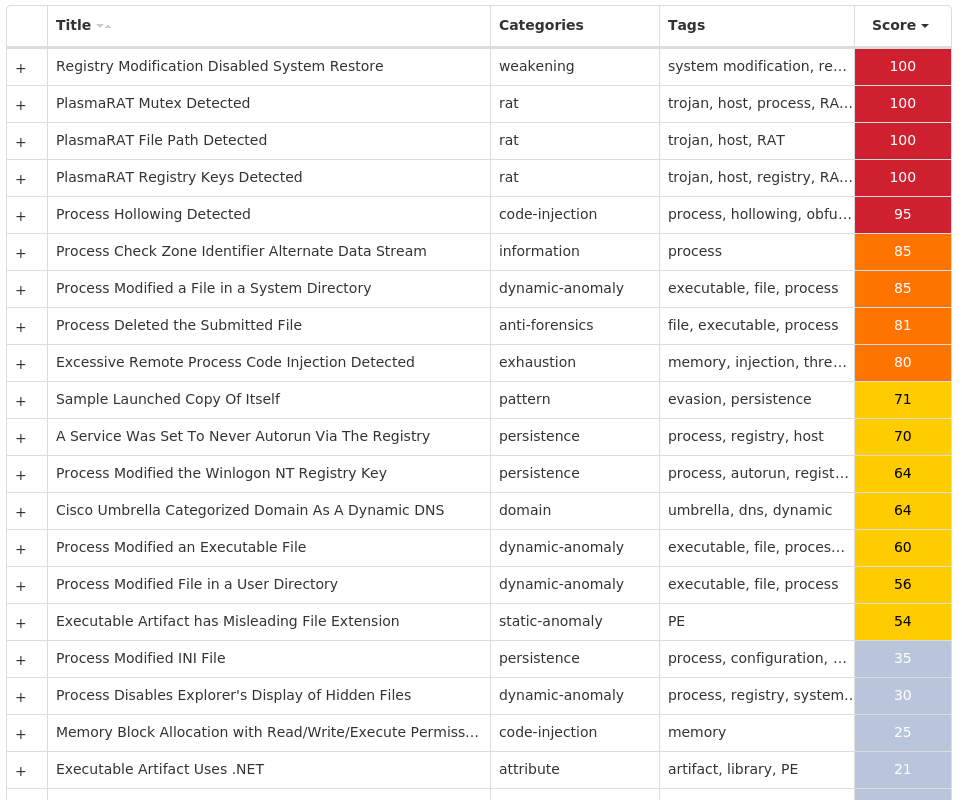
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 5 and May 12. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
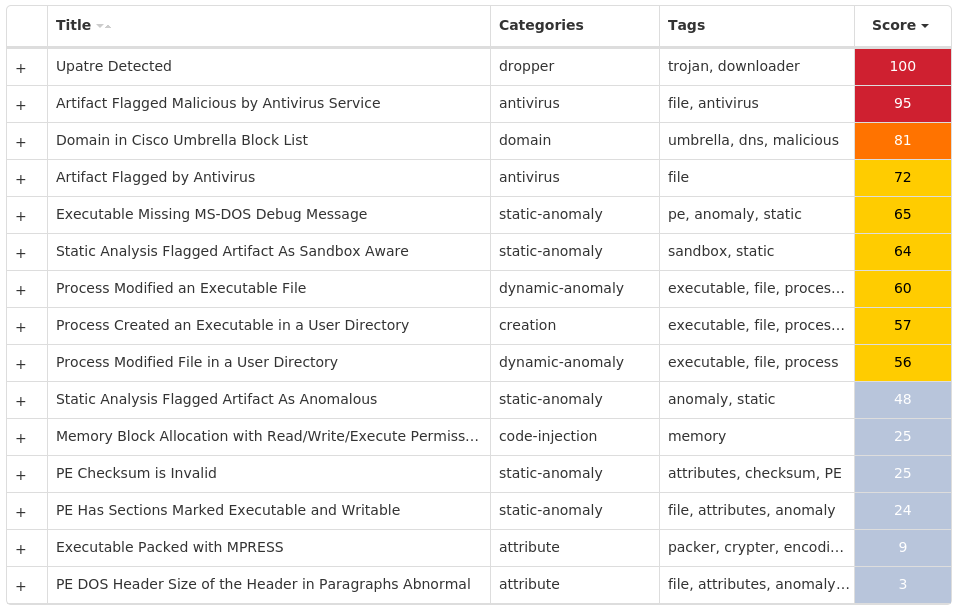
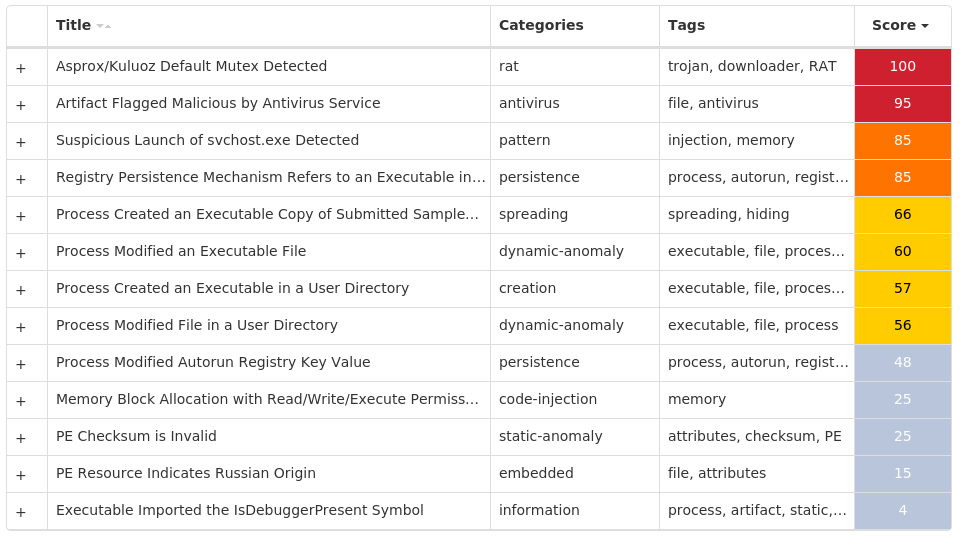
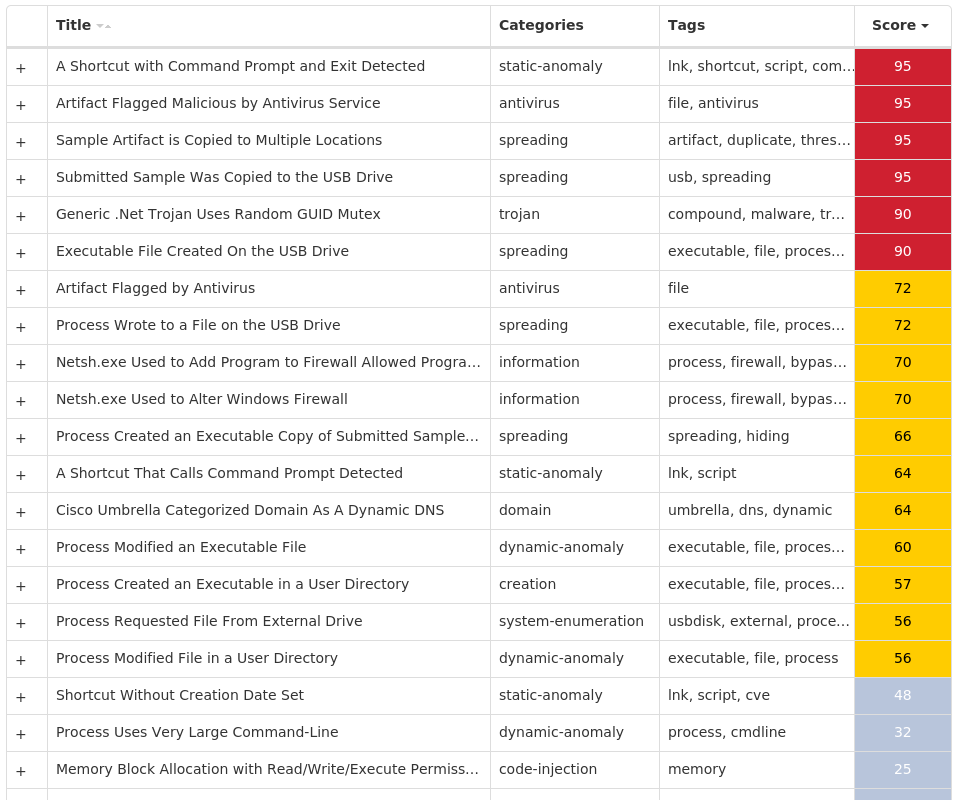
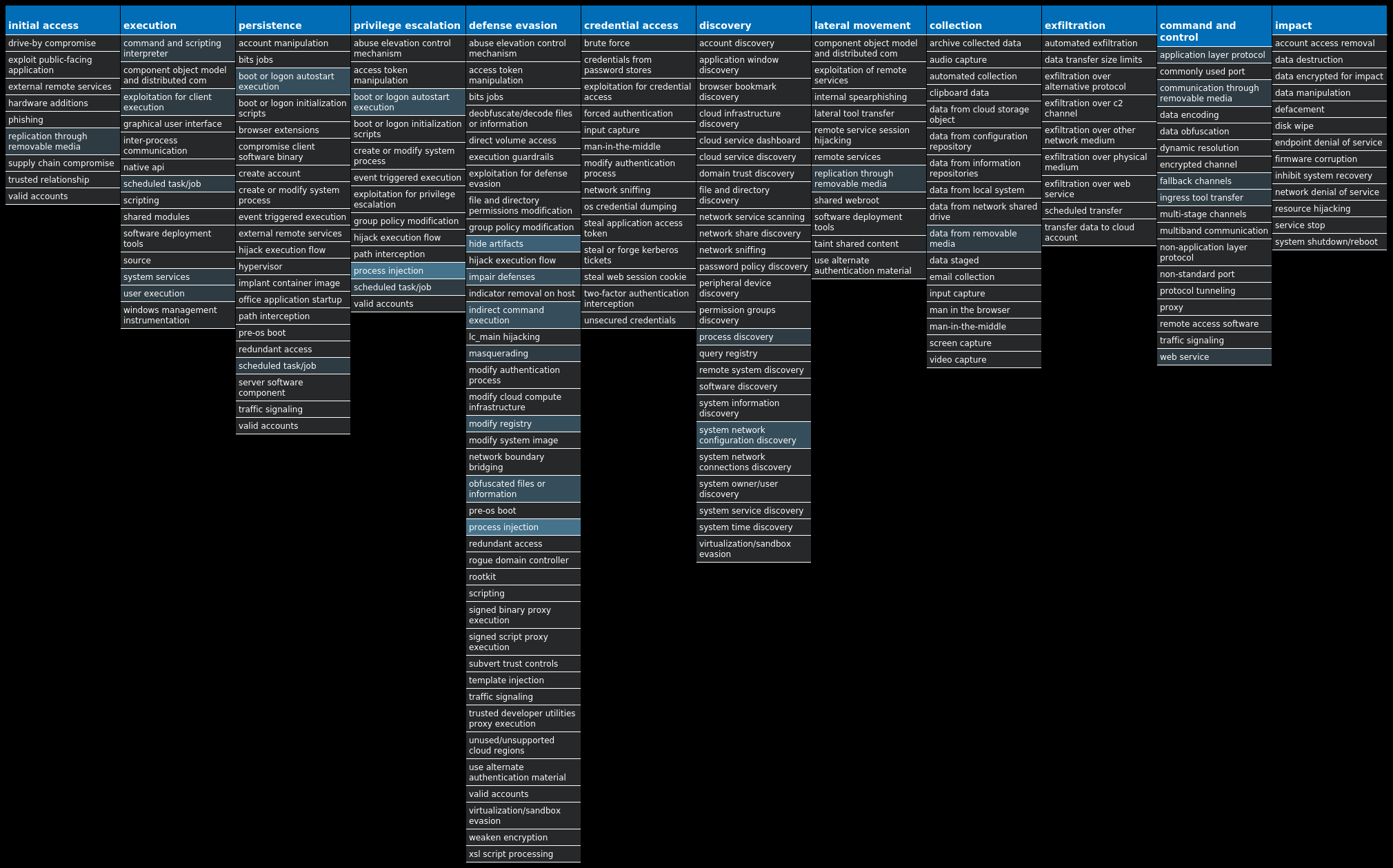
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Downloader.Upatre-10001445-0 Downloader Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware. Win.Dropper.Kuluoz-10001444-0 Dropper Kuluoz, sometimes known as "Asprox," is a modular remote access trojan that is also known to download and execute follow-on malware, such as fake antivirus software. Kuluoz is often delivered via spam emails pretending to be shipment delivery notifications or flight booking confirmations. Win.Packed.Razy-10001440-0 Packed Razy is oftentimes a generic detection name for a Windows trojan. It collects sensitive information from the infected host and encrypt the data, and send it to a command and control (C2) server. Information collected might include screenshots. The samples modify auto-execute functionality by setting and creating a value in the registry for persistence. Doc.Dropper.Valyria-10001412-0 Dropper Valyria is a malicious Microsoft Word document family that is used to distribute other malware, such as Emotet. Win.Dropper.Glupteba-10001476-0 Dropper Glupteba is a multi-purpose trojan that is known to use the infected machine to mine cryptocurrency and steals sensitive information like usernames and passwords, spreads over the network using exploits like EternalBlue, and leverages a rootkit component to remain hidden. Glupteba has also been observed using the Bitcoin blockchain to store configuration information. Win.Dropper.PlasmaRAT-10000760-0 Dropper PlasmaRAT is a RAT that has many capabilities including mining, denial of service, remote desktop access, and keylogging. PlasmaRAT's sourcecode is freely available online and has been seen used by threat actors such as APT33.
Threat Breakdown Win.Downloader.Upatre-10001445-0 Indicators of Compromise IOCs collected from dynamic analysis of 29 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 29
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 51[.]222[.]30[.]16429
Domain Names contacted by malware. Does not indicate maliciousness Occurrences groupesorepco[.]com29 bulkbacklinks[.]com29
Files and or directories created Occurrences %TEMP%\hummy.exe29
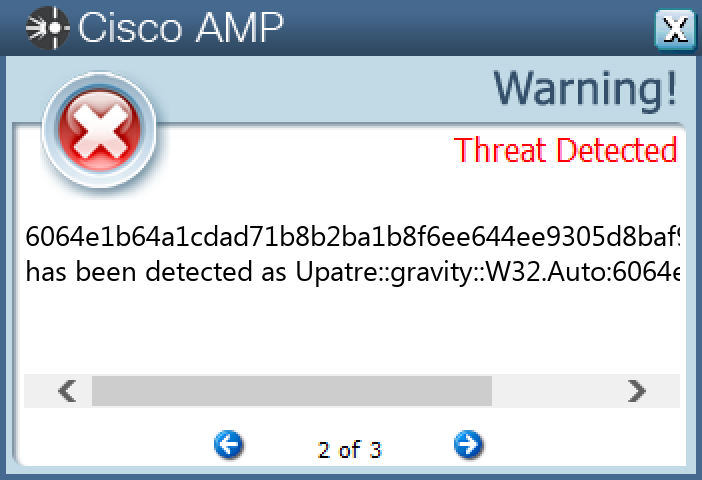
File Hashes 0323edc8d532da1aefe5766303a1e4aebeaab1659add9a74a07139bac4d49e21061783c38fa569ec6943032cd3e89adf46b85058ffce04568bc73de9afb837e40a762357e7fd4205bffb69d21b994d1d7904f2e3036df78a68f001ea275874b90cac5a7b8060ca7d072ef200ebe114e79db226c0c77b23a5bfdad6367ea662860fe6a1a25bc5f8e635ec6858e70a858d8ada70e4c756ce7ead552f9356f1bac110a891e850d4aa2cd19cd91667e4aa71a3f5c695c5768eaca0de9b7447af40fe119b4aada3e4c30184918106a31fdf69f9761311feaf60911835e36ec45be4d8138cff7ae6280470a0c46263b1c66ff095534dd2fdd55c205790601b35344de328f6b3ddad4f5eac964b447a327c65da4ebc78aab3a77ab771b4cec0a831e3d42d92e70ea5454c62b44dd8e103937a7247d8bdc568f781c4b34a6bcc98a05e6d30812a0a04339fb52e41985b348535455af8d3b6b7f0323f26879d61a1eff7fb34bda506acb7ec2bcf103e8ba957b62bd801bb0a7c51d15953088a5ff0e2593435cae9bfee37620eed0623fd3c451b6420bac82066b97392ba4dc1e012e3a2b936444340684422c57a04de89af9d8ce31014ade3aff049f2f909537efe7f65a537b5372bfd492c9541d1ddfcb4fd18aa73d4e2afe10c4c94a61b62b59cb41bbc3b14a24946a12d98d5ed001ff5ae0a1a4503e1a142a0aa013e4bdf164fe215ac4537b602ee160ee2e1e6881c43fc89b4805d67e50cd052aa602beb022e85217d48db71773aa5c9f3adad407f2fb053be71a589ddde373cd4d34a0dddbe8a568a4f73987d7bc3fba50f4b5bfc1d5c04e066b2a61297872c1fe3f5241ae8b867bb537ece66bbcc609d5878b3f39a0c5b9dbbe654fe8844991462ea06f00670be885a5deb3033c8335e05ea29369a24adf6292254ca61a13bfbb4dbf5dcd33aa97d5d69cea5ff1f6d0c9543f94f4a08d474822bbd462f3bd946b87482fb506356485e0ff03ec2782cdc0d47d71fd5921b585578a6727c6f5d8672a66eaaa1749f7c5eb916933bdc0557ab1f18f0779085afce4c9099525e719447b530b72cd173896064e1b64a1cdad71b8b2ba1b8f6ee644ee9305d8baf9735a63c5af65233a579
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
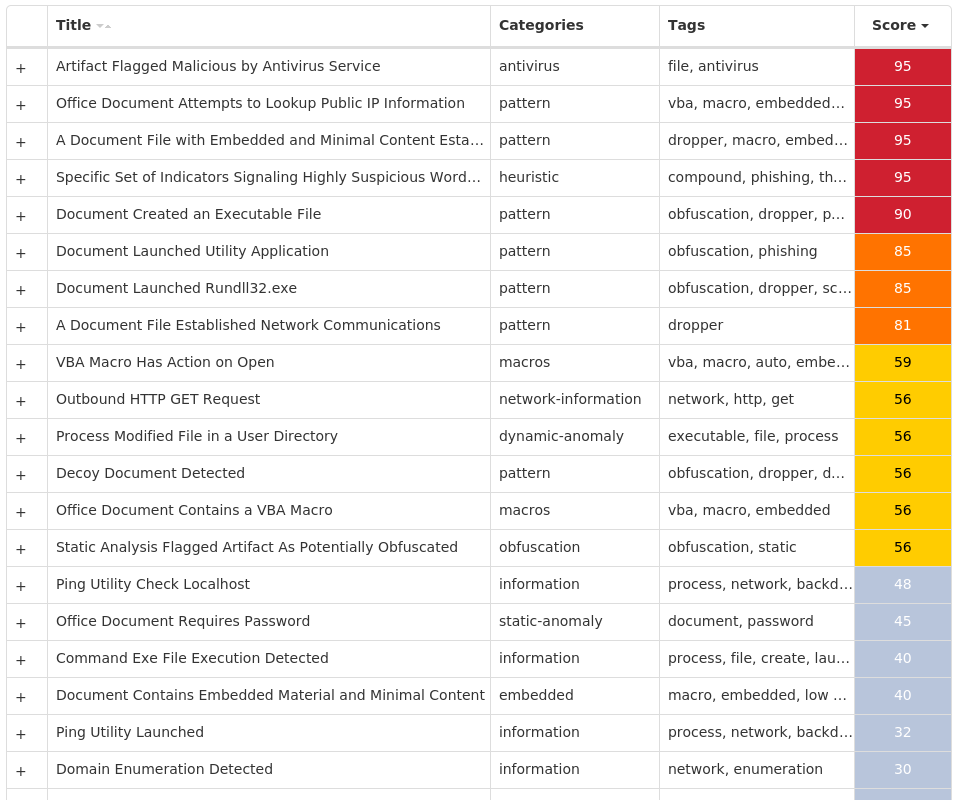
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Kuluoz-10001444-0 Indicators of Compromise IOCs collected from dynamic analysis of 32 samples Registry Keys Occurrences <HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'>23 <HKCU>\SOFTWARE\OLFPSCDU Value Name: gebgrgcs 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: upeqcbfi 2 <HKCU>\SOFTWARE\PNHARWEN Value Name: tkpkvuuv 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ipujklsd 1 <HKCU>\SOFTWARE\AIPUCTSM Value Name: uepvvthp 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: eohpdgar 1 <HKCU>\SOFTWARE\SIJOHJOQ Value Name: qbolerqh 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: jhqqjnsh 1 <HKCU>\SOFTWARE\UORQTLIO Value Name: rhwxoftw 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: dgtkjdtr 1 <HKCU>\SOFTWARE\MUTKAJBX Value Name: tdhgnwmq 1 <HKCU>\SOFTWARE\GCNUFLFR Value Name: tfrsnxbc 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: kkmcetlr 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: kmenlemq 1 <HKCU>\SOFTWARE\BLCQSVUT Value Name: kqkqgnfk 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: mpdsbbhd 1 <HKCU>\SOFTWARE\ECRARMIC Value Name: uqlbdvjl 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: dpmdtfdd 1 <HKCU>\SOFTWARE\KPQLPHTV Value Name: nqikbbnq 1 <HKCU>\SOFTWARE\RJPOTMOR Value Name: cdjoknmb 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ebgndtjf 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: jqhgvjhd 1 <HKCU>\SOFTWARE\IWIJWRJQ Value Name: nfurxpab 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vcdhnulu 1
Mutexes Occurrences aaAdministrator23 abAdministrator23 Global\<random guid>9
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 110[.]170[.]30[.]19514 199[.]59[.]57[.]14214 162[.]13[.]189[.]5212 193[.]46[.]84[.]8411 107[.]170[.]221[.]18711 23[.]227[.]182[.]20710 173[.]199[.]182[.]15210 212[.]129[.]21[.]21010 158[.]255[.]238[.]910
Files and or directories created Occurrences %LOCALAPPDATA%\<random, matching '[a-z]{8}'>.exe23
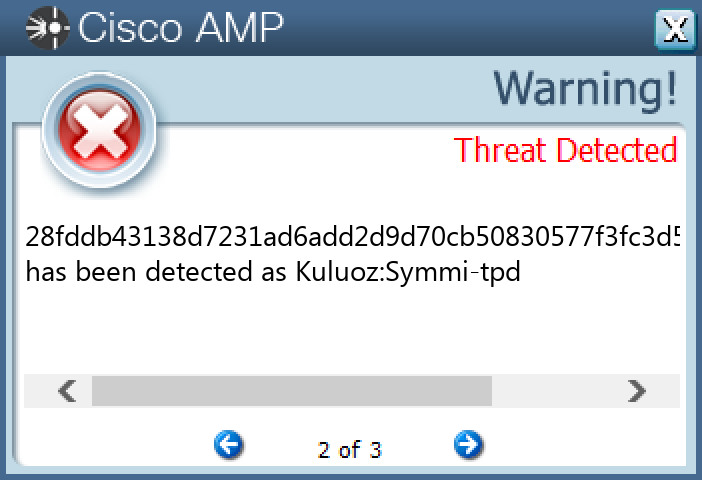
File Hashes 00342c05f0faeb777c292a4263a60cf34083f0703cd986e4d1afa9db05ed97c7034085f1acc8151203897dfa8e0c20c23cfdc7fb04dff1d8de9276c11a0fa35106a89d09af32a664b18cf9a3dc223e84a854f7259565c5542278a16cab9110210d4aff7efefaa88ec14b02ed12ca3deed7e6b273b6fda82d7066ae4cf9c8524218dba1ba835356d4cb36781959de355aec57d7bf50526c275ae75f5294433efe1a75b0eab3722538649b377d3f4f930d4870deb2ea120ec7ac0fafaba03500321c0644456cc0aa070ee81eb08163f46a7a74585857e9d818736e163e36fc6d4a1e3952115d2c916f845d10914bcec73daa539e6ed9a1d404122ccb7315cc0d5322b2f7a50c3abd93ff453f1670aa9f135227e971c2baf11e36f8dc69e84d4e5623154e22b273d45812a4b0f7088db886fa498a4669ee226aac8af08be3ff49b328fddb43138d7231ad6add2d9d70cb50830577f3fc3d5e0488dfa9a16a50b37233b50a69c558582c1caf27021b1733d7b92b38988fcc04078758b7c20ea0b1da3623e5b40872cd973897a401563c885e57f0cf6c4fa9d15efa2057b0e99c9c43388da6758e0411034e5c294709dab82dab9f9985d21326c615eac557087965fe3af803177e7d2463ca755b70baf550de4b7b506df719345e942f558af8f27c6946290e2b7639d68a9e911e8e4be461b189bc741c76d5245ea3d26d8beb0a9536559cc94f2a183c9db488431fc8d166c0e924907e9fc002968efa77ec9aa7679e561668af320f5a6dd2dfa03ee8eade9441ecd9badd88b1a2d3a6846a36eba092568fa2a7d64aa79b2d4f4ee58e3b296a17952de78a860f87a9b91f3098e0e08c5792a7b159c605f75b864d542491be2e6e97aee4c06e3051b0ee3a019b8fc74f5873b9c7431e18d1ab7f0b453240c4cba36ccac6a9628e536eb4d391d849443762205125608aadcdb458db35d865fede56c98722b717a44a2afe5e5a6983187662fac7e247c1362ccf340119f1baa8e4ff6aece558bba7b6ba2995397bff2b1f6f6d8ae4d2731a6ed1edee55880235c7d102900da1cb986db6c76bc0d157f9dc730fdae49c50d5339f8c19ab80c1fce2ce0a5d4d3a33e49bced57e50ea20126d
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Razy-10001440-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKCU>\ENVIRONMENT Value Name: SEE_MASK_NOZONECHECKS 7 <HKU>\S-1-5-21-2580483871-590521980-3826313501-500 Value Name: di 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Client 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\TASKBAND Value Name: FavoritesVersion 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 5d5e3c1b562e3a75dc95740a35744ad0 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: d5a38e9b5f206c41f8851bf04a251d26 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: d5a38e9b5f206c41f8851bf04a251d26 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\TASKBAND Value Name: FavoritesChanges 1 <HKCU>\SOFTWARE\{WEQ2-67R1-YUU3-EEQ2-TY74}1 <HKCU>\SOFTWARE\{WEQ2-67R1-YUU3-EEQ2-TY74} Value Name: US 1 <HKCU>\SOFTWARE\9B4E76249AEEC926B2BF5D22AB66FD6A1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 9b4e76249aeec926b2bf5d22ab66fd6a 1 <HKCU>\SOFTWARE\9B4E76249AEEC926B2BF5D22AB66FD6A Value Name: [kl] 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: c0fe9f26ddd18885f6e909b228e16080 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: c0fe9f26ddd18885f6e909b228e16080 1 <HKCU>\SOFTWARE\85586C1696EEF072F608E599824BECB71 <HKCU>\SOFTWARE\85586C1696EEF072F608E599824BECB7 Value Name: [kl] 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 5d5e3c1b562e3a75dc95740a35744ad0 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ff80315b890d700afbcc28650ff0e71b 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ff80315b890d700afbcc28650ff0e71b 1 <HKCU>\SOFTWARE\1FF2F8A6E8685E09EE6FCA84830B84DE1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 1ff2f8a6e8685e09ee6fca84830b84de 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 1ff2f8a6e8685e09ee6fca84830b84de 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: AhnLab Update 1
Mutexes Occurrences <32 random hex characters>7 RV_MUTEX5 {WEQ2-67R1-YUU3-EEQ2-TY74}1 5d5e3c1b562e3a75dc95740a35744ad012341
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 172[.]67[.]34[.]1701
Domain Names contacted by malware. Does not indicate maliciousness Occurrences expres123123[.]zapto[.]org2 kitty1983[.]ddns[.]net2 pastebin[.]com1 dz1993[.]ddns[.]net1 davidaf[.]ddns[.]net1 toune16[.]ddns[.]net1 honma123[.]codns[.]com1 jeffly12[.]hopto[.]org1 alwerfalli[.]ddns[.]net1 cyw0923[.]codns[.]com1 raeed99[.]ddns[.]net1 at-44[.]myq-see[.]com1 rootjuba1[.]ddns[.]net1
Files and or directories created Occurrences %TEMP%\<random, matching '[a-z]{4,9}'>.exe6 \$Recycle.Bin.exe4 %ProgramData%\RevengeRAT4 %TEMP%\RES<random, matching '[A-F0-9]{3,4}'>.tmp4 %TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp4 %TEMP%\<random, matching '[a-z0-9]{8}'>.out4 %TEMP%\<random, matching '[a-z0-9]{8}'>.cmdline4 \Documents and Settings.exe3 \MSOCache.exe3 \PerfLogs.exe3 %ProgramFiles%.exe3 \$Recycle.Bin3 %ProgramFiles%3 \Documents and Settings3 \PerfLogs3 \MSOCache3 %APPDATA%\Client.exe3 E:\RevengeRAT3 \RevengeRAT3 \RevengeRAT\Client.exe2 \Recovery.exe2 \RevengeRAT\USBPower.exe2 %TEMP%\melt.txt1 %APPDATA%\Microsoft\svchost.exe1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Client.exe1
*See JSON for more IOCs
File Hashes 05a1d8381fd31606265a05d9f4c158c69f574e417201969e67663e73f6f353210603e5cb577f35a2a5f144724434cdc41862673109967eb9927dc010465b92ee08a5c4cfb2b4cc1ee2a780c7c1309281709817fec2b6cf42a6392e648c83b84009a7facf4e659f04f37d6e00c32e6d670365fb00521c8d35e7ddf4cbca1aae1e0e05d6bbb0b482806dee87457dbdcbc934cea343999829a3c7827e8e635d3c331fecf366798b47c1b2bf57416201be85561ee853ebd4e604bc9f9abaea36b1ff2317b833127e989c808f8092e7b277734e9ebbccacecae7f185e6c62adeeb4b92d2bc5b6226d288b9abec0cf2443fd239df63c2eb1bebca28ae2e7cbfe03cb4835b7995b52e41c6a5eabbc6cb7a5f962586466ca4ceb2372ea608daccaead43f3a9a2051c0e02a724d3c33042fb683a68032ec397a6fcb29f7eef4e50d5178db42cb8ee5ee0724540cc2aa48bafa2e205f2449e5101c90f2a07f3d207a11564447c82197b05cd8e01804bc0c934754923e84de7a9485b53c885f662f2fab67dd532199cfe386343914f1f4be093ae6a5eb0755779c967e797443240891c711465fbaec0c6a28a21433747c6b4e2d3f8d2b484bf5bc02e664682906c95b528ad762780b161d3ba2c2839caac945bac274f62d8f564a64d620f3cdc8a925e69ddd6947b2474bc0e3305af7c6f64f418d4a8d9395cc25f9843532d939c538093b827260c6c20676bf6d9a15d58987b528ce716dc51180545966f7c586db15022ea37b930e43c39e416c81ec3acf2f22964e85d51c5c9c9a1ab95e5ee21f123820447ec938b09a5d5c0f6dbc1a0ca75cf669568d5df15118cfea89e9db0cc0eb18268c8b3a3e5a85939f3af1359083876303c483ad2a98d287f1c13187b794006bff95eef31a2af620c79e74f4b6743eb8176e5e50187ab26cd21e6b24e5a5b63357961b88ffa399625ff3cfe6e4161b8dc6b3fd5071ecdaab86889cd42e3ebb61149ff847764a3a4a2e4f3fba78b87fc6e8a722c3fee5093e9104292db204853314a57667097aa63516b88121a6e5249f7c953003916ced9341406b916b02e07d92a6d757c407570fc1b57ab1e18e77c48ae88ebc965a1a75a610b97f9167f81d4d
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Doc.Dropper.Valyria-10001412-0 Indicators of Compromise IOCs collected from dynamic analysis of 14 samples Mutexes Occurrences Local\10MU_ACB10_S-1-5-5-0-6786314 Local\10MU_ACBPIDS_S-1-5-5-0-6786314 Local\WinSpl64To32Mutex_10960_0_300014 Local\MU_IMDS10_S-1-5-5-0-6786314
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]237[.]62[.]2114 64[.]185[.]227[.]1554 173[.]231[.]16[.]774
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]ipify[.]org12 templogio[.]com6 johommeract[.]ru5 amesibiquand[.]ru3
Files and or directories created Occurrences %TEMP%\if.bin14 %TEMP%\if.bin:Zone.Identifier14 %TEMP%\zoro.kl14 %TEMP%\zoro.kl:Zone.Identifier14 %APPDATA%\Microsoft\Templates\~WRD0000.tmp\:Zone.Identifier:$DATA14 %APPDATA%\microsoft\templates\~$zoro.doc14 %APPDATA%\microsoft\templates\~WRD0000.tmp14
File Hashes 04ece234e8e543a378b27b440c3bfd4b8b5dffdc65f8b5048d625cda9fd6aa251330a9b1b83a5956ebb74c44a84673a35c1e84a078911e6de6b9a85f8fd808231c9d20896f1c44c2dbbb6bb05979c1ec374d097b9af4d881c0c1949ddc1d821f59a9d01ae23d1b0632f44d5720265c27a14d24c92d413edf39153d998e6269ec5adb541c551814e964482b45644033ea1c4ad4830d0384047a6906bbb86ac2435f4e57986604f7caf6831a25d3b53542d2665dedc0fedb8fc59dd72a914b096387ac85417295fde5f181265ebfa8028df41abfa17c7d8f5ab4794dab37af85758d0486539dacdf2201a32ac6090ec628139185c19099a010a3027bf6b6611fcda2903ebc67c3549f59ecf6718444f6826030fa29f3701460b9709edbd9aa675bae4b72f4a31cfee6f08af42333d5bfb1a2500249e8446a2e9fe4fa7e55ec0821b062dd8f8c46cb010cf562145e9a2836f5625f41af329e87ca2bbdc2fd05435dbcdcf1ec9bf276c3e6ea441e64ff91fe836857fc49c0c97b672adc0a64aa6873c1c2fd46ce19afa66360c6db20edba84c460b254dc4676949bf38bdd41cdd577cf4adca8773145cf0a1d4ba32d555643442e14e9181ae8450bfb79ab86144914
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
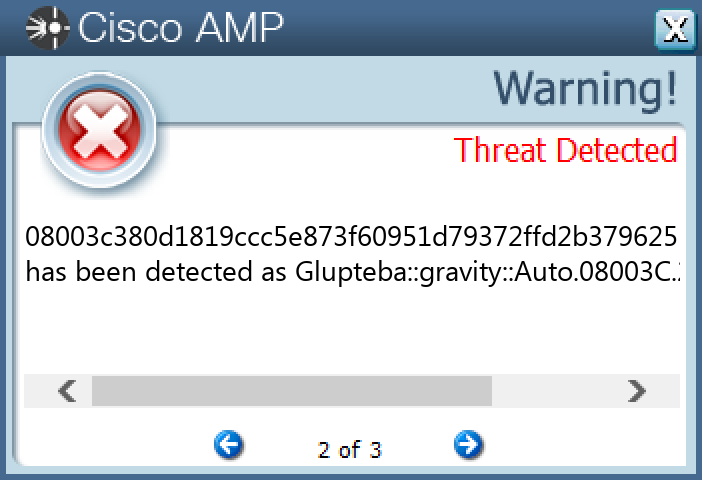
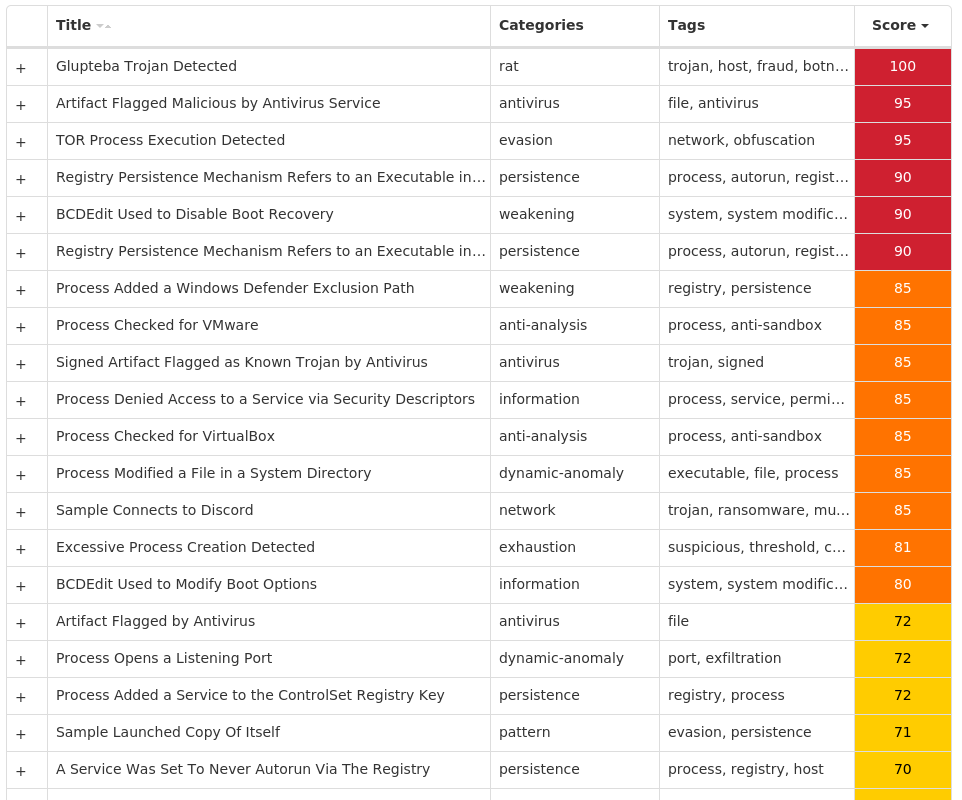
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Glupteba-10001476-0 Indicators of Compromise IOCs collected from dynamic analysis of 24 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\A1890984 Value Name: PatchTime 24 <HKCU>\SOFTWARE\MICROSOFT\A1890984 Value Name: PGDSE 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: WOW64 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: ObjectName 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: Type 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: Start 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ErrorControl 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ImagePath 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: DisplayName 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: WOW64 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ObjectName 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: Type 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: Start 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: ErrorControl 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: ImagePath 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: DisplayName 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: WOW64 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: ObjectName 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSERVICE Value Name: Type 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSERVICE Value Name: Start 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSERVICE Value Name: ErrorControl 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSERVICE Value Name: ImagePath 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSERVICE Value Name: DisplayName 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSERVICE Value Name: WOW64 24 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSERVICE Value Name: ObjectName 24
Mutexes Occurrences Global\SetupLog24 Global\WdsSetupLogInit24 Global\h48yorbq6rm87zot24 WininetConnectionMutex24 Global\qtxp9g8w24 Global\xmrigMUTEX313376
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 204[.]79[.]197[.]21924 20[.]60[.]148[.]19624 20[.]209[.]34[.]3624 185[.]82[.]216[.]48/3112 172[.]67[.]168[.]1129 104[.]21[.]54[.]1038 162[.]159[.]135[.]2337 162[.]159[.]133[.]2336 162[.]159[.]130[.]2335 81[.]3[.]27[.]445 185[.]82[.]216[.]645 162[.]159[.]129[.]2334 172[.]253[.]120[.]1274 142[.]250[.]111[.]1274 142[.]250[.]15[.]1273 74[.]125[.]128[.]1273 108[.]177[.]102[.]1273 51[.]159[.]136[.]1113 188[.]138[.]33[.]1492 193[.]0[.]213[.]422 94[.]100[.]6[.]272 162[.]159[.]134[.]2332 192[.]99[.]43[.]1712 162[.]55[.]91[.]192 157[.]90[.]183[.]1032
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences msdl[.]microsoft[.]com24 vsblobprodscussu5shard35[.]blob[.]core[.]windows[.]net24 vsblobprodscussu5shard60[.]blob[.]core[.]windows[.]net24 cdn[.]discordapp[.]com24 twopixis[.]com17 stun[.]ipfire[.]org5 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]mastiakele[.]icu5 stun[.]l[.]google[.]com4 stun3[.]l[.]google[.]com4 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]zaoshanghaoz[.]net4 stun[.]stunprotocol[.]org3 stun1[.]l[.]google[.]com3 stun2[.]l[.]google[.]com3 stun4[.]l[.]google[.]com3 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]mastiakele[.]xyz3 stun[.]sipgate[.]net2 server2[.]mastiakele[.]xyz2 server13[.]mastiakele[.]icu2 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]cdneurops[.]shop2 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]zaoshanghao[.]su2 server4[.]cdneurops[.]pics1 server15[.]zaoshanghaoz[.]net1 server13[.]xn--j1ahhq[.]xn--p1ai1 server14[.]zaoshanghaoz[.]net1 server2[.]zaoshang[.]moscow1
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\rss\csrss.exe24 %TEMP%\csrss\dsefix.exe24 %TEMP%\csrss\patch.exe24 %System32%\drivers\Winmon.sys24 %System32%\drivers\WinmonFS.sys24 %System32%\drivers\WinmonProcessMonitor.sys24 %TEMP%\Symbols24 %TEMP%\Symbols\ntkrnlmp.pdb24 %TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE0224 %TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE02\download.error24 %TEMP%\Symbols\pingme.txt24 %TEMP%\Symbols\winload_prod.pdb24 %TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E36124 %TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E361\download.error24 %TEMP%\dbghelp.dll24 %TEMP%\ntkrnlmp.exe24 %TEMP%\osloader.exe24 %TEMP%\symsrv.dll24 %TEMP%\csrss\DBG0.tmp24 %System32%\Tasks\csrss24 %TEMP%\csrss\injector24 %TEMP%\csrss\injector\NtQuerySystemInformationHook.dll24 %TEMP%\csrss\injector\injector.exe24 %TEMP%\csrss\tor\Tor\cached-certs.tmp24 %TEMP%\csrss\tor\Tor\cached-microdesc-consensus.tmp24
*See JSON for more IOCs
File Hashes 071b33b943aac7e83b9534293b6f1972222a5afdcb999592f9e790b5ba57f52108003c380d1819ccc5e873f60951d79372ffd2b3796251e988dafae9c70427a32437108d3504ad5ceeb7d274cad347762bf30bb5c17c4a8fa1f4222819443d1c28876d2e47d69866f632c84b6b636d778a2e7b1713953400743d166bf139b57056d685cb54f89d8d9db25793565e9381d290836d202fe0bff795c1671592306b5bac4d0210a77cd7d329b5a3755ffff5bc99eb64c2dcd9c7d07768fc06a22bf05f63d5bb5153ce469c558a3ab7d4400364538dcb9a9778373beb8a4cfa479dd574f2ebd1054d1da087fbbfa3e9bf179b596b7b6054a12a55266e06deea5f2d44786d44033834713cfccdc5b64ea4b0d6994cee31c39656a517eba77379cb80ea81b636167f8d4b1b3f53b7de2cc2ba3452dd292cfe2848934e31aca62a389d258506dce2e894bf764b5f3a3f1e31a5417cec38b9d341ad95f3fba31c767741959087940ad07100e45ed7bb0cbc65d4f95ce396302a73c2464b39b9781e937ce0a7b70a33159339131b1988befefefc61b43234769fa3016e54bc88dc6c4597bcb95d39e3a37f70aa9f4a755f919ae58692b575811d4a66859dc15f49d6f39cc5c2905fa662b31dc9409849b05a79a183330102a0de333db6b22c7e581bc385f6c9fda7212f9772ec3f2a48d4221de27d7aed46c8f2feaf31c526212027cb2b0fcd0220e3d48cd61ed5c802f3808c860b2d6e518ef0114c9a32ea9418cb6e0aeccf33241ede6bb57890ad95293b9b04e183156d1d1bd44f6409007a74b461c25edcb3ff440482062b597f384763466e432e7548753419dbd9099f2b2c87894899dcfffa036aa6b63672055b26d5c318ebeae94ec1870cf33b8928a7e5f72da649eed1582389bfbba92eaf222a033f525f073362c6bb68b3973ad5ddfc31c3b4d4f11f94d98dbd6b48af597e3d6461dfb2d9cd1e4bc565f9e726a7350e2244ba83f427bca7295f908f9c03656decabaa0c0e383a3e0adfca81b800ed2fb1265532fd726415da878f03c5faa72b3527b0d519b59adc86ff32a5c0685bde75fe55e5
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
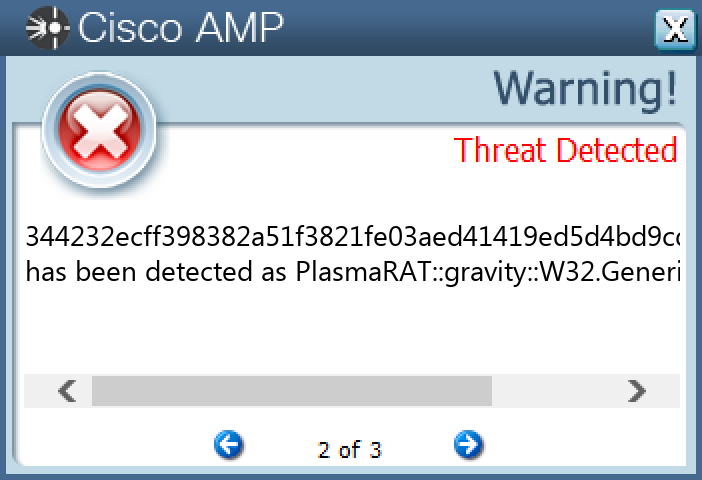
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.PlasmaRAT-10000760-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SYSTEMRESTORE Value Name: DisableSR 15 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED Value Name: ShowSuperHidden 15 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS SCRIPT HOST\SETTINGS Value Name: REG_DWORD 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SCHEDULE Value Name: Start 15 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS15 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\MICROSOFT15 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\MICROSOFT\SYSINTERNALS15 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: shell 15 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\MICROSOFT\SYSINTERNALS Value Name: 9481 15 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\MICROSOFT\SYSINTERNALS Value Name: PROCID 15
Mutexes Occurrences 491924515 8372918472648115
Domain Names contacted by malware. Does not indicate maliciousness Occurrences klobert[.]no-ip[.]biz15
Files and or directories created Occurrences %APPDATA%\msconfig.ini15 %SystemRoot%\SysWOW64\Windows Server15 %SystemRoot%\SysWOW64\Windows Server\wserver.exe15
File Hashes 07acf6655f3bd9f7efb8fb9673abf14a91d8e53c9c8b3d1712b730f79301b4dd10a24172f7877aa5174373a5a66f03d9e8239212ce0a4069b9f9f7a8fb8d869b344232ecff398382a51f3821fe03aed41419ed5d4bd9cdf1e2538c6504971dd545109c4b615ac61874e8559bc29c1e7aa4763963349870e3167a45c1e5e2b8d55901a1c2ee44b552a1de4ace0c80f12fc599b960bef0376b539322dcf3aa3d51734d82c665505125a70f3d0fa5efb17a0d83bdbe41e4f65fb0863806102672938c6b4b0dee6804fc5099abeb62c65e1ebcb44d44dacaaab862534b4da2628495a44d872660a3f839106f90c931aafd42471aded2897f1001fd43bac172829ae3a86ff8947d470e364a74a4472ba36d7d012ca8cd160114ec49338dbcfe8b6b5da8fc38426ef5e166448dfa69708bd765e684f2c2458d15630b8be8d2ee87e251b011b70a43700abfe0ec72edac2223216485aba02192887b738443abd96a7fc5c27c8c22462a0b8de5b80d3ca846ee400ae9f8e55da94b3595892358f88daf66c3ef3d5a345574dbab0f1535f4617b96e95a330f647788d3cb56c83302f92be4ea7485c628bce7f9b446ea559c3744cc7484aa2675f38298ea06beef15bc679deaf2c2366fbdc1ab0ba09c9358abf3969167e6fe9f9ba360654bdf7af3a26631
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK