Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 19 and May 26. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
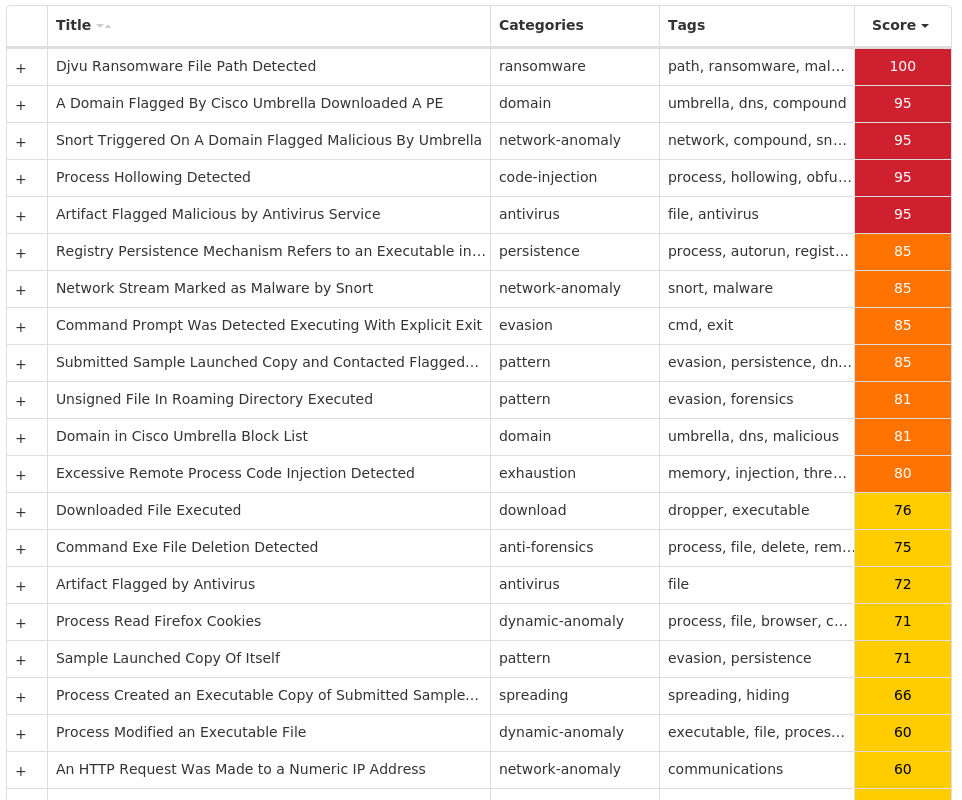
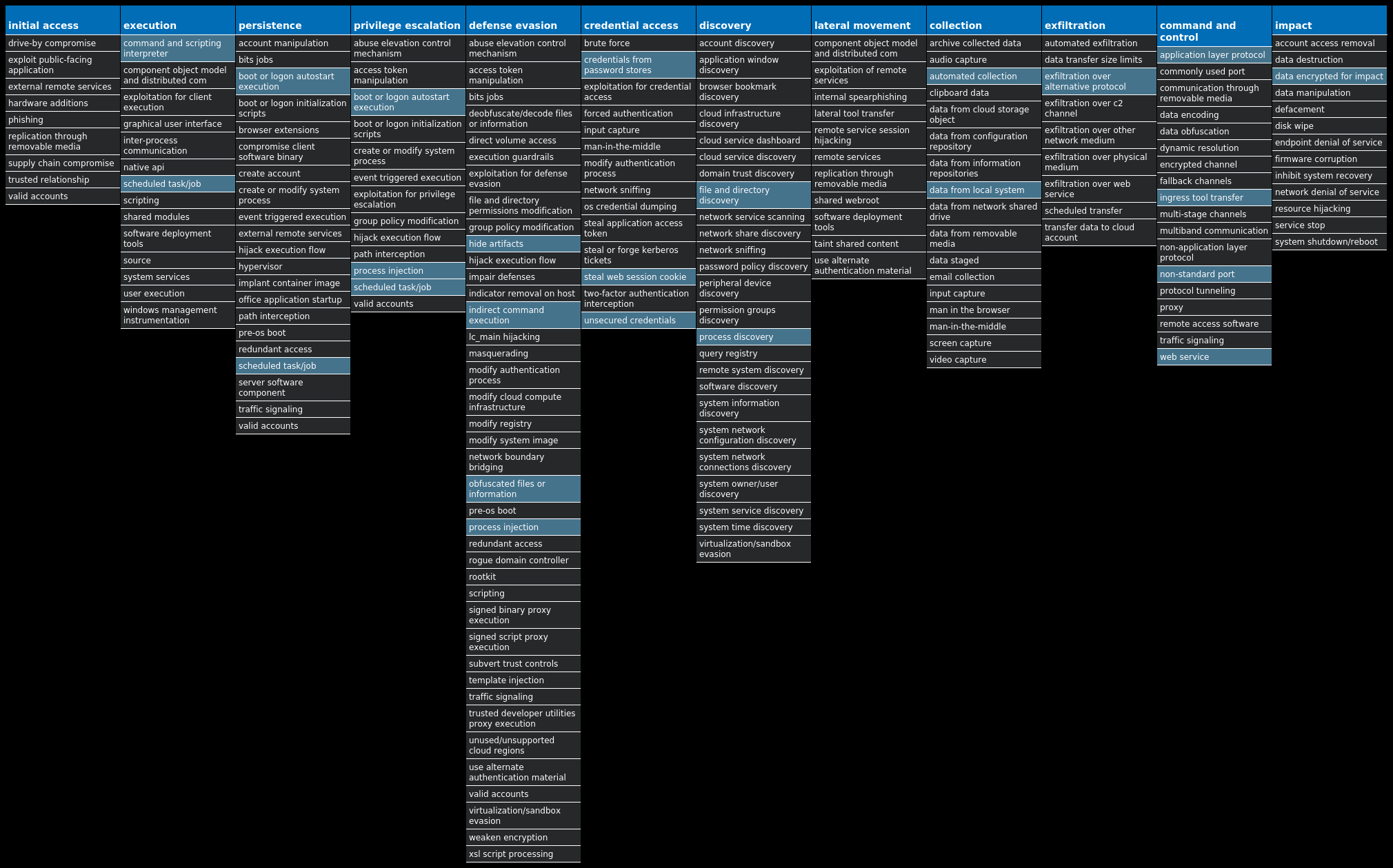
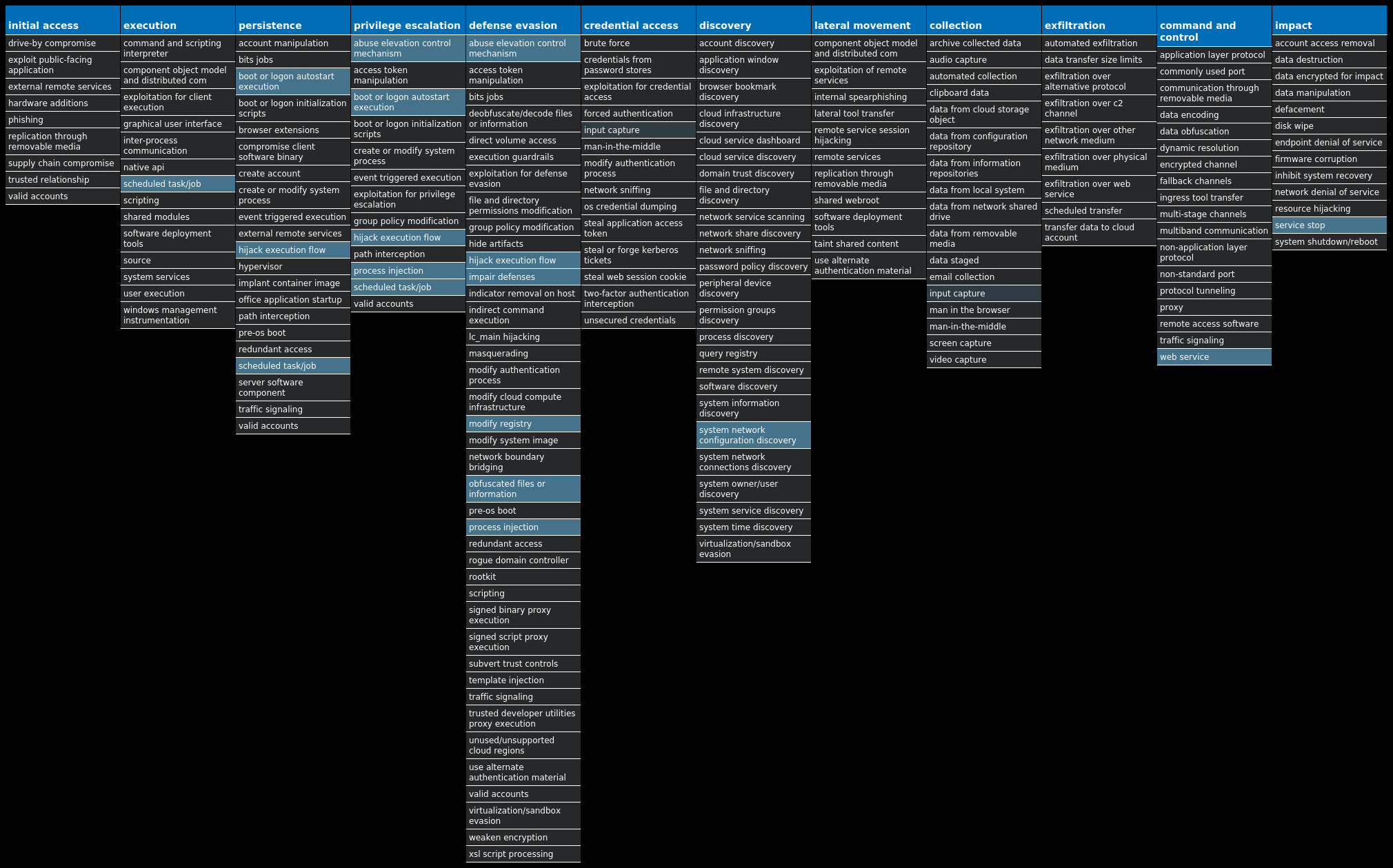
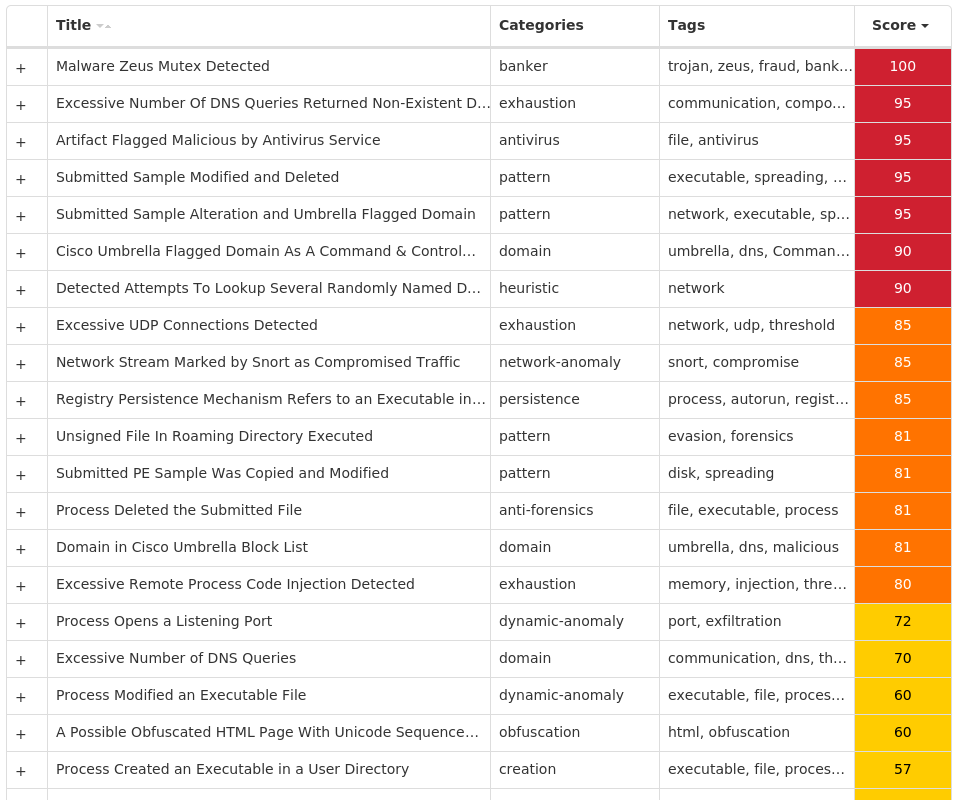
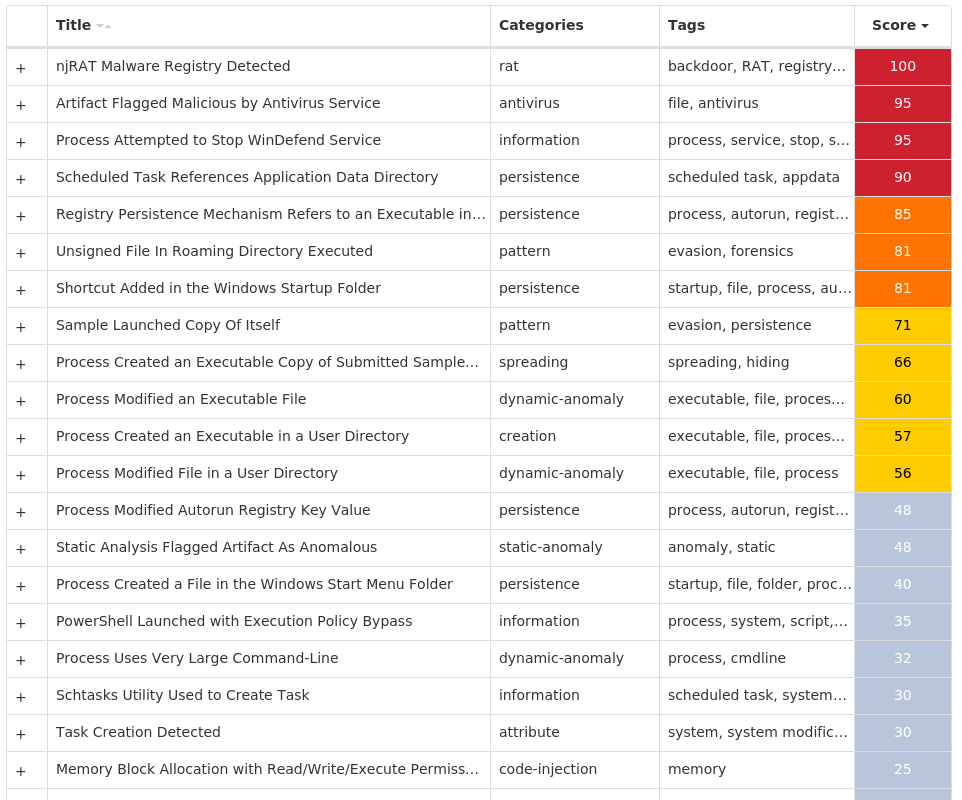
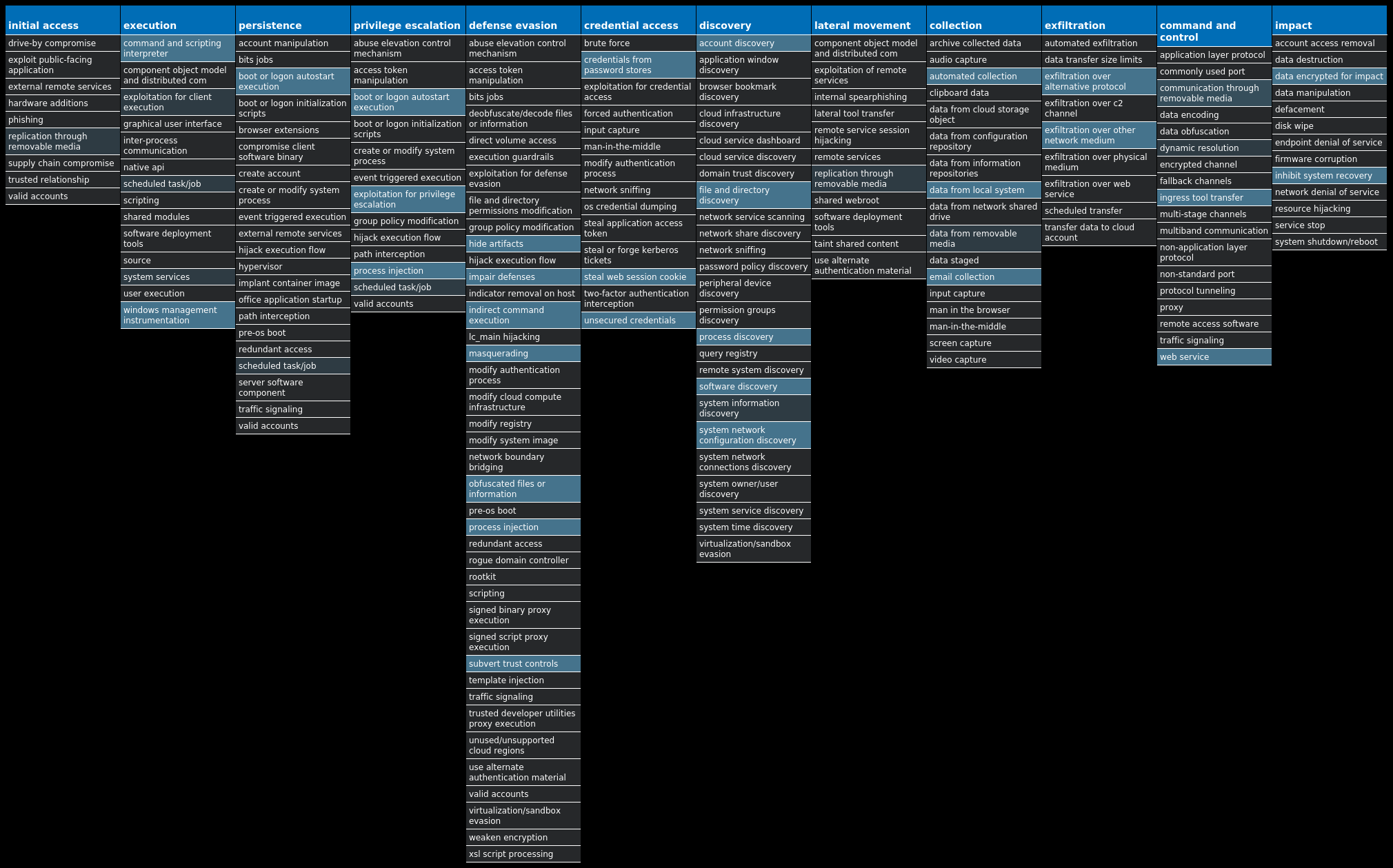
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
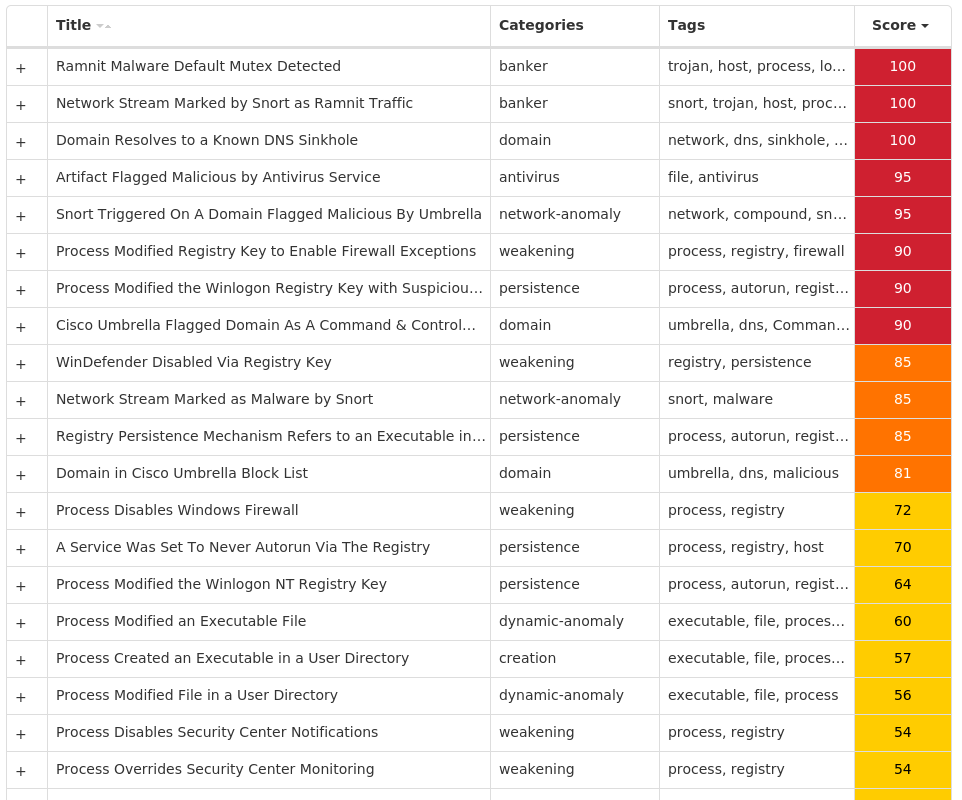
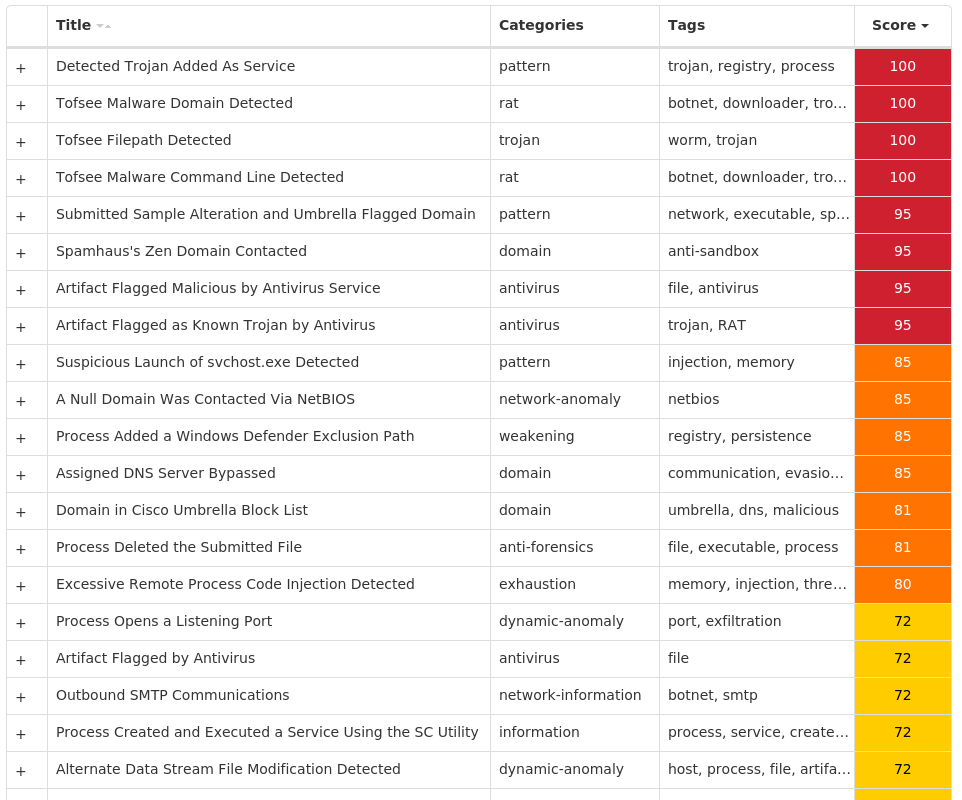
Threat Name Type Description Win.Ransomware.Djvu-10002408-1 Ransomware The Djvu ransomware encrypts victim's files with Salsa20 and is known for changing its payloads, ransom notes and the file extensions appended to encrypted files. It spreads via cracked or faked applications or updates, keygens or activators. The main payload uses a wide variety of anti-debugging and anti-emulation techniques, which includes checking the location of the system via the keyboard layout or websites. Win.Virus.Ramnit-10002385-0 Virus Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It also steals browser cookies and attempts to hide from popular anti-virus software. Win.Trojan.Qakbot-10002083-1 Trojan Qakbot, aka Qbot, has been around since at least 2008. Qbot primarily targets sensitive information like banking credentials but can also steal FTP credentials and spread across a network using SMB. Win.Dropper.Tofsee-10002081-0 Dropper Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and send large volumes of spam messages to infect additional systems and increase the size of the botnet under the operator's control Xls.Malware.Valyria-10002078-0 Malware Valyria is a malicious Microsoft Word document family that is used to distribute other malware, such as Emotet. Win.Dropper.Zeus-10002075-0 Dropper Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing. Win.Packed.njRAT-10002074-1 Packed njRAT, also known as Bladabindi, is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes and remotely turn on the victim's webcam and microphone. The Sparclyheason group originally developed njrAT. Some of the largest attacks using this malware date back to 2014. Win.Ransomware.TeslaCrypt-10002553-0 Ransomware TeslaCrypt is a well-known ransomware family that encrypts a user's files and demands Bitcoin in exchange for a decryptor service. A flaw in the encryption algorithm was discovered that allowed files to be decrypted without paying the ransomware, and eventually, the malware developers released the master key allowing all encrypted files to be recovered easily.
Threat Breakdown Win.Ransomware.Djvu-10002408-1 Indicators of Compromise IOCs collected from dynamic analysis of 19 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION Value Name: SysHelper 19 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: SysHelper 19
Mutexes Occurrences {1D6FC66E-D1F3-422C-8A53-C0BBCF3D900D}19 M5/610HP/STAGE217
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 162[.]0[.]217[.]25419 149[.]154[.]167[.]9918 116[.]202[.]7[.]23917 211[.]40[.]39[.]2515 210[.]182[.]29[.]704 201[.]124[.]33[.]1774 175[.]126[.]109[.]153 211[.]171[.]233[.]1293 211[.]59[.]14[.]902 175[.]119[.]10[.]2312 175[.]120[.]254[.]92 123[.]140[.]161[.]2432 190[.]141[.]35[.]32 2[.]180[.]10[.]72 95[.]158[.]162[.]2002 190[.]219[.]153[.]1012 211[.]119[.]84[.]1121 186[.]182[.]55[.]441 58[.]235[.]189[.]1921 190[.]229[.]19[.]71 49[.]12[.]115[.]1541 187[.]156[.]85[.]1081
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]2ip[.]ua19 zexeq[.]com19 colisumy[.]com19 t[.]me18
Files and or directories created Occurrences I:\5d2860c89d774.jpg19 \SystemID19 \SystemID\PersonalID.txt19 %LOCALAPPDATA%\bowsakkdestx.txt19 %System32%\Tasks\Time Trigger Task19 %LOCALAPPDATA%\3856b5d6-9eb0-496c-b0d1-db92b0f6ed6519 %ProgramData%\freebl3.dll18 %ProgramData%\mozglue.dll18 %ProgramData%\msvcp140.dll18 %ProgramData%\nss3.dll18 %ProgramData%\softokn3.dll18 %ProgramData%\vcruntime140.dll18 %LOCALAPPDATA%\7c34bb01-5d78-49c4-8bbb-73fdc7aa126218 %APPDATA%\Microsoft\Network17 %System32%\Tasks\Azure-Update-Task17 %APPDATA%\Microsoft\Network\mstsca.exe17 %LOCALAPPDATA%\7c34bb01-5d78-49c4-8bbb-73fdc7aa1262\build2.exe17 %LOCALAPPDATA%\7c34bb01-5d78-49c4-8bbb-73fdc7aa1262\build3.exe17 %ProgramData%\291861050018182567102343061 %ProgramData%\984340699417744013017792291 %ProgramData%\069587037100252482383029661 %ProgramData%\510852629415865907756702851 %LOCALAPPDATA%\3856b5d6-9eb0-496c-b0d1-db92b0f6ed65\64d18a6e518bf68b453134e9fe01968e924fc67e3b6b5274668e606d62842b61.exe1 %LOCALAPPDATA%\3856b5d6-9eb0-496c-b0d1-db92b0f6ed65\75022ede411ab60fd9e55d3fa517edfe8488101c916d0b0d91161c8c98da9be8.exe1 %LOCALAPPDATA%\3856b5d6-9eb0-496c-b0d1-db92b0f6ed65\1ed3247b3c2cf5da57d068a93257520d2303b7254fec98110d67194503472a97.exe1
*See JSON for more IOCs
File Hashes 05adccd18a70fd6acb444cb84a27cc488ac86eb449f1a6aea0c8b186cdb39d820c43f3559ee70d362f7cefaf9544dd8c85af4fdbbea04377e223fb7aa5d2a7f81ed3247b3c2cf5da57d068a93257520d2303b7254fec98110d67194503472a97232a8cdd9f6d456804c395d931f9cadb0cf453fb1a191346a8c666e34690cb6c2531aaaf65fa1782e75d54dca67853cb8c1d73e33f2544ec42ba332a87c0979354d5ea5f0619772766771810cc0f3bf03efd5a354cf60ffa3122a9d346fabfd2566cb2138f15aad520cd94cf58dc608a897e804798e0a9139e3b3b1637196f61633e55e6345323a0417415fdb9cf9ac4f4fc2ef7d90a297756e4427cfada76e964d18a6e518bf68b453134e9fe01968e924fc67e3b6b5274668e606d62842b616661877adf148008ca24225159bfba44e0d4e48b2c45602912fe7393f7c3bc3d75022ede411ab60fd9e55d3fa517edfe8488101c916d0b0d91161c8c98da9be87a9688b68fad5a342d6466a61f10df068126418107182f30860d913516e3aa438a0b4cb2e8b68882e37d49cc0dc6d2cd32bea57930015a2ca926475fc5c6f01d8f1d63d1d9b0dbb9886f4fb29074ee97d365c321bc8200525e2711b76dd186f6c5483715a06cb05516e089d79c7e6d54eae258e603c037694479fe701635a2a3c5ded0916b0a6f7c1b259db833a62ac4b0d80c4889aaf8fe1b05867758285e85cc86e630d4c4236ce2f4778b4f14c6984370c5b921d7ca0526bf2a5aac47247eef2614ae93a4b8bf90788e7083129a7ce24ac2452120649251c14700404358b7f343f2cd877c79dcbd80c57427455a1c7c2ea4ad348173753ea849eb4c64c483
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Virus.Ramnit-10002385-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusOverride 25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusDisableNotify 25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallDisableNotify 25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallOverride 25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UpdatesDisableNotify 25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UacDisableNotify 25 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLUA 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: EnableFirewall 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DoNotAllowExceptions 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DisableNotifications 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC Value Name: Start 25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION Value Name: jfghdug_ooetvtgk 25 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: JudCsgdy 25 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Defender 25 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: Userinit 25 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: Userinit 25
Mutexes Occurrences {7930D12C-1D38-EB63-89CF-4C8161B79ED4}25 {79345B6A-421F-2958-EA08-07396ADB9E27}25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 193[.]166[.]255[.]17125 195[.]201[.]179[.]20725 35[.]205[.]61[.]6725 63[.]251[.]106[.]2525 63[.]251[.]235[.]7625 142[.]251[.]35[.]17425 162[.]249[.]65[.]22125
Domain Names contacted by malware. Does not indicate maliciousness Occurrences google[.]com25 ygqqaluei[.]com25 atw82ye63ymdp[.]com25 mdofetubarhorbvauf[.]com25 warylmiwgo[.]com25 caosusubld[.]com25 bekvfkxfh[.]com25 xomeommdilsq[.]com25 wwyreaohjbdyrajxif[.]com25 grbjgfprk[.]com25 xxsmtenwak[.]com25 ydchosmhwljjrq[.]com25
Files and or directories created Occurrences %LOCALAPPDATA%\bolpidti25 %LOCALAPPDATA%\bolpidti\judcsgdy.exe25 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\judcsgdy.exe25 \TEMP\K9eEf4fVf25
File Hashes 069becc422d6f6f1a739f36c19977e86f973de8ac71d43707f821509eeb7e3ab0737a484e81ccea1561a2d09482722f4b1b78020b471cc9285762f297a19a9e908f041ec2fafe6d1b6d4a4df0fd492a490a815bef4c45407c28f01a53eb2f7e9112d9844d869a67cc760eb9619a8f96648abe63dd788841b2189708a4ab33e7919888aed71f14a4b18a67e9b8520a79ce32f9a830a887bea6a8e065c90e483d81e08f5c1a773ee61cf068aa8b5b1962f60c974797f2bbbf0af783834278a57601e43f958047862b254dd56ef12ad553dd1b1b479c66725ff682d17333918027224975482f70ca48e97a8ae892db449c45d959580cf1799cce910eb62e1d5dc482f2e8b9e8e1257ab1d1f6242b2ee21088c03d9b9160d9b6a3c7e6ed045e787103120f89d41fba5cfbe8b5e1e9afb4022cfec268620cc3f5bae0f47bcb368d92e3424188e777af669655e6710ba4954fb973110bca6d0c69aa40ed97e1f64f5d33441e7896f39a452d1391c2391e71aecf9bb5b135871887f35c8566f96c571d63688dd56fd61ff5ecf322ada31deec7c26d22ea4e3a634d4a06845e65962182f4023b5e53d127c9a9d1b268e62a988c64010ac96b0ca509c345fa379e082ac385370afb0a0c823ade197b86217534fda5969ef7dd45aa9f48128a31e401cc356556ee8a712446234cf175b2b96280ab6fd4f3b3f8dc76930c3b3d9ec31b68ca373045fc3593bb96604879c80f5b3222f5723815b52240fdd6a7e6c1c58ec1596797514dff7a8b29b0bea85875a39715ee091fbeaa31fdad4428a4f6863a9b8c48257c33afc6f826716bbe89628006659a25006f4276a80c2284965a70abad3b483eb00995d90f5e09ee93c2dbaa365f9a3cd5ea02ab32c35e26e5c8bc5af7f6886cc81d40db039da90b44b476b79e2da8ea0d87580130fe52f93f12c100090af8ece6f1fd15062ed6f52d02be64f58979065c28e8b135244b7cba144e37f42469d4dfffc0a7b70f370f7d1a5802415df422813f7ecbaba01e9f0c96270b08a579e1559f93288f34005b9eff555fa227d4c0188a0bd378cbba392fae9ab0b0f1b9fc031cd7bcccfb61552939bc5a445acc5b23d3b3aa3932ac10b249c479a9ea3
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
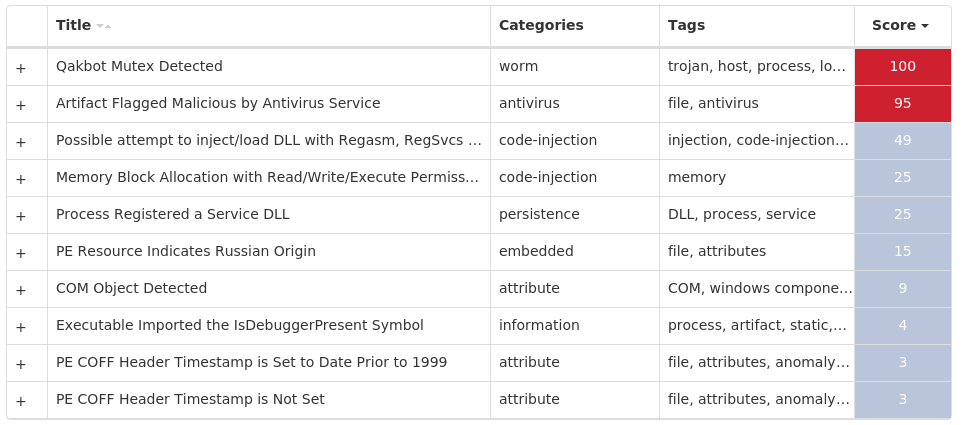
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Qakbot-10002083-1 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK25 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: bd63ad6b 25 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: bf228d17 25 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 79eea72 25 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 7a96a5f8 25 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: f7b512d3 25 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 88fc7d25 25 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: c22ac29d 25 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK Value Name: 5dfca0e 25
Mutexes Occurrences Global\{06253ADC-953E-436E-8695-87FADA31FDFB}25 {06253ADC-953E-436E-8695-87FADA31FDFB}25 {357206BB-1CE6-4313-A3FA-D21258CBCDE6}25
Files and or directories created Occurrences %APPDATA%\Microsoft\Xtuou25
File Hashes 003803cfea14ea1ab8c50539f44899c47c3962b255e4fa860f8bf513f9fcd14f01462998ce5cb3fc03173775cba990c84af3191917232a907a081a002ff14161095c224641480b341cd291e9ab1835ff1c322a60aa2f3f01cc0cc63e057a965d1589c63722c29e201f1af10147c65f50b32b51b65af22162943e80513ae240182342220f71c1da2099259d088baeb86e26629021cc7181a62ef1a115e62f4ae92555c939e0c07be5e4d628a3ed27405b859b60255a0d58894ef74bcb6e1fc4ef2d1f3f248e4d7eaad2aa9bde02c671ce353f265a43467c17a6529c827c15ff232e1ab538cf381702daac8f75ac7e50ea80fbd0384d543c1672c5b98d1c28371337256e6f2f172b77e661508b309bd16afff42f6f33ee2905f85bfd3d4e53aad33c70a36f03f83982f59c9556f8a56e8db86eae11e9636efceb36eeed643fefdd3e0454880bbdaf74bac5b7b650faedeb88d480f56f1d5a50865c0ed2c046f7a340333e980e0b55a72c7e0a8e62c20d1b3a10bb2ea02da374e0096f2658164fdb40c795e60417e3b40aaab07762816b8fee0f137a9100fe49a1f05ade040560c846f660dee641dee51b74d0b3d5d6afe7368595ce5bbc6f1b83fad3cdf0c5d0eb48031b637cf6693f3bbaa0201fa061901af40019322a845ce0962d8bc32dd5dd6c5c213e33895e5165434df3c88a95fc00cfbd5486cb5d2a79c0a1b377331f7c70f15f684cead742cdb5dd0ec113a12840e9e875ab9a447345cd0bda1320214b7bea8cbef55a24b5c109b720ec4efdd02df4aaa56b3083ee0d0d9f43505c9d408c3319e8e85a9352d0d5c33d0e04c982751d61245b93739547e18ef0fc15a993900ea93d982f08a4ca8cda388a66d1f166d750a1f9044fbbd8a0c37f4135cc2b903183498401aef0e57881291dfc86f4cb764329b4c854b868c9b6ac753da5ab9120b6001e32807a18409932a72476cdb931773d3836b771718378b4ef74c39e938e715d3a5b8f9331dd1e6537b97c0d5c6f22270ac4c000475e997fded94a8c9610015dcc3cc02e0759e8baeec6731b0b859c10e98af16164bee87a46c0e1709a379d1b51277a1ab1f17f91d25693ff1cb80a255dc45c9e86fd8df3aca36277
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Tofsee-10002081-0 Indicators of Compromise IOCs collected from dynamic analysis of 20 samples Registry Keys Occurrences <HKU>\.DEFAULT\CONTROL PANEL\BUSES20 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>20 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Type 20 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Start 20 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ErrorControl 20 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: DisplayName 20 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: WOW64 20 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ObjectName 20 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Description 20 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config0 20 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config1 20 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config2 19 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ImagePath 17 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\isupldcy 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\kuwrnfea 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\zjlgcutp 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\jtvqmedz 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\gqsnjbaw 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\scezvnmi 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\cmojfxws 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\xhjeasrn 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\dnpkgyxt 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\rbdyumlh 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\lvxsogfb 1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 80[.]66[.]75[.]25420 176[.]113[.]115[.]13619 80[.]66[.]75[.]419 176[.]113[.]115[.]23919 176[.]113[.]115[.]13519 45[.]143[.]201[.]23819 31[.]13[.]65[.]17415 31[.]13[.]65[.]5215 20[.]44[.]209[.]20911 185[.]161[.]248[.]12710 176[.]113[.]115[.]849 66[.]254[.]114[.]418 142[.]250[.]64[.]688 20[.]112[.]52[.]298 149[.]154[.]167[.]997 104[.]16[.]119[.]507 104[.]244[.]42[.]666 52[.]101[.]40[.]296 104[.]18[.]13[.]336 104[.]127[.]87[.]2106 142[.]250[.]217[.]1966 104[.]244[.]42[.]705 142[.]250[.]65[.]1965 20[.]103[.]85[.]335 20[.]84[.]181[.]625
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences microsoft-com[.]mail[.]protection[.]outlook[.]com20 microsoft[.]com20 vanaheim[.]cn20 249[.]5[.]55[.]69[.]bl[.]spamcop[.]net19 249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org19 249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net19 249[.]5[.]55[.]69[.]in-addr[.]arpa19 249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org19 249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org19 www[.]google[.]com19 i[.]instagram[.]com15 www[.]instagram[.]com15 api[.]twitter[.]com11 in-jsproxy[.]globh[.]com11 mobile[.]twitter[.]com8 www[.]pornhub[.]com8 api[.]steampowered[.]com8 identity[.]bitwarden[.]com8 t[.]me7 www[.]evernote[.]com6 steamcommunity[.]com6 docs[.]google[.]com5 ev-h[.]phncdn[.]com5 auth[.]gaijinent[.]com5 www[.]tiktok[.]com4
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile20 %SystemRoot%\SysWOW64\config\systemprofile:.repos20 %SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>20 %TEMP%\<random, matching '[a-z]{8}'>.exe17 %TEMP%\Administrator.bmp1 %TEMP%\nwcnlas.exe1 %TEMP%\udjushz.exe1 %TEMP%\hqwhfum.exe1
File Hashes 238ce8c9c1843ed679b1fbb20b895036dcaf7a774ccdd208991e1aa7d2e8b971275f63b3fa7aa1136c6d135806cd618f2fe36e184bc3b12925c6e9ae79d468b72c141ed24be119c7f61824c2dc962a096d36721844695fca23c5f943d51e41e2310144f3ba280383cc3a74d91167092c9eb19bb99d7a778d7c18ff63696790803741e95639f74b4f83da4714046c786d2c3dfe2e46f1cd66bf7258e8056e7f4a3ed81f6036ce912ad798d96d56f36e59aa41e95f36cc6e9b2ca18e595a1fa2d846f25d898d70e882d1b0cdd1deec43c2a8d444f156eb7b47fa120b15084aee8955b5ce7205447783ec1b1894ad61cb73061803559989171a6bd03d64ed4589fc603b5e4db94e0c034ed1d2cee6d1288c3da702d92948ddd546426c524da8ba3d6223c2e338ac109c51eaa357ab1886c8ea9ff3780b2e9ff71b4c7d3865bf3a56722e5c91ecf06847724305f285a3f349fce7f2027d4960d101fcc922a35af69c7d8d5064d6347eab9b3075de62aecfb724c9de766932da7e0228b70fdf1c63f7a4c66af7621c1c9194da75d307c48045f337f70f3e7955d617fc5966939d51f8a80cfe1db921aada4e1a6b20fb60abe99a3bbc600b102cd54afad440f008a1d6be1017245c789df35b3d30d38a25b485ff307a07d5bdf71062629fb7eff7f7abc48668266709447939ac10f570b38c8eb474219ec05009fc748b9ec347033828d03eb3758c52095597e1bef352c808d743831b838f84e22a215c808110d62fc4eb9e999898a7a1b0668a81378f4962434e6373896bfeea0f0274c66f9e3b6b35f929b9f4cf0e41a10d35fcebe508f8ef8a5bc0e52b1ee0b75abc058997117f6ffa2c7e4264186b27bc40d6c149dfbe6d551ea39d6ab337a4d295484ac331ac14
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
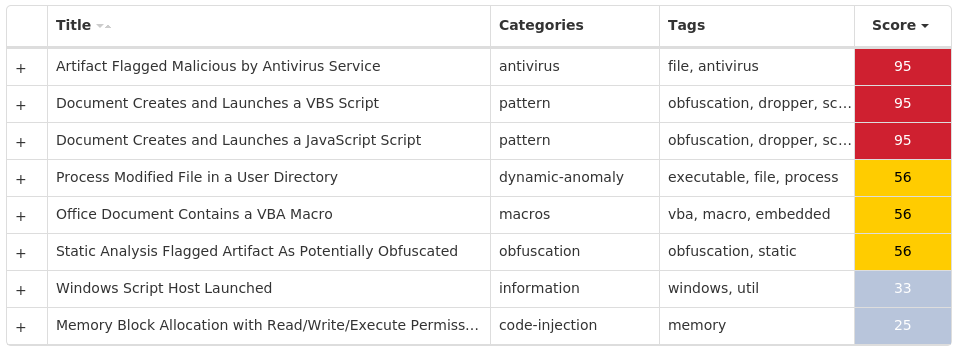
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Xls.Malware.Valyria-10002078-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\FILEEXTS\.JS25 <HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\16025
Mutexes Occurrences Local\10MU_ACB10_S-1-5-5-0-6786325 Local\10MU_ACBPIDS_S-1-5-5-0-6786325
Files and or directories created Occurrences %TEMP%\sfoWQ.txt25 %TEMP%\sfoWQ.txt:Zone.Identifier25 %APPDATA%\sfoWQ.txt25
File Hashes 09214b75e113f9df8029db90913919de573c5d16ca8005453a9b4df5c2744ab40d7dcea3a78eccc8abc6d1ddb7761bf5c0d15c79159af7af22fa6c06a7c764911e9cef0c192fff11cba232a102639387bca0af47e9fcd160a55d20065c54cf083a6e2f267fbdd6b5a1248c6e56612f18594e1d5c0a3d8d4d9dd69711f426913f49c980bb98d56a511b2adfe87a2e2f03dc172e1c0cab88fb72eaaca7d7f892fa4fd4219515547335f22d38747308304a193f3736f62c131a2866ba4ea8c2efab55c31c60c2143a851b33ba43bd05a4ca4ed1f49d34d650c764325d52159bd3bc57879f11611c36bfeec0fc76275ca7a98181382a6e9ee120980da2f63b2006775d7a2f9dbfdd4972d426ac27035251ca04b70ee49568a07b54b9b0bb20b539f660c215a73729207311b3fa8bdf9d3a92979b3b4a3647c6473f8e9e94cc844d4761e6f84d6d68a96fd8d52f792c21b5121e218b405e14b08041fa1bcd7a2815f66ace2eb7f0abd2231439d20ae7280432bfeffc0ff54030fd8b45c925788b5b45750e11c32b4992167d3b803e15d11d678a242f3accbde86e8b2897abea12017e7776a45f3bb6e284fc41398d99c7d4078d35333b29d0cd822d143c5662c6e9817935a802c774f09510b7ea92e1c71518308e3522c2f78e5a3b3514df9d26105f7c031d1f559da9eb3c4fcee035f403abb2dc3d19c0ac2a7b4f9ef87a21e9c45c807ab83a7b2a132266e1e127f46feb5b35a6a40b63154e5a52116fcb852adba482dfb38db754f42799d4505d8f17ad12fc6d6830c32df2c3fa1aeabbedb5475f8fcb8cd84bbac5f2fd9431f7287702da9b5c59c3d3d7aa4db6ba456e87db532591493c3eb2098e1dc17ae1966bbac80411bb43adc318f69680d845e74245c4c693af1d5c4066a77c419cf00614044c269ef119582c428e8ff15a3da71328fdca94b5d0f1b6def10685e91c5f739acbfb09d533f440dba4f0f62a6f90a892b5e49b3076343bb665bc9c0baa44f5b4d08ac9e74dc310906099e453b6270032106aa1668447abe6177554d6e752d61a74aaa135013b4bb9952becb248045da09b3fa1f553a776fa0302b46393ddb10d6130839018c28a1220bc8457ef18f17dc45c
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Zeus-10002075-0 Indicators of Compromise IOCs collected from dynamic analysis of 35 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\GUZUESLO Value Name: hbch1bi 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Mezas 1 <HKCU>\SOFTWARE\MICROSOFT\GUZUESLO Value Name: 3055dc04 1 <HKCU>\SOFTWARE\MICROSOFT\GUZUESLO1 <HKCU>\SOFTWARE\MICROSOFT\GUZUESLO Value Name: 11822b80 1
Mutexes Occurrences Local\{<random GUID>}1 GLOBAL\{<random GUID>}1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 172[.]245[.]217[.]1221 86[.]133[.]91[.]1531 84[.]59[.]129[.]231 27[.]54[.]110[.]771 184[.]56[.]203[.]91 174[.]103[.]25[.]1991 107[.]221[.]229[.]2161 172[.]5[.]238[.]2221 107[.]196[.]239[.]261 206[.]205[.]226[.]1301 142[.]251[.]40[.]1641 122[.]30[.]92[.]101 201[.]22[.]95[.]101 68[.]84[.]52[.]2271 24[.]31[.]240[.]2541 76[.]218[.]94[.]541 71[.]3[.]137[.]2081 98[.]95[.]188[.]1441 107[.]217[.]225[.]1581 180[.]35[.]68[.]1861 31[.]168[.]72[.]1551
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]bing[.]com1 www[.]google[.]com1 eqbaguldaxkwhelpbukqxgeuauci[.]net1 wgmvttwcmhhheeasgvofuqoiwo[.]org1 plrhyhjvjffywctkbahgiivxcpr[.]info1 hinbnfxgpqskneahavuoxvtyd[.]com1 qgkzlqraigymbmobukpjtmdib[.]ru1 sxbambmzfifirlnjxsbenrbtpz[.]com1 caozbupzdetgvwinbojtgxxwcqs[.]info1 xrkyxprttpemeqfamztgfykjdet[.]org1 zdphmsfahetgarpjdbmkvxcscnf[.]net1 pztknpblhkrhimnlbrcvspdinb[.]biz1 hpfmztgmrgqhiusfmvlbdtwdiam[.]ru1 pvdigajzpwkkfizfmmjmrpkjfeto[.]com1 cyscqgqsscutljrwqwnbcufexkr[.]net1 nfkbojqskjulbydktduoskztpf[.]org1 pvtgqceifucelgmhekrgmfe[.]biz1 gaaqciscmfiqwthiztlpzscjnyteq[.]com1 vcfqgmhdyxkirrghiblndeixojz[.]ru1 fqtfyjvdqbbqoztirtwvwdkrqk[.]com1 ivpzeiwkwkbxnvcwgqcljnifiz[.]info1 qkpibzvwrwirqcyhhudykgimz[.]biz1 xkvcuqyrstcgyvkpnijdixgbeei[.]net1 mblwytskjplvduxceypeqylce[.]com1 raihobdypsocykrtlcisgnzzl[.]ru1
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\LZP4377.bat1 %HOMEPATH%\AppData\LocalLow\odaj.koc1 %APPDATA%\Uwname1 %APPDATA%\Uwname\mezas.exe1
File Hashes 02df10e355b422c5bb5e2d597ed5ba186ccd75b1555a02f499ac181b2120ed0305f6fef63c053c000bbeb362cb05bff689439af1087333a75c69c424581549ba14053671d31720f2f9221951c1505e601fd9167ff801a805aa816b317f5e912c168294fb9090044b7bb6c09db9ad27e2e65cde38a71c3596bc9f2081f071110316b90f6758b5c39c711ad687a80b7a2ecac0fb7a6d0692d6d16b10f11ae4c1f8199818c986a03706929b3f1645dd372d53640f43ef052746cebe6d260d38917b1c5bbb2c3aeee33f6cf3a96baeb0c5e88ea1f39fc71975bba8ec090bb04b51c428b99d76eee9430304deb161a95e4bb136f20165ea3f217099e5663281e298092b32f617e4dbf6056ef402d619be0c310184c8c6b510058aacba678d19dc4aa02dfeefc5caf4511a29ae3fe30a9da8ad2c62ad2ae9fd39ebc2db46a463957597334d15fcafebf426192ef6d1535eeaa4a7de8126b74e58fbacc6ec94e4f3ab5b34b6c7ed9349de1a287d0d5592b78cce35522702e91b8ab5db3d62eae6b67b5e374bd4c2b34ae49846a760619880fd804faed9566d35d25eeda4189c47f9866064034a052248997224a7e1687a7ed958e5f948f921f3fac55ad2edbb12570daf6553bb3b7256019f2a51d44b06e823ba23b75c675d881387cdc5483008ecb9837cc58d096942f3ae0460683bc9f5c35112655be103075ef8f7a58abaf550c979854a72dd3fbe2c2a0b18ae0bd660757333e10e893b2487390312886634a093be869d634387c01e319a72f24bdfb0b4c9a2c808aa88a72f7ad171544b713d596d881d68cc2ac29affc59650aa7ada44c7973fcb014c2f8535b1648a365469e6829635dd11d2da647afc6bf13c4ce3c8fabd7dfb128f6cfea32d12f7e06f0b4992a85a35b0487200ca1f49801827aabf6e747ea4a2b07dfd5f7310d3b88b5e3db4a9f73e6255dbaa0f11d9b1d75d70278ff41f8df374dd31869a68a73d1008e041af17b70024313eec53d55c113e7c167ad243fb43eeea842f04070d160e9c3f0fc17798890e73cbfdd95ec9cc21d6253e9a1e823362efa300a3b103f754a19a45c3b064b3355cd6ab93b68eb0c4651ef6c39601cd5a3419e5cfc50dbf8ef2d581
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.njRAT-10002074-1 Indicators of Compromise IOCs collected from dynamic analysis of 23 samples Registry Keys Occurrences <HKCU>\SOFTWARE\7E3975E4EF230D7D91954 <HKCU>\SOFTWARE\7E3975E4EF230D7D9195 Value Name: 8BE2FB14B479CCDD9BC15BEAF091A52DF492882CB14B74F194A69E01EEF8E94C 2 <HKCU>\SOFTWARE\7E3975E4EF230D7D9195 Value Name: 6E2CF9A6CE187C062019E955FF60F4FC3EF815C130C306272E592ACCF4FC927A 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 737bd67e46d5cadac827d831840e1c9e 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 74863e1e5b984f4d9f6114e67967ba5a 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: d9dbb7f30ccf6b9605ba0f91e4001e71 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: dc9f4568244aa164419d8d55d41d338c 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: e4f591a3b114bf24d3f9b3a6ef913cb4 1 <HKCU>\SOFTWARE\7E3975E4EF230D7D9195 Value Name: 0452D60D658A43929BF2D5BC049E2C57C2D61F58B6444BAB88834C870305DFDF 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: c2527172636652462d2476d220259bd2 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 3845e39e1f3dcec4ff7961b0a2f0ba67 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bbeb2271f980d0c2e59e411521a4e871 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 890bacd47c7d51fd7312becbd950c7bf 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 708d8fc0a77c9a0879ac7cb1189ea39a 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: d5d3c1f0e4d5aef3a94d97f2fb26b8d6 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 9520744a7360c89a58faf9868697bdea 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 2cae9becdde38041e4e330e3f52f0a60 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: e58abc3caa74411ce434a3aa461ead84 1 <HKCU>\SOFTWARE\7E3975E4EF230D7D9195 Value Name: 91E582DD0FE0224A74B326FAA35161958AAE425DF4B6151646B9C330E7BD5487 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 6598d612c9ecbbb158c36266743d42c8 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: b8b4e1b25a2b6f817649b78b5b5a5d29 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: b152c91bc1c4e0824480fad7befedebf 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: cc4f48707ebaf216d4fef0b4c0c61272 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 5be60fdc5ddb62f32a7de89740b3cd166e812a191d5b4813db31d0a45ab00677 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 12d415023bdd583b20d45b79802e10e84dd45196c3d1caafc488024d3be9eca6 1
Mutexes Occurrences ogqaAwjfB2yh3bfL2 SCv88LFTFFI8dR9w1 1QnSO4JAiZV6WpHF1 N4axFUgaXdIayzbn1 22gJEda1Zfw2vwfK1 hQjSOlWGIZB5DO8N1 nsly6rwu2jgM0E2F1 MuT3h4qwhzPDqNiv1 i92Ri83XAhIENZeN1 CpM0BozFwJiJLCI41 HYYqdMBVvkvW9qet1 iGfoxbmflgpokAoH1 b6yNsMdOe03HL9LG1 leyfUfKDaom1wjaJ1 cCWueNtsBI6pgZxq1 MfH1eroMODfvADCS1 QGrfowgnGcHxTGed1 S7lyHQsJzumSHESB1 3tZldvx3UxeahMbo1 catUiEXpaeVC068N1 axlm4DdNg7oDuPl81 mIZVGJlfF3sM9H741
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 209[.]25[.]140[.]1807 193[.]161[.]193[.]994 209[.]25[.]140[.]2234 209[.]25[.]140[.]2112 18[.]231[.]93[.]1532 54[.]94[.]248[.]372 18[.]229[.]146[.]632 172[.]67[.]34[.]1701 3[.]67[.]112[.]1021 18[.]228[.]115[.]601 18[.]158[.]58[.]2051
Domain Names contacted by malware. Does not indicate maliciousness Occurrences metal-msn[.]at[.]ply[.]gg6 ayman03-31268[.]portmap[.]io4 0[.]tcp[.]sa[.]ngrok[.]io2 pastebin[.]com1 5[.]tcp[.]eu[.]ngrok[.]io1 engine-perception[.]at[.]ply[.]gg1 battery-columbus[.]at[.]ply[.]gg1 members-path[.]at[.]ply[.]gg1 asked-dress[.]at[.]ply[.]gg1 insurance-chocolate[.]at[.]ply[.]gg1 works-threaded[.]at[.]ply[.]gg1 visit-tamil[.]at[.]ply[.]gg1
Files and or directories created Occurrences %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\3845e39e1f3dcec4ff7961b0a2f0ba67.lnk1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\bbeb2271f980d0c2e59e411521a4e871.lnk1 %System32%\Tasks\c2527172636652462d2476d220259bd21 %APPDATA%\bbeb2271f980d0c2e59e411521a4e871.exe1 %APPDATA%\9520744a7360c89a58faf9868697bdea.exe1 %APPDATA%\890bacd47c7d51fd7312becbd950c7bf.exe1 %ProgramData%\708d8fc0a77c9a0879ac7cb1189ea39a.exe1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\d5d3c1f0e4d5aef3a94d97f2fb26b8d6.lnk1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\9520744a7360c89a58faf9868697bdea.lnk1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\890bacd47c7d51fd7312becbd950c7bf.lnk1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\708d8fc0a77c9a0879ac7cb1189ea39a.lnk1 %System32%\Tasks\3845e39e1f3dcec4ff7961b0a2f0ba671 %APPDATA%\d5d3c1f0e4d5aef3a94d97f2fb26b8d6.exe1 %System32%\Tasks\bbeb2271f980d0c2e59e411521a4e8711 %System32%\Tasks\890bacd47c7d51fd7312becbd950c7bf1 %APPDATA%\2cae9becdde38041e4e330e3f52f0a60.exe1 %System32%\Tasks\d5d3c1f0e4d5aef3a94d97f2fb26b8d61 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\2cae9becdde38041e4e330e3f52f0a60.lnk1 %System32%\Tasks\708d8fc0a77c9a0879ac7cb1189ea39a1 %ProgramData%\e58abc3caa74411ce434a3aa461ead84.exe1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\e58abc3caa74411ce434a3aa461ead84.lnk1 %System32%\Tasks\2cae9becdde38041e4e330e3f52f0a601 %System32%\Tasks\e58abc3caa74411ce434a3aa461ead841 %System32%\Tasks\9520744a7360c89a58faf9868697bdea1 %ProgramData%\6598d612c9ecbbb158c36266743d42c8.exe1
*See JSON for more IOCs
File Hashes 0370568ad761d369d0fe91aa0bf745ed954676aea7674e3238bf5f133cff49ed10f1764ba7cb74110a0a9db2920c7d3007bbd3e13df111a2b697f3c244ad3a2112d415023bdd583b20d45b79802e10e84dd45196c3d1caafc488024d3be9eca61a4101c995b330093388628b206da88250bcceebc0c3ef6b25334db5babfe5fb305d0c9e1e847a7306285575091f523f521dea096cfc8db5a7b32e465ac180bc353d5db9b2e6175843d74a62770d7fd2a82b43d06154b7cef6137e49a23c74ba5be60fdc5ddb62f32a7de89740b3cd166e812a191d5b4813db31d0a45ab006775f2bd99627a93373f1a3ca2728063698863b10b0479faf782fab447a1e061e2d720fb13f797dbba6a0ec19877c644abb0dde8bf6906b2ea4559a2a7cafe6b5cd73619700a7d06a97037c3dc393146d58f7624356f766f9bb19fe9d33308522f280b8a0a5cca9ed908dec4f2441a9515efa3bde5a0b67a689316816c4ad6eae858c66b9dec0e884de4cc10f46b73f666ebe0ed0c5709a80fc7bedf0f4eddea47395f8c56216adfc5127dfe195128001298dd815b85b2335f8da2def24b5364ee3b26c13faf1b58138c2e4bb181ecf5cd561bef6fa0e9dfc343248453d34be55bdb8338d589b1622dffb54ce8f512b8b70df7315ee75b28f47000e39cd5b9a40c4c043c8d127281746c9c81a202bfb9f9a2ff3150775b50285d78e78c069d04712c6042c265751e439c5a96222b5821e2c526614b3189d614ddc1e89f8e41433d6d4268de943471bbfb03cd03056504d6e0ff7c81ad6b684d6af6d28d89f5d4c08db67fb81e08ae38d7241c2247b0429e261481c3e069f7be47bb5a71dd0ed8e9fe75fd2007d1c704022a95ba8a0726c737a980eedb99bef704c83da5742c154bbeb13e60e5169d58acf9264f620d7474c697b48fde63db5c9af551d5431c9aaf8ed74db49ccee7eb4b157dfaa6ddc6faf068f267eb9ff50000225879bfdb4b8cef6e407e5b8ce98202da3776a3936e61a07e3acd5538eace8d232d763b0b707ef
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
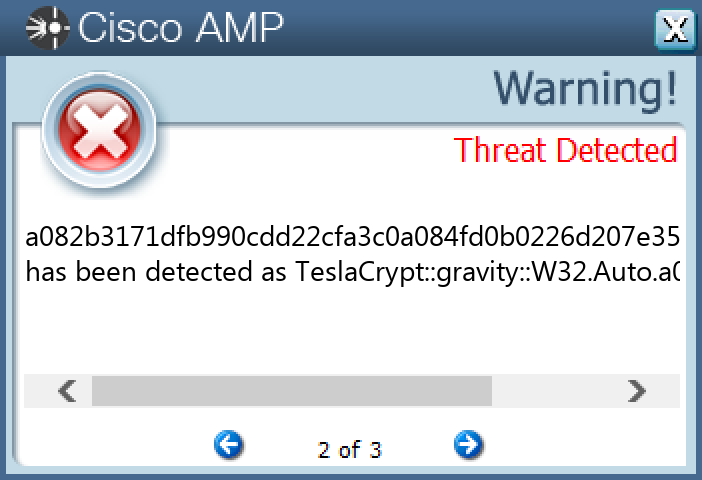
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.TeslaCrypt-10002553-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLinkedConnections 15 <HKCU>\SOFTWARE\XXXSYS15 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.CHECK.0 Value Name: CheckSetting 15 <HKCU>\SOFTWARE\XXXSYS Value Name: ID 15 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'>15 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'> Value Name: data 15 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Eoawaa 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Update Installer 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: BCSSync 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: pjluoctfesrw 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: pooqkvflocpc 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: fwxkhpyjafio 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: eacropxvpihj 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vnqeujgcjhuk 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: exetrpjyrtxg 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: njlwvbxfxmkw 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: efwffgphvtdj 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: unwhvdemefqp 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: tfeckcphtbxc 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: gqvoaslhlyoj 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ypojwqitnhyi 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: tguywpqhaosq 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: jhrayyslywvo 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: rcjftpogpimu 1
Mutexes Occurrences ityeofm9234-2342315 c7312001 -9caf4c3fMutex1 FvLQ49I›¬{Ljj6m1 SSLOADasdasc0009001 SVCHOST_MUTEX_OBJECT_RELEASED_c0009X00GOAL1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 85[.]128[.]188[.]13815 162[.]241[.]224[.]20315 34[.]98[.]99[.]3015 35[.]205[.]61[.]6715 23[.]221[.]227[.]1869 23[.]221[.]227[.]1746 194[.]58[.]112[.]1651 204[.]95[.]99[.]2431
Domain Names contacted by malware. Does not indicate maliciousness Occurrences biocarbon[.]com[.]ec15 imagescroll[.]com15 music[.]mbsaeger[.]com15 stacon[.]eu15 surrogacyandadoption[.]com15 worldisonefamily[.]info15 apps[.]identrust[.]com15 api[.]wipmania[.]com1 n[.]ezjhyxxbf[.]ru1 n[.]hmiblgoja[.]ru1 n[.]jntbxduhz[.]ru1 n[.]lotys[.]ru1 n[.]oceardpku[.]ru1 n[.]vbemnggcj[.]ru1 n[.]yqqufklho[.]ru1 n[.]yxntnyrap[.]ru1 n[.]zhgcuntif[.]ru1
Files and or directories created Occurrences %ProgramFiles%\7-Zip\Lang\ka.txt15 %ProgramFiles%\7-Zip\Lang\kaa.txt15 %ProgramFiles%\7-Zip\Lang\kab.txt15 %ProgramFiles%\7-Zip\Lang\kk.txt15 %ProgramFiles%\7-Zip\Lang\ko.txt15 %ProgramFiles%\7-Zip\Lang\ku-ckb.txt15 %ProgramFiles%\7-Zip\Lang\ku.txt15 %ProgramFiles%\7-Zip\Lang\ky.txt15 %ProgramFiles%\7-Zip\Lang\lij.txt15 %ProgramFiles%\7-Zip\Lang\lt.txt15 %ProgramFiles%\7-Zip\Lang\lv.txt15 %ProgramFiles%\7-Zip\Lang\mk.txt15 %ProgramFiles%\7-Zip\Lang\mn.txt15 %ProgramFiles%\7-Zip\Lang\mng.txt15 %ProgramFiles%\7-Zip\Lang\mng2.txt15 %ProgramFiles%\7-Zip\Lang\mr.txt15 %ProgramFiles%\7-Zip\Lang\ms.txt15 %ProgramFiles%\7-Zip\Lang\nb.txt15 %ProgramFiles%\7-Zip\Lang\ne.txt15 %ProgramFiles%\7-Zip\Lang\nl.txt15 %ProgramFiles%\7-Zip\Lang\nn.txt15 %ProgramFiles%\7-Zip\Lang\pa-in.txt15 %ProgramFiles%\7-Zip\Lang\pl.txt15 %ProgramFiles%\7-Zip\Lang\ps.txt15 %ProgramFiles%\7-Zip\Lang\pt-br.txt15
*See JSON for more IOCs
File Hashes 08ebc4366098a724b58093793a462378a5470db3eadfca7c18b8f7126aad2ecb0ba923eb73b1cb82d42ff8645951a98c45316a731fb2a0c0f395778e2a2a51793337931b618168c2c64296cc81b799a18f8782a26238f9dd2611d100c2238d75487a322749e90bdf30fac46a5288fabf7bcdebe59af9919982ef8c262f80d97b858834e73fe318b38ee3892cd7176018ee7f0d92d77ac51720a2adf2e7f5968aa082b3171dfb990cdd22cfa3c0a084fd0b0226d207e35392a9575b5b3de0fde7a3a7a5c48776290b7ea21051c68ea52e03db8a48557ee427db38fcb39fe3bd12a68adce292f5e29c375c48cc0a948919bd7e8220cd77ceff3a4dd5db253d24aba92906b93160cc0bd8839140fda9176bb4fd2ea43b02048abe9530adb02812cccf5b6f7838462079df7cd50bcc5a88a5fd1898858b7705a535614816c70910e4d007157de960ff25746397334372a2651d6360826585eeefdc4157cf991cd58ed2388700bb70974763294d5d5ca53c1e71010f6515547ddf9a6911af3630778cd3e8d5372326ecdc926ec6fc0ea043f11561161a9faae8232276a2513cf2149ce6b62755739953f09eca8a85937fcbe0f184533c50c67715804946f4c2c4f655eb8db1b9fc2448610fd85c267b461e2faf987f982577381450563ee0d24ae186f8bc090131eb16ee8007f62dabbe472eed7c7354436f8aec9372a81e2e686164
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK