Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 26 and June 2. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
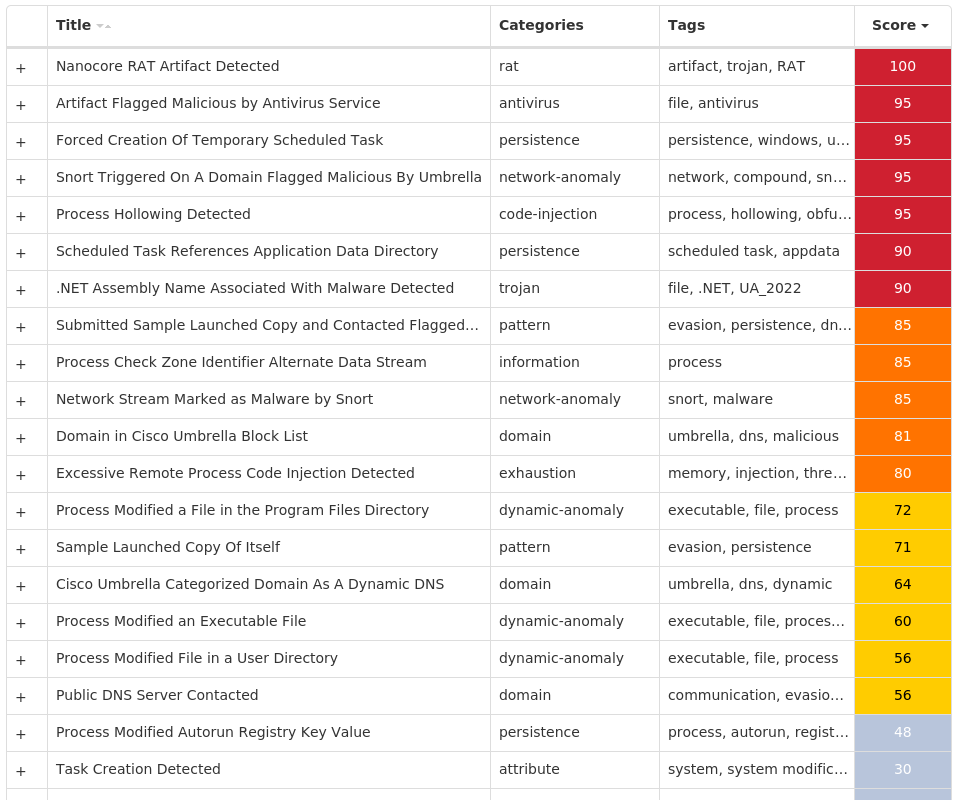
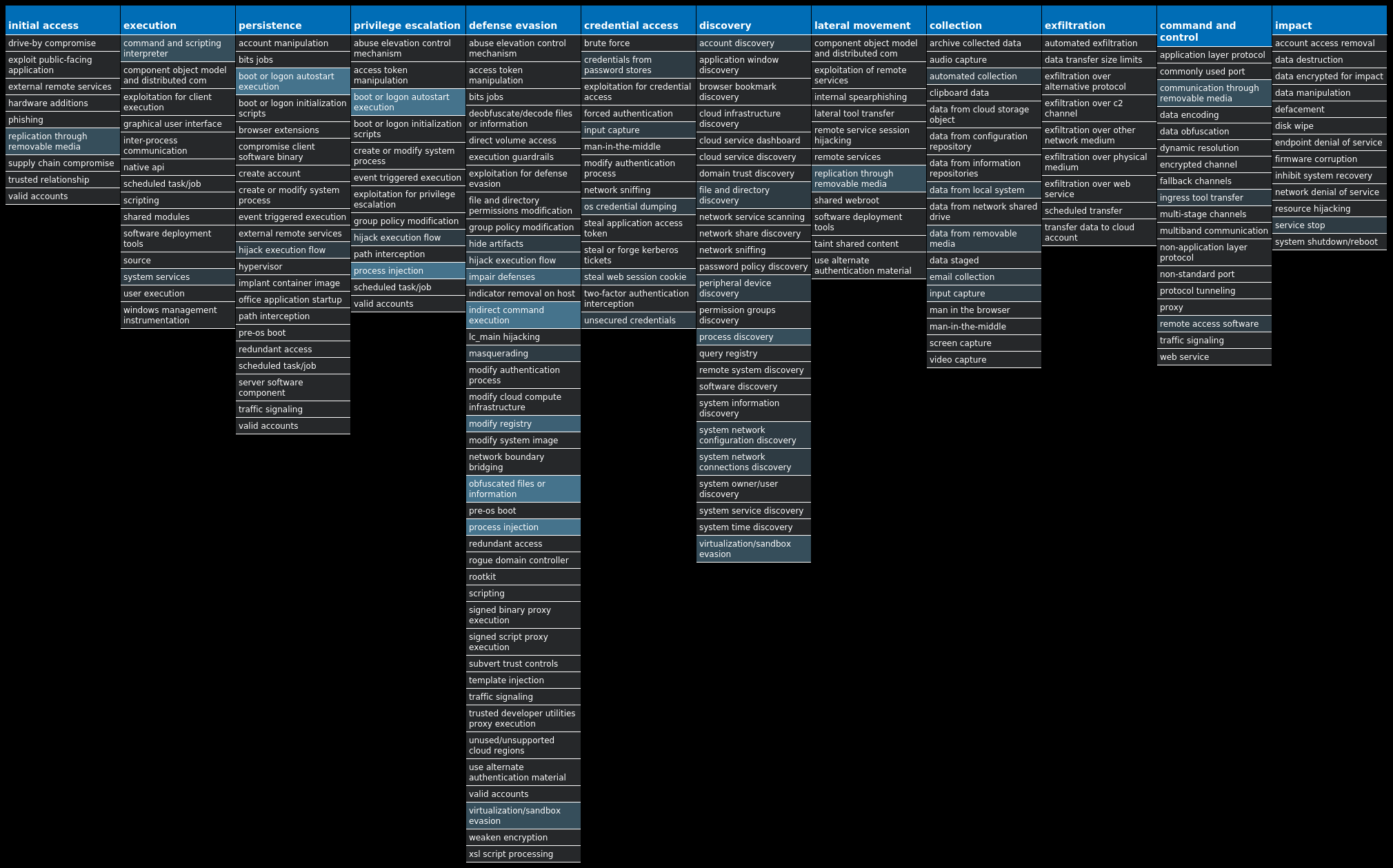
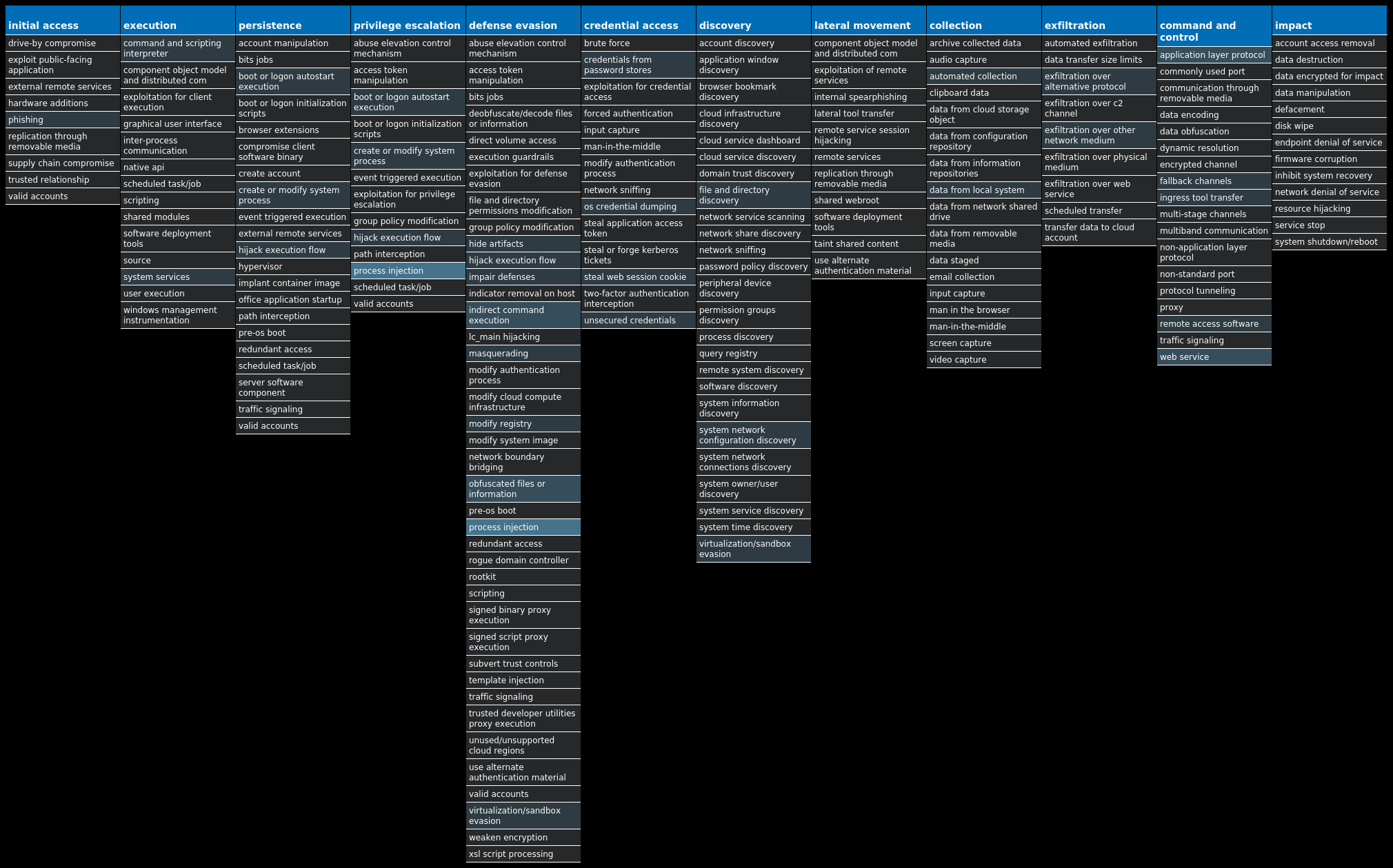
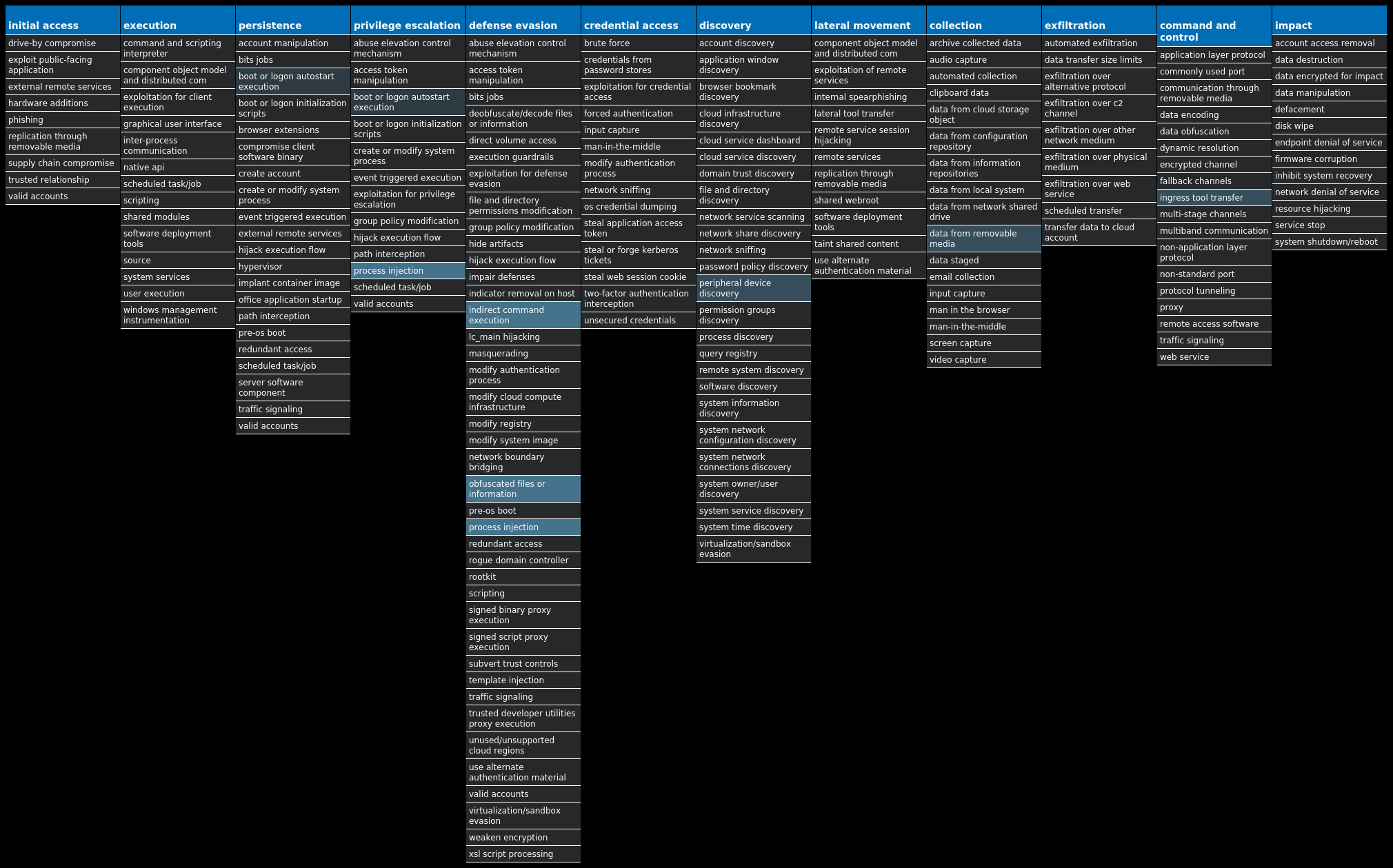
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.Nanocore-10003611-0 Dropper Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes. Win.Dropper.Glupteba-10003588-0 Dropper Glupteba is a multi-purpose trojan that is known to use the infected machine to mine cryptocurrency and also steals sensitive information like usernames and passwords, spreads over the network using exploits like EternalBlue, and leverages a rootkit component to remain hidden. Glupteba has also been observed using the Bitcoin blockchain to store configuration information. Win.Downloader.Upatre-10003575-0 Downloader Upatre is a trojan that is often delivered through spam emails with malicious attachments or links. It is known to be a downloader and installer for other malware. Win.Dropper.DarkKomet-10003567-0 Dropper DarkKomet is a freeware remote access trojan released by an independent software developer. It provides the same functionality expected from a trojan, such as keylogging, webcam access, microphone access, remote desktop, URL download and program execution. Win.Dropper.Tofsee-10003414-0 Dropper Tofsee is multi-purpose malware that features several modules to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages to infect additional systems and increase the overall size of the botnet under the operator's control. Win.Dropper.Bifrost-10003394-0 Dropper Bifrost is a backdoor with more than 10 variants. Bifrost uses the typical server, server builder, and client backdoor program configuration to allow a remote attacker, who uses the client, to execute arbitrary code on the compromised machine. Bifrost contains standard RAT features including a file manager, screen capture utility, keylogging, video recording, microphone and camera monitoring, and a process manager. Bifrost uses a mutex that may be named "Bif1234," or "Tr0gBot" as signs that it's been successful. Win.Virus.Expiro-10003154-0 Virus Expiro is a known file infector and information stealer that hinders analysis with anti-debugging and anti-analysis tricks.
Threat Breakdown Win.Dropper.Nanocore-10003611-0 Indicators of Compromise IOCs collected from dynamic analysis of 20 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: AGP Manager 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\TASKBAND Value Name: FavoritesVersion 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: newapp 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\TASKBAND Value Name: FavoritesChanges 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: YLcqPJe 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: MmRKwR 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\TASKBAND Value Name: FavoritesResolve 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\TASKBAND Value Name: Favorites 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: sOFvE 1
Mutexes Occurrences Global\{0d867adb-3500-4c95-b576-70e197aae229}1 SBmdTDfceAO1 dguPijsTgw1 O64O3T231GHA5GE51 urTYJlYpYYNDkAVkNuNKf1 kHCbAyHopHm1 fsmTWPRqOirFDgctmfcTeCy1 AeqWcHrmYllWoFRInLc1 zfBIOx1 tIJFKdFWJdJzxCITKNerlYSxEC1 hmRipQYdtfQNsUPHFxksrc1 gtRQfGqEtQfZ1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 64[.]185[.]227[.]1553 23[.]193[.]194[.]1481 173[.]231[.]16[.]761 104[.]237[.]62[.]2111 162[.]241[.]60[.]791 46[.]105[.]157[.]2411 45[.]12[.]253[.]2421
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]ipify[.]org5 apps[.]identrust[.]com1 mail[.]nereus[.]cl1 ucnano180523[.]ddns[.]net1 mail[.]sgsbauto[.]com1
Files and or directories created Occurrences %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp8 %System32%\Tasks\Updates7 %APPDATA%\Microsoft\Windows\IECompatCache\read_it.txt1 %APPDATA%\Microsoft\Windows\IECompatUACache\read_it.txt1 %APPDATA%\Microsoft\Windows\IEDownloadHistory\read_it.txt1 %APPDATA%\Microsoft\Windows\IETldCache\read_it.txt1 %APPDATA%\Microsoft\Windows\Libraries\read_it.txt1 %APPDATA%\Microsoft\Windows\PrivacIE\read_it.txt1 %APPDATA%\Microsoft\Windows\Recent\read_it.txt1 %APPDATA%\Microsoft\Windows\SendTo\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Accessories\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Administrative Tools\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Maintenance\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\read_it.txt1 %APPDATA%\Microsoft\Windows\Themes\read_it.txt1 %APPDATA%\Mozilla\Firefox\Profiles\<profile ID>.default\bookmarkbackups\read_it.txt1 %APPDATA%\Mozilla\Firefox\Profiles\<profile ID>.default\read_it.txt1 %APPDATA%\Mozilla\Firefox\Profiles\<profile ID>.default\webapps\read_it.txt1 %APPDATA%\Mozilla\Firefox\read_it.txt1 %PUBLIC%\Documents\read_it.txt1 %PUBLIC%\Music\Sample Music\read_it.txt1
*See JSON for more IOCs
File Hashes 10090f0b186fb4818b017583c10e21e56ac1a9365020211c619bfc652fab01fb1d1639113b0f01d2044ab2b41b3198a73497245faba4364ae7ea10a0ef39b2671f96eaeda59db9e5803a11f4d045b309aed1e4d63e9952af0491b69edbf435072548dd5666787e050a7d3b96f5afadfd255858fae037a49b7ee7a91ecfbe916727618a1f5fcade2d1b13452dc9e463b295273d115483928e3a671cb8e7a8009334d66474f8157ba70f6de429b8e624cd05a5512c46daf4f9ccd8c6adad5baece3541875e5b62e84130450e229c73132431f93277343cf5214b65846d6000a7b93625699aceef8218cece58914659f6ba003e6f26ad033645ed738b4972050aa53b308d520b3707fed24d11275ec37f85bb4543d0098ef6c7ec965837a5a55dca7e407cf9ad8a6c49b22e15151b5fd82bf6f0f6361c5e3f3abe9b76af8bf68f7e8c9b30a3a8e903fdaa354943efe56e15a10ccc7515c5d7bee8b7ee624f5b22119748fc497d427eb41191ea495d907cd5d2dd9455ed20bf08df947bdb15d84baf9cd47c4593254f37eb5bef6b0d887f7132ce6d9678af33799da736d6073382faae6389876208f0c72afd8dfb44720bb2b94e31f9f8cf446c49c55748c912b44db13a9b8c3312ce8b485d1ddbc9a4c840a08e94793b109f2e7aef32b46fb999e3b7839de29a4736fb565b36d5c4aeea0eea28c8384ae8249a1bce267ec75f4196c4c96c2c76d0f6caa554e1bda74e44ba7fab6a678200cfc40189a7f489af5d23e0b1008f8c4231c9e35552a08a4a708e8bd978f72f7b8b9991f6e7926d6fbaa7e5950c07075986a0e853f4e919e1c39f0e64a878ff97143a1d49ea5a4eb186dfefca8f75ee68a472ea90763b970f83c9285c1178064f8174be4916e7da9ca740
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
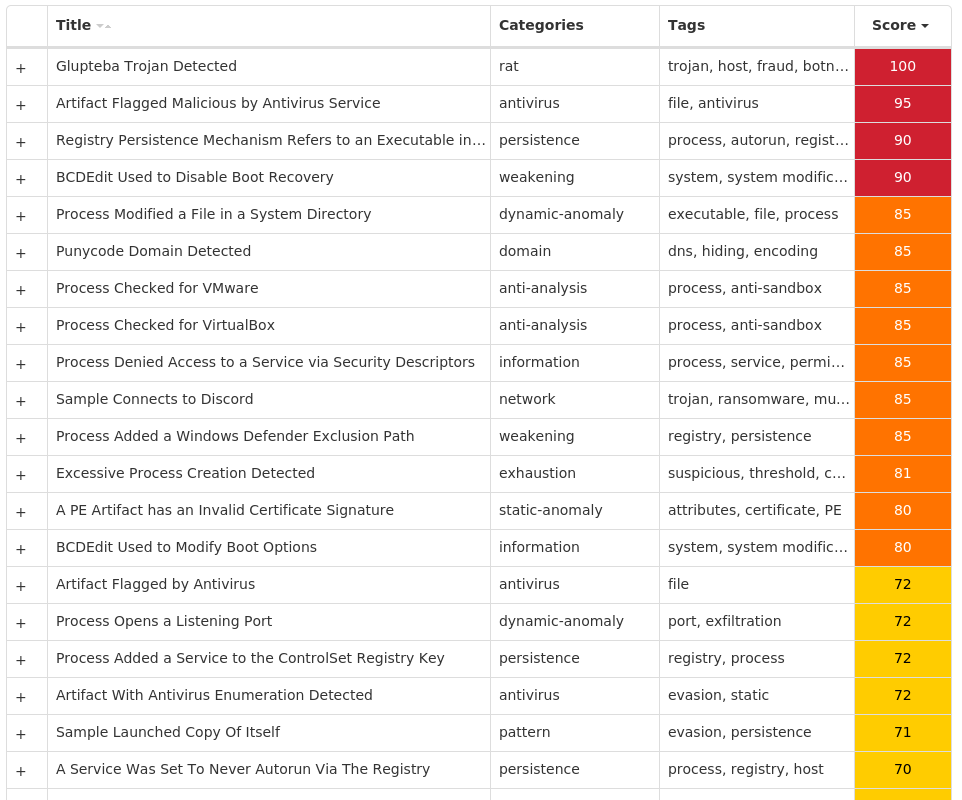
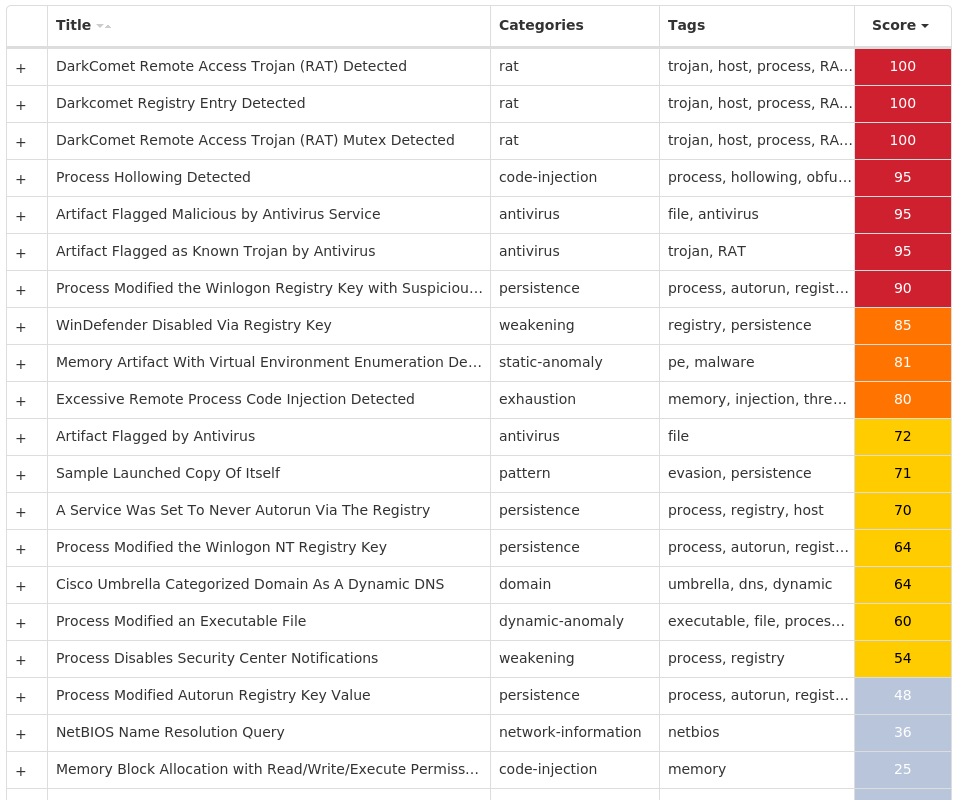
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Glupteba-10003588-0 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\A1890984 Value Name: PatchTime 10 <HKCU>\SOFTWARE\MICROSOFT\A1890984 Value Name: PGDSE 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: ErrorControl 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: ImagePath 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: DisplayName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: WOW64 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: ObjectName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: Type 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: Start 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: ErrorControl 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: ImagePath 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: DisplayName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: WOW64 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: ObjectName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: Type 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: Start 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ErrorControl 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ImagePath 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: DisplayName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: WOW64 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ObjectName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: Type 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: Start 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: ErrorControl 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: ImagePath 10
Mutexes Occurrences Global\SetupLog10 Global\WdsSetupLogInit10 Global\h48yorbq6rm87zot10 Global\xmrigMUTEX3133710 WininetConnectionMutex10 Global\qtxp9g8w10 Global\kn29r6c61 Global\473ggh6j1 Global\wpewcqppg8z44x891 Global\IV71LG3P1 Global\986spw6e1 Global\ag7xpe521 Global\wpsSerMutex51
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 204[.]79[.]197[.]21910 20[.]209[.]34[.]3610 162[.]159[.]133[.]2336 20[.]150[.]70[.]366 142[.]250[.]15[.]1275 172[.]67[.]186[.]1135 185[.]82[.]216[.]484 162[.]159[.]134[.]2333 81[.]3[.]27[.]443 74[.]125[.]128[.]1273 185[.]82[.]216[.]503 20[.]150[.]79[.]683 104[.]21[.]1[.]43 162[.]159[.]130[.]2331 162[.]159[.]135[.]2331 108[.]177[.]102[.]1271 142[.]250[.]112[.]1271 172[.]253[.]120[.]1271 185[.]82[.]216[.]641 20[.]150[.]38[.]2281
Domain Names contacted by malware. Does not indicate maliciousness Occurrences msdl[.]microsoft[.]com10 vsblobprodscussu5shard35[.]blob[.]core[.]windows[.]net10 vsblobprodscussu5shard60[.]blob[.]core[.]windows[.]net10 cdn[.]discordapp[.]com10 fastprivate[.]me8 stun1[.]l[.]google[.]com5 stun[.]ipfire[.]org3 stun4[.]l[.]google[.]com3 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]mastiakele[.]ae[.]org3 stun[.]l[.]google[.]com1 stun[.]stunprotocol[.]org1 stun2[.]l[.]google[.]com1 stun3[.]l[.]google[.]com1 server3[.]mastiakele[.]icu1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]mastiakele[.]icu1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]\xd0\xbe\xd0\xba\xd1\x80\xd1\x84[.]\xd1\x80\xd1\x841 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]zaoshanghaoz[.]net1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]mastiakele[.]cyou1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]cdneurop[.]cloud1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]zaoshanghao[.]su1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]zaoshang[.]ru1 server4[.]zaoshanghaoz[.]net1 server6[.]zaoshang[.]ru1 server14[.]mastiakele[.]cyou1 server1[.]xn--j1ahhq[.]xn--p1ai1
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\Logs\CBS\CBS.log10 %SystemRoot%\rss10 %SystemRoot%\rss\csrss.exe10 %TEMP%\csrss10 %TEMP%\csrss\dsefix.exe10 %TEMP%\csrss\patch.exe10 %System32%\drivers\Winmon.sys10 %System32%\drivers\WinmonFS.sys10 %System32%\drivers\WinmonProcessMonitor.sys10 %TEMP%\Symbols10 %TEMP%\Symbols\ntkrnlmp.pdb10 %TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE0210 %TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE02\download.error10 %TEMP%\Symbols\pingme.txt10 %TEMP%\Symbols\winload_prod.pdb10 %TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E36110 %TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E361\download.error10 %TEMP%\dbghelp.dll10 %TEMP%\ntkrnlmp.exe10 %TEMP%\osloader.exe10 %TEMP%\symsrv.dll10 %TEMP%\csrss\DBG0.tmp10 %System32%\Tasks\csrss10 %TEMP%\csrss\injector10 %TEMP%\csrss\injector\NtQuerySystemInformationHook.dll10
*See JSON for more IOCs
File Hashes 22212563c82d627560b8a141299031992fde210f22c6be2471d3497bf8cff13b57feb1fe02b13382d369b5626e872a6159ff6dea32bad5a6d7ce6b6f6a93016d9c005e337df63510b6a2a4758df8d4840b6b1ad35ee9eba3bfcdde9cd1fab858c79398d04526ad67bb70628850a35678abcdb7772c11d7539354750dd9d7d36ecbb12735307be5876ab96badb940f8e5870542005c6f5220e968d41e7d84d835cdc9e61ff13c55f8a332ccfe2a1e6d2b2cf356a6954f6d555e4edf91f5a56db9d349d2bfed8f0eaa962d8adcc5e47c9ec234a8acc9ffbfcbfdbe547711fa43eddaf42e9987a8e7d8c7223a38a8083d8588278673653fbbbc3612ef675c269292f7ae491824c410240f87ba1cffa233cfb761bc2c856e97785685dae707110c68fcf0cd38f5e888254400b44cfe246b76588c2fcdd89c4e4d38b33d7c099ff83c
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
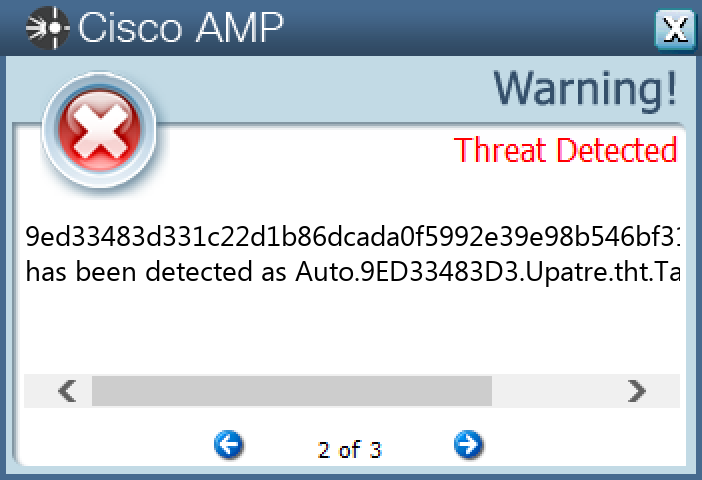
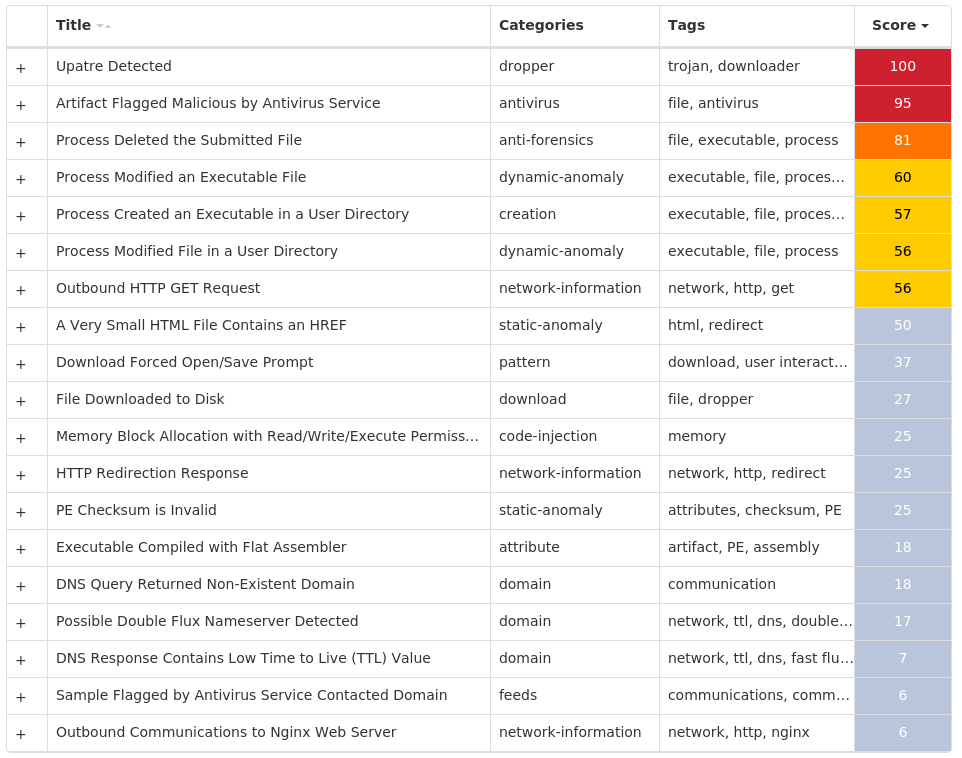
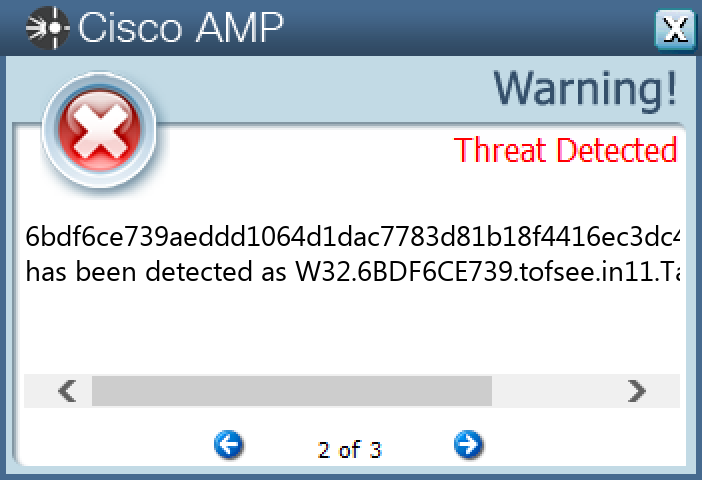
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Downloader.Upatre-10003575-0 Indicators of Compromise IOCs collected from dynamic analysis of 27 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 94[.]23[.]247[.]2021 104[.]127[.]78[.]81 85[.]13[.]138[.]1001
Domain Names contacted by malware. Does not indicate maliciousness Occurrences x1[.]i[.]lencr[.]org1 infodienst[.]diakonie-sh[.]de1 kaluhanimale[.]com[.]br1
Files and or directories created Occurrences %TEMP%\uiszf.exe26
File Hashes 0025f3df6883176730c11dac5900248e88697beeefc2b416eeb269ed0e3f6d3d010fac5139b82b321981a91ff0f5d4e5f099d12507434444daa16f0b19b38825035d1ca9d46f6d91d25e1861f313b5efd49ce750e3728ee0bc406e884283be5307526fdb8515176737d2b75cd161a23fbb9b6e24f715ad690bbbe29f92a3e37e0a7e1e4186d76c4666eb488589e23c9bf0640ddc69ec0e51115bcca282266c501aae1b61199b29d0e9c3887be69c4d4228e7030d86e3c15b5246c4e0bb47e0ce2fbd448b7452dea7da39f66fee3400c07291bbd188045b5326cfc66a712fafba3384ec513e547d2b7871157b10f796ec2ebcf808aec27c8a9e29af1b444f315b338ae2aee340172e93599dea6dfdc4c8a5628f9e8f1f1c814d9a812b4cafe67d35f7b5f210514d3e7e27113d6f20a72dfc0ee9ad33c19e81ab0db9c8641396443e0b9bcf7f7865ce98cbe2c87a7861f042dfc1843f881490344629b5fcc6126d503505f469fab6de7541033fe3afac3ee5b4f19d5a8302053b85be7c8048882350bd00b339efa25ae7af859a73cd96209f1a2def1c0ce5e355b2540eb91f299066a85cbecb34d3402306a6c9624479a5e31eec6dfb2fa2f3c3d5ee9b23cf5ce468b7763595a7baa39c5c7f7ea48d3537e541bc200947d7b1c727ee8aa036da7d6a0e2dea633f6b1de94d30f46f2b9c914c76ee8c7e3dda513a5259b6721cbcd472607710f6e1dcea2105ffb997577ad687b1b9d7eb09ffcb5c89c032dd892025751f678451a083a52a47e78463232cb9d48a68450769244ebaa4c6b2e6e0b82b7a341ced949f3462f6d130ba72ce6dc310bcb3fdb1eb6258c9d8982cc14166f78cf7459eff3f04765e169772f48f80530fce269caa7d0e3e686e6313988d033590d5b5b3a6c4f42f0f841446abc41119b9fc98a71d007eb577ad57a88bf3617892e1488eea266e986ed57bc6e9e4a1865922da4800262e65c26777179f28d5e59ed33483d331c22d1b86dcada0f5992e39e98b546bf31a4c42341ace7b325f70a275f74d769cfcc30e2c903f0ab6d0bf80945f406968e0dbf1bb272f7d4e7977a981b8bcc43366a937b1d430ba51ffea163f31fe7677bdcfb7e85933316ff7cb
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
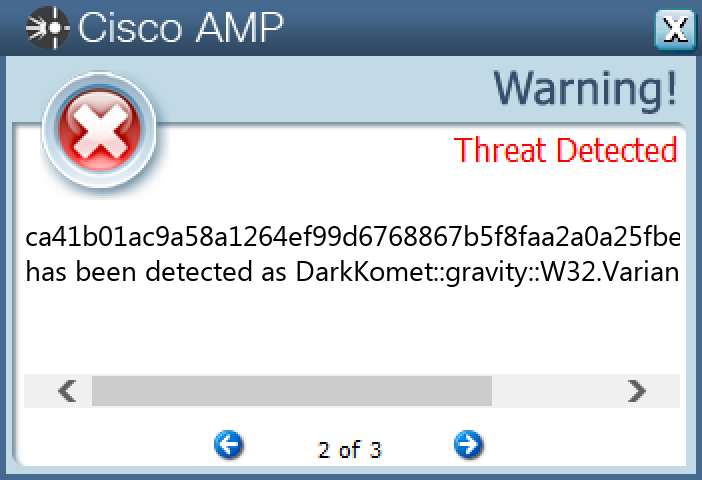
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.DarkKomet-10003567-0 Indicators of Compromise IOCs collected from dynamic analysis of 13 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DoNotAllowExceptions 4 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\INSTALL4 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN4 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS4 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST4 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SRVID4 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SRVID\ID4 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\INSTALL\DATE4 <HKCU>\SOFTWARE\DC3_FEXEC2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: winupdater 2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\BLANK2 <HKCU>\SOFTWARE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\BLANK2 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SRVID\ID Value Name: DC596I04Z1 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Value Name: blank 2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: blank 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: blank 2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\BLANK Value Name: StubPath 2 <HKCU>\SOFTWARE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\BLANK Value Name: StubPath 2 <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\INSTALL\DATE Value Name: DC596I04Z1 2 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST Value Name: C:\Users\Administrator\AppData\Roaming\explorer\local.exe 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Login access 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103 Value Name: CheckSetting 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{9BF73D4D-CEB3-CB24-E75B-560EEDBE2CA5}1
Mutexes Occurrences <random, matching [A-Z0-9]{10}>6 _x_X_BLOCKMOUSE_X_x_1 _x_X_PASSWORDLIST_X_x_1 _x_X_UPDATE_X_x_1 DC_MUTEX-F54S21D1 zXeRY3a_PtW|000000001 ^F3*%P$-D4rQ1 Global\autodateService1 DC_MUTEX-0TUK2B21 Global\SoS9WKC7SI9OK7SYGECG9YWWMKSK7CG1 Global\OWoIWCUAG5YUAKsSQ9UKkO9kq1YmGWS1 Global\autodateServicu1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 78[.]159[.]135[.]2301 23[.]49[.]102[.]351 92[.]241[.]164[.]2261
Domain Names contacted by malware. Does not indicate maliciousness Occurrences idisconnectpeople[.]no-ip[.]info2 blackshades[.]info1 mayfair[.]hazardflow[.]info1 snkbot[.]no-ip[.]org1 incognegro[.]zapto[.]org1 hf55[.]no-ip[.]biz1 pit[.]deepbit[.]net1 liquidus2[.]no-ip[.]biz1
Files and or directories created Occurrences \Autorun.ini3 E:\Autorun.ini3 %APPDATA%\explorer2 %APPDATA%\explorer\googlechrome2 %APPDATA%\explorer\local.exe2 \autorun.inf1 %APPDATA%\Mozilla\Firefox\Profiles\<profile ID>.default\prefs.js1 E:\autorun.inf1 %APPDATA%\chrtmp1 \Windupdt1 \Windupdt\winupdate.exe1 %SystemRoot%\SysWOW64\Windupdt1 %SystemRoot%\SysWOW64\Windupdt\winupdate.exe1 %APPDATA%\Java.exe1 %APPDATA%\windows.exe1 %TEMP%\help.bat1 %APPDATA%\Microsoft\lsass.exe1 \TEMP\chro.dat1 \TEMP\dial.dat1 \TEMP\mess.dat1 \TEMP\mail.dat1 \TEMP\ptsg.dat1 \TEMP\iexp.dat1 \TEMP\opra.dat1 \TEMP\ffox.dat1
*See JSON for more IOCs
File Hashes 0288fb5c371a33c58883927f547cefb16b0165ad7c9e922f0afa0d6b726296fd22640c422be4ff514eade1863c819fbf393139f6e41347c666ac48255abd82c63d5672271dce5a19477c12854cfc9f224a41b33227ab6b8b30922126136ebb9e623d563a4b10b4c2c79651a9228317a7658a3e295b4a16234fbcf0f156b8522878c41240c9dd752e4fc0aa7c5cd72764cac96ad07a59492e23f0617abc6b3e9d901a662f47c5423de665e80c39dd46d3763a292b169b19fcdb89f139fcb2e4c9c8b2959233223bd921754946e44b73a6ba0c55722deeebfb7e6d2eca00148c27ca41b01ac9a58a1264ef99d6768867b5f8faa2a0a25fbe9b4f3a808a5403462cde6b551a67008f464c5b0e4e7f38d2757eb95f918ee397782897bce8e258b50ae1110329c1f8ef7c54506a4ad279d1560609d4b8eab7da8e68fafbfa5f78948cebf5882fd086a182a61f2906b3414230746985fd5837d9175fb8a60916ea46e2f29de80fc940c88fd423fc0dd88d48e3ab131f0d3fd0dc9344f79bfd6855a3f5f500baa7beaedf08be0feaa75a33812495fde2648a80c2f5e64526f6879b4bb6
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
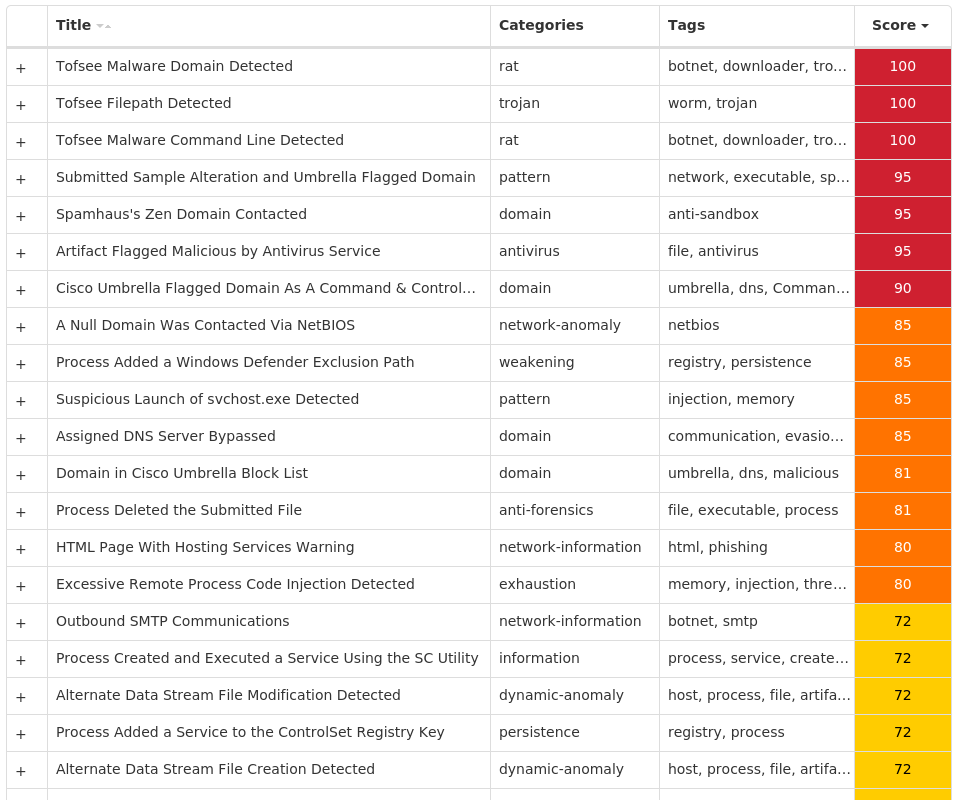
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Tofsee-10003414-0 Indicators of Compromise IOCs collected from dynamic analysis of 28 samples Registry Keys Occurrences <HKU>\.DEFAULT\CONTROL PANEL\BUSES5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Type 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Start 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ErrorControl 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: DisplayName 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: WOW64 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ObjectName 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Description 5 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config0 5 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config1 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ImagePath 5 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config2 4 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\oyavrjie 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\nxzuqihd 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\gqsnjbaw 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\zjlgcutp 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\dnpkgyxt 1
Mutexes Occurrences Global\<random guid>8 3749282D282E1E80C56CAE5A1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 80[.]66[.]75[.]2545 176[.]124[.]192[.]1185 31[.]13[.]65[.]524 142[.]250[.]176[.]1964 176[.]113[.]115[.]1364 80[.]66[.]75[.]44 176[.]113[.]115[.]2394 176[.]113[.]115[.]1354 45[.]143[.]201[.]2384 176[.]113[.]115[.]844 104[.]244[.]42[.]1983 157[.]240[.]205[.]633 31[.]13[.]65[.]1742 104[.]16[.]120[.]502 52[.]223[.]241[.]72 40[.]93[.]207[.]12 20[.]112[.]52[.]292 20[.]81[.]111[.]852 212[.]82[.]101[.]242 40[.]93[.]207[.]72 192[.]178[.]50[.]682 104[.]123[.]192[.]2202 103[.]20[.]200[.]2091 142[.]250[.]184[.]2381 31[.]31[.]198[.]2391
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences microsoft-com[.]mail[.]protection[.]outlook[.]com5 microsoft[.]com5 vanaheim[.]cn5 249[.]5[.]55[.]69[.]bl[.]spamcop[.]net4 249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org4 249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net4 249[.]5[.]55[.]69[.]in-addr[.]arpa4 249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org4 249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org4 i[.]instagram[.]com4 www[.]google[.]com4 mobile[.]twitter[.]com3 www[.]instagram[.]com2 video-weaver[.]lax03[.]hls[.]ttvnw[.]net2 www[.]evernote[.]com2 www[.]amazon[.]com1 www[.]tiktok[.]com1 completion[.]amazon[.]com1 outlook[.]office365[.]com1 slambminerals[.]co[.]zw1 ebay[.]es1 api[.]youla[.]io1 usinfo[.]hvf[.]ru1 uteplenie-05[.]ru1 mirror[.]04fx[.]net1
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile5 %SystemRoot%\SysWOW64\config\systemprofile:.repos5 %SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>5 %TEMP%\<random, matching '[a-z]{4,9}'>.exe5 %APPDATA%\D282E11 %APPDATA%\D282E1\1E80C5.lck1 %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c51
File Hashes 008287c73e9c9e8964d5f615500010e75ac4b737efe8addced3c76f6e91e19f30f42edd76f7309fbf1e26780e1e3e184dfa6d291ef6516ab8ae9c3107082eb3916938ef04245cc85a978529dbf17dbad84d361edb8561b8a42fd9e7f1ec32357176091498be9e921bbda75219f294d79890b02d5a6a43ec57b4df79f1536e7831acf37095f74755c7eeef714919f783616b1f83c316bbee6a934210ede39bfce21f0ce1042da578786da666a47fbf0101147e0a16c2c0fbb2b110eb6e46130a72436911de6028f64f426467d1d1b8cd3b50e3c84fca97ac7a2239ec9a1e394b947a1812f58beda34ca7b20f6ec29af7e933696d7352011ba59facad26496e79d5cb714dd0f231451185cd9b42027a1012b33f7dc74550c25116083405ac3478f61bb445b5986840c291ec769d672ee12eb458c754166a8e8ad3007a188ed40626bdf6ce739aeddd1064d1dac7783d81b18f4416ec3dc421f7cc6dc32c78f03fd76879ab7212540d378168b2564b9f37db4537b50f6dc369c26b647e85c444c57790eeb5febfc4bcc7aa3b14c3dcd81a4fbd00bf727f0c0cd9623e4d3179fad947b62f413d06f80ee52c866aae87586af3c40ff58fabcdc8107a508fcab9a703d7c7ceeedb2701b97482120051287570bb5d67749a285921664f3b17c926b687d879e3b5e6a12fdcd87b61d7b5fc2ec074c8e7b8e6ef92e0bde7c4692ac58d798989e6a13fa14aa8bf6a4c683f09fd69e8b30fcee7a1454fd88a311bc4acd6137a7a195b0d16fa842d7d4aac43142d63c4cabfe46444a85e83aa444fe4f781b56be1e2462735391e9a7a9054c9acbbfec29e464b37e1d932655d46dd0700bb3e3c3212b135d7d55ca971ad91c7f8690e979d8b312e75097527ff081b21f0b8973c83fd9a15592cb220254275dd623a561e7f0cd7cb9083ee2b48c08a399cd32a5cf3ae9f22ff51fed8cf68b9d33fb356211bd1f262b6e9537bbce47829fbe2526d57922015161e3384aa16923df485962f4c2748efc5428abdf2186d92310e889e052d025bda86a537b081d1aeb774af8a278bcea52b1bf8dece5549c9533b5f5f2b4c728867bcc659b1f180783aa3c748f2ee95f0d2f6ed2fdc13869b1b9f0ff
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Bifrost-10003394-0 Indicators of Compromise IOCs collected from dynamic analysis of 36 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\MEDIAPLAYER\HEALTH\{AA317502-AC9B-420F-AF7C-5E2088BA5EEA}9 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKLM 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKCU 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5460C4DF-B266-909E-CB58-E32B79832EB2} Value Name: StubPath 1 <HKCU>\SOFTWARE\((MUTEX)) Value Name: InstalledServer 1 <HKCU>\SOFTWARE\((MUTEX))1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5460C4DF-B266-909E-CB58-E32B79832EB2}1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA FOUNDATION1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA FOUNDATION\NETWORK1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA FOUNDATION\NETWORK\HTTPD1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA FOUNDATION\NETWORK\HTTPD\PROXY1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA\WMSDK\LOCAL1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA\WMSDK\LOCAL\AUTOPROXYCACHE1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA\WMSDK\LOCAL\AUTOPROXYCACHE\LAN1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA\WMSDK\LOCAL\AUTOPROXYCACHE\LAN Value Name: AutodiscoveryFlags 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA\WMSDK\LOCAL\AUTOPROXYCACHE\LAN Value Name: DetectedInterfaceIpCount 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA\WMSDK\LOCAL\AUTOPROXYCACHE\LAN Value Name: LastDetectHighDateTime 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA\WMSDK\LOCAL\AUTOPROXYCACHE\LAN Value Name: LastDetectLowDateTime 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA\WMSDK\LOCAL\AUTOPROXYCACHE\LAN Value Name: LastDetectTime 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA\WMSDK\LOCAL\AUTOPROXYCACHE\LAN Value Name: LastDetectUrl 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA FOUNDATION\NETWORK\ROLLOVER1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA FOUNDATION\NETWORK\ROLLOVER\GENERAL1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA FOUNDATION\NETWORK\ROLLOVER\LATCHSET1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA FOUNDATION\NETWORK\ROLLOVER\GENERAL Value Name: Count 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS MEDIA FOUNDATION\NETWORK\ROLLOVER\GENERAL Value Name: Time 1
Mutexes Occurrences <random, matching [a-zA-Z0-9]{5,9}>15 XTREMEUPDATE1 ((Mutex))1 Global\a393cd01-ffd9-11ed-9660-001517e12f471 Global\0c0f8821-ffd9-11ed-9660-00151716a7e41 Global\2781b741-ffd9-11ed-9660-001517ee3e821 Global\1dbccce1-ffd9-11ed-9660-001517e5ebdf1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 142[.]251[.]40[.]1108 94[.]198[.]224[.]1831
Domain Names contacted by malware. Does not indicate maliciousness Occurrences o-o---preferred---algerietelecom-alg1---v11---lscache8[.]c[.]youtube[.]com7 o-o[.]preferred[.]algerietelecom-alg1[.]v10[.]lscache7[.]c[.]youtube[.]com1 kazanthehacker[.]no-ip[.]biz1
Files and or directories created Occurrences %APPDATA%\addons.dat6 %SystemRoot%\InstallDir1 %SystemRoot%\InstallDir\Server.exe1 %TEMP%\x.html1 %APPDATA%\Microsoft\Windows\((Mutex)).cfg1 %APPDATA%\Microsoft\Windows\((Mutex)).dat1 \TEMP\f4e67cdc9c5c2547833f8a35d3436e51af2934e8d2a3ed280e254bfaf3c25085.exe-up.txt1 \TEMP\08d25f18e27e564f0883159978b50290e7ebd2912d1b05d0b2aa8392a5f5c3ad.exe-up.txt1 \TEMP\a593220da78456dd5469edf080f5fe9dba4ae832f33abe8d47ce69ad68ddf22c.exe-up.txt1 \TEMP\ea64a1c424d6b6fb01662d7fabfdde8e6e1759ce623d400af77519e9f389dad3.exe-up.txt1 \TEMP\fae008550d11d591bd8a205e020d9d0fd48bdc2e581ae7463f0e8698e2a22542.exe-up.txt1
File Hashes 03a486f1e58a32af783feb2273f139d67122266734e907782c5b6c41761329fd05766408d060971c3a733be4c0769c62d7a7f65c482eec3539eb856af2f27fa208d25f18e27e564f0883159978b50290e7ebd2912d1b05d0b2aa8392a5f5c3ad0c9998474a98ff2c888ce06321cd1ca96638605b4e2cd6c5718a81a2f1512b680f32c1e4073454efafe313094bb5d6c9f990e700d69cb4ca7e699a5328791e5d1b013415c69fa449fd92d5f2af6ef028063cafba50edaa348935637c31b863eb2a2fdae3db1da7c63f0f5011a96e641ca6bdf15519c478fbb6201f6434b2ec42457a99913c4786a464eed2c5071df024e929860dd9cbb5067fde5ada1e4c91ac4a4bd82d14d058f9db132ac66bd2595276beb1237413328f04185103ac4a5faf5e92bde9c6e41934843b329f30fa394747a78b0f1bf55fe238b6c5230b3a21ff60e31846bf8abf55a9ec25ba662b8baf80274612050fa6fe99e310155d9efded698383bfc72fd8365db3c5d813a7de3e0382e94b277540611758bf14521c0590739be7ae257e3e0d410ce63b06c12e9b78a8547c3dcc0db51aaf2b08e21d44f876f45f300c257f6b9b675a633a58e6cfa959b45f0d8c4adfc218b944db25e98f7d91952bb27f017806f964f1e5a4e9a60722b28dbaa821e5c3e1164ff63d9a16894a0f93d1b6ae784ea66a94316c9f8eae96f0cba6758dc56d188b1d854e61a889911b1d88e8830368dfcf69598339e1b7b19c3b3639f46beabd4b49020603b58ad02d524a25295aa279cfe2b74163c4691ac7b6f21077c2ae2e214d1df6208a8d097e10fd12d5ac2e845f74129c4b226eb806a250818bc618ccd2c861be6716a1fe7e8686cc160e1d2f5eb2e6a050a1f5f408f33b32653c82f4c62704d4edd2a593220da78456dd5469edf080f5fe9dba4ae832f33abe8d47ce69ad68ddf22caa018e7efbfd40775ce525ac2b04bcf27f2f2218808e0071a84b41584e9ce429ab2d876b1763b356b3ecd6d643092bc8c7dd82d1c0bc84867b6dc0ccf6d6d61bae4856c49aac3fa4e058b4e2392a18e0a5dfe69b82d3a13d1b468d1f8e4c0000b39b5dd08c5d720bb1c8eb7e1a11765b74f51e30c263650782168b0b3d54ab4b
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Virus.Expiro-10003154-0 Indicators of Compromise IOCs collected from dynamic analysis of 17 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32 Value Name: Start 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64 Value Name: Start 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Start 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE Value Name: Start 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE Value Name: Start 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32 Value Name: Start 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\ALG Value Name: Start 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\EHRECVR Value Name: Start 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICROSOFT SHAREPOINT WORKSPACE AUDIT SERVICE Value Name: Start 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSPPSVC Value Name: Start 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64 Value Name: Start 16 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\MEDIA CENTER\SERVICE\VIDEO\TUNERS16 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\MEDIA CENTER\SERVICE\EHPRIVJOB Value Name: DRMInitResult 16 <HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE Value Name: AccumulatedWaitIdleTime 16 <HKLM>\SOFTWARE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\LISTENEDSTATE Value Name: RootstoreDirty 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\STATE Value Name: AccumulatedWaitIdleTime 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\.NETFRAMEWORK\V2.0.50727\NGENSERVICE\LISTENEDSTATE Value Name: RootstoreDirty 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\ALG Value Name: ObjectName 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICROSOFT SHAREPOINT WORKSPACE AUDIT SERVICE Value Name: ObjectName 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\EHRECVR Value Name: ObjectName 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSPPSVC Value Name: ObjectName 16 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\EHSCHED Value Name: Start 12 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\MEDIA CENTER\SERVICE\SCHEDULER12 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\MEDIA CENTER\SERVICE\SCHEDULER Value Name: ServiceFailures 12 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\MEDIA CENTER\SERVICE\SCHEDULER Value Name: ServiceStarted 12
Mutexes Occurrences Global\OfficeSourceEngineMutex16 Global\Media Center Tuner Request16 Global\Multiarch.m0yv-98b68e3c311dcc78-inf16 Global\Multiarch.m0yv-98b68e3c311dcc78493cd690-b16 Global\Multiarch.m0yv-98b68e3c311dcc789ea72c54-b16 http://www.microsoft.com/windowsxp/mediacenter/ehtray.exe/singleinstancemutex12 Global\MCStoreAddStoredType_a1d78cdcc411921ce3b07770aa2a0e0745789b1112 Global\MCStoreCreateTable_a1d78cdcc411921ce3b07770aa2a0e0745789b1112 Global\MCStoreOpen_b4cae1f9a3aead62bebb934ca33cadb730c8d3ed12 Global\MCStoreSyncMem_02004a9f865399b5c2a02973d5e53544ed4ce2ea12 Global\MCStoreSyncMem_5ea381292eeb3ed3e61dc84a3dbd4d7f59767eca12 Global\MCStoreSyncMem_71bdfe29063ac557a4e7b3205ed180408457fcd412 Global\MCStoreSyncMem_7715dc857070a1523dea43f32f1fe67c1ce58e0b12 Global\PVRLibraryLock_a1d78cdcc411921ce3b07770aa2a0e0745789b1112 Global\__?_c:_programdata_microsoft_ehome_mcepg2-0.db12 Global\__?_c:_programdata_microsoft_ehome_mcepg2-0.db:x12 Global\eHome_DbMutex_112 Global\eHome_DbMutex_212 Global\eHome_DbMutex_312 Global\eHome_DbMutex_412 Global\eHome_DbMutex_512 Global\eHome_DbRWMutex_112 Global\eHome_DbRWMutex_212 eed3bd3a-a1ad-4e99-987b-d7cb3fcfa7f0 - S-1-5-185 Global\PVRDiskMonitorLock_a1d78cdcc411921ce3b07770aa2a0e0745789b112
*See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 63[.]251[.]106[.]2516 206[.]191[.]152[.]5816 167[.]99[.]35[.]8816 82[.]112[.]184[.]19715 173[.]231[.]184[.]12210 103[.]224[.]182[.]2519 199[.]59[.]243[.]2239 72[.]5[.]161[.]128 103[.]224[.]182[.]2084 64[.]190[.]63[.]1364 178[.]162[.]217[.]1072 178[.]162[.]203[.]2022 91[.]195[.]240[.]122 35[.]205[.]61[.]672 85[.]17[.]31[.]1221 178[.]162[.]203[.]2261 5[.]79[.]71[.]2251
Domain Names contacted by malware. Does not indicate maliciousness Occurrences cvgrf[.]biz16 npukfztj[.]biz16 przvgke[.]biz16 zlenh[.]biz16 pywolwnvd[.]biz16 knjghuig[.]biz16 ssbzmoy[.]biz16 uhxqin[.]biz15 anpmnmxo[.]biz15 lpuegx[.]biz15 vjaxhpbji[.]biz13 ww25[.]uhxqin[.]biz9 ww25[.]anpmnmxo[.]biz9 ww16[.]uhxqin[.]biz4 ww16[.]anpmnmxo[.]biz4
Files and or directories created Occurrences \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\DW20.EXE16 \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\dwtrig20.exe16 \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\ose.exe16 \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\setup.exe16 %CommonProgramFiles%\Microsoft Shared\OfficeSoftwareProtectionPlatform\OSPPSVC.EXE16 %CommonProgramFiles(x86)%\microsoft shared\Source Engine\OSE.EXE16 %ProgramFiles(x86)%\Microsoft Office\Office14\GROOVE.EXE16 %ProgramFiles(x86)%\Mozilla Maintenance Service\maintenanceservice.exe16 %SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe16 %SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe16 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe16 %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe16 %System32%\alg.exe16 %System32%\dllhost.exe16 %SystemRoot%\ehome\ehrecvr.exe16 %SystemRoot%\ehome\ehsched.exe16 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.log16 %SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngen_service.log16 %SystemRoot%\Registration\{02D4B3F1-FD88-11D1-960D-00805FC79235}.{33EC2C09-9668-4DE7-BCC0-EFC69D7355D7}.crmlog16 %SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\ngen_service.log16 %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngen_service.log16 %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngenservicelock.dat16 %SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\ngenrootstorelock.dat16 %SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\ngenservicelock.dat16 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.lock16
*See JSON for more IOCs
File Hashes 1b9b0bf994336557950714a3501beb9af7d644358872733dd3ab49d1bfc7f7762714633aa8e3b05103ba0dd92c97f535a3174d30cc365b144fd1e76c4bef931f37eb385f36c1f21a36b6bd29cf684cf3537b74c7230f62b784df5441aa57b72b46251ae3625c070d6f262c8fa620bb0a5ee9947730a8d8750342efc33e15d69f543d155d1cf71b6cfcbc1f1de78c843f3abec95a3dce9d519db380795d5893506468fe8ec51dc27a5ebe9b0fd2c0bb8e5e492868b98fcbde8a729297bc03fd8466b3d3d622be554c5dd939b2457c4f9b669a1e82f0bca0d0c1ae89ead8ae7fdc681aeb91e0102d018b765885fa4b3c24462698d4c66c00c49f5e1153be2afdf7763ada5bd0a94469cd5c765cab392a4b443b6cfddebc4cd6352ae151da5fc054807b5a1a240bb2750c90fe76f28c81dba120c7a088a643730937d28bb817fe39834e15242912cffa68dfc1e6acbb6ba9f0951974c80c6d858157472c0edbd1a5a2fd371a2321facf47d75cdfeac2b88076f9eeb401241aff44810ecf8cf6f0b1af65508f8dfad40f084cc222172ffe6d925d45b5dd0b8b3c0a324c127de2453dafad241234b3666b67a6114147579289f9aceb4b69ec269f8bcf5abead167e53c8774e855e434605aca4268812982d2fac3bfda3d90769863d9119ac14e775dee38aa1569670346e76402ade2b423fa9207079b16d58b3b737648c4262c68189f03dd68c60f9e691f3fcd6022b43a99060818eca93eb4eb5c9663e11bb4ca003
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK