Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 2 and June 9. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
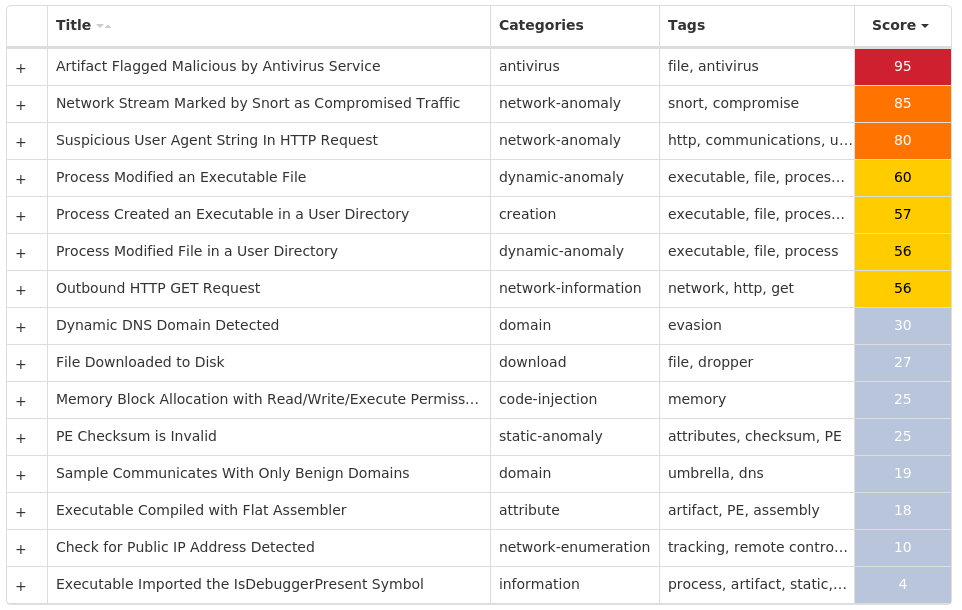
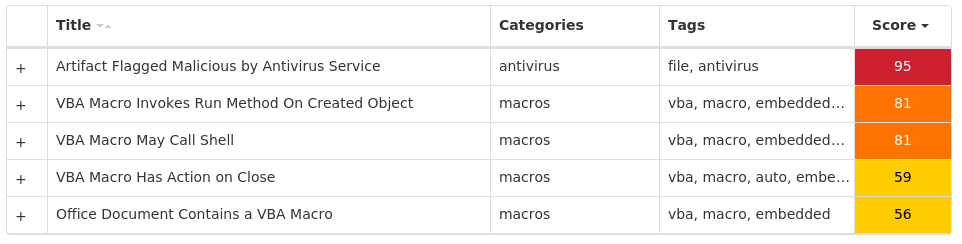
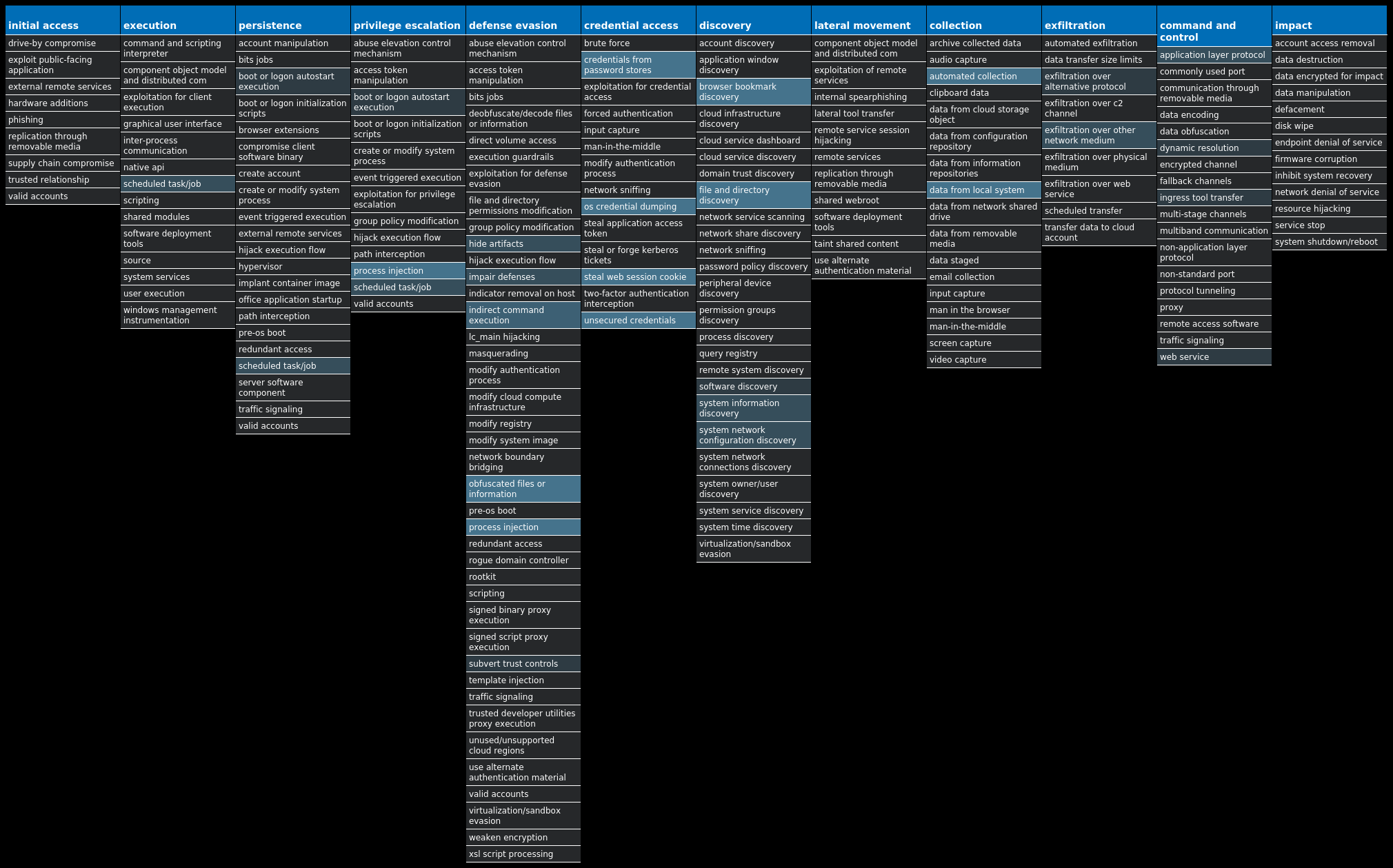
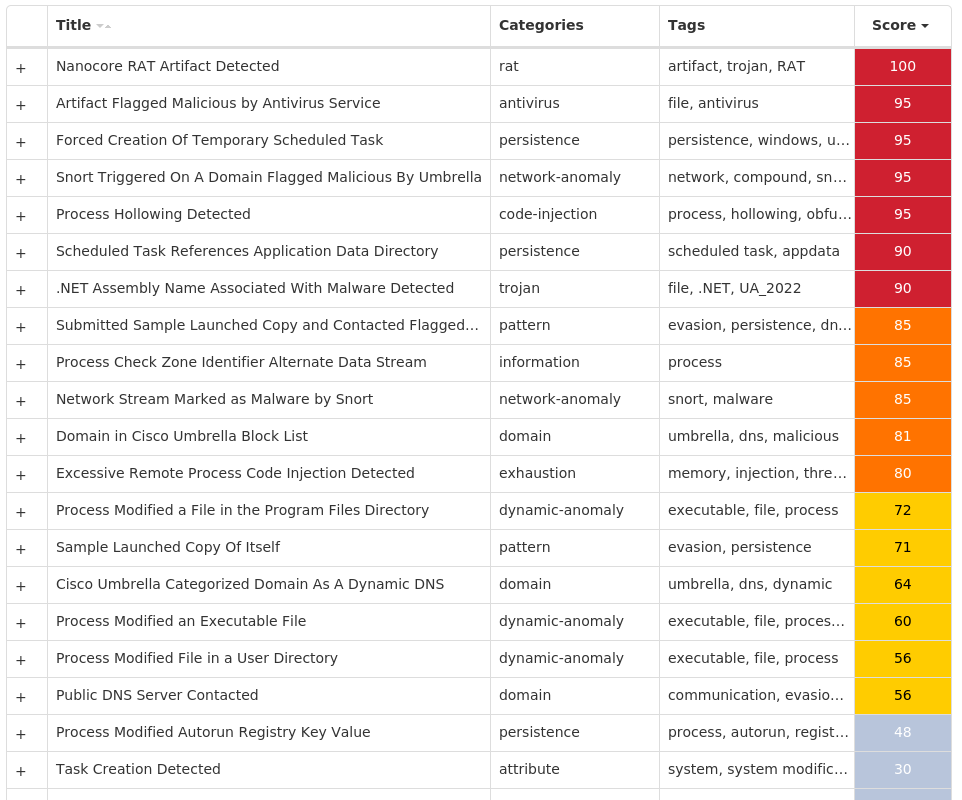
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Virus.Ramnit-10003937-0 Virus Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It can steal browser cookies and attempts to hide from popular anti-virus software. Win.Packed.Zusy-10003901-0 Packed Zusy, also known as TinyBanker or Tinba, is a trojan that uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe." When the user accesses a banking website, it displays a form to trick the user into submitting personal information. Win.Malware.Zbot-10003849-0 Malware Zbot, also known as Zeus, is a trojan that steals information such as banking credentials, using methods like key-logging and form-grabbing. Win.Packed.Upatre-10003658-0 Packed Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware. Doc.Downloader.Valyria-10003621-0 Downloader These variants of Valyria are malicious Microsoft Word documents that contain embedded VBA macros used to distribute other malware. Win.Ransomware.Ryuk-10003991-0 Ransomware Ryuk is ransomware known for targeting large organizations and asking for rather large ransom payments to recover the encrypted files. The infection has been associated with emails that contain malicious attachments that first deliver Emotet, which is used to deliver modular payloads such as Ryuk. Ryuk encrypts a user's files using AES-256 + RSA2048 encryption algorithms. Win.Packed.LokiBot-10003974-0 Packed Lokibot is an information-stealing malware designed to siphon off sensitive information stored on an infected device. It is modular in nature, supporting the ability to steal sensitive information from several popular applications. It is commonly pushed via malicious documents attached to spam emails. Win.Dropper.Nanocore-10003611-0 Dropper Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes. Win.Dropper.Glupteba-10003588-0 Dropper Glupteba is a multi-purpose trojan that is known to use the infected machine to mine cryptocurrency and steals sensitive information like usernames and passwords, spreads over the network using exploits like EternalBlue, and leverages a rootkit component to remain hidden. Glupteba has also been observed using the Bitcoin blockchain to store configuration information.
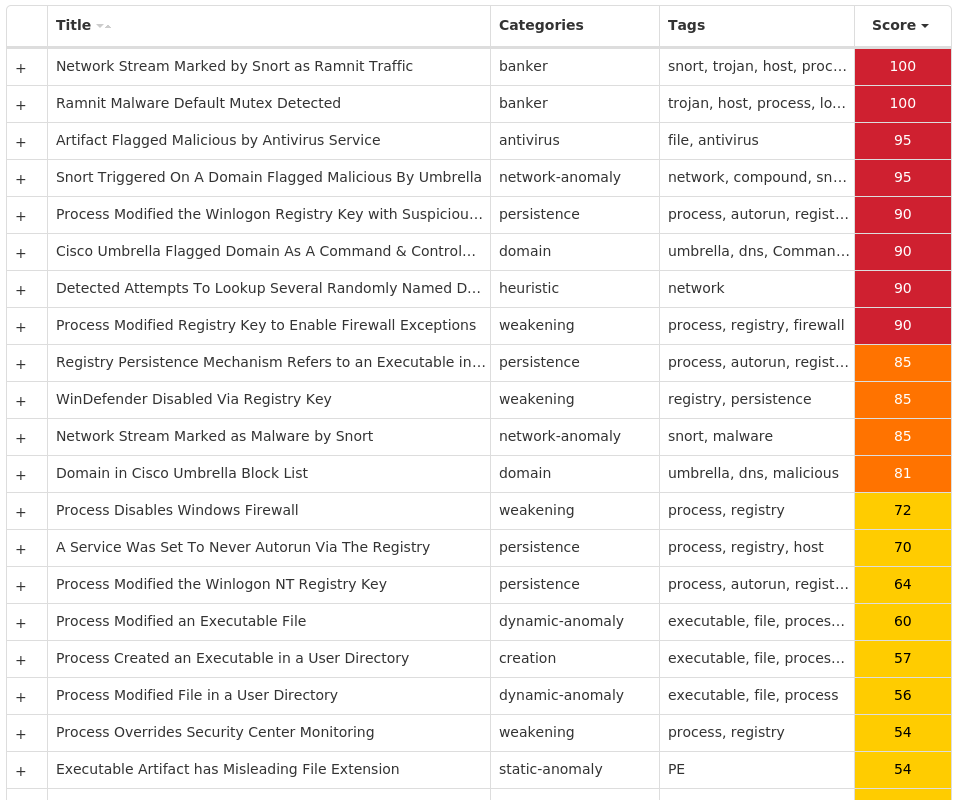
Threat Breakdown Win.Virus.Ramnit-10003937-0 Indicators of Compromise IOCs collected from dynamic analysis of 19 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusOverride 19 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusDisableNotify 19 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallDisableNotify 19 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallOverride 19 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UpdatesDisableNotify 19 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UacDisableNotify 19 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLUA 19 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: EnableFirewall 19 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DoNotAllowExceptions 19 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DisableNotifications 19 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 19 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 19 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\EFS Value Name: Start 19 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC Value Name: Start 19 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION Value Name: jfghdug_ooetvtgk 19 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: JudCsgdy 19 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 19 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Defender 19 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: Userinit 19 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: Userinit 19
Mutexes Occurrences {7930D12C-1D38-EB63-89CF-4C8161B79ED4}19 {79345B6A-421F-2958-EA08-07396ADB9E27}19
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 46[.]165[.]254[.]20118 72[.]26[.]218[.]7018 195[.]201[.]179[.]20718 208[.]100[.]26[.]24518 35[.]205[.]61[.]6718 206[.]191[.]152[.]5818 72[.]251[.]233[.]24518 142[.]250[.]80[.]4618 162[.]249[.]66[.]2118 45[.]79[.]19[.]1964 198[.]58[.]118[.]1674 96[.]126[.]123[.]2443 45[.]33[.]23[.]1833 45[.]33[.]2[.]793 173[.]255[.]194[.]1343 45[.]33[.]20[.]2353 72[.]14[.]185[.]433 45[.]33[.]30[.]1972 72[.]14[.]178[.]1742 45[.]56[.]79[.]231 45[.]33[.]18[.]441
Domain Names contacted by malware. Does not indicate maliciousness Occurrences google[.]com18 testetst[.]ru18 mtsoexdphaqliva[.]com18 uulwwmawqjujuuprpp[.]com18 twuybywnrlqcf[.]com18 wcqqjiixqutt[.]com18 ubgjsqkad[.]com18 iihsmkek[.]com18 tlmmcvqvearpxq[.]com18 flkheyxtcedehipox[.]com18 edirhtuawurxlobk[.]com18 tfjcwlxcjoviuvtr[.]com18
Files and or directories created Occurrences %LOCALAPPDATA%\bolpidti19 %LOCALAPPDATA%\bolpidti\judcsgdy.exe19 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\judcsgdy.exe19 \TEMP\qMFJQ3E19
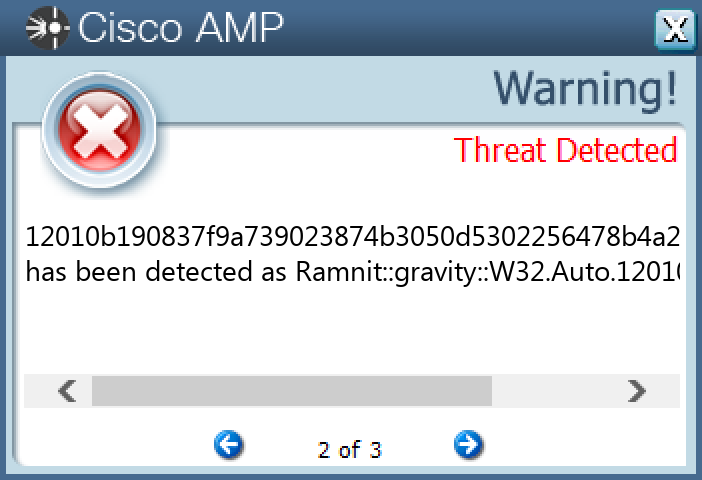
File Hashes 06148818f98f51bcd14a7b92ae2ed10d0bec53e3e3c3f61cd237e481f82c0d320d0a7f29e2670fbe81142948619e4eeafbd7665640f72b7c7c65c7351d4f40180db3b8a863fecf11852063a528c06760a6036bf0b59c3e7098e4d9663f6be9b712010b190837f9a739023874b3050d5302256478b4a2b118ebe6b985a63a3d883868284340c86e65f2123d8c28b12b8cc6bcf3d4ce78a7fe172066dd1aa54a863a3af352a97262fbf28da273ab68b7ce8b20c6684c9af3366629d08306d89c333aa9915ca67ab0a4e2f39abeea140aa6b572a56101401f77c2e71a176e8a343b5a3a5256f59dc95a179b57b2153814492fdfc3236ebe059497785d7d1bc7d5ef5d8da870059a98227317238c0d55fd72e56991df2e7d5000e4d1e8b928ac3d5862b22a8010083fb6892e76e975f65ee3dd19b814fe26388e11d3ae7d9464b6f4735e73cf6f2feb06e0ea685e3470cab216e5e716e055b06e1def285e6d6013c2802ac9bbe5a0aa104f81b94789bf45d1901ac9e9508239fb2497ba118553b9a7818d517ec1eaf19125c90a296cf03b5f24d7a4a0c09ac602f2057d02653b54d0866f4dc906a46ef7c7d66ba04f789ab73addd75f796acb2053ab26ad6808ca87a0e670deda039e728698d0bd77d675bb43b2ba59ad7072df420679702aad5b6faabda214459610e3f99d7010fa6e1aa3c14b516d5931a247497e164061d4ea78ad141e9754ffc131fc78c926b5b939cb0c1da8a2fa7b5c186e3e7b948dfbad59d855760b6d0d9960c9926d4cc54b2db0812262041fc8c63bb164d75a99323fd0f67ea22f1630d61e9f77d154fbe98d67978d36b6e08ac8f898996bfc88334ee5
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Zusy-10003901-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Mutexes Occurrences Global\<random guid>26
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 45[.]15[.]157[.]1479 45[.]15[.]157[.]1317 45[.]15[.]156[.]1705 172[.]67[.]75[.]1722 176[.]123[.]9[.]1422 104[.]26[.]13[.]311 94[.]142[.]138[.]41 5[.]154[.]181[.]541 5[.]154[.]181[.]391
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]ip[.]sb3 guongelasenne[.]shop2
Files and or directories created Occurrences %LOCALAPPDATA%\Yandex13 %LOCALAPPDATA%\Yandex\YaAddon13
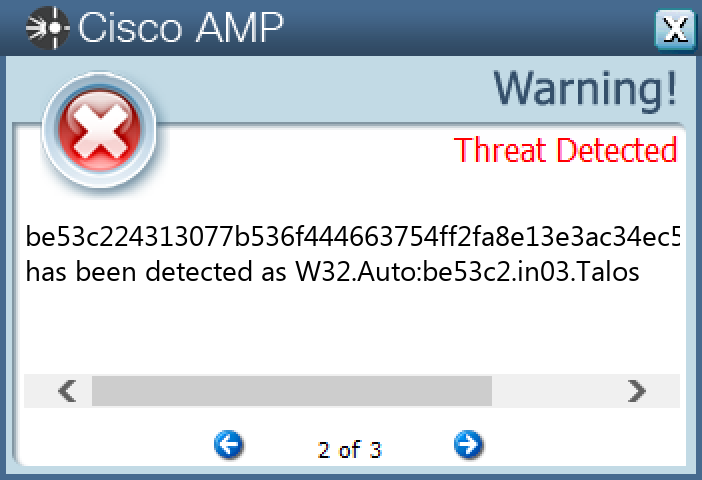
File Hashes 1c71e9931848f48aad664d040cfc4aad4ba16bb51e025260402bfb7c48da384f29a5153d6f84d6f5c377b2c63e8e36f4df259de9f9ecbc4742e0b91f699274722a988d986f530d6005bd904674c86f56ad319073f912c73c8a85eac9e6b83bd84894acaf378a905a66f58363b62f6c15114105ad32eff416ca882eebbf5c4a6f4c8b74d8bda98ef787f8b00a4378fb7eda2562d3effce4dc49b68fc20d5cb9dc5291640da9164fa51f930cce3108dc619f0fba6bf362f4b2e4af4a05798f41366b5f8229b2347cb6a106ad4a531400541265f1081eb9d3e396565f3712b95f416d4819c3cd10adaced6a56b61be1798502f956fb72f6a12dfa3977caacc58c3c74d44b2efd64c3fe0d3efad1c6dcb1e4a6f33cc8ca9aab2c4d6e6a71f853034874ed62fbb15df9fe0add0406f468763fa5eac405442a13e5760b08f4ffc279237665128519d49eb1f5163d25cc4d7e714acc7e54fb9981a34bd072b326373d3076955cf8d50051264cf788f0ac30759a7b649f94cde8026bd0db04bc2cfdb1ba786b41d5cf21945a248441d5399e8f73e4942340ac830f689131a22e99f3830f8c585bd8737ad360171f432d99d9956a81359f19805c036f235114fddc9fe100910022461f1df0c7b35f8989466e56ee45a00619970e8a1283ff8cc2f20d28e6936a8a99ea8442e2c99f59472b079b8d421400a847da07c9c862912a5462588d9dde8babb0deaefcbdb486b211cec17481c0c83b87d2fa525f97faa8be2c2b8b9f07595bd50329ee24499caaac018cd47de494dff4fb70db28eb3791fe027456b1780701caae81b5c1273e811a325fb0be44e8106eb4687d47d3e1bfe151ed2abe53c224313077b536f444663754ff2fa8e13e3ac34ec544cf63d627e8eee8ceca2b4c008f9a7378c5f5cbb18034569e0c092f2aa267f3dc49e442637edca4f2dc7859f512d405c6e2fcdd13a876c5e7177fe8d63f9367ebf6c3bc7b920e2d11dcef4ecf58ba5e9383ed5466f2583b457de189b91302d7e36c3eb114052e678de033d499892e6303ceeeefb7d54e35f263838e68dd75fd5d4f01a4c0b6fe7a84ed96b5ea4373e5b3569ebb2758bf02c2ec6507198ed650435af90199af25c4d8
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Malware.Zbot-10003849-0 Indicators of Compromise IOCs collected from dynamic analysis of 19 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: {2EC645E8-BA31-AD44-55BA-04D54CAC27C8} 5 <HKCU>\Software\Microsoft\<random, matching '[A-Z][a-z]{3,11}'>5 <HKCU>\SOFTWARE\MICROSOFT\HASELA Value Name: 15g98acf 1 <HKCU>\SOFTWARE\MICROSOFT\HASELA Value Name: 2b9j8h79 1 <HKCU>\SOFTWARE\MICROSOFT\MYEV Value Name: 3681g598 1 <HKCU>\SOFTWARE\MICROSOFT\MYEV Value Name: 14086jd2 1 <HKCU>\SOFTWARE\MICROSOFT\HASELA Value Name: 1986jd4h 1 <HKCU>\SOFTWARE\MICROSOFT\MYEV Value Name: 32hej976 1 <HKCU>\SOFTWARE\MICROSOFT\EWJI Value Name: 22fgba7e 1 <HKCU>\SOFTWARE\MICROSOFT\EWJI Value Name: 1a87b40 1 <HKCU>\SOFTWARE\MICROSOFT\EWJI Value Name: 26afjc78 1 <HKCU>\SOFTWARE\MICROSOFT\OWQE Value Name: 1h6222j8 1 <HKCU>\SOFTWARE\MICROSOFT\OWQE Value Name: adcbh3i 1 <HKCU>\SOFTWARE\MICROSOFT\OWQE Value Name: 2130e0ga 1 <HKCU>\SOFTWARE\MICROSOFT\YCRO Value Name: 3617de7j 1 <HKCU>\SOFTWARE\MICROSOFT\YCRO Value Name: 13gj76b9 1 <HKCU>\SOFTWARE\MICROSOFT\YCRO Value Name: 32bdb4gh 1
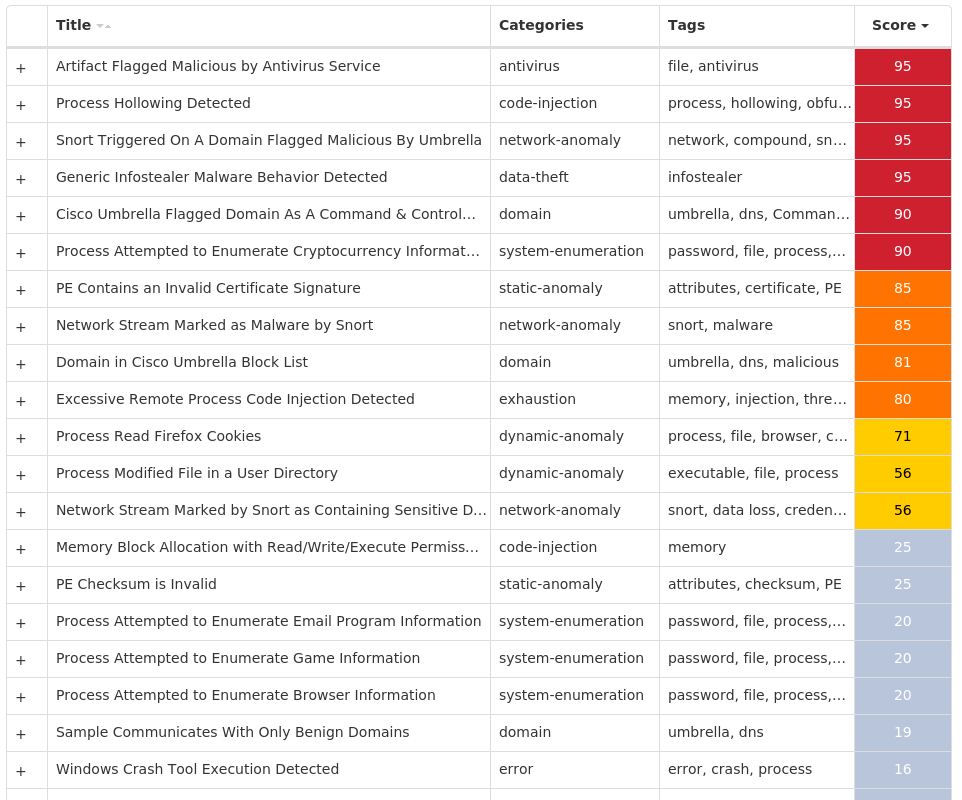
Mutexes Occurrences Global\{C30C6CF2-932B-408E-55BA-04D54CAC27C8}5 Global\{73DE6ED9-9100-F05C-55BA-04D54CAC27C8}5 Global\{A9348FD8-7001-2AB6-55BA-04D54CAC27C8}5 Global\{A9348FDF-7006-2AB6-55BA-04D54CAC27C8}5 Local\{C8D239CA-C613-4B50-55BA-04D54CAC27C8}5 Local\{C8D239CB-C612-4B50-55BA-04D54CAC27C8}5 GLOBAL\{<random GUID>}5 Local\{<random GUID>}5
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 194[.]94[.]127[.]985 99[.]103[.]42[.]495 108[.]83[.]233[.]1905 81[.]136[.]230[.]2355 1[.]186[.]47[.]2445 80[.]252[.]59[.]1425 69[.]36[.]201[.]2445 76[.]106[.]141[.]1135 69[.]132[.]202[.]1475 64[.]219[.]114[.]1145 87[.]5[.]135[.]465 65[.]34[.]235[.]1065 180[.]247[.]151[.]55 190[.]38[.]87[.]2075 142[.]250[.]176[.]1964 190[.]33[.]36[.]1753 161[.]184[.]174[.]653 89[.]228[.]231[.]1083 186[.]47[.]175[.]673 13[.]107[.]21[.]2002 71[.]42[.]56[.]2532 202[.]80[.]43[.]2472 50[.]147[.]96[.]1042 173[.]212[.]188[.]172 142[.]250[.]64[.]681
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]google[.]com5 www[.]bing[.]com4 fuvkkvvsbiozqkkbymrxgpkzvstgt[.]info1 wsojvgontopjhzhwoxxojblpj[.]biz1 rwnfpdydqkvxfahfybislz[.]org1 rskbqhhmgejbtkcelndededuqcyluc[.]org1 vgxtcqlwtnzqcdfefelrjv[.]net1 ukdprmromnucbwxghidulh[.]info1 tejbeagmhtvspfgiqobecekzmfh[.]biz1 wojnylnvgpvhqprjvdatlbropto[.]com1 hqkdkznsctlblbbqxphizxcux[.]ru1 ljmbhvslffmpzzhpnnfaugqxzdtcy[.]ru1 jbeaewovgwolreanrtpnhcufuyl[.]com1 havwofgivkuktomvztibykzvh[.]biz1 aqppxopjwkhqgahekvswlrojem[.]net1 orsgljbmtoabaonyjfgqdafaqk[.]info1 fuxwamlnfoffmxgdvvshmuoucmn[.]org1 xauwfyplbprdmrdswpnxtemde[.]org1 rvbuvwjrjznvnbqsjbxozsw[.]biz1 wojibbavgtkhyhaisgpfsai[.]net1 nzxjxolruskfsgguwkppbptz[.]com1 hqqdxifwoytzdnribypnxkqc[.]com1 xkshwsonwzphufsydaulj[.]ru1 tctxnvnfypqoguqwlwswspbmpdu[.]ru1 fmrggmtctchyllkzhqtiifhqvkib[.]com1
*See JSON for more IOCs
Files and or directories created Occurrences %TEMP%\tmp<random, matching '[0-9a-z]{8}'>.bat5 %APPDATA%\<random, matching '[a-z0-9]{3,7}'>5 %HOMEPATH%\AppData\LocalLow\<random, matching '[a-z]{4,6}.[a-z]{3}'>5 %APPDATA%\<random, matching '[A-Z][a-z]{3,5}\[a-z]{4,6}'>.exe5
File Hashes 0638ccf6ab30044979265a6c249045a807f797f795cd35c6662f1368351704a708de3e8b52a1ae5a70c36e9e0c119d54f1e412667aee3d75384bf23625ee4368179c6808ca96450adc50593587f3657158b95e0b7b18d57a17ca1ecd6467ab421d9b7783b5aa2fc027982ef8147b80ae3fbae04b8beef0e6f10d29884f47dd421fcb36bbf70e6b2048157b80f87b670a7ec3f12a1f05ec09e1a9a3560e6013cd2e6982f483a07e50820ff992014d66785db20a07b720d69d858286aa665703443c3e1b42700ae8b0f8c8fd67296449f5bade0ff6696bad03061a87aa0449e7d978e2e9fea0dce051e9c54712869a7c219f9587040f92d60b9394e3c01b6f4d7e83b94be137857db80c5c5c56bde288660eb57ae78db520af32101b12949f43b3a8f8541231e010480d10deeca483f669b3705eb9f9155a285fc885cfb3c5f065b1df831bcdfebfa7ca46092e3de13d4916bee6ad5880c5fefcf4d22a0f02ad54b6419fc237fab15ffd1f5387040a7d7d2987280f28cea1fdfd5615240a3cf3c4ba141c89b3ce1b23b425999d8362d368765fdb8c827d5b75e47cdd95a41e45ccce4a87af49e6ea05fce91ad4a43c2d9fa68cca54c2560e9c3cd1864c83064caece5a9cf18cb500ad6f6411d5f3d37d1f6a4f73f19132aaa36d26db01fd9d47ecda34f5a540b1a271dde98a8e7ae9a64025ba7e2154b071de38361049346200f1e5f55ad1027078b8492c0d09e98816ee64aecea385d1c9053bdc7bc9a4fc416feab7b0d16f2933cdee9a4ee95b264b31526e0a5e131b7e49060df93b790980a3f6b7f84a31b530e08a419afe6d4b228f4a2271e6e9075f5af20a3985467b6537
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Upatre-10003658-0 Indicators of Compromise IOCs collected from dynamic analysis of 105 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 93[.]185[.]4[.]90104 193[.]122[.]130[.]029 193[.]122[.]6[.]16821 132[.]226[.]247[.]7321 158[.]101[.]44[.]24221 132[.]226[.]8[.]16917 176[.]36[.]251[.]20814 24[.]220[.]92[.]19312 67[.]222[.]197[.]5411 69[.]163[.]81[.]21111 67[.]221[.]195[.]611 76[.]84[.]81[.]12010 67[.]206[.]96[.]689 216[.]254[.]231[.]119 72[.]171[.]9[.]1469 67[.]207[.]229[.]2158 85[.]135[.]104[.]1708 104[.]174[.]123[.]668 24[.]33[.]131[.]1168 84[.]246[.]161[.]478 67[.]222[.]201[.]2228 162[.]153[.]189[.]1438 69[.]8[.]50[.]858 72[.]230[.]82[.]807 64[.]111[.]42[.]647
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences checkip[.]dyndns[.]org105
Files and or directories created Occurrences %TEMP%\guzakbet.exe105
File Hashes 0000184c2bf83493ce58794679be94ee431ab23d45685b7dcfa64c35e2a1fcab014ab5c4620483729398a175ae10660faeb5bf7efd68e882859e81a585870d0201f780ea7234c9196814cb5a7f0f58282966f913ef23121a785169992bb6437c023d61e66aed8846590d7fd1e185d72864fccfcfc2540b259ad023c199b671730242d3e659006128358a7531dc5fdcb71561b2a82512ed21c6283731fc5a771603f1bd10d5036123120fe3fcc0c84ef26d4f6b9e9506b33b0851c78d2deb0f0d06075bf7b39f70f68a36f5ae808c4b70824559e60bd63b241bf7f838ebe6760206df2ad130f7d346c1ad75b341dccf51640acd5aca5126f6476ffad517fbe3aa0858a55586120cb9e7827c540e07078af4ac697f70ab53546a15187126afe5bd09736ce208d4bcbe7f4a18c21749aa4ed23d2724b164aaa289bea73af5d127fa0a8609cb85233a683e73a94544c2152e0f0f83c847e61a77fa787fa7cc7bf6780c6f859f4bd0351d596342a635d6e28ca457da90aac6248b4a55770715adab540cba2641937df34648711938c327a7565095891322b877ee46e94eb8f02075970cdf031f6415c1ab3e3c804a4af403b9b196906c77e1915b4cc82b3ed163886111e1fa7640fb1705c67740344fe19de354efcb0c8e12ffae9dc76b77ff4bdcb012679751aa2c8fbcbe32d17e9e3d61b8274514dc0866645096ab6c9b4797505712ce1cb11a4ae1201fe972607698b42418ebae504b24654e95f65680072bf1dd12ee667b11450888a07f348eb46fa075c0bef95c57654769301e9287a4aa20fa13f610014a486c7e6585ffa2cda3d455bf59d36ed6eb144cbd0c9e7933acb92716d0e440f0d0145804f56fe9651b9ee71252ee53d615030c93f36d959e923f0c17fbf17ee60022aacc492fdc406dd28bff8ac8a89614159bbca0c89acbbd9cd01b5e0b2583fac04db8c84ad0970066cf42233437ce05b11a3752ffbfee2d76b61c48286e5605c2f5f300f6267bd4abb8db72bd1963b0100930d6802b4c8f03631c6af8fab4c4ed60ddbe41d90a6dad4cf442d38bb59bb17884445a8479f7f7fc1d2b14e902557a04a501ccee11c9327d27c1e3247c275406e7c12e5b13e5f08c
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
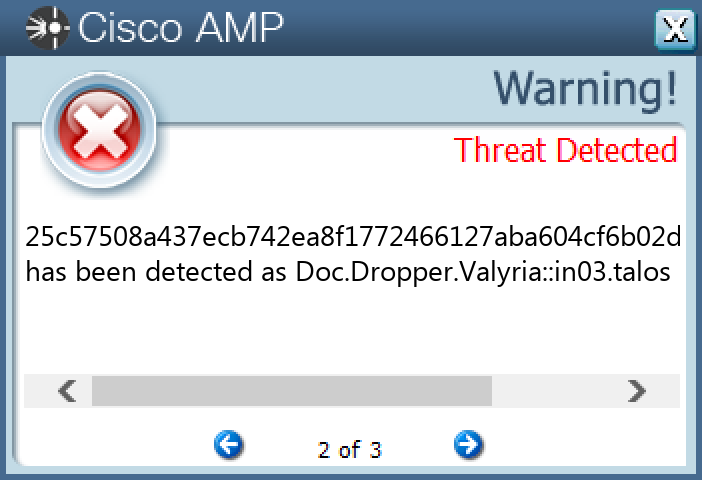
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Doc.Downloader.Valyria-10003621-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\RECOVER Value Name: Name 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\RECOVER Value Name: Path 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\RECOVER Value Name: Extensions 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WRDPRFCTDOS Value Name: Name 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WRDPRFCTDOS Value Name: Path 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WRDPRFCTDOS Value Name: Extensions 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WORDPERFECT6X Value Name: Name 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WORDPERFECT6X Value Name: Path 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WORDPERFECT6X Value Name: Extensions 16 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\STARTPAGE Value Name: StartMenu_Balloon_Time 1 <HKCU>\SOFTWARE\MICROSOFT\OFFICE\14.0\WORD\RESILIENCY\DOCUMENTRECOVERY\8BC02081 <HKCU>\SOFTWARE\MICROSOFT\OFFICE\14.0\WORD\RESILIENCY\DOCUMENTRECOVERY\8BC0208 Value Name: 8BC0208 1
Mutexes Occurrences Local\10MU_ACB10_S-1-5-5-0-6786316 Local\10MU_ACBPIDS_S-1-5-5-0-6786316 Local\WinSpl64To32Mutex_10960_0_300016
Files and or directories created Occurrences %LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRD0000.doc16 %TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp16
File Hashes 07a207d41d5669719706ae493e174c74252cb42b8139c97726edb721942901d7098833c966a76c0b54818a472507c96d274f4ac6c93a428aaa65fb9dfb5984a120657c7da5149507db1c410432cacb916fb109616f74ade4d95caeb2d9dc5dc123b5d97be4f74c16ac98a931c3997d0c6fa3aa5e703db2d2dac224a2e310a84c25c57508a437ecb742ea8f1772466127aba604cf6b02d73937181c35cd5508c634bd0b0976be0df40c197b1933c3080245208df18a9fe66e74fe46631159aa0d3b3a789fe9d6d3bb526243af373bc36ef169e01068f2df9153669cf3bcebbab046a139afae1f3f5a9a8c82311a5453aead22f3d8209c01d5c5c69626c4a56fb55711ce07377f183293ef7e3598f9b7f06d562e4dddb301fbb75718d0fba0930a6b1b0d48bc95a2068a506218a7eba91670b4d462e8e149cf7c9d1b0bdfb7d00c726fb562b5bc3a73709947bd5422d188d2ec5adc0425cfdf189200fae56b85917637d57389c1436e16c045d30151dca6027975112e0c0132ea5ccff2071d81d1938390d91eea8cb1b605b1040aa44bc62368b3dad6b59e495e8bfd462cf74d05b2f975840dc1e961a6f9e63f32bc02ccc88af0bf33b8bffcbda147c96e6651fabdc72b3bc3f55b0166abe6a449727351bed7327624efedc4e76acaeb5f1b7b86cb7aefb789788152ad2a80efdbc50a2527a1cb57cdd37203029b2482d040eeb2
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
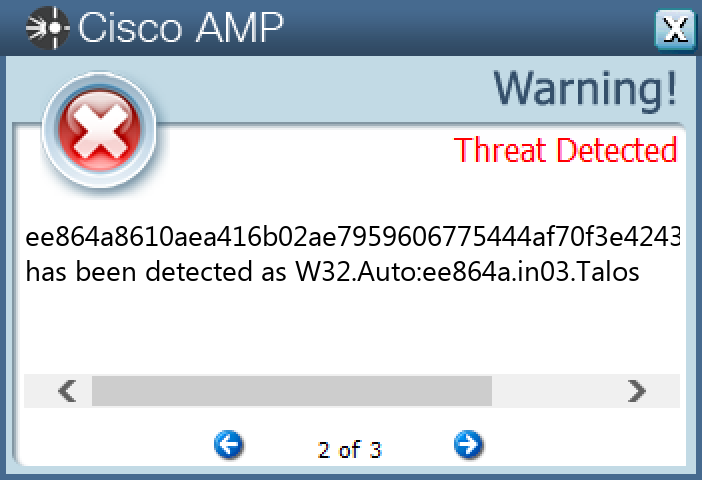
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.Ryuk-10003991-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Mutexes Occurrences rykmutex14
Files and or directories created Occurrences %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\ryuk.exe14 %ProgramData%\Microsoft\Windows\Start Menu\Programs\Startup\ryuk.exe14 %ProgramData%\ryuk.exe14 %System32%\Tasks\RYUK14 %System32%\Tasks\ryk14
File Hashes 0d25bbbeb68847cab4f3805bb8028ca901aa569abb038660c5febfe2ba24ec09557013f396529759dfe68b14246f96d448623fbadc75052a7892a34c60a2758a5a0c6b1b2235159f7b144ad1aee1c084c7914b1e1f294c4cbad7a163df3081cf5b12f08466104a9318ceed9a4ff13f1c1fdbcf734e3b5533dd1e86dad213da1f5fce1d810a5e1c7536496c1b73eff77c9c3d92ac41f86959a1be5349663403ae750bbdf6d68ab7df6e55ea92090328af5d02d4a2c1158cee5ee7190f5c785c1e775745a0c067961761fa0fba5a2bef456413cd9096906d8772d4b9da6bf5e8b68c983fc99712412b33c356e0fbba3e58ca1ca0501537ea11c81cba0198442abebe1b021843326399a29f22897b25162986389905d25102c47a7d7a5853cc315ac293249b528d552bbad69228ffb8b823163f35db8eb79498ab9307f490ea8cf6d1600035b5cead621bc33e7024a4bb9ecf6a9583f23aaabb98e393ccfbac9601da6b32948b1c01dbf1b5322199a935b8bbd8d6514ffc43ff5355f22eeed1f171ee864a8610aea416b02ae7959606775444af70f3e424315edf3463c87e66f4c3f534d1038be3bf9e0909d28ed1acb77825d1424b691a9259f4b7f605e105aaeafe4547b20cf40de0e33ed545949f3e0dfef815b5add252d233177386910643a6
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
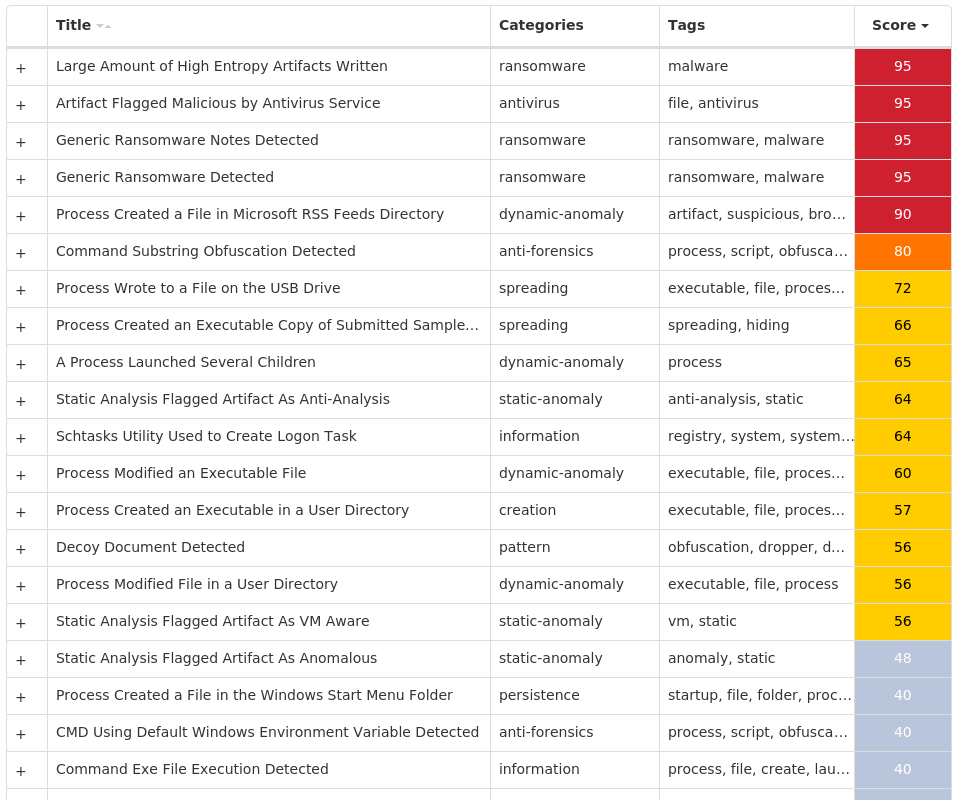
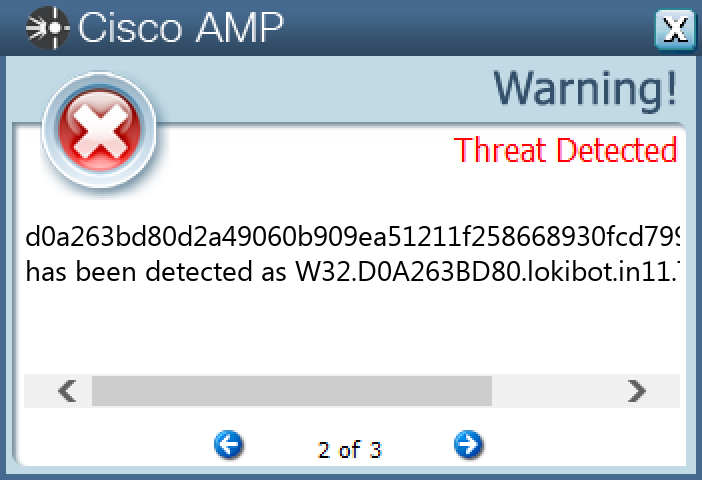
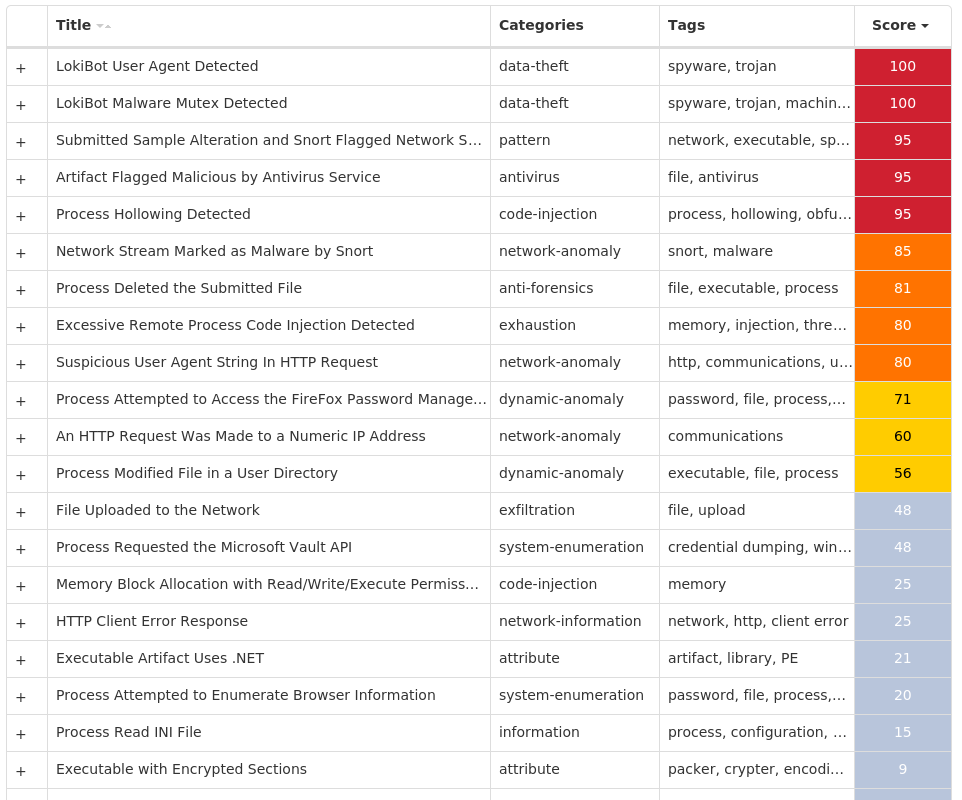
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.LokiBot-10003974-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: efbng 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: aCcAwFD 1
Mutexes Occurrences 3749282D282E1E80C56CAE5A3 jDpDPnOkffrC1 XUFjBW1 fqBVRTwaHZHtrCfkQpOiNQIvCL1 xIumJSsKuOAlYSHwskpJ1 SKfeirAyTRLShRHdbvBVtbvsraX1 aIkjkqIVKPdZEKabRIYzdZ1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 213[.]165[.]67[.]1022 64[.]185[.]227[.]1552 185[.]246[.]220[.]852 193[.]9[.]21[.]1241 193[.]122[.]130[.]01 132[.]226[.]247[.]731 104[.]237[.]62[.]2111 185[.]246[.]220[.]601
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]ipify[.]org3 checkip[.]dyndns[.]org2 smtp[.]ionos[.]es2 mail[.]fiziopet[.]si1
Files and or directories created Occurrences %System32%\Tasks\Updates4 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp4 %APPDATA%\D282E13 %APPDATA%\D282E1\1E80C5.lck3 %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c53 %APPDATA%\zqxqdlu2.oka1 %APPDATA%\zqxqdlu2.oka\Firefox1 %APPDATA%\zqxqdlu2.oka\Firefox\Profiles1 %APPDATA%\zqxqdlu2.oka\Firefox\Profiles\1lcuq8ab.default1 %APPDATA%\zqxqdlu2.oka\Firefox\Profiles\1lcuq8ab.default\cookies.sqlite1 %APPDATA%\sbxsrkxv.nfz1 %APPDATA%\sbxsrkxv.nfz\Firefox1 %APPDATA%\sbxsrkxv.nfz\Firefox\Profiles1 %APPDATA%\sbxsrkxv.nfz\Firefox\Profiles\1lcuq8ab.default1 %APPDATA%\sbxsrkxv.nfz\Firefox\Profiles\1lcuq8ab.default\cookies.sqlite1 %APPDATA%\efbng1 %APPDATA%\efbng\efbng.exe1 %APPDATA%\XwGFCFzeTqkeUe.exe1 %APPDATA%\vhnjipHhvAgPbD.exe1 %System32%\Tasks\Updates\XwGFCFzeTqkeUe1 %System32%\Tasks\Updates\vhnjipHhvAgPbD1 %APPDATA%\wvd2jiis.qhp1 %APPDATA%\wvd2jiis.qhp\Firefox1 %APPDATA%\wvd2jiis.qhp\Firefox\Profiles1 %APPDATA%\wvd2jiis.qhp\Firefox\Profiles\1lcuq8ab.default1
*See JSON for more IOCs
File Hashes 2bed887fca5ae34bb249eb750e20b7542c9209a169745ad2bd9176618042f8ee34efc543781328d0d7161f144577197ea501c83974cc4edc0df012273d758d9a3a826443754835af98b522ef9648a2602e6ef02a6da8138c71ec6780a09fd49946481912ad5fa03359e9e75c73502e78a8c50fb3e809ddb53c10807c4226855f4be6b367cd8fbbd9b5b047a1581775dc0157188fbea49760ce60abff3c4bd79b62ed901f438fc72b696fd6fafaa0d7fa8b1d5a6b96a281844effc456de3ada1f8f4c439db759beb01af1ec4d073406792073028abf8fbca33867396a499ca70a9039395504a883d92a51c3abcc21e65191a1237d58d5cc36aa205a2696a7fd6a961d2c3c698385223f128f5caa0e9a8260cefb0b8a29664f219d64fdcba7941ead641230d3be8895193642d333ed88e1d6e94c209dfcb6c1932cd6a7f324a82fad84a593f03c9a1ee16ea026718cbc46d921acdb940e49c7a78b26abf4dfd3b5b0f38fbfb54d1735e9cb425df68fe633ed49c562176317d36bcfaea1095ef6eac4ef2ace35064a224b5ecaf23baef88a1095190ae3d9639a388e9b21196c8b9cd0a263bd80d2a49060b909ea51211f258668930fcd799b28f8490d784db7c31de8b8b962c35b011fdd5a2154a43d468a8c00efe547f89c79b0d1f4b62677eb49ee63ce54918a139d72523b3c11a62e00a1cc1573c01f4ac7bc4decaca7eed021
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Nanocore-10003611-0 Indicators of Compromise IOCs collected from dynamic analysis of 20 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: AGP Manager 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\TASKBAND Value Name: FavoritesVersion 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: newapp 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\TASKBAND Value Name: FavoritesChanges 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: YLcqPJe 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: MmRKwR 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\TASKBAND Value Name: FavoritesResolve 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\TASKBAND Value Name: Favorites 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: sOFvE 1
Mutexes Occurrences Global\{0d867adb-3500-4c95-b576-70e197aae229}1 SBmdTDfceAO1 dguPijsTgw1 O64O3T231GHA5GE51 urTYJlYpYYNDkAVkNuNKf1 kHCbAyHopHm1 fsmTWPRqOirFDgctmfcTeCy1 AeqWcHrmYllWoFRInLc1 zfBIOx1 tIJFKdFWJdJzxCITKNerlYSxEC1 hmRipQYdtfQNsUPHFxksrc1 gtRQfGqEtQfZ1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 64[.]185[.]227[.]1553 23[.]193[.]194[.]1481 173[.]231[.]16[.]761 104[.]237[.]62[.]2111 162[.]241[.]60[.]791 46[.]105[.]157[.]2411 45[.]12[.]253[.]2421
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]ipify[.]org5 apps[.]identrust[.]com1 mail[.]nereus[.]cl1 ucnano180523[.]ddns[.]net1 mail[.]sgsbauto[.]com1
Files and or directories created Occurrences %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp8 %System32%\Tasks\Updates7 %APPDATA%\Microsoft\Windows\IECompatCache\read_it.txt1 %APPDATA%\Microsoft\Windows\IECompatUACache\read_it.txt1 %APPDATA%\Microsoft\Windows\IEDownloadHistory\read_it.txt1 %APPDATA%\Microsoft\Windows\IETldCache\read_it.txt1 %APPDATA%\Microsoft\Windows\Libraries\read_it.txt1 %APPDATA%\Microsoft\Windows\PrivacIE\read_it.txt1 %APPDATA%\Microsoft\Windows\Recent\read_it.txt1 %APPDATA%\Microsoft\Windows\SendTo\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Accessories\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Administrative Tools\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Maintenance\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\read_it.txt1 %APPDATA%\Microsoft\Windows\Start Menu\read_it.txt1 %APPDATA%\Microsoft\Windows\Themes\read_it.txt1 %APPDATA%\Mozilla\Firefox\Profiles\<profile ID>.default\bookmarkbackups\read_it.txt1 %APPDATA%\Mozilla\Firefox\Profiles\<profile ID>.default\read_it.txt1 %APPDATA%\Mozilla\Firefox\Profiles\<profile ID>.default\webapps\read_it.txt1 %APPDATA%\Mozilla\Firefox\read_it.txt1 %PUBLIC%\Documents\read_it.txt1 %PUBLIC%\Music\Sample Music\read_it.txt1
*See JSON for more IOCs
File Hashes 10090f0b186fb4818b017583c10e21e56ac1a9365020211c619bfc652fab01fb1d1639113b0f01d2044ab2b41b3198a73497245faba4364ae7ea10a0ef39b2671f96eaeda59db9e5803a11f4d045b309aed1e4d63e9952af0491b69edbf435072548dd5666787e050a7d3b96f5afadfd255858fae037a49b7ee7a91ecfbe916727618a1f5fcade2d1b13452dc9e463b295273d115483928e3a671cb8e7a8009334d66474f8157ba70f6de429b8e624cd05a5512c46daf4f9ccd8c6adad5baece3541875e5b62e84130450e229c73132431f93277343cf5214b65846d6000a7b93625699aceef8218cece58914659f6ba003e6f26ad033645ed738b4972050aa53b308d520b3707fed24d11275ec37f85bb4543d0098ef6c7ec965837a5a55dca7e407cf9ad8a6c49b22e15151b5fd82bf6f0f6361c5e3f3abe9b76af8bf68f7e8c9b30a3a8e903fdaa354943efe56e15a10ccc7515c5d7bee8b7ee624f5b22119748fc497d427eb41191ea495d907cd5d2dd9455ed20bf08df947bdb15d84baf9cd47c4593254f37eb5bef6b0d887f7132ce6d9678af33799da736d6073382faae6389876208f0c72afd8dfb44720bb2b94e31f9f8cf446c49c55748c912b44db13a9b8c3312ce8b485d1ddbc9a4c840a08e94793b109f2e7aef32b46fb999e3b7839de29a4736fb565b36d5c4aeea0eea28c8384ae8249a1bce267ec75f4196c4c96c2c76d0f6caa554e1bda74e44ba7fab6a678200cfc40189a7f489af5d23e0b1008f8c4231c9e35552a08a4a708e8bd978f72f7b8b9991f6e7926d6fbaa7e5950c07075986a0e853f4e919e1c39f0e64a878ff97143a1d49ea5a4eb186dfefca8f75ee68a472ea90763b970f83c9285c1178064f8174be4916e7da9ca740
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Glupteba-10003588-0 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\A1890984 Value Name: PatchTime 10 <HKCU>\SOFTWARE\MICROSOFT\A1890984 Value Name: PGDSE 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: ErrorControl 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: ImagePath 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: DisplayName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: WOW64 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXWDDM Value Name: ObjectName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: Type 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: Start 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: ErrorControl 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: ImagePath 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: DisplayName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: WOW64 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXSF Value Name: ObjectName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: Type 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: Start 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ErrorControl 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ImagePath 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: DisplayName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: WOW64 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXMOUSE Value Name: ObjectName 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: Type 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: Start 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: ErrorControl 10 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VBOXGUEST Value Name: ImagePath 10
Mutexes Occurrences Global\SetupLog10 Global\WdsSetupLogInit10 Global\h48yorbq6rm87zot10 Global\xmrigMUTEX3133710 WininetConnectionMutex10 Global\qtxp9g8w10 Global\kn29r6c61 Global\473ggh6j1 Global\wpewcqppg8z44x891 Global\IV71LG3P1 Global\986spw6e1 Global\ag7xpe521 Global\wpsSerMutex51
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 204[.]79[.]197[.]21910 20[.]209[.]34[.]3610 162[.]159[.]133[.]2336 20[.]150[.]70[.]366 142[.]250[.]15[.]1275 172[.]67[.]186[.]1135 185[.]82[.]216[.]484 162[.]159[.]134[.]2333 81[.]3[.]27[.]443 74[.]125[.]128[.]1273 185[.]82[.]216[.]503 20[.]150[.]79[.]683 104[.]21[.]1[.]43 162[.]159[.]130[.]2331 162[.]159[.]135[.]2331 108[.]177[.]102[.]1271 142[.]250[.]112[.]1271 172[.]253[.]120[.]1271 185[.]82[.]216[.]641 20[.]150[.]38[.]2281
Domain Names contacted by malware. Does not indicate maliciousness Occurrences msdl[.]microsoft[.]com10 vsblobprodscussu5shard35[.]blob[.]core[.]windows[.]net10 vsblobprodscussu5shard60[.]blob[.]core[.]windows[.]net10 cdn[.]discordapp[.]com10 fastprivate[.]me8 stun1[.]l[.]google[.]com5 stun[.]ipfire[.]org3 stun4[.]l[.]google[.]com3 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]mastiakele[.]ae[.]org3 stun[.]l[.]google[.]com1 stun[.]stunprotocol[.]org1 stun2[.]l[.]google[.]com1 stun3[.]l[.]google[.]com1 server3[.]mastiakele[.]icu1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]mastiakele[.]icu1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]\xd0\xbe\xd0\xba\xd1\x80\xd1\x84[.]\xd1\x80\xd1\x841 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]zaoshanghaoz[.]net1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]mastiakele[.]cyou1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]cdneurop[.]cloud1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]zaoshanghao[.]su1 e93c35a1-5b7c-447e-bcec-65b84e83dd99[.]uuid[.]zaoshang[.]ru1 server4[.]zaoshanghaoz[.]net1 server6[.]zaoshang[.]ru1 server14[.]mastiakele[.]cyou1 server1[.]xn--j1ahhq[.]xn--p1ai1
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\Logs\CBS\CBS.log10 %SystemRoot%\rss10 %SystemRoot%\rss\csrss.exe10 %TEMP%\csrss10 %TEMP%\csrss\dsefix.exe10 %TEMP%\csrss\patch.exe10 %System32%\drivers\Winmon.sys10 %System32%\drivers\WinmonFS.sys10 %System32%\drivers\WinmonProcessMonitor.sys10 %TEMP%\Symbols10 %TEMP%\Symbols\ntkrnlmp.pdb10 %TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE0210 %TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE02\download.error10 %TEMP%\Symbols\pingme.txt10 %TEMP%\Symbols\winload_prod.pdb10 %TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E36110 %TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E361\download.error10 %TEMP%\dbghelp.dll10 %TEMP%\ntkrnlmp.exe10 %TEMP%\osloader.exe10 %TEMP%\symsrv.dll10 %TEMP%\csrss\DBG0.tmp10 %System32%\Tasks\csrss10 %TEMP%\csrss\injector10 %TEMP%\csrss\injector\NtQuerySystemInformationHook.dll10
*See JSON for more IOCs
File Hashes 22212563c82d627560b8a141299031992fde210f22c6be2471d3497bf8cff13b57feb1fe02b13382d369b5626e872a6159ff6dea32bad5a6d7ce6b6f6a93016d9c005e337df63510b6a2a4758df8d4840b6b1ad35ee9eba3bfcdde9cd1fab858c79398d04526ad67bb70628850a35678abcdb7772c11d7539354750dd9d7d36ecbb12735307be5876ab96badb940f8e5870542005c6f5220e968d41e7d84d835cdc9e61ff13c55f8a332ccfe2a1e6d2b2cf356a6954f6d555e4edf91f5a56db9d349d2bfed8f0eaa962d8adcc5e47c9ec234a8acc9ffbfcbfdbe547711fa43eddaf42e9987a8e7d8c7223a38a8083d8588278673653fbbbc3612ef675c269292f7ae491824c410240f87ba1cffa233cfb761bc2c856e97785685dae707110c68fcf0cd38f5e888254400b44cfe246b76588c2fcdd89c4e4d38b33d7c099ff83c
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK