Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 07 and June 14. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
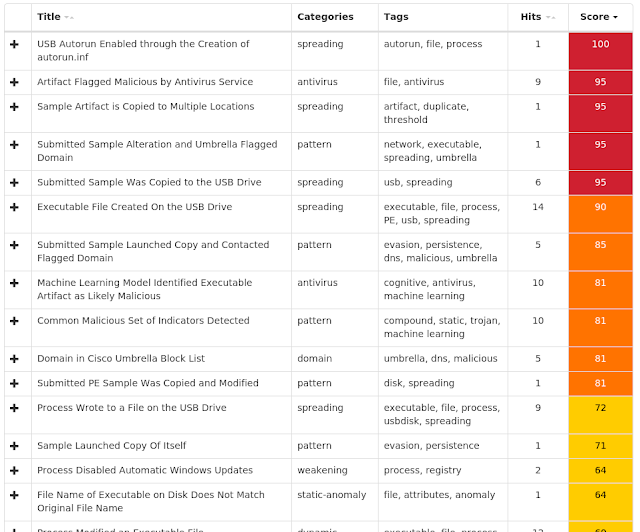
Win.Trojan.Gh0stRAT-6993126-0 Win.Worm.Vobfus-6992861-0 Win.Dropper.Nymaim-6992731-0 PUA.Win.Adware.Qjwmonkey-6992589-0 Win.Packed.NjRAT-6992540-1 Win.Malware.Tofsee-6992280-0 Win.Malware.Yobrowser-6992453-0 Threats Win.Trojan.Gh0stRAT-6993126-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\Software\Microsoft\Windows Script Host\Settings
26
Mutexes Occurrences guduyinan.gnway.net
6
127.0.0.1
2
soiufnrfjowieursmpwoeirfujaiurvnapoai39w45
2
y927.f3322.org
2
ddos-cc.vicp.cc
2
192.168.1.100
2
linchen1.3322.org
2
\BaseNamedObjects\linchen1.3322.org
2
119.98.51.129
1
115.28.32.138
1
203.156.199.11
1
q727446006.gicp.net
1
zy520.f3322.org
1
169.254.22.15
1
118.244.153.46
1
121.199.6.242
1
192.168.1.68
1
850967012.f3322.org
1
169.254.25.100
1
a678157.oicp.net
1
192.168.0.13
1
192.168.0.101
1
cfhx.f3322.org
1
xueyang22.gicp.net
1
\BaseNamedObjects\www.touzi1616.com
1
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 118[.]5[.]49[.]6
2
197[.]4[.]4[.]12
2
115[.]28[.]40[.]12
2
49[.]2[.]123[.]56
2
118[.]244[.]185[.]113
2
116[.]255[.]131[.]145
2
174[.]128[.]255[.]245
1
189[.]163[.]17[.]5
1
54[.]76[.]135[.]1
1
188[.]5[.]4[.]96
1
61[.]142[.]176[.]23
1
27[.]9[.]199[.]217
1
110[.]251[.]189[.]65
1
114[.]239[.]19[.]101
1
222[.]186[.]27[.]216
1
115[.]28[.]44[.]116
1
123[.]131[.]15[.]109
1
120[.]9[.]228[.]6
1
119[.]98[.]51[.]129
1
101[.]16[.]198[.]98
1
203[.]156[.]199[.]11
1
115[.]28[.]32[.]138
1
169[.]254[.]22[.]15
1
121[.]199[.]6[.]242
1
118[.]244[.]153[.]46
1
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences guduyinan[.]gnway[.]net
5
y927[.]f3322[.]org
2
ddos-cc[.]vicp[.]cc
2
linchen1[.]3322[.]org
2
xm974192128[.]3322[.]org
1
guduyinan[.]gnway[.]com
1
278267882[.]f3322[.]org
1
a3328657[.]f3322[.]org
1
www[.]touzi1616[.]com
1
jie0109[.]hackxd[.]net
1
zy520[.]f3322[.]org
1
q727446006[.]gicp[.]net
1
850967012[.]f3322[.]org
1
a678157[.]oicp[.]net
1
cfhx[.]f3322[.]org
1
xueyang22[.]gicp[.]net
1
Files and or directories created Occurrences %TEMP%\jnbxmapdsg.vbs
1
%TEMP%\rlzocrfujx.vbs
1
%TEMP%\bvjkzncqf.vbs
1
%TEMP%\mxoejtdhe.vbs
1
%TEMP%\ofcspybli.vbs
1
%TEMP%\imopeshvj.vbs
1
%TEMP%\paybqnqnd.vbs
1
%TEMP%\ntvxzbqf.vbs
1
%TEMP%\rvxmapdsgv.vbs
1
%TEMP%\dkaqshjynd.vbs
1
%TEMP%\vbdsgvjy.vbs
1
%TEMP%\noqftiwlzo.vbs
1
%TEMP%\ovxncegixm.vbs
1
%TEMP%\qhxurnkcs.vbs
1
%TEMP%\eyaodrgujx.vbs
1
%TEMP%\zyvhdvlis.vbs
1
%TEMP%\zdrshixlao.vbs
1
%TEMP%\waoqethv.vbs
1
%TEMP%\ulabqeth.vbs
1
%TEMP%\othjxmapd.vbs
1
%TEMP%\zdeguvky.vbs
1
%TEMP%\gzgjxmoqeg.vbs
1
%TEMP%\fqwzqhkh.vbs
1
%TEMP%\ulabqrguix.vbs
1
%TEMP%\vrfxlaods.vbs
1
See JSON for more IOCs
File Hashes
0477c2b9ba7eecc8b0827400576860257e62a306a3e0c310eb84c537ec47e01813287e727a2be4b6a3533e768b4babfd9191ec65002abcdf77c43e69278963be1d7633311c1f671c60422a4d6723aa10a37e833e2d5df732f3988b3e379b2ee92a38fbbcef4bc83582ccd98c9bf96ff29e4c915d90802ec799420420f2cad6e62b19de056a388d0ee3672be895f4e446c42053034c68675585dd3fb54b8d1eb73821a10495fb4759fbab1ef7868eeb1e207ea6bf4211370f072b0215a14b46c83ae58dca3ce80c3ed4b65f610eee921dbeb3343619caace78c6afe21ec237f083d54f0fbd50f0b91f635a9ecc89ef8cb58c021bb60326b5fa2db75989d1bff5a3fdd3b5333f7e526e80599add12fdeef663c59ad79ef4e71491204303837773047c349433e77aefb18ea384f6ab4759f7bd49466f7a747255d19d4648fecc76249752684078dfa74cd25adbbdc9bbf7a98e6f96f5355cd52b8b77738506673e74e5a282c7230242d090844875c9f5c432dc2c4bad3ba13fa2a7df86843785f7553e08241abdfe3f13d6aa875642638d1badc6ec59cdb9757fe0fd598dc73692757fc8d1737521cb0af37fcf70079603dc0eb5da1b3bbef9bad334dfe791760685ba20f4aaf94b4f418501ae977d1f6cf947accf8134c3b9487b42cdd65ef715b5fab1a54d1338b2cb906aae3b2f5292d47445aae2af383c2a0e99b4ccf86326260f6548844d59e59dc90a12fcb97396793c20687947a6eb5cc543debecf607d161caab6c70480cd6db4f33234cfc86467bff26c2e19b804211be8c822218a940623fbdc46be1a797f743894e3e1cc003a29692d6fb9b3246de80282207d99b9c63746003a0c8fcdf11f9367ca5102c8413ee5e2cd298079de5a3ab0ba5493ea766b770d0d2e02739e0495d30f9f56c717989eec3f1da96c7ffa01b05deffeb3768d644144b33f4766a3e11a33c471cf877d5801e1833d1d1813d4a06125ff2a96a820f70fc59abd8d0b5202de65a9fc51312d18322e55b24d1f63a2339ff13d36cb616c3229fd37e2615de709496215cc9138436b16eab265e9feae9d81cfac26ed77af0d3929a62256c7aac5068ff7ca337460cb813863d7c528e95f503cc59See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Worm.Vobfus-6992861-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WindowsUpdate
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
Value Name: ShowSuperHidden
25
<HKLM>\SOFTWARE\WOW6432NODE\Policies
25
<HKLM>\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\WindowsUpdate\AU
25
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU
25
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU
Value Name: NoAutoUpdate
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: jauxec
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: qiusooj
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: mokiy
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: wiiorit
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: kuivuo
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: viezus
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: fonef
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: znxaaq
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: reiiraj
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: wauul
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: wlcug
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: wzzuf
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: laociek
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: tioila
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: tstoj
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: yeeuqov
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: vyjuos
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: zeuub
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: teozuim
1
Mutexes Occurrences \BaseNamedObjects\A
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 216[.]218[.]206[.]69
1
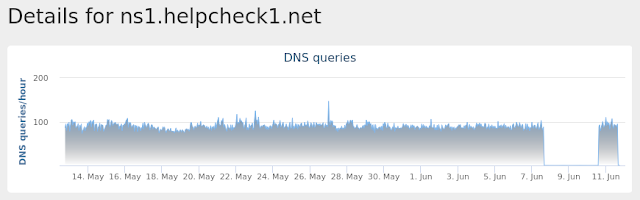
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ns1[.]helpchecks[.]com
25
ns1[.]helpchecks[.]info
25
ns1[.]helpchecks[.]at
25
ns1[.]helpchecks[.]eu
25
ns1[.]helpchecks[.]by
25
ns1[.]helpcheck1[.]org
25
ns1[.]helpcheck1[.]com
25
ns1[.]helpcheck1[.]net
25
Files and or directories created Occurrences \??\E:\autorun.inf
25
\autorun.inf
25
\??\E:\System Volume Information.exe
25
\System Volume Information.exe
25
\$RECYCLE.BIN.exe
25
\??\E:\$RECYCLE.BIN.exe
25
\Secret.exe
25
\??\E:\Passwords.exe
25
\??\E:\Porn.exe
25
\??\E:\Secret.exe
25
\??\E:\x.mpeg
25
\Passwords.exe
25
\Porn.exe
25
\Sexy.exe
25
%HOMEPATH%\Passwords.exe
25
%HOMEPATH%\Porn.exe
25
%HOMEPATH%\Secret.exe
25
%HOMEPATH%\Sexy.exe
25
\??\E:\Sexy.exe
24
%HOMEPATH%\Passwords.exe (copy)
24
%HOMEPATH%\Porn.exe (copy)
24
%HOMEPATH%\RCX1.tmp
24
%HOMEPATH%\RCX2.tmp
24
%HOMEPATH%\RCX3.tmp
24
%HOMEPATH%\RCX4.tmp
24
See JSON for more IOCs
File Hashes
03f2507d1db297b7176fddce8540639e2a8986045af7d4cf27b09a424629a08d181896288ffa6cfea0d847eda1cbce7462fbdfbf6536c6b6d874155f8d23058c366c47a2774078e135f48b03f4facbbba80aa4e294d523f0112d1cf001a93e4a59570b2c73227359544e6c7fde4ba2368170ca48482cdb530de097bb833c177d5a8e8c501cc8864d928beddb8837e0ce70f272a9a6ae13d175dfcbe52d2f3d7e5b4ebc908f6cff3ad1acc262790b3b7ad1e2e65031c7b0f8c55f700ae499f40d5c314363a05429b3a76149ed8a0ab9b9342b69d76794ba9d02e3ab09092ff4ad5f06f5540689bd9346ae76995c25e8efd60d10c22ec9f6723cd6467dabd0b78e60398eff74f6a02cd6dad118d7dc028102b56b20dc6ff7bc0c383b6accdac8e960b898046d99e11912349e895685616d5c59a1d0e6d05fa23fdb654a96c6793162070e7ac4e86195d915ffecd132823e178fb7eaad331fea65926fa2bb80f23b6b63b301a133703b5a6fe3c99c4e2c5a421490daf2a26682a83b95b1eaecb18671999972c8bd0259bab9d76a6e2d9525a141ad7ba151d0b8bf77876b6d6660c77271cb745dcca0d0bb516b7ff4cd69d2c5c261df33e48091890450ca789ae081753c11420e4a06bcb790a51918923c564c6da62c46d923eeb3541e342667a45375a188c634a0c857220ee7c6ad848293ec08d1d8a9f6027f39a02194665edffe7da2c1a73cfa87b1a66d4c0bbe2b1b18ae7540e3ae4de407092fe5f56a44d77280107ca033df25818e9bb64aed5f088c98b4c75d8a3ed3d3a47bb0f2660a2b2d8b76268bc5255134ff460ee3356797657f98f8a0cc6fef98d0e173e367b6734b92944feb88a896a922c9a88fef2683e864b931fd919c4405eeab4ed6cc2a7e02a3b82b5badf315c723973a8e8d8441351a6aea76541d888bdf1db29fd4b3721bae5a2a2a0cd106146aa40390596bba6c72fa7d8c75ab237b3cbb040946fcac19afb4401b564b6330f107b4a8d95e7d28429957929140a84ee99f01eae3fc5619b3f564ef2e4550601f2728da6eec584fadcb7b5060a0df91ed2cbf4e306c5189c80909dfb38fc5646008338b31bf576275d59c5880403adc8e5bb072eec9ce1bSee JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
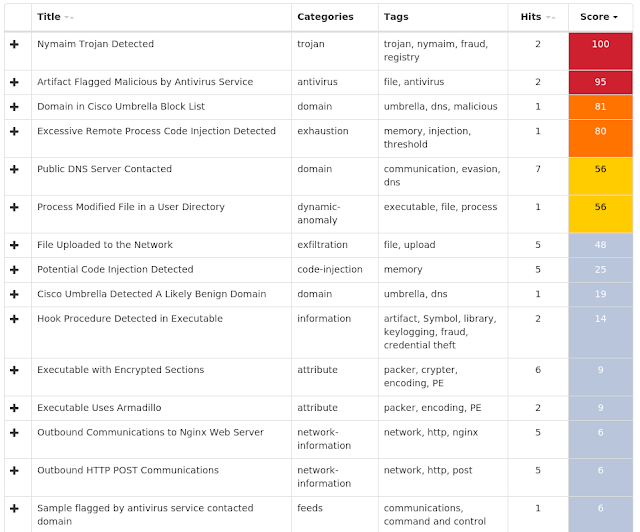
Win.Dropper.Nymaim-6992731-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\Software\Microsoft\GOCFK
24
<HKCU>\SOFTWARE\MICROSOFT\GOCFK
Value Name: mbijg
24
Mutexes Occurrences Local\{369514D7-C789-5986-2D19-AB81D1DD3BA1}
24
Local\{D0BDC0D1-57A4-C2CF-6C93-0085B58FFA2A}
24
Local\{F04311D2-A565-19AE-AB73-281BA7FE97B5}
24
Local\{F6F578C7-92FE-B7B1-40CF-049F3710A368}
24
Local\{306BA354-8414-ABA3-77E9-7A7F347C71F4}
24
Local\{F58B5142-BC49-9662-B172-EA3D10CAA47A}
24
Local\{C170B740-57D9-9B0B-7A4E-7D6ABFCDE15D}
24
Local\{764A5E5B-9D8B-4E3E-3AE5-6BA089B04B34}
24
Local\{D6E0445C-66CF-7E18-EE4D-5700342376D0}
24
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 66[.]220[.]23[.]114
24
64[.]71[.]188[.]178
18
184[.]105[.]76[.]250
18
Domain Names contacted by malware. Does not indicate maliciousness Occurrences jexzc[.]in
24
nenpzs[.]com
23
Files and or directories created Occurrences %ProgramData%\ph
24
%ProgramData%\ph\fktiipx.ftf
24
%TEMP%\gocf.ksv
24
%TEMP%\fro.dfx
23
\Documents and Settings\All Users\pxs\pil.ohu
23
%LOCALAPPDATA%\giy4vh3
5
%APPDATA%\io77x
5
%LOCALAPPDATA%\av1165d
5
%APPDATA%\tv2
5
%ProgramData%\0c7
4
%LOCALAPPDATA%\g816
4
%APPDATA%\p3f
4
%LOCALAPPDATA%\r4v2rp
4
%APPDATA%\3w7
4
%ProgramData%\3e9sq
3
%ProgramData%\qi39
3
%LOCALAPPDATA%\yp870bk
3
%ProgramData%\4b8s2
3
%ProgramData%\q8216p
3
%ProgramData%\94z
2
%ProgramData%\igzk4
2
%LOCALAPPDATA%\ycq1ac
2
%APPDATA%\867j
2
%ProgramData%\9d0g9
2
%ProgramData%\0186d9m
2
See JSON for more IOCs
File Hashes
08beb94545dabf135ef630b432f00fc603f3797328b5a9681d9d1a80412381470be51b6a0e11b6d807c4e6d2eea49b0c9e60c23babbb48ff17c27ee2e2050eef0fee18d7562b359c642e4a953d08251b36c3971f8fc9dbfce46af98fe26f04e8160fb874c1e78de9cb2e7d6a829e5f1e40aba2edae9de7a274a9639b80b6df9d17b5939fc77e2acb9a76c9baa6c4de01822ef4633da4732a49c4cd26f2ff024c1bef5f7889b5b8528bd9f20d6218dd4faa6ff70ad60cfd182e80374045ff9faf281bae2b93ae03725217deac68fd1f513d0a0267dda486e4d2d51f92044c8fca41d57f15b7c1ffd1c4bc5af862da97963405eace4c67574d68fcd39eb4dbe6c044b688082d3305d8e0d29bf7d6d78b60078592f1bda83a90ec6d227823d0e2974cde92c748f5aa5912a83d075dae2241de2496d4f4cf8e69a04a65c2080ff0b8507340f713f0c6f4172253b20bab21bdc6dbdd7ad4866d037894acdf167c60dc50a3f7c98b739d33ff4ba7b3ef38e553a42d7b47bc8b34f2d877055da9eaa1e9514affb7cd921abb88040abc8beb7af9139488da9f625dfb8647fdab665c38c55bf35c74cfc5908e266e3d59615a16b30eb9b6de68759fe346257b420edf674867989a565971fbe6f02c909b0696edc0de6ec1234129c4df4455a1f63a70218969f167f13f7e93a17d8dfaf59eb97014aa1446db339e300982aa8dc5ca3f14e370e414e8f7895b3ed7dec9e71693f1f8ca9ad6421fe9b3c0d38280cdb1c4608a74bb6e3a0ddaf3f2d7ad6e12513004c6efd77ad6a21f2faeef0fedd214f5f3fc74d43a9e8803c815e03184619fe2ea10029e8db22c68a24290495b506fcea48e7b6a3b68714b06b9f749a20c22461ff0c7e0759f7a5ca8d51e318dec2d88be517eb6295c6f70a823a6a02f1728cb16827c545737e0b7a0a5a1cb06ebbcf965a582c92424c692ee6769d9e2f3e9e9accf5c45794cd27b95a68f507eff88850a9883929ceb3274a34650127a4cb9ccac5b5bcb559fd43f39b6b64081bd3255dccb8c665d48bddc2f4436223689fd97f11790481f8df7f0e4c91af31aed0b4a471191e25ed856ffb9ea7cea06e4de5e5eb689063324e9268730e03cd34f4dc3ee68See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
PUA.Win.Adware.Qjwmonkey-6992589-0 Indicators of Compromise Registry Keys Occurrences N/A
-
Mutexes Occurrences ATL:MemData03EAPC
10
\BaseNamedObjects\ATL:MemData03EA899552
1
\BaseNamedObjects\ATL:MemData03EA830021
1
\BaseNamedObjects\ATL:MemData03EA841675
1
\BaseNamedObjects\ATL:MemData03EA358075
1
\BaseNamedObjects\ATL:MemData03EA675052
1
\BaseNamedObjects\ATL:MemData03EA134349
1
\BaseNamedObjects\ATL:MemData03EA414408
1
\BaseNamedObjects\ATL:MemData03EA124406
1
\BaseNamedObjects\ATL:MemData03EA651689
1
\BaseNamedObjects\ATL:MemData03EA172892
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 47[.]102[.]38[.]15
10
39[.]108[.]27[.]173
9
47[.]95[.]181[.]45
2
36[.]99[.]227[.]233
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences x[.]93ne[.]com
10
cdn[.]zry97[.]com
1
Files and or directories created Occurrences %System32%\d3d9caps.dat (copy)
10
%System32%\d3d9caps.tmp
10
%APPDATA%\GlobalMgr.db
10
File Hashes
068eda364702ce61530d3b06ff1edb490fa157572ebf936ad9ad0d913c44e46d0c748be9a32bc9ce08709f67a45fc9e3e76a06b6e30091ea6e75014651449bd61211299848ddadcaefe019ade6a5394a744297e5fbe8182d0156faffe2f40e34275b0dad9af4cad57d9fe546b7f8c11e55b848b2ca68959bbe8d45fc3195a85b326d9df48f47cad42b8a6bac64061b9e2592d62ad5c8fd2a727865f84a79b6c932a0d53d2716251728d4120e5cceb4eb8894fd830841d9476820cd868420d37a6f5854d4dce3170393d74fb216573d08b694d7ec2982f02d3e46fe34b3ba0ed770ab5cb1653e39937408d71b70c9bd3952c572a2b54bc2b039794130efe5ae778da41212571b8b910ec657bc8f1b67ef22dd3c15e40280d5c6f93a5104227c0f90a457c02c2e659902d1be908c53c38eec47574101f14477c22ec87968b5b8709ae31bf1c30051d3438f3548d5f7593c24aa9297cb9f89b26b04d01482f776229dcb833bbac2d4fabafe49babb53b127349be1ee1444031cccb77d2752206813c3e2f2e2e17f0408b11bd9cc8dc3ea97364fec6d3dea07ba896901d24f89fef4c48b5755d64f2fa9fe6bdeec4605d5352e196db78d507608fc9f181be93f9da1c4e26e43528d8be9dba86a1b7c30b4ef8bdca67b56bbcab2d7fc76cb12004b14c88992429426ed40e4a5ff37c0ff0b3ecdb52a07f7e6b4b2377a6c4160263419d29b9fa55f21577991f220bec9bbc89969e843b6b03f7dad0084e80b86961c97d2bcb4e712ee873f8cce82a2783b84bf2a11f275e9064581cf00fd88323e803ddace1d73cd93785decdc4993f12de1b214b0a836539063c5fac8b154ce948eb1db55da939400d9d718b39e20280da3317cd1d35a522ec4927b059fefea4aa754df38320eb4d1eedf53b9927cb734bf2506e3d38d04c9279e65aea08391bc6caae8a913bb3211a926e04ce387dadf74d262e287070ad08192153b4a07f8914544ed613488a7bdde693d5b819ce946a8e9865426b9ea7cbbab8a867dc4db79d483 Coverage
Screenshots of Detection AMP ThreatGrid
Win.Packed.NjRAT-6992540-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\System\CurrentControlSet\Services\NapAgent\Shas
32
<HKLM>\System\CurrentControlSet\Services\NapAgent\Qecs
32
<HKLM>\System\CurrentControlSet\Services\NapAgent\LocalConfig
32
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\Enroll\HcsGroups
32
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\UI
32
<HKU>\S-1-5-21-2580483871-590521980-3826313501-500
Value Name: di
32
<HKCU>\ENVIRONMENT
Value Name: SEE_MASK_NOZONECHECKS
32
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: ParseAutoexec
32
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 7a6058fe5633bcc68b913467734f0f12
1
<HKCU>\SOFTWARE\7A6058FE5633BCC68B913467734F0F12
Value Name: [kl]
1
<HKCU>\Software\5d6c253999006e0a364768488fca8056
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 5d6c253999006e0a364768488fca8056
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 5d6c253999006e0a364768488fca8056
1
<HKCU>\SOFTWARE\5D6C253999006E0A364768488FCA8056
Value Name: [kl]
1
<HKCU>\Software\81d13862f7a9e91b88ef1cf04880f30b
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 81d13862f7a9e91b88ef1cf04880f30b
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 81d13862f7a9e91b88ef1cf04880f30b
1
<HKCU>\Software\c4356a2f1cc184765354ac346ff3c760
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: c4356a2f1cc184765354ac346ff3c760
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: c4356a2f1cc184765354ac346ff3c760
1
<HKCU>\SOFTWARE\81D13862F7A9E91B88EF1CF04880F30B
Value Name: [kl]
1
<HKCU>\SOFTWARE\C4356A2F1CC184765354AC346FF3C760
Value Name: [kl]
1
<HKCU>\Software\92c90be64c51c97abffcb0136889e008
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 92c90be64c51c97abffcb0136889e008
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 92c90be64c51c97abffcb0136889e008
1
Mutexes Occurrences \BaseNamedObjects\23f0e3bce589df29a3e6f3e8879b41c1
1
cf56ee275cc59274062dc1b03224ca99
1
7224ecb50ef565a251e4dca6d8280c72
1
ddb5e6e34f69e8c18573f23e18eb66b5
1
dbac86ee556aeefaf987b893994aa8a6
1
9933a39bcdb4ca2ba91ddfbf0eb49c28
1
27e6ba15367cfc6ccdb30fd12c8ebc9a
1
551c2891c1a5b14d85bd8205beca398a
1
6f548f49442e3cf6cd712e1421ced30b
1
ea48d06232228d6119e51286c4c0d7cb
1
6843bfb57b172a29eaca1016ea14dd34
1
b6a24dab009c0449997c4b895176ddee
1
b17b3051ec3895b563f6189b117c7103
1
61d4512a2b96204a3981459fa733229e
1
b1471de1dda54e505e7a2fe5dc250cbd
1
5b9aa31356f88f5efd2d650bab2fd205
1
227ae895ae9adabb3c9cc7efd9b8f180
1
cf10c5de3b577ea5f5b8886499972c21
1
89ced9869827e13512140dfd15310bdb
1
7a6058fe5633bcc68b913467734f0f12
1
5d6c253999006e0a364768488fca8056
1
81d13862f7a9e91b88ef1cf04880f30b
1
c4356a2f1cc184765354ac346ff3c760
1
92c90be64c51c97abffcb0136889e008
1
d8cff2de0df1355a3d74ec30295aa1da
1
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 2[.]91[.]138[.]211
2
197[.]206[.]180[.]205
1
85[.]170[.]230[.]163
1
185[.]17[.]1[.]245
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences youwave932[.]no-ip[.]biz
10
dmar-ksa[.]ddns[.]net
3
karem[.]no-ip[.]org
3
alkhorsan[.]linkpc[.]net
2
sabridz[.]no-ip[.]biz
1
alkhorsan2016[.]no-ip[.]biz
1
amiramir[.]noip[.]me
1
MSKGH[.]DDNS[.]NET
1
mskhe[.]ddns[.]net
1
paleb[.]no-ip[.]org
1
yeswecan[.]duckdns[.]org
1
megatn[.]publicvm[.]com
1
Files and or directories created Occurrences %TEMP%\server.exe
4
%TEMP%\svchost.exe
2
%TEMP%\svhost.exe
1
%APPDATA%\google.exe
1
%TEMP%\system.exe
1
%TEMP%\win32.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\9933a39bcdb4ca2ba91ddfbf0eb49c28.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\27e6ba15367cfc6ccdb30fd12c8ebc9a.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\551c2891c1a5b14d85bd8205beca398a.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\6f548f49442e3cf6cd712e1421ced30b.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\cb0bc0e4b97025e4a12cd7655f373600.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\ea48d06232228d6119e51286c4c0d7cb.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\6843bfb57b172a29eaca1016ea14dd34.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\b17b3051ec3895b563f6189b117c7103.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\b6a24dab009c0449997c4b895176ddee.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\61d4512a2b96204a3981459fa733229e.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\b1471de1dda54e505e7a2fe5dc250cbd.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\5b9aa31356f88f5efd2d650bab2fd205.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\cf10c5de3b577ea5f5b8886499972c21.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\89ced9869827e13512140dfd15310bdb.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\7a6058fe5633bcc68b913467734f0f12.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\5d6c253999006e0a364768488fca8056.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\81d13862f7a9e91b88ef1cf04880f30b.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\c4356a2f1cc184765354ac346ff3c760.exe
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\92c90be64c51c97abffcb0136889e008.exe
1
See JSON for more IOCs
File Hashes
04675d38c3f123c6cfe12a8b96c840894985d77a044aa009b6f6a2d1d9bd42a5070a2b244bfb020dc8c3203831e14d3f27f3a3d5a7bc0df2e1a1acc1b7a5b48a0bfae405fffc2cb791f7eefb7c4d2efe4b76235289e5a043718bc6ed7480c4f10c75f012571cc271d8c19d95b714f425bf6f5ef7b09a646c18cd0b99e0050ede0e37c0759ded6594cf671c82ea8d8404b2c8ad34c8b7c772d4f4bcdbc01f6b28133d714e145400b9adc0ac24584745443fee2a9cdcda31bd3251264e46c846071444bf151e764ffe3402827f60a142f20a0e6060ad8fb80255e1a82c63ec70e0146054936453e72343079c7c89517cef5a8e270ba827c321ce6c6740775df7c419b06c7cf56e2148202b8051d64823817d8c81afd9e6061e6e625b953439b9eb26f3184e05046a17a8a470a0ca2088a8774641729eb86c6f84310707014dfb6b2d4c6b0074ca4866f50c7242882e467a65da7f7dc28fd9c2bbd09caa6f99a8d6369f407ad2e8321d87ac5f32241d7cf2a0e72aae0b8c0caed4f30faa042ed85e3bb55a41fa1c485c018b03b521beb74a4baea14bc2b89b8b69713e07079771f93d0946ab360b335a58789cc81cb5711e438f312426b2477b2777a256f2b772c6452ec0f00cee0a7ea6c104d9835af5f3999c50b37d22081dee4b47e75b794cad469d100e0e62a4099313c485e24f134abd32e598a7f65f147342ac7ea9274f2a4cd937a9a1914666ebe671b2b9f4db59806dbacd6ae784b10f5b625e1448649f560a570d89a632b81d34cf4d1e20a86c35657d9211ac4061c419883e2b108e635da16143a544f7c51cdd146540b5393113a6768162328cfccb5e484c64472ec6619b638736132bd02470c09508cb63a3fb753c6ee0f8dab4f4af6c2694f9095f6323174f37df70906257ac7b545eeed4e1cfaea1cbbba74d5acc49230fadcf7364f50c68d48d152eba786380b7a1db84f94f28c63f34ccb499008e1889ee0675694a3485ae77c8e024295e34caf2f335eeb61d4ebcda6fd5789086526ae44a9f6aacdb0640cda4db32f307b91e4d0d6bb4d88429a14308fb90ec573a9c892afb7530fc29bdc4ae5be727789818541dafcb590bdd708e64e8bde0a4c99b37b2f7See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Malware.Tofsee-6992280-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\System\CurrentControlSet\Services\NapAgent\Shas
17
<HKLM>\System\CurrentControlSet\Services\NapAgent\Qecs
17
<HKLM>\System\CurrentControlSet\Control\SecurityProviders\Schannel
17
<HKLM>\System\CurrentControlSet\Services\NapAgent\LocalConfig
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\Enroll\HcsGroups
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\UI
17
<HKU>\.DEFAULT\Control Panel\Buses
17
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config3
17
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\wpdjiqwl
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\wpdjiqwl
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WPDJIQWL
Value Name: Type
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WPDJIQWL
Value Name: Start
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WPDJIQWL
Value Name: ErrorControl
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WPDJIQWL
Value Name: DisplayName
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WPDJIQWL
Value Name: WOW64
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WPDJIQWL
Value Name: ObjectName
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WPDJIQWL
Value Name: Description
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WPDJIQWL
Value Name: ImagePath
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\gzntsagv
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\gzntsagv
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\GZNTSAGV
Value Name: Type
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\GZNTSAGV
Value Name: Start
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\GZNTSAGV
Value Name: ErrorControl
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\GZNTSAGV
Value Name: DisplayName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\GZNTSAGV
Value Name: WOW64
2
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 239[.]255[.]255[.]250
17
69[.]55[.]5[.]250
17
192[.]0[.]47[.]59
16
144[.]76[.]199[.]43
15
176[.]111[.]49[.]43
15
46[.]4[.]52[.]109
15
144[.]76[.]199[.]2
15
85[.]25[.]119[.]25
15
43[.]231[.]4[.]7
15
172[.]217[.]164[.]132
15
94[.]23[.]27[.]38
15
216[.]146[.]35[.]35
14
208[.]76[.]51[.]51
13
172[.]217[.]192[.]26
13
74[.]6[.]141[.]40
13
212[.]82[.]101[.]46
12
98[.]136[.]96[.]73
12
98[.]136[.]101[.]116
12
67[.]195[.]228[.]87
12
66[.]218[.]85[.]151
12
213[.]205[.]33[.]63
12
98[.]137[.]157[.]43
12
87[.]250[.]250[.]89
12
74[.]125[.]193[.]26
12
172[.]217[.]6[.]228
11
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 250[.]5[.]55[.]69[.]in-addr[.]arpa
17
250[.]5[.]55[.]69[.]zen[.]spamhaus[.]org
17
250[.]5[.]55[.]69[.]cbl[.]abuseat[.]org
17
250[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net
17
250[.]5[.]55[.]69[.]bl[.]spamcop[.]net
17
250[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org
17
microsoft-com[.]mail[.]protection[.]outlook[.]com
17
whois[.]iana[.]org
16
whois[.]arin[.]net
16
sweety2001[.]dating4you[.]cn
16
honeypus[.]rusladies[.]cn
16
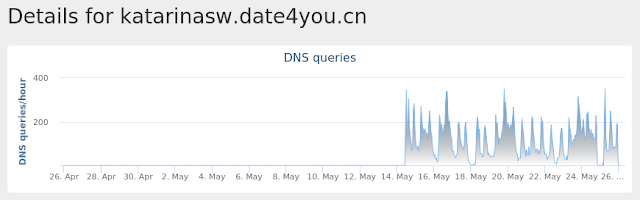
katarinasw[.]date4you[.]cn
16
marina99[.]ruladies[.]cn
16
mx-aol[.]mail[.]gm0[.]yahoodns[.]net
13
hotmail-com[.]olc[.]protection[.]outlook[.]com
13
mx1[.]emailsrvr[.]com
13
aol[.]com
13
mx-eu[.]mail[.]am0[.]yahoodns[.]net
12
tiscali[.]it
12
mxs[.]mail[.]ru
12
mx[.]yandex[.]net
12
mx[.]yandex[.]ru
12
msx-smtp-mx2[.]hinet[.]net
12
tiscalinet[.]it
11
inmx[.]rambler[.]ru
11
See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile:.repos
17
%SystemRoot%\SysWOW64\config\systemprofile
17
%HOMEPATH%
15
%SystemRoot%\SysWOW64\wpdjiqwl
3
%SystemRoot%\SysWOW64\gzntsagv
2
%SystemRoot%\SysWOW64\athnmuap
2
%SystemRoot%\SysWOW64\slzfemsh
2
%TEMP%\utjfmin.exe
1
%TEMP%\evorylxw.exe
1
%TEMP%\gstniefc.exe
1
%TEMP%\otggjiyd.exe
1
%TEMP%\edtpwsx.exe
1
%TEMP%\uutzkyfi.exe
1
%TEMP%\rlnkeakp.exe
1
%TEMP%\azlhmwgt.exe
1
%TEMP%\wytkbvcv.exe
1
%TEMP%\uboorcup.exe
1
%TEMP%\uxffdbfo.exe
1
%TEMP%\ondzgch.exe
1
%TEMP%\arknuhts.exe
1
%TEMP%\tyllondi.exe
1
%TEMP%\qpfbiej.exe
1
%TEMP%\jhokjsqh.exe
1
%TEMP%\lkwsxhre.exe
1
%TEMP%\pjlicyin.exe
1
See JSON for more IOCs
File Hashes
116bb71b6e6866ba5862d18e5361fe70ad2f9adb3ed8f5f1606e2561bff9fa792b9c74a2ffb4d1164048adec4381d151922244be8855026bff683abbf4122684397ad676785c8e47422e723c081e44172dd935bcfe1389a039ac4bb1013c50c059639b75a9ebe2fdcf6ec9623454f06455a5fa6f0a23e47cece96d98c8c0f324650c6dae8c1553d599d15e7c3d2235a393f498b743538674c7a1d87a8b627d907b962ff72c455f123c5ee0ba29aeea11e6fa23d595a0be8aad7b0235d5280d7985bd864d585a37662a1c6a28daef2ac8c97996e52bf37209e76b0a8a9d6494e1a1fd580e38af18c70ede2540e309a513e85b9a06423aee45f35fbbf1bfa517b9a94cea85efa1c6842892248e1724cd17fb66a34435c9797d9809c3e25a5e6770bad0767a0cf7088aed7904551b26bafd66b4bbc1257518275a1b277f27d1f7a9c3bb4a36939e8f6d2acf8b57b0676ca8c7bafea33cfd15bedecf192f0610e6e9c5ed772f6cb0aa202fb87049bd20063741fd62023f7d9c924876e28711dab3f2de76a7d7af2c38342333014608b75117a2d1868d9020f62fdd117cdfb5ed30fae1cfadc86259f90b2f1fb5cd23bd267a94ed8c8a2d72035b6e335fd5e68d5866ec4960b3885c4bb63032883cd088585e4f347c4ac9659f49982f999775d90a21f1e790bcc0711047ab255646e07ef7d2fb644c45b24a4bc67250e2c8ee9318a1f7699a1eafb0aded81818b28fd1c897e3e2e22d9d7b4297d97654a5aca09da49 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Malware.Yobrowser-6992453-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\Software\Microsoft\RestartManager\Session0000
33
<HKCU>\SOFTWARE\MICROSOFT\RESTARTMANAGER\SESSION0000
Value Name: Sequence
33
<HKCU>\SOFTWARE\MICROSOFT\RestartManager
33
<HKCU>\SOFTWARE\MICROSOFT\RESTARTMANAGER\SESSION0000
Value Name: Owner
33
<HKCU>\SOFTWARE\MICROSOFT\RESTARTMANAGER\SESSION0000
Value Name: SessionHash
33
Mutexes Occurrences Local\RstrMgr-3887CAB8-533F-4C85-B0DC-3E5639F8D511-Session0000
33
Local\RstrMgr3887CAB8-533F-4C85-B0DC-3E5639F8D511
33
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences %LOCALAPPDATA%\Programs
33
%LOCALAPPDATA%\Programs\Common
33
%TEMP%\is-C6FN7.tmp\32dfee8be7cca7d0ed5b84fe8deff6d7177042a802586d16c26176ec58952309.tmp
1
%TEMP%\is-9HDTO.tmp\_isetup\_setup64.tmp
1
%TEMP%\is-9HDTO.tmp\_isetup\_shfoldr.dll
1
%TEMP%\is-9HDTO.tmp\trithiweate.dll
1
%TEMP%\is-7CPIN.tmp\36ca931623f279c6683ace47e425666510034f5e18441f90e895a3fc6cd2bbdb.tmp
1
%TEMP%\is-0142V.tmp\_isetup\_setup64.tmp
1
%TEMP%\is-0142V.tmp\_isetup\_shfoldr.dll
1
%TEMP%\is-0142V.tmp\trithiweate.dll
1
%TEMP%\is-CRK4O.tmp\42827e85051a54995e67aeb54b9418968224f6c299887e4afca574e08b2b76c1.tmp
1
%TEMP%\is-Q964A.tmp\482675e5774d1714ae17b5daefd13697fe3a921feb20fc4360065c2135b9c7b0.tmp
1
%TEMP%\is-9AA9G.tmp\3f2c22316bc2184f740f39499e41002c6d525a2c4c18dd0b9170c90410a5e4d1.tmp
1
%TEMP%\is-T68TS.tmp\4a55c9ceaa100182f6fc1ce9c8ec3c0f9eb58b7841c46c7d1d66fa5eaa4f410e.tmp
1
%TEMP%\is-8V9B2.tmp\_isetup\_setup64.tmp
1
%TEMP%\is-8V9B2.tmp\_isetup\_shfoldr.dll
1
%TEMP%\is-8V9B2.tmp\trithiweate.dll
1
%TEMP%\is-P9KOG.tmp\_isetup\_setup64.tmp
1
%TEMP%\is-P9KOG.tmp\_isetup\_shfoldr.dll
1
%TEMP%\is-FPHCP.tmp\_isetup\_setup64.tmp
1
%TEMP%\is-P9KOG.tmp\trithiweate.dll
1
%TEMP%\is-FPHCP.tmp\_isetup\_shfoldr.dll
1
%TEMP%\is-FPHCP.tmp\trithiweate.dll
1
%TEMP%\is-3SHVR.tmp\_isetup\_setup64.tmp
1
%TEMP%\is-3SHVR.tmp\_isetup\_shfoldr.dll
1
See JSON for more IOCs
File Hashes
02be7ea7484ce02344237e4aab046aaa3af0f67f5b5bc7530b7757c1820083740912999b354d903202f981d327670d3dd5a6f37f3c3374cfbf29b9d5dce86e5a0bd58e14131755d1671174225ea1349a9c9ca54e76a29c2696aab762859ed6ea1150e22d4d164cd9a07ee28a6c6d33e657e10e1af6f06a3423c56a5f0449b02c1609b08dc860872a1a37967ec01e9c8d90813e42f4c32a4a5c7651b226bf1c7f16ee969920278d950596ee85505d40ed1b4265d6fdfa35dc55dd6d188c43261418c140ae4eb5f0bdff9f07ba176fba6873e5359ff689145bf4d41defec9f635f224b4f9f98e7d9887ebcae15c02d8973264f31d12ff87a30d696139a316e2cf9259546449e9e630fbe3bdcfbda7c51de9c1e7bb93022bda08d89bea95ad23a2426b5593a4e7c8b5accf97029cf6c646c7769cecd36d105153f228f03a20f24be2e39806e189e988a6bb094359db5aab14638a1737fded6ab00095425672aa13d2fc0b64cf4ab9d6a6a3b607b999b1e47551bfb62acf143bd08faebf0485157d732dfee8be7cca7d0ed5b84fe8deff6d7177042a802586d16c26176ec5895230936c8f82ff5ebd1647044f14b83dbfb93e1ad5e8e80d95cb2f6e3f463cf4ac94e36ca931623f279c6683ace47e425666510034f5e18441f90e895a3fc6cd2bbdb3f2c22316bc2184f740f39499e41002c6d525a2c4c18dd0b9170c90410a5e4d142827e85051a54995e67aeb54b9418968224f6c299887e4afca574e08b2b76c1482675e5774d1714ae17b5daefd13697fe3a921feb20fc4360065c2135b9c7b04843bffb11be8da31b059e63973b2f97a3a093cf80b537cb19629f49099a35c44a55c9ceaa100182f6fc1ce9c8ec3c0f9eb58b7841c46c7d1d66fa5eaa4f410e4f349d22bc1cb7e4defbd97debebe906a5408351e7069cf5cc2333338d5be8ed5677386b0050cff2f5a2c12430999d569dc744944f2f2d9c29f3bab6d5d43edf5ca1ade829002a58684dc8ff37b11e7b07d91b61a26d89a6736f884d14a0d00f5ddbe11ee1e50f6a198f1e331e55621fcfc02870f6e8b4e4d5d171bf008938b564543ddc78b58da0236310fcee0b447e153d94a4cd393c1975bbe6b000acc960See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Exprev Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. Madshi injection detected (3267)Kovter injection detected (2041)Process hollowing detected (1016)Excessively long PowerShell command detected (676)Dealply adware detected (284)Gamarue malware detected (197)PowerShell file-less infection detected (53)Atom Bombing code injection technique detected (45)Fusion adware detected (35)Installcore adware detected (32)