Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 9 and June 16. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
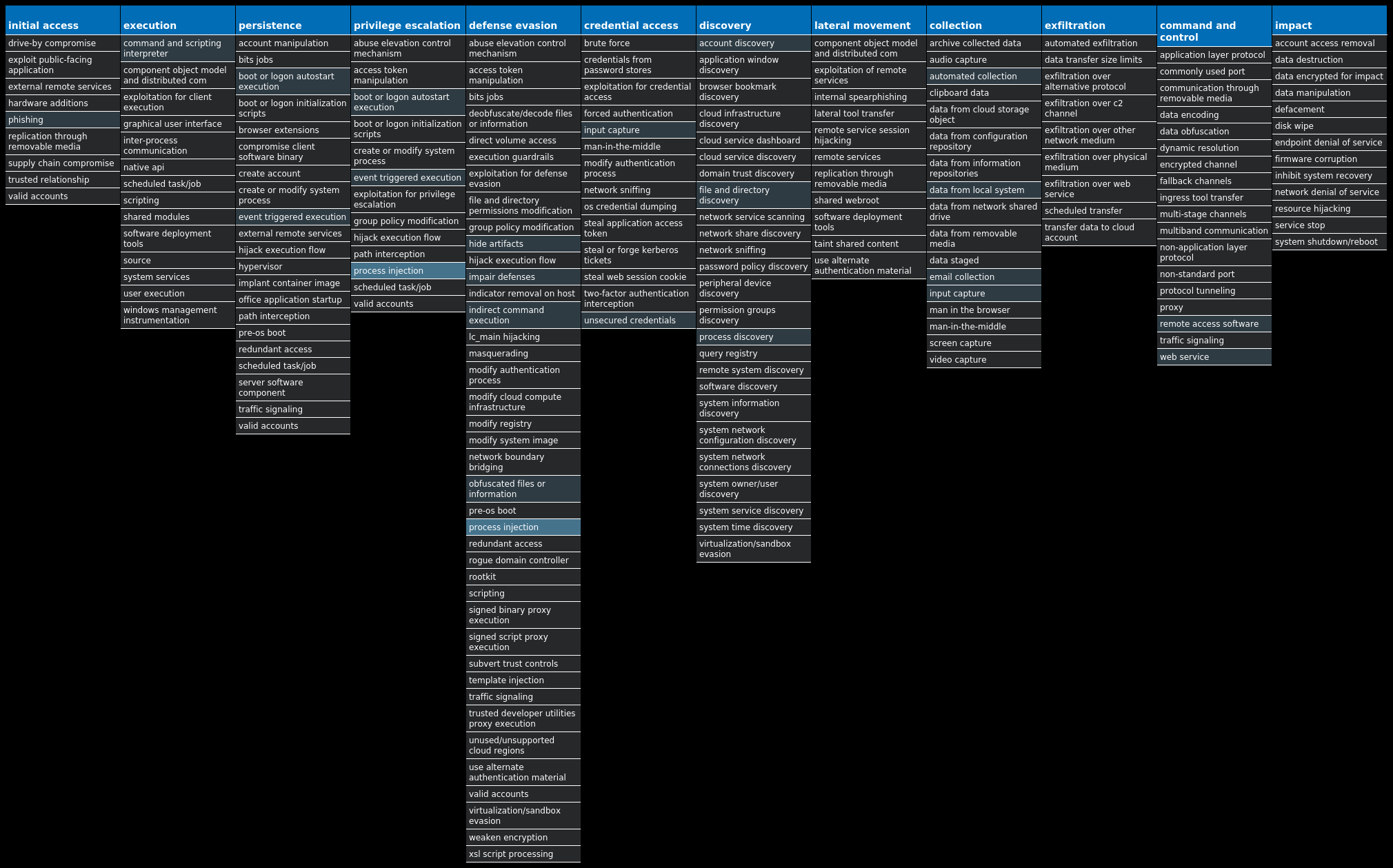
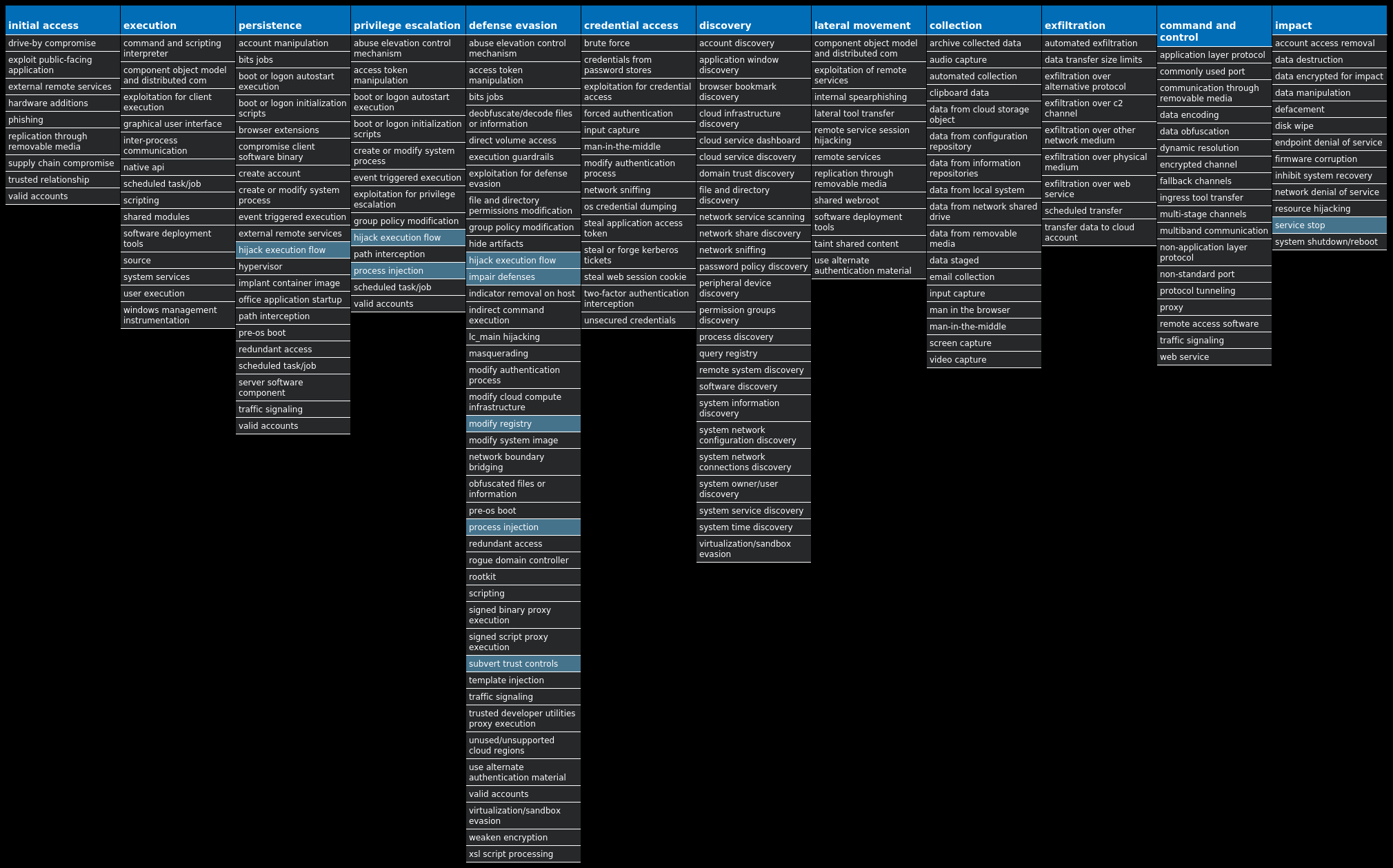
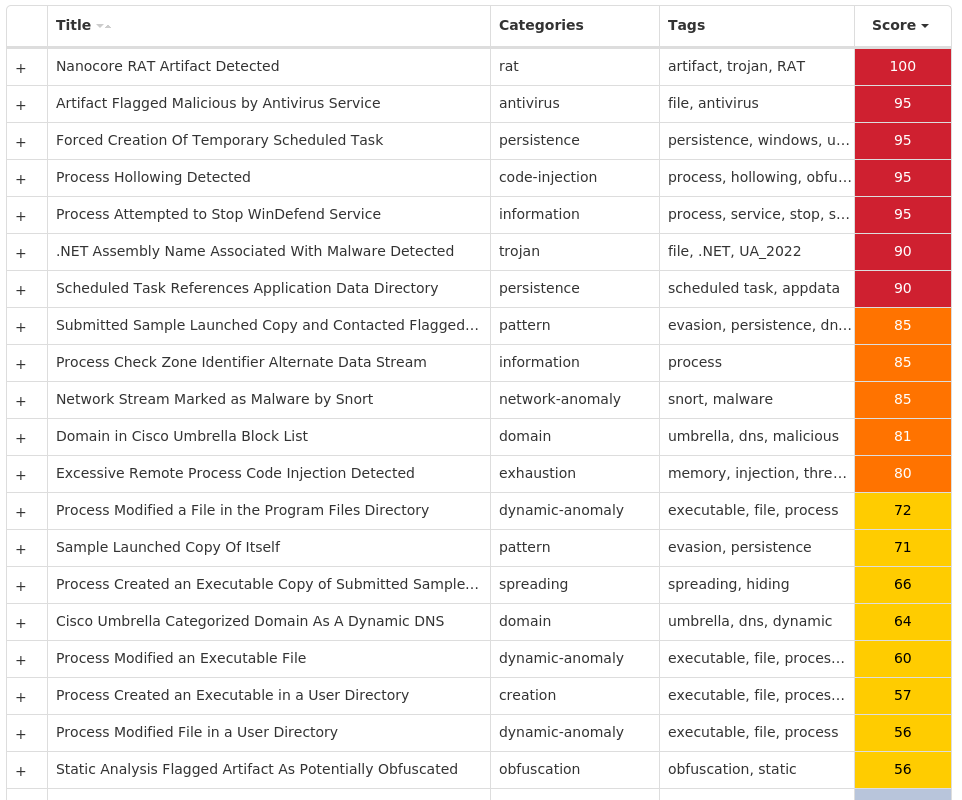
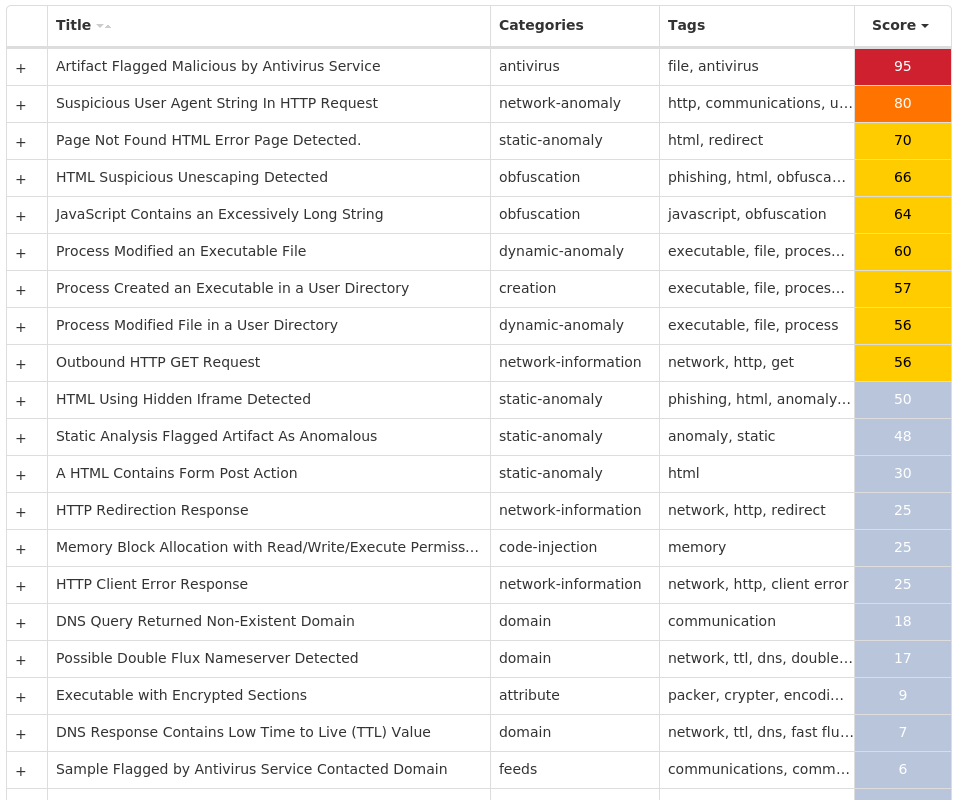
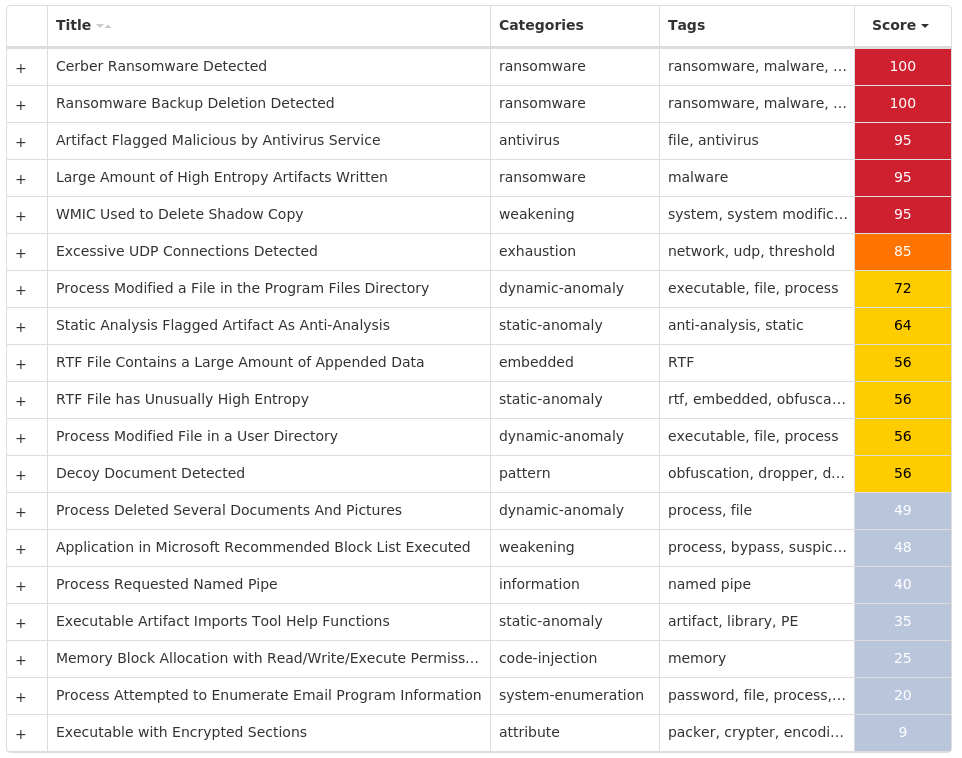
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.Zeus-10004541-0 Dropper Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing. Win.Dropper.Kuluoz-10004513-0 Dropper Kuluoz, sometimes known as "Asprox," is a modular remote access trojan that is also known to download and execute follow-on malware, such as fake antivirus software. Kuluoz is often delivered via spam emails pretending to be shipment delivery notifications or flight booking confirmations. Win.Packed.Redline-10004447-0 Packed Redline Stealer is an information-stealer written in .NET and sold on hacking forums. Win.Packed.Nanocore-10004398-0 Packed Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes. Win.Dropper.Ap0calypseRAT-10004380-0 Dropper Ap0calypseRAT is a Remote Access Trojan (RAT) that has many capabilities including arbitrary command execution, keylogging, remote desktop access and file exfiltration. This RAT has shown up periodically on underground forums and has been seen as an additional payload dropped by other malware families. Win.Packed.Upatre-10004369-0 Packed Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware. Doc.Malware.Valyria-10004248-0 Malware Valyria is a malicious Microsoft Word document family that is used to distribute other malware, such as Emotet. Win.Ransomware.Cerber-10004233-0 Ransomware Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns, other file extensions are used. Win.Virus.Ramnit-10004200-0 Virus Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It also has the ability to steal browser cookies and attempts to hide from popular antivirus software.
Threat Breakdown Win.Dropper.Zeus-10004541-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\PRIVACY Value Name: CleanCookies 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104 Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Idugibufy 1 <HKCU>\SOFTWARE\MICROSOFT\TAID Value Name: Keewabanr 1 <HKCU>\SOFTWARE\MICROSOFT\TAID1
Mutexes Occurrences Local\{<random GUID>}1 GLOBAL\{<random GUID>}1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences unchangedantivirus[.]com1 uhgnc43fgjl82309dfg99df1[.]com1 uhgnc44fgjl82509dfg90df[.]com1
Files and or directories created Occurrences %APPDATA%\Noalxe\ocses.ukk1 %TEMP%\tmpa0a62141.bat1 %APPDATA%\Noalxe1 %APPDATA%\Pysiha1 %APPDATA%\Pysiha\orisv.exe1 %APPDATA%\Yrnin1 %APPDATA%\Yrnin\rogi.aqt1
File Hashes 0eae875ca8ee8ea1875cab7a5d0e3c9c7af1a402cb978503c794453b613e614c23ec2f58279589e488b31acbe11616e9330e797478153693f830b89d22acd7d32e1b0cdae24a711bbf07934bcef5d729c984cc4d075d7a88334f2a434d09cd7237af0d523354241a0e0c39786f158e24c17f394d3211fcc0f7a3422e858235185ac479b9b3acc452dfe29c18a06ed5dfca8844ef7dbdf695a215a7b9316d6d9560fd5cbf3e51f74d45c4821043e303d6c4f6b1e108c3fab7049a7f361bbffd4661d04496b6765bd8adc5e5d6beaacdec45a943e55d8eb5566331829815aae8de6d8f1d0bbf470a12b700813c309e7b1c641667be9ee4d07ddc5b9670e147e7976ff603ff02897c372646410cc8e3b62a2759d333d469ca3c6b0a88c5829a27968dd6322a5fca13c5888901c97e995a61cd55d43c695c423bc7cb9fbeea67a14a903ed73feb1f20767ab7032f389e1595fe91c3cad364d53e8386ee86c14776ffc64bc76836aa66b5602911eb766d82a70f2d503a3df88907c453dfa783eb4621ce06e1e2b1b89ad5e98499910d0e4151ccf49fb6c806b1f13e28551c1ca58aefde6d74aba65daf28da4d18c0ea604a6919ffdd9c59beb07f9aa159b8d74cc8f4eff388de6e2e104e64d0d28fe61837afd2cf053ddb3ca40d8ad5ed6654570d9c
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Kuluoz-10004513-0 Indicators of Compromise IOCs collected from dynamic analysis of 43 samples Registry Keys Occurrences <HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'>43 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ewdtednn 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: kfgsdpdv 1 <HKCU>\SOFTWARE\XLWVBVLN Value Name: xtxmwque 1 <HKCU>\SOFTWARE\ERIUEKCR Value Name: dwpjqlpa 1 <HKCU>\SOFTWARE\FKGDWLFC Value Name: btcgqtxv 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: pwjcpvtg 1 <HKCU>\SOFTWARE\TRDDWSJW Value Name: hkwogctf 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: lwrnfwdh 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: btomjvqp 1 <HKCU>\SOFTWARE\BUGITDDP Value Name: txxsdgjg 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: doviudox 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: tuqsrtec 1 <HKCU>\SOFTWARE\EOBOTIUK Value Name: ulgvwopi 1 <HKCU>\SOFTWARE\PILXJFXK Value Name: ktkriwfo 1 <HKCU>\SOFTWARE\IDCCIMKF Value Name: tmumianw 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: lwkqralw 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vuemrbob 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: rssaalxp 1 <HKCU>\SOFTWARE\EFOKESHU Value Name: xulsnjws 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: fllgmrwq 1 <HKCU>\SOFTWARE\GIEJFQCE Value Name: iuqwifxx 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: toqdahjd 1 <HKCU>\SOFTWARE\ELNQDQUF Value Name: uhvnsbhc 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vtjkaseh 1
Mutexes Occurrences 2GVWNQJz143
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 78[.]157[.]209[.]22828 85[.]25[.]108[.]16427 94[.]23[.]84[.]9426 94[.]32[.]66[.]5625 177[.]87[.]64[.]2522 109[.]169[.]46[.]5920 176[.]31[.]110[.]16518 91[.]121[.]98[.]6016
Files and or directories created Occurrences %LOCALAPPDATA%\<random, matching '[a-z]{8}'>.exe43
File Hashes 04be2d1165429f6a1fc8217db32e549eeeb54983aa4c44f26e1147d054d954e10672e260b9febfd47b8536c8cd17866dc5cad82fbd9acf6778225c69617f8df413f0e1860121210bdcfd59887053156fee80c0e7e61ad1b2109a3ca027060ef5161dd94d902139168107ee72aa66fc2bb00ecbe72a9ea3a2645a2e5f3edb43bc1c5e6a11a293501d1bd41d302a7cbde8e8efc67916e4a063a5757f476190c48f31c10bfe9039675974640b3404fbbdccf660bbef3319ed011766f4e7e2dc6d4834861226330e4af50b8e03f6e9d8457ff1d1c9a7d3eeb1fc930a9f70a315dd54360e964ae4aaf043ea27780f20ab266bf55470e3d58fa20550c9f2c520823fbe42657321367294c31f060614894a0f13b1f38613cf3e013c94a835496e86a53745bedf4f08cc21eb94088a7ebd942915d8e3f834d0632cfb9264d92228c8a4f147ea467e5da54049ec9c40d2173a97fb87dae67546faba7dce0631ad88fa3fa947f9eabe7f83bbce4b0d52282ba627f678ecc48604201101f7650ecc72a3b7146ceeb2ab8b3d41fb927e0ffdcada6da07cac54124cdb8f0c9de15553a4254af575ed32ca3cc84d402a91fb13088ac3421917d427efb55bf2442b71f6dfd6a3987ef5f3c744b456b04c79e14c5923a7cfbc3894f14a473a564d843dce62293b5a86497472773d474e05b8ecccc82dfd17d7a4ad6c38e6911d03d6956aedadd49a92f407eb8a0b4562acd7f1c27c86ed365b37c37bbc2fda343efd0fe22ea73bd195528ad474a06ae5c23200fac691561cae115466dd07e7f60cb5e9bf667443f597fc7992ceecb79f0e43c702fc69a564941b9c909ffd422a7af6a8d1c575ffdd9f8eaa58bddf52d4ebc3603f00b6b19d76fe5ae486a308ac7d21330486fa0f87a23c17fe1c893ac18bcc2d524adc6b8be07ee6ed2277701d2b43a1681ba60a29a3a34b395a54043f247e09b8f6656ed66c74c6d02735e49a87e118749a1daa37ac097abc44ceac4f6f0b6a33e876a76284a9aad676ce924bda277925b3f12bf5ae08cd70435a6eacc7097babc6c26ecae3484bf8ca73ac1ae4f8078eef69d017ae622c4057b66fb39cc1a341f50ceaaa7146fe4c1e06d0d6e316547cff821da4
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Redline-10004447-0 Indicators of Compromise IOCs collected from dynamic analysis of 21 samples Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER Value Name: DisableAntiSpyware 21 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoRebootWithLoggedOnUsers 21 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoUpdate 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableBehaviorMonitoring 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableOnAccessProtection 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableScanOnRealtimeEnable 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableIOAVProtection 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE21 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES21 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES Value Name: TamperProtection 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableRealtimeMonitoring 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AUOptions 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AutoInstallMinorUpdates 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS Value Name: DisableNotifications 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: UseWUServer 21 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE Value Name: DoNotConnectToWindowsUpdateInternetLocations 21
File Hashes 0468aed948c966d973379f3321ad632bdb47462597eb37293fa63a6df50e786e0687ed000a8d454afd71dd8d2e434e05c292549453d1180fd870f1dd587ef2572e2d5d81146d974295d70f7f95da3f5889d6b89d9f6f74a106a67aa18c46c25633e02bfb76e29daba2408b0b54204bcf31322e43db27b9bf07f500d098b21c2a3d902c3c1daeee902e45427922d488b20bdb888bab2903e1c3a5bac13e0840f34454448516eadaed2c73673e3c679d00701a2d3f507cbe91e7a7ddf83a5229f052f0a8605e16fee96555022ae5a2582a8f0a1c9ca9e2edf8370aa5036d5803405857ead2de1bdd70583dc0bac98fa748e394a8f84eedfef2b181fffc6d0df0975c4b0c1c06ee33622fb00eca697f4b938b920f06fd14639d19f38356d0e933916eb8c09718aab1e22c32014d73bfa92dc1407f09329c46e61623576f74a8b7cf7083871d557bb3098401cf258925cd1ab00f18f323520bbb782009adad50207274aa4dfe0587680b1ec5ce307fbfa72e4292717f1a9332ff6b0e468c6ad0ba3a7c83d296cd1bc895b62a94b332de51759bcdc7d91bbeaf405bd9bc05776467217ff6bef8276020721e56160e9a442802174452775c16e794045eb99d2ca503ca8a51f12210bccebcf84558d3897b8bce2031698e62d83631d9fa1cab68ef0ef8991ef14f09db06924ccfcdd44b4ea839c6b9560a97a39608501fbf966606f592a05410fc760c1241b56d09033c1064bdecc8e722e5e65d21bc23120b27f70852a89ac9215339a2ec16d4d7246f12e4c481af063f727fd1246fe786cca1a2aefab41f1d01b3d5ef152d8b444a519a87b361977c4a126aff585ca79c5ef3d4d41ce59fdf54e139fd6637781a4f59ac8024338e8f4488792d927c1d02999e6e93bbea06e33529354e8d2569880a850d7f62307bedb2b91f1f5f7c3a1d48c859bb9c
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Nanocore-10004398-0 Indicators of Compromise IOCs collected from dynamic analysis of 18 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: AGP Manager 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: uqlXk 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: zfftgT 1
Mutexes Occurrences Global\{72ec1ea3-16bf-4e76-a7cf-15ed5e2a0279}3 KN-B-3-EU54G0CZ01 ZGDBwvZGELZLRCPChpvbfrWD1 wSloCryfIXeX1 AbaRaIBjYcRU1 DKSNfcypnrJXzjQjnZkRUIeIcus1 rtTbzYl1 iixYkwOUaWaDXPy1 tPTDaoIJnJFZnITdQgYpOTvc1 yCLOiDYWs1 NeczCEHFGCL1 CfXwBOmH1 pixAspxhe1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 149[.]154[.]167[.]2203 192[.]169[.]69[.]263 212[.]193[.]30[.]2303 64[.]185[.]227[.]1553 104[.]237[.]62[.]2112 173[.]231[.]16[.]761 199[.]188[.]205[.]551
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]ipify[.]org6 api[.]telegram[.]org3 december2nd[.]ddns[.]net3 december2n[.]duckdns[.]org3 smtp[.]joycepackglobal[.]com1
Files and or directories created Occurrences %System32%\Tasks\Updates11 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp11 %ProgramFiles(x86)%\AGP Manager3 %ProgramFiles(x86)%\AGP Manager\agpmgr.exe3 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C53 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs3 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator3 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat3 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\task.dat3 %System32%\Tasks\AGP Manager3 %System32%\Tasks\AGP Manager Task3 %APPDATA%\uqlXk2 %APPDATA%\uqlXk\uqlXk.exe2 %APPDATA%\OuInyVb.exe1 %System32%\Tasks\Updates\OuInyVb1 %APPDATA%\XkYmbRyk.exe1 %System32%\Tasks\Updates\XkYmbRyk1 %APPDATA%\mCAZjSlOqEdVo.exe1 %System32%\Tasks\Updates\mCAZjSlOqEdVo1 %APPDATA%\w3jtb4ed.rph\Firefox\Profiles\1lcuq8ab.default\cookies.sqlite1 %APPDATA%\bCaWJAu.exe1 %System32%\Tasks\Updates\bCaWJAu1 %APPDATA%\vJyKicblmfOPOF.exe1 %System32%\Tasks\Updates\vJyKicblmfOPOF1 %APPDATA%\drltEKUBys.exe1
*See JSON for more IOCs
File Hashes 097d71f426327cb3ffb6f83f5751a9a81dd7e8ad0a854f66882f7de1c572a34b16ef953132f6f51c904ccd3e04c933c20110c1dcbab443059df7218392291d5f3e7d7ffec0914a65f010b8a994fe91efa814e2e2a99ba5e6d349aa0b6aa4a19c3f5edf6f921e14f2640763e7178c2646a2131df0f8f447ae59100f3110939d9d5bed2e9d405ecb76915833a5b3e5c81afbfdc4b0bb742c4524e740dd25582eb76fa4a794d4d0968b2aa5aa59739952e3d45f44d8a9cc73c75c138fcb789914fa7f368076cc5c5cee446a8491832c17332673709bc739f6e3e3deeddfaf2f53267f9b57c29724dc1ff00b7760dcce1e38bf94335a2e44393882b276205f7ed21881d6168162bbf9e13bde19c24fd797075a7ddde876c233f971c9114f1b0334fb8b6d1769bdcbfe25f0fb3e1cd47b99e71d8dbecd010c0e1456529f43d4a0a8c49e3dd1cab3bb5c9980d75079dd5525cf724e0e496bf6fd7db27bf8124506b883b0664bf756d2e493d222fc3e52f2ae50e9a1b29582ad345979e76695442ff984ba9882d95e3ae22ec4ed90535f81b6396a259a5e1ea940cec487b4b1d6ff9e41c5c46c7bdb0a6a9db80a1b2393a2d2dcb2cc497f678779c3aac38b2b0db3f80ccaf3bf03258eea3f9dc186324f276796170edb45560f68226ef651190a18f5b7d26c2932bf50586ecc8c7f9df6d07116f7bea135ab4ebd51ce0dccf0d48b640ed547ab6d0b28d86c32e3d981adc3c5476797c58a6a684a45c3ee0a74847fb571f17c5f11699824e0256b4b0b8ac64a97bf0ba7545e9149cf5f3b0e7f10cc4828
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Ap0calypseRAT-10004380-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\PRODUCTNAME16 <HKLM>\SOFTWARE\WOW6432NODE\PRODUCTNAME\PRODUCTID16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: smss.exe 4 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Grup 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Ad 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Sifre 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Delay 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: MsgGoster 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Metin 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Baslik 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Buton 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Icon 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Bindir 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Dosyalar 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Mutex 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Baslangic 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Anahtar 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: YuklenenDizin 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: ProgramAdi 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: ActiveX 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Injecsiyon 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: Persistent 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: UserMode 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: KernelMode 3 <HKCU>\SOFTWARE\APOCALYPS32 Value Name: SafeMode 3
Mutexes Occurrences 45646546513213212314652456456456412312341 461231231232343F4CCJFJF1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 142[.]251[.]16[.]1081
Domain Names contacted by malware. Does not indicate maliciousness Occurrences smtp[.]gmail[.]com1 irc[.]yetcar[.]com1
Files and or directories created Occurrences %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\699c4b9cdebca7aaea5193cae8a50098_d19ab989-a35f-4710-83df-7b2db7efe7c515 %TEMP%\FileTmp.exe15 %APPDATA%\chrtmp4 %SystemRoot%\SysWOW64\krsr4 %SystemRoot%\SysWOW64\krsr\smss.exe4 %SystemRoot%\apocalyps32.exe3 \TEMP\htm.htm3 \autorun.inf1 \DFGDFJJJJDFJDFJGFDJTURTURUTJJF\DFG-2352-26235-2322322-624621221-2622255\Desktop.ini1 \DFGDFJJJJDFJDFJGFDJTURTURUTJJF\DFG-2352-26235-2322322-624621221-2622255\usbBlock.exe1 E:\autorun.inf1 %TEMP%\x.html1 %APPDATA%\explorer.exe1 %TEMP%\google_cache2.tmp1 E:\DFGDFJJJJDFJDFJGFDJTURTURUTJJF1 E:\DFGDFJJJJDFJDFJGFDJTURTURUTJJF\DFG-2352-26235-2322322-624621221-26222551 E:\DFGDFJJJJDFJDFJGFDJTURTURUTJJF\DFG-2352-26235-2322322-624621221-2622255\Desktop.ini1 E:\DFGDFJJJJDFJDFJGFDJTURTURUTJJF\DFG-2352-26235-2322322-624621221-2622255\usbBlock.exe1 %SystemRoot%\SysWOW64\krsr\resim.jpg1 %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\02fc8fb78d4f7516019d9a99eaf6a46d_d19ab989-a35f-4710-83df-7b2db7efe7c51 %LOCALAPPDATA%\MicrosoftWindows1 %HOMEPATH%\Desktop\FileTmp.exe1
File Hashes 0215d4876a89e1e97d9d16fcb8d4293b70874e880da2a790324f4ba1c89fa6770c280a807d5204b88c7b97a0e340dcb7ff02dbfd6624cc604810c827b19bf6ef0fafb3b24927a122e09d985b46892183525e8d2761a9664bd6c315077b8426e322935e7dd6dcac90dcb7bd7c8673d698cf0d9ce1ba17e9521972e6cab3108ba14094a534c91356eb309950a2af41a71fa0946d0cd7805317add9301dff1a7c664dc3b2af98444125472257b2f71757780e397aedb40d3bc2bef6e802f51c8fdb6c859987613e72c57035cfd1366c9459e3a9aab7c91ccdf1f62f72147b3403e1794e30e6c7ee69b90c7c11604894960b12d6e91c9beae00b6eb8afec385a13f38575e16b50af09d45f8c41e53b6536e09eb9afbc8b64f28d53099e13a7e0a185b2d844009088d53d786216d0e2fa7cae6f78e1c5bc0bbd13dde45793d768c285ccb3df8c3b9282df23439b28521c55a02d6dbb26c5335649f5665a2c008fd316ce16cc3411128c2468e8aa4243e06966f13a1bc2d2e1e095cee27385e90793e8cfa8b22f7a6fa856dbd0dc0b7e65f3158aaffa6f5250d56c3359a492ca1ab5b1d71388aa0d24fe340538c4e5afb0a31fc9d0d6e2e1d5a00f593b01c08080d636df7a53b1caffc0b468a6d50e0e0e2702493ef0b6eb301f8056df68ecf77d0998eaab6cf6107294be0dcfa7e7b613f958292b44fcd81ab8cf0689ef8046691bbf
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Upatre-10004369-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 62[.]149[.]128[.]4525 104[.]21[.]95[.]4820 172[.]67[.]143[.]6517
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]hotelduomo[.]it25 villaveronica[.]it25 eusuhm2013[.]org[.]uk25 hotelduomo[.]it25
Files and or directories created Occurrences %TEMP%\3001.exe25 %TEMP%\flashplayer_update.exe25
File Hashes 0bd56e6e6f59c56b7c107cb5c4818d2fba44f5b6d90fbab7cc908277f3ab8fa315dac903808c9f19a7961f37efe828dac86499fe17b387aa6d0eff603b4e84c0178d1a55d207bf045f46c06e1472c858be7fddf5b7e211d8177b4a8055bbfd7e1d79a2799a768478a6ac9111d95de3007db84ae45db838111c639fe120a1b4692084fb1579880cdac8757c9675305e7ec288696dfff8e6d54bc867297506b7dc452e6481a7e3b68b60cf9070f226a226e2f25265fc912c7786a5e9980b2379d6493483be6b18a1eb48c8f4d68540d89ebba2e61f510710ce37baa33acaa1d7324df79454fea97f276930f3f1beca2428e6023667f1aeb8888a06b80507d344135345e4664c128601cd83db03478f1b56b0d243d220523ae06a8367249647b2c45a3a2c4fbd72c6899493fa8b62bffcd11577d0bf08efdca665928b375b6544df6a233b869b6e42631810e63dfbcdc92b9dd2562c7b543c930c1ef03519038914710a55ca42b9ef9157a180f121705b186ca703dcb486cdb409b4c4ed76ae4e417ac9aadae064910cc8dda80676b46a91129fc531c3b4ffa0c76a9d90add55cee7ed5e9c3153bb9b3ba7ef009dd366ade67cdfd03c662dbd9214e7bbf5dcfe36188f7031f98b73d4b64d77cca04ca9da65ab66b4cf4fb0b4aec24f60f74ae2afba0142cd7f3a3e9f9818dec2eed7b8e77adc7839345218fdd1aa36b98b0a10c48b00a23aedf65dbf47724b491d79548b716473d0869bf3da8831e73d96a6cf583b4d850d517edee9687b77db88e95fae97fd3a933afcdd34573a4a53b8fd6c532bc79376797465a0d5372091b3aeb61a60a0156e3eef782c73643c8a054e287aebee9c3f33fd8395e24302b80270f34eb826449f16a3a24bb587e5280fe070bc3c56848ba6e48aa286190532b3db0cbea18fa288dea3c172f7cde56e05a5d5b45d605dfc24d5e87f32eb1183e3d98cf1fe7c9f803da3df91c5007c2ccb2c4831ad76eeea034cbbc2963a8662ae9f8358d1bd8131d411d1fccae5b858baf354f1edbf2e22dc003baf9dc18eb9e9fb2fd4e30e1938e125b4daddc0a7060030fb2f1f1796960b14a1acc6e311f2a4d8396c8cd3314cf633e5c0e45ecc853276aec93
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Doc.Malware.Valyria-10004248-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\RECOVER Value Name: Name 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\RECOVER Value Name: Path 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\RECOVER Value Name: Extensions 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WRDPRFCTDOS Value Name: Name 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WRDPRFCTDOS Value Name: Path 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WRDPRFCTDOS Value Name: Extensions 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WORDPERFECT6X Value Name: Name 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WORDPERFECT6X Value Name: Path 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WORDPERFECT6X Value Name: Extensions 16
Mutexes Occurrences Local\10MU_ACB10_S-1-5-5-0-6786316 Local\10MU_ACBPIDS_S-1-5-5-0-6786316 Local\WinSpl64To32Mutex_10960_0_300012
Files and or directories created Occurrences %LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRD0000.doc16 %TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp16 %TEMP%\tstCB.tmp1 %TEMP%\tst8A.tmp1
File Hashes 107479966d4b35898bdeb753a278f768f528f1c80c7f47b04e6edd03299213da1ba2125381e7bdead242b125c8738cd3f4f76461f49fbac4053ca16e485e4d98305ac4ccfa8247c18ee6d7438b0b827cd3438d577bd21d72c60c85b1b1f238a23ed436702d2164ba3793c060aba4c59deb25a302937fbfe867b59f2f0500e9a74995552476481e01376eb5cc12e37ae790901269426391a8858aa16e098188ed5d2587aa6f25a10fbd3b8fc785a45dba26e5af6e903be60c463260d9a23425e76ff9a9af5fa5dfb6ef845bbf477c51f7f7f353a8a16db6934c30de79ce9e7816730bef2d9ab49edf6b7dd202eb53b9baf1d880e028c77a41bfc08624a28638a278d2d231cd0148c921922c39f55567ef427a70be683d191b7bebebe4a33e6d1f7c9a7b2c38bd8cb013dbd0afa4dc04ed18192b446adce9b90f91e5a9fa63416ba16d9ce88f407d4b6206b8e2247cc34c1c06024ccae288cddffd538bccc0e4cda451ede4494e70fc141fb41bab361e09a38999d2bc5d0892998b4776cea917e1c3544f8a454aa3e1607c27daf1e066f6a46b6ab825732b1cd5b91f03613dc299e18c7e50298f4d2376d4717b47c40d5cc1dc0420e067b689b2f2e89780de2212e46ed5ef523d86713e96e26c59bfcb74e3827088d99789f03cac8a994648d181ffaea1038257ef5cbdc371fecd200670002bf68e278130c3dba13476d61d2f02
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
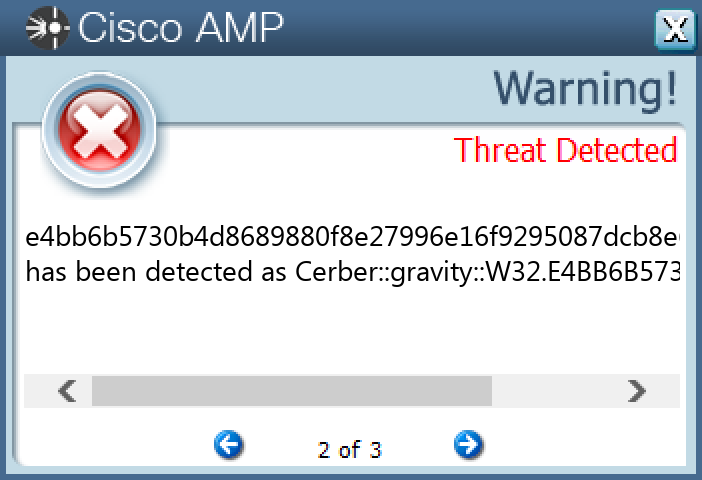
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.Cerber-10004233-0 Indicators of Compromise IOCs collected from dynamic analysis of 23 samples Mutexes Occurrences Global\<random guid>14 shell.{381828AA-8B28-3374-1B67-35680555C5EF}9
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 194[.]165[.]16[.]0/229 65[.]55[.]50[.]0/279 192[.]42[.]118[.]0/279
Files and or directories created Occurrences %TEMP%\d19ab9899 %TEMP%\d19ab989\4710.tmp9 %TEMP%\d19ab989\a35f.tmp9 %ProgramData%\Microsoft\RAC\StateData\README.hta1 %ProgramData%\Microsoft\RAC\StateData\RacDatabase.sdf1 %ProgramData%\Microsoft\Windows\Power Efficiency Diagnostics\README.hta1 %ProgramData%\Microsoft\Windows\Power Efficiency Diagnostics\energy-report-2015-04-30.xml1 %ProgramData%\Microsoft\Windows\Power Efficiency Diagnostics\energy-report-latest.xml1 UNC\PC%APPDATA%\Microsoft\Document Building Blocks\1033\14\README.hta1 UNC\PC%APPDATA%\Microsoft\Templates\LiveContent\Managed\Word Document Building Blocks\1033\README.hta1 UNC\PC%APPDATA%\Microsoft\Templates\README.hta1 UNC\PC%HOMEPATH%\Documents\OneNote Notebooks\Notes\README.hta1 UNC\PC%HOMEPATH%\Documents\OneNote Notebooks\Personal\README.hta1 UNC\PC%HOMEPATH%\Documents\README.hta1 UNC\PC\Users\All Users\Microsoft\RAC\PublishedData\README.hta1 UNC\PC\Users\All Users\Microsoft\RAC\StateData\README.hta1 UNC\PC\Users\All Users\Microsoft\Windows\Power Efficiency Diagnostics\README.hta1 \MSOCache\All Users\{90140000-001A-0409-0000-0000000FF1CE}-C\README.hta1 \MSOCache\All Users\{90140000-002C-0409-0000-0000000FF1CE}-C\README.hta1 \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\README.hta1 \MSOCache\All Users\{90140000-0117-0409-0000-0000000FF1CE}-C\Access.en-us\README.hta1 \MSOCache\All Users\{90140000-0117-0409-0000-0000000FF1CE}-C\README.hta1 \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\README.hta1 %ProgramFiles(x86)%\Microsoft Office\Templates\1033\ONENOTE\14\Stationery\README.hta1 %APPDATA%\Microsoft\Access\README.hta1
*See JSON for more IOCs
File Hashes 014df8e6a9101e4bb3264ac22b8d9cc7e52d347345ed4c0b1cd14d74f274c8fd44928f1ae73a27aa1efb8090ae480e0170efe804e20e326b670864e163db142745176a6084162f91e5bb0c7ecad4df0cf74c3d0b2cd4068d1e6cd955daef373445790f44b1fdb4bb6b6abad4c546c2cb123fc1ad6e24b2a628d1e8f1935fcade45b258b3964c4a1a669a1b78abfd9c65482008517a1a8cf2b701372793e01b4a6dd5b22b53d2b2188190fa41ecf428fbff415e647f84b6c2f99dc9173380bd2a6e70ebf060d8eaa7082daaa93cf93e7e65fe2cf28ae1cd32de9e4b5581c24a8675c07c449e5feaf70c3281fa229fea8899f4dce2679113590ab4bafdaee2eb817a7b239613d44d0b690cee93022de0a4171fc2040e6eafd6002fbd4a77f1685b833f575a4adeab246ed7d030c7a6d04c6d9111fda1718e02e9806d429d6dc1819f51c07df0b2abfa2fa3a57039d887563694b41e85eb117e6089480ea37345b4a197f793517d4d1434ec520b1222022f78631bebf6ae1b97455969c0b073ff17a80053812cc6891019818d073908f9e1c4c9a6b0c7463c57df063efe1ac0c834aa7ca754bdd16d64f5f056b1168776d53ea277533ff9ea11ef9b39a59dcbca18b0edafda97209ec938343ecdbc4f37e8ae504ca25a7ed7b3b9864351527c5d76b4d519e8832cd8099d0d25b85356aa3f920d80324d21268b8bbaedff2338b14cc119aa10c3c7c13b42139247e4f1677b769bbc5f349a12fad8367ca6ef8ca5d0c9e36700005e5626e60c259b805c30693d1350f3bdfa20465ebbdb6af1b4d724cbd226056cb33b29094eed23dcf9311952da3675350d934a0014c50b2e2e27c5daf9fd8e34e9dfb0458ee5f1797316c67b7066a3a99393f8db3a96e86fd61dc4dec9b3063fbce95033b844f69145d05c9911986195c80a9e1d69128d411b2653dfccf92c7ab071fc8a664e4faaecc299dc3a0f10c4ff345d64c7364906d77533e4bb6b5730b4d8689880f8e27996e16f9295087dcb8e612cf80c9be1c5b81c68
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Virus.Ramnit-10004200-0 Indicators of Compromise IOCs collected from dynamic analysis of 21 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\VOLATILE\00\MACHINE\SOFTWARE\CLASSES\TYPELIB\{8C11EFA1-92C3-11D1-BC1E-00C04FA31489}1 <HKLM>\SOFTWARE\WOW6432NODE\VOLATILE\00\MACHINE\SOFTWARE\CLASSES\TYPELIB\{8C11EFA1-92C3-11D1-BC1E-00C04FA31489}\1.01 <HKLM>\SOFTWARE\CLASSES\MSTSCAX.MSTSCAX.1\CLSID1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{A41A4187-5A86-4E26-B40A-856F9035D9CB}\VERSIONINDEPENDENTPROGID1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{A41A4187-5A86-4E26-B40A-856F9035D9CB}\INPROCSERVER32 Value Name: ThreadingModel 1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{A41A4187-5A86-4E26-B40A-856F9035D9CB}\MISCSTATUS1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{A41A4187-5A86-4E26-B40A-856F9035D9CB}\MISCSTATUS\11 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{A41A4187-5A86-4E26-B40A-856F9035D9CB}\TYPELIB1 <HKLM>\SOFTWARE\CLASSES\MSTSCAX.MSTSCAX.21 <HKLM>\SOFTWARE\CLASSES\MSTSCAX.MSTSCAX.2\CLSID1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{7CACBD7B-0D99-468F-AC33-22E495C0AFE5}\PROGID1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{7CACBD7B-0D99-468F-AC33-22E495C0AFE5}\VERSIONINDEPENDENTPROGID1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{7CACBD7B-0D99-468F-AC33-22E495C0AFE5}\INPROCSERVER32 Value Name: ThreadingModel 1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{7CACBD7B-0D99-468F-AC33-22E495C0AFE5}\MISCSTATUS1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{7CACBD7B-0D99-468F-AC33-22E495C0AFE5}\MISCSTATUS\11 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{7CACBD7B-0D99-468F-AC33-22E495C0AFE5}\TYPELIB1 <HKLM>\SOFTWARE\CLASSES\MSTSCAX.MSTSCAX.31 <HKLM>\SOFTWARE\CLASSES\MSTSCAX.MSTSCAX.3\CLSID1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{3523C2FB-4031-44E4-9A3B-F1E94986EE7F}\PROGID1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{3523C2FB-4031-44E4-9A3B-F1E94986EE7F}\VERSIONINDEPENDENTPROGID1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{3523C2FB-4031-44E4-9A3B-F1E94986EE7F}\INPROCSERVER32 Value Name: ThreadingModel 1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{3523C2FB-4031-44E4-9A3B-F1E94986EE7F}\MISCSTATUS1 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{3523C2FB-4031-44E4-9A3B-F1E94986EE7F}\MISCSTATUS\11 <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{3523C2FB-4031-44E4-9A3B-F1E94986EE7F}\TYPELIB1 <HKLM>\SOFTWARE\CLASSES\MSTSCAX.MSTSCAX.11
Mutexes Occurrences Global\SYSTEM_DEMETRA_MAIN1 Global\edccfa21-0855-11ee-9660-00151741784b1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 107[.]6[.]74[.]761 142[.]250[.]80[.]461
Domain Names contacted by malware. Does not indicate maliciousness Occurrences google[.]com1 zahlung[.]name1
Files and or directories created Occurrences %ProgramFiles(x86)%\Microsoft Office\Office14\Groove\ToolData\groove.net\GrooveForms5\FormsMacroTemplate.html1 %ProgramFiles(x86)%\Microsoft Office\Office14\Groove\ToolData\groove.net\GrooveForms5\FormsPreviewTemplate.html1 %ProgramFiles(x86)%\Microsoft Office\Office14\Groove\ToolData\groove.net\GrooveForms5\FormsPreviewTemplateRTL.html1 %ProgramFiles(x86)%\Microsoft Office\Office14\Groove\ToolData\groove.net\GrooveForms5\FormsPrintTemplate.html1 %ProgramFiles(x86)%\Microsoft Office\Office14\Groove\ToolData\groove.net\GrooveForms5\FormsPrintTemplateRTL.html1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\IDE\VsWizard.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\IDE\msdis150.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\IDE\msenc80.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\IDE\msenv.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\IDE\mspdb80.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\IDE\mspdbcore.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\IDE\msvb7.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\IDE\vslog.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\IDE\vssln.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\IDE\vstlbinf.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\Packages\Compsvcspkg.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\Packages\Debugger\cpde.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\Packages\Debugger\cscompee.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\Packages\Debugger\shmetapdb.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\Packages\Debugger\vsdebug.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\Packages\dirprj.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\Tools\VDT\vdt80.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\Common7\Tools\VDT\vdt80p.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\VB\Bin\msvbprj.dll1 %ProgramFiles(x86)%\Microsoft Visual Studio 8\VC#\VCSPackages\cslangsvc.dll1
*See JSON for more IOCs
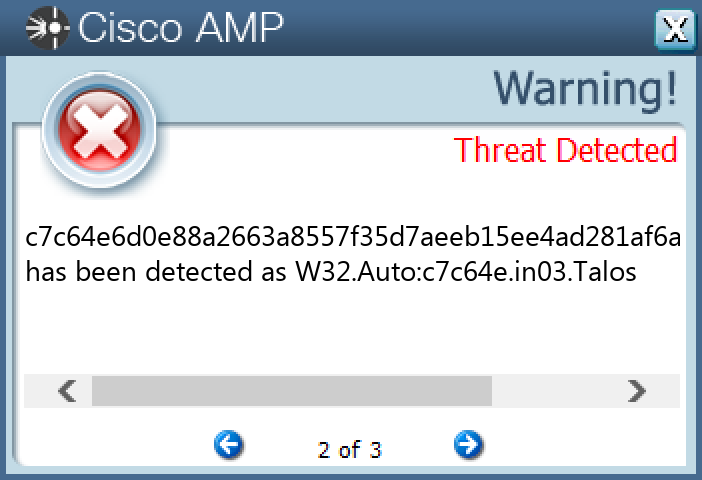
File Hashes 182842a0a84e56435b8f7a625137a0d1bc0ab44be0df60bfe44d8b560842c93924d69cf7dd629250d0cdebbae146525ec9db913b596c9c21ad22a7c54d39c9a33f9cdadb6bdffa0259111aef35af5b1cd49900a024181bdfaca49e00162edb8b438259174450f0a034eb3356e5cd9fde06468fd71369fcf350d78ebc99e0a9ce4adc301787ef8f4c954e69d7ef629657366e17f6a891c33c1eee3a83a7f64e9c593487ca56545968d3b79d6d945f0747938b5d7c2fe3884e2e1d9bc0138f3af26d2133f6563cff051a57d19c50875a799b2490b686a7f1d11d2c13b342243509755f131bf7d3438c2d49127dbce152bbb66b0954602775fa58d13a1584a435518202953b0fe4d73156bae712ab5cc481d5bc9134745dcd5b8b5c50e18a5500f383cc953df29bdf1a059cce0966a6f31defebc4c5709d149f38fbd3e04c7a0e8591e436eb7463ff9ef416858a0e46b73fd4a8e738b504b7f8ebb27283eef65d47a0bc4dc1f8cc7615a66d62afef67d2eee6af39c0ba59396bc5472c726474ae49a24fc35cad24e3ed2357528adf84cc03b77205de39ed4e6922b676282150597fa291dfed9100241eb471c331f70ac8b5c6c323d79e1252055bd7aa4e31c62be7b29e1261cf467039caf09f2b63254c88a9cbca4fccbad91a5009572cda59e83bc7c64e6d0e88a2663a8557f35d7aeeb15ee4ad281af6adfe1a26ca11b435ba9cd66f497dcf49c54ca5ebeb7d6f19dc65e959ddaf288bb477884f5394c035bea1ea892a3dc73f8dab3a84b24f88b843600e8357fd56d85f9fc90fb858ec2c4fa7eb803216f92e5bf2cea2320d9e9490eda37655f6d51971a6ea83f99bf62c875bfceccca0f030731609c20119d192627e92b55963e82ccbae5aab42cabf139e41febb2993cbbb1593e630bd7d814115518fb038d81497e9945cb3c5da3de2d9ee
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK