Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 16 and June 23. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
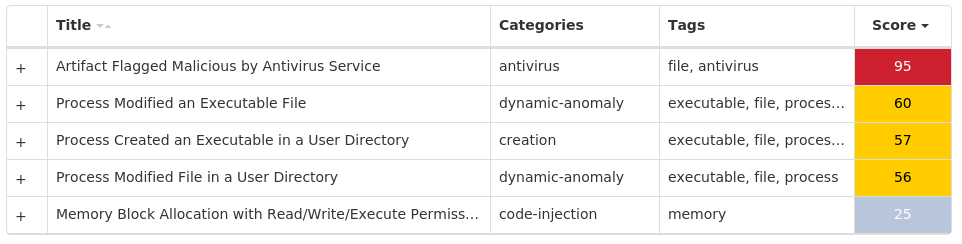
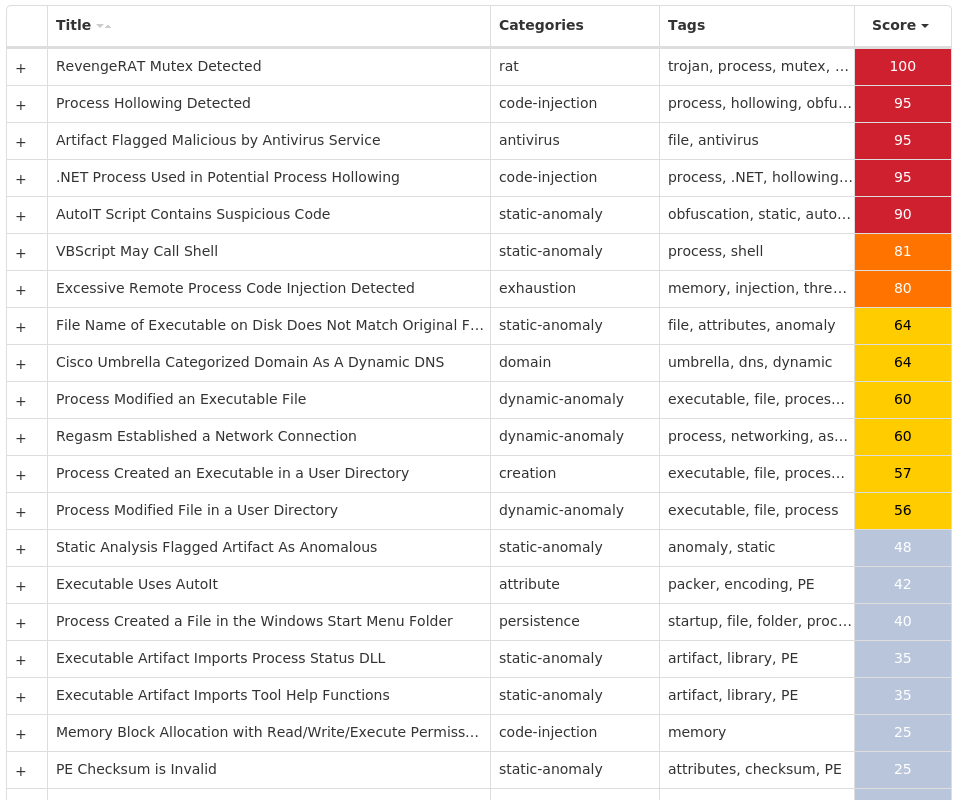
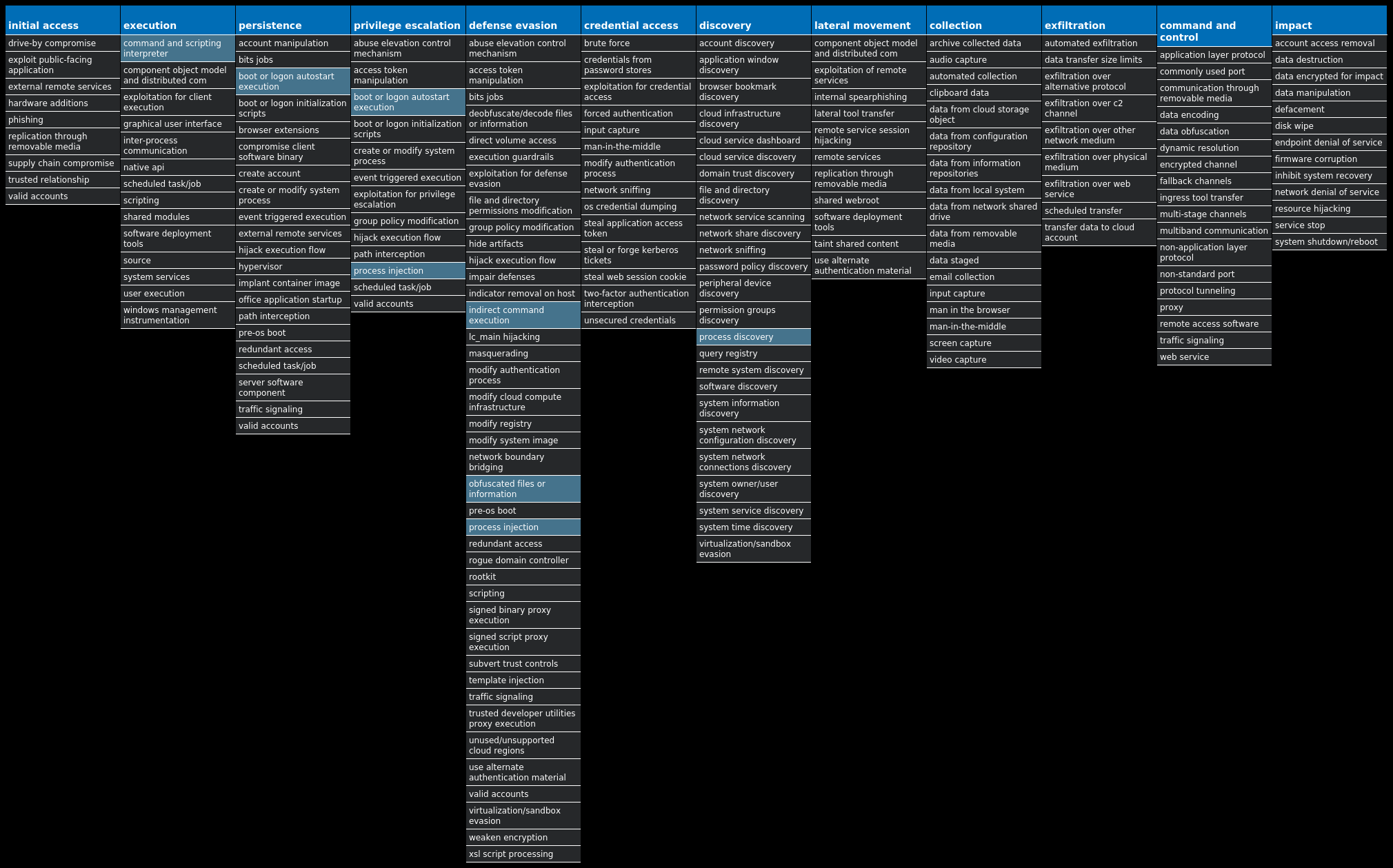
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Downloader.Zbot-10004448-0 Downloader Zbot, also known as Zeus, is a trojan that steals information, such as banking credentials, using methods such as key-logging and form-grabbing. Win.Dropper.Kuluoz-10004513-0 Dropper Kuluoz, sometimes known as "Asprox," is a modular remote access trojan that is also known to download and execute follow-on malware, such as fake antivirus software. Kuluoz is often delivered via spam emails pretending to be shipment delivery notifications or flight booking confirmations. Doc.Downloader.Valyria-10004543-0 Downloader Valyria is a malicious Microsoft Word document family that distributes other malware such as Emotet. Win.Dropper.Tofsee-10004548-0 Dropper Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and send large volumes of spam messages to infect additional systems and increase the size of the botnet under the operator's control. Win.Malware.Bublik-10004580-0 Malware Bublik is a downloader that targets Windows hosts. Although it's primarily used as malware to distribute various banking trojans, it's also capable of extracting and exfiltrating sensitive information from the host. Win.Trojan.RevengeRAT-10004611-1 Trojan The RevengeRAT remote access tool allows the operator to perform a wide range of actions on the infected system, including eavesdropping on the user, exfiltrating data, and running additional malicious software. Win.Dropper.XtremeRAT-10004704-1 Dropper XtremeRAT is a remote access trojan active since 2010 that allows the attacker to eavesdrop on users and modify the running system. The source code for XtremeRAT, written in Delphi, was leaked online and has since been used by similar RATs. Win.Packed.Upatre-10004837-0 Packed Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware.
Threat Breakdown Win.Downloader.Zbot-10004448-0 Indicators of Compromise IOCs collected from dynamic analysis of 29 samples Domain Names contacted by malware. Does not indicate maliciousness Occurrences pro-viewer[.]com29 agrimarsystem[.]pe29
Files and or directories created Occurrences %TEMP%\realupdater.exe29
File Hashes 053a330f699d8c4699b1c6bc7ec2f2a2bd6b9257c4a0eee8d514b2ad4b55e88c096401e776c273e5c580f401cbaab5d2b74a1541299d8d0add5d99d68866958c0a0e51d77206354a7a525c0ca44835e7657ec25378f814ae0ecab0dee94a98000a43fe36f8e691f067eb8b2fc41a186c53808c6e606d31c66360a2778497f7380c555bbddffcc35759b381e0508cf0666fc1b0f9e5aba0d6f5f125c42acb903b0fecc3ec5645e4b7d93650d5ddfcbe87705828aefdcc3125ad3fb1136178070315156356f6965001ad4f3cc867352f5c9b4c5bed56b16a9562e2f6d5ddd1f01b15cd28a2bf63f2d5398e6ff68bb2c18a5ccab0deb03dc875d6113520a2f82b4d1d292629b26d830c600d93d71e944daca4d84f57a065f3a24f30e2faf5d56809227c80b9ffc7b3aedb0331fa2c558e5691758a11c1409b3e229998ee10477481239cb1e55ddbb69bb3d00572d58384aadbcf2a6fa609b69fe761220bb5ae7894248625ec043b72d80c240b9513123a05fe9066756e76c846a7ff3413e782341627700ad54347a4cb183652fb686c4ea73ac6651b3a6af40c694fdd0a632922b928959a0fac78cefae567abc5fe3cd33183c26ba73cf349befe43ac832848022a3a3283e24b8693a60341593cf3d57e5e279305a9607d30ca8b948fd9f866eca8518253b8c0fad2934c8d06195a63030b99b7bfe2962fe42248b9e5572e435e5953d4b89860e7b7cc296cd5917d46a9720b8b0baacb7b31db7d571e61c591a1815936c22f97b9933088de3d142707736a64744e81c372183f8fee986328d919d55d75c21c11022d4fdfc7fd6591b59111982aa567bc69e3fccf6298da1055b5155de5879da208a90f46d08c6bb416a5a2f78c804ea20464dbabc34eb0390aa4f56103228f4365322d5ceae300620cc66fbf84eb9dfdbc6a0022c268dc83aa65a663ab006084041b1b6bf6f260f412c34fc56664a3a2ab0faf6a454233530b2e5d762d6eb6820eefbf2e46e2174a9ada9841d3ed55a09ac3d62fd97a14077304df79b060e8975e684bda3cf79b45ccf9389b5679cbef2cb63656b94ee2ff34f5e189ba7325f5bcd26a21c89daa30726013bb6d59812ec104b81a7229024f91510d
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
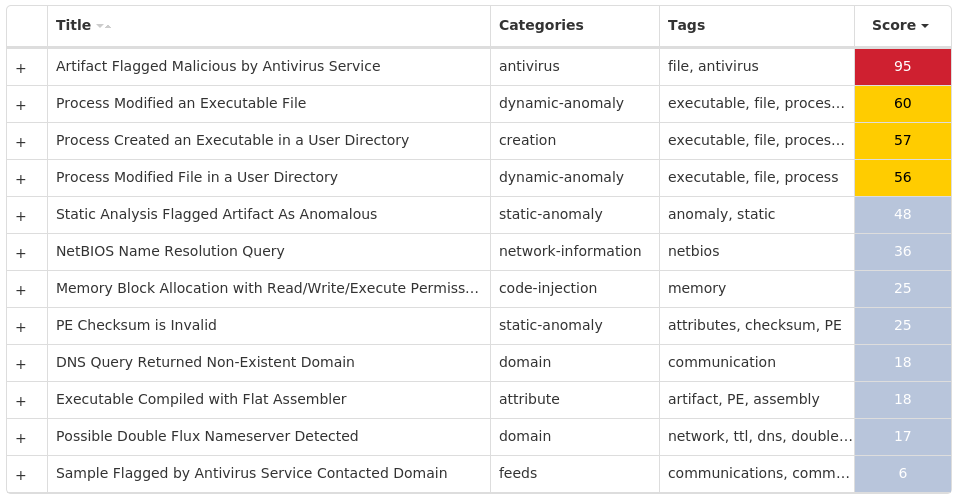
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Kuluoz-10004513-0 Indicators of Compromise IOCs collected from dynamic analysis of 43 samples Registry Keys Occurrences <HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'>43 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ewdtednn 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: kfgsdpdv 1 <HKCU>\SOFTWARE\XLWVBVLN Value Name: xtxmwque 1 <HKCU>\SOFTWARE\ERIUEKCR Value Name: dwpjqlpa 1 <HKCU>\SOFTWARE\FKGDWLFC Value Name: btcgqtxv 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: pwjcpvtg 1 <HKCU>\SOFTWARE\TRDDWSJW Value Name: hkwogctf 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: lwrnfwdh 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: btomjvqp 1 <HKCU>\SOFTWARE\BUGITDDP Value Name: txxsdgjg 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: doviudox 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: tuqsrtec 1 <HKCU>\SOFTWARE\EOBOTIUK Value Name: ulgvwopi 1 <HKCU>\SOFTWARE\PILXJFXK Value Name: ktkriwfo 1 <HKCU>\SOFTWARE\IDCCIMKF Value Name: tmumianw 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: lwkqralw 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vuemrbob 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: rssaalxp 1 <HKCU>\SOFTWARE\EFOKESHU Value Name: xulsnjws 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: fllgmrwq 1 <HKCU>\SOFTWARE\GIEJFQCE Value Name: iuqwifxx 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: toqdahjd 1 <HKCU>\SOFTWARE\ELNQDQUF Value Name: uhvnsbhc 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vtjkaseh 1
Mutexes Occurrences 2GVWNQJz143
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 78[.]157[.]209[.]22828 85[.]25[.]108[.]16427 94[.]23[.]84[.]9426 94[.]32[.]66[.]5625 177[.]87[.]64[.]2522 109[.]169[.]46[.]5920 176[.]31[.]110[.]16518 91[.]121[.]98[.]6016
Files and or directories created Occurrences %LOCALAPPDATA%\<random, matching '[a-z]{8}'>.exe43
File Hashes 04be2d1165429f6a1fc8217db32e549eeeb54983aa4c44f26e1147d054d954e10672e260b9febfd47b8536c8cd17866dc5cad82fbd9acf6778225c69617f8df413f0e1860121210bdcfd59887053156fee80c0e7e61ad1b2109a3ca027060ef5161dd94d902139168107ee72aa66fc2bb00ecbe72a9ea3a2645a2e5f3edb43bc1c5e6a11a293501d1bd41d302a7cbde8e8efc67916e4a063a5757f476190c48f31c10bfe9039675974640b3404fbbdccf660bbef3319ed011766f4e7e2dc6d4834861226330e4af50b8e03f6e9d8457ff1d1c9a7d3eeb1fc930a9f70a315dd54360e964ae4aaf043ea27780f20ab266bf55470e3d58fa20550c9f2c520823fbe42657321367294c31f060614894a0f13b1f38613cf3e013c94a835496e86a53745bedf4f08cc21eb94088a7ebd942915d8e3f834d0632cfb9264d92228c8a4f147ea467e5da54049ec9c40d2173a97fb87dae67546faba7dce0631ad88fa3fa947f9eabe7f83bbce4b0d52282ba627f678ecc48604201101f7650ecc72a3b7146ceeb2ab8b3d41fb927e0ffdcada6da07cac54124cdb8f0c9de15553a4254af575ed32ca3cc84d402a91fb13088ac3421917d427efb55bf2442b71f6dfd6a3987ef5f3c744b456b04c79e14c5923a7cfbc3894f14a473a564d843dce62293b5a86497472773d474e05b8ecccc82dfd17d7a4ad6c38e6911d03d6956aedadd49a92f407eb8a0b4562acd7f1c27c86ed365b37c37bbc2fda343efd0fe22ea73bd195528ad474a06ae5c23200fac691561cae115466dd07e7f60cb5e9bf667443f597fc7992ceecb79f0e43c702fc69a564941b9c909ffd422a7af6a8d1c575ffdd9f8eaa58bddf52d4ebc3603f00b6b19d76fe5ae486a308ac7d21330486fa0f87a23c17fe1c893ac18bcc2d524adc6b8be07ee6ed2277701d2b43a1681ba60a29a3a34b395a54043f247e09b8f6656ed66c74c6d02735e49a87e118749a1daa37ac097abc44ceac4f6f0b6a33e876a76284a9aad676ce924bda277925b3f12bf5ae08cd70435a6eacc7097babc6c26ecae3484bf8ca73ac1ae4f8078eef69d017ae622c4057b66fb39cc1a341f50ceaaa7146fe4c1e06d0d6e316547cff821da4
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
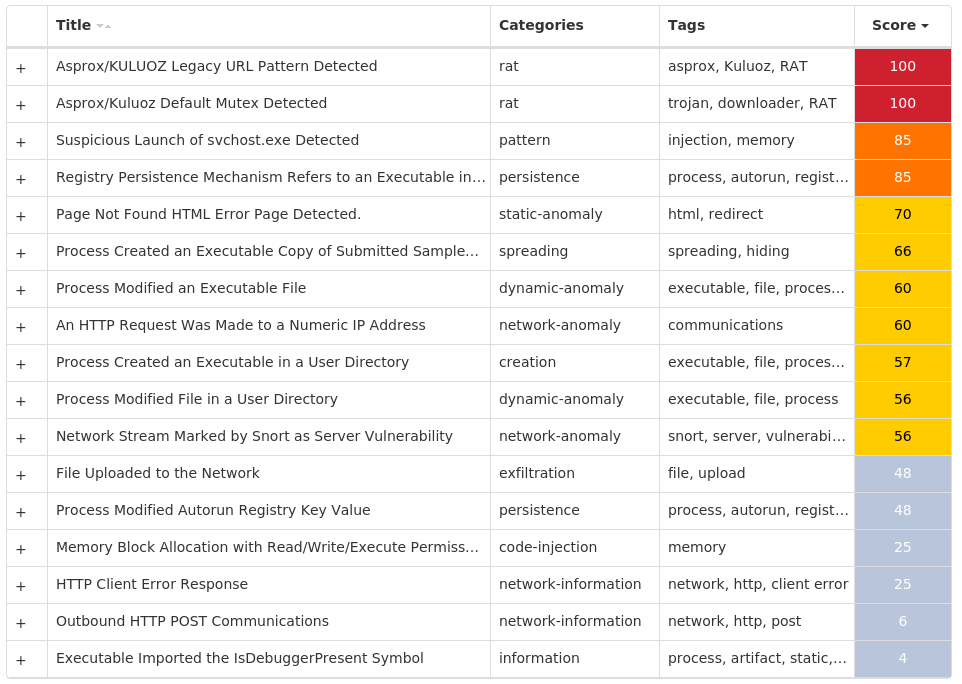
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Doc.Downloader.Valyria-10004543-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\RECOVER Value Name: Name 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\RECOVER Value Name: Path 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\RECOVER Value Name: Extensions 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WRDPRFCTDOS Value Name: Name 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WRDPRFCTDOS Value Name: Path 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WRDPRFCTDOS Value Name: Extensions 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WORDPERFECT6X Value Name: Name 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WORDPERFECT6X Value Name: Path 16 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\OFFICE\14.0\WORD\TEXT CONVERTERS\IMPORT\WORDPERFECT6X Value Name: Extensions 16
Mutexes Occurrences Local\10MU_ACB10_S-1-5-5-0-6786316 Local\10MU_ACBPIDS_S-1-5-5-0-6786316 Local\WinSpl64To32Mutex_10960_0_300015
Files and or directories created Occurrences %LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRD0000.doc16 %TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp16
File Hashes 03467831309586db00451ece187de1b4294ccfe4df9c3a44b554632b5bf42be7168707fcadc59088773a10141ea7a5d4d586e345e6637c6f831df0423f330f612651e81960ba8b4d9f71beff3402bfe03e4bc5a328b9ccf58a49fa10e70297202f2ced0420e68ca325fc6a4c03bec2945b0164ed7cc4e1f3fbf4ff1e8baa92af3324bb313bdf400aa777d05e8f7d0368c708c45857661fb75d5d89a7fb8ccfdb4fa10efe326beacbacd2fd9751b69fa54a3086454e627c6be454bfb4760e09cd688d6753c1d46a3f0938b3eb151b48ce50b191477ee048af86944a84fcef9e707681a084c13f352046dd0d519198210ecf0ac7d5f821e629b39eb7aa8ba0d3427efbb2480cd82231f9d9c81e40745ecb2aa0c7228ad6383a8b929215bed753ff8cf066b7f08cc018e28fff8b6de40d86382967ea5c63df2fb2dc3e8e0ee46727a0ee2881f4992d7f256b824fb535cd19524d487edc590951cc7c47164aee1db0a2419f02381d9e7301ae637aa4e5c905f7e1d81d92fbf893e8ef68754bf08305b3eb9b1a7c972460fa7c9fe3aa911cc505c5b4b9804d6c71678da99c178b6d18b78259b174c68679a885425d64d9d8c46c163358b658553533f35f08e696b937c07dc139b1d0a717071bccb552bb394afc3012f960cc182d7a934144492d6520e7feb77a1b6b712a0c22e855974f564cde98aaa927ea989aa8747bbb5833f321
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Tofsee-10004548-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKU>\.DEFAULT\CONTROL PANEL\BUSES15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Type 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ErrorControl 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: DisplayName 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: WOW64 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ObjectName 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: Description 15 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config0 15 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config1 15 <HKU>\.DEFAULT\CONTROL PANEL\BUSES Value Name: Config2 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'> Value Name: ImagePath 11 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\scezvnmi 3 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\kuwrnfea 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\tdfawonj 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\qacxtlkg 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\isupldcy 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\wgidzrqm 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\pzbwskjf 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\cmojfxws 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\dnpkgyxt 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS Value Name: C:\Windows\SysWOW64\lvxsogfb 1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 91[.]203[.]192[.]7815 80[.]66[.]75[.]25414 31[.]13[.]65[.]5211 176[.]113[.]115[.]13611 80[.]66[.]75[.]411 176[.]113[.]115[.]23911 176[.]113[.]115[.]13511 45[.]143[.]201[.]23811 176[.]113[.]115[.]8411 31[.]13[.]65[.]17410 142[.]250[.]176[.]19610 157[.]240[.]205[.]638 5[.]61[.]236[.]2358 34[.]117[.]59[.]816 20[.]84[.]181[.]625 77[.]75[.]78[.]1045 104[.]47[.]53[.]364 20[.]112[.]52[.]294 104[.]18[.]12[.]334 104[.]18[.]13[.]334 93[.]115[.]25[.]104 212[.]227[.]17[.]1863 104[.]47[.]54[.]363 104[.]16[.]120[.]503 142[.]251[.]40[.]1313
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences microsoft-com[.]mail[.]protection[.]outlook[.]com15 microsoft[.]com15 vanaheim[.]cn15 249[.]5[.]55[.]69[.]bl[.]spamcop[.]net11 249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org11 249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net11 249[.]5[.]55[.]69[.]in-addr[.]arpa11 249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org11 249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org11 i[.]instagram[.]com11 www[.]google[.]com11 www[.]instagram[.]com10 api[.]youla[.]io8 identity[.]bitwarden[.]com7 login[.]szn[.]cz5 78[.]192[.]203[.]91[.]in-addr[.]arpa4 api[.]debank[.]com4 www[.]google[.]de3 api[.]twitter[.]com3 imap[.]gmx[.]net3 in-jsproxy[.]globh[.]com3 www[.]bing[.]com2 www[.]yahoo[.]com2 twitter[.]com2 www[.]google[.]co[.]nz2
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile15 %SystemRoot%\SysWOW64\config\systemprofile:.repos15 %SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>15 %TEMP%\<random, matching '[a-z]{8}'>.exe13 %TEMP%\yhnywld.exe1 %TEMP%\jsyjhwo.exe1
File Hashes 044c17fc7e490ab96ab3dccf6175835de270084d56655f52ec151d4401620d0d06e591c1937a87cf3cb761600917baec71b79e735d4f709b61de0e498d3e341d07d4da3a27188a788540f90c842de1d2bb6afb225c1a7d131a54e40bf511fd500cb53f5d3a4a05fb3194456f40cbe544d5756a472a8309baa3e057ec05a67bf219b0a306ef0d0410815f39e2276bd5ae2ca123229b7c542fd3b72d457dffcd44395f1e0d90a33b3ae5a53e6c3681dc78ee92049f47fb0730e7125b0d8c864e3a3a94a34b9a894ae78e3b3ecd80696c38d4365586ec04fb3b11792d3bd50b32e14a69cb97a79e0847fb09982fe2f1a882c8747bd31e35d7d5cdadd4c10abce6234bcb95f3d5f545d546036460b6738428a9ed2b29b0ef47a9dcef958e8481ef8155d72870eb0c4f64fa1c586856e93a470718497a5145e4c73407e55656968b5a9ed0459acce7f212e4a05c8dab6924927c070985ac2290501744868fbebb0a05d92be544ba54da794f253b8341715b09c2fa1b79e90492ab30ab3fad0108457de69ab82896844467cb51d5f4e374eda1c27424062830dcbb7bd040e6bfb4e13bea1e4c113df6a534213ddd95745d5d39b9064cd80dbe9f8c0f5164e14cf83d55f99c02ea4c0ffa3c2d792df9a040fe3deabafb56cae22d0995116f962037c587fc98619ec7847e749b3865dec97103f7a6f2eccbd0af1b5f9172e39ef183d139
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Malware.Bublik-10004580-0 Indicators of Compromise IOCs collected from dynamic analysis of 118 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 69[.]10[.]32[.]149118 66[.]23[.]234[.]229118
Domain Names contacted by malware. Does not indicate maliciousness Occurrences double-six[.]com118 cocoon-beach[.]com118
Files and or directories created Occurrences %TEMP%\gike.exe118
File Hashes 008272d4b93a5cefd6943952d63388198b67a34e06a93dca0e9698c0639f4f02017c9042d7cfab02d6444805d617bfda04a590d8ee0131f0dcbb73d9f422264e01d019832f6f09a0eab7ffcb294466825148ef642519b37f225cea25fd8ccd8205878e434aefab9098e57e734d21ba96eb2731dc2022e7619ff42e6c283ac1c507f8041820745c7de03ab380cdbc33fad9da6c9e87243ce4d6af1664ab2e5cae08de6b552e704a0bb100dcd244c0950ffb90d7d021d042f3bad4b66eab1c633b09e30d34ef79c10fd0f431ba287a8e89ea08c7919501a42e95ddf0b02b7a54dd0d970e4dca39e6ac5d389f25ba528eac251bff7df4c15aa85e96d3c680dea37a1078763c2070758f2d7af2a32cfeac195b1b19af9d7f83433451469a6456d69a116eb648e4098b4994e20822ae2dea5f9a05bf280774e96e7f17537eeea128c1127769bcc6688cc1c682313689d4c0ce7915a8295797a90f4586fb379694c3fe12d38c601be82a710b29744fa9856add702bba2c1cfc9d8f36726df449fa90ea146acf9b7a358237258cebeaa0870b7500c470d65855832a79ad1858de485ba415c9b7a21edfd29a057d881d7f4a98405dd530122b29c7d5ab15042b9f25536c163a3b460ddcdb4561169c9466d48ded8d4535e34e4d51fee2713f6f2006f472173272cf5e8e9349b8d4ff45e6f9378fbfcd437bfaa10fc5c7b7d8adabdd998d17e0b0e3be6ebbf026d4b7ff6da60925516f6b29e2b5f5bfd33f49544659d0311895e011ecb8c5efa5610c55e27a8f32dd6d4e2e24aad0f7375c6b22b13a367318b0fe90a4749d21a70e7775e456f3b258638de1b10dc7c8dfad2c87bb4b4150193de0289b48eec0d8da266d3f1ff3e5a265fa72cff2db27b45a96f58f8f3c60195c1acc646ec1f37bba891e6b6448734361ce77b79e99cb7f3d6a54e5265da11961cf9e8b78d5a638cf76bdaa2144a559056acbb97c7658cd3e3338016ff1f81ae225224fdb2f8a7ecd7420c3b5f85600b87445e6ac9810978e8f21fcb8de3d1b16fc65b34fb4cb5de9a4660bc53f3c4f27ef2d69d88f82e150eca94495471a1b21be6f06de9138a7131f2c037d1cf3aafb0cbc7e05f9e7111649593cb3f736
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.RevengeRAT-10004611-1 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Mutexes Occurrences RV_MUTEX-PiGGjjtnxDpn25 cacls25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 186[.]85[.]86[.]13725
Domain Names contacted by malware. Does not indicate maliciousness Occurrences marzorevenger[.]duckdns[.]org25
Files and or directories created Occurrences %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\AudioHandlers.url25 %APPDATA%\at25 %APPDATA%\at\AudioHandlers.vbs25 %APPDATA%\at\MicrosoftEdgeCP.exe25
File Hashes 0117e5f0ed99601ec0c14007fe47f9595c1c8eeb1e02ddec403051d930fd75e9015bb3bb231fcc3c3d713891ab7f6e38aaf58df3b071c013a0a7b6c45eed736801ad4793cc16f1a08ea244cbfa95f140591d34069a2195816afe15648a7c505d0309ad59c21006514055ef9354e2dae635c26d3c2d990559615526a9fe72ff54032ec8facc409ce44eb692039a972d305213033060b16c0b74a4e8c4612b15d3042d6522cbe511cb76ba9e2541765697c444e149461fc5f16d0f836fc837d934049b5956595ccc11469be36bb2486c84491ff6caf63480a9f5e41dcda29d2e6a05fc5d966f35135922a80ea79a61bdfdbde06ac33a8f02f8fc8928831208b03c062a17b83b98fb2fe0263a1a24c4ebd04545a7503fbeba00bac6abe24905b79007827334bbbbd7bb30a4a0b18eedfad4cedb9a95165e74203ddc57af8403600708e942f92597380308bdf60888cf976732fe581d73b06bcce1414acf72ff23e9096c931004be830b3447cbd1e311c5b5040d06aa37e5b15e2a03a67f87e5c5d20ae3a8fe5d4d198339a6e0ac66db05aac82c3fabca4c94e5073b5fcc9adc33d60e0866a83d3f643b698ddd1110014afd436509d6e43282f8a95b9b29c876f4fd0e41b57c5d12757477f5a55a6ef4249382cb00b9647d16b4088020c77d9d4bf0107375aeb10e843e51c1f58395d0d116f866564b225d41acd0ba673ffaa521f3123fb6d0a6007cfc3bfc66afbd4bf783c3c2a178a61052363a9bc4a1a6dbbe9e1248073a0c941d199fb86632cd612d42f7ea6c7000c66162eac5e254298b6c0b127bd3b50ba83a61fa6d2e578ae65a7bf35582f9e3c91aaa26e346feb8d4a8fd12bfae2e5e4d8a4e8966677ff4235a56fca5fbfeb5abd71b8d4b469358db7558133b506e59475c536601b8121c75b5060c3de8a12f7d94e5980903af85fc6f6a1425ef0c15d0d2d9a791c5cbf94ced34972ba6f6f44490a4cb5a82bcfd2f8ded1533454353df127eb59613f0adbcdf7f2f5278b97cf59bcf815e0bd675edc5a01615738e28738e78deed28921851783adc75a45e5f7258be1802e98d8f889f5a16659f71c91f7a0bf4dfb354dc3222d128159d8862febd0810564c606d4d4b26
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.XtremeRAT-10004704-1 Indicators of Compromise IOCs collected from dynamic analysis of 11 samples Registry Keys Occurrences <HKCU>\SOFTWARE\XTREMERAT10 <HKCU>\SOFTWARE\XTREMERAT Value Name: Mutex 10 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKLM 6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: HKCU 6 <HKCU>\SOFTWARE\6JHGESKCRETMKY0GNF3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{4J2HF5HQ-7067-T665-0KA3-I527GLTEG0RC}3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{4J2HF5HQ-7067-T665-0KA3-I527GLTEG0RC} Value Name: StubPath 3 <HKCU>\SOFTWARE\6JHGESKCRETMKY0GNF Value Name: ServerStarted 3 <HKCU>\SOFTWARE\--((MUTEX))--2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{UDSJO3L5-XD46-H5T2-PNM2-886W401Q2WFR}2 <HKCU>\SOFTWARE\ZMZE16K9PQ2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5TT7UVKI-8JUS-13K8-RDC6-4BUSL8303LK2}2 <HKCU>\SOFTWARE\ZMZE16K9PQ Value Name: ServerStarted 2 <HKCU>\SOFTWARE\ZMZE16K9PQ Value Name: ServerName 2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{5TT7UVKI-8JUS-13K8-RDC6-4BUSL8303LK2} Value Name: StubPath 2 <HKCU>\SOFTWARE\--((MUTEX))-- Value Name: ServerStarted 2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: flood 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: update 2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{UDSJO3L5-XD46-H5T2-PNM2-886W401Q2WFR} Value Name: StubPath 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: floods 2 <HKCU>\SOFTWARE\DHA1Y0SUCZS1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{BWTHDBX6-O60P-1046-3686-46E7X3KCQBDG}1 <HKCU>\SOFTWARE\DHA1Y0SUCZS Value Name: ServerStarted 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{BWTHDBX6-O60P-1046-3686-46E7X3KCQBDG} Value Name: StubPath 1
Mutexes Occurrences --((Mutex))--4 6JhgEskcretMKY0gNf3 --((Mutex))--PERSIST2 ZmzE16K9PQ2 ZmzE16K9PQPERSIST2 ZmzE16K9PQEXIT2 dHa1Y0sucZs1 Global\a0262f01-0e7a-11ee-9660-001517a883dc1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences hack4ps[.]no-ip[.]info3 xkiller[.]no-ip[.]info3 jooh2010[.]no-ip[.]biz2 deadsand[.]no-ip[.]biz2 xn8n8[.]sytes[.]net1
Files and or directories created Occurrences %SystemRoot%\InstallDir5 %SystemRoot%\InstallDir\Server.exe5 %APPDATA%\Microsoft\Windows\6JhgEskcretMKY0gNf.dat3 %TEMP%\x.html2 %APPDATA%\Microsoft\Windows\--((Mutex))--.dat2 %TEMP%\InstallDir2 %TEMP%\InstallDir\wintimer.exe2 %APPDATA%\Microsoft\Windows\ZmzE16K9PQ.dat2 %SystemRoot%\SysWOW64\drivers\system32.exe1 %APPDATA%\Microsoft\Windows\dHa1Y0sucZs.dat1
File Hashes 373af591f388320bc53b81a7b272480cf9f64e63879bcdc726fd68350eb2a6793876228e644d8117295f156ae0e3bc71ea821806301e48f3d81d0fe3835af68e3c8dccb3be508a396735bbc358cd002a8d9b064429d1d5ceee153ded6f67132b4daebecc3d8de610264cfece61b81fbb6534259a0d886bee388b4bfa9321035e682ff093d570a76206a45da68991ccfddb4a080cbdaac25372462527ed2737077c366012bb68cd70ca388426bd9de1bb61385d6842357bc6e76d868b1e930f39868f2651415676ed612a62774f40f2ef3cbd2b3eec34ab279ddcefb5a335e6809d7bee885e6c6182d7615e375cc5c27a2f926f5d38b8c50dc46f359fb15f57e4b856a0ffda82e57693282206de21373d1628ec70326b84ff8f0930cc2f4a51bebcc11d1f898b2747579fe559497a83872a62c4ea2dd264b5149b86e41306ab0ff40eb3e9eb7c09a4bf83dded46a98fb11e134dd38662c4e61151067f18a5bc1c
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Upatre-10004837-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 77[.]68[.]74[.]18926 23[.]221[.]227[.]17414 23[.]221[.]227[.]17611 23[.]193[.]194[.]1381
Domain Names contacted by malware. Does not indicate maliciousness Occurrences apps[.]identrust[.]com26 benefitanswers[.]co[.]uk26 turnaliinsaat[.]com26
Files and or directories created Occurrences %TEMP%\updtool.exe26
File Hashes 009bd2bdbfa4169b22ffd51316b4d6d971e9133928899af2208c72408eb095ac024f0326c797d429a4dcecc5f1662a9cbb969bc5b0129c78c4c90dcbdd4069bc04c3de6445aefd13b88212d29589db04d7f6412bfee3e80d66513d259555d2fe0584d6cbafdec4ddaaba676ee9930af23dcdbb5e181d2203d936bfe78533022d0688967894c414690f2b7de3dcf6c63036c5ce61e8bb4c6db3f3e691cfdefc34079f9fdb7e1ae7c9547460b35cee345b3659e206752462a7f51a0fe31ef758c807ad32619621f1ce3c9329e64cb51c24b23971fc9caffd27891e7cacb781381c0b6f1f1b68e8352e642d12009ce48934e763ca1ee263ebf822670835937cb6e40b727beadc2a3f3afcd9d682932a9c6f392ba2a8c635de8290aaa671344e6e130c39e82c2b7da1d44e2686b0721616cbb04a26dcda7c896249426b1349546f720c6905dfc5d219d7405783ceba466330985ff038ce77c1448622b6ead9a8fedd0cd2f46a6d76025030ba0516e6ef5d935dee87aa1128fb9029810481604007ea0dcf26c0fdad8837add51b5268b5f3cf02ec9e3d8936f166bb164f2610f92ce810dc3db45b5ad14d8bb58ebfe38d87f316a82f625145a6940ed6d2cffc3d341310dd94a660c56eef86d3c4cb9ff8b1311e22e758a1d0b79c70fa23d3dec6fc4411ea59d574a39a7b2c60867451384e7cc9d33ae88c645bf641e861463d587e8e1201d6a2e6658cc9d6bbd03b22d4a8197a6aa7f3b550782c1c59b8015b26e190125266dc5e9a92d17d4469fed2cd60d0c76e3c90a469aed67a24308fa0b9f3e5125fd5f9590f0212ce2a55458ae5100d9296443b6b7cebbf17c577becb2c4150150c6538ad632823036986338622382a62fe871cb2e99aa45a6e94b64f4c485f1b66181c20015201e6216f8151dd6d83f3becf83f47d4a16ab894e497804ed8e1c2e0a6d68ae602e91db7269d692b746d38724cc46511716253d35c4a77b99181db13bbbe5da803bad25cef3241af377e04b66bee57653c1804903587663ff671e343f2293fa3247342f1b831cabd98115fd0f282e2c5693736359c70cf447061ea6fc867b76d2f596f5e139fb3288e07525075bc116605c399995aef7d3d843
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK