Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 30 and July 7. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
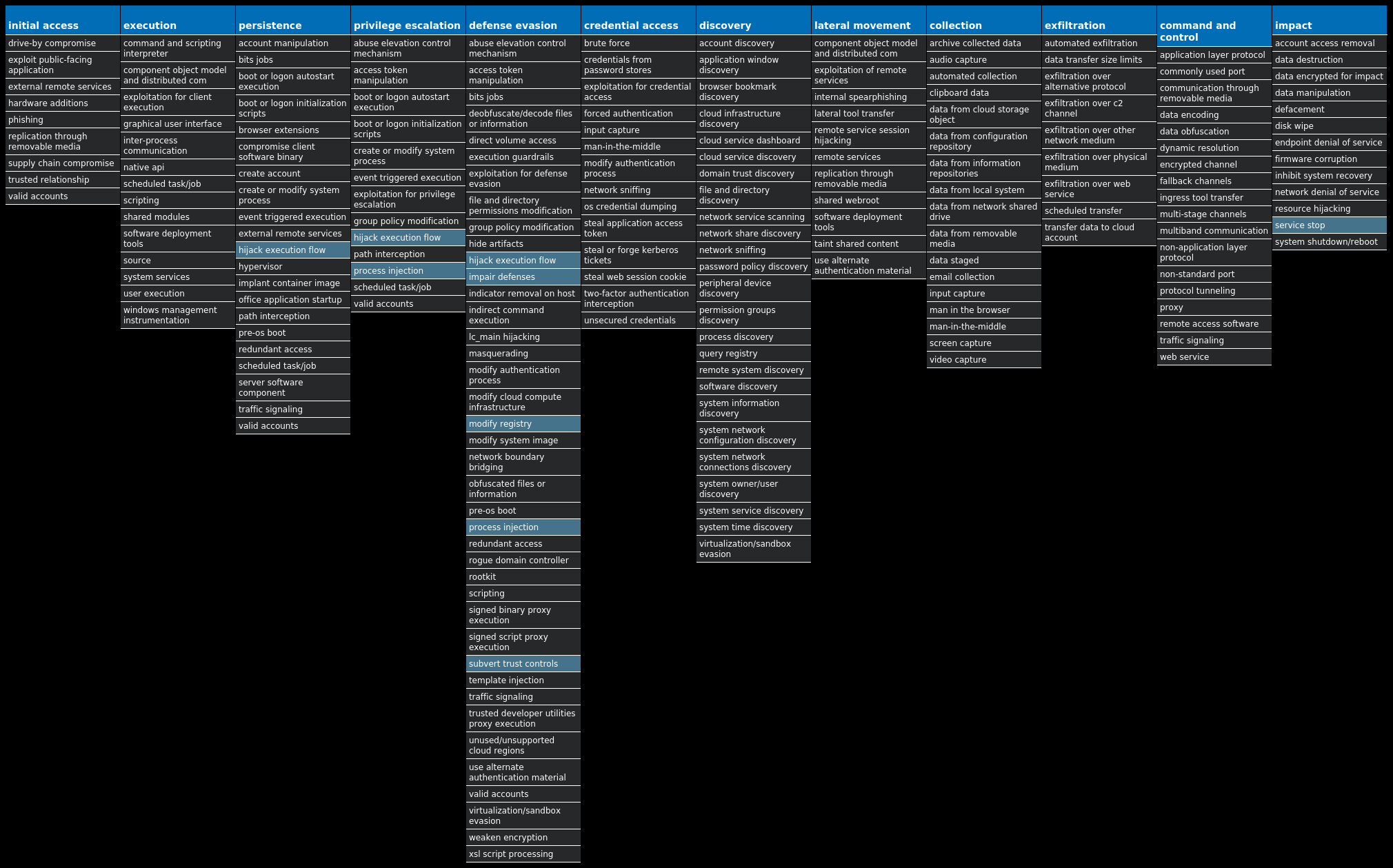
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Virus.Xpiro-10005555-1 Virus Expiro is a known file infector and information-stealer that hinders analysis with anti-debugging and anti-analysis tricks. Win.Packed.Dridex-10005543-1 Packed Dridex is a well-known banking trojan that aims to steal credentials and other sensitive information from an infected machine. Win.Packed.njRAT-10005525-1 Packed njRAT, also known as Bladabindi, is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes and remotely turn on the victim's webcam and microphone. njRAT was developed by the Sparclyheason group. Some of the largest attacks using this malware date back to 2014. Win.Packed.Azorult-10005443-0 Packed Azorult is a banking trojan that attempts to steal credit card data and other sensitive information to facilitate cybercrime. Win.Worm.Vobus-10005311-1 Worm Vobus is a worm that spreads itself through removable drives. Once installed, Vobus will often download and execute additional malware. Win.Packed.Zusy-10005219-0 Packed Zusy, also known as TinyBanker or Tinba, is a trojan that uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe." When the user accesses a banking website, it displays a form to trick the user into submitting personal information. Win.Packed.Upatre-10005147-0 Packed Upatre is a malicious downloader often used by exploit kits and phishing campaigns. It downloads and executes malicious executables, such as banking malware. Win.Packed.Redline-10005632-0 Packed Redline Stealer is an information-stealer written in .NET and sold on hacking forums.
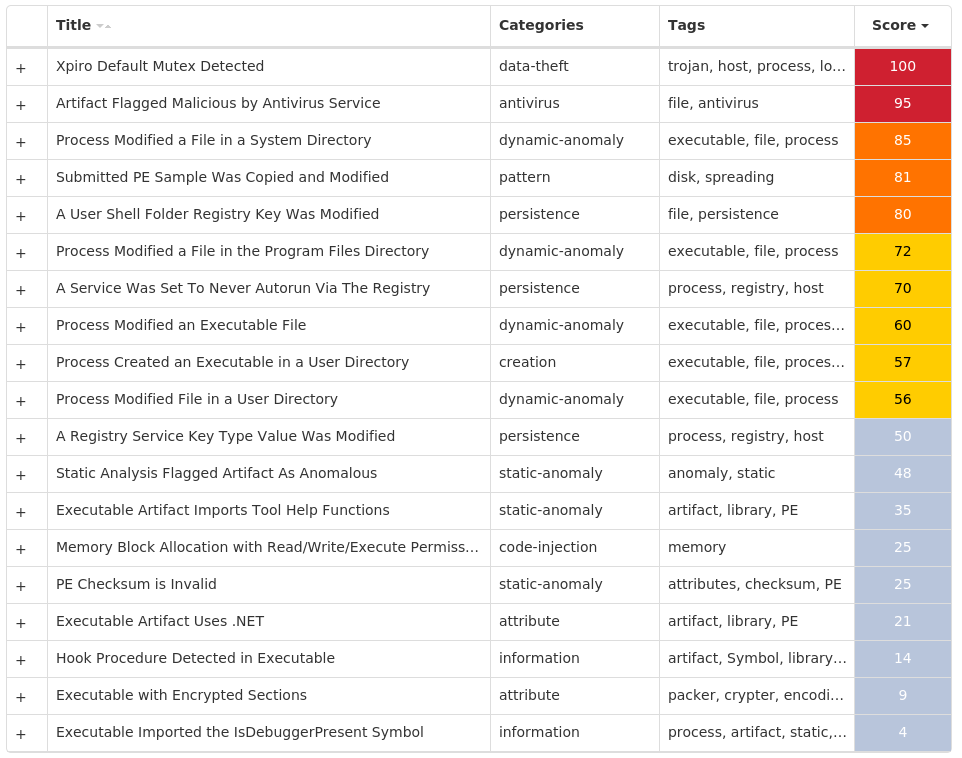
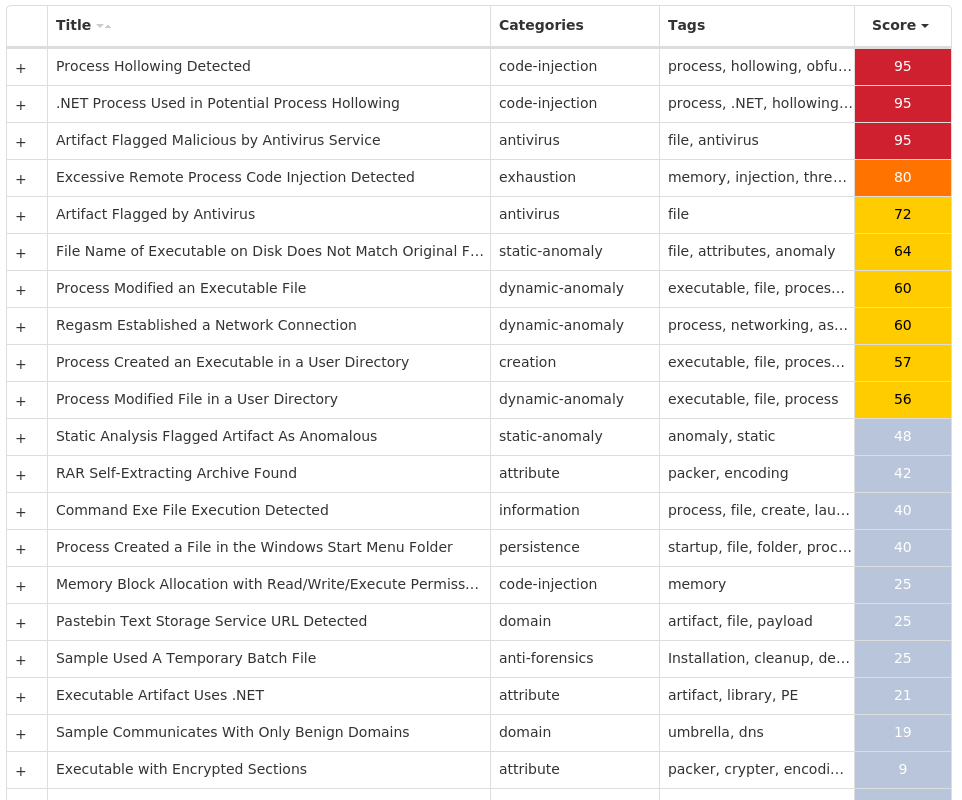
Threat Breakdown Win.Virus.Xpiro-10005555-1 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64 Value Name: Type 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64 Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Type 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IDSVC Value Name: Type 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IDSVC Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IEETWCOLLECTORSERVICE Value Name: Type 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IEETWCOLLECTORSERVICE Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE Value Name: Type 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER Value Name: Type 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE Value Name: Type 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\UI0DETECT Value Name: Type 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\UI0DETECT Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VDS Value Name: Type 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VDS Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32 Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\ALG Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\EHRECVR Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\EHSCHED Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\FAX Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MICROSOFT SHAREPOINT WORKSPACE AUDIT SERVICE Value Name: Start 15 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSDTC Value Name: Start 15
Mutexes Occurrences Global\mlbjlegc15 Global\Media Center Tuner Request1
Files and or directories created Occurrences %CommonProgramFiles(x86)%\microsoft shared\Source Engine\OSE.EXE15 %ProgramFiles(x86)%\Microsoft Office\Office14\GROOVE.EXE15 %ProgramFiles(x86)%\Mozilla Maintenance Service\maintenanceservice.exe15 %SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe15 %SystemRoot%\Microsoft.NET\Framework64\v3.0\Windows Communication Foundation\infocard.exe15 %SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe15 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe15 %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe15 %System32%\FXSSVC.exe15 %System32%\UI0Detect.exe15 %System32%\VSSVC.exe15 %System32%\alg.exe15 %System32%\dllhost.exe15 %System32%\ieetwcollector.exe15 %System32%\msdtc.exe15 %System32%\msiexec.exe15 %System32%\snmptrap.exe15 %System32%\vds.exe15 %SystemRoot%\ehome\ehrecvr.exe15 %SystemRoot%\ehome\ehsched.exe15 %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.log15 %SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\ngen_service.log15 %SystemRoot%\SysWOW64\dllhost.exe15 %SystemRoot%\SysWOW64\msiexec.exe15 %SystemRoot%\SysWOW64\svchost.exe15
*See JSON for more IOCs
File Hashes 1c73aef0dcdc4d9a5ecdba97fe58600764bf70698f2893bd24955c94917087e534d20a508da57e8592ae17817b6f966cc5c3f512e85d42655890c20bc37bc5eb412039c2acef1049a258be2f2915b5c07ce2af0faff727d5e8dc6264e93ba8685c5d9773a002fe318d3ccb93974e1f446991e22871d8e30591e1867c429b24975cb478d11f449bf98c4e4226f2f1a372aaddfc9e9766817152a07ed0c09fbee65fa1db30a27b52b990e8b984153599496710d36e49ae2937c26c36d83ee651836d1c0f751b17a85a1f51f61ef519534cf12188401ba96a68fdd7fd7a163baf05752c6582e31e1b78c7285c4e22ccc0bfb83ffc8cb2da715a2f3dbe1e92d84fcd761ccc8a2cfc286adf98f038c7934d3503647f6572a992f1e1c3db1d4ef25b089cc86a485a7bd3055a19eccf403df3b5c0ad11730a4a6fd1b5a7a0a3b1671b06b7d7a1660272801230a95d96929f762f60c5283db517fd3424b9dd8c419a9a7fd25a78b131cf423df645ef22b64cc0207462200cb4b79625a0a9d6006ccfe1f6e12f82e10138672ee10051aaec374e1a76614b51be1dc901827f0e0a53f10841f9de73708d356991bbbba348627b8aa27cda1aa0be4f70eb5e777da201d21d3ffe50543951519ea8dddfebd01cf957e494009f03184eef2d664b7c22b6493d10
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
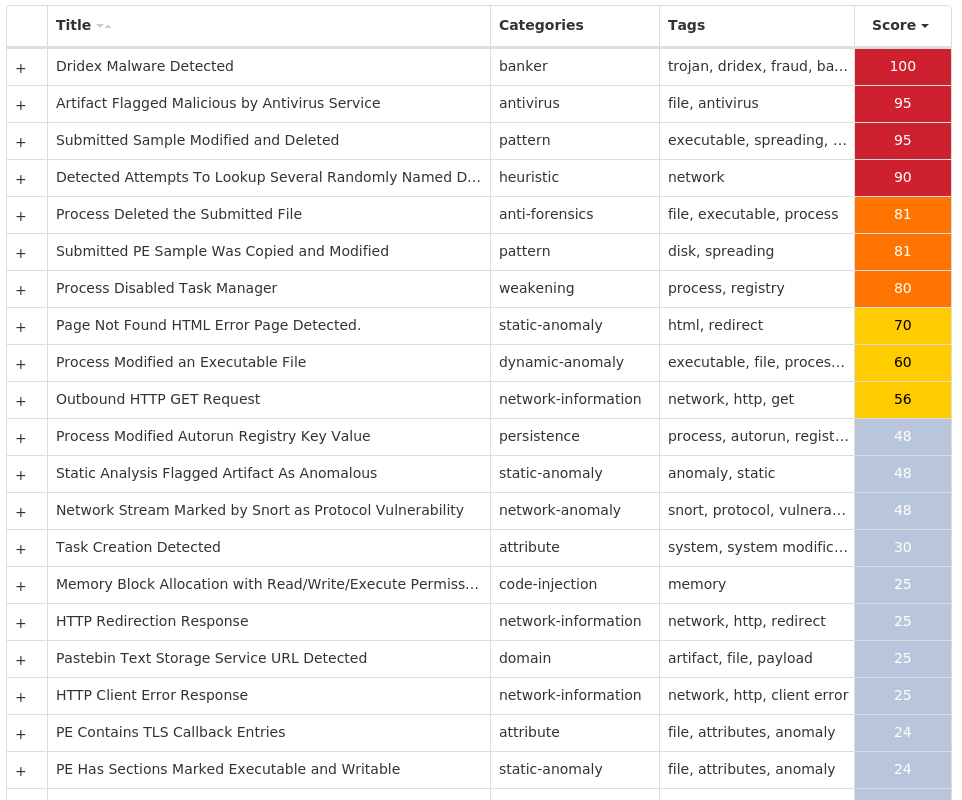
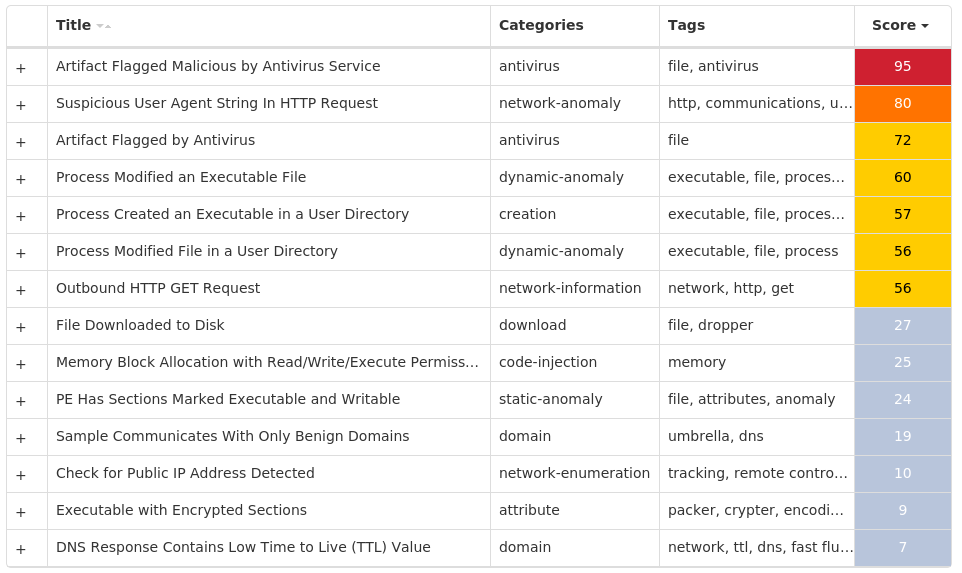
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Dridex-10005543-1 Indicators of Compromise IOCs collected from dynamic analysis of 22 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: trkcore 22 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: DisableTaskMgr 22 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.CHECK.0 Value Name: CheckSetting 22
Mutexes Occurrences <random, matching [A-Z0-9]{10}>22
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 142[.]251[.]40[.]20622 104[.]20[.]67[.]1439 104[.]20[.]68[.]1437 172[.]67[.]34[.]1706
Domain Names contacted by malware. Does not indicate maliciousness Occurrences pastebin[.]com22 w[.]google[.]com22 www[.]4rak7wdwbb[.]com2 www[.]y8206x7iky[.]com2 www[.]b80gtnqzu9[.]com2 www[.]zlkmezpnrd[.]com2 www[.]sx1zwrixed[.]com2 www[.]whi33nj4zg[.]com2 www[.]buytdummiu[.]com2 www[.]kta6uvcf0u[.]com2 www[.]3wiqpi0pah[.]com2 www[.]yygtvkvcgt[.]com2 www[.]s4j08bdcq7[.]com2 www[.]ngjtj9t0t2[.]com2 www[.]5l4uaqwuiw[.]com2 www[.]edstvaaqay[.]com2 www[.]hojchurgkj[.]com2 www[.]kkhqgrgpxj[.]com2 www[.]tfakt9f97x[.]com1 www[.]7zgalqlihh[.]com1 www[.]6rgxtzw8t9[.]com1 www[.]oekvom89dv[.]com1 www[.]dwdvdo3uwb[.]com1 www[.]ci7zigeyi9[.]com1 www[.]p2fyffcb2d[.]com1
*See JSON for more IOCs
File Hashes 091ddfa7b114578be6349cf89f90db154beae89659343baa0614c737eefa2eda11364341fa9927e9a57ed6613053d7f7fa4f3ee96aefe74e5220bbf2d9e8b1881855173ba31bd5abf20506cd0246f96b8236d148d15d49cf7febdbdebfceda7c247dd8308dcde95d012a2d9e2d0a02e5bde8190447ac34f6db70527270c2e5102a72bba3d05ab4f34aed231ae08e618f89189a1977b1dcf3e7202dd67ffd3c7959d3cc03e038819bd8e0df14ce0e6a1aa56dd7f90376de5bd3b55be4bcce815d6e251bd367cc559675dfcb3e2cc06f46678df8c8d09ac200be3aa72e3e1018f674fee0f6b328a07d4872d9cc24c0055755ddfaff42d8931360b01be5a68ca201790052d4e1de8895f27b9f8e8a793ca30881e38aaadf4cb72ea1494c3a8fa4218e21d829fd35bb5003ca9f684e9e1e34d9410570cd6f0c60cc913320d7bc86d390d7caa057aa1bfdd85717d80b81438efebfac3e4e93f957f37f53e2acb817a59a94308fac175d05986c18b45f9080b00db004721128ac5968ec442ea10b4b1e9ff13e0b09f6cc091c731f2f31156d7f22f8b55ba90a942b87665dd8265b864da4d11246417b974b307134bf418c7f5c064b2c2d27b04d66aad21da8a0402bdea662c44567c8fd83bbb49bff70da518565b180ec9907e3983837e0246ce88e2db0813151265a9fb789d2d29579ecb6391c5022d11a65ed4c620740ffcabddc44b5e0dfca470779d7cd614832777d6323c0f99c39054c499f06335d7e726ffd7cc086c1142273d7589fff8d2c0f618660470f623e4ce27ba61d25729eb49ffa26c8b053d48ca41dae36f03ecdc0576f8b4dce657d9b016f01efd3c8bdcff5751ac9d873cbedfc31c3af3dbe22d7d62d0ab94f6ded9dcb858d99c3908bd627521ae2e27e6eba9e15fb02a99580f26a24b7c2926eff70b230cde70ef99476f35a1ae8a34ccd6158bf17cdd1a8493d964a1c3dd5edf130238224044bbf5047ea00cf
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
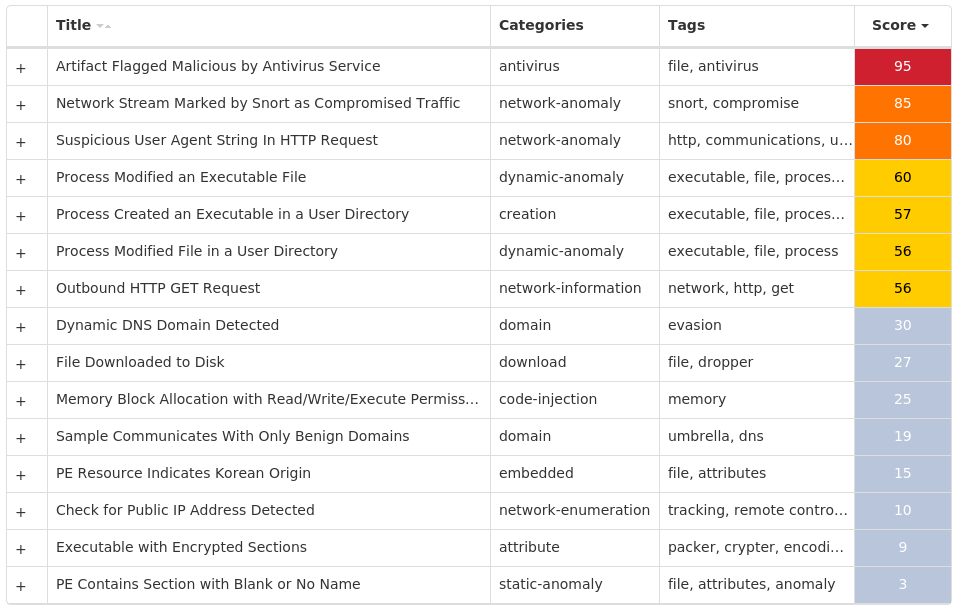
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.njRAT-10005525-1 Indicators of Compromise IOCs collected from dynamic analysis of 91 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS Value Name: Path 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS Value Name: Hash 2 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS Value Name: Triggers 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 0b2592d5bed09772be6f2120ec5d1e38 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 8bc2449a0b4cae186dff71d874ecdd87 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 74cdfe74037de0ebe063775a7be8d61a 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 09830ddf01a042c930963250c1b2cbb9 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 49879c18dd0a980ea7348c138e510ac1 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 8a258bb2745a1ee39524e97dccc49ac3 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 9bf535e06a1626c1a04514e4e7e60f3c 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: f5216625d81896bb7f49a4c94fade2d5 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 166c0d067030a42b438a748228b9c466 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 6462944e37e52e33dce88bf226802c41 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 4c0288488a0673a8f068842bcaa1eacd 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 7e222b88435d7fdadee551ee08735103 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: d4e4bba65005822ede934e597684e25a 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 35e466437eb1ebc61c9f46ca2bbf5bc8 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 087ffa5bebc0f6982f76d5d465437e42 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: c89e814d4b827b97e2dec133552e2bb3 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 1a723ba0bd7d3fdd081709949ec9a96d 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 36684bc19336ad3c85d296d273c3b5ba 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 522dcda6332f8fccbf277125a6b42b4a 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 991bf530df55926dc26eedc261e748fd 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: f6ccb4d45196e32da740e90956ea5435 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 11008ae525da4c3e48917b0e8f498699 1
Mutexes Occurrences 3bX4sJbA7K9pPu6V1 i1cBWf2dmosiaxFd1 QIIXTdrPWoBnhCHq1 CJa3depjkhz3Rrrz1 ljKzvz6mJDSTHsWK1 pTPz2lb6DYSu2BOH1 IqHiRcbuVnbxVcvI1 AQ7McAOn48gsMrao1 hZ3Y3pVPLfGoDuyt1 Co4sLNQFf87ujG8A1 q8cjIFLdoXfkFfVD1 k5P9hMH9jGFDLszo1 GKNiwCrZVGLnFY2s1 H4Y5eQv9rQ6DsZho1 79afw86ZTQhYbwqr1 HjNwpDYzmRCLWXfj1 Bh7a1PoudAiFeAk91 WlQ8d0s81SOpQQ0S1 nR335S89cB4gOSbp1 ecf0u5N2rEixFNpn1 sqEor2xkqS0Cycit1 DV8bYNJi3uczdksS1 70rrfj9Vryz3Nek01 XSLvYVsJZs3bsiZr1 hP1Pl4miMfRFMFLU1
*See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 208[.]95[.]112[.]191 193[.]161[.]193[.]9916 209[.]25[.]140[.]180/3113 209[.]25[.]140[.]21111 209[.]25[.]140[.]2295 187[.]84[.]121[.]1383 3[.]68[.]56[.]2322 3[.]67[.]15[.]1692 18[.]198[.]77[.]1772 52[.]28[.]112[.]2112 185[.]230[.]55[.]722 3[.]125[.]223[.]1341 3[.]125[.]209[.]941 3[.]124[.]142[.]2051 35[.]158[.]159[.]2541 3[.]126[.]224[.]2141 3[.]125[.]188[.]1681 18[.]192[.]31[.]1651 3[.]67[.]161[.]1331 3[.]64[.]4[.]1981 209[.]25[.]140[.]2121 18[.]158[.]58[.]2051 209[.]25[.]140[.]2231 212[.]187[.]4[.]1611 85[.]66[.]212[.]2351
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ip-api[.]com91 prevalent-63525[.]portmap[.]host3 white-camcorders[.]at[.]ply[.]gg3 lake-region[.]at[.]ply[.]gg3 hxd-54486[.]portmap[.]host3 m0m0w3b-55979[.]portmap[.]host3 4[.]tcp[.]eu[.]ngrok[.]io2 7[.]tcp[.]eu[.]ngrok[.]io2 considered-arrest[.]at[.]ply[.]gg2 q-medicaid[.]at[.]ply[.]gg2 countries-knights[.]at[.]ply[.]gg2 deletedapo-46418[.]portmap[.]host2 head-transit[.]at[.]ply[.]gg2 5[.]tcp[.]eu[.]ngrok[.]io1 6[.]tcp[.]eu[.]ngrok[.]io1 0[.]tcp[.]eu[.]ngrok[.]io1 ed-sleeping[.]at[.]ply[.]gg1 based-calculation[.]at[.]ply[.]gg1 ms-slovakia[.]at[.]ply[.]gg1 existing-bios[.]at[.]ply[.]gg1 wasted9sss1-42260[.]portmap[.]host1 which-wicked[.]at[.]ply[.]gg1 katarina1[.]ddns[.]net1 society-mastercard[.]at[.]playit[.]gg1 support-gone[.]at[.]ply[.]gg1
*See JSON for more IOCs
Files and or directories created Occurrences %APPDATA%\MICROSOFT\WINDOWS\START MENU\PROGRAMS\STARTUP\<original file name>.exe16 %APPDATA%\a5cd4f0b99bdf067173acf84d35d4420.exe1 %APPDATA%\9b652cfeeeba0e8895cbb61a14d7288a.exe1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\9b652cfeeeba0e8895cbb61a14d7288a.exe1 %System32%\Tasks\a5cd4f0b99bdf067173acf84d35d44201 %System32%\Tasks\9b652cfeeeba0e8895cbb61a14d7288a1 %APPDATA%\4bc880598bd07233f93104a7e6561610.exe1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\4bc880598bd07233f93104a7e6561610.exe1 %APPDATA%\44a60f57e78721124291fcf664cc3a0e.exe1 %System32%\Tasks\4bc880598bd07233f93104a7e65616101 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\44a60f57e78721124291fcf664cc3a0e.exe1 %System32%\Tasks\44a60f57e78721124291fcf664cc3a0e1 %APPDATA%\834a90d3bdf682a1a8a546e336afe6af.exe1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\834a90d3bdf682a1a8a546e336afe6af.exe1 %System32%\Tasks\834a90d3bdf682a1a8a546e336afe6af1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\d0d8fd8abb162af4bdb69572399956d3.exe1 %APPDATA%\d0d8fd8abb162af4bdb69572399956d3.exe1 %System32%\Tasks\d0d8fd8abb162af4bdb69572399956d31 %APPDATA%\02b50540c53ab7d1c24c07f9525c54509e72c73a99d4a96365365d2799bfeecb.exe1 %APPDATA%\1129d910145211033817289e086467903492b1c24a572521486518ff93916a74.exe1 %System32%\Tasks\02b50540c53ab7d1c24c07f9525c54509e72c73a99d4a96365365d2799bfeecb1 %APPDATA%\153954284c10d9cf8a2d6197f2f98ca1c47e0a4c3dfdf8701d010afda794a6a5.exe1 %System32%\Tasks\1129d910145211033817289e086467903492b1c24a572521486518ff93916a741 %APPDATA%\0a977484f6f9467af7eccef84a1d1522e04d8daf395fbd82e75c25a55b405ead.exe1 %System32%\Tasks\153954284c10d9cf8a2d6197f2f98ca1c47e0a4c3dfdf8701d010afda794a6a51
*See JSON for more IOCs
File Hashes 023fedd1d56923cedd19fa8692a1d5f07f44a674322a69b25db1f5d1ba1721d602b50540c53ab7d1c24c07f9525c54509e72c73a99d4a96365365d2799bfeecb030091e9ef98945ae7fec16072d9f8fb20f15f160389b8f7b0e60a7958e7647804ed989aacedc61f1b245e72672dfe559e8a5a2612fb4c771b0c67c2f16c8eed08a5fa046337acac2e274a197ba5344767a064288df49f9c9c04f33cb37d779d091a9232a700d62a7131fc0b9b7d1885f9bfaa89414b7d68a23860d2e6e25a4509f6d9681dcaadd0b66b76155abeff18d68bce3b0f50fbd104194bb6c071eb2e0a977484f6f9467af7eccef84a1d1522e04d8daf395fbd82e75c25a55b405ead0ade718a67d661f925e622044e0553692862976b1968a082537a6ceab77b0f0b0cb9b0d229cc0081f0431b39cb5f1a88b5035bbf38e94fb067a77d40006e33330de1e6d211afd3613d88877a823b4c8d744d74c9125e5fa23956a0d511ab4a8d0f47c2495d90cf0dacea0c9f45548862bf2574c7c4bd4350c8fb4716f34b48250f4fac4068cac09d0cbd2f6588fe70e154f15ef39d1a3490e0c580ac11e358e71129d910145211033817289e086467903492b1c24a572521486518ff93916a741294e9765dc4d6fdf8c09309552d594e81abb0a87da71565e95e9ca2baf53f9b135d9b51af134429131b1b0fa6b3cbb86dc32ca5730fd7a1fef91e36bb8e9b3d153954284c10d9cf8a2d6197f2f98ca1c47e0a4c3dfdf8701d010afda794a6a51ae3b1b699cc598232039ab3eb87f3981abb458494b2cea0553cef46bb01a4a11e990d15311ae6f3281a30755a04db031e82bcd71de9d648a7804a43c97db4891ea7a92374bf5ae3f9e6b3a84666b0b871e9dc48df95c1214690a402e08a15ce1f0346cf39bb2e8b7ffa37640738072fa201e36dccd4f3caba5757103928d73f2296b5ef4a6d30247835f12fbdfa618669b140ce0d1594031c52374c33e399752311cbef005dbe928ea0d9c734ccd84ba682003301b9f283d2da155268df58fa2317961afafb8424846335de62fed00e9102b2c7acc415567c43df808340c29f2483ae5ef59e5500981f69792add63f8287402f7020a84119379009d26939015
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
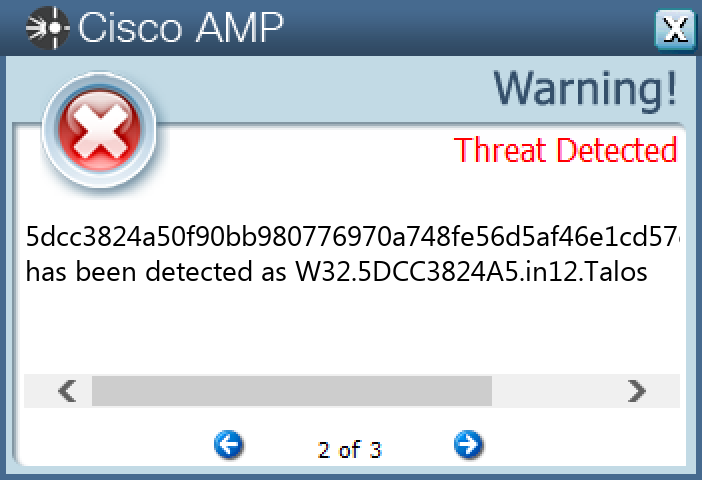
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Azorult-10005443-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Mutexes Occurrences Local\fadce40ba6f0cccb5201fbe46cd59acdaf356acc16 dfgekrgoerkgopskdwefjiweafasfminewiognowes16
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 45[.]140[.]147[.]21410 172[.]67[.]34[.]1708 104[.]20[.]67[.]1437 104[.]20[.]68[.]1431 34[.]117[.]59[.]811 23[.]221[.]227[.]1761
Domain Names contacted by malware. Does not indicate maliciousness Occurrences pastebin[.]com16 ipinfo[.]io1 apps[.]identrust[.]com1
Files and or directories created Occurrences %TEMP%\RarSFX016 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\System32.exe16 %TEMP%\RarSFX0\system32.exe16 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp10 %TEMP%\RarSFX0\ChatGPT-4 Online.exe2 %TEMP%\8LxnTgFTBZ.bat1 %TEMP%\UETUBSwFNh1 %TEMP%\aRMq8s2PZu1 %TEMP%\0Ar8UVsFFH1 %TEMP%\add4oKeLWK1 %TEMP%\rOqL1SoRtH.bat1 %TEMP%\EglYUAkHS51 %TEMP%\4y6pq4Mdxm1 %TEMP%\FEB5JxBvcP1 %TEMP%\57GSqsql8L.bat1 %TEMP%\csHnJfxfgw1 %TEMP%\8qPGiyvjgx1 %TEMP%\plAJRGijyy.bat1 %TEMP%\XzKdA23rT81 %TEMP%\RarSFX0\Cyber Ghost VPN 2023.exe1 %TEMP%\WaJhssybhA1 %TEMP%\XwytQc2jxF1 %TEMP%\q9ZCrYAkiS1 %TEMP%\zSrmjrCHbC1 %TEMP%\RarSFX0\BLTools v2.1.2.exe1
*See JSON for more IOCs
File Hashes 05c0d569f272ccb96a820ee096177c1303a3e0aa19ab98468e8237c33c6af37a3b552bdcaa5dacf399416f3db53c1cce8631d97e9e8d23410b5195400504a6745d868eba69e85085ea0b8baac4398297e012d2c00d376bd74414b73efe05b3a35ee5e591bb2ef8a32f74e08936129f473c1d66a9c61ca454ad86fd6c9a3451d066ad0798cdc38b13fade98886142b555ceb0097a82db1f509a6c3e8034b278ea72d53a6bed17fb482a405cd140160aa8a728e8912c88172e4e0409843778618882c6e1212af6da4a6a5a4428c9f51736999680daf5b75395082ab3139d6e28c28a6672b8b7165db85a63750a12a89f8c0d55f7f2a98042f25be8740324469ecc9759b11c05da965795091bdf9d1e51d9c0e3f90712ae1afd198b93d8ff1f5cb9b03e2c049c90e8245e9d3135a24515cce921ac529ddb0395ed2401c4cbe92fb8ba3adebd723bc59f52fcadcd698c651ce61ed6fb099d6583383edab66ac34f2fbfbf48fb4dd150dbc6c34b309dc308326a5b9ab40defafbe32060236243fe8bad618502188cb64718b8aed6a9343c65f6e319ce8c9f750855176f5b575a6807adaa375be093d880a65d9ce51c2b9127169dfce292c295c93dd4fb3dbc9b61b23e97912bb807c184d0cd506c9ecf6948ce0ae7a582b1eebb70ef29c8d8e999be1f8d79c98ef9080e10beb0760437bdadfed580347a423ee09fead93ec9d6a7b4a
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
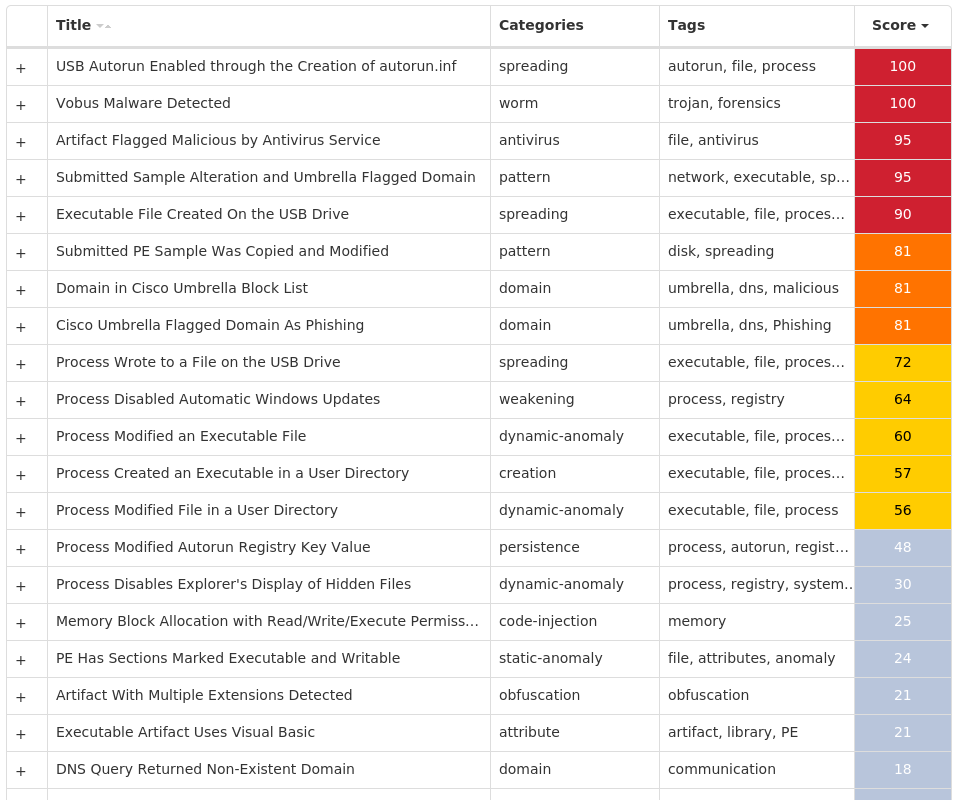
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Worm.Vobus-10005311-1 Indicators of Compromise IOCs collected from dynamic analysis of 63 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED Value Name: ShowSuperHidden 63 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU63 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoUpdate 63 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE63 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bzxuij 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vuinues 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ciheq 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: tuizao 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: liuoday 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: lauugoj 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: rafid 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: wiociey 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hauuyuk 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: leemiok 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: coakau 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vaaji 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: waepow 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: slhus 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: jqkaj 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vieyeg 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: jeowo 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: vaueriq 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: feaic 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: tueek 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: voeifis 1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 199[.]59[.]243[.]2233 212[.]32[.]237[.]922 212[.]32[.]237[.]90/312 212[.]32[.]237[.]1011 23[.]82[.]12[.]321 76[.]223[.]26[.]961
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ns1[.]chopsuwey[.]com63 ns1[.]chopsuwey[.]net53 ns1[.]chopsuwey[.]org53 ns1[.]chopsuwey[.]biz53 ns1[.]chopsuwey[.]info53
Files and or directories created Occurrences \autorun.inf63 \System Volume Information.exe63 \$RECYCLE.BIN.exe63 \Secret.exe63 \Passwords.exe63 \Porn.exe63 \Sexy.exe63 E:\autorun.inf63 E:\$RECYCLE.BIN.exe63 E:\Passwords.exe63 E:\Porn.exe63 E:\Secret.exe63 E:\Sexy.exe63 E:\System Volume Information.exe63 E:\x.mpeg63 \<random, matching '[a-z]{4,7}'>.exe63 E:\<random, matching '[a-z]{4,7}'>.exe63 %HOMEPATH%\<random, matching '[a-z]{5,7}'>.exe63
File Hashes 00b230ed3040b090a11e46ebd7207355a106112323dda09ea43050aaed2ce52100b3de85145ced57106d257f7266bb302c9d827239391e81b866766b6fe70f6b00da5d9a6a0e1c49bc47b6523dbf7883f2f067e3315d9e10a3444fdcee4cc44901043e907887d3472f6379f3586906e23a6087c9d71b70e035eea96d43366f5102d2ac467b6eecd05ae1d1a62ce97c16e346b4c8a9191276a7543fb3c71e993e03852fe9d85055f6a5f4d90a2cb92d2381815ff7847a7434677a4bb6df6f69210460f01fa91872b0a8931f41325941739b455c8905cb3f531f3cc3c921a2078606c4946c9caa563761996f13a02a5a6d5ec6e1812e6e75e2fefd6784030c4574072938f58f95ea4a2c047e243ff602300c402718b94de56138e491dcbea19df10766a841804df2fdea58be32ccb200ac721b5d26456305d810a14e4935980ac907fc95465e6ff9ff361066e2a884b8a03c8d48e1e4318ee329bccdd2cdb048940841ab260709bf50b78c24c7fe33ae736cf04b67b70de6960952a50b6e15ea60091f0b3be99e7bc7f68da59eedb6f54d953b270a77bc4c0dd2aa4e9b9ff060240932d38f962865f1ec97c477b5d6443c0ceea27db4377df54a62adf8f3bb72ab094f2f6350a4e45f0a00a6080c5beb701157f741c2ed12a6eaf80ebd8e28fb3409861dbfac06f827f0d5dd5f39a2a39bfc7873bba36d9a581c5d573ad28cf1110a18bd843c034727700b5af482c15bc3b4b84c038728ff4dca2fe305673facf90a9cfb2aad70e78ce59a29b98a9be61cf6ecfd9720184977b1a8d1b5bdac6fc70aa783e2ab54c5bd004e3d5de90cd5388b87aa193e488d93593f74a99870822a0be2cc908e48d871942d32c749340e89207226a2d6069afa799912f76ad8ba050c0f8266b4a01b4237847c05eca16cc276e9856cd59901e038cf6dfa9bb92c440e719bdf2a4a04eb06524a79e294451464abd7c9262efff5988bf32ca135ee1c0ec9e7c9648970a700177f81a9df8bbf2903c49cf57d8b476c960791f9a1b83f0f23de73c22b3ee5b70175866b76ce13ee5fceb2251b8de5713c182895b1d9fa0f3d7037a30dd4eb7ddd018165a5d33d0b88873e9ff8944c65d7cfe674ea5ede
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Zusy-10005219-0 Indicators of Compromise IOCs collected from dynamic analysis of 27 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\\PARAMETERS\INTERFACES\TCPIP_{9EB90D23-C5F9-4104-85A8-47DD7F6C4070} Value Name: DhcpNetbiosOptions 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\\PARAMETERS\INTERFACES\TCPIP_{9EB90D23-C5F9-4104-85A8-47DD7F6C4070} Value Name: DhcpNameServerList 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\\PARAMETERS Value Name: DhcpScopeID 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\STARTPAGE Value Name: StartMenu_Balloon_Time 1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 188[.]120[.]194[.]10127 104[.]18[.]114[.]9715 104[.]18[.]115[.]9712 173[.]248[.]22[.]2275 178[.]214[.]221[.]895 69[.]144[.]171[.]444 98[.]222[.]64[.]1843 173[.]248[.]31[.]13 98[.]246[.]210[.]273 71[.]194[.]36[.]733 24[.]19[.]25[.]403 208[.]123[.]130[.]1733 24[.]220[.]92[.]1932 109[.]86[.]226[.]852 66[.]196[.]61[.]2182 65[.]33[.]236[.]1732 69[.]163[.]81[.]2112 173[.]248[.]31[.]62 71[.]99[.]130[.]242 68[.]119[.]5[.]322 64[.]111[.]36[.]352 173[.]248[.]27[.]1632 97[.]92[.]125[.]742 98[.]204[.]215[.]922 24[.]148[.]217[.]1881
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences icanhazip[.]com27
Files and or directories created Occurrences %TEMP%\razacer.exe27
File Hashes 06083b300390634454ad9514dcb76dc292eba525af7f4f6fb88a88a030d0137d0725f9403e693eb417343f5ebef2fb8b20c17573c50c49dbea7472e1acd18f8907a54115a35c502296f144ab1ac063f864625740eed210bf629ae1d90c9f854c0bb14de5996c44ca206c9d1478552d43734e742011570024979432a8df791e99169218c7d50803982b06a8120697f5fb06dd7b20aa5b5553ea3efeb6b6fd3be518164491280f48454547e2da06e674aad8bccf34b5553126b69f6a58278f7b21249810e968de4a12fa3ee4e03de6ae42e8f847c1204c727a75be9db8911b8da425634be35352d5a07898857fecd62f480add2eabc7fe27804dab7f902824ce912ff0e715a62f844013326b7f54ea64c8b2a9bf9f68486aca4d6cdb06de2150bc3c705dc7d93b66549cac81441570b60889c2c64bcbb83e6e2c18437428aa73e642d4defa7c09129009f8abd4fbdb40c1ccf108eb489cf93c7426fd0e4c7fc7364396a3b692ade1b12b46b2563d30a52b9fe9b72e994f963733bb4277e93f7f0c4e8189a5d0a36afece1dbc25d022c0e129ec63ea9c56e2964a2407d1ec49c744516aca5b9005c1047d181e81e032d56d016f164434714e79bdaae190b0925d7d583108ea56a262d7b44b1bd95f5b37fb72b877238d8c303f973a20d9ec937703593814354f8668818c8eae406f77124745904dee97693bc5e76415cdc48ddf1a5cc7155737abff0909fc82c2ccf83271d243103b849f9bf3c373c57a058a346b5d2210e4072588e6dec44e5a3cde746af95f360e19d0a40118bd05c84d88755c5fcb277befd5cc98b19eafaf75dd2c9ca702d11fbd18b8237e27fae489fffec7719f3e2bae12ec1df14690ce4fce04b2c8513126b639842903fe0c973ad12dd1774be5523ba128c6f3337f18c856eaa8bd91b7caa6c9b1d877efc667f91440567a0f2400ffbc9b97ec7686eacf526225f17effc9e9305f15ed84504ed01e65bf7e910440620fdaf0cefab1be85029f602455af04f90efbe5c64383757978ee6b81c13a0a8f8e3e7e542f64527b02fcad467a4322f1e9912e0e4e02d14fdb7c56823dc8ce419bacd53d23884a1d604063e406d50165fb33ac69067b1dc3a34f32
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Upatre-10005147-0 Indicators of Compromise IOCs collected from dynamic analysis of 27 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 93[.]185[.]4[.]9025 193[.]122[.]130[.]06 132[.]226[.]247[.]736 132[.]226[.]8[.]1696 173[.]216[.]247[.]745 193[.]122[.]6[.]1685 84[.]246[.]161[.]474 77[.]48[.]30[.]1564 64[.]184[.]183[.]204 158[.]101[.]44[.]2424 76[.]84[.]81[.]1203 24[.]148[.]217[.]1883 216[.]254[.]231[.]113 72[.]174[.]240[.]1483 63[.]248[.]156[.]2463 72[.]175[.]10[.]1163 74[.]116[.]183[.]1363 64[.]111[.]36[.]522 178[.]222[.]250[.]352 85[.]135[.]104[.]1702 217[.]168[.]210[.]1222 104[.]174[.]123[.]662 24[.]33[.]131[.]1162 24[.]220[.]92[.]1932 188[.]255[.]239[.]342
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences checkip[.]dyndns[.]org27
Files and or directories created Occurrences %TEMP%\elarvolume.exe27
File Hashes 03795bdcc508f78484839595f6f02cb0c8e436403f221d61d8e72bdd9537532a07bc9395bad712c89043162111deb1e2d7ddf231d3ad3ad744e2723ead611a1e0e6e6b5de5aa9f5643c483e6055c23cfc98259f4edb900c88b87df62094a2c33108b13b50bb2dd6e91893f4636c0cb42881ddcf540ab8dc7500f42babe1fa0e3123238b09630d0b0a4d412425058da936535cd5d93a23a671dc3446ac3bc8f3a2259416d1a17347551e38526d6f74c9e2bbcc3590ae14bea9a7ca0c7251225032316cc68d9745701459c3cb5fff4e3f31d1961bcce438fdf96881b4af494196c2623040cb9b5ca61bcc3ac56cf81f14f7f4d790757669e8b622f1ef52db4f9bb272ada068cc6851150e7f5bcd17c403ab6ea9d1ad62c7d851f2c7568dd7c1bbc29dd6f15e2a3ef0c72850b498e00b660c51082c5858ccdf68dd3888e444d5f732abfc6bd75edc3f060c8d50e98a120122e89791d2487103971dba12fc4b2c9ef38472a9975c5777b029d38f3b149d452f1a95d5e194c89d2294566b2ed3cbdb7389b0a459a839e8f323c1f3e1395f0ee22bb34926e523758040a05a51a2a26c948230f3752a9d8f27114ffa640fd575a1ec52511d2b116c6fa77fa06234f4b4c5ba22ca3d809a8b68a08127f22dbe3b3e7e5623c990d8391542881417fe7ed155dcc3824a50f90bb980776970a748fe56d5af46e1cd57c977eb544cd6c6a2525652ccf42445786444e5daa5a4a169a2c3d7fbcefd6692a0a6609760cac9a070268ca72fb9914c65ea445cf666592487a72d7ce52251eef3ecc5e04842b69d1346be7bbc2fe05ac253df3e05a06b8a40b09002a72bfd7f1df9d8f36c465f1a86a700c9b142a2ea5e55281df2381c3b1fa1c4fd02d87929a672fc86b256cff9de28f7f6d0542b33cdd583b9b7dab279cc39f0c4960c73aa65fb0ea6fb5a1020a998ff74c0bf36a7a8eb9416f26cc307761b1d0cb9fc8813a3e79749c898b8a371a92443bb6d0a9f15410a79afb3a94f875156c4515d6d981fbf811ec14b53606f2940aaeb071e193227fcae9ce88fa5dc0d7b29fbcaa037085922b75b9f84e48a797f40bf0644e2234bd6ff3e790d4fc394612d18edf3dcf9c483246d919efee96
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
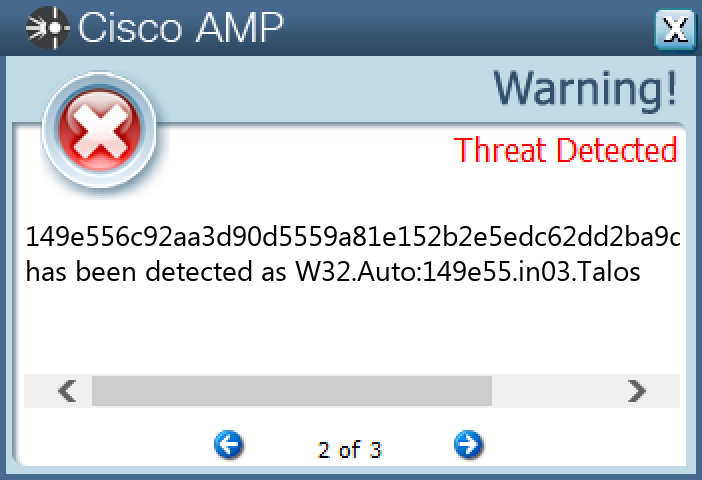
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Redline-10005632-0 Indicators of Compromise IOCs collected from dynamic analysis of 42 samples Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER Value Name: DisableAntiSpyware 42 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoRebootWithLoggedOnUsers 42 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoUpdate 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableBehaviorMonitoring 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableOnAccessProtection 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableScanOnRealtimeEnable 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableIOAVProtection 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE42 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES42 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES Value Name: TamperProtection 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableRealtimeMonitoring 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AUOptions 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AutoInstallMinorUpdates 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS Value Name: DisableNotifications 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: UseWUServer 42 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE Value Name: DoNotConnectToWindowsUpdateInternetLocations 42
File Hashes 013f9a67879da9274a96e9252732f1275cae7ae76cea876b256cb405881477ed023a107f218ddba25a9974b938023a233de0738c94bc35a8aa1fcbf5fb5be6b20630f02d54915d443b89a0caee7e099fcf1e0be4ee5cf2e6341ac33531a6a6590c5a5d3d2f150e55cf47476e5e0058ea8bcceb155a09dcc6acff0e34f773965c0d2ea64a807283f0998f74e131bd95436a73e7f09d7db1cebd2a5c6160ab25a7116e012f29aa293084be378f00485fb92dcfe3703eb7d687109976c5c54c795311e1492ad2c4eca711c4f120eda65391660f4a889c7df1e378f347ece9c23c3f14017b66abc03e1062a6bee7b2d75a3d49fa6960f08bdb8631c8ec920784eeea1413b8951a3b3a61ebc2a4947cf81f3053d924286b6c76bd2ea0d4cabcc3f6df145c8037c413f00333b72c129d488eca8b900ef583f84e8370d4f1646bf5b71f149e556c92aa3d90d5559a81e152b2e5edc62dd2ba9d454af1ed967ac1da0dcb16674c540246f15bd1f7aaf7d450a84a81b408cb3767265e96671c974310a2dd19a7ede77d763b2897bae40e13d2179434374005bf0736eb59413fef040a12c21ac843c2dbe6f48eb4a0bbc6d39479df09a7dad86821558cdc330d6c09bac9241ad96dc3b615d9bbf725586c0f5abfffb2cf29c2303f27a5d92a1945292649591b1f622f76d669eefc8dbc9d51f4d10747cba3521cc6073fc2dae4ef23d01aad1bb6186654216b8090a26720ce9ce91ff1b279a09ee315187fc8f12237d939451cacbbb632e0141ab9562a88a0e88a668d8f451396069456b9f6b09b65b2c66b1f0ecb8d77e1a2a4ad3a90626bc296288dc7dfe689b0b90d8221fd7216ffd01b212792319c73f82e9a4f0691ec902f97c16e7e762a76b8776bf3d3e2373f833222aa379527abdc74bc57a59fa4c9dbec82fc714607a143506c9625ccb3473e4f2810221a2656afb58b3fb2f99ff98c1c002f68a7cea35b4b2a43e1a424bc45032b4eb458a5f42d854d93daf743d0c7a6c099ff17e599c86c6ebd316c00afdc5b2be65b87d98057081d253c3e880e90229e8a984c316237b95349a65bc0d729822c811d54e832c20ac045df28accb86ca3e3e1687d1c5e4552b108e699ce5b55d
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK