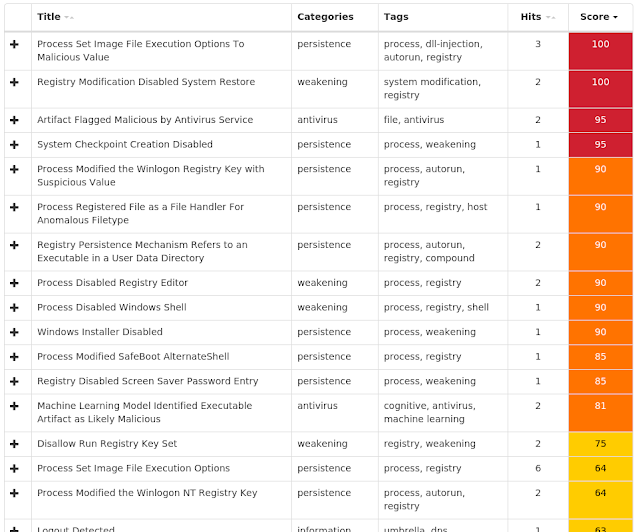
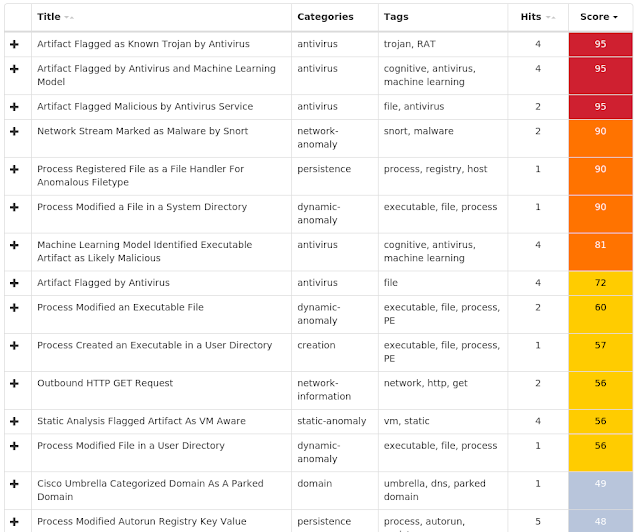
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Aug. 2 and Aug. 9. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
Threat Name Type Description Win.Malware.Swisyn-7105182-0
Malware
Swisyn is a family of trojans that disguises itself as system files and services, and is known to drop follow-on malware on an infected system. Swisyn is often associated with rootkits that further conceal itself on an infected machine.
Win.Worm.Phorpiex-7104335-2
Worm
Phorpiex is a trojan and worm that infects machines to deliver follow-on malware. Phorpiex has been known to drop a wide-range of payloads, from malware to send spam emails to ransomware and cryptocurrency miners.
Win.Malware.Zusy-7102354-1
Malware
Zusy is a trojan that uses Man-in-the-Middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe". When the user access a banking website, it displays a form to trick the user into submitting personal information.
Win.Worm.Brontok-7102096-1
Worm
Brontok is an email worm that can copy itself onto USB drives. It can change system configuration to weaken its security settings, conduct distributed denial-of-service attacks, and perform other malicious actions on the infected systems.
Win.Worm.Socks-7102087-0
Worm
Socks is a generic worm that spreads itself via autorun.inf files and downloads follow-on malware to infected systems.
Win.Malware.Formbook-7102043-1
Malware
Formbook is an information stealer that attempts to collect sensitive information from an infected machine by logging keystrokes, stealing saved web browser credentials, and monitoring information copied to the clipboard.
Win.Malware.Tofsee-7101989-1
Malware
Tofsee is multipurpose malware that features a number of modules used to carry out various activities, such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator’s control.
Win.Malware.Chthonic-7101817-1
Malware
Chthonic is a banking trojan derived from the Zeus family of banking malware. It is typically spread via phishing emails and attempts to steal sensitive information from an infected machine. Chthonic has also been observed downloading follow-on malware such as Azorult, another information stealer.
Win.Malware.Remcos-7101023-0
Malware
Remcos is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam, and capture screenshots. It is commonly delivered through Microsoft Office documents with macros, sent as attachments on malicious emails.
Threat Breakdown Win.Malware.Swisyn-7105182-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMSS
9
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMSS
Value Name: Type
9
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMSS
Value Name: Start
9
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMSS
Value Name: ErrorControl
9
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMSS
Value Name: ImagePath
9
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMSS
Value Name: DisplayName
9
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMSS
Value Name: WOW64
9
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMSS
Value Name: ObjectName
9
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINMSS
Value Name: Description
9
Mutexes Occurrences xinduanyou
9
Global\aca756c1-b9e5-11e9-a007-00501e3ae7b5
1
Global\ad6324e1-b9e5-11e9-a007-00501e3ae7b5
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ZFT[.]QBAIDU[.]INFO
5
che[.]qianma[.]info
4
Files and or directories created Occurrences \SfcApi
9
%SystemRoot%\inf\oem13.PNF
9
%SystemRoot%\inf\oem13.inf
9
%SystemRoot%\LastGood\TMP4.tmp
9
%SystemRoot%\LastGood\system32\DRIVERS\winyyy.sys (copy)
9
%SystemRoot%\Temp\OLD5.tmp
9
%SystemRoot%\inf\INFCACHE.0
9
%SystemRoot%\inf\INFCACHE.1 (copy)
9
%SystemRoot%\stin.bat
9
%System32%\DRIVERS\winyyy.sys (copy)
9
%System32%\drivers\SET3.tmp
9
%System32%\drivers\SET6.tmp
9
%SystemRoot%\winsys.exe
9
%SystemRoot%\winsys.inf
9
%SystemRoot%\winyyy.sys
9
%SystemRoot%\SMSS.bat
8
%SystemRoot%\lsass.exe
8
%SystemRoot%\winhost.exe
8
%SystemRoot%\SysWOW64\SMSS.bat
1
%SystemRoot%\SysWOW64\lsasys.exe
1
%SystemRoot%\SysWOW64\winhost.exe
1
%System32%\SMSS.bat
1
%System32%\lsasys.exe
1
%System32%\winhost.exe
1
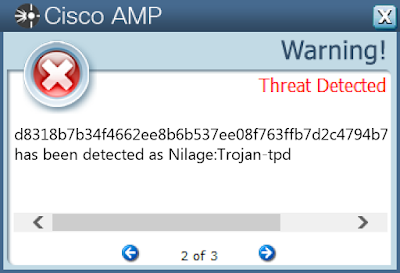
File Hashes 0f502626053f598a870375325ba7f7c81c2a791d0fd2401d4d6bd27c784b5f90
37e5a76ef3b1de92c162fb42b6e783a9734ccb1d4f61e1252ec9a8aba6417ca2
64b2a00a400501b742eb336eceee3a398b418315ed676e37e4d4f3fc7ab76e2c
722449fd99d698856b809df09e75e79ec4cee7840960e3df72a8ceb3d954134c
729d483257c6907c3f423d344f2cb5c9a78a899455ef246fc033c965043272bb
96d5ea254ca506622c2c70c4bcb8594c62a20db7ce9552deb302166bda37b226
b784fc881fb56dceeaad3afbad770a3c76eaa1acc389877be514af02413c06e7
d8318b7b34f4662ee8b6b537ee08f763ffb7d2c4794b722561d305db65c6fc5f
da0c26355fd7abdd3683beb7ab9f96efdec52207c150664bd177de4d794e6a53
de782ca97daf89c1208ea57618498de7aaa6f4ddbbc9794f3491dc947cca8cc3
e4aeeaf8b385bfccc637411b5030ab6c91a289cff425a14953e6549073478aa0Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
N/A
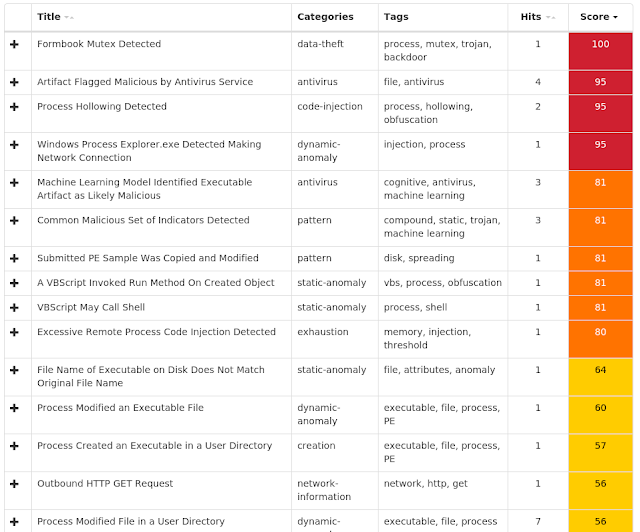
Screenshots of Detection AMP ThreatGrid Win.Worm.Phorpiex-7104335-2 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
Value Name: C:\Windows\M-5050402520507690204050\winmgr.exe
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Microsoft Windows Manager
15
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Microsoft Windows Manager
15
Mutexes Occurrences t1100
15
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 195[.]22[.]26[.]248
15
199[.]247[.]8[.]13
15
208[.]100[.]26[.]250
14
216[.]218[.]206[.]69
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences srv1300[.]ru
15
srv1000[.]ru
15
srv1100[.]ru
15
srv1200[.]ru
15
srv1400[.]ru
6
Files and or directories created Occurrences \autorun.inf
15
\Secret.exe
15
\Documents.exe
15
\Pictures.exe
15
\505050.exe
15
\Movies.exe
15
\Music.exe
15
\Private.exe
15
\windrv.exe
15
E:\autorun.inf
15
E:\Secret.exe
15
E:\505050.exe
15
E:\Documents.exe
15
E:\Movies.exe
15
E:\Music.exe
15
E:\Pictures.exe
15
E:\Private.exe
15
E:\windrv.exe
15
%APPDATA%\winmgr.txt
15
D:\autorun.inf
15
%SystemRoot%\M-5050402520507690204050
15
%SystemRoot%\M-5050402520507690204050\winmgr.exe
15
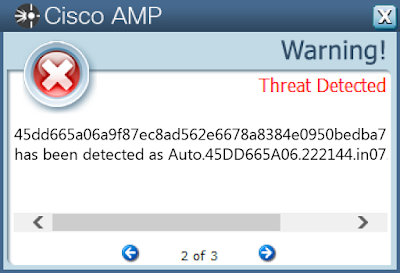
File Hashes 45dd665a06a9f87ec8ad562e6678a8384e0950bedba7beebba9c905157d1be52
4890d7aa8b302210932dacef3a0452ada7ee9c6565b1175f75925915e6036331
4ae81c49804d96d6913fc91ec79c77c0a16f09a5628cd9e6365bb621217ed3c9
5327d5502aa0e6cb6456809fc27cfcd1b0830a9cfd337d2a9493ec47a2eb6530
81489692294fa6e70b73f959a30a7bdd684141a72d3153b409f45173753acb82
8b66de0f1099ff243fbea1782c0ab7566bb9a201818d7793641e797c52067cab
8c03c0f22d09ba5384b804eced1c56e74f6c6df97d35a21f0d596dc2c80e5f5c
90b7e12af41916b8c82d0d83f6073e5bbc95f3c4ff1fd29391d50e7115967460
a0287b2bc66e1f6695d9c7e4ad6f70e8b1099f3f4b9761a4428e8ff02b173962
a80da89dfba6049d759500b272030ea7a97ab0d7cbe386456ddb65fa24b7f738
ce79b0e5a78be79315d2f20c6998812b75f4b95646d457034b4a534467e71558
d3da28644ddeaa70d828a659e27b83abcc284e578a62c26d1a4efc418cdac942
d6a90b5ff319cf5eb51d7b202c77e7e8037d2b160b80807e027ceb2e9834a29e
d8797103159c7ebf48b8ff67033f61866b1e46f70f82a91ce33b8afe27f0252e
e571c9202cd58870434c981bc0cf546473c446145d77362b1fdf7eb75f18400cCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
Screenshots of Detection AMP ThreatGrid Win.Malware.Zusy-7102354-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: F5DBF765
20
Mutexes Occurrences F5DBF765
25
\BaseNamedObjects\5145C9BD
11
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 216[.]218[.]185[.]162
23
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ynefefyopqvu[.]com
17
Files and or directories created Occurrences %APPDATA%\5145C9BD\bin.exe
23
%HOMEPATH%\AppData\LocalLow\F5DBF765
22
%APPDATA%\F5DBF765
21
%APPDATA%\F5DBF765\bin.exe
20
File Hashes 03e74e58f2aed047d6bac9bde066206c64d3e48a4c865d86e29bc62edbb19c77
0eb478d5757cb872b80386250de948ac3abc76b5ebf0d7f2ab38f6a6ad95479c
0f779f8c2d4d342da2fc6bda22eb75bcc3939102ecea72847fafd9cbc10e26ad
1ed3291baf7d32ab690b56f430399d7c46d261176c5b05b3cf8f2cdd1f9a4681
2828b72f4856b8054ff75af987aa43d84f2d42405979c99e89e6082afc47d6da
2bcd2e02bf0cefed898990ae64791f9c294c50695542e2cf0e073c1f12dfed94
2bf93320c70c222aa89db3df81845d9277dc8eb7ff764b63f5ad4c5b78839557
2ecbe3620a6f08eadaf5c14aa35b2975b07ee41827f7004b692a7508b6a3c1a5
354d64a310cc3ce7a957c29f8654201ee0e79237609172e746aa25b5e038b837
3776eb64c25acfc28fd35fe6a123a0b4b1e0ee7e4ff2cde20169f1a914c01df1
39627480021a400069ee270b040601af19aaaf669bc6db2bf64058e14fb13875
3d0a697fec4326426bf22ae6b848700a3274c55767fb18a8e0748fc7f3024597
3e7ed99b45129a136287f785dffb67b044da28fd2232190fafc30c759c447a96
460de49bf98a472753462a9264bf40ea24b95fa667f3b8d7d010ca3fa94b715a
47e8ec99e3c0bb7526b381db1bec98b13df1deb95c56868703309bf4979155d2
48a0d3749139aebb4d435db7158aa1916e4d305139d3db168c795c68b9431ed6
4c46b50c94ad30df7661d5be4eaf3da8ed1f8f1924fa25f0b87f9e2bc5b21dc8
4cad121b0408001868b22b92d7def0a3125efe64ebd5d28bfbd933395fecf512
5ecd70109eec90c8ac0869398a4da72f9264ef5f3f61f2be883456ddd9bc6a32
62a2d6d129e578279b691542eea61040212cc4f26855beecd991118343d081cf
62afaeae9d1bc8473416423c46423951eb35cac6927798f6d9967a8fb358af2a
6b2d254b662c18e9a23fead0e661587c3f46b8fc8fac940fedb13e4e2b3d8bd6
6f3c9f7a94b4f3a3ecf29bcd646a55bb3d286ffd20b98fe2d984594dd73dbb5e
72683fb9644dbdc7d2fc1ba436d7f7379f2ce86fe3dac5431d29160abff07755
72c16952c7f016b6bbac0e1cc243aec6d9eacb1c1db8c3f744499584672580e5*See JSON for more IOCs
Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
Screenshots of Detection AMP ThreatGrid Umbrella Win.Worm.Brontok-7102096-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\CONTROL PANEL\DESKTOP
Value Name: ScreenSaverIsSecure
25
<HKCU>\CONTROL PANEL\DESKTOP
Value Name: ScreenSaveTimeOut
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: NoTrayContextMenu
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CABINETSTATE
Value Name: FullPathAddress
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
Value Name: HideFileExt
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
Value Name: Hidden
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: NoViewContextMenu
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: DisableRegistryTools
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: DisallowRun
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: NoTrayItemsDisplay
25
<HKCU>\CONTROL PANEL\DESKTOP
Value Name: SCRNSAVE.EXE
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: nEwb0Rn
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: n3wb012nAdministrator
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: n210bw3n
25
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SAFEBOOT
Value Name: AlternateShell
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Shell
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Userinit
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\AEDEBUG
Value Name: Debugger
25
<HKLM>\SOFTWARE\CLASSES\LNKFILE\SHELL\OPEN\COMMAND
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION
Value Name: RegisteredOrganization
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION
Value Name: RegisteredOwner
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: NoFileAssociate
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: NoFileAssociate
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: DisallowRun
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\DISALLOWRUN
Value Name: 1
25
Mutexes Occurrences Local\MSCTF.Asm.MutexWinlogon2
25
Local\MSCTF.CtfMonitorInstMutexWinlogon2
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 51[.]141[.]32[.]51
24
Domain Names contacted by malware. Does not indicate maliciousness Occurrences time[.]microsoft[.]akadns[.]net
24
Files and or directories created Occurrences %System32%\winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
25
%HOMEPATH%\Local Settings\Application Data\winlogon.exe
24
%SystemRoot%\nEwb0Rn.exe
22
%System32%\DamageControl.scr
22
%System32%\JawsOfLife.exe
22
\nEwb0Rn.exe
22
\Documents and Settings\All Users\Start Menu\Programs\Startup\Empty.pif
21
%HOMEPATH%\Local Settings\Application Data\WINDOWS\CSRSS.EXE
21
%HOMEPATH%\Local Settings\Application Data\WINDOWS\LSASS.EXE
21
%HOMEPATH%\Local Settings\Application Data\WINDOWS\SERVICES.EXE
21
%HOMEPATH%\Local Settings\Application Data\WINDOWS\SMSS.EXE
21
%HOMEPATH%\Local Settings\Application Data\WINDOWS\WINLOGON.EXE
21
%System32%\WishfulThinking.exe
21
\about.htm
18
%ProgramData%\Microsoft\Windows\Start Menu\Programs\Startup\Empty.pif
2
%SystemRoot%\msvbvm60.dll
2
E:\Download Administrator.exe
2
E:\MP3[NEW-RELEASE].exe
2
E:\nEwb0Rn\New Folder.exe
2
\Download Administrator.exe
2
\Friendster Blog.exe
2
\MP3[NEW-RELEASE].exe
2
\Mini Games.exe
2
\StyleXP-WindowsVistaPack.exe
2
%LOCALAPPDATA%\WINDOWS\CSRSS.EXE
2
*See JSON for more IOCs
File Hashes 642e0acdbece0f1e99604f63488e2d0ae4845080adba80ecfc55cbc95db05bc5
73fcbb6f10cd849bff109dd05cf89d9b612302faed9c382791d6df4d024bc009
7e98f0308fd88e97e4f80b1e2c6845e18186e07d2a27d936bccadad719114334
809f403efb1c7f19a30cfdd62841b898ebfbc1e91626928bb372ad630d8d9b81
81dc5726d4af65258dec6ccf0dda1327fcacb9b950539992fff82859c6645a27
85506de211f0441c3bbf0e98668a7d3d1c2a62aadc07ef82968245644fca4b00
8ef7ee2b458b006e3364f972a744031cb99c9a9d7bb4329b4a41e6d0e1cbb784
96093b99c83298eeb0aa6ac9a9c006f23ad8d8c1818b8a88c62ea1f88fd7d368
9784b14130ecabb2d53ea4226e79f6dca68e9bf31a83cc447a0113464582a5df
99da8c945884ce7e214aba8f0b363532082d660bae2693c098b230701d236b7b
9b4eabfb075dd32ce295b7dab5a0347f7c5f89021c8804cf88152b0be7de1544
9bf0202ddec81f84ad07867e28214decfef7fd5bd1327a6b9482de823d90ff60
9da800449b88fbc076c16d4fa6d42645367e9b0e1c3306ad5f65df77b3348a72
9de658e0f67bdcae688d74907763d87f280086e5c47cc0c2ee545f8cf675a42d
a2cbadc9bb11b4174d11407599ae95ee3680054e04105b0ef435628dcc252954
a84944ae92cc5732281c71ffa5b17b68ee362441bc8093da4d59bc0ca5723f74
a86c3e90ba9c53348dde346e5bebf63d8198dafabf82baaf298f5b8c23ff4fa8
b36b7ceef1d16e877580931a8ec5a70462f0513a4d113bcb1e3e198830aa3447
c600cf8b855fefb4e9e1e4d0c1f0d92c58eee1f06d53a88b0d96ecac94e7dbfd
c88906c44642322a0ad3fd0207e9873d89d16d15b317c0e51d1fed28138ce210
cba998582b123d210bccb81e49db805736439eba5f4735883d4597e2c5895f85
d296651dfc3d2d3f31115e48e815449bf71d06a64318462c1bd2f0e299d6a63f
d38e3cfe3f57ddea4f4b8966b4b51812af1ac688849a8bbee086ec905f0406d1
d3a23ff88633039f39ea421a2d197e3b6d9bb26ad6e5500dfb559b126884fbac
d5456a558e240fbe2e116155e4a04c8c038550ab4c2c4103d9e49da2a8ba495f*See JSON for more IOCs
Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
N/A
Screenshots of Detection AMP ThreatGrid Win.Worm.Socks-7102087-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ntuser
11
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: autoload
11
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SCHEDULE
Value Name: ImagePath
11
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ntuser
11
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: autoload
11
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 208[.]100[.]26[.]251
11
23[.]20[.]239[.]12
11
104[.]25[.]37[.]108
8
104[.]25[.]38[.]108
3
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]hugedomains[.]com
11
fewfwe[.]com
11
fewfwe[.]net
11
static[.]HugeDomains[.]com
7
Files and or directories created Occurrences %HOMEPATH%\cftmon.exe
11
%SystemRoot%\SysWOW64\drivers\spools.exe
11
File Hashes 16c60b7975280008e5491cae5e71fa48671be5c97010488faf63956c6552c628
44f3b28713682be10e02bdf52a99290b733931bac2e8c0b4102e4f458b1284bd
5943ca2e22ce53fcc9b7caabfca8d8cf721ccbd4f536833b10a370303fcaf505
7e9b3d25d766a1ff8520187b8f49387b1f654778ba58838e37e0ff741ab10f73
8dfb856841b2f70e2bffb74f26225dcc42d65d3fa6250767397ac30bf21823f5
a52c2e6216c1685d35385419c9c8cd854ea70490f923bbc3eaff92df26bafbc6
a73604e5b2456cc803dae1b79d91db32ce2535562bdc73eb762394540c79d7af
b9510728d8c9d3807e26ba9286f3ab6890e335a197b377201b939230a3d6d69b
c8a3ac87c01529800bd6461d94702428322c7a3aed93ed676f0a55d3d56addd9
e4c7f241397b5a46c3081214f1eb67b51bd6d5dd20cd984db4f5ac164f260bf1
fe80f9c59fc294d3a6fe8d973ea687f92daf1a6988e13a26bcec20f34f44ab25Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
Screenshots of Detection AMP ThreatGrid Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: Registry Key Name
11
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\INTELLIFORMS\STORAGE2
8
<HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX
8
<HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX\20.0.1 (EN-US)\MAIN
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9375CFF0413111D3B88A00104B2A6676
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9375CFF0413111D3B88A00104B2A6676\00000001
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9375CFF0413111D3B88A00104B2A6676\00000002
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9375CFF0413111D3B88A00104B2A6676\00000003
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\0A0D020000000000C000000000000046
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\13DBB0C8AA05101A9BB000AA002FC45A
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\33FD244257221B4AA4A1D9E6CACF8474
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\3517490D76624C419A828607E2A54604
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\4C8F4917D8AB2943A2B2D4227B0585BF
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\5309EDC19DC6C14CBAD5BA06BDBDABD9
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\82FA2A40D311B5469A626349C16CE09B
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\8503020000000000C000000000000046
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9207F3E0A3B11019908B08002B2A56C2
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9E71065376EE7F459F30EA2534981B83
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\A88F7DCF2E30234E8288283D75A65EFB
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\C02EBC5353D9CD11975200AA004AE40E
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\D33FC3B19A738142B2FC0C56BD56AD8C
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\DDB0922FC50B8D42BE5A821EDE840761
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\DF18513432D1694F96E6423201804111
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\ECD15244C3E90A4FBD0588A41AB27C55
8
Mutexes Occurrences 8-3503835SZBFHHZ
11
551NC37UWE1041Fz
11
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 213[.]171[.]195[.]105
2
213[.]186[.]33[.]5
1
74[.]220[.]215[.]74
1
154[.]91[.]238[.]82
1
208[.]91[.]197[.]39
1
47[.]91[.]169[.]15
1
103[.]251[.]238[.]111
1
185[.]218[.]125[.]67
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]aamyz87[.]info
3
www[.]ingenuity[.]degree
2
www[.]activeliberal[.]win
2
www[.]beautagram[.]com
2
gmpg[.]org
1
www[.]cyqunli[.]com
1
WWW[.]SOJAH[.]STORE
1
www[.]qhdljj[.]com
1
www[.]tzhmc[.]net
1
www[.]yourbostonrefinance[.]com
1
www[.]immersive-journey[.]com
1
www[.]studiodennis[.]com
1
www[.]wanggh[.]com
1
www[.]americatourbus[.]info
1
www[.]kalayab[.]download
1
www[.]shaoerjia[.]com
1
www[.]maybrooktaxiandlimo[.]info
1
www[.]tipshots[.]com
1
Files and or directories created Occurrences %TEMP%\subfolder
11
%TEMP%\subfolder\filename.exe
11
%TEMP%\subfolder\filename.vbs
11
%APPDATA%\551NC37U
8
%APPDATA%\551NC37U\551log.ini
8
%APPDATA%\551NC37U\551logrc.ini
8
%APPDATA%\551NC37U\551logri.ini
8
%APPDATA%\551NC37U\551logrv.ini
8
%APPDATA%\551NC37U\551logim.jpeg
7
%ProgramFiles(x86)%\Amb80q
1
%ProgramFiles(x86)%\Amb80q\serviceslds.exe
1
%TEMP%\Amb80q
1
%TEMP%\Amb80q\serviceslds.exe
1
File Hashes 0d9c018014931c251ac8bf951a99fcb974673e895f27e62fa6ead981b2d7b4a2
152f38878f5a8b19fef76f086f60f9a350bacfb55ced80cdbceb200b88e9c9fa
2908ff55a23aa61c2393df98cd6847f60343f296aeeb7bcc60c510701dcbf84f
2b6f4aad989ddca53c3cb56bbddb52e8577cbb40939f97ef9c7efb60d24a39ae
2c82db5284c54272e4ba7ac3523ffccf496d1584fd99444c0eaa225773e29721
6fc83ce9acf100506d039461642290e798f46baaf8034b5f2ead098edc3d9f4c
78663a1055ddd96e74b633b43128c83378787b52f031194ebaeccf69a0222645
c1b420d09459d96aa0bbc12a6b010a6d12b5910ffbd0289fa7a3ed3aebfac40d
d27385d640966750e4ead578539a36a62ba0ae5c9083f03865927ef5deac2d8f
d7bb858da997925668b1f85b83ba9f01b381a16de1ee6c37d003658cb98c4990
e4baf530d129b0a3a87e5de09ce86efc7c6c532ec91ade78c934d5e8d818938eCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
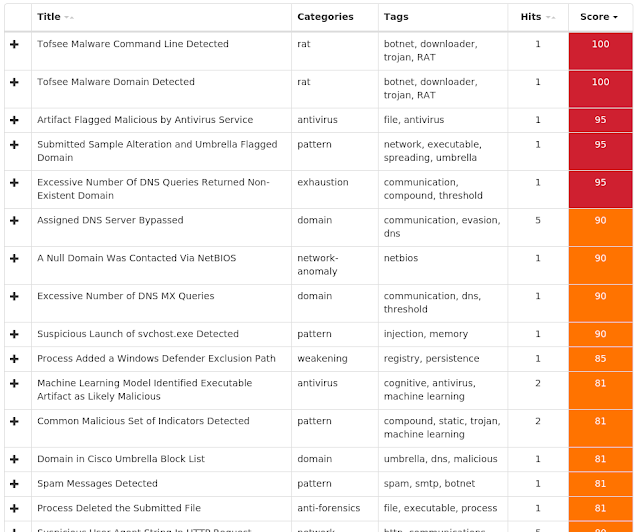
Screenshots of Detection AMP ThreatGrid Win.Malware.Tofsee-7101989-1 Indicators of Compromise Registry Keys Occurrences <HKU>\.DEFAULT\CONTROL PANEL\BUSES
15
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config1
15
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config2
15
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config0
15
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config3
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Type
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Start
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ErrorControl
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: DisplayName
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: WOW64
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ObjectName
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Description
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ImagePath
12
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config4
4
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\wpdjiqwl
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\xqekjrxm
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\qjxdckqf
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\unbhgouj
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\ibpvucix
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\athnmuap
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\tmagfnti
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\piwcbjpe
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\slzfemsh
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\mftzygmb
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 239[.]255[.]255[.]250
15
69[.]55[.]5[.]250
15
46[.]4[.]52[.]109
15
176[.]111[.]49[.]43
15
85[.]25[.]119[.]25
15
144[.]76[.]199[.]2
15
144[.]76[.]199[.]43
15
43[.]231[.]4[.]7
15
192[.]0[.]47[.]59
15
74[.]125[.]192[.]26
15
168[.]95[.]5[.]117
15
98[.]137[.]159[.]25
15
188[.]125[.]73[.]87
14
172[.]217[.]12[.]228
14
213[.]205[.]33[.]62
14
212[.]82[.]101[.]46
13
67[.]195[.]228[.]106
13
168[.]95[.]6[.]59
13
74[.]6[.]137[.]65
13
96[.]114[.]157[.]80
13
213[.]209[.]1[.]129
12
66[.]218[.]85[.]139
12
213[.]205[.]33[.]61
12
67[.]195[.]228[.]110
12
209[.]85[.]202[.]26
12
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 250[.]5[.]55[.]69[.]in-addr[.]arpa
15
250[.]5[.]55[.]69[.]zen[.]spamhaus[.]org
15
250[.]5[.]55[.]69[.]cbl[.]abuseat[.]org
15
mta5[.]am0[.]yahoodns[.]net
15
mx-eu[.]mail[.]am0[.]yahoodns[.]net
15
250[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net
15
whois[.]iana[.]org
15
250[.]5[.]55[.]69[.]bl[.]spamcop[.]net
15
whois[.]arin[.]net
15
250[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org
15
hotmail-com[.]olc[.]protection[.]outlook[.]com
15
microsoft-com[.]mail[.]protection[.]outlook[.]com
15
honeypus[.]rusladies[.]cn
15
marina99[.]ruladies[.]cn
15
eur[.]olc[.]protection[.]outlook[.]com
14
mx-aol[.]mail[.]gm0[.]yahoodns[.]net
13
aol[.]com
13
msx-smtp-mx1[.]hinet[.]net
13
ipinfo[.]io
12
smtp-in[.]libero[.]it
12
libero[.]it
12
tiscali[.]it
12
etb-1[.]mail[.]tiscali[.]it
12
tiscalinet[.]it
12
mx3[.]qq[.]com
12
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile
15
%SystemRoot%\SysWOW64\config\systemprofile:.repos
15
%TEMP%\<random, matching '[a-z]{8}'>.exe
15
%SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>
15
%System32%\<random, matching '[a-z]{8}\[a-z]{6,8}'>.exe (copy)
14
%TEMP%\ondzgch.exe
1
%TEMP%\rqgcjfk.exe
1
%TEMP%\baqmtpu.exe
1
%TEMP%\qpfbiej.exe
1
File Hashes 03014df764784dff0d3c56cccdbfb07ca0c04cdbd302403ebedc466e83e18f6c
0c30a1e0c3e91cbaf62beb5e217b44f5065f7e97c19d0eb181e0d37720be178d
213b7ea1e4fee2c08e48c1536b099ab55b0ace638710a8c1920a834ac80648b5
23dc9f05f6003f3730b5731072eb9754fbf80a353cdbe94704a5e425a18aa0e5
31702562438866f49dddb8c0fc8e6d9b68ec2eb73b142c899479102850de0fdd
398288b17c7ffc8b569ac4c8623cb4e1dc4c97da2a021bfd86182fd23e92735c
5a3fe5af1026e7f6217e91cc4b6d1c888efde908369b1b8a216c6e954c648d3d
5d9dc6e667bd105d7e2e77162e87e94b0c5a72be94c1ae726e45ccf4d23753bb
7c73e7cfd0be419b1538309b2a5fb45a2515808fe92492db79e0cbbdce976643
8895dda1641282ea209e8482269cb7c34f2da9843c9d0293fc3d6aec2612e212
8ef82ce7ed1ed7c6ddd446b4a8a7144acac21aab0af0ee82ac764b525ea00b07
b9c035fd6f4d2a6b8d619812b98764885927b80f3a8369e87495f95b2bcbf44d
d2f043f4002cdcbd88319a360dc11a0aec1ebae63f37ef9a845beb23779a1151
e42a5b04986cbdc9c13fcb99b2e1e0a2d156e6faaf1369ed71a92220a1347f06
e4c584dd32770439810067fe8607f74a64380fe354725ff4a5d42215b873b1e1Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
Screenshots of Detection AMP ThreatGrid Umbrella Win.Malware.Chthonic-7101817-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
Value Name: Hidden
24
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLUA
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Start
24
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
Value Name: ShowSuperHidden
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS
Value Name: Start
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: Start
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV
Value Name: Start
24
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: TaskbarNoNotification
24
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: TaskbarNoNotification
24
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: HideSCAHealth
24
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: HideSCAHealth
24
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
Value Name: 2827271685
24
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 20[.]45[.]1[.]107
21
40[.]91[.]124[.]111
21
192[.]42[.]119[.]41
18
40[.]67[.]189[.]14
15
20[.]41[.]46[.]145
8
192[.]42[.]116[.]41
6
40[.]90[.]247[.]210
2
Domain Names contacted by malware. Does not indicate maliciousness Occurrences dnshkjashsdk3d111[.]ru
24
www[.]update[.]microsoft[.]com[.]nsatc[.]net
21
Files and or directories created Occurrences \TEMP\005F5E~1.EXE
1
\TEMP\1B106F~1.EXE
1
\TEMP\0956E4~1.EXE
1
\TEMP\382BAE~1.EXE
1
\TEMP\00BA93~1.EXE
1
\TEMP\12CC7F~1.EXE
1
File Hashes 005f5e12924dad7fe014a84db45f13429f6ece0b8247f5d352d715b2846c0c4f
00ba939c36fa3b49267f278dc9bb198bc9ae990ce888720048bea52a40cf1c23
0956e4f5453664330032f4d772aba4fc67c67543ca6b5b5970277d3509c0b947
12cc7fd46b6a47ac1c87526633c7a608d31275b31c885f8f47bb994d8ae19e90
17e720effe9bb9123f12df8149180130f8239870cf0d9267f67cf476b6ab44e5
1b106ffffabfe8c46bca9ad44e1fd47a2150a99a701452d4a6d2e51fb968a1af
382baee7e059546686749c2e25e7077db13f724e67629aa253033b53c4aff934
38fa5765572ad2cd028f6aa284d0b780b881d390dd5a8ae32c06d39e7442c026
42c5dd7eebdd5bd210832a6588259e33e737208817c4c1817615b3995c3ac378
4471cabd599d69896184f4e9264f377961488fb4c6cdf41992e0f5b2096c9899
46901064a8beca5f66dd0e9072feab0abb6ec3223b54f6bad81959a306915b47
62828391fca3a6d82749ca15cd2eb5d28153001457df7f1806377235a95603f5
63641d47b507920bd79600352d71655abed663ebe9347ccc5f7841b9dcb95d1b
73b71b837f43a97bfab5c6f541d54b7b090fef3893a0e78b769140a946ba162a
75da2447c69b6b0d78ace3c73e9302688b46cf1bdddac5c61d0c7c8403d39036
7a38d305151c979898e46d7d52dcb8bd4dc67485415a7d122c81facd320bcba8
8be6459aa2282ae9cf52ec766d7c8c55721988ba866339e358d15ae47fbae61f
8c1ab54da3a2372a624d22d902278e048942e9a495b71d330f1eee4073b14eb7
8c495bba75c5ab08e66063bd323525502188899663ad8ac5183baa2a42583bb8
8e3fd8961f232fdbf26019c56901c76db886ed56f86fba8c2f3f0631d33f969e
a7316bed0f3820f1ca51eb4c687c763d059d086b610a4250a4051d795b47fd44
acc883924cc2e4b6f5f979a2586e2246a9837faa07702c6a18f90a086d681796
aebb9e807054a61b9125efa05507a9e2cdc6812bd286c007367713d1f377b514
b01cefc142aee229491e1b19a32888b921f1935c4d472807b7d115dc568356e4
b50a5542b24d20aa60a3614699c36f4f75062c7492955b9785fad0df4d0c1525*See JSON for more IOCs
Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
Screenshots of Detection AMP ThreatGrid Umbrella Win.Malware.Remcos-7101023-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\REMCOS-LOPOXR
25
<HKCU>\SOFTWARE\REMCOS-LOPOXR
Value Name: exepath
25
<HKCU>\SOFTWARE\REMCOS-LOPOXR
Value Name: lic
25
Mutexes Occurrences Remcos_Mutex_Inj
25
Remcos-LOPOXR
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 95[.]140[.]125[.]58
25
Files and or directories created Occurrences %SystemRoot%\Tasks\Stencilens0.job
25
%APPDATA%\antepenuit.pif
25
%System32%\Tasks\Stencilens0
25
File Hashes 081f8d61a3cd912e00e9f53f6a8a3923164cb86205cdaab63abd9b2814ed9777
0a7cfd1b34af81f40d8f05f85bcfa9139bf9ec2eff82fcda1fba409b5a7650f2
0bed354bdcb152cbd012fe1c37d53c8c02da11c11084e8eb83bf577bdd80a464
0d0a83234404e0c08958aafcb6910f6cdfd7dc75d9713bf654c89b99fc341bdc
0d271c5c9ca84e2ab86f6c95d32802e7ec64b846d07b7bf81d0f82409b1b2101
1092677328703cc000e9c63be2b0a2f46103c14f053e9ee079ffd7f0ca2d6f8f
1831367e74cc96e0f72ec11f054525e6c024215bde7b61f110f9b73338ce03cf
1a801a28dfffaea7742f1d467a2c80bb8632b39db214d22abc804f0bc6515cc6
2027c7d8d4403334509ae483d7e0c8be28640a39d4bd9441f87cdc259b92ca4c
2e16d6892291790348a9ebe49ca192925a8db1a7a286c0fbb44c30ba1dff74e2
354c76d9316c5ba1edd6b052f361ec42e925b878915879c1ca903f81b05bfd7b
36c6f434e27087f707a813495e82bdbeac383507ce5a2ca3816e4557a4cddb5e
376746cbbf27f98f9f07676bdb6a5e556fee27b1ae1c388416f17d5e4bc4c62f
392474631d8c58ec089b896569d6e362484865b479c85e2c0906b87349bce68f
3adb3198ca6ac80a842b6aba596fef43eda6aca0f32dbdf59d60133eabde541d
40b75ec8743801bfcbac60c8f0b232971aa61bfb031fe829132a8537c63b9a41
40cf7790bd379a14cecc933b48e6f341164ad872d5ee61136b91092cbfe14aba
49c149ba04e9af98c5da19d305556af3d7cdacf6e2044abfef604b0e5bb38d29
54a0550408c68795a9652e18a4e3820cca6c16246c2e8198497e795dba448644
585061420029af8f635eefe1834874a422d140b8adfbc77d0e789ea9d4ade500
5914996ccdfda579afbd3116cae43d5bd35db5eee27545a60ddef3270af351f1
5a756ce1c997dd1615ea2fc97e5dd3cfcbc29a5f848e5ea6ede37e3d526d4ce3
5e7c49bef106709d6cfc9d85b8d82dc0583f42c1701cb7990e700914db842186
5f9034f63a3cf362b1d2f7baf35a7fadceccd2add363bf7ef3cae4e95a6afb86
5faf5309caaeb3ed3d1b4825b55646c83d769d22c226420bb6418e037cd2f029*See JSON for more IOCs
Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
N/A
Screenshots of Detection AMP ThreatGrid Exploit Prevention Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities.
CVE-2019-0708 detected - (2337)
An attempt to exploit CVE-2019-0708 has been detected. The vulnerability, dubbed BlueKeep, is a heap memory corruption which can be triggered by sending a specially crafted Remote Desktop Protocol (RDP request). Since this vulnerability can be triggered without authentication and allows remote code execution, it can be used by worms to spread automatically without human interaction.
Madshi injection detected - (1399)
Madshi is a code injection framework that uses process injection to start a new thread if other methods to start a thread within a process fail. This framework is used by a number of security solutions. It is also possible for malware to use this technique.
Trickbot malware detected - (1212)
Trickbot is a banking Trojan which appeared in late 2016. Due to the similarities between Trickbot and Dyre, it is suspected some of the individuals responsible for Dyre are now responsible for Trickbot. Trickbot has been rapidly evolving over the months since it has appeared. However, Trickbot is still missing some of the capabilities Dyre possessed. Its current modules include DLL injection, system information gathering, and email searching.
Excessively long PowerShell command detected - (1002)
A PowerShell command with a very long command line argument that may indicate an obfuscated script has been detected. PowerShell is an extensible Windows scripting language present on all versions of Windows. Malware authors use PowerShell in an attempt to evade security software or other monitoring that is not tuned to detect PowerShell based threats.
Kovter injection detected - (466)
A process was injected into, most likely by an existing Kovter infection. Kovter is a click fraud Trojan that can also act as an information stealer. Kovter is also file-less malware meaning the malicious DLL is stored inside Windows registry and injected directly into memory using PowerShell. It can detect and report the usage of monitoring software such as wireshark and sandboxes to its C2. It spreads through malicious advertising and spam campaigns.
Process hollowing detected - (297)
Process hollowing is a technique used by some programs to avoid static analysis. In typical usage, a process is started and its obfuscated or encrypted contents are unpacked into memory. The parent then manually sets up the first stages of launching a child process, but before launching it, the memory is cleared and filled in with the memory from the parent instead.
Gamarue malware detected - (152)
Gamarue is a family of malware that can download files and steal information from an infected system. Worm variants of the Gamarue family may spread by infecting USB drives or portable hard disks that have been plugged into a compromised system.
Dealply adware detected - (118)
DealPly is adware, which claims to improve your online shopping experience. It is often bundled into other legitimate installers and is difficult to uninstall. It creates pop-up advertisements and injects advertisements on webpages. Adware has also been known to download and install malware.
Possible fileless malware download - (95)
A site commonly used by fileless malware to download additional data has been detected. Several different families of malware have been observed using these sites to download additional stages to inject into other processes.
IcedID malware detected - (52)
IcedID is a banking Trojan. It uses both web browser injection and browser redirection to steal banking and/or other financial credentials and data. The features and sophistication of IcedID demonstrate the malware author's knowledge and technical skill for this kind of fraud, and suggest the authors have previous experience creating banking Trojans. IcedID has been observed being installed by Emotet or Ursnif. Systems infected with IcedID should also be scanned for additional
malware infections.