Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Oct. 18 and Oct. 25. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
Threat Name Type Description Win.Dropper.Emotet-7355854-0
Dropper
Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails.
Win.Malware.Ursnif-7355802-1
Malware
Ursnif is used to steal sensitive information from an infected host and can also act as a malware downloader. It is commonly spread through malicious emails or exploit kits.
Win.Malware.Upatre-7355650-0
Malware
Upatre is a trojan that is often delivered through spam emails with malicious attachments or links. It is known to be a downloader and installer for other malware.
Win.Dropper.Kovter-7352197-0
Dropper
Kovter is known for its fileless persistence mechanism. This family of malware creates several malicious registry entries which store it's malicious code. Kovter is capable of reinfecting a system even if the file system has been cleaned of the infection. It has been used in the past to spread ransomware and click-fraud malware.
Win.Malware.Trickbot-7352185-1
Malware
Trickbot is a banking trojan targeting sensitive information for select financial institutions. This malware is frequently distributed through malicious spam campaigns. Many of these campaigns rely on downloaders for distribution, such as VB Scripts.
Win.Virus.Expiro-7350682-0
Virus
Expiro is a known file infector and information stealer that hinders analysis with anti-debugging and anti-analysis tricks.
Win.Malware.Tofsee-7349716-1
Malware
Tofsee is multipurpose malware that features a number of modules used to carry out various activities, such as sending spam messages, conducting click fraud, mining cryptocurrency and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator’s control.
Win.Malware.Nymaim-7348211-1
Malware
Nymaim is malware that can be used to deliver ransomware and other malicious payloads. It uses a domain generation algorithm to generate potential command and control (C2) domains to connect to additional payloads.
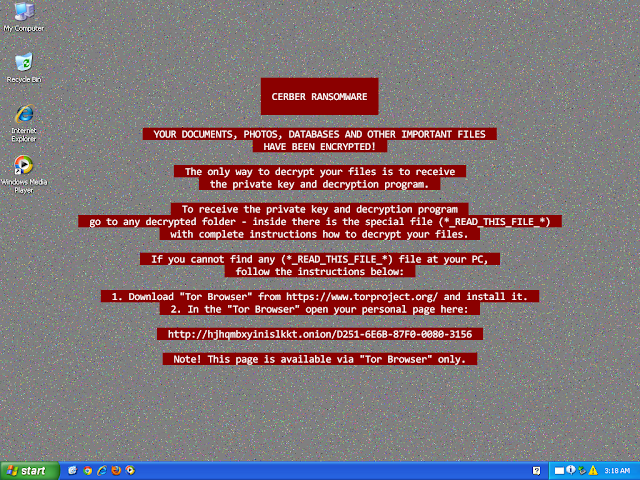
Win.Malware.Cerber-7343756-1
Malware
Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns, this is no longer the case.
Threat Breakdown Win.Dropper.Emotet-7355854-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPOOLERIPSPS
10
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPOOLERIPSPS
Value Name: Type
10
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPOOLERIPSPS
Value Name: Start
10
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPOOLERIPSPS
Value Name: ErrorControl
10
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPOOLERIPSPS
Value Name: ImagePath
10
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPOOLERIPSPS
Value Name: DisplayName
10
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPOOLERIPSPS
Value Name: WOW64
10
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SPOOLERIPSPS
Value Name: ObjectName
10
<HKLM>\SOFTWARE\CLASSES\MFCCALC.CALCULATOR
10
<HKLM>\SOFTWARE\CLASSES\MFCCALC.CALCULATOR\CLSID
10
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{62C4DD10-F45E-11CD-8C3D-00AA004BB3B7}\PROGID
10
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{62C4DD10-F45E-11CD-8C3D-00AA004BB3B7}\INPROCHANDLER32
10
<HKLM>\SOFTWARE\CLASSES\MFCCALC.CALCULATOR
10
<HKLM>\SOFTWARE\CLASSES\MFCCALC.CALCULATOR\CLSID
10
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{62C4DD10-F45E-11CD-8C3D-00AA004BB3B7}\LOCALSERVER32
10
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{62C4DD10-F45E-11CD-8C3D-00AA004BB3B7}
9
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{62C4DD10-F45E-11CD-8C3D-00AA004BB3B7}
9
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{62C4DD10-F45E-11CD-8C3D-00AA004BB3B7}\PROGID
9
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{62C4DD10-F45E-11CD-8C3D-00AA004BB3B7}\INPROCHANDLER32
9
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{62C4DD10-F45E-11CD-8C3D-00AA004BB3B7}\LOCALSERVER32
9
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\\PROGID
1
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\\INPROCHANDLER32
1
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\\INPROCHANDLER32
1
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID
1
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\\LOCALSERVER32
1
Mutexes Occurrences Global\I98B68E3C
10
Global\M98B68E3C
10
Global\M3C28B0E4
8
Global\I3C28B0E4
8
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 45[.]33[.]54[.]74
10
54[.]38[.]94[.]197
9
173[.]194[.]68[.]108/31
8
74[.]208[.]5[.]15
7
193[.]70[.]18[.]144
7
172[.]217[.]10[.]83
7
74[.]208[.]5[.]2
6
74[.]6[.]141[.]50/31
6
205[.]178[.]146[.]249
5
173[.]203[.]187[.]10
5
173[.]203[.]187[.]14
5
205[.]204[.]101[.]152
5
74[.]6[.]141[.]44/31
5
17[.]36[.]205[.]74/31
5
178[.]128[.]148[.]110
5
209[.]141[.]41[.]136
5
217[.]69[.]139[.]160
4
205[.]178[.]146[.]235
4
69[.]147[.]92[.]12
4
65[.]55[.]72[.]183
4
159[.]127[.]187[.]12
4
94[.]100[.]180[.]70
4
94[.]100[.]180[.]160
4
23[.]227[.]38[.]64
4
172[.]217[.]3[.]115
4
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences secure[.]emailsrvr[.]com
8
smtp-mail[.]outlook[.]com
8
smtpout[.]secureserver[.]net
8
smtp[.]mail[.]com
7
smtp[.]mail[.]ru
7
smtp[.]aol[.]com
6
smtp[.]comcast[.]net
6
smtp[.]1and1[.]com
5
smtp[.]prodigy[.]net[.]mx
5
ssl0[.]ovh[.]net
5
mail[.]paypal[.]com
4
mail[.]mail[.]ru
4
smtp[.]dsl[.]telkomsa[.]net
4
mail[.]widatra[.]com
3
smtp[.]dropbox[.]com
3
outbound[.]att[.]net
3
smtp[.]emailsrvr[.]com
3
smtp[.]verizon[.]net
3
smtp[.]idmsa[.]apple[.]com
3
smtp[.]cox[.]net
3
mail[.]enterprisesolutioninc[.]com
3
smtp[.]mxhichina[.]com
3
mail[.]americashomeplace[.]com
3
smtp[.]fatcow[.]com
3
relais[.]videotron[.]ca
3
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\spooleripspsa.exe
1
\TEMP\aatgsjewU4YpaJ.exe
1
\TEMP\4uwvBUGZ.exe
1
\TEMP\sqjjfdnz8obMXZL.exe
1
\TEMP\D9VaRGmZ.exe
1
%SystemRoot%\TEMP\D3F5.tmp
1
\TEMP\PdapKX6bjx.exe
1
File Hashes 0bf9f6907fd3f6a3f5734b23120671230c480b03c96a1779348f9cdc49bb58f8
11f97585ad2aeb41f4c972b2e29523d4ca70cc4a065547d9abca659d2c3193d1
418ba2dbbda1d95428128998352856705040857f1008fbdf809cdeb7c174211f
9d8895333339dde00e8778e9181cfbf0df29e35c0dda842aa30ff7a44b96cd11
a3a3de174e94beb142799b6f03c84bfe4c563e287a6a5288bbd64ccc9910ce24
aea84511050a07ff22e621888f19921585485fd171228cc6ad723f4c1b90225f
b988217de26056f0db1ba17940d5fc0e138c59fc46652d7b5046281f8152aa0b
ca3889a38bf35766b0ad59605bd6d3f6c333309f690708a3b51f7e80cc32be85
d4363da6ccb0a0ef3c69010d7351a2d9459e4c5fef26fe00c240eb901125cd78
ddb191fb3328dd25f79f79133e821cdb36590a80cabb1e6a1206fd11a19445ecCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
Screenshots of Detection AMP ThreatGrid Win.Malware.Ursnif-7355802-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: api-PQEC
10
<HKCU>\SOFTWARE\MICROSOFT\IAM
Value Name: Server ID
10
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
Value Name: Client
10
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
Value Name: {F50EA47E-D053-EF14-82F9-0493D63D7877}
10
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
Value Name: {6A4DAFE8-C11D-2C5C-9B3E-8520FF528954}
10
Mutexes Occurrences Local\{57025AD2-CABB-A1F8-8C7B-9E6580DFB269}
10
Local\{7FD07DA6-D223-0971-D423-264D4807BAD1}
10
Local\{B1443895-5CF6-0B1E-EE75-506F02798413}
10
{A7AAF118-DA27-71D5-1CCB-AE35102FC239}
10
{<random GUID>}
10
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 208[.]67[.]222[.]222
10
172[.]217[.]10[.]110
10
172[.]86[.]121[.]117
10
Domain Names contacted by malware. Does not indicate maliciousness Occurrences resolver1[.]opendns[.]com
10
222[.]222[.]67[.]208[.]in-addr[.]arpa
10
myip[.]opendns[.]com
10
Files and or directories created Occurrences \{4BC230AC-2EB3-B560-90AF-42B9C45396FD}
10
%APPDATA%\Microsoft\Dmlogpui
10
%APPDATA%\Microsoft\Dmlogpui\datat3hc.exe
10
%TEMP%\<random, matching [A-F0-9]{3,4}>
10
%TEMP%\<random, matching [A-F0-9]{3,4}\[A-F0-9]{2,4}>.bat
10
%TEMP%\<random, matching [A-F0-9]{4}>.bi1
9
\TEMP\4F03FE~1.EXE
1
%TEMP%\CE0E\6707.tmp
1
\TEMP\69E08A~1.EXE
1
%TEMP%\47D0\A3E8.tmp
1
\TEMP\85FD74~1.EXE
1
%TEMP%\903.bi1
1
\TEMP\906352~1.EXE
1
\TEMP\A11B56~1.EXE
1
%TEMP%\3634\1B1A.tmp
1
%TEMP%\3E3E\1F1F.tmp
1
\TEMP\BB271B~1.EXE
1
\TEMP\C1C116~1.EXE
1
%TEMP%\8878\443C.tmp
1
\TEMP\CA13C5~1.EXE
1
%TEMP%\C9AC\64D6.tmp
1
\TEMP\D66D2E~1.EXE
1
\TEMP\E4F5F1~1.EXE
1
File Hashes 4f03fe32e46386a2379e65b631e786cdeeec223017069d2731a723e4d2c50393
69e08aa34638b3b213dc3c7f7a188e4d56685ca8abd4bfa97f575757a1f4bc12
85fd74ee1f19173597c3995376c31c617c0cd615d1d4e862edbe2459200397ed
90635217dd43e1ccfc8c25aef6619b1a929b5e7d1800b9cebd8686d052243611
a11b566c7bd562cb4cdee2c1bc92313a11ebdacf4fdde58c224eb7eac0e6faf1
bb271b6725170345188008dfb90069c9f741b93cf0a504a9c70f177c2dd670cb
c1c1165edb4b0853d6433961aec1b54982fe3273a094d53bb1b2f23e9f6713de
ca13c5fb577c3a218a3be31c59145137e11b4c7188839b7962a3ce3e7d6277ec
d66d2ea9744ca077c3dc76c303a284c1d2b863151931ddcce656fb35a52289e6
e4f5f19e945a41ad8f0ec7e9c35b23ea039a5a2bdaaf8e42a78c8f86b231334eCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
N/A
Screenshots of Detection AMP ThreatGrid Win.Malware.Upatre-7355650-0 Indicators of Compromise IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 83[.]136[.]254[.]57
8
Domain Names contacted by malware. Does not indicate maliciousness Occurrences cardiffpower[.]com
8
Files and or directories created Occurrences %TEMP%\hcbnaf.exe
18
%TEMP%\hgnddkje.exe
17
File Hashes 0001e614c453604df0274956181e30350b7d6b1b91a169efdcbfee9a14a17626
01cd20d9212c000b7d8d97c47029b1b487050ead1b65e1c9c34e475f0f178add
055c1293bfc73671ac423aca35488dc3ec7510523695b8bf50d2f52e625680b7
1abc3b0481dc17e7aa7176b87605503b0baa9e340b4c5e673597fd06725f72f8
1f1db1372645d08bf117d2154ef9f67a2163295900b6311e4cd2268669601c1c
27e9f49d26c1202470242da4fe53199b74f525ee13bee5b34b1d613f2d5f2983
4200aca5bfb24f7b02cbcd39c7d6f4c773ed34eec17ac11ad9d5cee5aaba1940
669b62caaa55cf04de326355b319e16f481092c8098b418f9f2b09051b5e9088
8412bf5346bedec07e58c31bd15ddd98d31e8686c9f870444b2bbd1c8b527cb7
9476469b243db70017ef61c6da483e516516380136a4799015a4ef056e9f1742
9fe8e8a4818e3d63741c4c21ebb9e240d1a26573614162c0b313246b387ef13d
a9d192a121401a7bb63b4fb403f346153090f239ff0761d2f12d12b7bc49741f
bcecb26d7f81aa151a5d2f74f91029a6b1160bc02f431b3c617971ecdeb9e79b
e0b5ae5ad859b17ee532cb274f952ee18254fe941b3d8a129fddda85c65225fb
f480866abfdfd00f7c4a383f1acc9cdd01915d67fed1db367e8dd1cb41171983
f4968453af8a196794abe13cca1747da16b15850c99428778c9a1f6609ca22db
fbd5dcf3f1a93947cb72d9b9d48189810c630d32e94b6f2bbb1811a349e1fb00
fc51c46b56c0a23b400789cd2408a8e8f0204ebb544a410298578c277227cea9Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
Screenshots of Detection AMP ThreatGrid Umbrella Win.Dropper.Kovter-7352197-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: iexplore.exe
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: iexplore.exe
25
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: regsvr32.exe
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: regsvr32.exe
25
<HKLM>\SOFTWARE\WOW6432NODE\3E7DC3D9A3
Value Name: ab87b5d3
25
<HKCU>\SOFTWARE\3E7DC3D9A3
Value Name: ab87b5d3
25
<HKLM>\SOFTWARE\WOW6432NODE\3E7DC3D9A3
Value Name: 626beb1a
25
<HKCU>\SOFTWARE\3E7DC3D9A3
Value Name: 626beb1a
25
<HKLM>\SOFTWARE\WOW6432NODE\3E7DC3D9A3
Value Name: 52e3fdae
25
<HKCU>\SOFTWARE\3E7DC3D9A3
Value Name: 52e3fdae
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
25
<HKCU>\SOFTWARE\3E7DC3D9A3
25
<HKLM>\SOFTWARE\WOW6432NODE\3E7DC3D9A3
25
<HKLM>\SOFTWARE\WOW6432NODE\3E7DC3D9A3
Value Name: 13faecd5
25
<HKCU>\SOFTWARE\3E7DC3D9A3
Value Name: 13faecd5
25
<HKCU>\SOFTWARE\3E7DC3D9A3
Value Name: 214fab25
25
<HKLM>\SOFTWARE\WOW6432NODE\3E7DC3D9A3
Value Name: 214fab25
25
<HKCU>\SOFTWARE\3E7DC3D9A3
Value Name: 89d39e9a
25
<HKLM>\SOFTWARE\WOW6432NODE\3E7DC3D9A3
Value Name: 89d39e9a
25
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 3f88794a
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
Value Name: f50e45da
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 3f88794a
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101
Value Name: CheckSetting
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
Value Name: CheckSetting
25
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100
Value Name: CheckSetting
25
Mutexes Occurrences 4C2A424BDFE77F08
25
Global\377DB1FA5041B00C
25
2CAEEF5D79FF2C96
25
5F02253DDD3215C1
25
0F8579C06C8A73E7
15
Global\148FEA91D04ADF73
15
35A61B8070E50AA3
15
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 82[.]21[.]65[.]83
1
166[.]141[.]185[.]163
1
93[.]229[.]231[.]137
1
142[.]250[.]246[.]73
1
159[.]182[.]203[.]131
1
63[.]121[.]210[.]194
1
42[.]97[.]167[.]153
1
113[.]179[.]182[.]225
1
156[.]34[.]80[.]75
1
218[.]64[.]159[.]231
1
182[.]94[.]255[.]58
1
84[.]226[.]162[.]67
1
212[.]123[.]72[.]164
1
183[.]74[.]168[.]214
1
20[.]118[.]2[.]20
1
168[.]141[.]179[.]181
1
114[.]97[.]61[.]121
1
201[.]32[.]115[.]236
1
108[.]124[.]8[.]164
1
212[.]246[.]227[.]79
1
68[.]6[.]254[.]161
1
159[.]133[.]144[.]196
1
16[.]215[.]96[.]194
1
189[.]183[.]233[.]195
1
60[.]194[.]81[.]71
1
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]cloudflare[.]com
2
cpanel[.]com
1
httpd[.]apache[.]org
1
cp[.]aliyun[.]com
1
netcn[.]console[.]aliyun[.]com
1
bugs[.]launchpad[.]net
1
manpages[.]debian[.]org
1
files[.]ofile[.]com
1
www[.]zerodistance[.]fi
1
File Hashes 015d420249c90969fc15bd3c81839c05242c68e42135bc6e04743f16c3db8247
119e68e1ed3d764e9ccedbffb4e2adc1522b9a9c4672c8a52c70d3b75af919f1
19595e9e80a2da27c682814726e373d7207e6681b9a4b96a5744736976342f46
1fc7d5d27d4817cacae040833970a636a41a6cfe9fa783de92cdad2e93a620ac
21f75f1a46cc68cde8bc7cc10d63bca95a561268ad49d943afc8ca177cc89184
26555d26c4afce1e035031d293aab4acdb12a77530b375421be6e0bb80742057
41ce8bc25ec1a3bf85e346656cdfdcd1eaa4070c3783d133f25ffcebf55bb6d8
423e4d33687cb3e6fe4ebce6d36fa2d0b94006b28ad08de89fa2d2be2db4046a
533b055f7be13fe6c40eb49bebf93901b22ea3ada9babf100675c7ca53cd0c03
605ea58c8282dc5ef581f31b24647d463562d646a5be2004a174773416ec106c
6181608294d3482931e3a65f1e7c63182327076506e1c7c51583b57ef115d8ed
69ba2b3868404234ead2f364cbbfd1a13af9da0fbfa77845a09e06525f3c107f
72e70aa9877033cdf9c6d77f767545cd1365f7034a4da22c823eea4d60eb1bee
76d567e13a7cb9d97682944975accbeb0c4f3f6858ab84f64af849c4d5df25bb
8136ceed3bc05c0ebe9b0ac8bb9c9925eb781f6fa4a994c976f3ff24f692e962
91f71c8b5385d7441e2f8b82ce5be7f17a9c9fddd431c45dafab309d2fd76145
9218ea373d7322c49a3248b94b13366499f23d30b1f17ea63c3c19fe788376a6
97603c7315e26964dd15bdfb9a5932340271a949352364ebcb694282dd282ed1
9e7ce5f193afa02fc3165a34366981a34a1685deaf2b249f4fb089c8a25e77fd
a318a5c36defbd74a7ad1ef3cca3670dadb918d692ce1e97c62b8022bb5a7ee6
c36a861e05aac4fa885836f60b871cc116085e05351d8a1a586db85dc902786f
d0120bc8873d60781fd8a0640ce9d37a2f8daefc90747196ba70f4e7b5af41c1
d1fe8fea741f9758292df1b335ed203c4f9f6ec462690dd7338f043a01ffae8c
d89115020458a087bb71f7f338e8b5cc9182c98d6559cf0573c5a87304fdd65b
dfe7a1d91600e7bde92d16deb4a3bee5da7c01391d55f3e03c57e817d7bff7c6*See JSON for more IOCs
Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
N/A
Screenshots of Detection AMP ThreatGrid Win.Malware.Trickbot-7352185-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: DeleteFlag
23
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Start
23
Mutexes Occurrences Global\316D1C7871E10
23
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 200[.]122[.]209[.]78
8
176[.]119[.]156[.]225
6
31[.]202[.]132[.]22
5
190[.]0[.]20[.]114
3
152[.]89[.]245[.]209
3
103[.]122[.]33[.]58
2
181[.]143[.]17[.]66
2
45[.]160[.]145[.]216
2
37[.]44[.]212[.]179
2
80[.]173[.]224[.]81
1
119[.]92[.]23[.]203
1
201[.]184[.]69[.]50
1
190[.]109[.]178[.]222
1
68[.]186[.]167[.]196
1
45[.]160[.]145[.]11
1
185[.]255[.]79[.]127
1
45[.]160[.]145[.]179
1
117[.]204[.]255[.]139
1
103[.]87[.]48[.]37
1
195[.]123[.]237[.]155
1
190[.]109[.]169[.]49
1
Files and or directories created Occurrences %APPDATA%\browser\settings.ini
23
%APPDATA%\browser
23
%System32%\Tasks\BrowserStorage
23
%APPDATA%\BROWSER\<original file name>.exe
23
File Hashes 0627afe0eb7517208d514c54b83436885eae259fa984bd6dbcfeb788ce5f2b80
0e21da4e3c8dfd077454f417b8b602b281887dbc487cce3e60a508b03ec7a897
2820d3a726768ac98f7357f182fa0f27e63743c025a40025f316a281dbecfe66
4e6f460398ab227ece450409e1343665b73a73f1c330b9ebbb8a03c8c2171f1b
587e038e8e3bf1e2a4005a89dea96f084d2e6a2c89ab0eea9c3a112997e48c1e
66b9b21677bfbb131aaab959f603091db4ce740a92c2376d84df43343b2de68d
69b4a369319e0c9c16fee1fe7db6f5ccc20076e4296a000f92f756ef1cb31533
756bf7440aa067883f18db9c567fa11c45aa9a7ee05e86bd2f759a726500d90d
80096a877332490f8e5d303906335e5420e8a95f90109c08596330ab0d77cf8a
843019efa320b08991d64ce99faaa5a254af828f6f8be64715f6e5f3833769be
877f01088ac912f8e7cfffd81b86ba21d8eeaccb5e3f675fd5299efab7e8fc5f
8fc61570c2e05fd746da7e7e14d9558afe38b0f00e6ccf2c43e0fd46247fb8f2
9706de7a46a3a13ba3275aa583ac70b31071a8fb30e3bd1061ceb0c3ea6532fe
a5eb7f6a1d253fe60bf02e19a8858fd80dc4a7358f660d84fa85b6f6e011b11e
bd26a6bd3d52b26c66f1b3503b0dd901a68318a66caa846d77fde10ad6f9668a
c84b91da836a003057d90123e25cbaec576a20d1f98c621d777de47cdfdd40e3
cad65e1ce6ec9e36e8073c79a0a406997ed825e65af3952e55ea9c44c6e39122
ce5393632e1c0adb91af5ffc8a6b486141cb895a3b762b853ebfdb3518563dbf
d0e9f2ba27da2bee48617c219a2a5e4b2db9d96b5e19ac16098384c3bb36c65f
d54747ba18aec6ee4a9670148fd420dab486992f37df1e577abd9bc4d5dd2eb6
dd5ae9ad15a51845b317b83ba6d0bf2f010b2dfae3c85e7099b95c9bb0ea09a0
f79bac124531d2050d668a510e074930f5c1c9af7997a9513a8f16eb7549a8b7
fc061e1261397c24a7d074a7cac01e74af9f47b6300911f3734104c1557928d8Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
Screenshots of Detection AMP ThreatGrid Win.Virus.Expiro-7350682-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32
Value Name: Type
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32
Value Name: Type
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP
Value Name: Type
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE
Value Name: Type
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER
Value Name: Type
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE
Value Name: Type
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32
Value Name: Start
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AELOOKUPSVC
Value Name: Type
16
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\AELOOKUPSVC
Value Name: Start
16
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101
Value Name: CheckSetting
16
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
Value Name: CheckSetting
16
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100
Value Name: CheckSetting
16
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102
Value Name: CheckSetting
16
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104
Value Name: CheckSetting
16
Mutexes Occurrences kkq-vx_mtx1
16
gazavat-svc
16
kkq-vx_mtx67
16
kkq-vx_mtx68
16
kkq-vx_mtx69
16
kkq-vx_mtx70
16
kkq-vx_mtx71
16
kkq-vx_mtx72
16
kkq-vx_mtx73
16
kkq-vx_mtx74
16
kkq-vx_mtx75
16
kkq-vx_mtx76
16
kkq-vx_mtx77
16
kkq-vx_mtx78
16
kkq-vx_mtx79
16
kkq-vx_mtx80
16
kkq-vx_mtx81
16
kkq-vx_mtx82
16
kkq-vx_mtx83
16
kkq-vx_mtx84
16
kkq-vx_mtx85
16
kkq-vx_mtx86
16
kkq-vx_mtx87
16
kkq-vx_mtx88
16
kkq-vx_mtx89
16
*See JSON for more IOCs
Files and or directories created Occurrences \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\DW20.EXE
16
\MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\dwtrig20.exe
16
\MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\ose.exe
16
\MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\setup.exe
16
%CommonProgramFiles(x86)%\microsoft shared\Source Engine\OSE.EXE
16
%ProgramFiles(x86)%\Microsoft Office\Office14\GROOVE.EXE
16
%ProgramFiles(x86)%\Mozilla Maintenance Service\maintenanceservice.exe
16
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe
16
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe
16
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.log
16
%SystemRoot%\Registration\{02D4B3F1-FD88-11D1-960D-00805FC79235}.{33EC2C09-9668-4DE7-BCC0-EFC69D7355D7}.crmlog
16
%SystemRoot%\SysWOW64\dllhost.exe
16
%SystemRoot%\SysWOW64\msiexec.exe
16
%SystemRoot%\SysWOW64\svchost.exe
16
\MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\DW20.vir
16
\MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\dwtrig20.vir
16
\MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\ose.vir
16
\MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\setup.vir
16
%CommonProgramFiles(x86)%\microsoft shared\Source Engine\ose.vir
16
%ProgramFiles(x86)%\Microsoft Office\Office14\groove.vir
16
%ProgramFiles(x86)%\Mozilla Maintenance Service\maintenanceservice.vir
16
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\mscorsvw.vir
16
%SystemRoot%\SysWOW64\dllhost.vir
16
%SystemRoot%\SysWOW64\msiexec.vir
16
%APPDATA%\Mozilla\Firefox\Profiles\1lcuq8ab.default\extensions\{ec9032c7-c20a-464f-7b0e-13a3a9e97385}\chrome.manifest
16
*See JSON for more IOCs
File Hashes 356d00dc8ff16fb18f68ccf4f622ab551979b6e14fb802a5c7f394038e19b384
40601e6f4ecb0879bf458b2ce1912ca780b723f971a6cf7c0dd900dd97ff024c
598726fe4b882d2510f3d05d60d58627fd9cf7b90d26187c344a5d9e27902588
5fb45cd8e75ac1418c72843ab892622ebcf9b6c744b5373bd79d825ddb202814
6ef92eff4e1fa8f4093880e24a99341fbe6f9365437920f995af24a73c73a71a
701ae8d2647c886f84c538a9846abdc98ebab9adf994143e17b298f7a6158085
7450df6862c201f3954495ee2b9e1f18b699b7a050cfbfe41db2f68c04b46d76
84f35b43d4f36e1135ce90853af4b5ee0bc1b4969740e4abb2551f067027c9ee
86e65f10866176f9b20bfb6b6b793d743576f532e811e638c4a6fa238e17c900
9739ae5c12dce410017a5ca6be2f169e97d23da942eaf85e0f365a33035478a4
9ce9ec31b261d6ecd124f6b5b2b408ae1b17ca78aea5287ea2b93e1ecfb76e8e
a3c8e47460067b1733559dbbc2d7245a569e3e4aa67b36c67c74ca7f64511d26
acc76ce4ad9708b1a0562fcf8cc27c1ba06e9cbac781b438bdf6b57bd775d3dd
c0f4595ecff664a7d0ec7669a084128915c9a01a4ba058ccb4c4ea04c636fe25
e35f51fc7fe79189d163f04b9f083bc2f0127b72645045693d864e6d0e4004af
f5e1a8f1c48cd0cda719e7da167f91c3e0696f4a259a22b0160763b7aeacf602Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
N/A
Screenshots of Detection AMP ThreatGrid Win.Malware.Tofsee-7349716-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Start
32
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
28
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Type
28
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ErrorControl
28
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: DisplayName
28
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: WOW64
28
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ObjectName
28
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Description
28
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ImagePath
20
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
4
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Start
4
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS
Value Name: Start
4
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: Start
4
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\kjsstakc
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\jirrszjb
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\qpyyzgqi
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\fennovfx
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\wveefmwo
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\cbkklscu
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\ihqqryia
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\dcllmtdv
2
<HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES\DAC9024F54D8F6DF94935FB1732638CA6AD77C13
Value Name: Blob
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\vuddelvn
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\lkttubld
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\xwffgnxp
1
Mutexes Occurrences {<random GUID>}
4
Global\VLock
3
Frz_State
1
Sandboxie_SingleInstanceMutex_Control
1
18550D22-4FCA-4AF2-9E8E-F0259D23694F
1
b7969e9f2199
1
<32 random hex characters>
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 103[.]248[.]137[.]133
28
111[.]121[.]193[.]242
28
104[.]47[.]54[.]36
17
104[.]47[.]53[.]36
11
40[.]113[.]200[.]201
7
40[.]112[.]72[.]205
4
40[.]76[.]4[.]15
4
5[.]9[.]49[.]12
4
144[.]76[.]133[.]38
4
45[.]63[.]25[.]55
4
89[.]18[.]27[.]34
4
87[.]98[.]175[.]85
4
104[.]215[.]148[.]63
3
5[.]135[.]183[.]146
3
45[.]32[.]28[.]232
3
141[.]138[.]157[.]53
3
45[.]63[.]99[.]180
3
108[.]61[.]164[.]218
3
45[.]56[.]117[.]118
3
96[.]90[.]175[.]167
3
104[.]238[.]186[.]189
3
84[.]201[.]32[.]108
3
185[.]133[.]72[.]100
3
193[.]183[.]98[.]154
2
23[.]94[.]5[.]133
2
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences microsoft-com[.]mail[.]protection[.]outlook[.]com
28
ponedobla[.]bit
4
myexternalip[.]com
1
ipecho[.]net
1
checkip[.]amazonaws[.]com
1
nekfad[.]xyz
1
Files and or directories created Occurrences %TEMP%\<random, matching '[a-z]{8}'>.exe
28
%SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>
28
%TEMP%\<random, matching '[0-9]{4}'>.bat
28
%System32%\<random, matching '[a-z]{8}\[a-z]{6,8}'>.exe (copy)
27
%TEMP%\<random, matching '[a-z]{4,9}'>.exe
7
%APPDATA%\By\By.exe
4
%APPDATA%\winapp\client_id
3
%APPDATA%\winapp\group_tag
3
%System32%\Tasks\services update
3
%APPDATA%\winapp
3
%APPDATA%\WINAPP\<original file name>.exe
3
%APPDATA%\winapp\qtmld.exe
1
%APPDATA%\HNC\User\Common\90\Fonts\Fontlist\signons.exe
1
\container.dat
1
%LOCALAPPDATA%\589ff121627b2b278b78a4a16bbdac82a879c808
1
%LOCALAPPDATA%\589ff121627b2b278b78a4a16bbdac82a879c808\container.dat
1
%SystemRoot%\Temp\1676.bat
1
%SystemRoot%\Temp\atfjtxxz.exe
1
%TEMP%\updbb837023.bat
1
%APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\compatibility.mik
1
%APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\cookies.wic
1
%APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\extensions.exe
1
%APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\webappsstore.oty
1
%APPDATA%\MozillaMaintenanceServiceu
1
%APPDATA%\MozillaMaintenanceServiceu\MozillaMaintenanceServiceu.exe
1
*See JSON for more IOCs
File Hashes 074af81963d44e82625056fa1772e2ab6e8b5bbfb58919c4ed4fea1e22df0a58
0d84479eb9868d33fc22a93e8f8a8555dc80c38a00197017bc86e91b3af9da9c
0f6a235a6e9a6eb292a6c5ada9043ad1efde537f19598849682f1eeb0d828e75
173100397fab511b430ba1d2f417ed19fcaadfe3d8ca8e97af6a05432fbaf3a6
2b5f5d317466ee9c4b54b6d840c0cf0e76e9633640df3a9c8f041212239839d2
2e3e02ff35a656d7edfcf29878e501492d4529f68b90b9d2bfa56314f5ffac99
37c6a10dc539555beaef7b4f73418f6721a37b2dbd1f0cecd891381b779a2d22
38ae264016466acb3d215c1451898050580e2a5bbc41cfe6dc441ce9e9dc0690
39ae2c5a2c33d0182ac83cc4440fc1ff6d5c78e3f6a861d0cc2bbc67ec16d0a4
3a303bc815ab0032c143f191f949ff833b0cc31b4349de8460bb4efd7dc1d4d8
3d085c1a1719b6520867aa16997a3aaa214efb2bac1e3ba9f4365def6cd3425e
3ecff383a31433ee6ea3b4faf9a83ed88beba6836d73cf5e45c35c4b2da88fb5
49e4a03514e44969dfd0e0e9d8c6ab90aad572461e92de573ed07f2fd289e943
5099df074e08c348f605a2171b0bd2c0fd8d118eee0d2c53f70f148aa0819e3c
519e96344029271df9b3f758a6891f8342492e43f28efa02796880e8cfaedd70
51be864bb2a297d99bf04cea956400e088ff86029c0031aa9c42f0491efcb544
530d0f977e0f3f34e4876e145677280dc662ea1d84ceb23ba34c7406582bfc71
544d256e79b29963fdeb13a39843c9c40f346d1fb977927c9ede0b37d9bea71e
5d3796595808d10fc9953dc33085e88722a75238f478471cc3723e74b1fffc7f
5fa50f66fd754d9207960ddae6764e45bfb084e9134ac5c4e7755cb9a1e92825
62386fac16d57a15f34b0874a7125f20e21442da376eb7ca1eca86f9edd8cf48
63c93baef82f65d8b47634c77eb5c250ec0546e8f86395ecad2b96a0c6e726b8
655726d8f43ae4d74631cbd1dfcf0a9649461360ee402ae574cc48a2b869a913
6d7fd6fd6ef01477b0e3b075f3d0783ce9168abded6d237f4579987d3a02f744
770dba34f27b6d21d3857e54d9fbb22694428aa1d019b5da7e93d8bedcb1b92f*See JSON for more IOCs
Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
Screenshots of Detection AMP ThreatGrid Umbrella Win.Malware.Nymaim-7348211-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\GOCFK
9
<HKCU>\SOFTWARE\MICROSOFT\GOCFK
Value Name: mbijg
9
Mutexes Occurrences Local\{369514D7-C789-5986-2D19-AB81D1DD3BA1}
9
Local\{D0BDC0D1-57A4-C2CF-6C93-0085B58FFA2A}
9
Local\{F04311D2-A565-19AE-AB73-281BA7FE97B5}
9
Local\{306BA354-8414-ABA3-77E9-7A7F347C71F4}
9
Local\{F58B5142-BC49-9662-B172-EA3D10CAA47A}
9
Local\{C170B740-57D9-9B0B-7A4E-7D6ABFCDE15D}
9
Local\{74966FCB-4057-0A33-C72F-DA1761B8A937}
9
Local\{457A7A9B-5537-F010-1620-E1BCC38A93D1}
9
Local\{<random GUID>}
9
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 64[.]71[.]188[.]178
13
66[.]220[.]23[.]114
8
184[.]105[.]76[.]250
5
Domain Names contacted by malware. Does not indicate maliciousness Occurrences qjgtlozoh[.]com
14
ezgouisk[.]pw
9
ryron[.]com
1
onubkqstb[.]com
1
jeajlfdtoua[.]in
1
ysxmebrfyg[.]net
1
oxfab[.]pw
1
bwapyvznpflh[.]pw
1
voszetuy[.]in
1
klspisvji[.]in
1
ofiracujrsdy[.]net
1
istpmxnf[.]net
1
sianowq[.]pw
1
gpkoz[.]pw
1
sdghuwtwxsm[.]com
1
uslrspq[.]pw
1
kwchhgmla[.]in
1
Files and or directories created Occurrences %TEMP%\fro.dfx
19
\Documents and Settings\All Users\pxs\pil.ohu
19
%ProgramData%\ph
9
%ProgramData%\ph\fktiipx.ftf
9
%TEMP%\gocf.ksv
9
%ProgramData%\<random, matching '[a-z0-9]{3,7}'>
9
%APPDATA%\<random, matching '[a-z0-9]{3,7}'>
9
%LOCALAPPDATA%\<random, matching '[a-z0-9]{3,7}'>
9
%TEMP%\bpnb.skg
1
%TEMP%\mlo.aqz
1
\Documents and Settings\All Users\ju\xcio.cxj
1
File Hashes 3ef2abee25c7ba9f153048e3c400f2935e3e40f988e79b55d12843a90b85a2c1
5816c31cfc9208418279e80e661be48705b54eef97612e2a3acb6b43e1520707
6743826da7e312a954d21cffa0e795599c64ac484ab913da0516d9a8c27c7d8f
74eba0187ce6b3abbc20e1ab98c0732fbf79f680b65ecd7c45eafd81370d0e5e
8dcf86bd3796d59fa421e8b2c442355a72c8a58eb489bc268063c8823bc880ba
97950901d1a3cb6713d8e59e21b4312e3ebc98f0e67071590b0b0514a67cdf1e
98e61798ed2d611ddb45b515bb45fbdd8b45ca5820f50297b4a3152e20d6768b
a6bedf7f7e6fa95b3181e466468ec1812227396d18b51e027ffd670fc4699d4d
a97dc1afeec16c38f5d92e1096930bfa61a60a8c4ccd3f378f5eb6f27ac5a58d
ae65aa4775949b46281b12ffccd29da2aa2ba9463b7a26b17d9170153da8ab85
aee701fe3b36b6441a17ae591f6272764dfaf1361d688ca353813e022b90b545
b8d7cf0c79024e1cd6564731df735059705896d635951019b21d3719a69e64e6
bfa4b25db8ca23842ea3c6d977668c6110b0ca23919b395864065f09e8f15638
c3791696930b1226ccc03537ee50cdf275069b39524b808e3857ae9e85d6ca15
c8f6c7ff30e91b7236802bffaa759ada33ad7963bd3401912d3df9c108205a10
d1c761853ebdfd063cbe19d1a6f5ca1823bef0f6c527064846e20f1c8df8c54e
d913691cdc1b1140905af020364afbc3144989b7a7947332efb29ef95440597d
de8ff7107c7566fa9d68c49f0808c2c47df83fabeaa99b70a2f30da9f6d4c1a1
deee1f14fe06f8ceac4f617cba37d027664b9bc171cf0f1a3fca9c78da4df525
e5210cb809f2f6c04d51994491cf29edcaadc338df7294051406e5dd6b0d2d8e
eb5ac18bb9bbce53b7522955ee36eccc8d21c5347c54b3830c5085cb323b6838
f9f839ec0ee45b5bc8b2dc65ed2747c662de954d7b14d8d00cb1fc47878f513a
fe76a31b8ac35d140fb815504c739f952bc9f1625f5d936e837af21e5f1c1b3bCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
Screenshots of Detection AMP ThreatGrid Win.Malware.Cerber-7343756-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
28
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
Value Name: PendingFileRenameOperations
25
Mutexes Occurrences shell.{<random GUID>}
26
shell.{381828AA-8B28-3374-1B67-35680555C5EF}
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 178[.]33[.]158[.]0/27
26
178[.]33[.]159[.]0/27
26
178[.]33[.]160[.]0/25
26
178[.]128[.]255[.]179
17
150[.]109[.]231[.]116
15
54[.]164[.]0[.]55
13
34[.]206[.]50[.]228
12
104[.]24[.]111[.]135
11
104[.]24[.]110[.]135
6
216[.]218[.]206[.]69
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]blockcypher[.]com
25
bitaps[.]com
17
chain[.]so
17
btc[.]blockr[.]io
17
bc-prod-web-lb-430045627[.]us-east-1[.]elb[.]amazonaws[.]com
9
hjhqmbxyinislkkt[.]1j9r76[.]top
5
Files and or directories created Occurrences <dir>\_R_E_A_D___T_H_I_S___<random, matching '[A-F0-9]{4,8}'>_.txt
28
<dir>\_R_E_A_D___T_H_I_S___<random, matching '[A-F0-9]{4,8}'>_.hta
28
\I386\COMPDATA\EPSON3.TXT
26
%TEMP%\8f793a96\4751.tmp
26
%TEMP%\8f793a96\da80.tmp
26
\I386\COMPDATA\BOSERROR.TXT
26
\I386\RUNW32.BAT
26
%TEMP%\tmp1.bmp
26
<dir>\<random, matching [A-Z0-9\-]{10}.[A-F0-9]{4}> (copy)
26
%TEMP%\d19ab989\4710.tmp
25
%TEMP%\d19ab989\a35f.tmp
25
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp
25
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.bmp
25
File Hashes 0571ddf62e8bcf0dfc91f61079145ef5a334ade39ffd45d7ce88b4cbe42a15d3
09606b24a726b8179417a36c9aca18f44ebcf98f2240fbb398b70c49090d050b
162012945f91033f3683b742d660795cc2e184f41d6db3a15703e38024ce7985
1974b3f6d08447d18279bce6cd737aec3438cbda3cc90d8fd625fdc9e06339eb
1f86d067251a326322db9afea633b6ef9419eb456eded355220fe590ea2f11c5
283bd9ce2b81146780f060c00fdb7e11701cb617a55b5b6e15217b8041fb5480
2b75044e81ecbee8f6da594a277e37d7a232e934ef9de81b8185e4c0213564a6
2dbf7bed5adcba2ce1f48736431a2041ec2c6a581a6edc4c0883f6394022316c
34012082527c5206f58fe4dc7ed65aa785864ffc57b69ef36a2684a0bd77df93
37ae3f37a90f62a3247ac2b2afaa2a7b7feca603fd9258a23be3b0c06fad3baf
394e282ad6f08c49e67258afb5be535d98ca35b2bffdfd4cc6f866ff909da21c
41dfd05edf2657153e9f265e5f41877660b0fe9b3d4c46d82a0560234fe7d911
54be4270379a47819af99f6b455af363531d0c035f6f645b0505240cbe2e18df
58a71b81fb151fc64383e7adad9aadab56188c8e5107fe157889b598d80331b9
5cde373946029302a628504ae7fe6c26037ba6c6e7cf575aa33258808dc7b4d3
5e3b677a238a772109ab8282964d0a7dc4a68e422471589eeb58dacf4f3b1917
5f5c89d4cae98e32d764146b5ea87879ed6c355171535e1ca1b65f8a5d2fc296
69747e554bef6e4fec803333c19df48b7317848feb58842849fdb3797d41f66c
6d1ed5c4c21f2f9fa42d1cede8411ae9347ae85c03a76dd212856187c66328b3
797adc29fe0dddbfb03aec9344dd2f93a702bb57920f35bd7decb92873b2ea86
79acc4d7034c595c35d2280281699064e114bc6ca7dcc461c2077a2d350f78c4
821923194cc976d5b0785d114769c85b473e7e7316f0bfab3e60f94404bd9a91
8232399d1c7350132d3347c6aeffcea06c38e6c8fbf3527399a51d7fc3bff1bb
831872753224405c5553a509d3ac4af91032d789cba67977e43e1b0b68abe543
91f928319c927531fb3c2863eefd2fff358a962887d8fd8deeeead74d3602562*See JSON for more IOCs
Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
N/A
Screenshots of Detection AMP ThreatGrid Malware Exploit Prevention Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. CVE-2019-0708 detected - (69038)
An attempt to exploit CVE-2019-0708 has been detected. The vulnerability, dubbed BlueKeep, is a heap memory corruption which can be triggered by sending a specially crafted Remote Desktop Protocol (RDP request). Since this vulnerability can be triggered without authentication and allows remote code execution, it can be used by worms to spread automatically without human interaction.
Madshi injection detected - (2294)
Madshi is a code injection framework that uses process injection to start a new thread if other methods to start a thread within a process fail. This framework is used by a number of security solutions. It is also possible for malware to use this technique.
Process hollowing detected - (321)
Process hollowing is a technique used by some programs to avoid static analysis. In typical usage, a process is started and its obfuscated or encrypted contents are unpacked into memory. The parent then manually sets up the first stages of launching a child process, but before launching it, the memory is cleared and filled in with the memory from the parent instead.
Excessively long PowerShell command detected - (304)
A PowerShell command with a very long command line argument that may indicate an obfuscated script has been detected. PowerShell is an extensible Windows scripting language present on all versions of Windows. Malware authors use PowerShell in an attempt to evade security software or other monitoring that is not tuned to detect PowerShell based threats.
Dealply adware detected - (226)
DealPly is adware, which claims to improve your online shopping experience. It is often bundled into other legitimate installers and is difficult to uninstall. It creates pop-up advertisements and injects advertisements on webpages. Adware has also been known to download and install malware.
Kovter injection detected - (183)
A process was injected into, most likely by an existing Kovter infection. Kovter is a click fraud Trojan that can also act as an information stealer. Kovter is also file-less malware meaning the malicious DLL is stored inside Windows registry and injected directly into memory using PowerShell. It can detect and report the usage of monitoring software such as wireshark and sandboxes to its C2. It spreads through malicious advertising and spam campaigns.
Gamarue malware detected - (156)
Gamarue is a family of malware that can download files and steal information from an infected system. Worm variants of the Gamarue family may spread by infecting USB drives or portable hard disks that have been plugged into a compromised system.
Installcore adware detected - (88)
Install core is an installer which bundles legitimate applications with offers for additional third-party applications that may be unwanted. The unwanted applications are often adware that display advertising in the form of popups or by injecting into browsers and adding or altering advertisements on webpages. Adware is known to sometimes download and install malware.
PowerShell file-less infection detected - (49)
A PowerShell command was stored in an environment variable and run. The environment variable is commonly set by a previously run script and is used as a means of evasion. This behavior is a known tactic of the Kovter and Poweliks malware families.
Reverse tcp payload detected - (38)
An exploit payload intended to connect back to an attacker controlled host using tcp has been detected.