Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Oct. 21 and Oct. 28. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
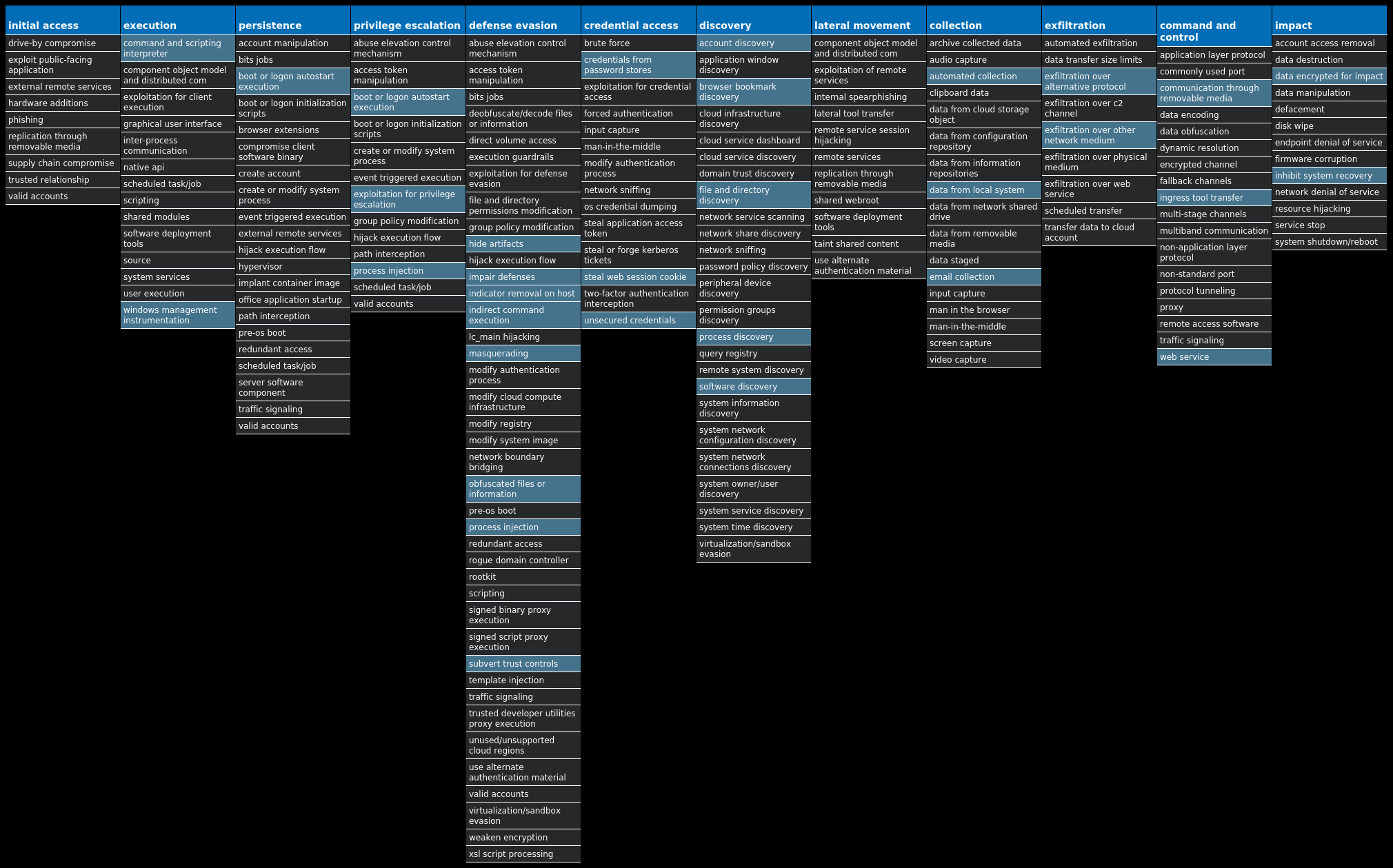
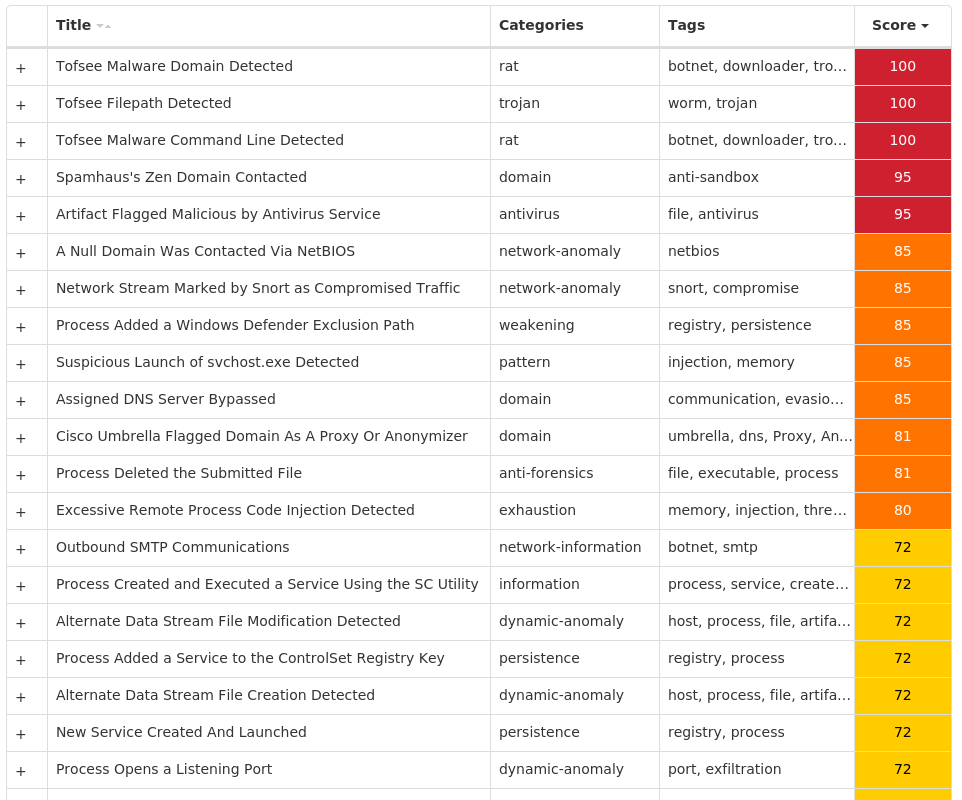
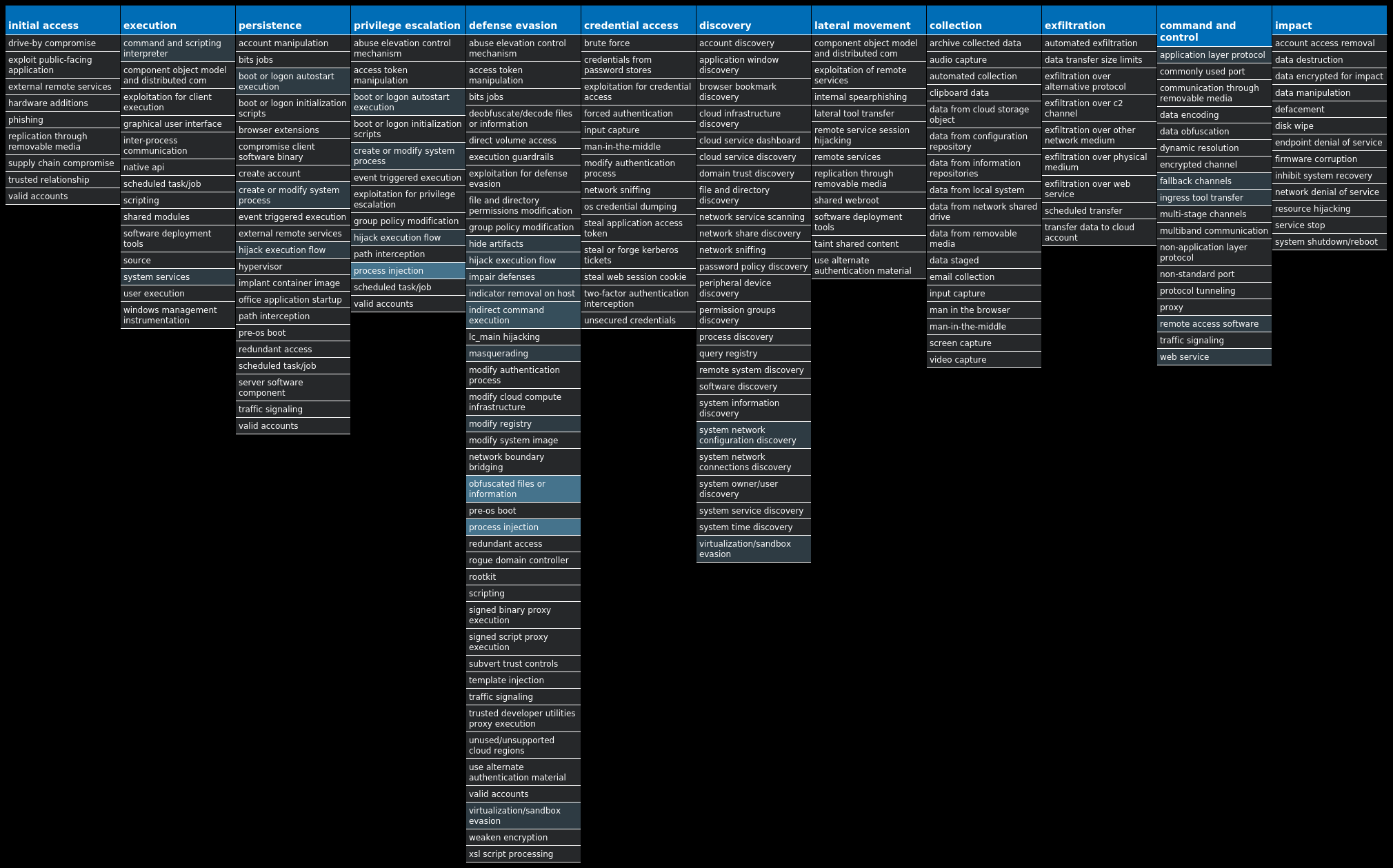
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Ransomware.Expiro-9975896-0 Ransomware Expiro is a known file infector and information-stealer that hinders analysis with anti-debugging and anti-analysis tricks. Win.Malware.Python-9975702-0 Malware Win.Malware.Python is a generic name given to malware written in Python and typically compiled into a Windows executable using tools like PyInstaller. A vast array of supporting libraries, proof-of-concept exploit tools, and example code makes developing Python malware easier than with lower-level languages. Examples of functionality commonly seen include the ability to spread laterally by using EternalBlue PoC scripts and file encryption performed by ransomware. Win.Ransomware.TeslaCrypt-9975567-0 Ransomware TeslaCrypt is a well-known ransomware family that encrypts a user's files with strong encryption and demands Bitcoin in exchange for a file decryption service. A flaw in the encryption algorithm was discovered that allowed files to be decrypted without paying the ransomware and the malware developers released the master key allowing all encrypted files to be recovered easily. Win.Dropper.Tofsee-9975514-0 Dropper Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages to infect additional systems and increase the size of the botnet under the operator's control. Win.Dropper.NetWire-9975493-0 Dropper NetWire is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam, remote desktop and read data from connected USB devices. NetWire is commonly delivered through Microsoft Office documents with macros, sent as attachments on malicious emails. Win.Malware.Zusy-9975509-0 Malware Zusy, also known as TinyBanker or Tinba, is a trojan that uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe." When the user accesses a banking website, it displays a form to trick the user into submitting personal information. Win.Dropper.Nanocore-9975783-0 Dropper Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes. Win.Dropper.Zeus-9975496-0 Dropper Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing.
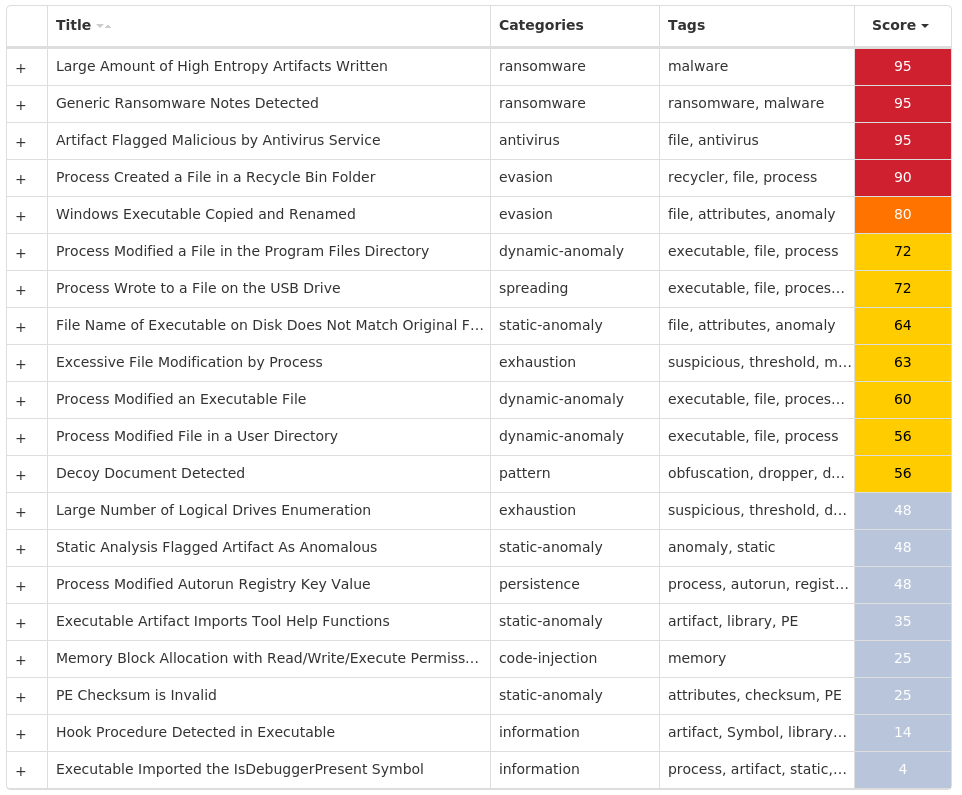
Threat Breakdown Win.Ransomware.Expiro-9975896-0 Indicators of Compromise IOCs collected from dynamic analysis of 11 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Bandera 11
Mutexes Occurrences Local\Kasimir_C11 Local\Kasimir_E11 Local\azov11
Files and or directories created Occurrences %CommonProgramFiles%\Microsoft Shared\OFFICE14\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\OfficeSoftwareProtectionPlatform\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\ar-SA\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\bg-BG\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\cs-CZ\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\da-DK\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\de-DE\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\el-GR\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\en-US\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\es-ES\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\et-EE\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fi-FI\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fr-FR\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fsdefinitions\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fsdefinitions\auxpad\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fsdefinitions\keypad\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fsdefinitions\main\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fsdefinitions\numbers\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fsdefinitions\oskmenu\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fsdefinitions\osknumpad\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fsdefinitions\oskpred\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fsdefinitions\symbols\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\fsdefinitions\web\RESTORE_FILES.txt11 %CommonProgramFiles%\Microsoft Shared\ink\he-IL\RESTORE_FILES.txt11
*See JSON for more IOCs
File Hashes 48d7f7863c81e0e57028ac6e814481f2e6b68265c6ce70d9dd968b994d20d909 5bec449c5576c6058e433e0956ed4b12c7e7efac228cc24ea3699f4438dd47c2 6b256ec96a2b7c3ad17b466a7e83757db2089ed052d4b9ec0e40bc6f361701fc 74ed39c697aa29c039aa99e22bc7a7f24800bc4b49ef2e2ead506b358ae31fd1 77baa451013dd0954954ed0f0dfee226c8fde1efad6c8258fa344a22270be1fe 7d3796de860cbe546ec6995b029105c8b038c874e09f99130ae9fc4a12907dbc 7fc41d16920c4aec8aabd10b931dec9e7a217fda7f18d28948072bd67017fe81 9b92f5c1fc45bad7f799e117ed66021c6fae8de2397f87b9d1d001aecba2b9ed af40a21bc7632196cdd83b382e64712bc1f7ccf78d7e0366a7fe92f01b801f2d d3af50ca06a53360b82bbf7ee08d0bd5a7b85570573b7d7dbb940bd76257f4ae f16d23d3f26348b5b4bd6a10e72bc47b5506beeba9c6982a75351fa3046d8a12
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
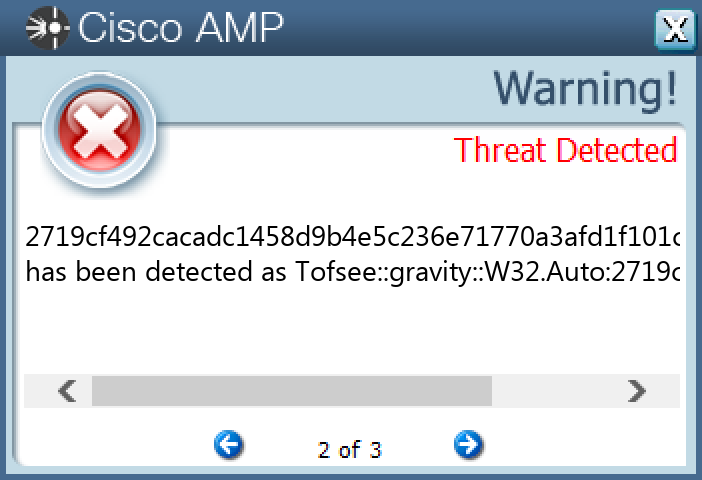
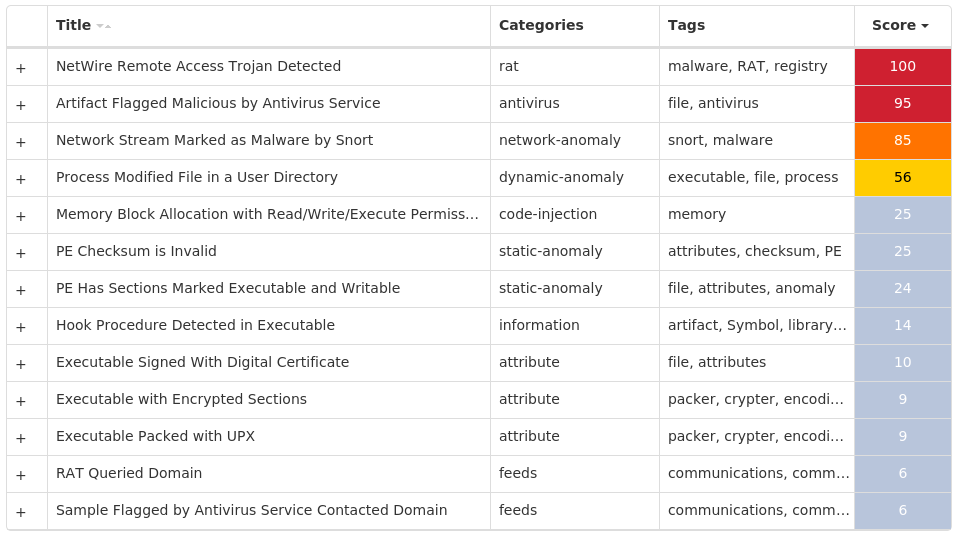
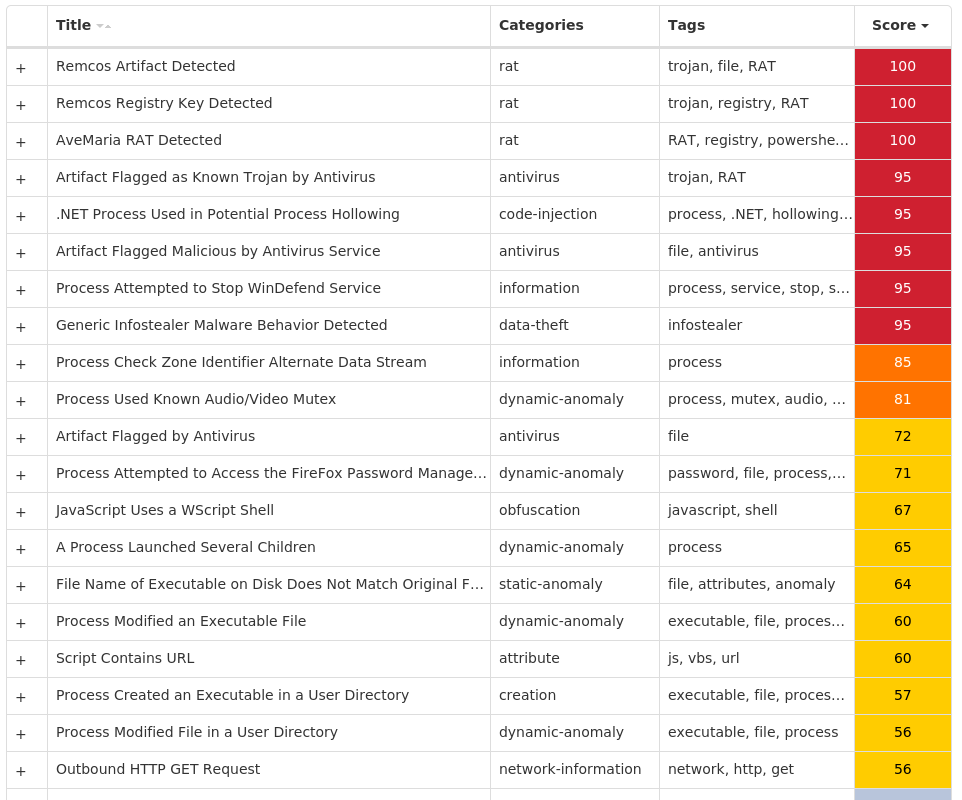
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK
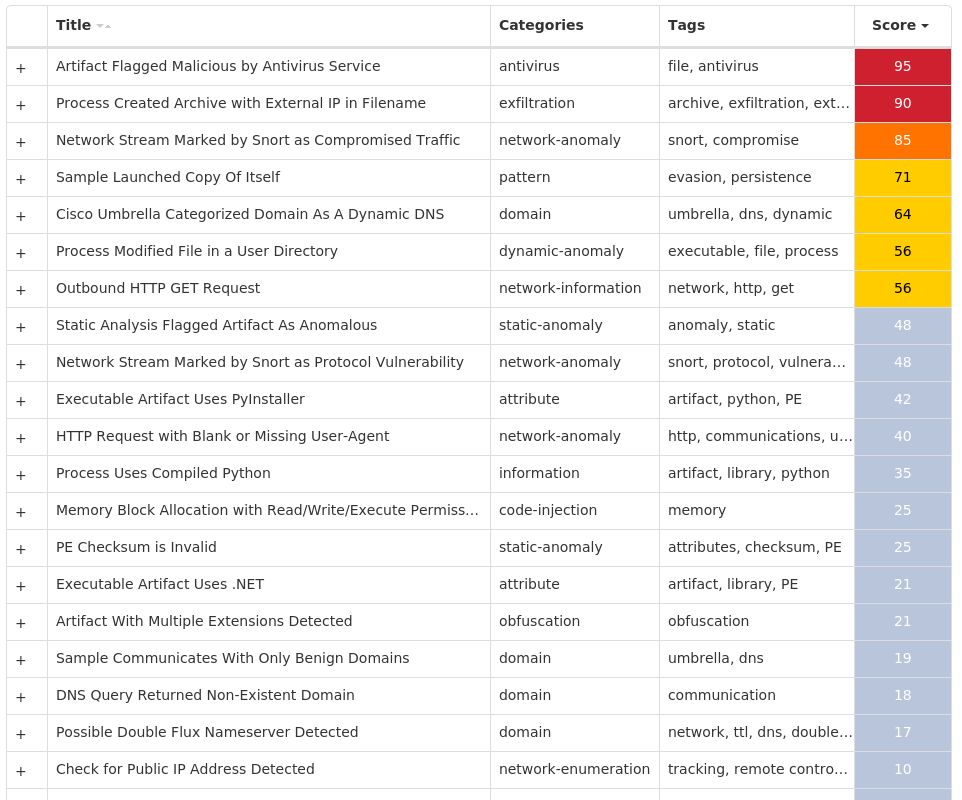
Win.Malware.Python-9975702-0 Indicators of Compromise IOCs collected from dynamic analysis of 12 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 195[.]216[.]243[.]1305 172[.]64[.]201[.]111 193[.]109[.]246[.]541 195[.]216[.]243[.]241 193[.]109[.]246[.]71
Domain Names contacted by malware. Does not indicate maliciousness Occurrences s30[.]ucoz[.]net5 hacker[.]my1[.]ru1 s51[.]ucoz[.]net1 ifconfig[.]co1 foxlocfe[.]beget[.]tech1 s54[.]ucoz[.]net1
Files and or directories created Occurrences %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\MICROSOFT.VC90.CRT.MANIFEST11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\_CTYPES.PYD11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\_HASHLIB.PYD11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\_SOCKET.PYD11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\_SQLITE3.PYD11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\_SSL.PYD11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\BZ2.PYD11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\MSVCM90.DLL11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\MSVCP90.DLL11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\MSVCR90.DLL11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\PYTHON27.DLL11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\SELECT.PYD11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\SQLITE3.DLL11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\UNICODEDATA.PYD11 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\CRYPTO.CIPHER._AES.PYD10 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\STILLER.EXE.MANIFEST8 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\BASE.EXE.MANIFEST4 %TEMP%\_MEI70023 %TEMP%\_MEI181622 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\INCLUDE2 %TEMP%\_MEI<pid, matching '[0-9]{1,5}'>\INCLUDE\PYCONFIG.H2 %TEMP%\_MEI160421 %TEMP%\_MEI119221 %TEMP%\_MEI69621 %TEMP%\_MEI122021
*See JSON for more IOCs
File Hashes 2416bca21805c6f5609a5e586cbf1a9accc6bd998b995c9c6b9860b1e9a9ed03 5c3b5e3af4a3e84ff761540bf53b4f195dd141ea056c513f7c5eed3db7ad87ac 5f342770a198cb54ef588119464110c7bd2bd960e48d8d446e249b2ef97ed914 6b4ca43f4b927cbdb3cf10b9af4e8df6997fc71bbaf4aa88b542bb3dfc6c7746 7dc655800edf00b6c93703114370a3e2fe695070e0f4fff79d1ae490dcfb409f 84346f76580a2174013a4e8c372dbac9b86a65074ec386d8d659059772191a3f a11580d4e516004a3eab714772da817b61ea1a7c181dec6374907354d8698019 bbbb3f64e85674d266a32c305d482fb17270c5d50e28c6929652fc21a53ab8d4 bf740d4635bb91aa21dfa36624301f7f49794b1713c33d3e1537e57e1329a276 ef987b23c5bcc7389b8e7d997ffa16c60af4c9ce744897d4b4ae7bf2512be2df efd87875851ad1680e30c4f8e86ff81b23cd7e3cfe8d44f99193fcc3438810c6 f457d5a7d4360bdab03090822ccc4fea1eaba4f5f2916d606102c2fc4e60e8de
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
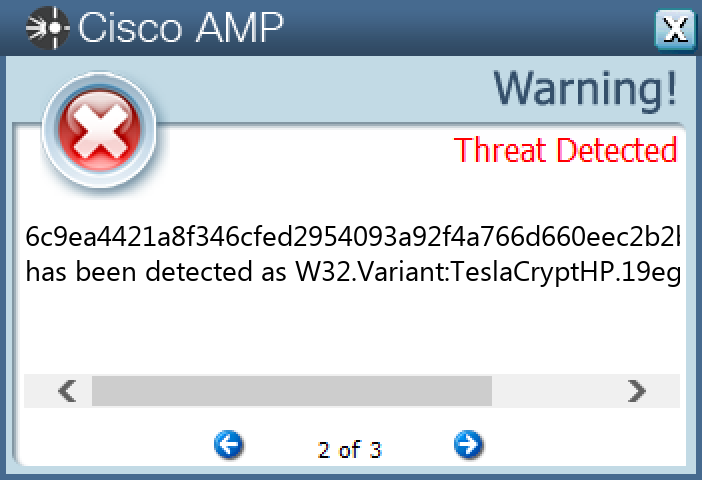
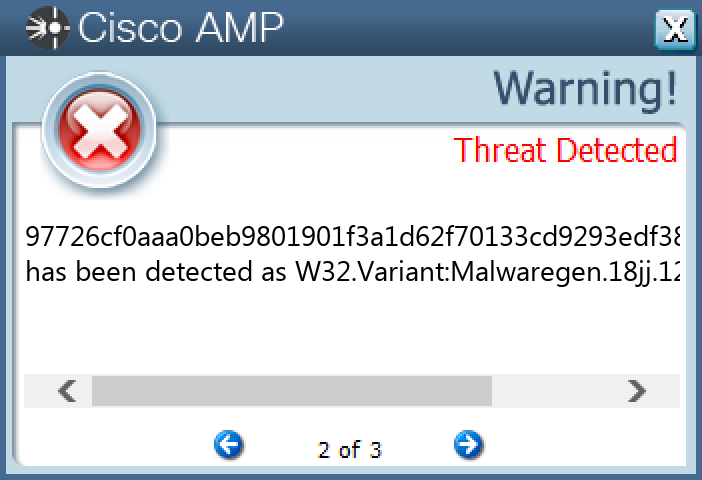
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.TeslaCrypt-9975567-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEMValue Name: EnableLinkedConnections 16 <HKCU>\SOFTWARE\ZZZSYS16 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.CHECK.0Value Name: CheckSetting 16 <HKCU>\SOFTWARE\ZZZSYSValue Name: ID 16 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'>16 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'>Value Name: data 16 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: LanguageList 15 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: iailwniqqrkd 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: jbrsvmmoxcdi 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: beyyyiobuykb 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: brsvgmmwodxs 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: liocswrtiebv 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: gjiicsigtiet 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: rujiosgmikeb 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: ebtjbrvmmoxp 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: acbxpbagteqq 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: liosrmebtbrs 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: liioclswirgt 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: gmngteydhyoa 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: fmgbydhobbux 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: odxscdpinfyi 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: mngtbtyyabtp 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: kckyhnovjlat 1
Mutexes Occurrences 8765-123rvr416
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 85[.]128[.]188[.]13816 162[.]241[.]224[.]20316 34[.]98[.]99[.]3016 154[.]219[.]146[.]24516 23[.]221[.]227[.]1659 23[.]221[.]227[.]1696
Domain Names contacted by malware. Does not indicate maliciousness Occurrences biocarbon[.]com[.]ec16 imagescroll[.]com16 music[.]mbsaeger[.]com16 stacon[.]eu16 surrogacyandadoption[.]com16 worldisonefamily[.]info16 apps[.]identrust[.]com15
Files and or directories created Occurrences %ProgramFiles%\7-Zip\Lang\ka.txt16 %ProgramFiles%\7-Zip\Lang\kaa.txt16 %ProgramFiles%\7-Zip\Lang\kab.txt16 %ProgramFiles%\7-Zip\Lang\kk.txt16 %ProgramFiles%\7-Zip\Lang\ko.txt16 %ProgramFiles%\7-Zip\Lang\ku-ckb.txt16 %ProgramFiles%\7-Zip\Lang\ku.txt16 %ProgramFiles%\7-Zip\Lang\ky.txt16 %ProgramFiles%\7-Zip\Lang\lij.txt16 %ProgramFiles%\7-Zip\Lang\lt.txt16 %ProgramFiles%\7-Zip\Lang\lv.txt16 %ProgramFiles%\7-Zip\Lang\mk.txt16 %ProgramFiles%\7-Zip\Lang\mn.txt16 %ProgramFiles%\7-Zip\Lang\mng.txt16 %ProgramFiles%\7-Zip\Lang\mng2.txt16 %ProgramFiles%\7-Zip\Lang\mr.txt16 %ProgramFiles%\7-Zip\Lang\ms.txt16 %ProgramFiles%\7-Zip\Lang\nb.txt16 %ProgramFiles%\7-Zip\Lang\ne.txt16 %ProgramFiles%\7-Zip\Lang\nl.txt16 %ProgramFiles%\7-Zip\Lang\nn.txt16 %ProgramFiles%\7-Zip\Lang\pa-in.txt16 %ProgramFiles%\7-Zip\Lang\pl.txt16 %ProgramFiles%\7-Zip\Lang\ps.txt16 %ProgramFiles%\7-Zip\Lang\pt-br.txt16
*See JSON for more IOCs
File Hashes 0502cc9e71be0177740f017b2a39920b17b6dee086eaaaeac86d94695f487ab0 07d786c92884ec850f027c69105a9873af40f9b7a791125c7027e93535a8a4a6 0f6c94d68a5a4c7b1ad783d18d0cca77a666b1c1f9ec706ae0fc4e80a22efc14 1356961713ad39e25becf68dfdf5cdbca78244f48fe2f986ce01092faddf3f91 2745e19a70c60b974097846b20a609a9de44f1577cac42f0329beba0c0ae9a10 5cf701f03a55da0835b83c76a3090f819d85e11da0ad375efd242c2c881eb553 6b274e28f0ba3e332b6fba0c98344f53b60ce4c9c8a5beaeed2efad513f95614 6c9ea4421a8f346cfed2954093a92f4a766d660eec2b2b479a6799df0fa7c052 7565650a8a680a7ff84e3756c23548a292d8d1b809e4596b804f9e032844d5fe 8071d13d112c0509d2298c5b4df811ebeed37ca0ff0c4ee609f7e0d62ba60b3c c5b47f42ab07618cd782b2459e06505f0c89c94e6596b53b66ce84779809783e c70e314a85c183b41b319577e1ebad64353b883018cac97de2188520dbcd778e db56aa4b9c6bfeba509b8fa1caa9dbc99cc11361b5415983c9e9b96e3efa9efb e5a88c3f19be2662c768c74ceed7ac7d519d0bfd3c4c7e74a82b1342d387c7f7 e88174cc6ed524e21dc39215e6bd425524fad1884418e8c37050eec7eda3a79c ede4b8fdfba8799bc09ba2bc4b0f5f2ba6a7d52276e59fc1b7ef2a13d948c11f
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics Umbrella MITRE ATT&CK Win.Dropper.Tofsee-9975514-0 Indicators of Compromise IOCs collected from dynamic analysis of 30 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: LanguageList 6 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @explorer.exe,-7001 4 <HKU>\.DEFAULT\CONTROL PANEL\BUSES3 <HKU>\.DEFAULT\CONTROL PANEL\BUSESValue Name: Config2 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\dhcpqec.dll,-100 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\dhcpqec.dll,-101 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\dhcpqec.dll,-103 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\dhcpqec.dll,-102 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\napipsec.dll,-1 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\napipsec.dll,-2 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\napipsec.dll,-4 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\napipsec.dll,-3 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\tsgqec.dll,-100 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\tsgqec.dll,-101 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\tsgqec.dll,-102 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\tsgqec.dll,-103 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\eapqec.dll,-100 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\eapqec.dll,-101 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\eapqec.dll,-102 3 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: @%SystemRoot%\system32\eapqec.dll,-103 3 <HKU>\.DEFAULT\CONTROL PANEL\BUSESValue Name: Config1 3 <HKU>\.DEFAULT\CONTROL PANEL\BUSESValue Name: Config0 3 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJPLOJAVValue Name: Start 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJPLOJAVValue Name: ErrorControl 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJPLOJAVValue Name: DisplayName 1
Mutexes Occurrences Global\<random guid>14
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 52[.]223[.]241[.]73 142[.]250[.]176[.]1963 20[.]84[.]181[.]623 80[.]66[.]75[.]43 176[.]113[.]115[.]1533 176[.]113[.]115[.]154/313 176[.]113[.]115[.]156/313 157[.]240[.]249[.]1743 176[.]113[.]115[.]1583 157[.]240[.]249[.]633 209[.]140[.]136[.]233 77[.]232[.]42[.]2123 66[.]254[.]114[.]412 81[.]19[.]77[.]1682 142[.]251[.]35[.]1632 142[.]251[.]41[.]32 104[.]18[.]139[.]442 104[.]18[.]138[.]442 104[.]18[.]41[.]1822 146[.]158[.]48[.]162 217[.]74[.]64[.]2361 212[.]227[.]17[.]1781 212[.]227[.]17[.]1861 212[.]227[.]17[.]1701 67[.]195[.]204[.]1511
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 249[.]5[.]55[.]69[.]bl[.]spamcop[.]net3 249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org3 249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net3 249[.]5[.]55[.]69[.]in-addr[.]arpa3 249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org3 249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org3 i[.]instagram[.]com3 microsoft-com[.]mail[.]protection[.]outlook[.]com3 microsoft[.]com3 www[.]google[.]com3 www[.]instagram[.]com3 video-weaver[.]lax03[.]hls[.]ttvnw[.]net3 ebay[.]ca3 svartalfheim[.]top3 www[.]google[.]es2 imap[.]rambler[.]ru2 www[.]avito[.]ru2 www[.]pornhub[.]com2 m[.]avito[.]ru2 www[.]ladbrokes[.]com2 sports[.]ladbrokes[.]com2 ebay[.]co[.]uk2 www[.]google[.]co[.]uk1 check2[.]zennolab[.]com1 www[.]google[.]com[.]br1
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile3 %SystemRoot%\SysWOW64\config\systemprofile:.repos3 %SystemRoot%\SysWOW64\ijplojav1 %SystemRoot%\SysWOW64\wxdzcxoj1 %SystemRoot%\SysWOW64\yzfbezql1 %TEMP%\sylgzgto.exe1 %TEMP%\yewlqja.exe1 %TEMP%\yohfclsr.exe1
File Hashes 07acbe7ace04425952f97b833b66e13042821008c3c6ecafcd99db550f4e51ff 0f6a579a7bd335f53885dd1a99633672048fa1174d49bbfc82debc47ee5a01b4 1022d83eb4f651a60a5543480d1cf927f3b94a8f65fe2c585ff5d3fc01a3e2ab 1e988dec3815d6b897163152c32fddb9278da0c7332fc854960e3ed72b762e5c 2719cf492cacadc1458d9b4e5c236e71770a3afd1f101c2e668f16883d3384ed 2b544da4344b11910da5d39df878c584340768b1620b8281dc2197f1f35192a6 30163e6c941441971ee56080b9cd75d6de161928d6a829f2929c7f93201f5aa3 32a7a824ab47b46b9127b1ad2528761e4550cbdbcd288f73c115fb14b3b63736 34b715eae6eccad529c3b023a4eae89d8a3e4bc8008d9d4121f015062fcb1a28 3797edf753b5105c88e3c9b65d1a74e8b66512ebe1bdf28bfeca43c4c772ae9e 383d478c916b12593aa6cb1fbad1efe4626de0deaf9bc9393157110e439d7dda 3c259d3a8be8689d664eb2c1f19b23924a15a547bde106756e1d163cdfa5ddb9 47ac3d18dc7010640808ab90a5a83881593a6ab8a5bc178ff72f983e26c3476f 4c49350beadf0bcd622edba56ac59b9dc60b8399ef03171d64419a805d38c771 6ac2f6ee9985ce4d851363e44d1addd6e7ee21567c9f90383e31620289efe8f1 704e56f31923a2aa98588a1825a9b3f076a0d8e0e16ba1b1e54dd692200d21e1 7056525891cd72c3a0284a3703b95954b6e696f099405072119af7c94dd49ed1 7e33162c7a2545cde7956cb206942b5efb0679547dc11df2bb522df90e305ae7 86be3e6fbe1e6a3124824662219b14aebeb3773fed757413ab07f6fffeeb405f 8bb2b3b5725fe1eb24d7b735d7d1a7f190de9a3ec9829fbe3eba3c79bdbc97e3 a134848dd8d69c11037df0a847dd97315052c66ba2047bf4507c001d37c081c5 a9b68bacc11075d6122397501dffb44cea0b1a380089b382ae692f0ccc934346 b255efb1930336e883bfd414b0e690798c3cd88c3211fd052f304876ad3f4975 b65a3f4551edbe2fbdc5fdb107e9dba0d48054b6b2f1de041bd6cb6e59d0a75a d8527861208a446ffd3984def2f8c7436ba135c4f889f6481e74f1e470ab5b10
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA
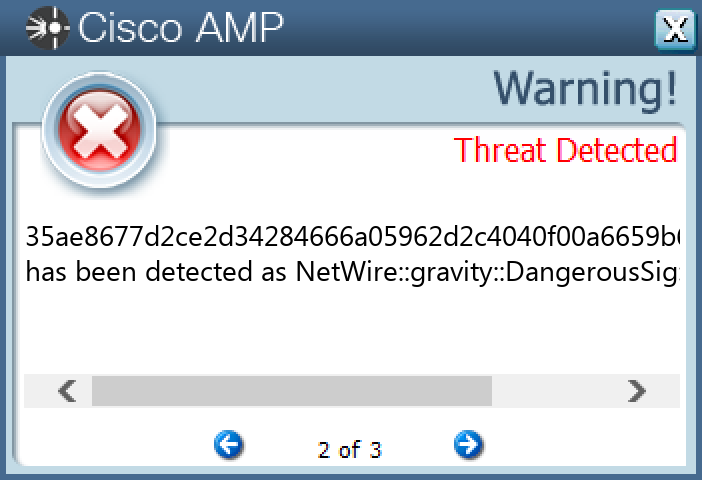
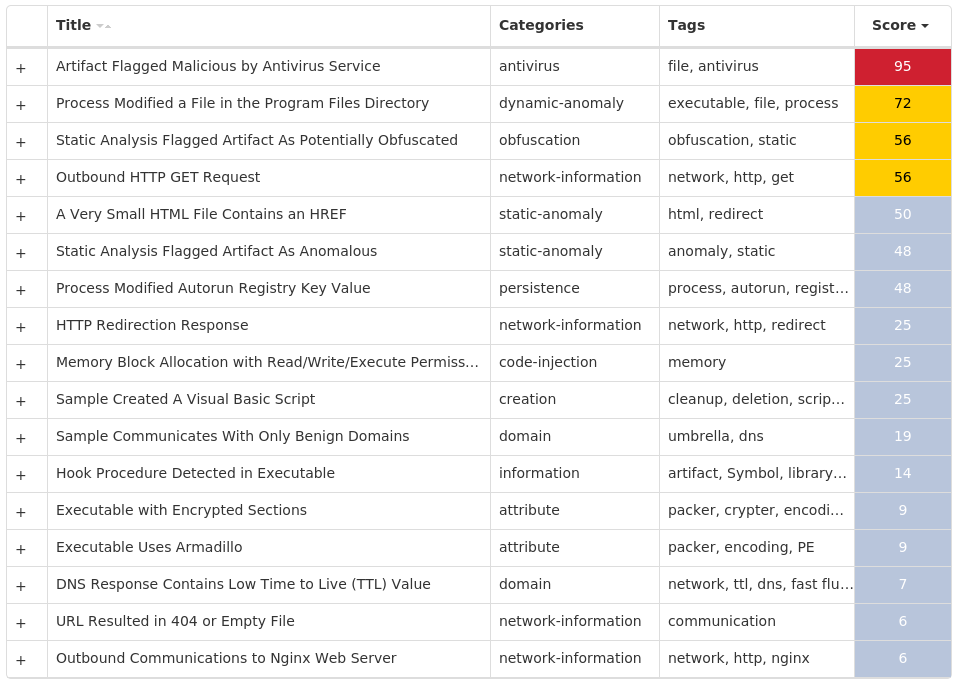
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.NetWire-9975493-0 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKCU>\SOFTWARE\NETWIRE13 <HKCU>\SOFTWARE\NETWIREValue Name: HostId 13 <HKCU>\SOFTWARE\NETWIREValue Name: Install Date 13 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: ͯ>ûšor·0Z¿B< 1
Mutexes Occurrences -13 uEsnBFvU1 KqXbpBPb1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 198[.]44[.]237[.]13113 213[.]152[.]162[.]1811 128[.]127[.]104[.]801
Domain Names contacted by malware. Does not indicate maliciousness Occurrences s2awscloudupdates[.]com13 rad[.]airdns[.]org2 mary[.]airdns[.]org1 maria[.]airdns[.]org1
Files and or directories created Occurrences %APPDATA%\Sqlite313 %APPDATA%\Sqlite3\sqlite3.dll13 %APPDATA%\Install2 %APPDATA%\Install\Host.exe2 %APPDATA%\Install\en-US\Host.exe.mui2 %APPDATA%\Install\en\Host.exe.mui2 \TEMP\en-US\35ae8677d2ce2d34284666a05962d2c4040f00a6659b69f73ce66b2c3aef1abe.exe.mui1 \TEMP\en-US\f900cfa0611b2d2c99f975b8c95004b1d242f38b98f21bca481b3657798648ce.exe.mui1 \TEMP\en-US\a1f353d7b9b7cb667b7b6f9352c773b8a19c6f40f78be9e4b6ab4fc50c4497ec.exe.mui1 \TEMP\en-US\a88e598775669dd18d412a5d09146a34997a92a775f35d3a6fe07b7480ad94ba.exe.mui1 \TEMP\en-US\708a90c4f7fb24fd4218e156ea9063c4212a90ffa5b1237626c0912197741f01.exe.mui1 \TEMP\en-US\7557c69e1f2533fbc6d8bf0c7f8a87846be47aa37729d0e4c217b457800383e2.exe.mui1 \TEMP\en-US\d300e87856166119b69443e0126490dcdc10e7f45267df106f5131a21507fbb3.exe.mui1 \TEMP\en-US\762c6142714e0fc189c61a31b7740a7bd4be1926a3c553a5dc3a807a70bd8d0a.exe.mui1 \TEMP\en-US\7976c28a6a4bd4a38abef0115de6bea17e125924657e50c0bf52b20b99567709.exe.mui1 \TEMP\en-US\087d7a59cd5a14848767dd04cfa15e7bcca0318c36c5681d4ee7f57082571611.exe.mui1 \TEMP\en-US\4fa03ce7749c6a3c77b9f7a310bd74c23777b66d21b3847b916d6388060b7797.exe.mui1 \TEMP\en-US\2e2472ca9ff77b5bca5383f823f2c6c883eee37877b12982f8638b11d7fbaad8.exe.mui1 \TEMP\en\a1f353d7b9b7cb667b7b6f9352c773b8a19c6f40f78be9e4b6ab4fc50c4497ec.exe.mui1 \TEMP\en\35ae8677d2ce2d34284666a05962d2c4040f00a6659b69f73ce66b2c3aef1abe.exe.mui1 \TEMP\en\d300e87856166119b69443e0126490dcdc10e7f45267df106f5131a21507fbb3.exe.mui1 \TEMP\en\f900cfa0611b2d2c99f975b8c95004b1d242f38b98f21bca481b3657798648ce.exe.mui1 \TEMP\en\708a90c4f7fb24fd4218e156ea9063c4212a90ffa5b1237626c0912197741f01.exe.mui1 \TEMP\en\a88e598775669dd18d412a5d09146a34997a92a775f35d3a6fe07b7480ad94ba.exe.mui1 \TEMP\en\7976c28a6a4bd4a38abef0115de6bea17e125924657e50c0bf52b20b99567709.exe.mui1
*See JSON for more IOCs
File Hashes 087d7a59cd5a14848767dd04cfa15e7bcca0318c36c5681d4ee7f57082571611 2e2472ca9ff77b5bca5383f823f2c6c883eee37877b12982f8638b11d7fbaad8 35ae8677d2ce2d34284666a05962d2c4040f00a6659b69f73ce66b2c3aef1abe 4fa03ce7749c6a3c77b9f7a310bd74c23777b66d21b3847b916d6388060b7797 68ff4d529c94e56eee0898ebd031e6b652e62e8d1096728fff618351506cfb58 708a90c4f7fb24fd4218e156ea9063c4212a90ffa5b1237626c0912197741f01 7557c69e1f2533fbc6d8bf0c7f8a87846be47aa37729d0e4c217b457800383e2 762c6142714e0fc189c61a31b7740a7bd4be1926a3c553a5dc3a807a70bd8d0a 7976c28a6a4bd4a38abef0115de6bea17e125924657e50c0bf52b20b99567709 a1f353d7b9b7cb667b7b6f9352c773b8a19c6f40f78be9e4b6ab4fc50c4497ec a88e598775669dd18d412a5d09146a34997a92a775f35d3a6fe07b7480ad94ba ab568b69e55ad53d2cec6f1f5e2ce523e30950d81f456bde5c88bb982cd4107c b90b643d3662a8ac28ec08fd0ec30bfdf7ae826a66d0510fdc7d667014fbdcbe d300e87856166119b69443e0126490dcdc10e7f45267df106f5131a21507fbb3 f900cfa0611b2d2c99f975b8c95004b1d242f38b98f21bca481b3657798648ce
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Malware.Zusy-9975509-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: _dlg_ 26 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: LanguageList 24
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 103[.]224[.]212[.]22024 104[.]193[.]88[.]12622 104[.]193[.]88[.]12520 76[.]223[.]26[.]9612 13[.]248[.]148[.]25412 183[.]232[.]231[.]2252 112[.]34[.]111[.]74/312 69[.]16[.]231[.]601 199[.]59[.]243[.]2221 50[.]28[.]32[.]81
Domain Names contacted by malware. Does not indicate maliciousness Occurrences hi[.]baidu[.]com26 infoflow[.]baidu[.]com26 www[.]bb1d[.]com26 ww38[.]bb1d[.]com23 ww25[.]bb1d[.]com1 ww12[.]bb1d[.]com1
Files and or directories created Occurrences %ProgramFiles%\360Æô¶¯ÐÞ¸´.vbs26
File Hashes 15370edc0024e9eeeaa6e74cddfc112bfab76badfdd9adf60ae137b02ed84de1 235b63ee4006b3904f475d28f547dd30b15b507d006925a1e551b75d853be354 339e1872995e0ff08d9b180fb3d863f58a4a67fceb22221807b128b895549440 3ada6b64cb4e12c29c4a6f4a412a2974eac7ca874327f5c598f8e08e89447205 3df5b97c260c8740b38c808dd246aa33ef9b77af818cb8906d2f68ceed03221c 43dd6acfafd397197f9c6a61192f724d77aa0ccc8ccb052cd71669c9df453b56 5cec24c80e91b79a21b5069e40fedabc79d91b287b8e7ba87364dce1086348e0 64707d0cf54c44931ca35de74e124a6252a79d1f0f317f6cfdadf37f27d596fe 6a2108891f3d5de40f258865d2c6d1f243d1918a8583c0fd27138c2d4530ae61 734ba8c8e7d66d695699c0806662cb0fae54f5b2ec946f45b859e01a7c6c9230 77e0364ca9b9313780728d71db595e3f75382d19d80eb0a7bcd55f90e1662aca 78117bf7af2ed25213bf8c9e3111159d1392b4103126ce253ceb6b88c72e3c5a 801383f10d787b78bc9e6be7f3e9845d6ecc9b267be80a4680a14875b98c7d95 94d65c22a414d874e48cdbcfe8fb41d07f75f60a2220b59cab4c4a23f52d6ef0 97726cf0aaa0beb9801901f3a1d62f70133cd9293edf386a64eb4f22d691655d 9c6c499a07185be4a6ab30fb04ab4c06a6c5b43c0711689454fa1a69671f019a ac83f44c97a88792a989e6fb9a32adcddecb72d089e15c6898515d0f103fba8c af495c1178c622cc0f0a626705ee198e4d9a94c8f6ba0bd544d57fa324d5a43f bd408c9a38eb00aa5c43eb477de7c2471b0c6033f62505111e6eb3b382e98cf9 c1d64ae0f828d858701d8b99120dc685ee7d4931b4ed71689ac5e1df1706c778 c98e93059f69d27ed680bb79f938facf08ed708f18200b685aece691cf71111d cc32daed420122c8ac93b3ed806a4eb992d53224634c7cfa33eabc1a98eacac5 d15d3039ad318f8e4cc67dd666be03cc9e7f1ec79b650720b11fad175db1ce85 d640feddf6941ef4e0dc1b204f71a801d3328bf6d3f95015c11b3d20a6421ce5 da7791f1763927d332853b85f601aeeca719b8bfee2746a8bde12d4408e572c7
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
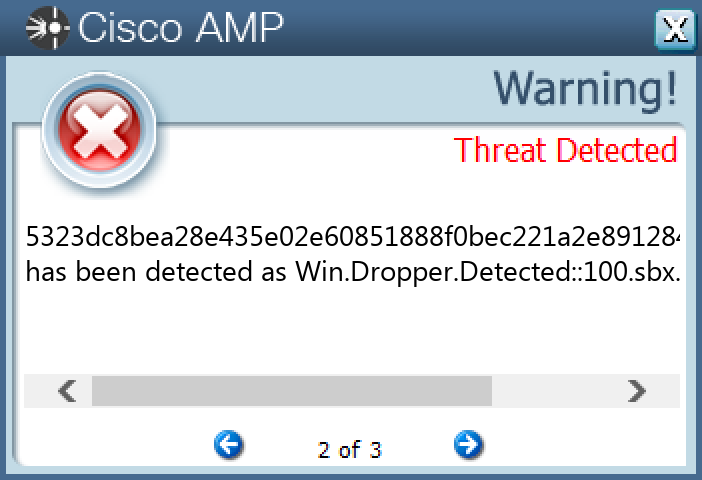
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Nanocore-9975783-0 Indicators of Compromise IOCs collected from dynamic analysis of 11 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: LanguageList 11 <HKU>\S-1-5-21-2580483871-590521980-3826313501-500Value Name: vjw0rm 8 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: WindowsUpdate 8 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEMValue Name: EnableLUA 6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\ENUM5 <HKCU>\SOFTWARE\RMC-563ZPZ5 <HKCU>\SOFTWARE\RMC-563ZPZValue Name: exepath 5 <HKCU>\SOFTWARE\RMC-563ZPZValue Name: licence 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\ENUMValue Name: Implementing 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEMValue Name: DisableTaskMgr 4 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM4 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\QCEME1IYEJ2 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\INTELLIFORMS\STORAGE21 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX1 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX\20.0.1 (EN-US)\MAIN1 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA THUNDERBIRD1 <HKCU>\SOFTWARE\RMC-85GW051 <HKCU>\SOFTWARE\RMC-85GW05Value Name: exepath 1 <HKCU>\SOFTWARE\RMC-85GW05Value Name: licence 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 10_68 1 <HKCU>\SOFTWARE\RMC-Z5IZJT1 <HKCU>\SOFTWARE\RMC-Z5IZJTValue Name: exepath 1 <HKCU>\SOFTWARE\RMC-Z5IZJTValue Name: licence 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 5_33 1
Mutexes Occurrences Rmc-563ZPZ5 Rmc-85GW051 41RP0D-U3D9vE55_1 3-PBOQTVC0TVJ3091 Rmc-Z5IZJT1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 129[.]204[.]138[.]2037 198[.]23[.]207[.]347 178[.]237[.]33[.]502 23[.]221[.]227[.]1692 203[.]161[.]184[.]322 91[.]195[.]240[.]941 162[.]241[.]217[.]1441 172[.]67[.]75[.]1721 172[.]105[.]103[.]2071 45[.]33[.]6[.]2231 149[.]56[.]226[.]651 207[.]60[.]198[.]1531 185[.]157[.]162[.]1151
Domain Names contacted by malware. Does not indicate maliciousness Occurrences apps[.]identrust[.]com2 geoplugin[.]net2 humasjatim[.]id2 api[.]ip[.]sb1 www[.]sqlite[.]org1 www[.]thicmewtwopics[.]com1 www[.]klodifiks[.]space1 www[.]halloweenoncentral2[.]com1 www[.]threadandcotton[.]com1 www[.]msk-kadril[.]store1 www[.]xinhucj[.]com1
Files and or directories created Occurrences %HOMEPATH%\temp11 %APPDATA%\Screenshots7 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\rfil.js7 %ProgramData%\remcos6 %ProgramData%\remcos\logs.dat6 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\start.lnk5 %TEMP%\68.144.191remcos_nostartdisabler.exe5 %TEMP%\rfil.js5 %APPDATA%\A1EB383543D3F00657D74 %APPDATA%\Microsoft\Windows\TEMPLA~1\ConsoleApp1.exe4 %PUBLIC%\vbsqlite3.dll4 %ProgramFiles%\Microsoft DN13 %LOCALAPPDATA%\Microsoft Vision3 %TEMP%\RegSvcs.exe3 %TEMP%\9_85\vftaj.ico1 %TEMP%\9_85\vmkgt.jpg1 %TEMP%\9_85\wkewvchi.vbe1 %TEMP%\9_85\wmqkgxt.docx1 %TEMP%\9_85\woidfl.docx1 %TEMP%\9_85\wokeqtct.pdf1 %TEMP%\9_85\xaxgwxkwnm.exe1 %TEMP%\9_85\xxjodntv.cpl1 %APPDATA%\Screenshots\time_20221024_104709.jpg1 %TEMP%\9_14\ini1 %HOMEPATH%\temp\tdthhc.ico1
*See JSON for more IOCs
File Hashes 05ff0119169151e0368468e6b0eb257b8f33a277b6eb54f67b6643be219df9f7 19afe3682757ba8172ecbd775d84fdec0bbfe1639b72474513ab22883911be52 2e37d7372a97df9e3955837eeae856489541aab815dffabc00bbc72af6483e9b 5323dc8bea28e435e02e60851888f0bec221a2e89128443f985a3adc1ff12353 5738abc5a8ab5ed53bafd105b4cd697e12fd89582fc0c94fb94785b7bfb7e03b 5cc4d6c30090fac70487754d80d491a446e56ae9e22162740f91157615ad00a9 7cf636aadbe071b92c7a6a4fb048bdd269ab70f51bc4cbef176ecdeba51a3fde 95b231f1f1825875bf20f26c86fcf119a0ed4b976fd05b8bbab7892288eaa1dd d5a3d49b177ae147218372995fa6f7c826a56a53ac569874bbb2073ef4b33ab2 ff9ccfcafcb9d31ff1b7ecd1fa83818bc9d6d118be8234e5ee9d09bc4a831cfb ffa521d2ccb7617f414bc4ab5b65f1b9b7122b9c1404783855aebf7096879c68
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA
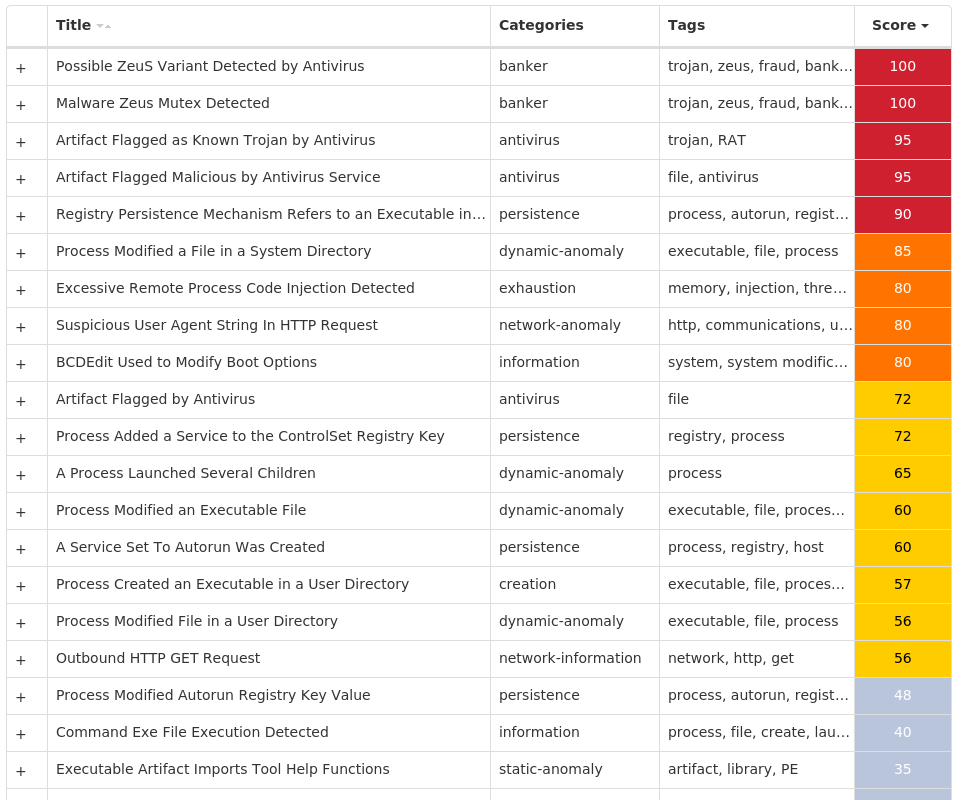
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Zeus-9975496-0 Indicators of Compromise IOCs collected from dynamic analysis of 14 samples Registry Keys Occurrences <HKCU>\Software\Microsoft\<random, matching '[A-Z][a-z]{3,11}'>14 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: Type 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: Start 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: ErrorControl 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: ImagePath 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: DisplayName 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: WOW64 11 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\448AC3FValue Name: Type 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\448AC3FValue Name: Start 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\448AC3FValue Name: ErrorControl 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\448AC3FValue Name: ImagePath 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\448AC3FValue Name: DisplayName 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\448AC3FValue Name: WOW64 1 <HKCU>\SOFTWARE\MICROSOFT\WAOXNUKIEQValue Name: 2074c57h 1 <HKCU>\SOFTWARE\MICROSOFT\FEHIOHXEYValue Name: 1733ih1b 1 <HKCU>\SOFTWARE\MICROSOFT\IHNUUNHOTEValue Name: 152j8jh0 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Adybma 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Ohtoyh 1 <HKCU>\SOFTWARE\MICROSOFT\XABOXEEVIZDValue Name: h81dj8e 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Oqin 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Ihfu 1 <HKCU>\SOFTWARE\MICROSOFT\PIUMACDOAWValue Name: 55429he 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Xelaj 1 <HKCU>\SOFTWARE\MICROSOFT\WAOXNUKIEQValue Name: 1ga25gg3 1
Mutexes Occurrences Global\{C30C6CF2-932B-408E-55BA-04D54CAC27C8}14 Global\{566D79B0-8669-D5EF-55BA-04D54CAC27C8}14 Global\{73DE6ED9-9100-F05C-55BA-04D54CAC27C8}14 Global\{A9348FD8-7001-2AB6-55BA-04D54CAC27C8}14 Global\{A9348FDF-7006-2AB6-55BA-04D54CAC27C8}14 Global\{C8D239CA-C613-4B50-55BA-04D54CAC27C8}14 Global\{C8D239CB-C612-4B50-55BA-04D54CAC27C8}14 Local\{73DE6ED9-9100-F05C-55BA-04D54CAC27C8}14 Local\{A9348FD8-7001-2AB6-55BA-04D54CAC27C8}14 Local\{A9348FDF-7006-2AB6-55BA-04D54CAC27C8}14 Local\{C8D239CA-C613-4B50-55BA-04D54CAC27C8}14 Local\{C8D239CB-C612-4B50-55BA-04D54CAC27C8}14 Global\{A5D858EA-A733-265A-55BA-04D54CAC27C8}14 Local\{E9745CFB-A322-6AF6-55BA-04D54CAC27C8}14 GLOBAL\{<random GUID>}14
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 89[.]37[.]121[.]8814
Domain Names contacted by malware. Does not indicate maliciousness Occurrences photovolt[.]ro14
Files and or directories created Occurrences %TEMP%\lsias.exe14 %TEMP%\lcm.exe14 %TEMP%\<random, matching '[A-Z]{3}[A-F0-9]{3,4}'>.bat14 %HOMEPATH%\AppData\LocalLow\<random, matching '[a-z]{4,6}.[a-z]{3}'>14 %TEMP%\Puohc1 %TEMP%\Puohc\kido.exe1 %System32%\drivers\152a2cd.sys1 %TEMP%\Iclyso1 %TEMP%\Iclyso\axodw.exe1 %System32%\drivers\15293c0.sys1 %TEMP%\Xydira1 %TEMP%\Evpa1 %TEMP%\Xydira\adybma.exe1 %TEMP%\Evpa\ihfu.exe1 %TEMP%\Jylyih1 %TEMP%\Jylyih\ohtoyh.exe1 %TEMP%\Usobyd1 %TEMP%\Usobyd\ulhi.exe1 %TEMP%\Veilp1 %TEMP%\Wywu1 %TEMP%\Veilp\oqin.exe1 %TEMP%\Wywu\xelaj.exe1 %TEMP%\Dyapxo1 %TEMP%\Dyapxo\duime.exe1 %TEMP%\Ompiuw1
*See JSON for more IOCs
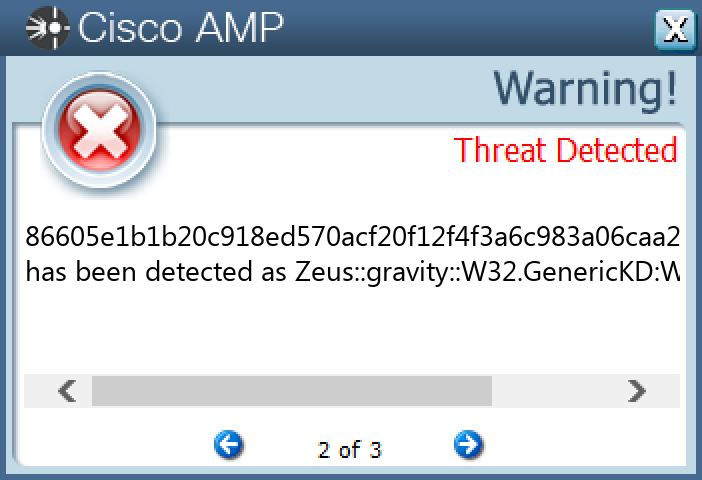
File Hashes 24265020107e90f6c9a98e74eabcc40608acd6bf2f9041b29bb7b3201b3f2394 479edb0ed909cf357ab6c224ae9fa52d5ebd328f8e7554c7efc10c38a0328578 711151da9ff81ef22ceb1a7f1038b39a1ed22fc310b61ce6e22d5601f818f04c 86605e1b1b20c918ed570acf20f12f4f3a6c983a06caa2c1ff3ed9f06cef94ef 8f839cca7e84cd987b3b5a52be7cb9008d4b13f6257d1b31d66ce03779707e17 990d9b63353cef9b82db13465e40b367cffe1b25590e9b417410b990a9e999c1 9e2e36ed25e3e93f3871c077923bb6fd2e425269c980afe975810f8d7fbf70e0 ba988da43985c2eafe1a5e0d504f8f61725298bb72719378ce0785a561cf307b c49e7b653e5e803dfdc77515c50eda4cd7865ebc5d295cead5466e7e05902739 c73763d5dbb740a09f1accadcfa2050f95ddeb0587b6039af83e7e96a6b1ec9e d0430e525a5d48c1213ed38c9ebb99fd35f917a032f5e8a294c9b297da2574ca e1b6a99f1e9da9767b8bd7e4a44058175118d3c1fa57c7be1a386b2e9dbfe78f f007f90c6db8e2e49beb5eef85bc5dc72a2948ef9b8bfc53c730077f2144cf30 f874eaaf9bdb7afdc4409434f455e5a7146fedb28f3d9413491006e560a635b4
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK