Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Nov. 11 and Nov. 18. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
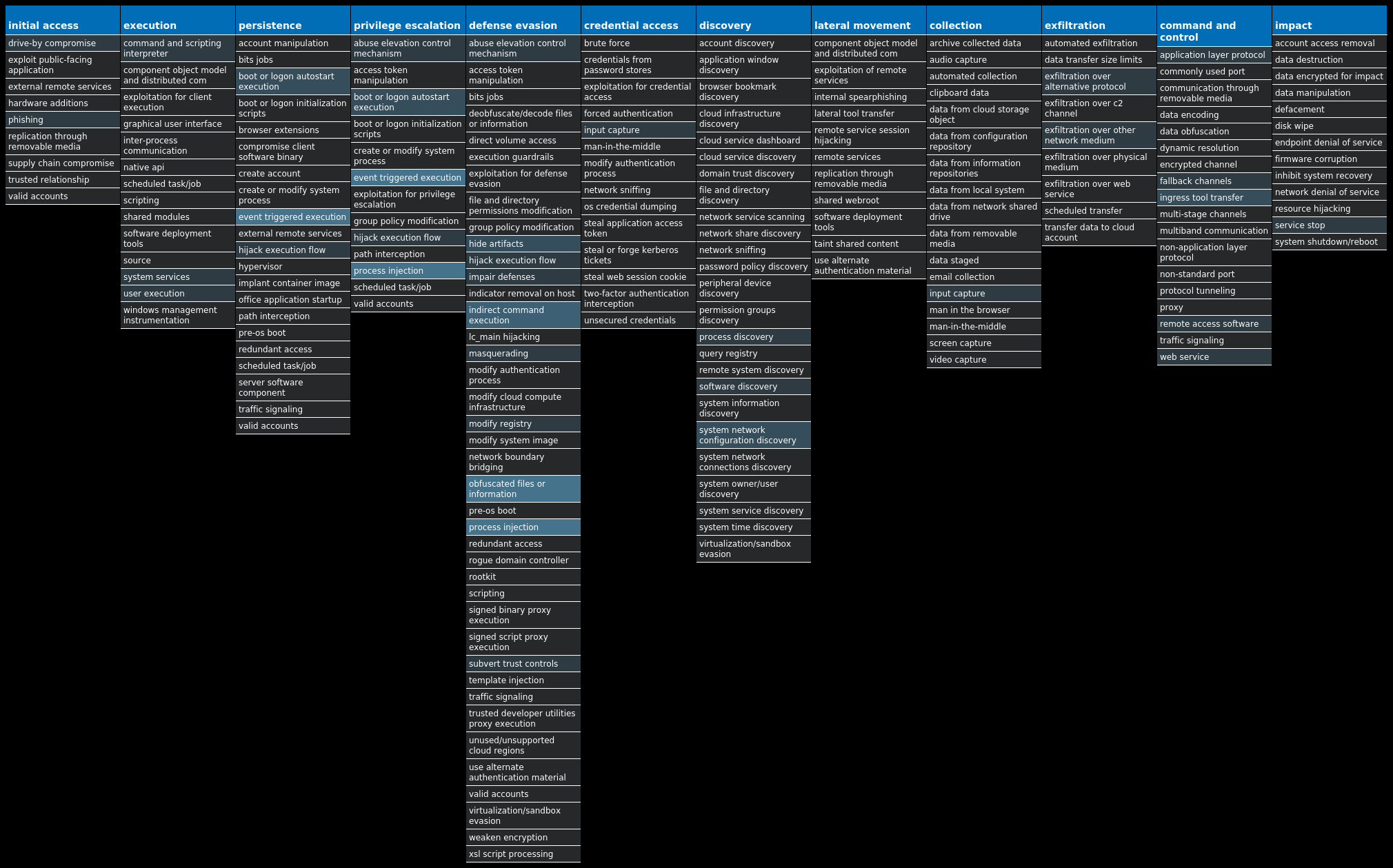
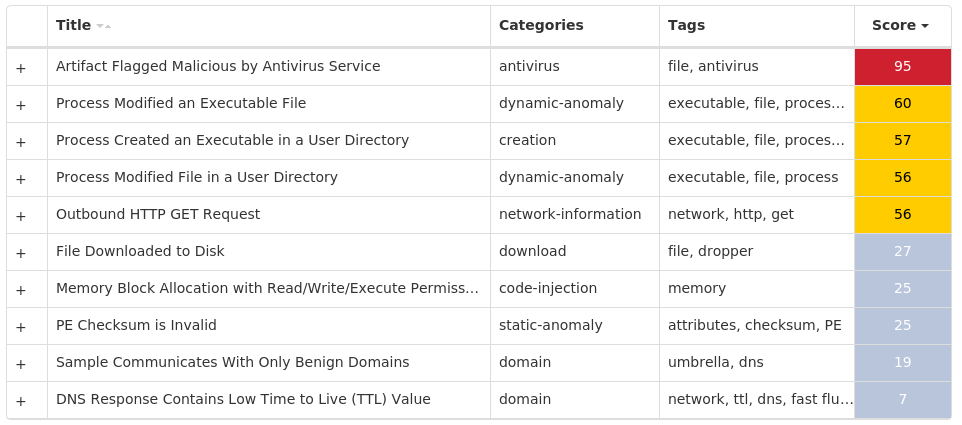
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
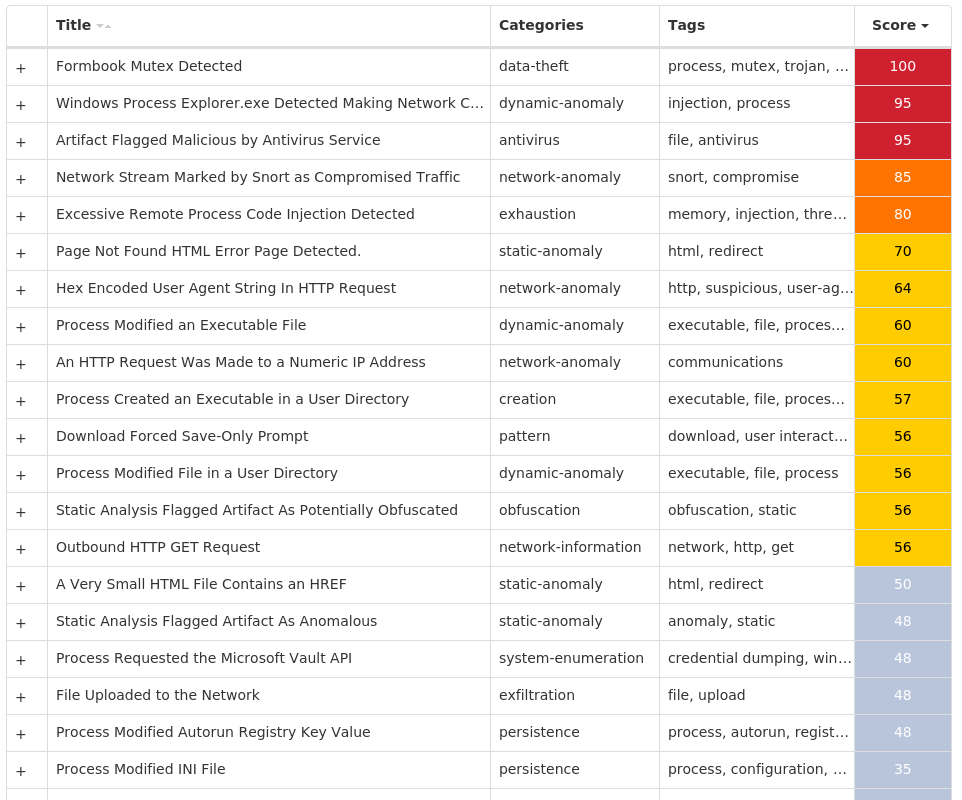
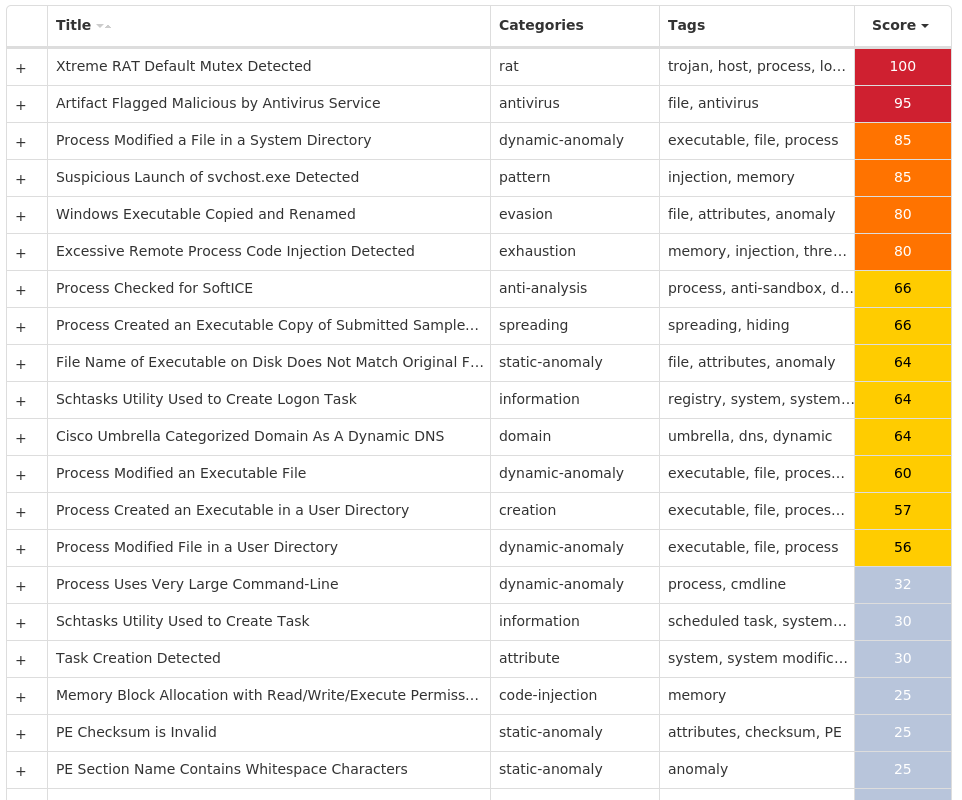
Threat Name Type Description Win.Downloader.Upatre-9977362-0 Downloader Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware. Win.Dropper.Emotet-9977383-0 Dropper Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a wide variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails. Win.Trojan.Winwebsec-9977467-0 Trojan Winwebsec installs itself to a compromised system as "anti-malware" software with desktop links and various persistence techniques (Windows service, Registry Run key, etc.). This family is known for using fake alerts for malware found on the system to deceive users into buying services before the "malware" can be removed. Win.Trojan.Hupigon-9977585-0 Trojan Hupigon is a trojan that installs itself as a backdoor on a victim's machine. Win.Trojan.Qakbot-9977748-1 Trojan Qakbot, aka Qbot, has been around since at least 2008. Qbot primarily targets sensitive information like banking credentials but can steal FTP credentials and spread across a network using SMB. Win.Malware.Zbot-9977753-0 Malware Zbot, also known as Zeus, is trojan that steals information such as banking credentials using methods like key-logging and form-grabbing. Win.Packed.Razy-9977758-0 Packed Razy is oftentimes a generic detection name for a Windows trojan. It collects sensitive information from the infected host and encrypt the data, and send it to a command and control (C2) server. Information collected might include screenshots. The samples modify auto-execute functionality by setting and creating a value in the registry for persistence. Win.Dropper.Formbook-9977759-0 Dropper Formbook is an information stealer that attempts to collect sensitive information from an infected machine by logging keystrokes, stealing saved web browser credentials, and monitoring information copied to the clipboard. Win.Dropper.XtremeRAT-9977807-1 Dropper XtremeRAT is a remote access trojan active since 2010 that allows the attacker to eavesdrop on users and modify the running system. The source code for XtremeRAT, written in Delphi, was leaked online and has since been used by similar RATs.
Threat Breakdown Win.Downloader.Upatre-9977362-0 Indicators of Compromise IOCs collected from dynamic analysis of 14 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\STARTPAGEValue Name: StartMenu_Balloon_Time 5
Files and or directories created Occurrences %TEMP%\xwjfk.exe14
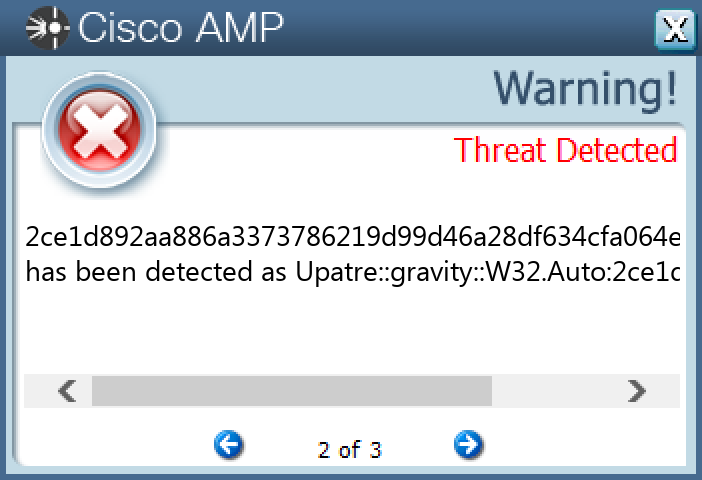
File Hashes 0ce28aeedff22a0e55bce0f016084d447194a425bfc57a1742bb3b001cbbf1330ed0c8332a8548cfe20569bc8b88c183765c4a88c59635e97e79ec954beae3e2 2ce1d892aa886a3373786219d99d46a28df634cfa064ef24d14eb44ce5ab41553248e557cdc359b6c89756027eb63024e109756c4ddf503c84992cdbfb88c5b0 35f11555b1becf3eaa7473c4e56a79cce67222141e7bf86312ce5eaaa23f3afc4499aa8e1de46ee210121562d5ffd13eb50ed2af4d16736a97e5675d506509e052431eb3908465b9c9286e9fe21cba8f8c684dc92842a9374b8f34654f3b271d5e23dc2d0bf866f139fa6ee6b95cf391e915cb4ee9c29cd79aa01bc9ef97da8c711fbfe4245a9865b17e9a61d7c5cfc6664823bbbb9d8f4c859f8f122b9f0729 750beaa4d43b84e5c2c9d0f8d7207b74af65d8dbeb3080f1b47dee70bbca521993b86b7a74458678d0d9438089a2f187a14d41a02458c4171be9cbf6966d920b a5bf30478a9b46d3eb6e38713f10c1f1e05ced7616a7401d09343eb0eec97425a5e5ebb80873575a9d1a524118ac2ca072753baf760153d4b3637f2a67155ae0 dc53e0268eff4a996409ba19d1b55df385dfd00ce6cbeda093991f1967aa0277
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
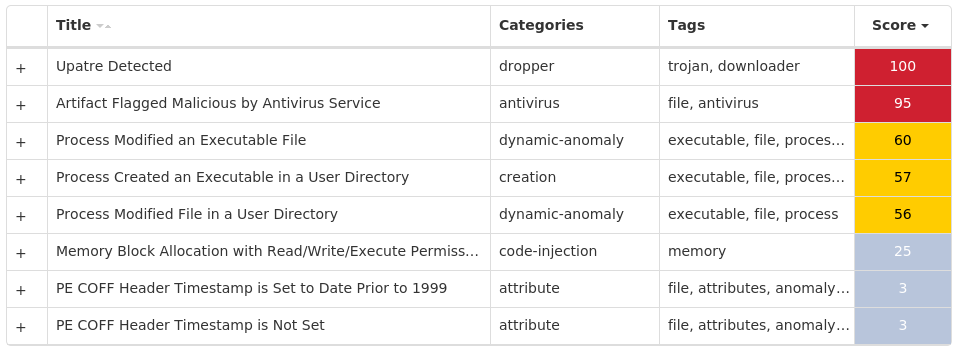
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Emotet-9977383-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A}Value Name: FaviconPath 15 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A}Value Name: Deleted 15 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPESValue Name: DefaultScope 15 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}15 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\APPROVED EXTENSIONSValue Name: {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} 14
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 13[.]107[.]21[.]2009
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]bing[.]com15 cyanteread[.]com15 hq92lmdlcdnandwuq[.]com14
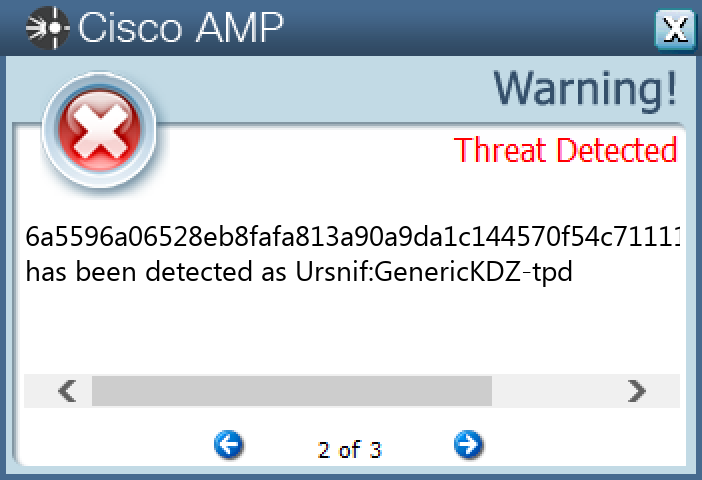
File Hashes 003d724d91ea724259e57e81c1c2236060ead1591eaa4b2afb20ab0b41e0b4ff0715018a8f89c3885ba377f91425d42d1695aa423534b3d1b51d9af17fba950508b991c330e72320ce4e56777a8704964b321b16252ba135c372d378257d000c0f0c41bb5a586c913d2ea5cad4fe4b0b3f381e80b9efe2657f94a024303d64c211edc1b99293a2f603d02802ced72b1167cd434d3d8aa631037347214f150541120cd11824305fe9f6a55710741164a80d5fb8c26888073cec3ffb84ac0c95531a80809e1f36f446829cd44ed8658dc6ea44a11d57dc39f9450d13d429d6c5eb 1ae3e6c08e544fe78b5703521773b57a8fa64d20ec1c50d99414eb910b9178582c738465fb32aed74b6b8b961eba819c683eae5a44262d686bd1c465cbaf6cb72e094ac541cbb2c1f509c1c12b352661582ae983a6316b6724a01a018ac599432ee9a3cfe4d921358e5b506678ffc8e2fb1e8b4759dab278607151bf47645530 39ff15f0d980885538a327a291305e63ff44ec63f508f44f7989adbc562d886f3afb9cb9b19a5d420914950f125f104c1e030a58c0ede92606bb15f1b9123b134687cc2e93ec5e9f5b80c8f2b3b34650bda86d15ccd1fe5da6d8157b4276b63b 48f1b41e40630b02a6c28f3ccf7c2cd21008ad4c61177878edc206fd16342ea5492818d79e1374c9167af43f6d4b20fd506e5c502a7b12d726bb220647a1c6a64dbfa6ab3115876b6c099aff4a463fa5b636f8f458ef94959738059280dd44de560a09676c1ce3d3fa574b922bbfdb4bb30281ad513d4540945d809efdc7bc876a5596a06528eb8fafa813a90a9da1c144570f54c71111041f2a71b3b71a6c836cc6c9c50e495679bac11e2ea84fe6fd210a8185253127dabce4be98fc8e7b417d6ae74b0fd5a239d0179d087939a4a0a6db6f9acfdc5d5f969e5fa98742993285c4c56f7393370a8c7cda68d51135e57d36193073f37b5fbe4c9998978a8c588a26339ebb413ccd632588fc2a003c4f39797d24721be1a039dbc54c92e3e0068b18c983993f5ea0653e33ef89b801cf5c3bb56b06782b1d6e87cb86d0882cfb8fc30d5ef233c3ef7c8f313cb9cd4b31992676a0ccad5ab68487717b7c92d816
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
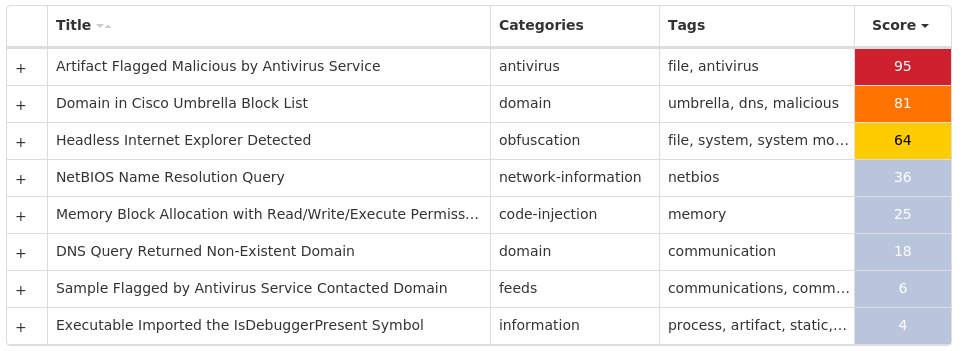
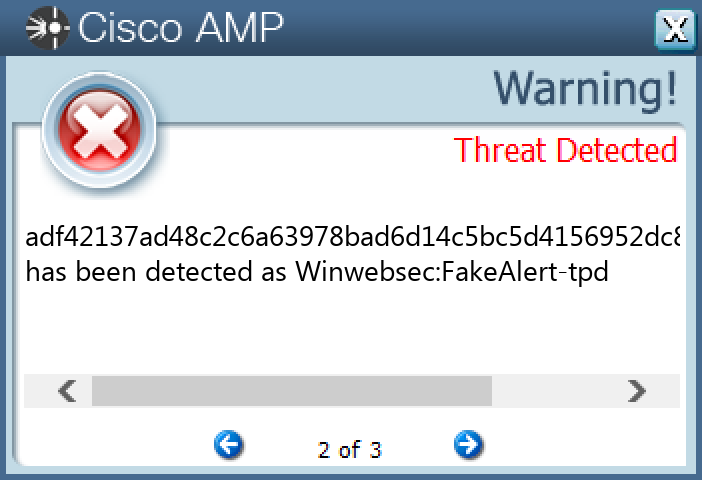
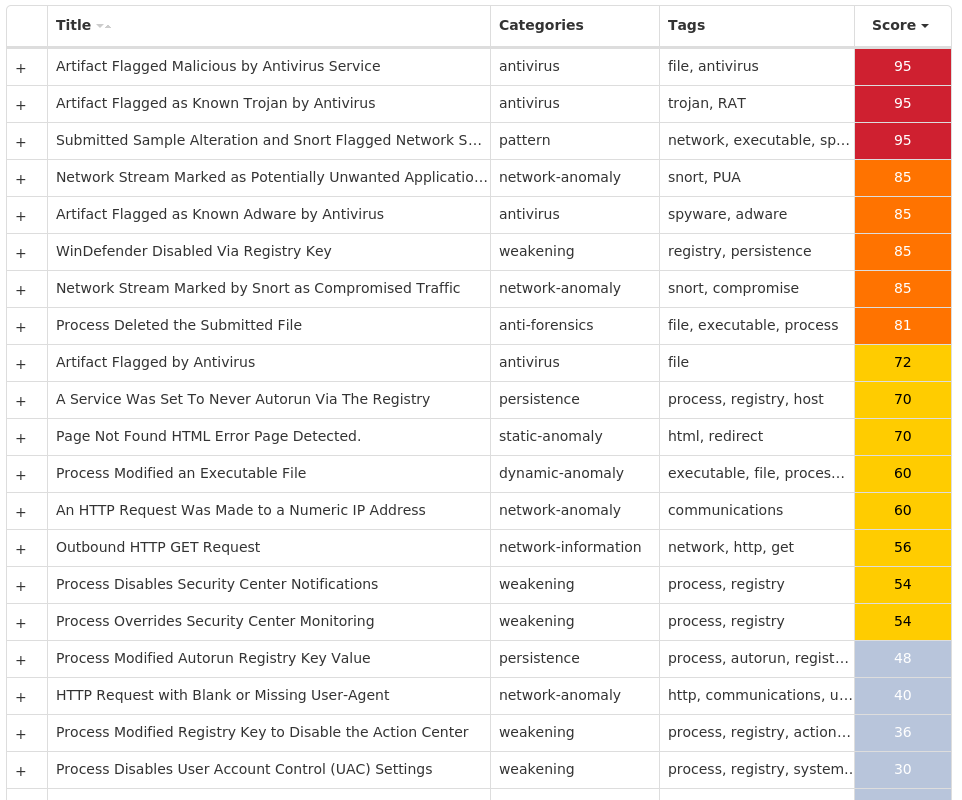
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Winwebsec-9977467-0 Indicators of Compromise IOCs collected from dynamic analysis of 13 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTERValue Name: AntiVirusOverride 13 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTERValue Name: AntiVirusDisableNotify 13 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTERValue Name: FirewallDisableNotify 13 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTERValue Name: FirewallOverride 13 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTERValue Name: UpdatesDisableNotify 13 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEMValue Name: EnableLUA 13 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVCValue Name: Start 13 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFENDValue Name: Start 13 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORERValue Name: HideSCAHealth 13 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERVValue Name: Start 13 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\LUAFVValue Name: Start 13 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SYSTEMRESTOREValue Name: RPSessionInterval 13 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDERValue Name: DisableAntiSpyware 13 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 7812A3CE2B17D97900000313F875EF60 13
Mutexes Occurrences 7812A3CE2B17D97900000313F875EF6013
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 112[.]121[.]178[.]19013
Files and or directories created Occurrences %ProgramData%\7812A3CE2B17D97900000313F875EF6013 %ProgramData%\7812A3CE2B17D97900000313F875EF60\7812A3CE2B17D97900000313F875EF60.exe13 %ProgramData%\7812A3CE2B17D97900000313F875EF60\7812A3CE2B17D97900000313F875EF60.ico13
File Hashes 15da981b1c9220e7be7a9bab45086c54c6abf5ca3f67f516d725aba78663a11728c0acdb4802add547be567598804823073f989255dc968de71bdacc0d1d150c48c44dd30bc5fc5618086f46a2d68d25f7ea2a180f1a3d9a063b9b8fbd66d1b6 4f56a26eff59d45fb967b577873438cb1d9b220c42c776af8ae4f99538a83d196ba6713b8c260e8a8010e3cadb3ae6943bdc786a06133314a5142d8c4692beec707b4b357151fdc654994e63f11104e360f937d200b2ef86d07e7f7e5ccc76817674d67e74b82a75d4aeb4d69199ad702b8c811081aa93736b4cf6e378c0d2cb 79bb080b2b89c40d866e6d28551b6414ebbd604aea5097413714ce06cdfbd9ee 8c5b085f532f6c82f7dd2e2a59333f69ec7729751ac0cb24b34a1e58ce96a456 8feadf32687dd1b0ec8a243c59c0d2b894fff34b5a96684da21652aec85e6b9f adf42137ad48c2c6a63978bad6d14c5bc5d4156952dc818aa3a355fef1ead750 e653a3adcae1506103a930f39ef8bcb5f7a9e215f60c89cca67c3b7b7ad9ec1e e6f2a5efdfc6795767941b3087576ebf715657baf1344e4547eb64c16bbf04ff
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Hupigon-9977585-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\FRUNDLLL17 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\FRUNDLLLValue Name: Type 17 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\FRUNDLLLValue Name: Start 17 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\FRUNDLLLValue Name: ErrorControl 17 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\FRUNDLLLValue Name: DisplayName 17 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\FRUNDLLLValue Name: WOW64 17 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\FRUNDLLLValue Name: ObjectName 17 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\FRUNDLLLValue Name: ImagePath 17 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\FRUNDLLLValue Name: Description 17 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\SETUPValue Name: Beizhu 12 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\WINOLDAPPValue Name: NoRealMode 12 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\WINOLDAPP12 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\LANMANSERVERValue Name: Start 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\LANMANSERVERValue Name: DeleteFlag 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SVCHOSTS1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUND1L1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUND1LValue Name: Type 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUND1LValue Name: Start 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUND1LValue Name: ErrorControl 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUND1LValue Name: ImagePath 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUND1LValue Name: DisplayName 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUND1LValue Name: WOW64 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUND1LValue Name: ObjectName 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RUND1LValue Name: Description 1 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SVCHOSTSValue Name: Type 1
Mutexes Occurrences Rwx_free12 Global\b66d3b21-6365-11ed-9660-001517e7b43d1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 157[.]122[.]62[.]2052 183[.]236[.]2[.]182 59[.]42[.]71[.]1781 49[.]2[.]123[.]561 23[.]89[.]5[.]601 222[.]198[.]42[.]2531 199[.]48[.]208[.]1501
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]163[.]com8 http1 11984[.]gnway[.]net1 yelaifeng2[.]3322[.]org1 genius3016[.]pimp[.]fc2[.]com1 lingfand[.]3322[.]org1 fish2008[.]3322[.]org1 z6366010[.]3322[.]org1 ahah[.]3322[.]org1
Files and or directories created Occurrences %SystemRoot%\SysWOW64\Deleteme.bat12 %SystemRoot%\SysWOW64\FRundlll.exe10 %SystemRoot%\SysWOW64\svhosts.exe1 %SystemRoot%\SysWOW64\ÐÔ¸£ÁªÃ˵çÓ°²¥·¢Æ÷²å¼þ.exe1
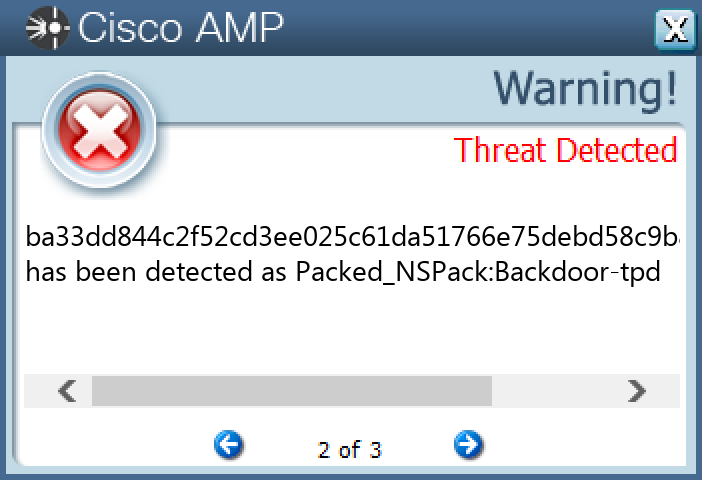
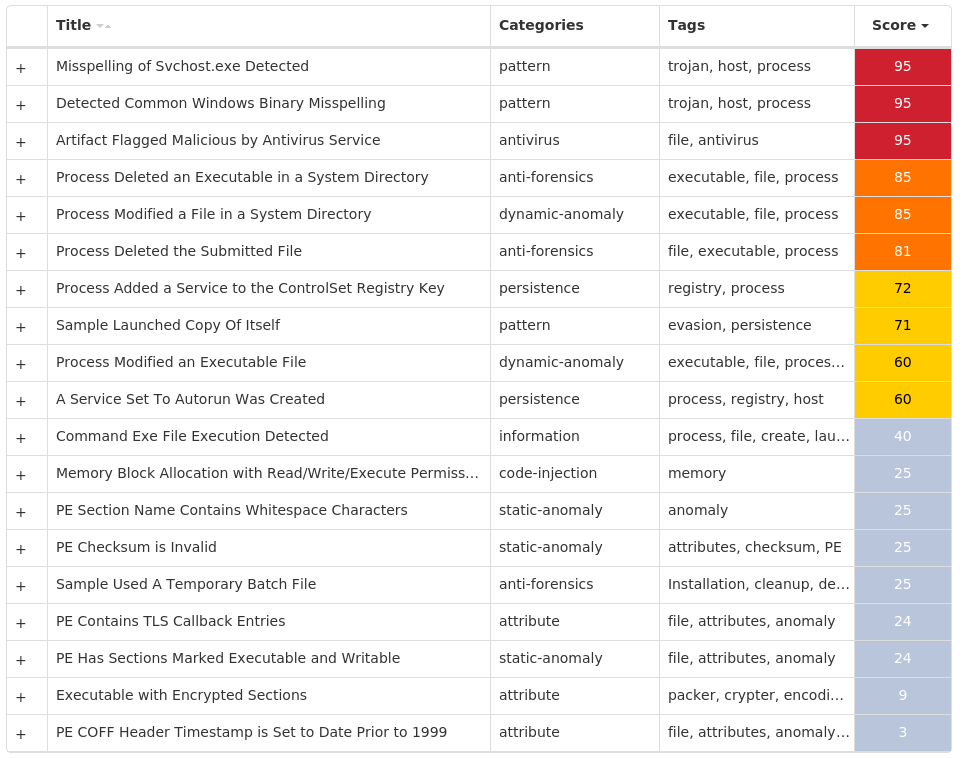
File Hashes 036f4e965137f92e4a23b68714ca07764dbef452fbe521a9ab436709ae2544e8 0556f362906bad908653298bb5859da2dcaafb7d3800bb3e8fb5ae0bd83183c9 10eb9ccf8455511663b12e65f9caeeba31500b13cb0a8cbd91bd142138fba92d 1e0071e523ae8094b1c94e0a98da912a8d027851554548af937dc1801828f042 2d5fec1d5b79d97a0c75420433543dad8b69cb5fbecdef425cc66bf20e0acf75 2e9c25ad8734a0fe91d142e2131e56ca38cc6c63e73010aba8650425fc417e0230f8e398e5a4dee30fdf9768f32cbc1d0ae0565d1aee33d4060cc3f147f753c53e1cc765da65267b5918ca105de32f1402c4fde86475543cc106878ff11618e7 44f4640ffbe6909163a5742de105ce43ed6200ef2cf7c50b285b702e4b2073ab4c6baba1332e86122a14864e31cddf7b49b3305e2e62c9895d62c49cc3c82bf45b2a993ef4e5078eb6692b341bcb44e73b41209500572b92dc926265b1dd1f5e 77e505dc53d30b4e03ceabb86a9fa7f0713724873a537594edcdfb6cf945beec8937293e8af2d13a8a6b811d19e6f1fbddeedf8cfa4987dc06f9b50c932152e8a6857ef8d31dc8d07d64be5cb7e8bfa05d4bf14dcdb41784bff4951c05b07466a91b79c69652b130894b2e51ec0654933e4fbff3cdb3f4199f061e421450309a aaf39fe00d7ac4fa5e2f2db7112226cae4119348681dab09c3e3aebf4f93cb9b b03a151d39ec64eb056d910c39da13b40399a4f3d38e59c3736550076b72e6a8 b09d7d116e7af15e20af41f6991b60ece18f87e5c58849d5b28c800e51ca1e35ba33dd844c2f52cd3ee025c61da51766e75debd58c9b849e1358a5b673a2bdcfbc0247ef0af6afa87f00dff77888d5ab0ee3b9a12eb5852a57bfed49f1450539 c7e8d59a821c63d10024c427c684bace71589e6abd52b6696a143f0896a9bdb4 cc43c386d58ee5c6b5a2a8693e9a6b86ac98c24049981cd33bfbdda1e0ce19f8d3fa1b573205ea85881f6a32dce9a40483b9ace3b67ca833a79c619b153c96a5dc6bd088fbb4d37ed3ec578dcbeb235b02083dc2e554b77a800f9af3f2af5331eb8d4c979fd1630a9b1e0db629aeb89ba0af2fd42352e88f0c908571a5aefbd0
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
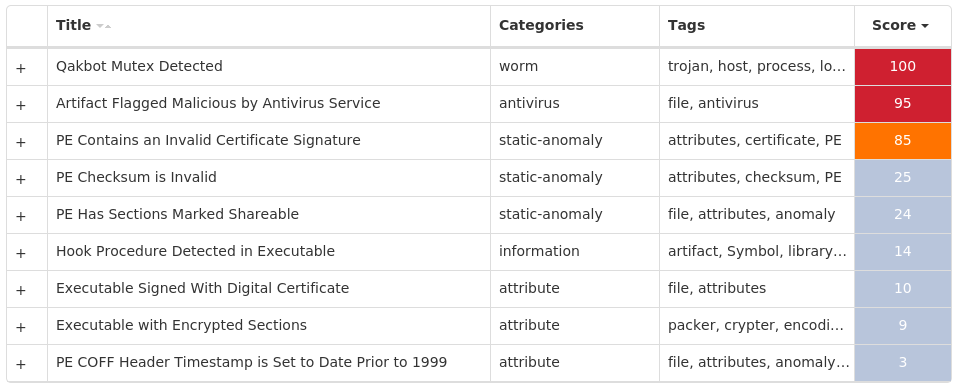
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Qakbot-9977748-1 Indicators of Compromise IOCs collected from dynamic analysis of 35 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\DFWOFIK35 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIKValue Name: bd63ad6b 35 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIKValue Name: bf228d17 35 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIKValue Name: f7b512d3 35 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIKValue Name: 79eea72 35 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIKValue Name: 7a96a5f8 35 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIKValue Name: c22ac29d 35 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIKValue Name: 5dfca0e 35 <HKCU>\SOFTWARE\MICROSOFT\DFWOFIKValue Name: 88fc7d25 35
Mutexes Occurrences Global\{06253ADC-953E-436E-8695-87FADA31FDFB}35 {06253ADC-953E-436E-8695-87FADA31FDFB}35 {357206BB-1CE6-4313-A3FA-D21258CBCDE6}35
Files and or directories created Occurrences %APPDATA%\Microsoft\Xtuou35
File Hashes 029b9c4ca487978b74ce2556e59e1215509c7bb09e9b61c2cab7e2c4d3e9ec71 02d0b6a9c0b162554969082d2bba2f49127a5f4a64536123ba34fa7d81dc429a 0b3616ac4a71aa74173b336da9153f523f6053677af12eeefb24d0a89a0a892f0dee39d387e2cbec11c99ccdf99ae016ae6d816d1e3f45fa61d2e2ea04f92479 0fa08984cf7b5be4ce4f88d85f577df912e531bc178a498679be2d1c868cc9d3 1331e1c43ea3422e707d26afae65656c39fd99f7662b558124e737e444c9d759 13dbac70a80b241a61a21b2e502d75f1b11e7479d1d11d9f18b364883d71456a1443961958783cf6d2d854a83bea4b6cba4c5ce0db63f3ffc13545adf3e2935b1538ad1d6923c5428ba86b809109f45c5f6e1c3e829549bc5a478d12b25ad703164404d2c09c326eb00d6aaf6e54516f17703610814bdcb280ddebd534682c1d16602d90ee3a42ab680de52eb9e702b6bb86694361bf59654fbbb30b8565ee11167d3327a1d3b48e991626a6985a5a8e29830d409419fa2ec9f8a742ae605afa1aafbdd50cd79775d2f6a141a8f92e66ae3a4b6313f5bbd885caa378d4338c97212add05616a4386bf4f3a67fd98aad30c56dcc75362f74ac86454bb96e55b03 217ed037185127b19651401953b69bd03fd0303004bbd6808313040a586a4344221b5cb284b9b80756eda21cbc33cf5d9b5096bd21d3fb36669e7eb3bc9bda90229a4e97b2761e39775890882b837be457df8f2835163f115d99e698d8d9a9032b75842ccbea7eec737fccb72ea4475b586db66bbd057d47eb086a912c3294da2b7bff2744783e8a824da19960cd2c66820dd980f712ad52654d4d5dabc862a52ef08045a1c4f1a43e78388cabb152f4ee20fe52954f9570735ebfe393334b8e 2f5504350fe8c88ef4b5ab92c3401b0c4d70e9894bc4684256058278cc8893bc314958084e6fb7708fb06410236e0132d26cf54c26f6ee9aafa10f8c60e16d0432123200969bbc95dfc0d16cfb6409e5d7d91351fd0340120bca5a2bb72caa84360e29803c92d6271531e87d9025f59db7a1546786e4013a072280d29e01428b 3905804a6dba4a25bcc469bbd18dee15e6731cbf47c233997b1829f8dac36276
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
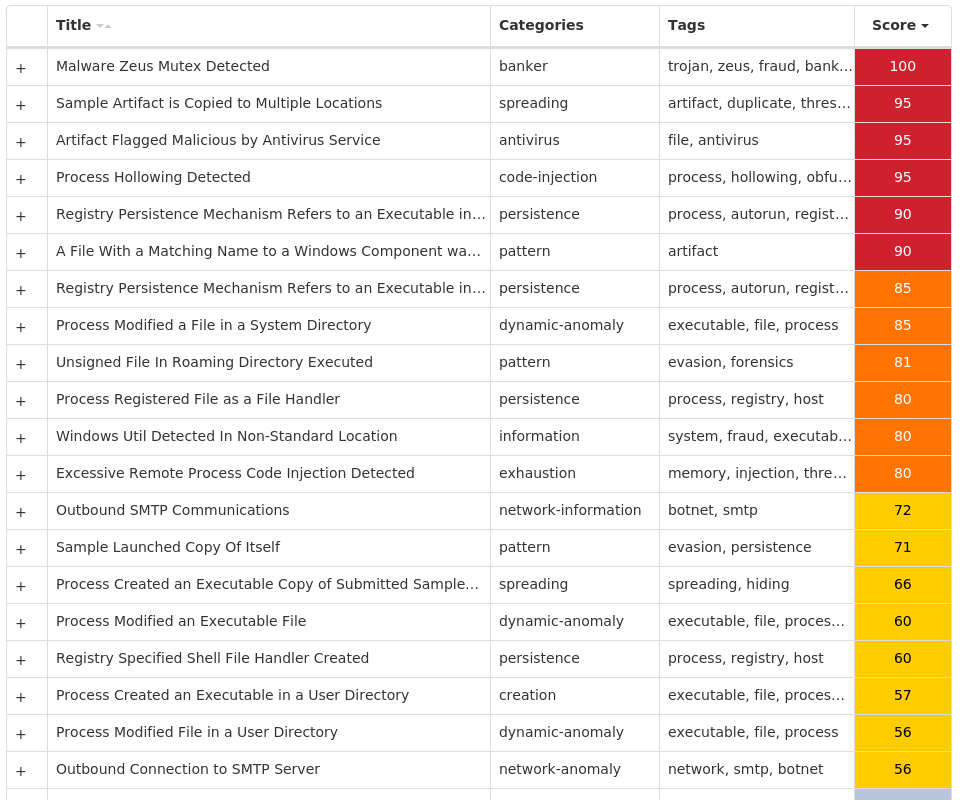
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Malware.Zbot-9977753-0 Indicators of Compromise IOCs collected from dynamic analysis of 35 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MATRIX31 <HKCU>\SOFTWARE\MATRIX\RECENT FILE LIST31 <HKCU>\SOFTWARE\MATRIX\SETTINGS31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\DEFAULTICON31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\SHELL31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\SHELL\OPEN31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\SHELL\OPEN\COMMAND31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\SHELL\PRINT31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\SHELL\PRINT\COMMAND31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\SHELL\PRINTTO31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\SHELL\PRINTTO\COMMAND31 <HKLM>\SOFTWARE\CLASSES\.MAX31 <HKLM>\SOFTWARE\CLASSES\.MAX\SHELLNEW31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT31 <HKLM>\SOFTWARE\CLASSES\.MAX31 <HKLM>\SOFTWARE\CLASSES\.MAX\SHELLNEWValue Name: NullFile 31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\DEFAULTICON31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\SHELL\OPEN\COMMAND31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\SHELL\PRINT\COMMAND31 <HKLM>\SOFTWARE\CLASSES\MATRIX.DOCUMENT\SHELL\PRINTTO\COMMAND31 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEMValue Name: EnableLUA 3 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVCValue Name: Start 3 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFENDValue Name: Start 3 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESSValue Name: Start 3
Mutexes Occurrences Global\<random guid>9 1FF35F9D14B75F818C01D1BD93F28E2098B68E3C3 GLOBAL\{<random GUID>}2 Local\{<random GUID>}2 ltcminerd_0.1.11
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 95[.]211[.]144[.]684 204[.]79[.]197[.]2033 34[.]102[.]136[.]1803 20[.]109[.]209[.]1083 37[.]139[.]47[.]1083 62[.]76[.]40[.]1773 81[.]169[.]145[.]1532 80[.]150[.]6[.]1382 195[.]78[.]66[.]1202 184[.]87[.]164[.]1112 23[.]218[.]129[.]1072 193[.]200[.]81[.]1722 185[.]137[.]168[.]952 109[.]123[.]223[.]772 219[.]87[.]140[.]1392 103[.]131[.]74[.]322 119[.]59[.]104[.]132 23[.]221[.]227[.]1692 34[.]160[.]73[.]2302 104[.]244[.]99[.]132/302 76[.]64[.]213[.]211 154[.]23[.]86[.]1701 23[.]231[.]93[.]1741 91[.]216[.]151[.]561 89[.]140[.]72[.]1061
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]msn[.]com3 x1[.]i[.]lencr[.]org3 wiatraki1panele[.]com3 williamsburgsoccertrainer[.]com3 yangzhouwebs[.]com3 whucprotections[.]com3 yghqlyz[.]com3 wirtualny1zamosc[.]com3 gondalarmes[.]com2 onedann[.]com2 howardsgroveboosters[.]com2 tenlightingsl[.]com2 www[.]glamone[.]eu2 imm1bkk[.]com2 sweetmata[.]com2 alt[.]hrgsm[.]com2 esserv[.]com2 52869881[.]de[.]strato-hosting[.]eu2 www[.]aktion-fernsehturmspitze[.]de2 slobstyle[.]com2 www[.]dorakawycz[.]de2 elmextrans[.]cba[.]pl2 yannick-strototte[.]de2 nach1900[.]homepage[.]t-online[.]de2 restauracemalahrastice[.]cz2
*See JSON for more IOCs
Files and or directories created Occurrences %APPDATA%\{a2a8f052-eba1-4da4-14b7-5f81a2a8f052}4 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\{a2a8f052-eba1-4da4-14b7-5f81a2a8f052}.exe4 %TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp4 %APPDATA%\bwwdfwju3 %APPDATA%\bwwdfwju\jisgivdt.exe3 %APPDATA%\svchost.exe1 %TEMP%\libcurl-4.dll1 %TEMP%\pthreadGC2.dll1 %APPDATA%\rundll32.exe1 %SystemRoot%\SysWOW64\csrss.exe1 %TEMP%\minerd.exe1 %TEMP%\mssF951.exe1 %TEMP%\mss405F.exe1 %TEMP%\mss203.exe1 %TEMP%\mss20F1.exe1 %TEMP%\mssA3D6.exe1 %TEMP%\mss408.exe1 %TEMP%\mss7D67.exe1 %TEMP%\mss43B9.exe1 %TEMP%\mss9897.exe1 %TEMP%\JLLA196.bat1 %HOMEPATH%\AppData\LocalLow\rexe.ajr1 %TEMP%\Hynyaq1 %TEMP%\mssDCB.exe1 %TEMP%\Hynyaq\yhopz.exe1
*See JSON for more IOCs
File Hashes 007bbed783770609db3a14b6dfbae7dec15af21a433688dbebd70bf169092502 026471be0093c51f875831775547db043d4142ded28cc14c9584c4321082a135048b669f3b888816c889da0b0b8f70af4bd520aa31e08088bb3acd0439732512 089fdfc6590b3f05862d34a5caf88139f8bbbbbdee17ac65efebe0fb0a269b880fd494d931d4f3253389d77d635037354493df1867bcbccac1d44fb10714fc70144dea9d435a7cb3088be366ec3ea8e923aeff931664721779de980344e4acfc1565e8085f833a11cd48e6fce7a98e5903bd8e91c72abde0c4df1c12e3fabff8 1713787353d3c3230842910efc916369ee732e18903777f5241f23e0ed587e22 183c509e3cb7250452e89f0ef166087e5e84a3a205b554bfa208cfdc52c8b04e 18b045aef6cc597fb3c13c1d15b8780f24372eddbb781ad86bd185d16f5aaf87 1bfdcd9b98d0127586e9daac5ab588d03f9d0f1430e9a8a54463e091f0c4b7d5 2501d1316553e09c71ba45f4f6b9d82659ce111b03aa1276d34084473545f1bb26dfd88fc6bbb40f6ccc9379160a6a65931eab1ba70734ba1f06cb4056cb56e729ef3e12750fb6052c69a9a7a0320500c086fefb2906bd8f2bdf76202155e908 2a84c8a7ec388c99551f626d0d4b119fa3d60b028754bdabe7229869baa5c5a72f214a2e7ed3c0758d9b701dced0626ccdcdf2de540e3777bdf28a3e0f7cfade349eaffc46c7d936a7fa38d23e04a195d5ab88cea61a943215b64d44ba90057a 3c6a863a4ad047c0e618f3eec1661a6879243c8e3f25cff1a6cd497a79c857333d56b2b9aadd13e523115e559e74c721a89d2184f2b3531487265f76cabb608b 465901d3fb9827b1fd5c1e41628a9004a8b6ed410d97750b0c65f74937e2a59d 46c0b59f0aa232643a1b4b6380e8a235e7e80605236cab2832b3029f2cae69f9 47409ab190e17b1f8daa3d1c74dc21df22a5722562020313f802aff0297f423248aa870faca9e24489633c7b3bcf3369d18cc81984f7954750e8d32f3615f3994a452f56d965c14bb5f63ab9c5bf487c05216b22446bf845125f15fe297b638e 4bec69cf6bb6f7224d8178831bf5c6c433827fe3aec27045f24bc9e555880b9f
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Razy-9977758-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 35[.]227[.]197[.]3625 45[.]32[.]181[.]13825 23[.]221[.]227[.]16916 23[.]221[.]227[.]1869
Domain Names contacted by malware. Does not indicate maliciousness Occurrences apps[.]identrust[.]com25 infacom[.]co[.]uk25 flowersinparadise[.]co[.]uk25
Files and or directories created Occurrences %TEMP%\finc.exe25
File Hashes 0175d9d196d36cb772c4cafef83b6215de0dd35cee939d1df133ce740b4ab3b5 045154cff7d3f9d97d9afd40d9dd635dd5ef07da0c3180f3eadfc03ecf785ee010616b845ffe5d716feff93cadcb7f7997511e53450d1ed385ce1810621e582c 1e2724326801060137e8d663843541aa1b39053c4e0ef5625bf82e128768e056 22ba433714e313ef103e8ad63d6e7e5b52c620c5ea75188790c87bb238b8fe51 26553309ce2fc1e233d4fc6500fdf444f63133b203c733d327c7237f97ccc73527e8bfb480ac07b81d718a9d47cd21397a00cc7d86c5bc94c08e17b585e79bc2 2939525931f070688b77f285bbb6622512e1c59b6c8940cd88c9dd0d4fa810ce3118f3ef507a09d79bace50ac5a65e66ffb0ae48dbfa186d0ca546047c6c50df3288a59d52c01dedf6840e13a0f1da64917caff7cc7d57aa1202e83cdf13f6a132dc1b28c7801bdffce2cefcd0847a836a660c937fa174e5313cce5767cd4dc5 336a9ff27d4ba7d098dfc868aaaf1c3b89bb7f32bba93e78f1099cb053ddc958 35c04ab20b9dbb2c4cc1690dbd5bb03502b5c8ea78f89ec49449d9ed35cae15c 36c58990cac473b32a557f7c8a48626cd7461185b28c88ed7ba4cd4da67f9037 3fd634470f5ab28653df7602b79db0bff83d0f004305fffeccdb677c225194274e2f9c24419d95d08d901326bbd54670c389f010128b90b9e681543c19875acd 510119f03e583221fbe6fc4800910a22ec8dd8b135a00a15f761357ccedc848c 53e9fabd45528ca20a95314dc89f364edf8005354677d014d7f1714b8099565b5a530b3e0d2c5332a182bb83eecf3d9efdfc5d55494a297138f911e7a0e0a57d 6227d4828c9148347ff4a08b7bd9f7232555b0b5a897b8c6f4322ac3db0e0fb1 62d20b635b51c75c17090a421ebb39510f1773274f5df3a795be7c10174b2c6b6814013b6be0296d581cfcfde7290da67e865a6cc77d4d43ac41f389dc86a385 68fcc59af4ce75c0c41114240c29668ade49d3b806fad36106506fe4cd378ec3 6ed8b2cb2d8650c1e69706918b33a5499256128f5db94079c1b6ca4a96cdc3c7 7afdb254aa725081a88b97256ba756ffb7eb343d9010696fbe5f24c9542e0ea7
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: LanguageList 23 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\ICM4 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\ICM\PROFILEASSOCIATIONS4 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\ICM\PROFILEASSOCIATIONS\DISPLAY4 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\ICM\PROFILEASSOCIATIONS\DISPLAY\{4D36E96E-E325-11CE-BFC1-08002BE10318}4 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\ICM\PROFILEASSOCIATIONS\DISPLAY\{4D36E96E-E325-11CE-BFC1-08002BE10318}\00024 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\ICM\PROFILEASSOCIATIONS\DISPLAY\{4D36E96E-E325-11CE-BFC1-08002BE10318}\0002Value Name: UsePerUserProfiles 4 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\INTELLIFORMS\STORAGE21 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX1 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX\20.0.1 (EN-US)\MAIN1 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA THUNDERBIRD1 <HKCU>\SOFTWARE\RMC-F7UBS51 <HKCU>\SOFTWARE\RMC-F7UBS5Value Name: exepath 1 <HKCU>\SOFTWARE\RMC-F7UBS5Value Name: licence 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Myqbdrvh 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Mwdwkwmv 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Dogyigqz 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Epngszrl 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Ozybvueo 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Yiziaslk 1
Mutexes Occurrences Local\Color CPL Startup Mutex4 8-3503835SZBFHHZ1 S-1-5-21-2580483-124416124171941 Rmc-F7UBS51 Global\bdd59e71-6121-11ed-9660-001517802c611 NP9N804-4HUZ1-6M1 S-1-5-21-2580483-200042065276741 Global\9dd66881-6490-11ed-9660-0015177db5a41 Global\70925d71-6490-11ed-9660-00151791cf121
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 13[.]107[.]42[.]12/3111 104[.]18[.]38[.]17410 172[.]64[.]149[.]826 85[.]187[.]132[.]1774 104[.]250[.]134[.]503 5[.]230[.]74[.]2332 204[.]188[.]203[.]1541 34[.]102[.]136[.]1801 23[.]227[.]38[.]741 198[.]12[.]126[.]2101 23[.]221[.]227[.]1691 216[.]250[.]254[.]2091 202[.]79[.]169[.]331 172[.]67[.]144[.]1691
Domain Names contacted by malware. Does not indicate maliciousness Occurrences onedrive[.]live[.]com16 cacerts[.]digicert[.]com16 strassenburgpharma[.]biz4 aljassimaluminium[.]com3 apps[.]identrust[.]com1 cncooksware[.]com1 uyoman[.]duckdns[.]org1 www[.]jsneibuquangf[.]com1 www[.]niaxnhmy[.]top1 bqkqug[.]db[.]files[.]1drv[.]com1 www[.]comfortableleaves[.]top1 oywkla[.]ph[.]files[.]1drv[.]com1 clhulg[.]ph[.]files[.]1drv[.]com1 54jjza[.]am[.]files[.]1drv[.]com1 oyvg6a[.]ph[.]files[.]1drv[.]com1 www[.]aibrey[.]com1 www[.]cooperlawnservice[.]dev1 www[.]tenoneintelligence[.]com1 www[.]l37insights[.]com1 www[.]cendla[.]xyz1
Files and or directories created Occurrences %ProgramFiles%\Microsoft DN11 %SystemRoot%1 %SystemRoot% \System321 %SystemRoot% \System32\KDECO.bat1 %SystemRoot% \System32\easinvoker.exe1 %SystemRoot% \System32\netutils.dll1 %PUBLIC%\Libraries\Null1 %APPDATA%\NP9N804-1 %APPDATA%\NP9N804-\NP9log.ini1 %PUBLIC%\Libraries\Myqbdrvh1 %APPDATA%\NP9N804-\NP9logim.jpeg1 %PUBLIC%\Libraries\Mwdwkwmv1 %PUBLIC%\Libraries\Myqbdrvh.exe1 %APPDATA%\NP9N804-\NP9logrc.ini1 %PUBLIC%\Libraries\Mwdwkwmv.exe1 %PUBLIC%\Libraries\hvrdbqyM.url1 %APPDATA%\NP9N804-\NP9logri.ini1 %PUBLIC%\Libraries\vmwkwdwM.url1 %APPDATA%\NP9N804-\NP9logrv.ini1 %PUBLIC%\Libraries\Dogyigqz1 %PUBLIC%\Libraries\Dogyigqz.exe1 %PUBLIC%\Libraries\zqgiygoD.url1 %PUBLIC%\Libraries\Epngszrl1 %PUBLIC%\Libraries\Epngszrl.exe1 %PUBLIC%\Libraries\lrzsgnpE.url1
*See JSON for more IOCs
File Hashes 0ee0f5bdc3de668920fb08715703eec62d967df44aeb8f87e7fbdfba1263d718 1d160af25e96ec1d33d50216a3eafdc16a1df90a6c62929e25f626dae138015b 1fcfeaf389a913d7f1a1aec60316b8b2b23c226d14764a6c2f2b5d393f0790c4 201bf83ddcbdf1880827e16099f5880cb500b84401e03513ec843c063ca473b0 2755f422c2fa4735f3eccbe0dc93aee31ec00d95c6692bb2fb41c2214c8bf24f 41597718a8b253d08ee21ceb7f6c529b7391a3b592bfa21c38fd4cdfe68d77f1 4b29834ae85fbe65a8d98050a0b9cd1a58a05fd00c6b3b4f21b3a31587a2c613 4c7b8c559d810145e6f98132d65c614ad8581d373dda1f4c717f571840182741 64d32e120cf032517e274b448258444f67eb71cafe3b613d7a80e85b7836e5eb 69c1794447fd793df47198ea31e77a87cee5a7d558803de5ce28001a17193179 6eefd52a0c37864ccfdebc013a387bcfc549875f3e0d18b15d11de6ecfd847cf6ffcc5061fbafa5eeee756b0292d6ec83109623b786b8e2f5ca5ecbd92a816c07bdc0d9213924f353a5f7d63292cdf7d5cfbff6d732f8b8d2e087705ffe6e9c9 8baa18efb525b31848e655555712186dfc249e9e7bc288fc2b4c3672ffc265669507dfa379dc81b7c5c0bb780cd7282d1afbbfb35382cb50e647dcee1ded95fa a721505426152ac7dc3b8db59c0c8b0958c9ba3d0801c0cba9dfdd2f707cdfebc2fddeddc5cc83dfdf29996689cb419697dab7588015ff0f14c579daa0799ab1c71639f403e5e817ccde3cf251e94d59d6ffd3ab277249ab248bde8ae649e762 c7c58aec8e57886b1549faadb1cb7630698f9981a337aaad04a5d90e4a0373dc cb5aae9535660a2fd396d43bea84e7ea5e8155ebb2cff8de91298345193e9432 d5827c128fceb9ce4e21534e7904ac75f26a8024fc1657bb8da3311e39130d07 e0db15a4f81c59402dfd7dab6fb7676e914c2496760d430c7fcaf1ad284744c0 e3e9372493eda8c15ef90b26f497b77d9b90498f73ca149fc3aca58cf45c841d e4f882faf23f8a28c47b0cc1dd560161c73d9c2c71cc43925b9c166aec6bb05b e9dce2c1d4f82eda9f6944903734e87a0871bbbde5c44f1fb8e49bb1f27b3875
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.XtremeRAT-9977807-1 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCEDValue Name: EnableBalloonTips 10 <HKCU>\ENVIRONMENTValue Name: ProgramData 10 <HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'>10 <HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'>Value Name: InstalledServer 9 <HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'>Value Name: ServerStarted 6 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKSValue Name: Path 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKSValue Name: Hash 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKSValue Name: Triggers 1
Mutexes Occurrences XTREMEUPDATE10 <random, matching [a-zA-Z0-9]{5,9}>PERSIST10 <random, matching [a-zA-Z0-9]{5,9}EXIT>10 <random, matching [a-zA-Z0-9]{5,9}>10
Domain Names contacted by malware. Does not indicate maliciousness Occurrences cooempresas10[.]ddns[.]net4 soporteshp[.]ddns[.]net2 amairadearmasmena[.]ddns[.]net2 isagarlo[.]ddns[.]net1 pocoyo[.]ddns[.]net1
Files and or directories created Occurrences %APPDATA%\Microsoft\Windows\<random, matching '[a-zA-Z0-9]{5,9}'>.dat10 %APPDATA%\Microsoft\Windows\<random, matching '[a-zA-Z0-9]{5,9}'>.cfg10 %SystemRoot%\SysWOW64\Drivers\System.exe6 %System32%\Tasks\tmp89762 %APPDATA%\{DE5Y-YTKY-3SBJ-94CJ-4SR8-PB88}1 %APPDATA%\{DE5Y-YTKY-3SBJ-94CJ-4SR8-PB88}\tmp7439.exe1 %APPDATA%\{5T5R-RLLB-E42B-SL9R-TBRY-I3EJ}1 %APPDATA%\{5T5R-RLLB-E42B-SL9R-TBRY-I3EJ}\tmp3925.exe1 %APPDATA%\{Y8UF-BKXQ-FSSP-J5M7-9C9X-LPBF}1 %System32%\Tasks\tmp74391 %APPDATA%\{Y8UF-BKXQ-FSSP-J5M7-9C9X-LPBF}\tmp4295.exe1 %System32%\Tasks\tmp39251 %System32%\Tasks\tmp42951 %APPDATA%\{W2EY-JOO2-LFEQ-SPKJ-MG38-9WC8}1 %APPDATA%\{W2EY-JOO2-LFEQ-SPKJ-MG38-9WC8}\tmp5932.exe1 %System32%\Tasks\tmp59321 %APPDATA%\{MERT-928T-CSXK-J96E-DSL4-YGU4}1 %APPDATA%\{MERT-928T-CSXK-J96E-DSL4-YGU4}\tmp1586.exe1 %System32%\Tasks\tmp15861 %APPDATA%\{PPY7-CD87-E6XQ-RE6Q-M6L9-9L39}1 %APPDATA%\{PPY7-CD87-E6XQ-RE6Q-M6L9-9L39}\tmp8628.exe1 %System32%\Tasks\tmp86281 %APPDATA%\{LSE7-8BS8-B3JR-OIKQ-C829-XPGB}1 %APPDATA%\{LSE7-8BS8-B3JR-OIKQ-C829-XPGB}\tmp8976.exe1 %APPDATA%\{CPXJ-X6EK-2X4B-EDB4-85RR-TL2S}1
*See JSON for more IOCs
File Hashes 1b1a7ef5d900e80a85f6e02a2f432d112a6f85787a53bb2a422ed3647310d604 1b6d4b2ea651082ef0295ce85770d10e7fa997fa56e96788f4d6173933a060ae 3bdb5349f4f238b621f85a5173ceb6d0db7fa02ac9cc6679d5507c0c4ab34899 4a9702f24c7f9efa64351c584520cf55f8bfaecd885e839cc47e3b5601325ca3 5ea2731f93008205c3c52a2e4c45ef0848bbe1071ae090cd3a9d7b9fd96fd306 7ce2b584bbac53f871b56f80ee9d17508712a0ecf64919045102d784adf8f7e9 7f836c438ac1da1cb625df75302eea31aaf136d51db79757060adb5cc0859dde 804891c67f42b39ecf4e388b925b172f4f3a9a25e03e07a87368cf6fcbedf017 b1667c3d39402772e4981081ed31115976e99a0b7d420c5faf47c5d66efb70e3 cb9f0d60960a2548b84aa50cc9828548f37fa91c395395ad394db0cfac45ad39
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK