Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Dec. 9 and Dec. 16. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
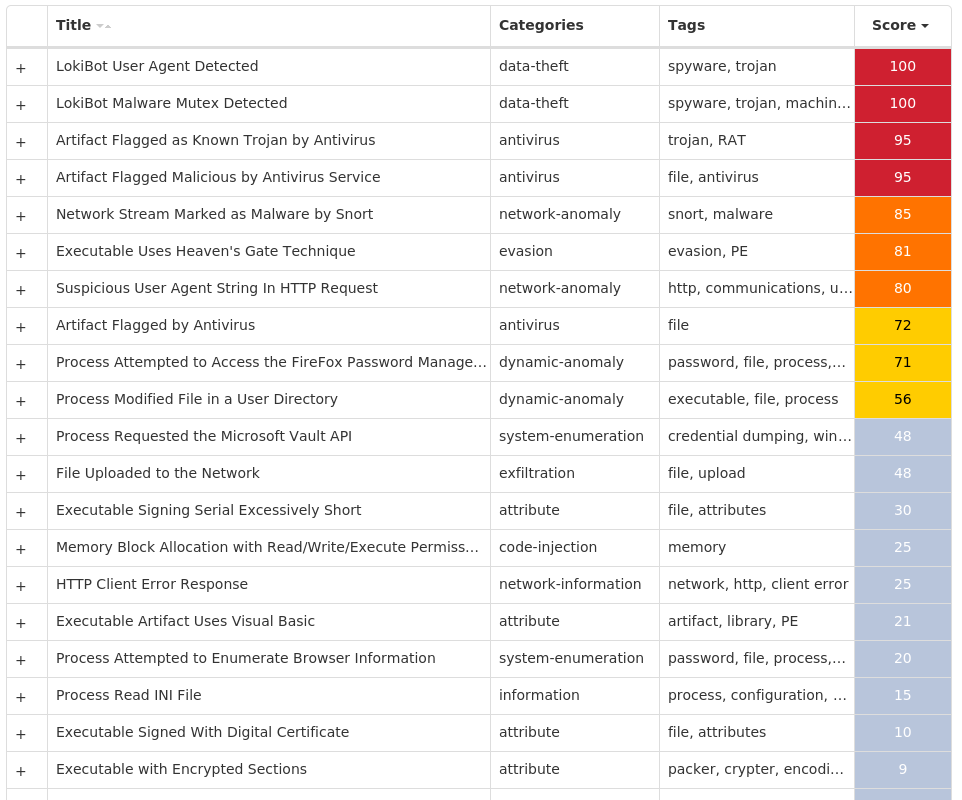
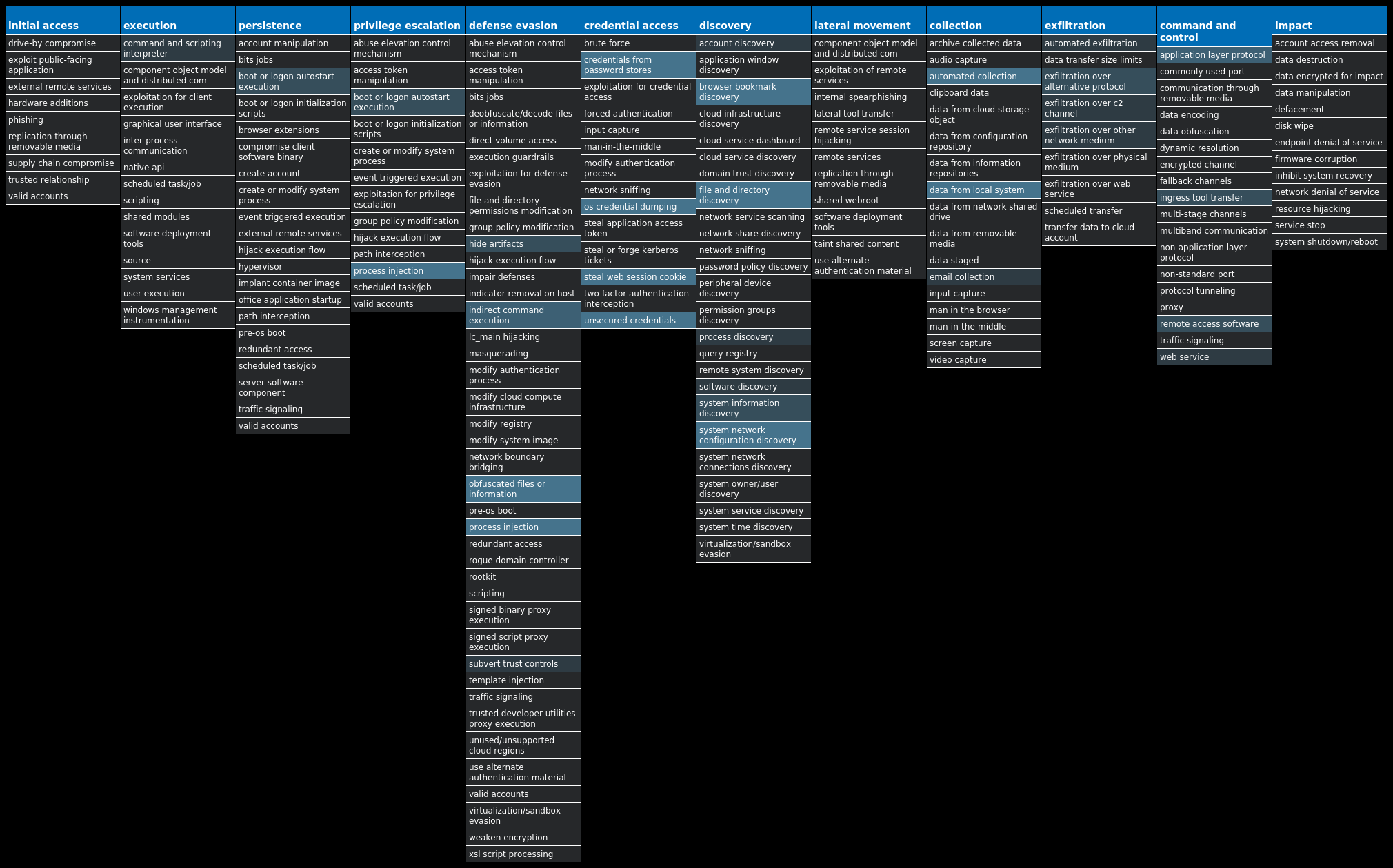
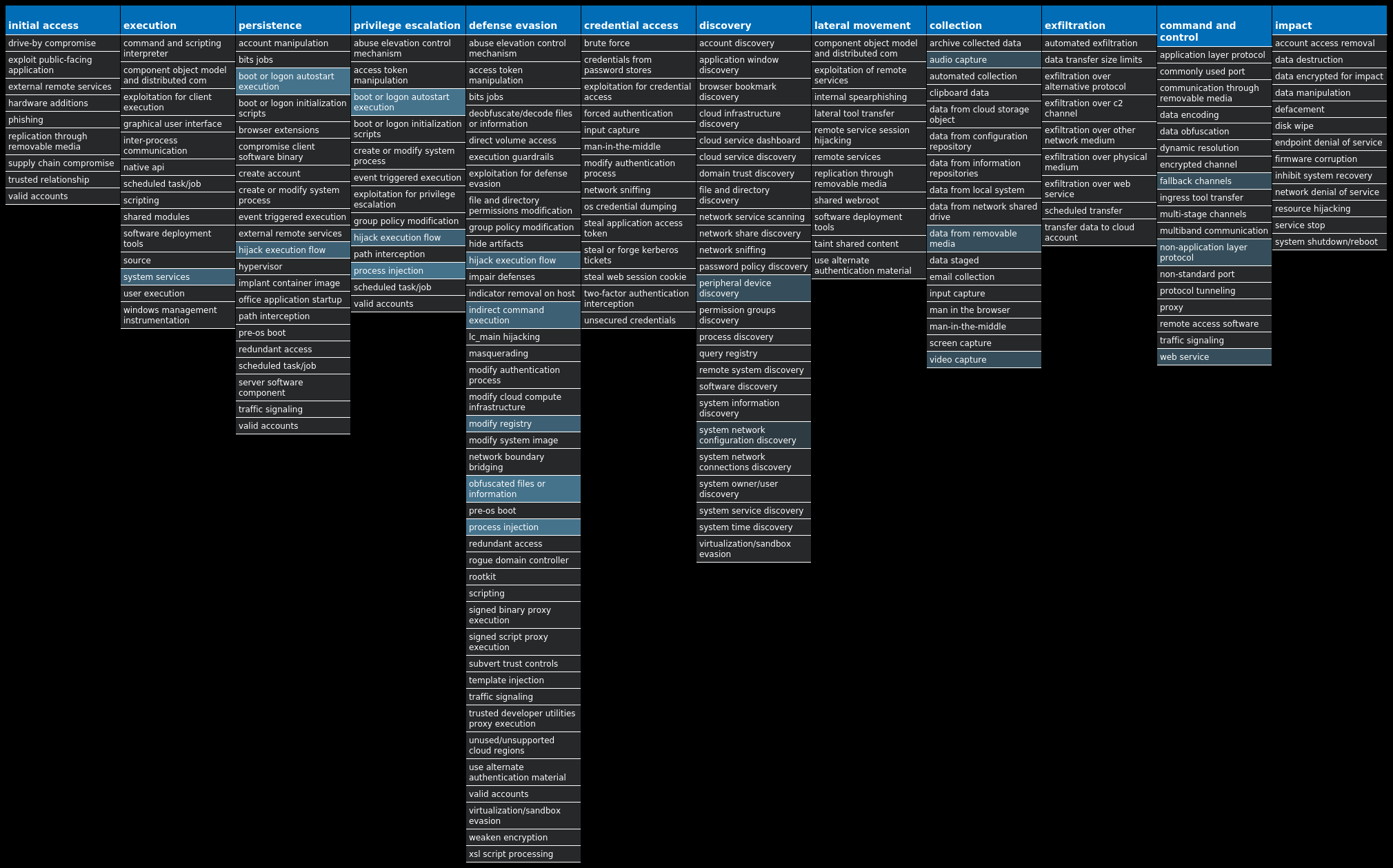
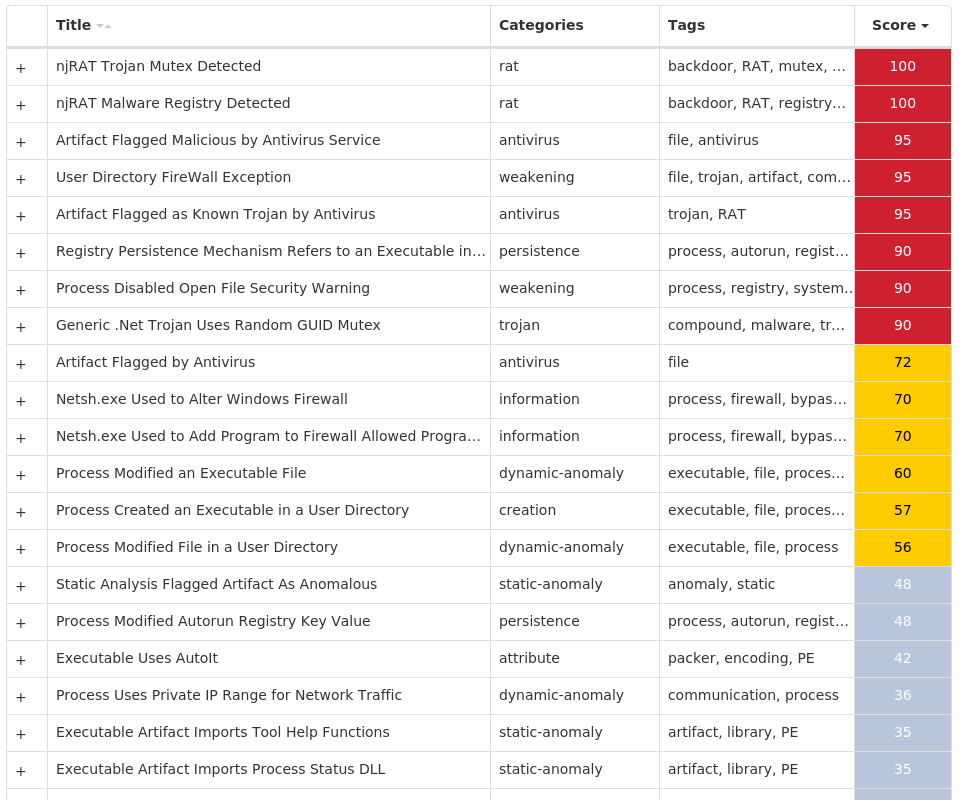
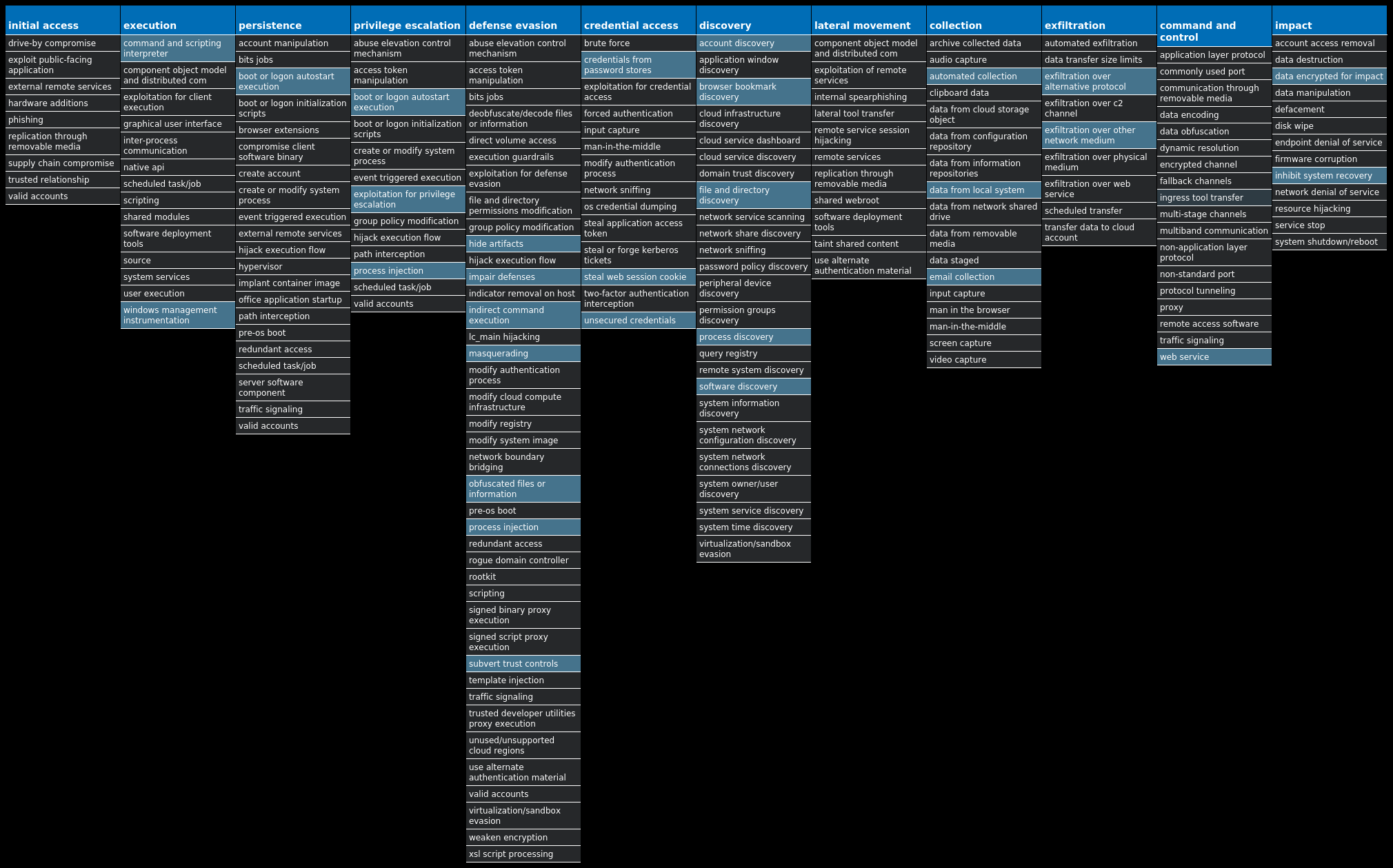
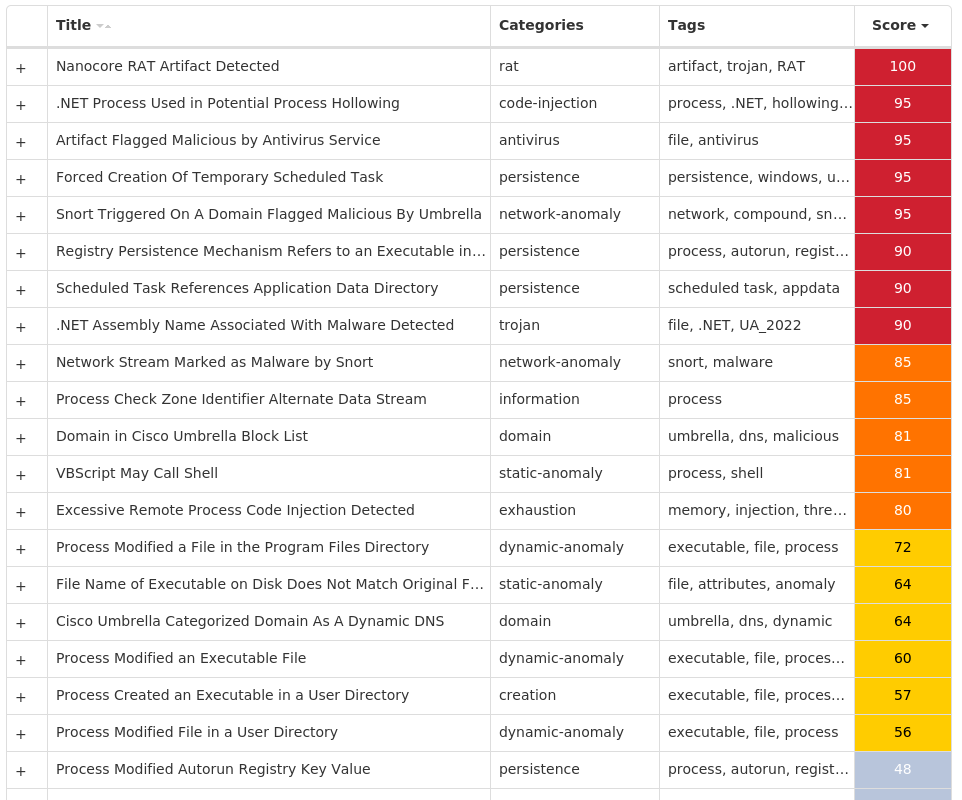
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.Lokibot-9980537-1 Dropper Lokibot is an information-stealing malware designed to siphon off sensitive information stored on an infected device. It is modular in nature, supporting the ability to steal sensitive information from a number of popular applications. It is commonly pushed via malicious documents delivered via spam emails. Win.Packed.Upatre-9980519-1 Packed Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware. Win.Dropper.Gh0stRAT-9980455-1 Dropper Gh0stRAT is a well-known family of remote access trojans designed to provide an attacker with complete control over an infected system. Capabilities include monitoring keystrokes, collecting video footage from the webcam, and uploading/executing follow-on malware. The source code for Gh0stRAT has been publicly available on the Internet for years, significantly lowering the barrier for actors to modify and reuse the code in new attacks. Win.Dropper.njRAT-9980427-0 Dropper njRAT, also known as Bladabindi, is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes and remotely turn on the victim's webcam and microphone. njRAT was developed by the Sparclyheason group. Some of the largest attacks using this malware date back to 2014. Win.Ransomware.TeslaCrypt-9980413-0 Ransomware TeslaCrypt is a well-known ransomware family that encrypts a user's files with strong encryption and demands Bitcoin in exchange for a file decryption service. A flaw in the encryption algorithm was discovered that allowed files to be decrypted without paying the ransomware, and eventually, the malware developers released the master key allowing all encrypted files to be recovered easily. Win.Ransomware.Cerber-9980410-0 Ransomware Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns other file extensions are used. Win.Dropper.Nanocore-9980555-0 Dropper Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes. Win.Dropper.HawkEye-9980407-0 Dropper Hawkeye is an information stealing malware that specifically targets usernames and passwords stored by web browsers and mail clients on an infected machine. It is commonly spread via email and can also propagate through removable media.
Threat Breakdown Win.Dropper.Lokibot-9980537-1 Indicators of Compromise IOCs collected from dynamic analysis of 21 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED Value Name: Hidden 6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Update 6 <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Registry Key Name 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: WORD 1
Mutexes Occurrences 3749282D282E1E80C56CAE5A12 Global\<random guid>5 d19ab989-a35f-4710-83df-7b2db7efe7c5{846ee340-7039-11de-9d20-806e6f6e6963}1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]16[.]154[.]364 104[.]16[.]155[.]362 172[.]105[.]103[.]2072 81[.]92[.]202[.]1361 81[.]17[.]18[.]1981 208[.]95[.]112[.]11 89[.]249[.]66[.]531 81[.]17[.]29[.]1471 3[.]232[.]63[.]711
Domain Names contacted by malware. Does not indicate maliciousness Occurrences whatismyipaddress[.]com6 optimurn[.]host3 thammyvienanthea[.]com2 changdeacorp[.]com2 ip-api[.]com1 checkip[.]amazonaws[.]com1 rikolexx[.]com1 hooklinez[.]us1 smtp[.]easterncarqo[.]co[.]in1 mytradecrypto[.]ug1 www[.]forgivers2019[.]tk1
Files and or directories created Occurrences %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c512 %APPDATA%\D282E110 %APPDATA%\D282E1\1E80C5.lck10 %APPDATA%\pid.txt6 %APPDATA%\pidloc.txt6 %APPDATA%\WindowsUpdate.exe6 %TEMP%\holdermail.txt2 %System32%\drivers\etc\hosts1 %TEMP%\subfolder1 %ProgramData%1 %TEMP%\holderwb.txt1 %TEMP%\subfolder\chop.exe1 %TEMP%\subfolder\chop.vbs1 %ProgramData%\B21QM0NIFTICFK3T1SLF1 %ProgramData%\B21QM0NIFTICFK3T1SLF\US_d19ab989-a35f-4710-83df-7b2db7efe7c58659815602.zip1 %ProgramData%\B21QM0NIFTICFK3T1SLF\files1 %ProgramData%\B21QM0NIFTICFK3T1SLF\files\Soft1 %ProgramData%\B21QM0NIFTICFK3T1SLF\files\Soft\Authy1 %ProgramData%\B21QM0NIFTICFK3T1SLF\files\information.txt1 %ProgramData%\B21QM0NIFTICFK3T1SLF\files\outlook.txt1 %ProgramData%\B21QM0NIFTICFK3T1SLF\files\passwords.txt1 %TEMP%\OFFICE1 %TEMP%\OFFICE\WORD.exe1 %TEMP%\OFFICE\WORD.vbs1
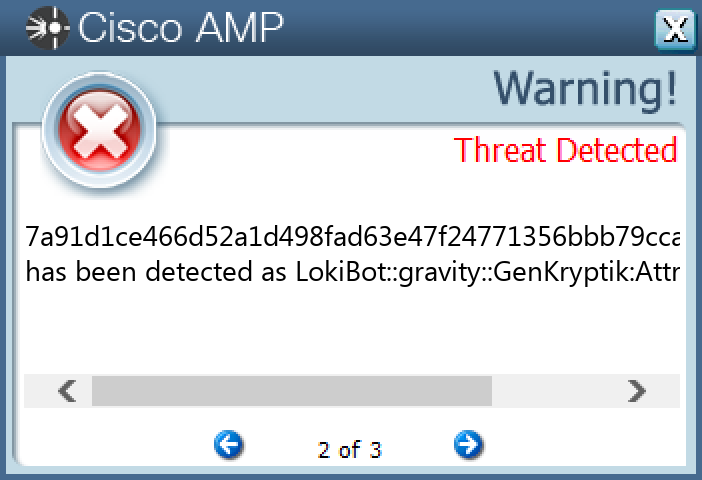
File Hashes 00eb04840db63230036691b00cacffe5567aadd6b229d17393fc8c719cf48dab05b6a0c3ab87724b04839a99ed6e25b3325df807106ebc7ce9066a4c77fe326f1182fc97b4bbff5c4e196604c56c432dbfd21333a298456429abf24c96c2b584353dbb46d2a041ec26b1b56c51166bf733de21550ef8dcba55d03705713d579147f5e1a9b0b645de6a2c17f817e3563c2aa2b2a2d1c2eb7fa266503d1871ccf453e152a481cd7982ebe8e8e75a9c075f220262dfced375704e2ca22dfb3e7c8761bdf6a8fda9449af2d057b6f6c11487c5ca41389f19ecc1dfa809f4cb4bdc336c30fa3b8b0ab3bc9c9311d3af030214806b1e5acb04cebdb3a559e4e7bf11b37385eb0f72f1aa66592d330fc64ed2d850c97abbf67d9e61206e29e646d2032f7a91d1ce466d52a1d498fad63e47f24771356bbb79cca25bd585026d78ead8077ce3ee2f73f5a31415b558e28a46c05817ae82fb6e58b381d7d0d3a5eec2f2938009a2d6798bde4245567a8472beb123edfb5631c13f1d8e6ec62ef0ff20c6178e9a4886218312983692cd92e8fc24cea285604b1ad4e933dbd572f8feb4a8d8a29a76409e778370383c89c0b69ce5291664268e9a65c3a7d3274a5a49398179a86c38bebebc72b6749ad50c370c738a83fe3799a1c0357c14099d0e1275750caa1e0983c213de92652f85e8ba2f5f0d8a8cd7ceb395981495ba1762917dfa33aa7079829cb7eaa96ef06d420f44ff2a834233ff9534c5dc8d4d04671b873a59b82e08212cee722bc2d004a001523a97572823e1be786e0dc596bed10d52a8fdc0b402a4f08b7d9a40d478350300d15c71de3da80c65d21e046a30ce37a459e3d4b206b6dff3baf8ead3fb174e80025d8f84edb4787813d0e704147097596c1bf9a5b6cf55cfdf80c976902388c26e62bbf622cd3434baa49dff92ffca8f6a58
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
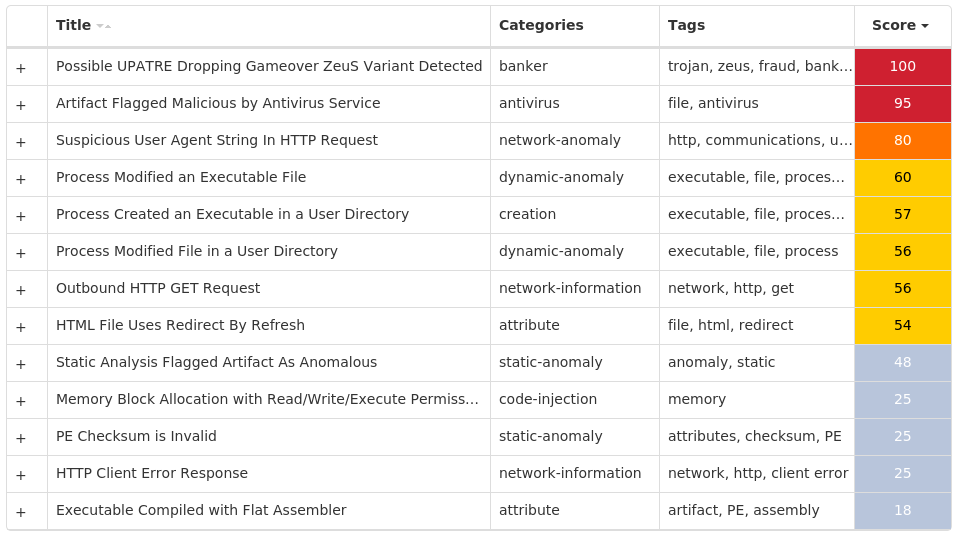
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Packed.Upatre-9980519-1 Indicators of Compromise IOCs collected from dynamic analysis of 20 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 34[.]102[.]136[.]18020 3[.]64[.]163[.]5020
Domain Names contacted by malware. Does not indicate maliciousness Occurrences waytoloans[.]com20 thevelvetpouch[.]com20
Files and or directories created Occurrences %TEMP%\foxupdater.exe20
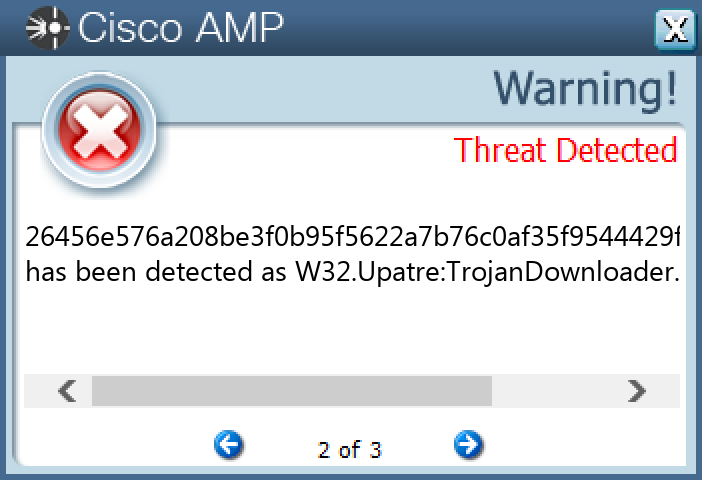
File Hashes 1ee828baaa452d0318a1badef9d56f8a8ee05d3599c9f6c8dcb54ae322a392fd25e06d5c6183431c27c5fb676df9299536afb875ed0f1c40b0971fa18dd4e89526456e576a208be3f0b95f5622a7b76c0af35f9544429fe1c358365db49be4e92ff4fa86d4572329e55dcf36c8b652f0eb54a036d78992f6ea989f9815a7ce1a431ab948d4c702eb811be5a32453a6a0257ad2721db88e5b1b09c5817e8786fc486ddd85daaaca6fce26f5be2ae7eb6e4cf84356bfcda16e1be69419a5f1711d4f897c309f9776ecd32c026fd95730f3d800e75d66e2a2c7316e87b18a0fde005bb31cd6bc300b99aa3ffd75669c0d5db8e72ee5e92fd4da1a142bf6d535ecb85bcb2180f9b47d6d47f3a34329abc443f2d3bda89bd473f99d1c9442281abc3a73ad9dbc8c06b67f3243d07694d080303b866df802240d107901405ae555e83d80641c380f6576daac3a5ed7365d4f244fdc78f2fbb3a4654b56deffbaf29a3d827590683047f223dad8f70661d8255f02f59c6153fb18d1e1d1e01347e4635886fd57bf637914755e2a5465ebc731bc7592beaf8e9431e0e58242e292ae1bcd897b7276724d6dcf490700bc2e0c8bcdc6c9d7b81cb129bcb0a964512ffa65f993ed23c90e7861a0d49b1dbf371a621552736c13a3cb9f9290aa19359ed05e63946d53247eb42ce346e399862371d235b997fd565b8823d39f82fa8c7788a85bd0c38e46f3903b1533741dfbb981944f4d10c7e273c6d3df8ba5b873ec7ed821dd3c60ded429342847acaa695775b8a12aa0e68a21e7de7405c0921ec19bb9e7e7edf096e5b0f47505a82e3224c9238305570075a7c1f270abf0762cf8149f47e95635e780e83bdcc9b067d3deac612bcabcc9fdb870730cddeddd3f34c90d68
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
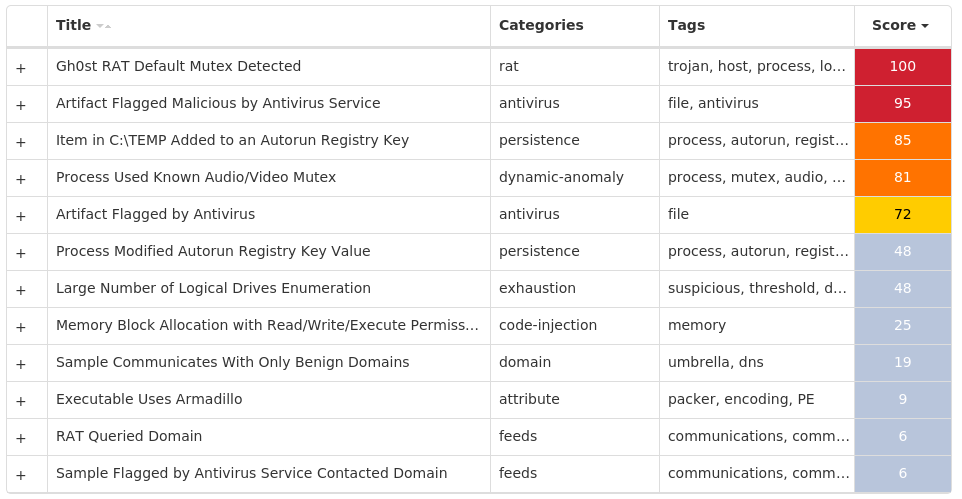
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Gh0stRAT-9980455-1 Indicators of Compromise IOCs collected from dynamic analysis of 15 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'>7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: Type 7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: Start 7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: ErrorControl 7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: ImagePath 7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: DisplayName 7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: WOW64 7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: ObjectName 7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: Description 7 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\RS<random, matching '[A-Z]{4} [A-Z]{8}'> Value Name: FailureActions 7 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN4 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSKSIG WCUGIQYA1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSGAQA MIWWEAEK1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSKSIG WCUGIQYA Value Name: ConnectGroup 1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSKSIG WCUGIQYA Value Name: MarkTime 1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSGAQA MIWWEAEK Value Name: ConnectGroup 1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSRCPV RFBCWOYQ1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSRCPV RFBCWOYQ Value Name: ConnectGroup 1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSGAQA MIWWEAEK Value Name: MarkTime 1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSRCPV RFBCWOYQ Value Name: MarkTime 1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSDETK YARSERIW1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSDETK YARSERIW Value Name: ConnectGroup 1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSDETK YARSERIW Value Name: MarkTime 1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSTEZX RZPQCQUK1 <HKLM>\SYSTEM\CONTROLSET001\CONTROL\RSTEZX RZPQCQUK Value Name: ConnectGroup 1
Mutexes Occurrences KyUffThOkYwRRtgPP1 127.0.0.1:8888:Rscdxm riifdjka1 171.214.11.140:6666:Rsmwis uuasausu1 127.0.0.1:8888:Rsrajf bxvuoiyo1 zxjice.e2.luyouxia.net:26000:Rsksig wcugiqya1 127.0.0.1:2022:Rsrcpv rfbcwoyq1 192.168.1.159:2022:Rsdetk yarseriw1 180.76.120.191:8888:Rsgaqa miwweaek1 lcaus786.e2.luyouxia.net:22785:21086:Rstezx rzpqcquk1 111.67.207.155:2024:Rsieyo ysssmucy1 192.168.1.45:80:Rswoae mymisigc1 wbswchrjx.e2.luyouxia.net:28720:Rsdivy soncwnqq1 ovo520.e2.luyouxia.net:20012:Rsqeiw yqkquikq1 chx031x.e2.luyouxia.net:6471:Rsflnl ppdpdwhy1 127.0.0.1:8000:Rsqqss iiqmoqcy1 ikun100.e2.luyouxia.net:28249:Rsghzj kmnmrnla1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 47[.]52[.]162[.]138 124[.]70[.]9[.]1493 123[.]99[.]198[.]2013 43[.]248[.]129[.]492 154[.]19[.]202[.]1861 120[.]26[.]55[.]1791 171[.]214[.]11[.]1401 180[.]76[.]120[.]1911 111[.]67[.]207[.]1551
Domain Names contacted by malware. Does not indicate maliciousness Occurrences guduo[.]xyz8 lqwljs[.]cn2 www[.]bing[.]com1 ikun100[.]e2[.]luyouxia[.]net1 sjlwql[.]top1 zxjice[.]e2[.]luyouxia[.]net1 wbswchrjx[.]e2[.]luyouxia[.]net1 ovo520[.]e2[.]luyouxia[.]net1 chx031x[.]e2[.]luyouxia[.]net1
Files and or directories created Occurrences %ProgramFiles(x86)%\Microsoft1 %ProgramFiles(x86)%\Microsoft\DesktopLayer.exe1 %ProgramFiles(x86)%\Cayeqau.exe1 %ProgramFiles(x86)%\Microsoft\px7B89.tmp1 \TEMP\62c619724cfde20c7571df62d38331b6Srv.exe1 %ProgramFiles(x86)%\Thrnvvd.exe1 %ProgramFiles(x86)%\Ygkuwmk.exe1 %ProgramFiles(x86)%\Gkykrps.exe1 %ProgramFiles(x86)%\Bwfjsue.exe1 %ProgramFiles(x86)%\Microsoft Fazazl1 %ProgramFiles(x86)%\Microsoft Fazazl\Vhipcno.bat1 %ProgramFiles(x86)%\Mgucqww.exe1
File Hashes 180ece74b103cdbf59f0a8f37f80d86735e257de0c63748342abc10e8884487723925c212a1511b15601983e61c448f0a81d5ff2400aad2b0dfb2130f83db26d39f7c40cdd521567c481ac4b6b876c2124aadc6068cb7706ea33097524ac4be945789525d5ccc00b4a5148aed0d15e980059525a4ce1ffd1b52f18e9f0606c2762512c22b06a8e3d2ceeff6e8a0acded0d2a45e476c1fda5abdb86704fc71ad66f3817e26b094cc3974970666a756edc4064ed535a347f04e74938a768cf8a2778ca6de2cbde73fd0096e4f14311d439fee3a2f7646b0717a89fa2c14addbcc9905f03f2f3bb2f8138d3f31484a3ccdb462606303fbe93f6b9e161f329a0caa996d6db813da96f1508ff61080d630ae46408cc609ab7c3a40be628149325c11c973c166822b4fb42e5f786842712f9688f34c2f6895d6a93e2fe926e39d1e183a265cf3a258b2af0b0e136f08569ebdf2ccd3f34513ed600d07accf8c270529bba771c968b5a7f61320d6393753544ea54c4caf47204335ac805016e5dcbec49bad7e73891556abd526f9cf32e4b2e961d2c8b911624c43158e6e641d8fdd093be79cac4f5fdef9437562409d9c4a37c985c3f9010f601efbbfe92d90c95e45af7f3f418df156e1a6d1ee27d611baf7d77b64f9ce309cb1cfd0052ead9542b0b
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
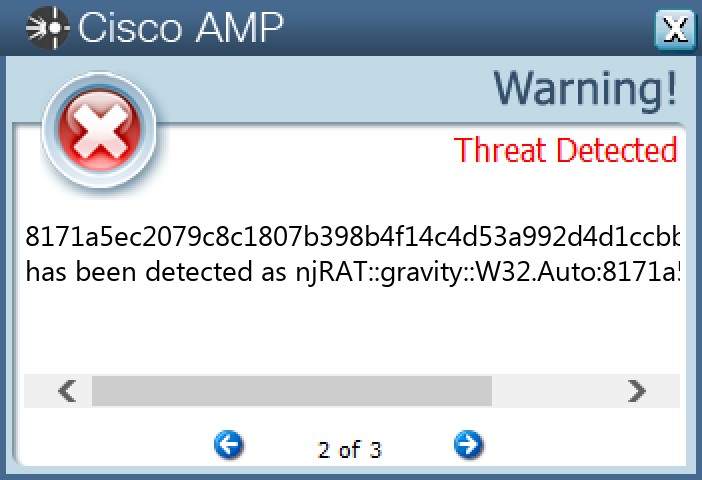
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.njRAT-9980427-0 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLUA 10 <HKU>\S-1-5-21-2580483871-590521980-3826313501-500 Value Name: di 10 <HKCU>\ENVIRONMENT Value Name: SEE_MASK_NOZONECHECKS 10 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: ConsentPromptBehaviorAdmin 10 <HKCU>\SOFTWARE\7657C14284185FBD3FB108B43C7467BA9 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 7657c14284185fbd3fb108b43c7467ba 9 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: 7657c14284185fbd3fb108b43c7467ba 9 <HKCU>\SOFTWARE\7657C14284185FBD3FB108B43C7467BA Value Name: [kl] 9 <HKCU>\SOFTWARE\A12F2B7635CAFFDE3957A7CC18CDE5A91 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: a12f2b7635caffde3957a7cc18cde5a9 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: a12f2b7635caffde3957a7cc18cde5a9 1 <HKCU>\SOFTWARE\A12F2B7635CAFFDE3957A7CC18CDE5A9 Value Name: [kl] 1
Mutexes Occurrences 7657c14284185fbd3fb108b43c7467ba9 a12f2b7635caffde3957a7cc18cde5a91
Files and or directories created Occurrences %TEMP%\server.exe10 %TEMP%\<random, matching [A-F0-9]{3,4}>10 %TEMP%\4108\4108.exe1 %TEMP%\3355\3355.exe1 %TEMP%\5654\5654.exe1 %TEMP%\700\700.exe1 %TEMP%\5102\5102.exe1 %TEMP%\3539\3539.exe1 %TEMP%\6788\6788.exe1 %TEMP%\3217\3217.exe1 %TEMP%\5426\5426.exe1 %TEMP%\377\377.exe1
File Hashes 027d80d4aef687ad5bcf965536b177137c0fc012b62e29dc247b315163beaef6078cc1681e4c0cb4d0f61091390d81527c9748ec45a9f98118b3fe97051220b7166b08c9b00a86bb21418bd00d3e9c445fb99ca32d14fde2c69a25082c6d7e5a3220271f4c7423c530db8a7c1c9714c6f1fad1be0b803c48ca5514c77583f0c767b37834e66be76fb637be3ce10edbc02dc8067a7fbd7570a27d8d47c1b8c0177eccbc3ead189e38be91f2838c4e8954455563a2c63e19d75558e8791619abf18171a5ec2079c8c1807b398b4f14c4d53a992d4d1ccbbbbf1d8ee60c1a51dbed88f06b89e9e53160a944ab25a30d2f59a82807303a34767ae6c81714d067640d8a72076cdb3cd82e07eca1a4282d46eb99515ee08400285a22dabcd88eab2e84e774c8e0fab651c62ee5f0aea84759cc83065afa144ee39013fbee749d209904
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
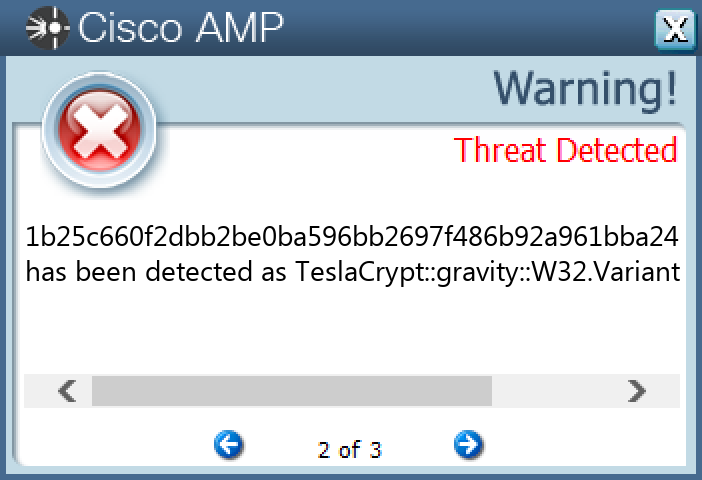
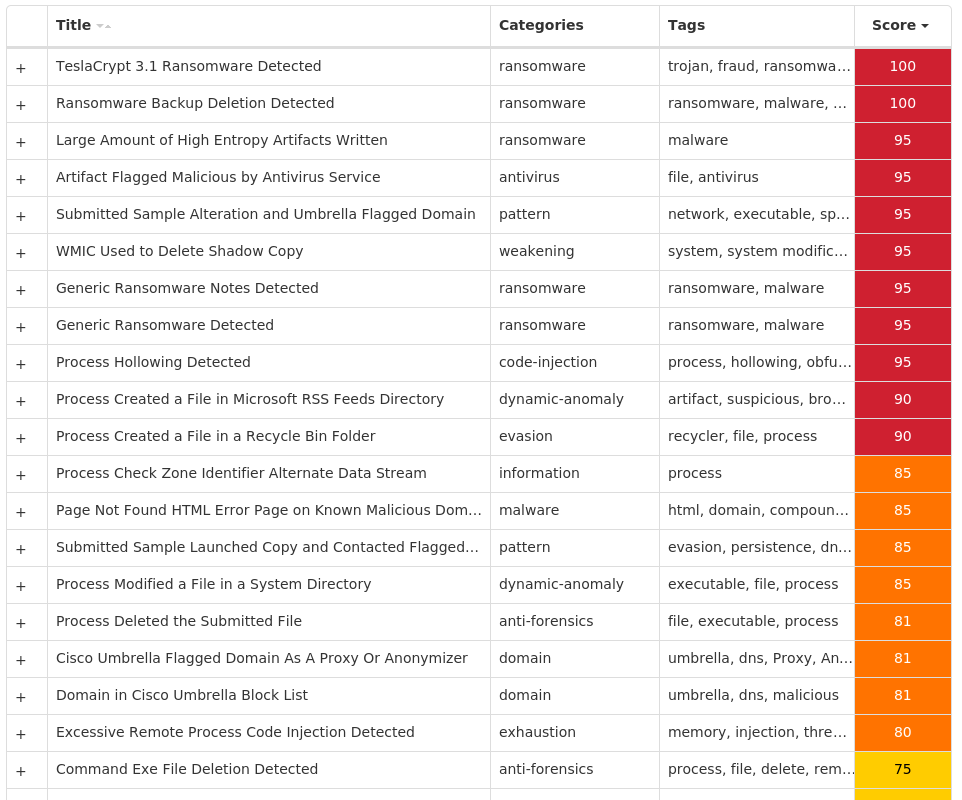
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.TeslaCrypt-9980413-0 Indicators of Compromise IOCs collected from dynamic analysis of 16 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLinkedConnections 16 <HKCU>\SOFTWARE\XXXSYS16 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.CHECK.0 Value Name: CheckSetting 16 <HKCU>\SOFTWARE\XXXSYS Value Name: ID 16 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'>16 <HKCU>\Software\<random, matching '[A-Z0-9]{14,16}'> Value Name: data 16 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: nljubyedlnab 2 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: tdwkvyomimyb 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hrajdeafhsjv 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: deafhsjvbsfl 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: lbkguwsbtylb 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: fkrqlfvsauct 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hexececgsnlj 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: rbdybcshwwth 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: fjklmqygvwoa 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: krqlfvsauctw 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: xvblbkguwsbt 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: hqijwghjvpgt 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: veeqiqypcbef 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: croscewyhlyq 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: qiqypcbefwpf 1
Mutexes Occurrences ityeofm9234-2342316
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 110[.]45[.]144[.]17316 50[.]87[.]147[.]7316 35[.]205[.]61[.]6716 2[.]57[.]138[.]4715 3[.]33[.]152[.]1479 15[.]197[.]142[.]1737
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ikstrade[.]co[.]kr16 lutheranph[.]com16 salesandmarketing101[.]net16 salaeigroup[.]com16 dustywinslow[.]com15 lovemydress[.]pl15
Files and or directories created Occurrences %ProgramFiles%\7-Zip\Lang\lv.txt16 %ProgramFiles%\7-Zip\Lang\mk.txt16 %ProgramFiles%\7-Zip\Lang\mn.txt16 %ProgramFiles%\7-Zip\Lang\mng.txt16 %ProgramFiles%\7-Zip\Lang\mng2.txt16 %ProgramFiles%\7-Zip\Lang\mr.txt16 %ProgramFiles%\7-Zip\Lang\ms.txt16 %ProgramFiles%\7-Zip\Lang\nb.txt16 %ProgramFiles%\7-Zip\Lang\ne.txt16 %ProgramFiles%\7-Zip\Lang\nl.txt16 %ProgramFiles%\7-Zip\Lang\nn.txt16 %ProgramFiles%\7-Zip\Lang\pa-in.txt16 %ProgramFiles%\7-Zip\Lang\pl.txt16 %ProgramFiles%\7-Zip\Lang\ps.txt16 %ProgramFiles%\7-Zip\Lang\pt-br.txt16 %ProgramFiles%\7-Zip\Lang\pt.txt16 %ProgramFiles%\7-Zip\Lang\ro.txt16 %ProgramFiles%\7-Zip\Lang\ru.txt16 %ProgramFiles%\7-Zip\Lang\sa.txt16 %ProgramFiles%\7-Zip\Lang\si.txt16 %ProgramFiles%\7-Zip\Lang\sk.txt16 %ProgramFiles%\7-Zip\Lang\sl.txt16 %ProgramFiles%\7-Zip\Lang\sq.txt16 %ProgramFiles%\7-Zip\Lang\sr-spc.txt16 %ProgramFiles%\7-Zip\Lang\sr-spl.txt16
*See JSON for more IOCs
File Hashes 152d8dfacdec0ebe7008b0ec41f110111209a69bda12c7e011ea824544479e101b25c660f2dbb2be0ba596bb2697f486b92a961bba24226aeb82d8f0ac2f8d47324b40debcda6f4b9795a3880ff35b56a92d865abb7c3525f6b40e28c52d95945063d5e6f90dbb6e360259ac24c11c62b1439f90966bdc72dedf60e243b9e87a521294a88093ea2b7a2b89ec3005b6398f20780874d410663b63429e58b1555a66e3b4babf44c3168e1524e84dafd4f19bbfd25feff600422f18553c0dc9c75d7dc78a81de59dc3f666c25c6d10ae730b50d6d2ee341088371f92f137a9385309c4498d0ed0c9941d61fed83e91942b40ac298b12acfccaeb9d84526103ff4c8a4cecd9cad126bbb98545d8bdb471fd1971187945eb71e5ccb873e90a84ee7aead3a9d7402d494048c934b5af612bdf8da822fa7b22e57b8fe48e98a92f772b8cd07e3707ed997f08cea9f73113be57561dd3d6286310fd096904deb8fc465c7d27df86a574f9e5e3f6b0a6ffd180da3c8d46e3ee94ea65eff4d1e782be9a915e302839fbcbdc6da9e8235013a8abce6425eba48eaf4dac3390360334ebe756eea3d4eae7eea6f718c8d6999c847f81d046d5a2800f90db40a12c1b2788d630fee10b9a36e59990b0a49cf0044f2f23f4fc0e9f7b56057d74c96d99b0736a584fa22998a51ea7dbbd88a0e1d1c11e88e1c0a801125d2e330348323987d00ccaa
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
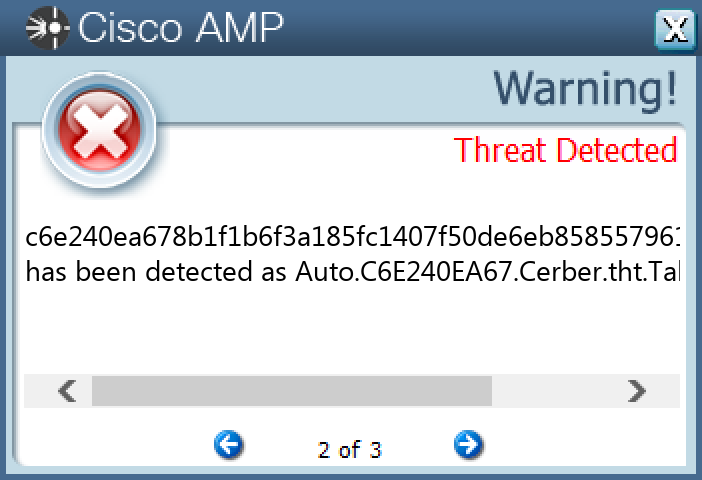
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Ransomware.Cerber-9980410-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 25
Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}25 Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!16613a825
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 91[.]119[.]216[.]0/2725 91[.]120[.]216[.]0/2725 91[.]121[.]216[.]0/2225 178[.]128[.]255[.]17916 172[.]66[.]42[.]23813 104[.]20[.]20[.]25110 104[.]20[.]21[.]25110 172[.]67[.]2[.]885 172[.]66[.]41[.]183
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]blockcypher[.]com25 bitaps[.]com16 chain[.]so16 btc[.]blockr[.]io16 p27dokhpz2n7nvgr[.]1lseoi[.]top16 hjhqmbxyinislkkt[.]1j9r76[.]top9
Files and or directories created Occurrences %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c525 %TEMP%\d19ab98925 %TEMP%\d19ab989\4710.tmp25 %TEMP%\d19ab989\a35f.tmp25 %LOCALAPPDATA%\Microsoft\Office\Groove1\System\CSMIPC.dat25 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp25 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.bmp25 <dir>\_HELP_HELP_HELP_<random, matching '[A-F0-9]{4,8}'>_.hta25 <dir>\_HELP_HELP_HELP_<random, matching '[A-F0-9]{4,8}'>_.png25
File Hashes 16ebbbbd2d978523d5a3aab8bd061eb664758aa22450ad965591b0972c1bd1e51fb3c24f7e64a802af37174a49e8fb4a93a65458918552c54c93c5794a852fe220c1fc5368a95da72dcd4260873d0bc3cc5fe7a0a70ead28de3f3925bc27aa322750f0c9766c949e73a28d9be59ec227e476efc81ccbf9a2180c78491324f8b7415fec7c4f2787631477a71a585003391201c8a2f25228fe34f7f14da451607d4b2fbc99af8bee1e7c8d6dfa31c758a464949b072def63379b54698c2bcb029551720195800c617254987a2cd380dd2917fc286b0e60202798fbf4969012b57055375bebf365b8f173a1af478725c273440f5bac83939da9d196a83d564ccf5057397ad4a1cd1f70971dab52e5efa14cdc370489e5672e18ee54b71da88d25ca5a8bfb98f3025a2cd0b432272f7e611914d4bcbaad861afd55e08e5a26c577ba60d04a29b992ed24711d2f240cacc63f34ab48bcf1332ac7b732d3de2edeb26a68e66db7f8cb147a6aa5cbc6b3cb7b0ad6a5569f8eabb662bfecddf9b58bdef173a322b14d0adcd35c2b77e6931f58e28edf2d79de499dffe93e411416930c007cc6160a71803a5e7fc8b01c0fed45b049081ddb3aeac9b1db7ae360f2f20af67d844d2401d7065a005fe109510e2263f60a0bbd11072f1c2e97434b033a4f0f817f0e050402f396b770b3ab4346e0c7ac067d478ccbe57f88277cb9fa07afcb85dfc22a0b450f06b46de29ccef88cab8e4466fa6653bdd3b03f421a0f8ce4da8f9a1c56809d5c7dbcdfe6697fafe81038bd2162956eb442c8978b04e7e6f4c9974b226b88a378aee906e397da4c8b8e849845cdf01b7a7ef1bdef73b1cb37a69f429762c580897cb4a71271725483d7d75bbb6d0840dbbe323140b31b1d2b0dbce7d560358ec4421bd73e2d00259c52866b171181f2a4a12844d4174769b725c6e240ea678b1f1b6f3a185fc1407f50de6eb8585579614ca2ce3731bc8070d3da3567e0f7c091e1707cbbd7909cfd9fe835fb48dcfb9d1efaaec49ebf5a737ddaca60c3f4577bc641c1b25f2bfb220649476db0999e81e3d4d7306069a7d6f6df4d3ff367a2f4d89d40586b8d44102bf1c3de97ab7ccef18c7f43b4993c1be3
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
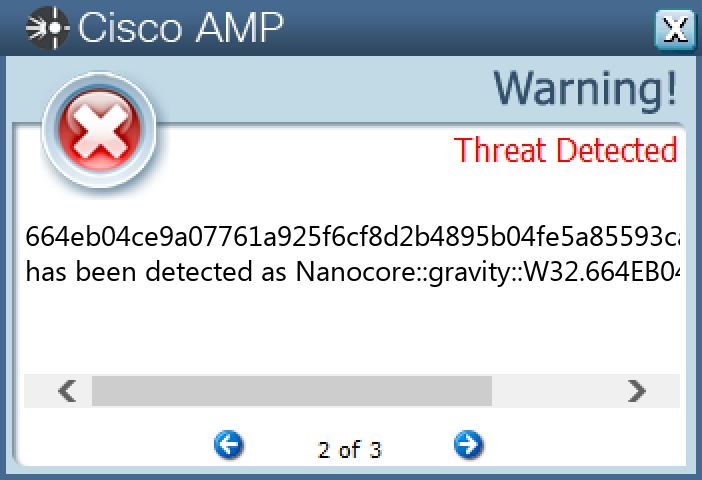
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Nanocore-9980555-0 Indicators of Compromise IOCs collected from dynamic analysis of 47 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7E Value Name: LanguageList 45 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: AutoUpdate 19 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: AGP Manager 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Chrome 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: WindowsUpdate 10 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: DisableTaskMgr 6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: newapp 1 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\INTELLIFORMS\STORAGE21 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX1 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX\20.0.1 (EN-US)\MAIN1 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA THUNDERBIRD1 <HKCU>\SOFTWARE\NETWIRE1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\ENUM1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: 7_64 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: 10_61 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\ENUM Value Name: Implementing 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE Value Name: 6_74 1 <HKCU>\SOFTWARE\RMCW-KMC20U1 <HKCU>\SOFTWARE\RMCW-KMC20U Value Name: exepath 1 <HKCU>\SOFTWARE\RMCW-KMC20U Value Name: licence 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: ddate 1 <HKCU>\SOFTWARE\NETWIRE Value Name: HostId 1 <HKCU>\SOFTWARE\NETWIRE Value Name: Install Date 1
Mutexes Occurrences Global\{042723c4-0804-4212-bf56-4b1b2669ca7c}12 8-3503835SZBFHHZ1 -1 1L2N233BRY01J7GZ1 J1P86SR380H1-G0M1 Global\96f3acc1-6da6-11ed-9660-001517dcb4c81 S-1-5-21-2580483-124424456293441 Global\d6071d80-6d05-11ed-9660-001517fac4b01 KL8ATO734X14Z-LY1 134bd404e63d2b071716d1ceddb584851 Rmcw-KMC20U1 Global\d4f7b8e1-7b75-11ed-9660-001517a920c41
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 192[.]169[.]69[.]2612 194[.]5[.]98[.]21912 162[.]55[.]60[.]28 52[.]20[.]78[.]2403 3[.]232[.]242[.]1703 77[.]88[.]21[.]1582 54[.]91[.]59[.]1992 3[.]220[.]57[.]2242 185[.]209[.]160[.]472 103[.]15[.]48[.]1101 50[.]87[.]253[.]1251 2[.]57[.]90[.]161 34[.]102[.]136[.]1801 79[.]134[.]225[.]161 3[.]18[.]7[.]811 45[.]33[.]6[.]2231 107[.]189[.]4[.]2531 35[.]208[.]225[.]541 156[.]254[.]174[.]1201 85[.]10[.]159[.]41 217[.]21[.]72[.]1101 103[.]79[.]76[.]1521 38[.]48[.]189[.]901 64[.]185[.]227[.]1561 198[.]12[.]91[.]2451
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 411speed[.]duckdns[.]org12 lowaspeed[.]ddnsfree[.]com12 api[.]ipify[.]org11 showip[.]net8 smtp[.]yandex[.]com2 alice2019[.]myftp[.]biz1 www[.]sqlite[.]org1 www[.]aaronmachado[.]com1 www[.]ashakendra[.]org1 www[.]665zzz[.]com1 www[.]njdshl[.]com1 www[.]manciniballroom[.]com1 www[.]cure-finder[.]org1 www[.]cryptopers[.]com1 www[.]teoshotthis[.]com1 www[.]denmarktennessee[.]com1 www[.]positiveenergyart[.]com1 www[.]nicodemusandcrow[.]com1 www[.]pluik[.]com1 mail[.]chabiant[.]az1 mail[.]springhotelhn[.]com1
Files and or directories created Occurrences %HOMEPATH%\temp45 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp24 %TEMP%\RegSvcs.exe19 %ProgramFiles(x86)%\AGP Manager12 %ProgramFiles(x86)%\AGP Manager\agpmgr.exe12 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C512 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs12 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator12 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat12 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\task.dat12 %System32%\Tasks\AGP Manager12 %System32%\Tasks\AGP Manager Task12 %APPDATA%\A1EB383543D3F00657D78 %PUBLIC%\Libraries\vbsqlite3.dll8 %APPDATA%\A1EB383543D3F00657D7\Files7 %APPDATA%\A1EB383543D3F00657D7\Files.zip7 %APPDATA%\A1EB383543D3F00657D7\Files\10_147_20121129071628.RTF7 %APPDATA%\A1EB383543D3F00657D7\Files\127SYLLABUSFA07.PDF7 %APPDATA%\A1EB383543D3F00657D7\Files\13ACX.PDF7 %APPDATA%\A1EB383543D3F00657D7\Files\143.PDF7 %APPDATA%\A1EB383543D3F00657D7\Files\15_DIPLOMSKI2006.RTF7 %APPDATA%\A1EB383543D3F00657D7\Files\167_VAN_OORD_V_THE_PORT_OF_.PDF7 %APPDATA%\A1EB383543D3F00657D7\Files\1_ANKITAMISHRA_ESSAY.DOC7 %APPDATA%\A1EB383543D3F00657D7\Files\2329444014.DOC7 %APPDATA%\A1EB383543D3F00657D7\Files\2590OTHERSUPPORT.DOC7
*See JSON for more IOCs
File Hashes 02d6acf24555c866c6fa3c37b06c8ff3b546a5b8f97e1e8cab2110c29e51c897069e629347920fa169623bf55556bf50da6d73b6d8129da71ed7832e76ec077408f06965c39cb6f46e18f1df24e72e06fea964197174ac839476d3957e4de495171777fc7d1801670cdc576c7cb7460fd4f4ad4eac5d00bc14b3a2f799a56ca2237f4691c8e3937129080c8d1a39e9a33df965f63c90977aab5348606f03ad48275adb18333faf91f3124dc54af4c201c11c8d25ecde94aed6ea5f373517c000356b30df4bbe9a2f99a450769fee9a947f5879868d6b60b183fb3faba39f64703a4ef6610b647f545e862e03d03df7a89b171831fa685a978b9d76dd092244063daa2ea1bfd5b57eabe55cc156a072ea901ff7c809648dd4d7aa6897c7a9bf3c5ab5b8f885449933f394fc287c5d224e7cb1c1e3f6f89d9d0abb812bb7d3d8055c9f6daab90ddba678686ebb3562b200be25bdbc5b8bf997aae9888372df30015e3eb3b01f08a5860eb53b7ef54c51378fbfc21584687d82ce8a0c7bfdf0bf746427b1234b3182b21cfe73e027a9943505033e0ca9c557504051581d77191158649ba0fa2b0d5b7835a732f9f52b2cc8536e730e224817b02218daebd4b0884865202bb1c6bc23e5e4297b0b00b1317a375f08134175e5b7e015a6d829dec596664eb04ce9a07761a925f6cf8d2b4895b04fe5a85593ca0208d995b438c8b5f76763500aabf5bb650acee7e50fb2b28559c25e46e43a67e84e849cfb6748968b690e2244879b7cdddc4b6208c8bcfae41548c1f651dae8fd576e281ddb30381b6a7d82c112ed34aecaf4b3aa622d946ccd5fdfd8141437c8410b7c36e4d4d4b56aa8a7e9eaaad38773e294e1334edd60fa25564999efdbb2e27beddc705cbe3d73f9758f83bfe78bbd7c137f3c2d92f6813e8f97e09a05da42e8897715313ae37b16e2c7b49690e83bb4140b3e0f29418c64a6aae02dc0c324b607ae048b7ebd7c749b55555779c476f8e206751528e729bed0069f7a9b91f7766a78b8c227928034fed4db2081f34b8048bab000a23044d35061868f53cb37a0f9de4951bdaf88c35140b891ab68d50c39cba262f80e48038a90e92f46b685240b07494714a6
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
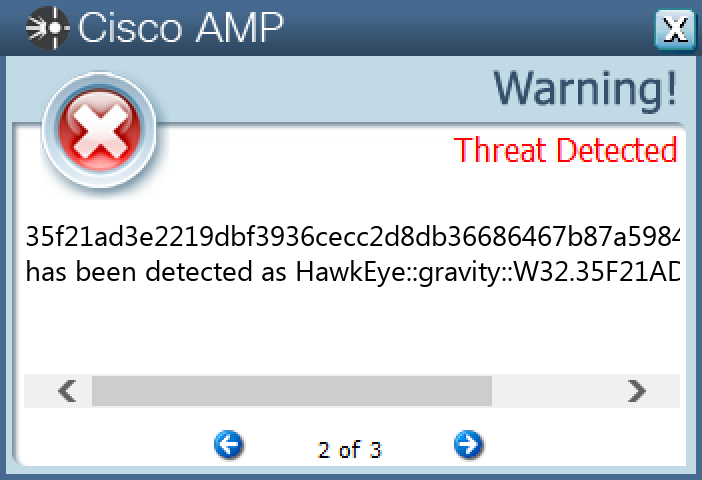
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.HawkEye-9980407-0 Indicators of Compromise IOCs collected from dynamic analysis of 17 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED Value Name: Hidden 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Update 1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]16[.]155[.]361
Domain Names contacted by malware. Does not indicate maliciousness Occurrences whatismyipaddress[.]com1 mail[.]curtisjnr[.]org1
Files and or directories created Occurrences %APPDATA%\pid.txt1 %APPDATA%\pidloc.txt1 %TEMP%\holdermail.txt1 %TEMP%\holderwb.txt1 %APPDATA%\WindowsUpdate.exe1 %APPDATA%\WindowsUpdate.exe\:ZoneIdentifier:$DATA1 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\gykjt.vbs1 %APPDATA%\gykjt1 %APPDATA%\gykjt\hhuyi.exe1 %APPDATA%\gykjt\hhuyi.exe:ZoneIdentifier1
File Hashes 0afc35bdc7a3c309c2d318c17fb022f4cb273b54f0e985214f35d78d2777b0b60da2d12cb707f7dc768729a23151d848f3b55a478c4f5ef2ad291438d7fd88191000dae94027ea5274106454778d70f0bc7763b787cab16a017cd846e76e47a91fb8d035253a9e76f108a7ffddf701cf15949ec012e4c26f0a6ecf67fc0af01c2a19ae94bf110da3cb0c99d67fa313d12f5e4518d1bd2d88b0e8213c9c7e8c2b35f21ad3e2219dbf3936cecc2d8db36686467b87a5984c842a08214f3ab1e3c83abccc8e7db8eb44d8baae4b98675c657901c080c5f79160f9cbe8ed9c3f2a4c42e162ab2cc30abb0197559cd158ed6fc614be33b6e9d1357917356b057f4ca7757d1ccf4061ca76d7b7de49d9124a74738c7835d9df0ad1074c8643da562aa19957b34b6ae296fb384c1a9af0656706b057dfd6f256095a555acaa875a1335aaaa39c2e014b8c48cd156777516987ae3ddde1c5993b47c07e6171e8ffa7733abe0d39b9872aaf2a65ec3ee3dbfae1250384af42af67722bd295f12700e120aac1d04473949f3e1018cf7bdf6117a3bd788c27932a0c304f09364983b96d689dc31306ed75a78889320033bdf936c9d801fd9da3b7cdda4aead41f8c8fbaa14bd2b9c63c6bc5b982cb25afe657fefe121593803e38cb60eb40484b6aed65ce87e34558232611b82301ed2aa168242353b3f079e3e1eb5cf31fe6fee06a6d9174f432a979674be1f744b5392c5034115f9761ecf7001c772d43516bc83e4bffdd
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK