Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Feb. 24 and March 3. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
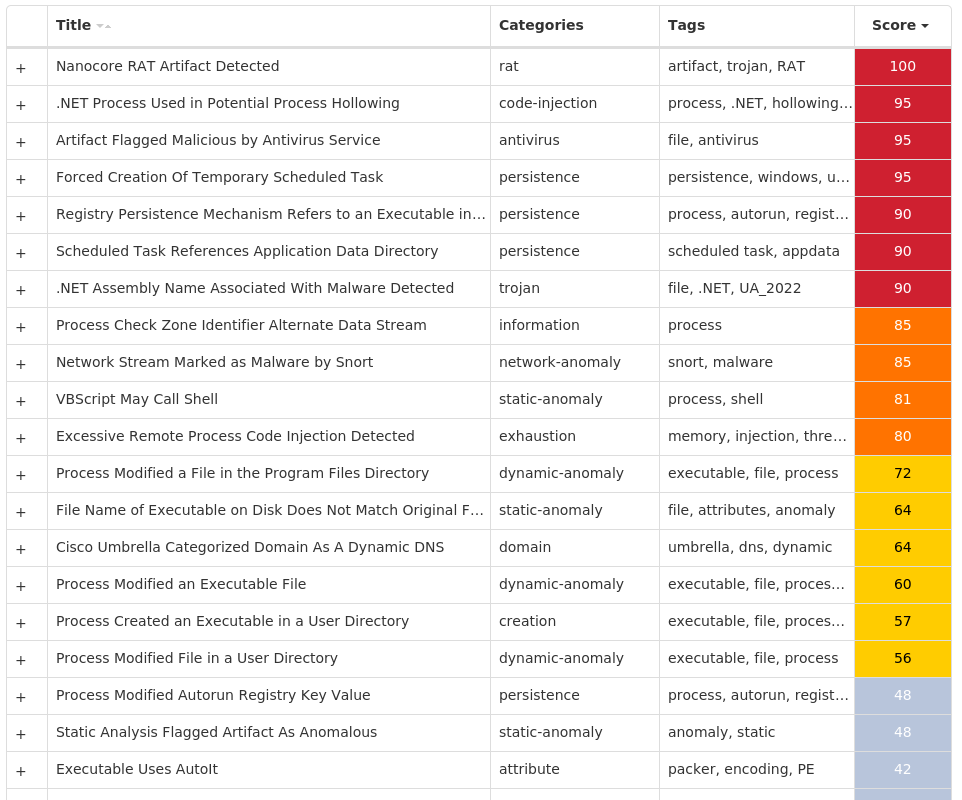
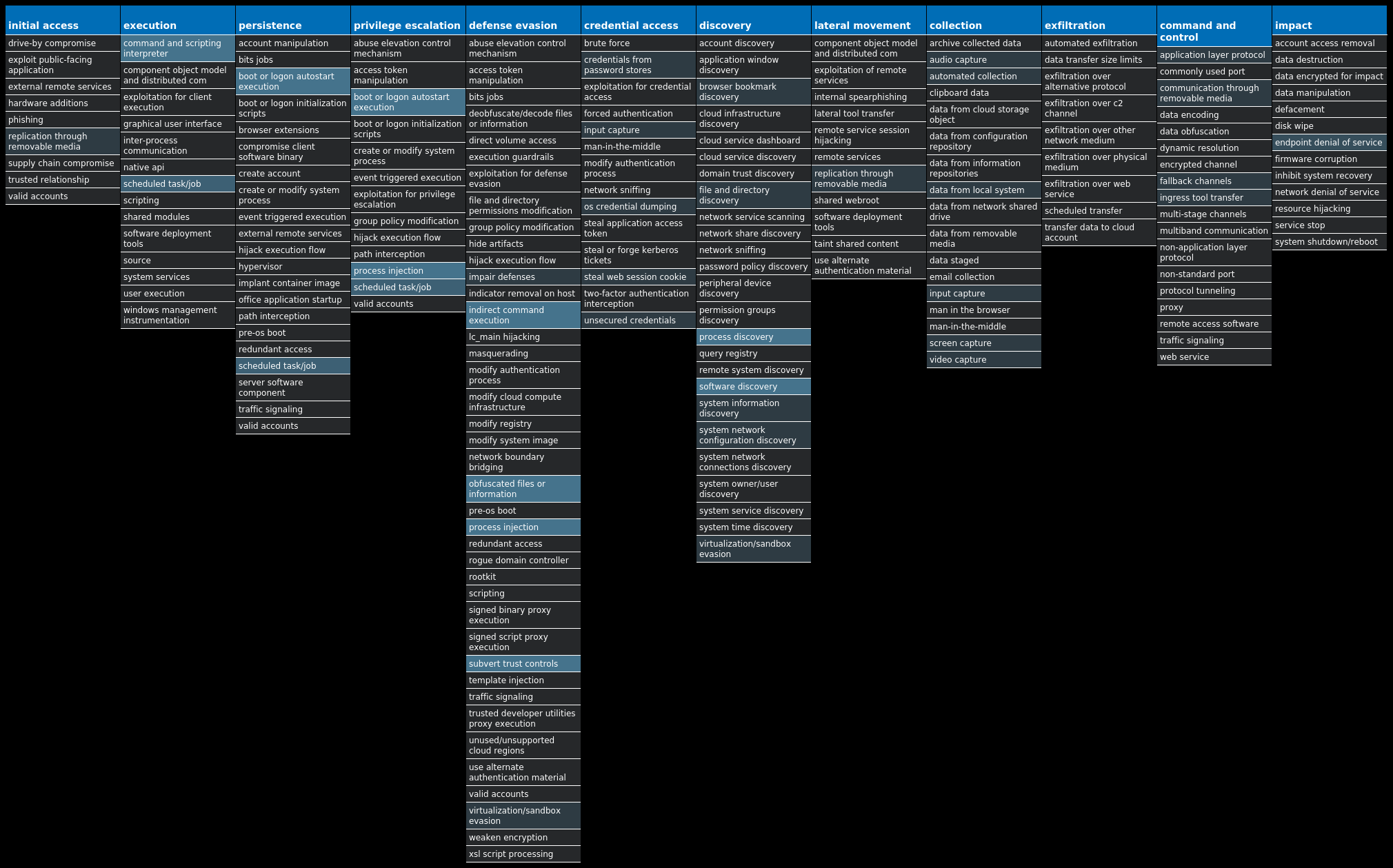
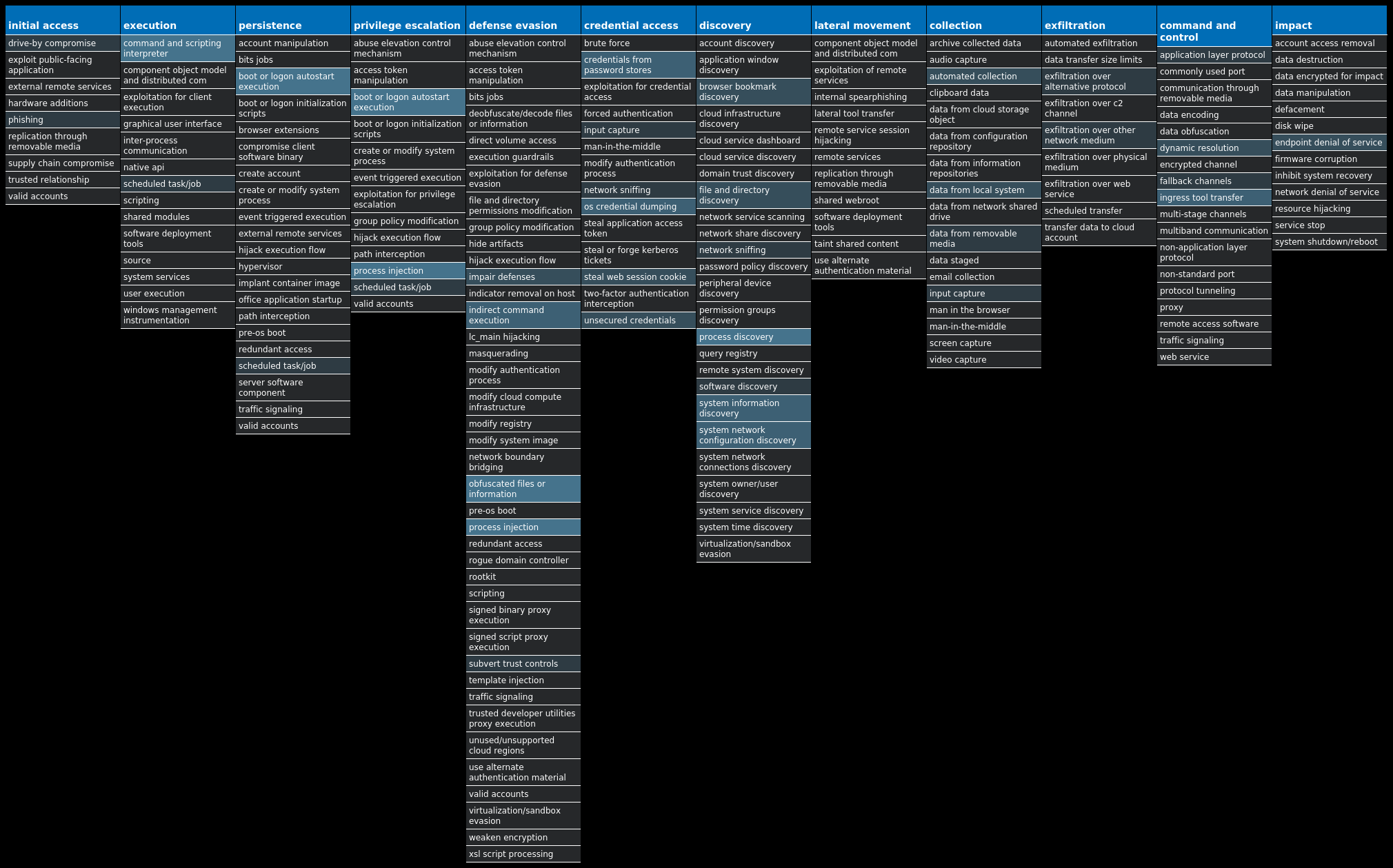
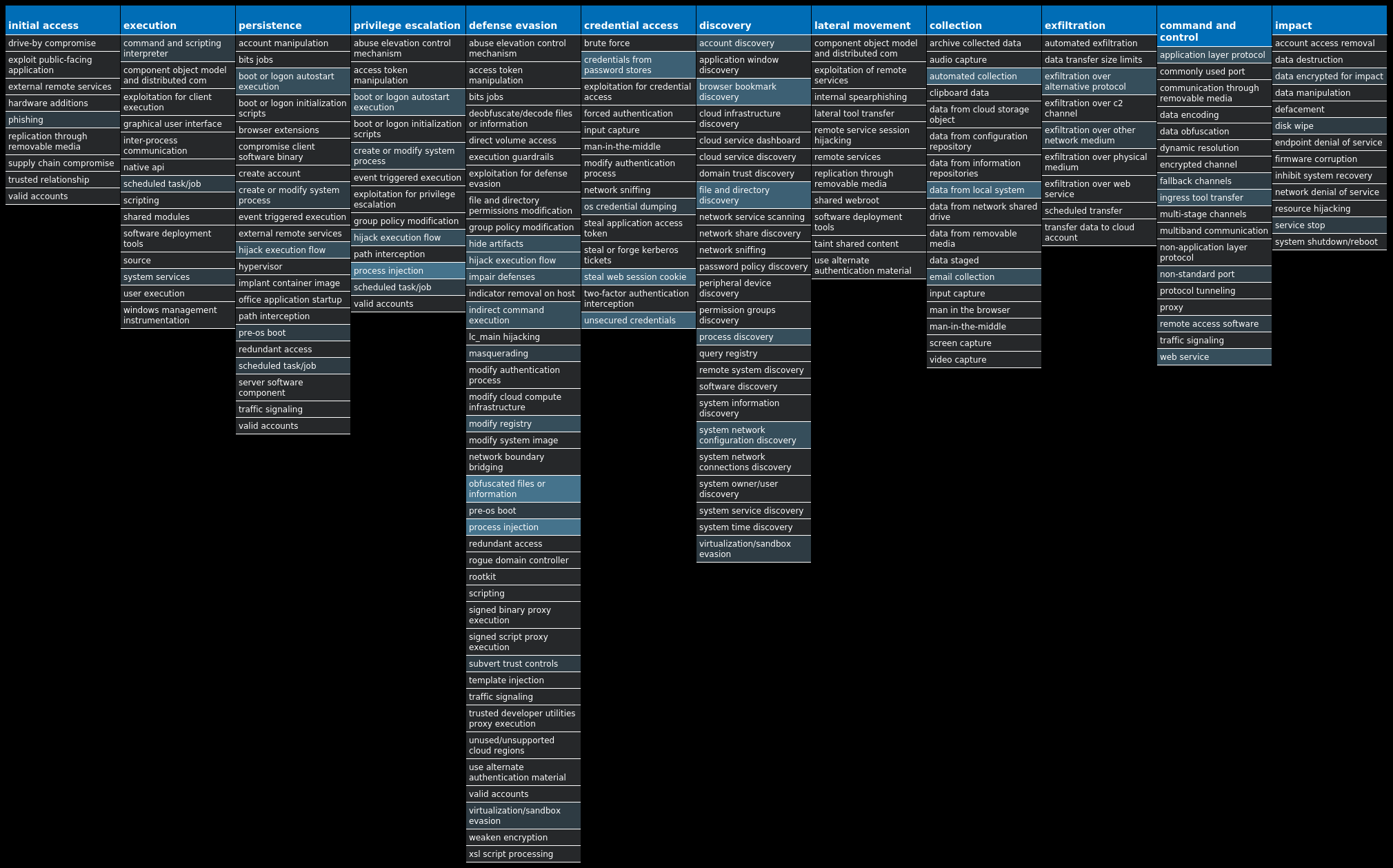
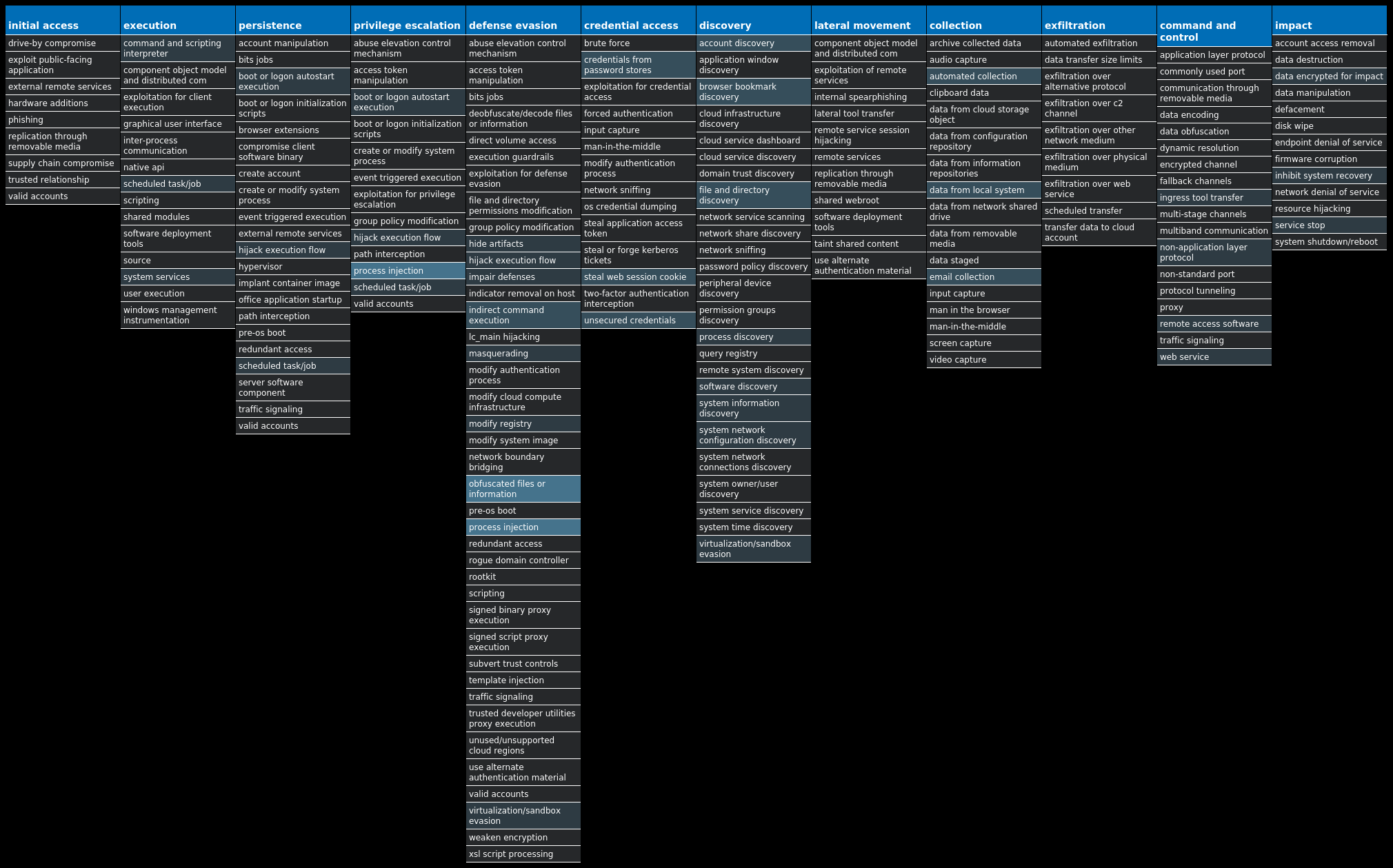
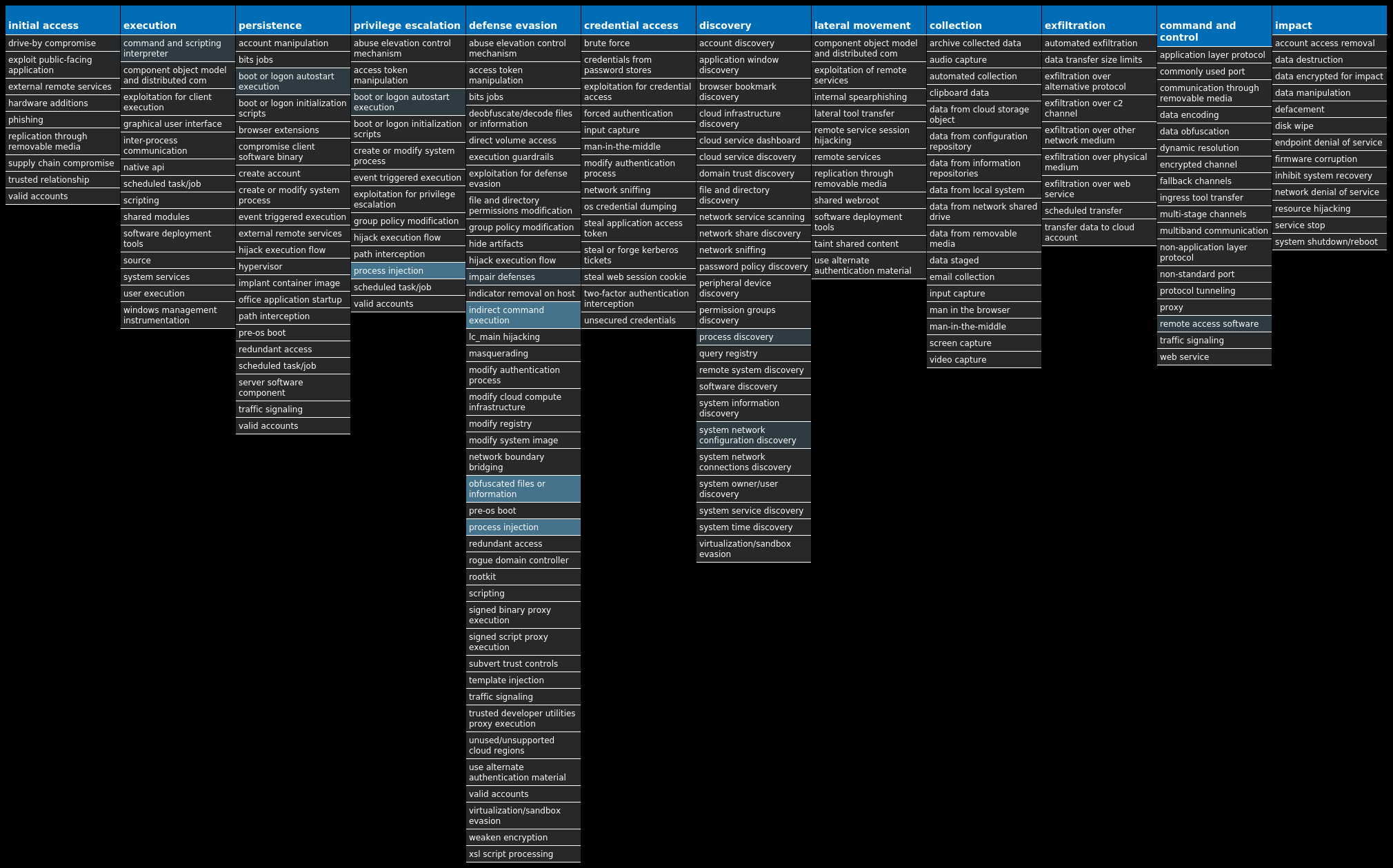
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.Nanocore-9988753-1 Dropper Nanocore is a .NET remote access trojan. Its source code has been leaked several times, making it widely available. Like other RATs, it allows full control of the system, including recording video and audio, stealing passwords, downloading files and recording keystrokes. Win.Dropper.NetWire-9988754-0 Dropper NetWire is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam, remote desktop, and read data from connected USB devices. NetWire is commonly delivered through Microsoft Office documents with macros, sent as attachments on malicious emails. Win.Dropper.Raccoon-9988770-0 Dropper Raccoon is an information-stealer written in C++. It collects system information and a list of installed applications, then steals cookies and autofill form details from various browsers (Chrome, Internet Explorer, Firefox, Waterfox, SeaMonkey and Pale Moon). The malware can also steal credentials from email clients like Outlook, Thunderbird and Foxmail, then scans the infected device for information about valid cryptocurrency wallets. Win.Dropper.LokiBot-9988785-0 Dropper Lokibot is an information-stealing malware designed to siphon sensitive information stored on an infected device. It is modular in nature, supporting the ability to steal sensitive information from several popular applications. It is commonly pushed via malicious documents delivered via spam emails. Win.Trojan.Tofsee-9989403-0 Trojan Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and send large volumes of spam messages to infect additional systems and increase the size of the botnet under the operator's control. Win.Dropper.Glupteba-9988873-0 Dropper Glupteba is a multi-purpose trojan that is known to use the infected machine to mine cryptocurrency and steals sensitive information like usernames and passwords, spreads over the network using exploits like EternalBlue, and leverages a rootkit component to remain hidden. Glupteba has also been observed using the bitcoin blockchain to store configuration information. Win.Virus.Ramnit-9988782-0 Virus Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It also has the ability to steal browser cookies and attempts to hide from popular antivirus software. Win.Dropper.Zeus-9988750-0 Dropper Zeus is a trojan that steals information such as banking credentials using methods such as key-logging and form-grabbing.
Threat Breakdown Win.Dropper.Nanocore-9988753-1 Indicators of Compromise IOCs collected from dynamic analysis of 20 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: AutoUpdate 14 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: AGP Manager 12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: WindowsUpdate 10 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Chrome 7 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEMValue Name: DisableTaskMgr 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM5 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKSValue Name: Path 1 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Explorere 1 <HKCU>\SOFTWARE\RMC-SDW3HE1 <HKCU>\SOFTWARE\RMC-SDW3HEValue Name: exepath 1 <HKCU>\SOFTWARE\RMC-SDW3HEValue Name: licence 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 8_28 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKSValue Name: Hash 1 <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKSValue Name: Triggers 1
Mutexes Occurrences GLOBAL\{<random GUID>}14 Rmc-SDW3HE1 fVfjAITAdJZZHOQHre1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 192[.]169[.]69[.]264 194[.]5[.]98[.]2194 194[.]5[.]98[.]2133 61[.]77[.]245[.]273 212[.]193[.]30[.]2302 194[.]5[.]98[.]841 208[.]95[.]112[.]11 50[.]87[.]253[.]1251 178[.]237[.]33[.]501 194[.]5[.]98[.]541 37[.]0[.]14[.]2091 194[.]180[.]48[.]2311 37[.]0[.]14[.]2071 194[.]5[.]98[.]1761 35[.]76[.]115[.]1701
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 411speed[.]duckdns[.]org4 lowaspeed[.]ddnsfree[.]com4 nexaustin[.]ddns[.]net3 december2nd[.]ddns[.]net3 december2n[.]duckdns[.]org2 ip-api[.]com1 express104[.]ddns[.]net1 geoplugin[.]net1 mail[.]chabiant[.]az1 lucasjules[.]ddns[.]net1 debtcollector[.]ddns[.]net1 ziggynas10[.]ddns[.]net1 vjhelena[.]duckdns[.]org1
Files and or directories created Occurrences %HOMEPATH%\temp20 %TEMP%\RegSvcs.exe18 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C514 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs14 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator14 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat14 %ProgramFiles(x86)%\AGP Manager12 %ProgramFiles(x86)%\AGP Manager\agpmgr.exe12 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\task.dat12 %System32%\Tasks\AGP Manager12 %System32%\Tasks\AGP Manager Task12 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp12 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\start.lnk1 %TEMP%\2_75\mgaj.exe1 %TEMP%\2_75\mtjgjgeh.ini1 %TEMP%\2_75\nlwwlt.icm1 %TEMP%\2_75\ocpdsfgrnc.exe1 %TEMP%\2_75\pgmacqfvo.icm1 %TEMP%\2_75\qfnsjk.xls1 %TEMP%\2_75\qhipjnx.ini1 %TEMP%\2_75\radrdjo.xl1 %TEMP%\2_75\resv.hpd1 %TEMP%\2_75\rfpigltf.xml1 %TEMP%\2_75\rfvsqumom.dll1 %TEMP%\2_75\rwdwdlsrqb.dll1
*See JSON for more IOCs
File Hashes 03dc3203b5d0b87922a2b37052fbd811513ef5fbd375ac368ba02fee5b7b7d911275159f00c20e3a56ed7844f341ba081355db88bde02b181e2104ab2a26406828facaeb8bf5891b98e09ae33d135c27bf57eb843705eaf972668cc963ce14122a6896423cc62446d775c28aedc44306fbf3ee3c4e15eff8ebb4cf148360b4d949c8a6cb3d7f0817936a9f51595dd7f607d3724f12d0f34260fb1b1ba9bd49c25a401401d3823892955203be4f68fb84be04434b58b1c46280beaab2b415f562638c76abb373cc07d17a9bba05eb6b30513fd7ac22353b4da3dca655fa5ecbcf772f73da7d1180275fa17101518f6c0e1e47e06212968d4205f5f21f722bcbd77c342306df5cdaf27e1ff23dc1fb540b1329800672a68195774c833dff83ed937d3315ea47058260603514218b5d3e16fdb1e62458611eb451b2582ad77811f47f409da996e6a0fc61d3bad74b1624e03339680ed574102b76e1261cf5724f8086ba7fd8f503b136fb289d01d6a0c0256cae56f4a4ec6e0b346219ca183f16718b3e6aee5a87a499739edb4a03c5ed50fcd35642785483567175c97fc94da229920d2fc8fdbff7bda0797d02f451c28dbf60f8f7b8d684acf909fe91bfd043bc93cc3c7d2b54465f675362bee33ae91ae3591743b6bcfd7689b8e5c46388f2a09a5216d36b5706e5f111dbd01311c23215eebc256179039021eab4dc7adae04ecb95cef0d5038d22effbbd91618e976e547cae2a842c1565e95ec7a6eb42da99dac75bb4510883c41a26819cfd8b83c77f2b09444abfc53370a142687c9eb2bedbfd78daf1138780c464584623838bb3d9cf60c985bf1c32f18d3400b5b1ccb3e07b12aa5e576d1ccb98dad6a38faa3adcacde35623e30cd4c07d2bfbc75a738
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
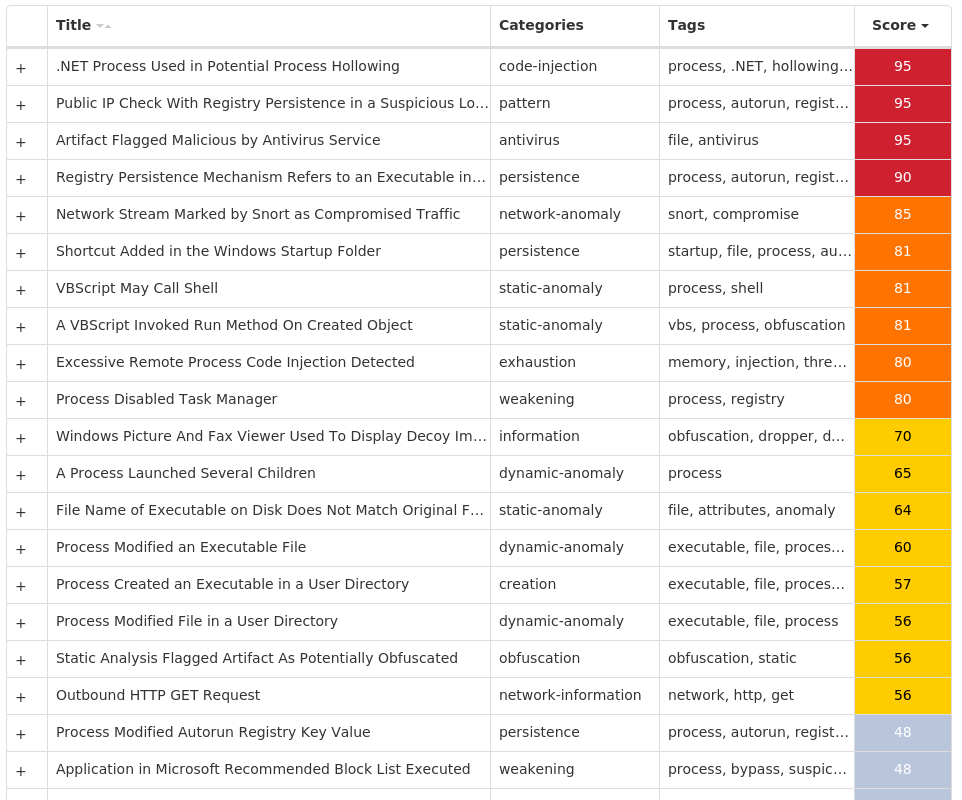
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.NetWire-9988754-0 Indicators of Compromise IOCs collected from dynamic analysis of 30 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEMValue Name: DisableTaskMgr 12 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM12 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: WindowsUpdate 11 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN7 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\INTELLIFORMS\STORAGE26 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX6 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX\20.0.1 (EN-US)\MAIN6 <HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA THUNDERBIRD6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\ENUM6 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\DISCARDABLE\POSTSETUP\COMPONENT CATEGORIES\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\ENUMValue Name: Implementing 6 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: AutoUpdate 5 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: AGP Manager 4 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDERValue Name: DisableAntiSpyware 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: Chrome 3 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: newapp 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 10_91 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 10_210 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 6_104 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 2_51 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 6_84 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 7_72 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 1_1010 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCEValue Name: 6_43 1
Mutexes Occurrences Global\{042723c4-0804-4212-bf56-4b1b2669ca7c}4 N0249TQWRV8507C83 L5808CUU0VA1BWEY3 22L8RUBQCAU3-4M82 382O0TAFATX0-HMF2 8-3503835SZBFHHZ1 1L2N233BRY01J7GZ1 J1P86SR380H1-G0M1 S-1-5-21-2580483-124435716687561 224N6440XBBIwH4Y1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 45[.]33[.]6[.]2236 158[.]101[.]44[.]2425 52[.]20[.]78[.]2405 192[.]169[.]69[.]264 194[.]5[.]98[.]2194 77[.]88[.]21[.]1583 107[.]161[.]23[.]473 85[.]10[.]159[.]43 154[.]82[.]84[.]1553 45[.]10[.]154[.]553 66[.]96[.]162[.]1422 66[.]96[.]134[.]422 85[.]187[.]128[.]352 132[.]226[.]247[.]732 195[.]30[.]85[.]1302 34[.]117[.]168[.]2332 142[.]250[.]80[.]512 162[.]213[.]253[.]2362 156[.]254[.]142[.]112 162[.]0[.]233[.]142 45[.]207[.]92[.]232 148[.]251[.]205[.]1882 179[.]43[.]152[.]1622 208[.]91[.]197[.]271 96[.]126[.]123[.]2441
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences checkip[.]dyndns[.]org9 api[.]ipify[.]org6 www[.]sqlite[.]org6 411speed[.]duckdns[.]org4 lowaspeed[.]ddnsfree[.]com4 smtp[.]yandex[.]com3 www[.]cure-finder[.]org3 www[.]50056[.]top3 www[.]housetelecompro[.]com3 www[.]artshreeinterior[.]com3 www[.]moidvain[.]live2 www[.]odonda[.]com2 www[.]syta-serg[.]com2 www[.]riveratpinny[.]com2 www[.]carparkingtrc[.]com2 www[.]remont-pc-nout-msk[.]online2 www[.]vertiboard[.]live2 www[.]unaandmyriad[.]com2 www[.]jpptraders[.]com2 www[.]ineedmybrain[.]com2 www[.]briarthornoh[.]com2 www[.]maotradersusa[.]com2 www[.]hartmannschneider[.]com2 www[.]aaronmachado[.]com1 www[.]ashakendra[.]org1
*See JSON for more IOCs
Files and or directories created Occurrences %HOMEPATH%\temp30 %TEMP%\RegSvcs.exe20 %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\start.lnk12 %TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp11 %TEMP%\sqlite3.dll6 %TEMP%\sqlite3.def6 %ProgramFiles(x86)%\AGP Manager4 %ProgramFiles(x86)%\AGP Manager\agpmgr.exe4 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C54 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs4 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\Logs\Administrator4 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\run.dat4 %APPDATA%\D19AB989-A35F-4710-83DF-7B2DB7EFE7C5\task.dat4 %System32%\Tasks\AGP Manager4 %System32%\Tasks\AGP Manager Task4 %TEMP%\8_92\nfurkm.ini1 %TEMP%\10_58\pogqmomls.dll1 %TEMP%\8_92\okqem.docx1 %TEMP%\10_58\qgidpskn.ppt1 %TEMP%\8_92\omtehbomd.exe1 %TEMP%\10_58\qhmc.mp31 %TEMP%\8_92\oowwjlp.icm1 %TEMP%\10_58\qjudhi.txt1 %TEMP%\8_92\ovsu.icm1 %TEMP%\10_58\qnlavo.pdf1
*See JSON for more IOCs
File Hashes 03cf2d97e464f97dc99ac1650ce7542acc73e7383926f1a15d013eddc4702f9812e754278ec242a825fdc544047dbb57bdfbccde6323d588cff91503c7a5700b1acc398247e7099476210d781b54e441d88d467e03dc0f91d84c2364ce06ad761e9bbbeb040fa46c67bc853dcc4f0e7f10c9bb1f45b67b0060b2b5fe2c1ad398208c5df5ceda6656fb7066fe23fe06177780df6126438699dc7d5c1c8d6d5d452ebdafb8af3419fb0314f5d093ac9372bc3941116afdf139fa35ae1aeb2d5b7d314fd8a990cc1553c5151fe2fd9d7455ec666c815b869f4f295c8120225bb8f24a88c189dd6beb4924f096977ebe52f845eacf024ec0b874220ebb0bdef5fe1c59ae255f4620d1f6487a326054d749e25f2b0a488f91be99bbbf71de481416256645aa0890f4de9661262d80d47f1abbece05fc710f36b321e9e15f3d88a5bf271e6f633bb9274e20dd4a135134fa7a18bae0c8498db19d8b4bc63ab179f8b357ee10006f987d6efdb7177fb82056d90f3e22a5085691abe740bd0b8fa9fe5ad817bee872912f8a1d0c62bb6eb3a9becea68bfa9414dddaf8ae8a4868b7ca160853b57522a37ee2f41d06b657c631cc95c81db9c75852ffa577f5b14cafe65d393152cb81ad98766bc4a14f491bd9c20f81ea74c7e0673ee901831399587ff369580bddf76a3d9179e760fba40850e85f6dc3baad1356165b78cf160bad11f289f80c921cc082a3671c8faed9cd04611a135e56f5410180722ec87f7e2d4fea39fe2d1d2f2055c824380db8cc4abc3b6c095d2563a67131efaca74e9873d40fea0bdb512eba63b251bb80ac8096fc233fe177b7f1dc44f3d854452a80f8020eca7614db6dcbe0c9a1ade9ac2caec0d1350b78802b5ffa3678ad513ce41ef6d5cba226fb52801754547873418da0f884d05c0adf410f4aa21bf2d111c0bd84dcec24b51269deb24875b522f92417bfbc4ce8d5fc03c40c48a81ed21e1a356aed9c423a2cd001b0aea90ff3ac2e191d3acde70e7511fa84dd57bd576d729144752cc8a3f7aca33ca406b9ca025c987e62601fd99d6cec98fbaf07e98b038c1f254d3d3c216728f58044cae30180c84e75db170ea200860ae9415004f3a0f167ec3
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Raccoon-9988770-0 Indicators of Compromise IOCs collected from dynamic analysis of 14 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\MUICACHE\82\52C64B7EValue Name: LanguageList 14
Mutexes Occurrences CS_CONFIDENCE_MEM_NUTEX14
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 165[.]193[.]78[.]23414 18[.]238[.]4[.]84/316 18[.]238[.]4[.]794 18[.]238[.]4[.]824
Domain Names contacted by malware. Does not indicate maliciousness Occurrences dpd[.]securestudies[.]com14 post[.]securestudies[.]com14
Files and or directories created Occurrences %LOCALAPPDATA%\Programs14 %LOCALAPPDATA%\Programs\Common14 %TEMP%\<random, matching '[a-z]{3}[A-F0-9]{3,4}'>.tmp14 %TEMP%\is-7237K.tmp\_isetup\_setup64.tmp1 %TEMP%\is-IJV12.tmp\rkinstaller.exe1 %TEMP%\is-7237K.tmp\itdownload.dll1 %TEMP%\is-IJV12.tmp\rkverify.exe1 %TEMP%\is-7237K.tmp\rkinstaller.exe1 %TEMP%\is-7237K.tmp\rkverify.exe1 %TEMP%\is-9QBB7.tmp\ec09c5b928cb50415355ff8fe2e3bc9600c7f5b88576e5f8c567df13790a7ab0.tmp1 %TEMP%\is-C1N07.tmp\fd8920c28fd2160ecd246fcf526acf3a23229001957d583b51301eb555830cc2.tmp1 %TEMP%\is-H93HR.tmp\b02b72bc93bf09f7986a98b461c33d7a55fc742b98997fd21688162f8d6d86be.tmp1 %TEMP%\is-C8UFO.tmp\19ff84f10af4e7f4960207a56a1f75eeb71cdcf3fd66339f72d28db735818571.tmp1 %TEMP%\is-70JO4.tmp\cff82abf5bc773973dc5dc12949a5957f0dd72b7e8120ead9dc3ef9c53221f43.tmp1 %TEMP%\is-2F8U3.tmp\RKBanner.bmp1 %TEMP%\is-2F8U3.tmp\_isetup\_setup64.tmp1 %TEMP%\is-2F8U3.tmp\itdownload.dll1 %TEMP%\is-2F8U3.tmp\rkinstaller.exe1 %TEMP%\is-II8FN.tmp\RKBanner.bmp1 %TEMP%\is-2F8U3.tmp\rkverify.exe1 %TEMP%\is-II8FN.tmp\_isetup\_setup64.tmp1 %TEMP%\is-II8FN.tmp\itdownload.dll1 %TEMP%\is-II8FN.tmp\rkinstaller.exe1 %TEMP%\is-II8FN.tmp\rkverify.exe1 %TEMP%\is-Q4D1S.tmp\942597777531fe8e56d8384e93e2255b60b4dc4794d0f05155f495f287b7984c.tmp1
*See JSON for more IOCs
File Hashes 1575ca0e85bfa0b05822dfadd84c2312208d84e9d7e5d733c44f57178ae64afb1770e4d91e8c72eb38df3fa14ad6877c631a3de50ccdeef7313c53d858c8372319ff84f10af4e7f4960207a56a1f75eeb71cdcf3fd66339f72d28db73581857128d0dfff5c89d5c32baf7b5cb84b33b39f9465a439287b628d49c8a33670f4ba2f1021c803f6757e6d3c32443c432a1e55ff020613476ff35982ca4f0106fd45534ade1fba8556b2bbc0cb0703ca35d26d292f87b47e025600ad741d15e331e5942597777531fe8e56d8384e93e2255b60b4dc4794d0f05155f495f287b7984cab9a5a8f157478327bf99e8fd7707a3eabe1a8b26e1837a9b0185203b3b0ab08b02b72bc93bf09f7986a98b461c33d7a55fc742b98997fd21688162f8d6d86bec12d766c1c5c2cbcf8b911c016bdd24f81143c8a9cd4502c3e2494f1a3f0197fcff82abf5bc773973dc5dc12949a5957f0dd72b7e8120ead9dc3ef9c53221f43d8f031b9b0ee9b4941538b26df741ab51c1911dc4024914dd427d7a0bd7b6a53ec09c5b928cb50415355ff8fe2e3bc9600c7f5b88576e5f8c567df13790a7ab0fd8920c28fd2160ecd246fcf526acf3a23229001957d583b51301eb555830cc2
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
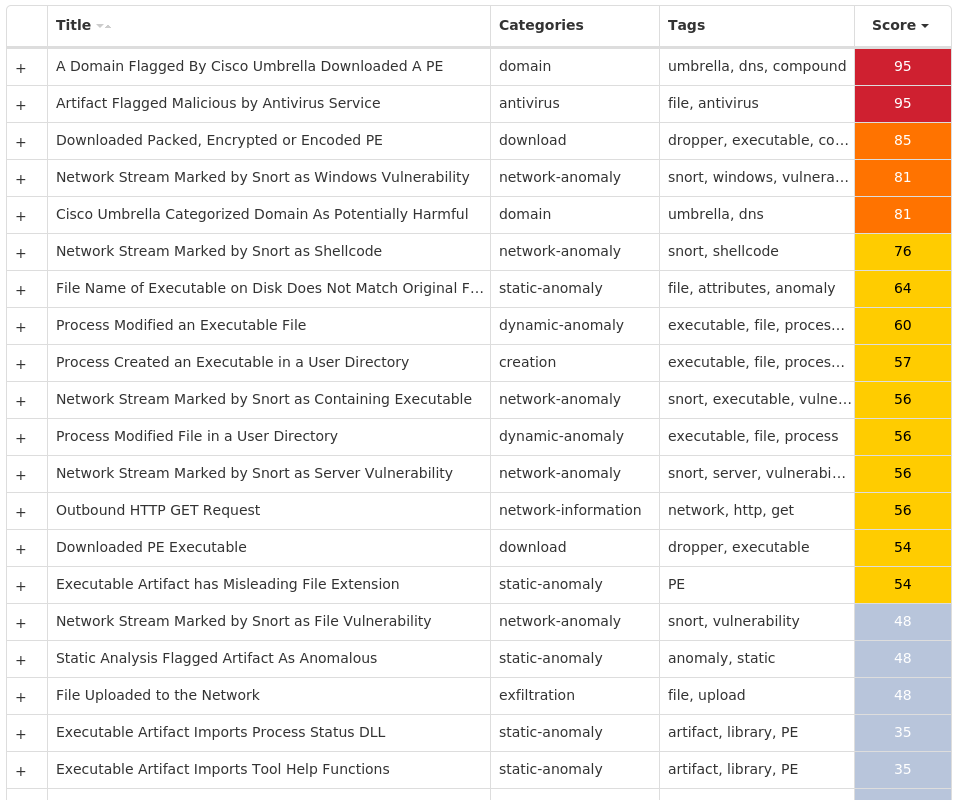
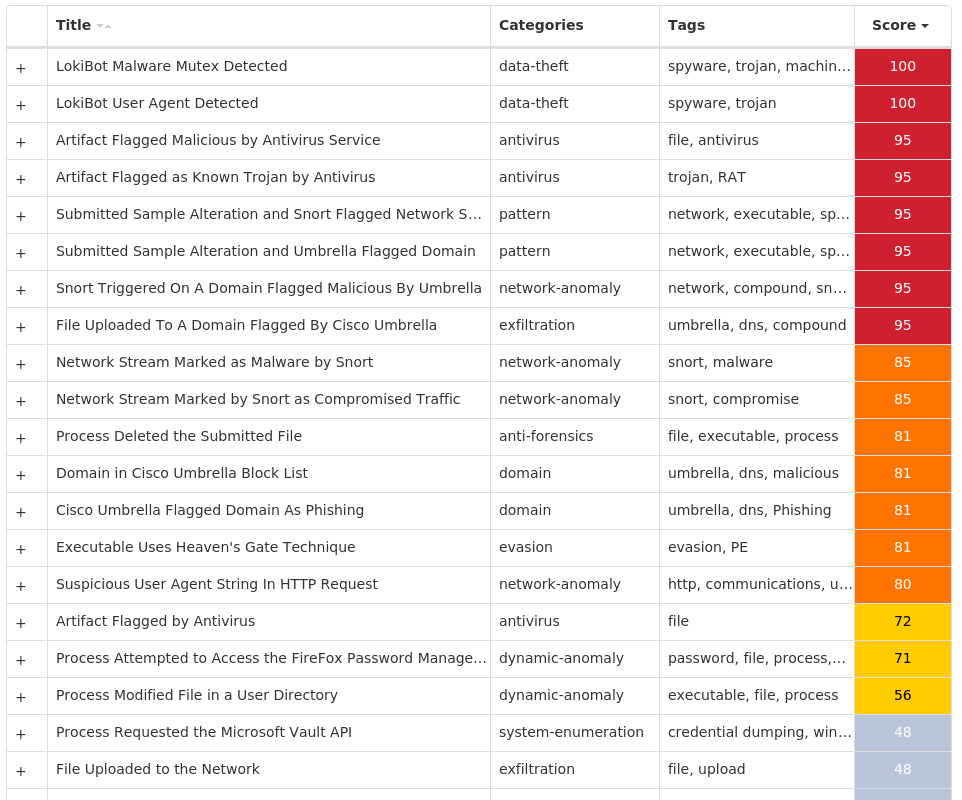
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.LokiBot-9988785-0 Indicators of Compromise IOCs collected from dynamic analysis of 34 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSIONValue Name: SysHelper 5 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: SysHelper 5 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDERValue Name: DisableAntiSpyware 3 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFENDValue Name: Start 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: NoAutoRebootWithLoggedOnUsers 3 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERVValue Name: Start 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: NoAutoUpdate 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableBehaviorMonitoring 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableOnAccessProtection 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableScanOnRealtimeEnable 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableIOAVProtection 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURESValue Name: TamperProtection 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableRealtimeMonitoring 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: AUOptions 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: AutoInstallMinorUpdates 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONSValue Name: DisableNotifications 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: UseWUServer 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATEValue Name: DoNotConnectToWindowsUpdateInternetLocations 3
Mutexes Occurrences Global\<random guid>17 {1D6FC66E-D1F3-422C-8A53-C0BBCF3D900D}5 M5/610HP/STAGE25 MSCTF.Asm.{00000009-4fb3f26-9d18-66b568-627b8a85e4b6}3 Global\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3 Session\1\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3 Session\2\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3 Session\3\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3 Session\4\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3 Session\5\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3 Session\6\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3 Session\7\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3 Session\8\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3 3749282D282E1E80C56CAE5A1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 149[.]154[.]167[.]995 162[.]0[.]217[.]2545 78[.]47[.]226[.]245 185[.]11[.]61[.]1254 179[.]43[.]154[.]2163 190[.]229[.]19[.]72 193[.]233[.]20[.]202 211[.]104[.]254[.]1392 109[.]98[.]58[.]981 175[.]119[.]10[.]2311 175[.]120[.]254[.]91 222[.]236[.]49[.]1241 211[.]119[.]84[.]1121 185[.]95[.]186[.]581 46[.]148[.]39[.]361
Domain Names contacted by malware. Does not indicate maliciousness Occurrences t[.]me5 api[.]2ip[.]ua5 uaery[.]top5 jiqaz[.]com5 sempersim[.]su1
Files and or directories created Occurrences %ProgramData%\freebl3.dll5 %ProgramData%\mozglue.dll5 %ProgramData%\msvcp140.dll5 %ProgramData%\nss3.dll5 %ProgramData%\softokn3.dll5 %ProgramData%\vcruntime140.dll5 %APPDATA%\Microsoft\Network5 I:\5d2860c89d774.jpg5 \SystemID5 \SystemID\PersonalID.txt5 %LOCALAPPDATA%\bowsakkdestx.txt5 %System32%\Tasks\Time Trigger Task5 %System32%\Tasks\Azure-Update-Task5 %APPDATA%\Microsoft\Network\mstsca.exe5 %LOCALAPPDATA%\3856b5d6-9eb0-496c-b0d1-db92b0f6ed655 \x5c\x55\x73\x65\x72\x73\x5c\x41\x64\x6d\x69\x6e\x69\x73\x74\x72\x61\x74\x6f\x72\x5c\x41\x70\x70\x44\x61\x74\x61\x5c\x4c\x6f\x63\x61\x6c\x5c\x4d\x69\x63\x72\x6f\x73\x6f\x66\x74\x5c\x57\x69\x6e\x64\x43e\x77\x734 %LOCALAPPDATA%\Yandex2 %LOCALAPPDATA%\Yandex\YaAddon2 %LOCALAPPDATA%\7c34bb01-5d78-49c4-8bbb-73fdc7aa12622 %LOCALAPPDATA%\7c34bb01-5d78-49c4-8bbb-73fdc7aa1262\build2.exe2 %LOCALAPPDATA%\7c34bb01-5d78-49c4-8bbb-73fdc7aa1262\build3.exe2 %APPDATA%\D282E1\1E80C5.lck1 %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c51 %LOCALAPPDATA%\8e9cfb64-0179-441e-8dff-4b7c453e48cd\build2.exe1 %LOCALAPPDATA%\fdc94fe5-09a5-427c-8fd6-709a6287f394\build2.exe1
*See JSON for more IOCs
File Hashes 018910c26377b8eec3b168e26b35b333fa347cbc6fa77be9c0788e9dc8dd06260968a06a8f908bffbaf5e7e12217bda5b509c2e7f47ac5dbdfa0abcdbf8a1ed313fc7443813437a303dac61f448cf20d8e3ecd46ab28dbf457c9de20ab82243618d9aa33f0f40eb0aa91e111be763175251c8088d0c9ede853a803266a9bf54f1f973d307ac6766796e6abcaf1c71b8e506859ebf82d9d176fafc564383b2e20216fa858d40ce79f6a98543b745b88f1614c472a22a50be0efe6ea067641f21025c3ef432bdb3c4029f7e8d13aeafcc968e15eb182486f55ff9df3d55ca6d28526317358d7dbcfdf4eb51ed2618f8c317d2a032a9f70e1c5d8bcf8fa906491413fa26f616dae2f0d52d7d0e1ec6b786b8e757249ec69214146d084f84a7c8ca442545d609e7c76810ad63ea4da09e1182d94c9f3b9ee2cdc769a0f9d04d484fe42962566d7307f109b21b537bce28deb8fc9b7dfa97fe03c2900682dd344659d46d0ab2a5bbd3ffc21b5ff3ca1c6ca79ea4ecff325e701a8f25a4de0d4d76c905079d940ab2475a812aae6ca021a2e6879304ab1ebd2fdbabb693271180c65785607aa9e4bc49ea0c2b5e2dd8dc7c5b6bd6c5dd4069be74aead19e2f1560c24f575656f599890d391cbb8de070552046dc2742010ff372075d0bde18cc29447459c0311a07b455fe897f86d3737f01553b7d70d5347d21efdf1b22801b37964a5b21ebc0dee72b38150ffd07aca61bc1eda50f146a56372f6a57039da54c265b5fb168bb6fb8907a04c177b5ac06bc9e79d6d7e17a0d397421b2b4833f548cf968d087e07cc6c62c45367a39176ffc69f88631879133d467f2c8d73a42ba4cc574c9d98c13fb33321f3d5bd933ef76ffeb3062050ee0d1f4f46a058948388aa77d9ea0ae2b533615f8f2fdb1b27e8f55022d647283616b6436eea46e0abcba9f82a189280a1eea50945259535d04e2d5195cb41dcaeaa49b35e5d34cbf412488843039df424aa2487063ae4033ef6fed36e617331b874cf452e22d4500c0f8498c6cbb65ba894cfd1282643d11f91c1b4e03069651a1957bfcafa623af36faa194883f86bb604e748e172034cad1d5ffee64f3f0c463f680c7ba144897a58654
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
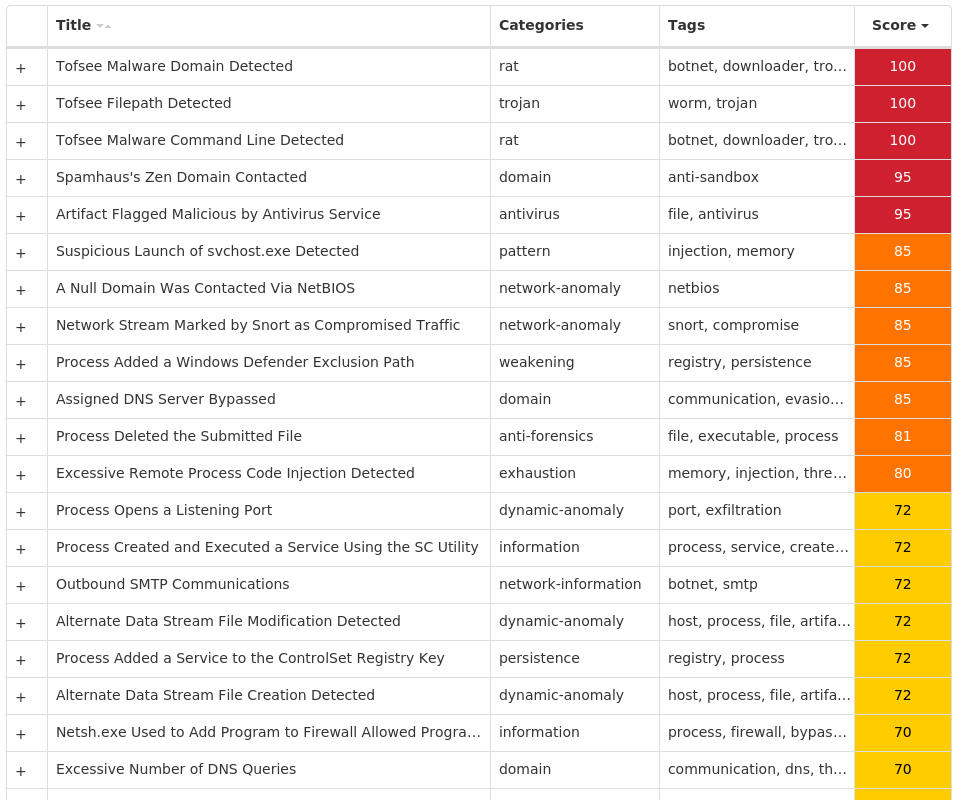
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Trojan.Tofsee-9989403-0 Indicators of Compromise IOCs collected from dynamic analysis of 35 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: Start 8 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSIONValue Name: SysHelper 6 <HKU>\.DEFAULT\CONTROL PANEL\BUSES5 <HKU>\.DEFAULT\CONTROL PANEL\BUSESValue Name: Config2 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: Type 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: ErrorControl 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: DisplayName 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: WOW64 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: ObjectName 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: Description 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>Value Name: ImagePath 5 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFENDValue Name: Start 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: NoAutoRebootWithLoggedOnUsers 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: NoAutoUpdate 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableBehaviorMonitoring 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableOnAccessProtection 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableScanOnRealtimeEnable 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableIOAVProtection 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES3 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURESValue Name: TamperProtection 3
Mutexes Occurrences Global\<random guid>9 {1D6FC66E-D1F3-422C-8A53-C0BBCF3D900D}6 MSCTF.Asm.{00000009-4fb3f26-9d18-66b568-627b8a85e4b6}2 Global\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}2 Session\1\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}2 Session\2\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}2 Session\3\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}2 Session\4\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}2 Session\5\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}2 Session\6\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}2 Session\7\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}2 Session\8\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}2 WTfewgNmxpcaVXHKTu1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 149[.]154[.]167[.]999 162[.]0[.]217[.]2546 78[.]46[.]235[.]1096 31[.]13[.]65[.]525 46[.]173[.]218[.]2095 176[.]113[.]115[.]1365 142[.]251[.]40[.]1005 80[.]66[.]75[.]2545 80[.]66[.]75[.]45 176[.]113[.]115[.]154/315 176[.]113[.]115[.]2395 176[.]113[.]115[.]1355 31[.]13[.]65[.]1744 142[.]251[.]40[.]1314 185[.]11[.]61[.]1254 95[.]158[.]162[.]2004 212[.]227[.]17[.]1703 217[.]69[.]139[.]603 193[.]233[.]20[.]243 45[.]155[.]204[.]133 212[.]227[.]17[.]1782 104[.]47[.]53[.]362 66[.]254[.]114[.]412 37[.]1[.]217[.]1722 104[.]244[.]42[.]662
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences t[.]me9 api[.]2ip[.]ua6 uaery[.]top6 jiqaz[.]com6 249[.]5[.]55[.]69[.]bl[.]spamcop[.]net5 249[.]5[.]55[.]69[.]cbl[.]abuseat[.]org5 249[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net5 249[.]5[.]55[.]69[.]in-addr[.]arpa5 249[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org5 249[.]5[.]55[.]69[.]zen[.]spamhaus[.]org5 i[.]instagram[.]com5 microsoft-com[.]mail[.]protection[.]outlook[.]com5 microsoft[.]com5 www[.]google[.]com5 svartalfheim[.]top5 www[.]instagram[.]com4 www[.]google[.]it4 auth[.]mail[.]ru3 imap[.]web[.]de3 imap[.]gmx[.]net3 work[.]a-poster[.]info2 www[.]google[.]co[.]uk2 www[.]google[.]com[.]au2 www[.]tiktok[.]com2 www[.]google[.]com[.]tr2
*See JSON for more IOCs
Files and or directories created Occurrences %ProgramData%\freebl3.dll6 %ProgramData%\mozglue.dll6 %ProgramData%\msvcp140.dll6 %ProgramData%\nss3.dll6 %ProgramData%\softokn3.dll6 %ProgramData%\vcruntime140.dll6 I:\5d2860c89d774.jpg6 \SystemID6 \SystemID\PersonalID.txt6 %System32%\Tasks\Time Trigger Task6 \x5c\x55\x73\x65\x72\x73\x5c\x41\x64\x6d\x69\x6e\x69\x73\x74\x72\x61\x74\x6f\x72\x5c\x41\x70\x70\x44\x61\x74\x61\x5c\x4c\x6f\x63\x61\x6c\x5c\x4d\x69\x63\x72\x6f\x73\x6f\x66\x74\x5c\x57\x69\x6e\x64\x43e\x77\x736 %LOCALAPPDATA%\3856b5d6-9eb0-496c-b0d1-db92b0f6ed656 %LOCALAPPDATA%\7c34bb01-5d78-49c4-8bbb-73fdc7aa12626 %LOCALAPPDATA%\7c34bb01-5d78-49c4-8bbb-73fdc7aa1262\build2.exe6 %SystemRoot%\SysWOW64\config\systemprofile5 %SystemRoot%\SysWOW64\config\systemprofile:.repos5 %SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>5 %TEMP%\<random, matching '[a-z]{8}'>.exe5 %LOCALAPPDATA%\Yandex4 %LOCALAPPDATA%\Yandex\YaAddon4 \{4feb3bef-c8f9-d16c-dfb8-933e58354094}1 \{ef6007c6-a5d2-ddd4-8b35-1c2c1f5d4a96}1 %APPDATA%\nsis_unscc28dda9.dll1 %APPDATA%\nsis_unscc29ad46.dll1 %LOCALAPPDATA%\3856b5d6-9eb0-496c-b0d1-db92b0f6ed65\6585b2ca812353618b651b010fba7b6e509c0a2ecbe835b139b47a7cefbbe022.exe1
*See JSON for more IOCs
File Hashes 07208125e50054249217e23d23cb0f1c60902b79039eada521e580a9874367c10e983029bc6537eadbb83c37bf4efb101bf2476223fecd1edc34f6834cede275243536284047d671c497feebc41ffab5b1d2989d10d83de822cab171621890602d19ffc8092b613bd178b1d0cfb180a9ebe78c47c0f748fe2afeec4308948dbe309cfe7002f5ba9a69acb5de1057fbaa8b69e9b241717d86c2af2607ce32b6d741e4b903ce4dcf1e0a138ce1edb1280d6fe2b50a222c925d3600903c4eb2fae249c47cdeb7a96f18843adc2c93765147823d9cc3b741766f1cc3257d19e6e81b4ce2353420b3fef9a268a018a0b8bb5d4389bd7ff288c1168af812dd81b2d54a5deb46b26699093388dbe8924984ff6989a9e3cd77d0d7aa2082d2b857e2001a645450dca48ce4a23d042d0ca06e084b511019e2876663828163ef176023fce26585b2ca812353618b651b010fba7b6e509c0a2ecbe835b139b47a7cefbbe022680ab026b99110c40b7082b3d30fa3f74ee17d49c1b6b3d97cb72ba4cf3323fc6a0c5287d68e8420000b47bf39348a10ca9cb6e3ec9b737d80b4a2608113901375d147c30c0b66e05b4e56a40f816de462668850d945e03dbe393feebc4746c775e4549d520b05828fa5b3d5e8907c26b37cbcb0e98887bce5a18d1d9b4820ed82c5eea49d1201505fe3346262c2ddf21d8f0a76c58b7c5922362b79d91e371685dc2a941050a6000b3bc6fed7fd47730d7bb6d7b7fb761b769a6e0e6b5012c98692802882838289b211bdbd397caf4c1c5e298aa1702764c6264d511fafedc28a7b8e7243c5aa78ce2415d735a3c4b9adb5f0760d935efbb62d6fb6870e9fff9550bd7e6baa67c488e005edc23aa29bcfa3dbe8dd643ad7165d5c90394ac6e5acf04fb26693384ef1090ab6854df66c2e4cef24a310a44a652330902d0bdef3b0d58abdf40c6e922ecad36224a0c65bc3f87fcd36c781566f5d7733b72e608bb2dc0720b0e858b49bd451a799fc531027ad712cf924d5e6599bdea94a2d53bcb79a6a8e5cb6aa996e9695384382fd3c1760e510bffc62a5f6b2ce96ff827b1db8368b4ce775b6e356334342e6daed7cd1623c9d8b35dd04b6c5e53de35efc4c
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Glupteba-9988873-0 Indicators of Compromise IOCs collected from dynamic analysis of 18 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERVValue Name: Start 3 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDERValue Name: DisableAntiSpyware 2 <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFENDValue Name: Start 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: NoAutoRebootWithLoggedOnUsers 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: NoAutoUpdate 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableBehaviorMonitoring 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableOnAccessProtection 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableScanOnRealtimeEnable 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableIOAVProtection 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES2 <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURESValue Name: TamperProtection 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTIONValue Name: DisableRealtimeMonitoring 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: AUOptions 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: AutoInstallMinorUpdates 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONSValue Name: DisableNotifications 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AUValue Name: UseWUServer 2 <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATEValue Name: DoNotConnectToWindowsUpdateInternetLocations 2 <HKCU>\SOFTWARE\MICROSOFT\A1890984Value Name: PatchTime 1 <HKCU>\SOFTWARE\MICROSOFT\A1890984Value Name: PGDSE 1
Mutexes Occurrences Global\<random guid>5 {1D6FC66E-D1F3-422C-8A53-C0BBCF3D900D}1 Global\SetupLog1 Global\WdsSetupLogInit1 Global\h48yorbq6rm87zot1 Global\xmrigMUTEX313371 WininetConnectionMutex1 M5/610HP/STAGE21 Global\qtxp9g8w1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 77[.]73[.]133[.]622 62[.]204[.]41[.]1592 204[.]79[.]197[.]2191 148[.]251[.]87[.]1121 162[.]159[.]134[.]2331 185[.]199[.]111[.]1331 190[.]117[.]75[.]911 162[.]0[.]217[.]2541 167[.]172[.]42[.]311 142[.]250[.]112[.]1271 20[.]60[.]161[.]2251 91[.]215[.]85[.]1551 45[.]15[.]156[.]2021 190[.]141[.]35[.]31 185[.]165[.]170[.]191 89[.]13[.]103[.]1861 89[.]58[.]60[.]2081 98[.]207[.]124[.]1631 109[.]123[.]233[.]1381
Domain Names contacted by malware. Does not indicate maliciousness Occurrences raw[.]githubusercontent[.]com1 msdl[.]microsoft[.]com1 vsblobprodscussu5shard35[.]blob[.]core[.]windows[.]net1 vsblobprodscussu5shard60[.]blob[.]core[.]windows[.]net1 cdn[.]discordapp[.]com1 api[.]2ip[.]ua1 stun[.]l[.]google[.]com1 bitcoin[.]dermichi[.]com1 electrum[.]leblancnet[.]us1 lavahost[.]org1 fulcrum[.]grey[.]pw1 uaery[.]top1 drampik[.]com1 fortress[.]qtornado[.]com1 electrumx[.]info1 vmd104012[.]contaboserver[.]net1 7326f935-56c7-404a-850e-453ee192e743[.]uuid[.]dg2sz7pxs7llf2t25fsbutlvvrjij4pmojugn75cmxnvoshmju6dzcad[.]onion1
Files and or directories created Occurrences %LOCALAPPDATA%\Yandex4 %LOCALAPPDATA%\Yandex\YaAddon4 \x5c\x55\x73\x65\x72\x73\x5c\x41\x64\x6d\x69\x6e\x69\x73\x74\x72\x61\x74\x6f\x72\x5c\x41\x70\x70\x44\x61\x74\x61\x5c\x4c\x6f\x63\x61\x6c\x5c\x4d\x69\x63\x72\x6f\x73\x6f\x66\x74\x5c\x57\x69\x6e\x64\x43e\x77\x732 %SystemRoot%\Logs\CBS\CBS.log1 %SystemRoot%\rss1 %SystemRoot%\rss\csrss.exe1 %APPDATA%\Microsoft\Network1 I:\5d2860c89d774.jpg1 \SystemID1 \SystemID\PersonalID.txt1 %LOCALAPPDATA%\bowsakkdestx.txt1 %System32%\Tasks\Time Trigger Task1 %TEMP%\csrss1 %TEMP%\csrss\dsefix.exe1 %TEMP%\csrss\patch.exe1 %System32%\drivers\Winmon.sys1 %System32%\drivers\WinmonFS.sys1 %System32%\drivers\WinmonProcessMonitor.sys1 %TEMP%\Symbols1 %TEMP%\Symbols\ntkrnlmp.pdb1 %TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE021 %TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE02\download.error1 %TEMP%\Symbols\pingme.txt1 %TEMP%\Symbols\winload_prod.pdb1 %TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E3611
*See JSON for more IOCs
File Hashes 0376b5ee34d46a7ab1ad3452365fbd44020fb67988a28cdd52735b5b8c302711048589ea3018e664d6fdc3faa93d652b6461e76e8353290ebde5df1b483f8c601d319f7e8db796613d3e9496cf26290a3a443158bec07226fd9c5c2b9966db6d23345f908b3895111ae284cfc4858887da2fe4640ed698c8fd9204c1384786fb250ed797d37c163a04589c7767db6865aaedd5b40a575bf06cc4675d1ce24869267d055f0fbae4dbdadefb989a99566d754233806bc00a7ca63f7dc377e085c646f334adfbad0b9ed2e259ba4da1379c626043b206ba2ce610872688e8914c845fe1badcbe953df5a0ef020647950ddbe437fd56191d6e75ea88919af4d5da287bc325495c9e3bfb94c3a652fa3c6a4e40207ceb3585ae4935bd27af341b0449935a798cfc4114c215688cf6d7b052491a4c24ff75ad7d04f62c066dd2bc9182a3333fe0c9924291ab54145fb772e785f9f5678a44d9c1254e36c710f28d53e7ba67657f3cf8b2ef26406717f012090363c33e1d439488d4afb0b18d37215c45cb886be0530f96ba6b95136e2134e79d40427ac37703236fe8455073d570b736d35a0b59e360c8ee6bccb1c07fd29592c4b2ec9a1a1aadbe2a3f91655eba5316dbce2ca6121577b89cb7fe355eb92c8a7bb8690672956a2ca58c111d9561758fec7dffd2498bc699649335dfde360c8f96acdb619fb9ae94b6bdd7d02caef8e6eed1f296204360f8f563e9dbceca4628aef8d7c4437c6359ac20d1bfc6fc9573fd81eb4c53e788ac14584f8fd628304c710db8f5cfe22a99aa4876f19d9858bf
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella WSA
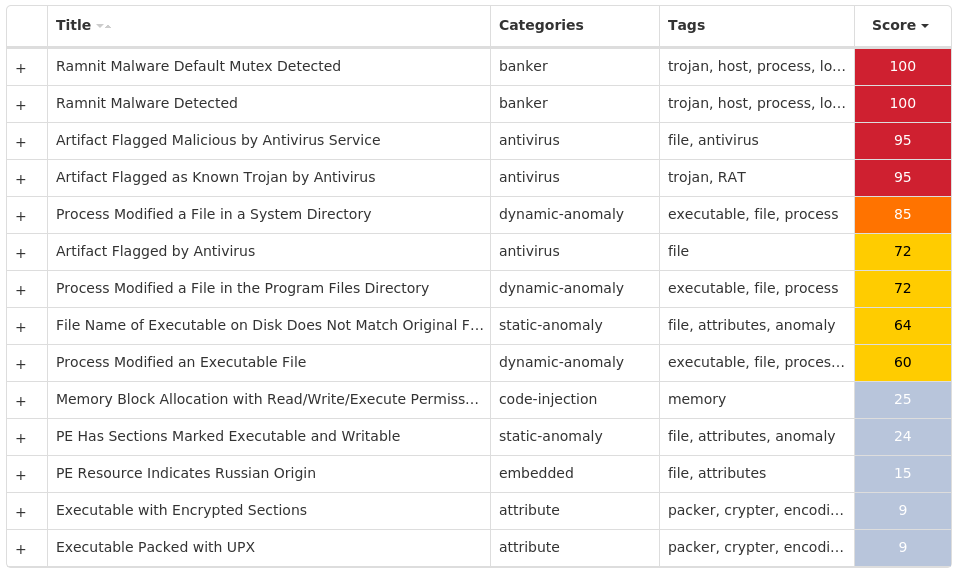
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Virus.Ramnit-9988782-0 Indicators of Compromise IOCs collected from dynamic analysis of 21 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A}Value Name: FaviconPath 21 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{0633EE93-D776-472F-A0FF-E1416B8B2E3A}Value Name: Deleted 21 <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPESValue Name: DefaultScope 21 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\STATS\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}21
Mutexes Occurrences KyUffThOkYwRRtgPP21
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 13[.]107[.]21[.]20010
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]bing[.]com21
Files and or directories created Occurrences %ProgramFiles(x86)%\Microsoft21 %ProgramFiles(x86)%\Microsoft\DesktopLayer.exe21 %SystemRoot%\SysWOW64\rundll32Srv.exe21 %ProgramFiles(x86)%\Microsoft\px7366.tmp2 %ProgramFiles(x86)%\Microsoft\px703B.tmp2 %ProgramFiles(x86)%\Microsoft\px8039.tmp1 %ProgramFiles(x86)%\Microsoft\px6FAE.tmp1 %ProgramFiles(x86)%\Microsoft\px73C3.tmp1 %ProgramFiles(x86)%\Microsoft\px702B.tmp1 %ProgramFiles(x86)%\Microsoft\px73D3.tmp1 %ProgramFiles(x86)%\Microsoft\px6FCD.tmp1 %ProgramFiles(x86)%\Microsoft\px771D.tmp1 %ProgramFiles(x86)%\Microsoft\px6E28.tmp1 %ProgramFiles(x86)%\Microsoft\px7192.tmp1 %ProgramFiles(x86)%\Microsoft\px70F6.tmp1 %ProgramFiles(x86)%\Microsoft\px71EF.tmp1 %ProgramFiles(x86)%\Microsoft\px6FFC.tmp1 %ProgramFiles(x86)%\Microsoft\px7911.tmp1 %ProgramFiles(x86)%\Microsoft\px728B.tmp1 %ProgramFiles(x86)%\Microsoft\px71A1.tmp1 %ProgramFiles(x86)%\Microsoft\px7115.tmp1 %ProgramFiles(x86)%\Microsoft\px6E67.tmp1
File Hashes 0c33bc8a10f6a48bf12e8df5262143d5cc5a4c7cfa6cadf82253b5517b2bec6717aef698ae9fd21f6ca4d973013ba565bfb869c729d89154ebf86b0ecbc634284e5d405a2e0be49aea162a6a2026ca997d420d58697b029bde0f85ed8d6441675542a9398f257317cc69b32b046392a38b1f70fb2ad6396a5f08d0c9e073e0a9632a6c249cb8eeacc68c0ff9f624435230113762dcb3d6b0d2c1329be82ee5746cbef0d719b5e47482d34e88a2fe4148b6816f3b482ba7e5ef6add28e8bb3d1d77b7aba8c4bc053f1dddbe4c267140a077be44f0bd040411c0ddfeb7c3e11e4d7b2ce3cf6c741a7fa5b1821f7d129382de6abe62f408467ca49884d9aa477075a46b04ebd27304cbef9f95dbd7606b480e1877fa3b0a2cda4edfb06302f67225a8cc4ae486f9149baadd5d998a8df360d4b45746d6833928c40cae5df933b438c3a8e97f914a1463534d8cfae9506c4a06d73ba9a2e44f90c3bc6c0e5aee3428cb946b8506091b0e31961a6ccad86a423d777629e6961a3f7d2616bb777ba541da812431fbc8469f869fcb5b83d2f09a13d9a3adb1f806d52491db16f830f712ded85d07d86dd3adcc23b21b1a37896a3a300e8710135dc920027663ef54b775e563dcb69817516eb88c4d896820047d97bb3f1a36f9f247ef3c510cc94e03d9e67f9d504fb931f908cfb2f5e8cb5af37e08ede82d5415e30b6d6197b7d44627e6813af7335f70cf2b05a3a05bdb398183ff4f5abe02bfad60de4733d8ebf10bf8bcc28164d3f4f1c3082e96e263038faafcc50e1d8749971deee447627e0e50f90d93f548a163f61764bccba91df85c9db6970666d8763333c4162a70b72615fe7785671e6ccb0b6e1361de8fd1f25ba8da76d956670552e54a484cae725748fef1705eea70e1de25c5ae65f18f7d2b0bba8e6dd3fafaebb86e535bc066adaa
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
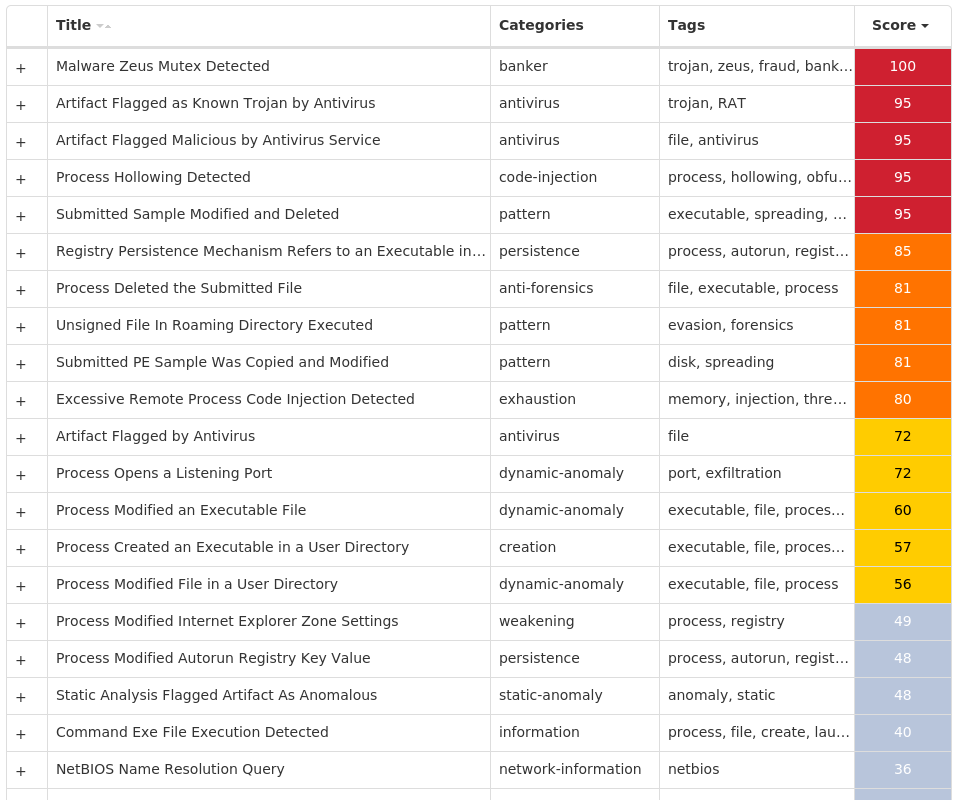
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK Win.Dropper.Zeus-9988750-0 Indicators of Compromise IOCs collected from dynamic analysis of 13 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\PRIVACYValue Name: CleanCookies 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104Value Name: CheckSetting 1 <HKCU>\SOFTWARE\MICROSOFT\UBVIY1 <HKCU>\SOFTWARE\MICROSOFT\UBVIYValue Name: Uwwuycd 1 <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNValue Name: {A6EB954B-36CE-6D51-9914-7AFC0F4D2293} 1
Mutexes Occurrences Local\{40FFE960-4AE5-8B45-9914-7AFC0F4D2293}1 Local\{6B598C52-2FD7-A0E3-9914-7AFC0F4D2293}1 Local\{40FFE963-4AE6-8B45-9914-7AFC0F4D2293}1 GLOBAL\{<random GUID>}1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ehsbgroups[.]com1
Files and or directories created Occurrences %TEMP%\tmp8b1ba708.bat1 %APPDATA%\Feyk1 %APPDATA%\Feyk\tued.ecu1 %APPDATA%\Itku1 %APPDATA%\Itku\unvoe.exe1
File Hashes 01a9202e01857ee31377711c893d5986672a4d090e16f0a4b379b35dda652a24087c75d498912b2e0037c5a23c203152d1e8cb521d744b1d1e2d3fd0e6e062df1f00b921d9b2678183af1bddc7bf00292f023c0c3b12c90571a1d961b7c5009148360a8b4dfd126db752d460ed8ceb40648c67db762459126f8df9a817df2bf26738a80543cbbf92d09122797cf787c144e0fb731b2563f2ee0856b6d004bae98687477c766f0fa9e440110916fa2df3bcbfe47c912026b896c10ff6dcf3eb508b3b348436737e08f6b1645e8e8b66bd3f81ee9b6070e4a61f01e4dba4d133b98f5a293c6153c6d223f942ee9f25434bc8237a248a653c1d9a2c6d100d78e4bd946422e0bb62a87310bb0645d19d22a007cc416b2f1d94029667efb96b1dc62ab22deb5464a94d5eb973664697ce0aa6d70b2d538747f30e45d45f3452c6aa29c40bfc195e4c12017fb7937fec5b03873408127e957a392d2dc59128a4a59bf3d661bed2c2d1613a03974d188aef1f74b7937674dd60ac63a2725f1c9f603e8beb6f7a2f954530cea44e1237c21285e88a2e7768b2943c220870e4fdce3eeee9
Coverage Product Protection Secure Endpoint Cloudlock N/A CWS Email Security Network Security N/A Stealthwatch N/A Stealthwatch Cloud N/A Secure Malware Analytics Umbrella N/A WSA N/A
Screenshots of Detection Secure Endpoint Secure Malware Analytics MITRE ATT&CK