- Cisco Talos has observed a widespread and ongoing financial theft SMS phishing (smishing) campaign since October 2024 that targets toll road users in the United States of America.
- We observed that the campaign targets people across several states in the U.S. according to the domain names used in the smishing messages.
- Talos assesses with moderate confidence that the toll road smishing attacks are being carried out by multiple financially motivated threat actors using the smishing kit developed by “Wang Duo Yu”, according to the intelligence obtained by Talos.
Toll road smishing attacks
Since the middle of Oct. 2024, Talos has seen ongoing smishing attacks impersonating U.S toll road automatic payment services (such as E-ZPass) with the intent of financial theft. The actors have so far sent SMS messages to individuals in about eight states in the U.S., including Washington, Florida, Pennsylvania, Virginia, Texas, Ohio, Illinois and Kansas. Talos identified these states via spoofed domains containing the states’ two-letter abbreviations that we observed in the SMS messages.
The actors send an SMS notification for an outstanding bill claiming that the potential victim owes a small amount of money, under $5 USD. They warn of potential late fees, prompting victims to visit a spoofed domain for the payment.
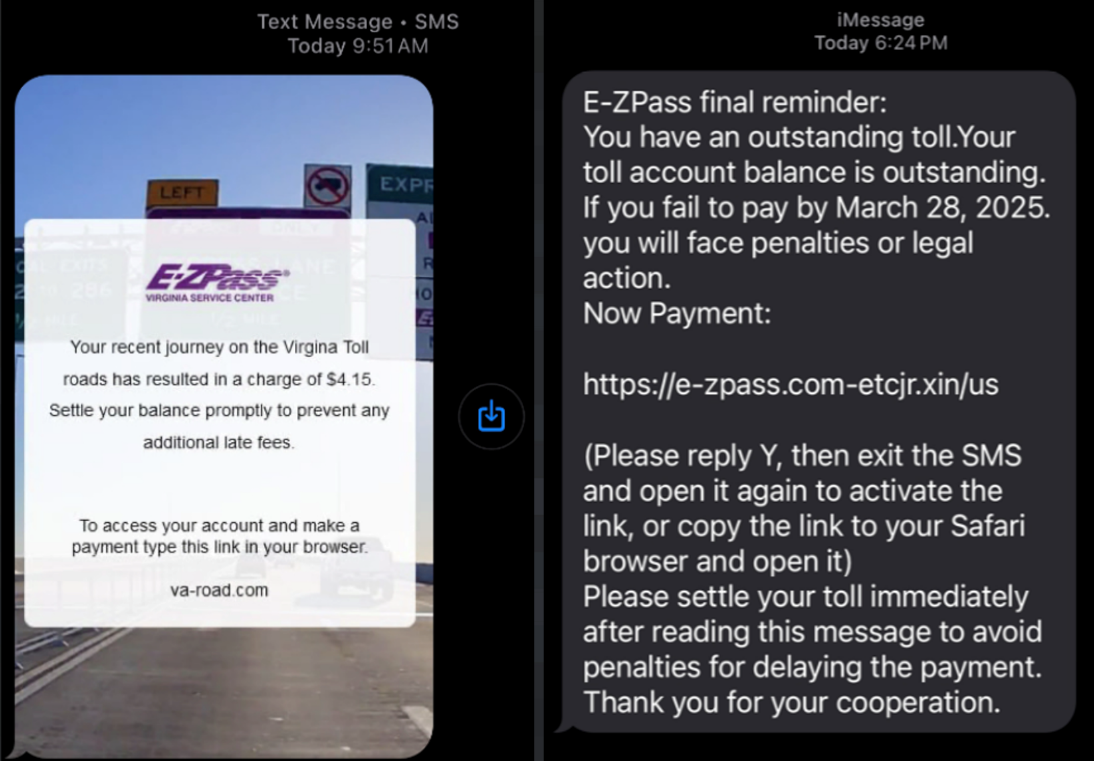
When the victim visits the domain, they are prompted to solve a fake image-based CAPTCHA, after which it redirects the victims to a fake webpage with the legitimate toll service's logo. This webpage prompts the victims to enter their name and ZIP code to view their fake bill. The fake bill displays the victim's name with a message showing that they owe approximately $4 and warning of a $35 late payment fee.
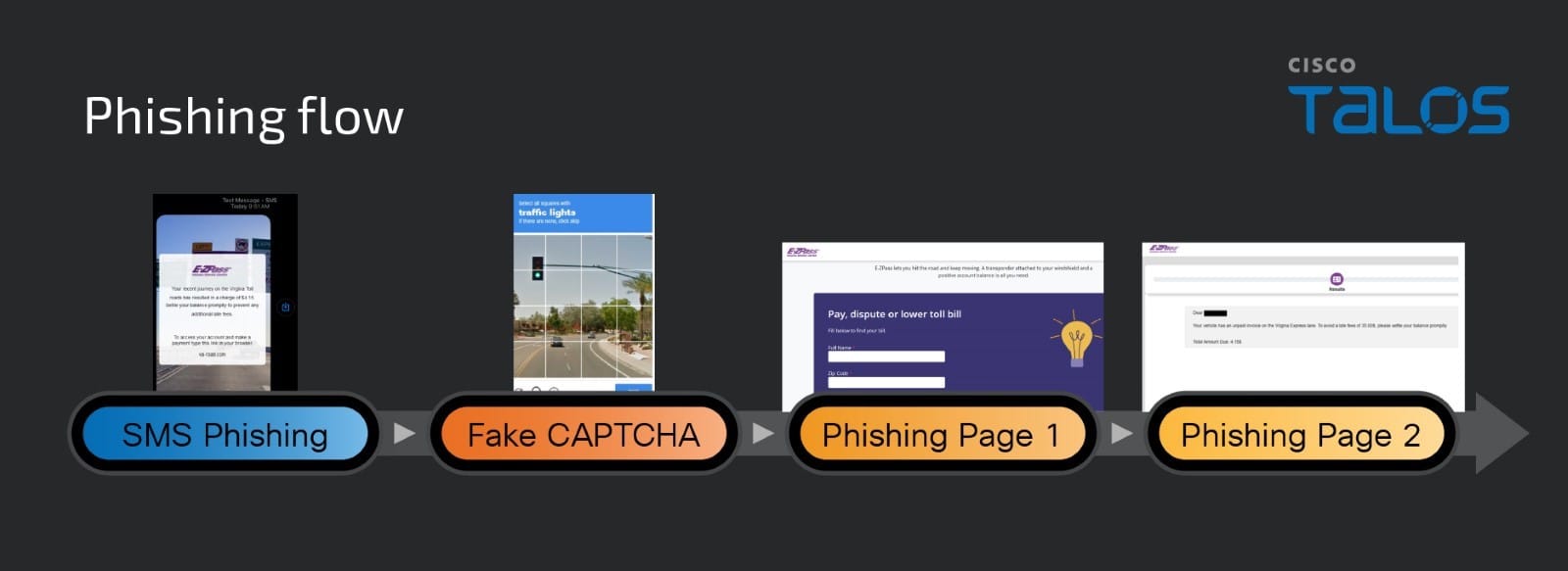
After the victim views their fake bill, they click the “Proceed Now” button which redirects them to another fake webpage. This site prompts the victim to enter their name, address, phone number and credit card information, which the threat actor eventually steals. Due to the limited visibility of the threat actor phishing infrastructure, Talos is unsure if there are any further payloads delivered to the victims' devices.
In April 2024, FBI’s Internet Crime Complaint Center (IC3) warned about a similar toll road smishing campaign where the threat actor used the same brand impersonation technique but with a slight difference in the SMS message language, monetary values and formatting.
Targeting toll road users in multiple states indicates the likelihood of the threat actor leveraging user information publicly leaked from large databases. For example, the threat actor behind the 2024 National Public Data leak released billions of records publicly which were then shared on private Telegram channels for further abuse. However, Talos currently does not have any evidence to suggest that the toll road smishing campaign is fueled by the National Public Data leaks.
Phishing infrastructure
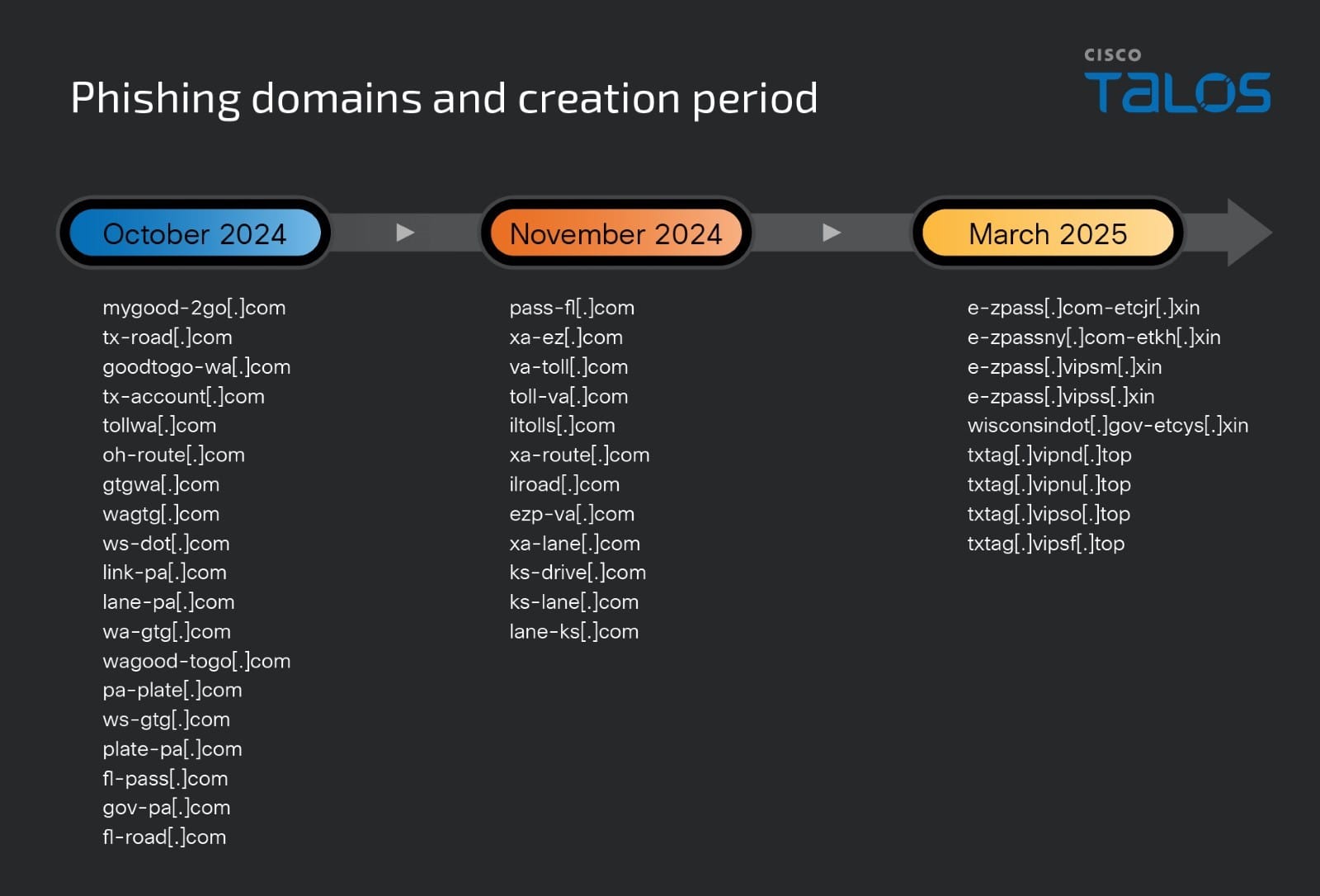
Talos observed that the actors have used several typosquatted domains in the SMS phishing messages to convince the potential victims to visit them. These typosquatted phishing domains were created during Oct. and Nov. 2024 and were observed resolving to one of the following IP addresses: 45[.]152[.]115[.]161 and 82[.]147[.]88[.]22.
As of March 2025, Talos is still seeing new domains registered by the threat actors for the toll road scams, implying that the campaign is ongoing. During our research period, these newly registered domains resolved to the IP address 43[.]156[.]47[.]209.
Smishing kits likely used in the U.S. toll road scams
Talos assesses with moderate confidence that multiple threat actors are operating the toll road smishing campaign by leveraging a smishing kit developed by the actor known as “Wang Duo Yu", according to the intelligence obtained by Talos.
We have observed similar smishing kits being used by the organized cybercrime group known as the "Smishing Triad." This group has conducted large-scale smishing attacks targeting mail services in multiple countries, including the United States Postal Service (USPS), as well as the financial and commercial sectors previously reported by Resecurity.
Talos discovered references to specific phishing kits that are targeting toll systems in the DY Tongbu Telegram channel on "老王同步源码开发教学" translated to "Lao Wang Synchronized Source Code Development Tutorial."
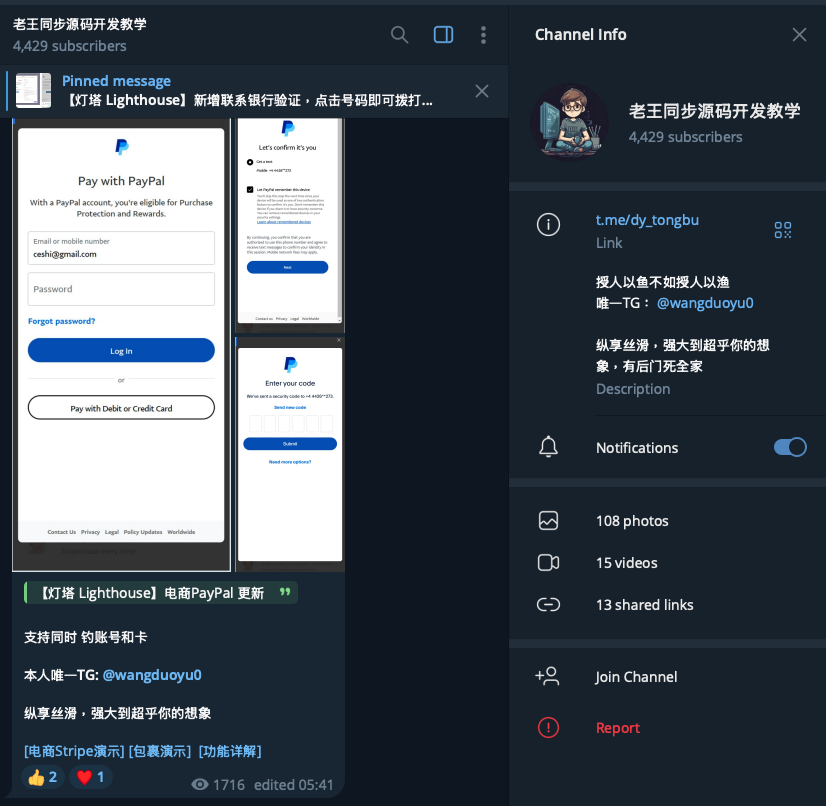
The Telegram channel shared details about a phishing module that allegedly spoofs the Massachusetts MassDOT's EZDriveMA toll system, as well as a phishing module that targets customers of the North Texas Toll Authority. At the time of publication, the Telegram channel had more than 4,400 subscribers.
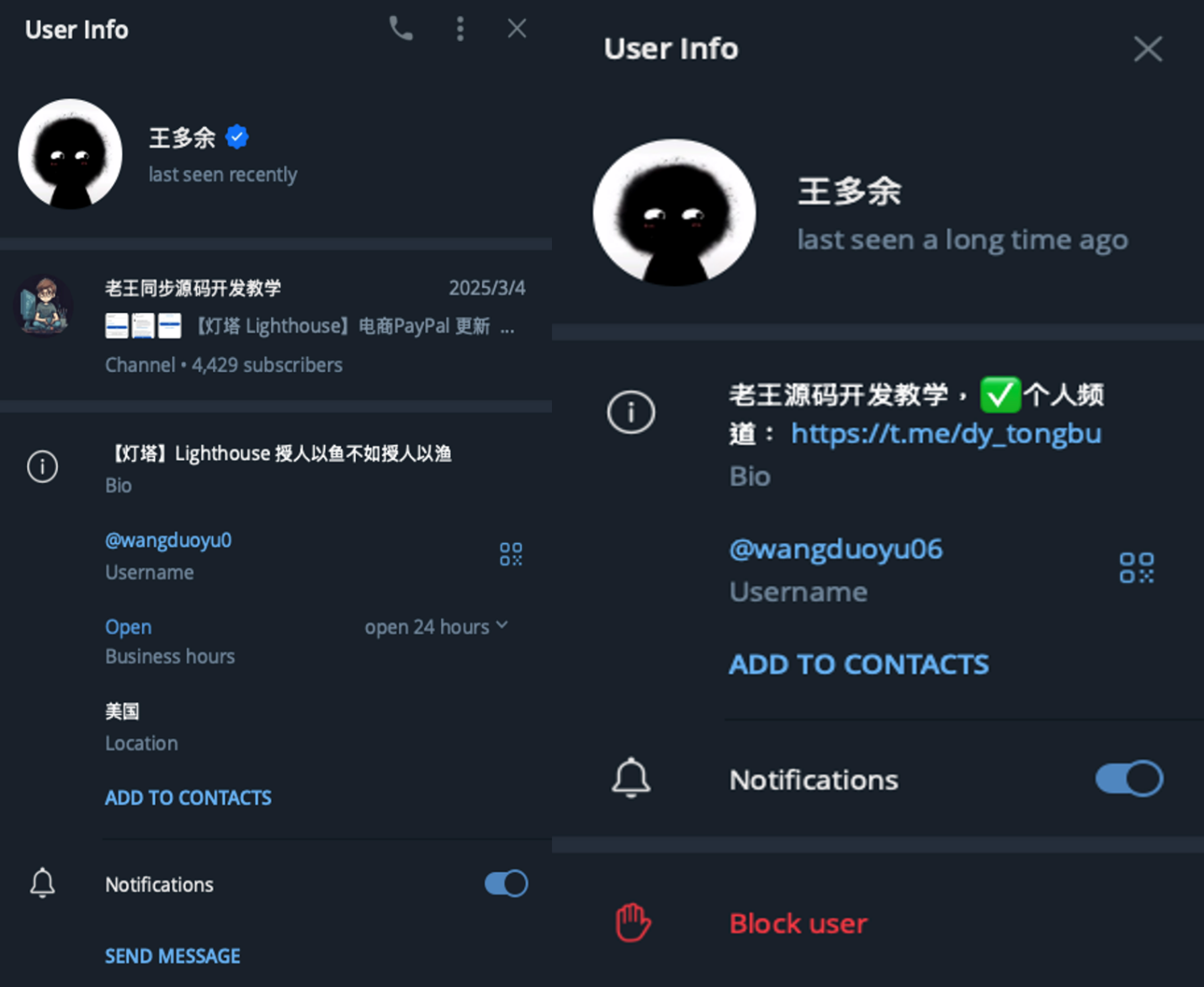
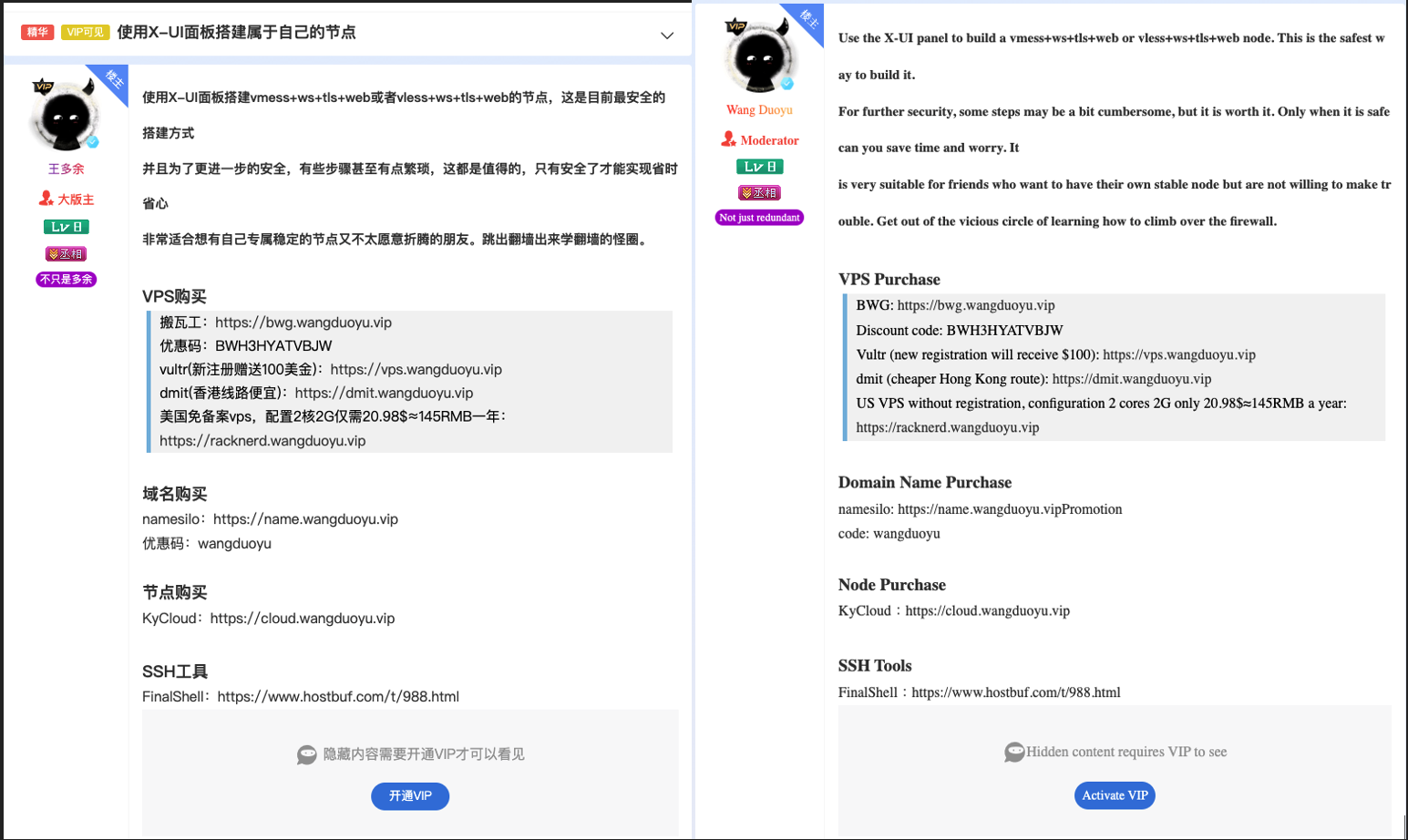
Further investigation has revealed that the developer, 王多余 (translated to Wang Duo Yu), has developed a similar smishing kit and operates the Lao Wang Synchronized Source Code Development Tutorial Telegram channel from two separate accounts. The pictures shown below display screenshots of the two telegram accounts related to Wang Duo Yu.
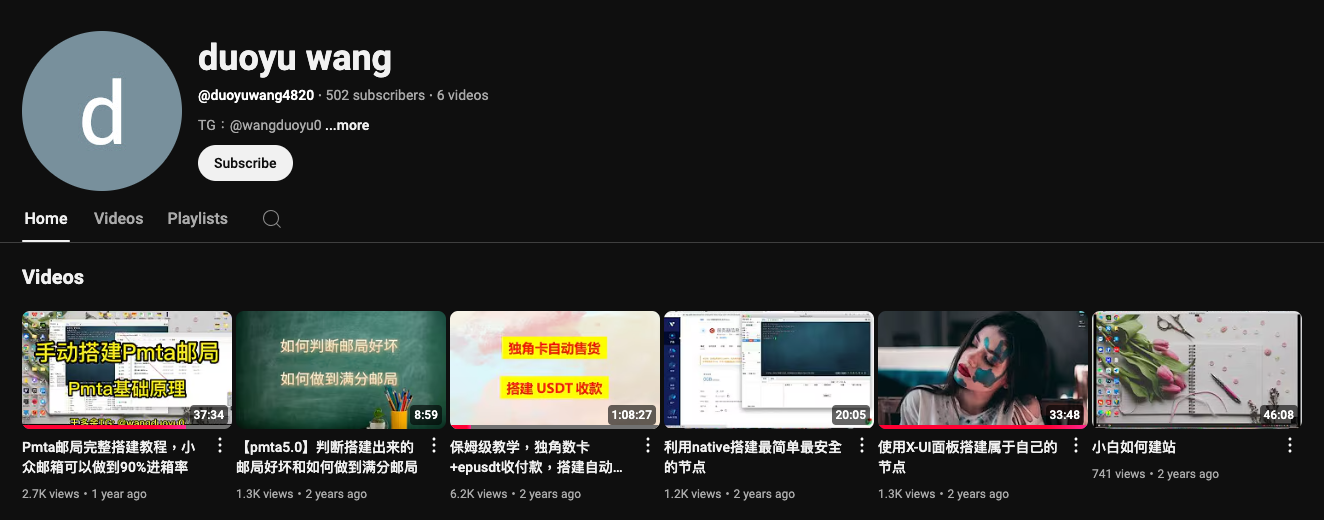
Additionally, we noticed that the developer has created a YouTube channel where they upload tutorial videos. These videos cover topics such as "How to Build a PMTA Mail Server," "Setting Up an Automatic EPUSD Payment and Vending System," "Creating a Pagoda Panel Website (宝塔面板)," "Building the Simplest and Safest Node Using Native Tools," and "Using the X-UI Panel to Set Up a VMess+WS+TLS+Web or VLess+WS+TLS+Web Node." Each video guides users on building basic web services or mail servers.
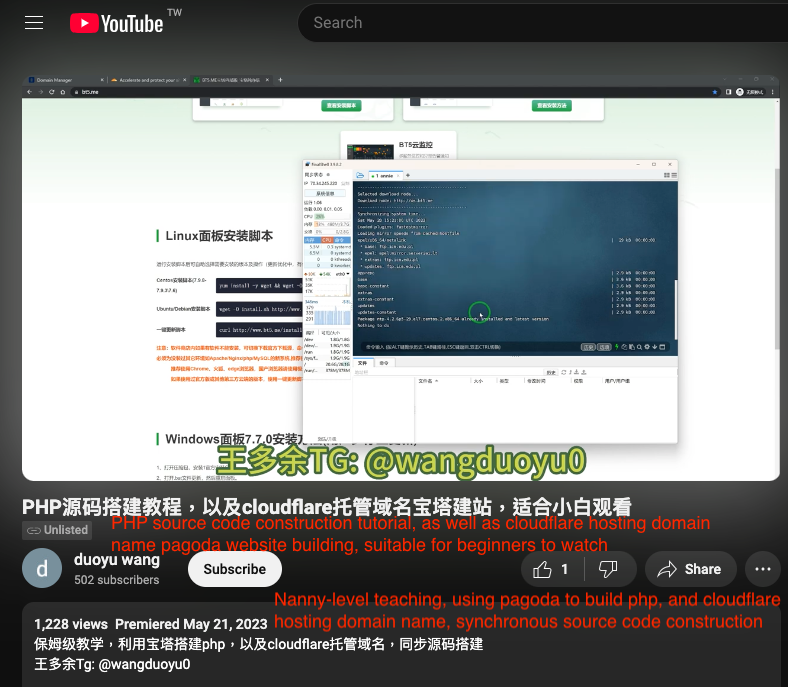
There are also some private video links that cannot be found elsewhere. Talos found one such video on a Chinese forum. To access the post with the video link, users need special permissions in that forum.
We also observed Wang Duo Yu promoting their smishing kits business and tutorials on other Telegram channels, also offering personal lessons that include full-stack development, mail server setup and Telegram bot development. The threat actor offers a two-hour lesson each day and provides one-on-one instruction via remote desktop, charging ¥5888 (converting to approx. US $806 at time of publication) per class.
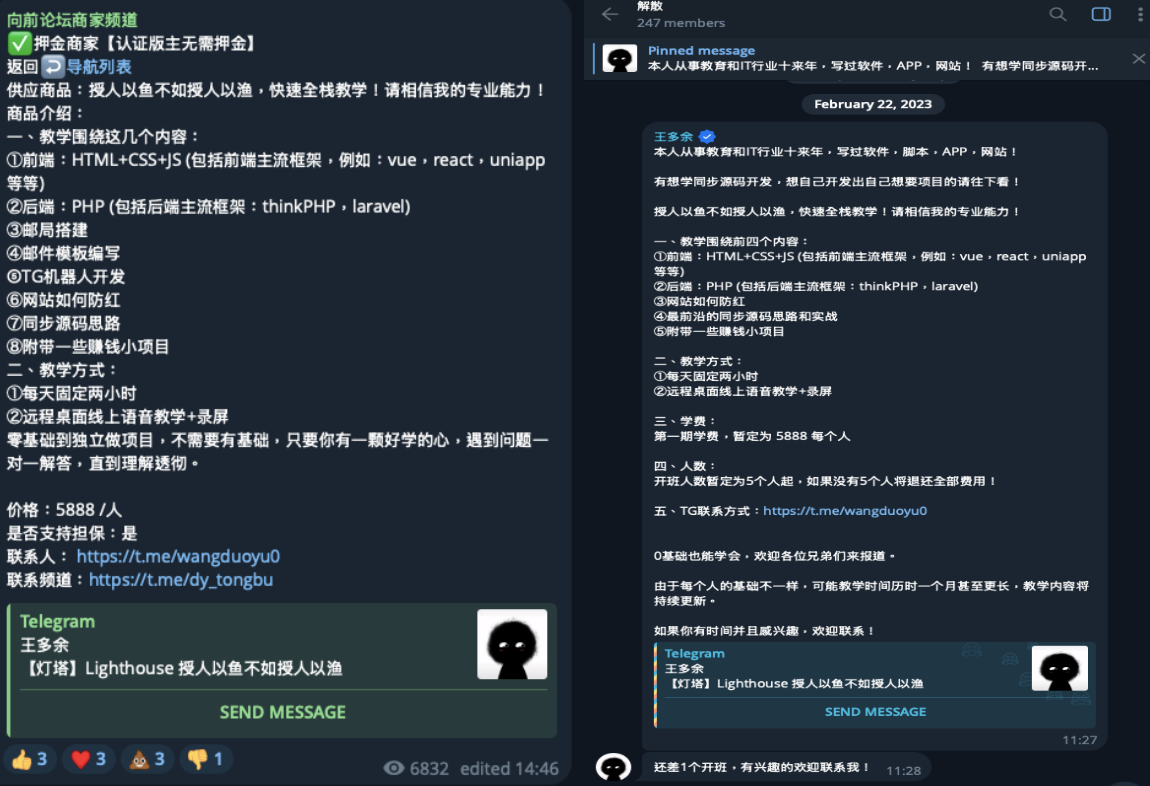
One of the Telegram channels shown in the above picture is called, “向前论坛,” translating to " Xiangqian Forum,” of which Wang Duo Yu is a moderator. Wang Duo Yu posted articles in this forum to increase subscribers, promoted their own teaching courses, and provided links and discount codes for purchasing VPS and domains.
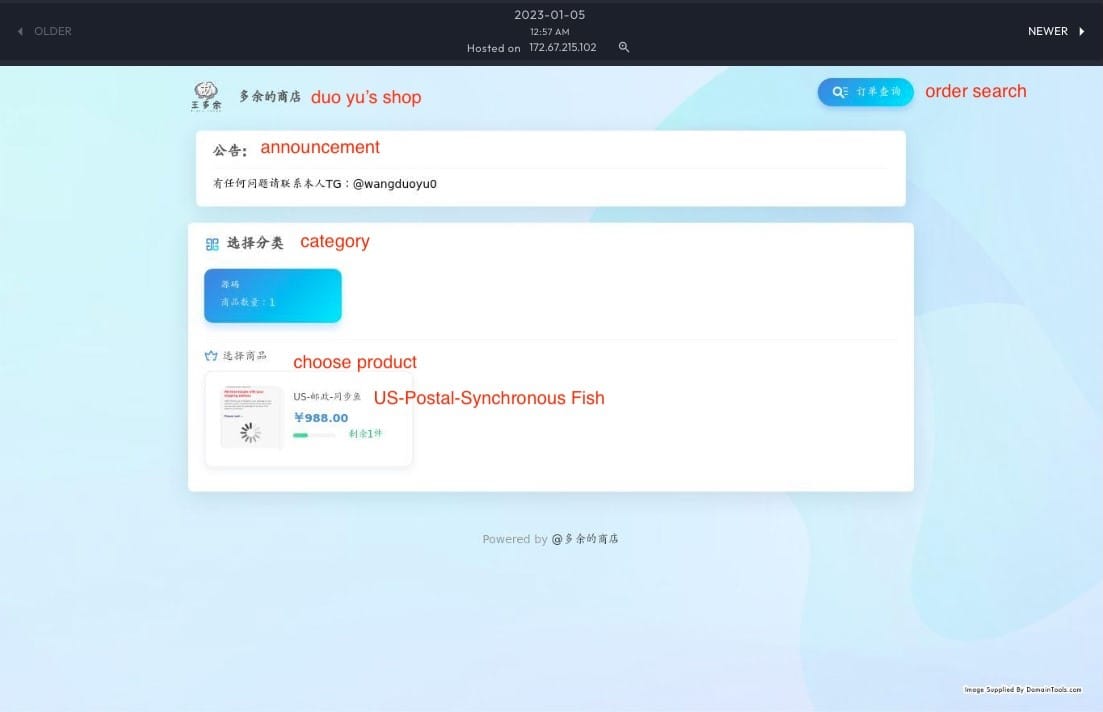
We also found an additional website selling the VPS and cloud services, confirmed to be owned by Wang Duo Yu. The “wangduoyu[.]vip” website was active from 2022 to 2023.
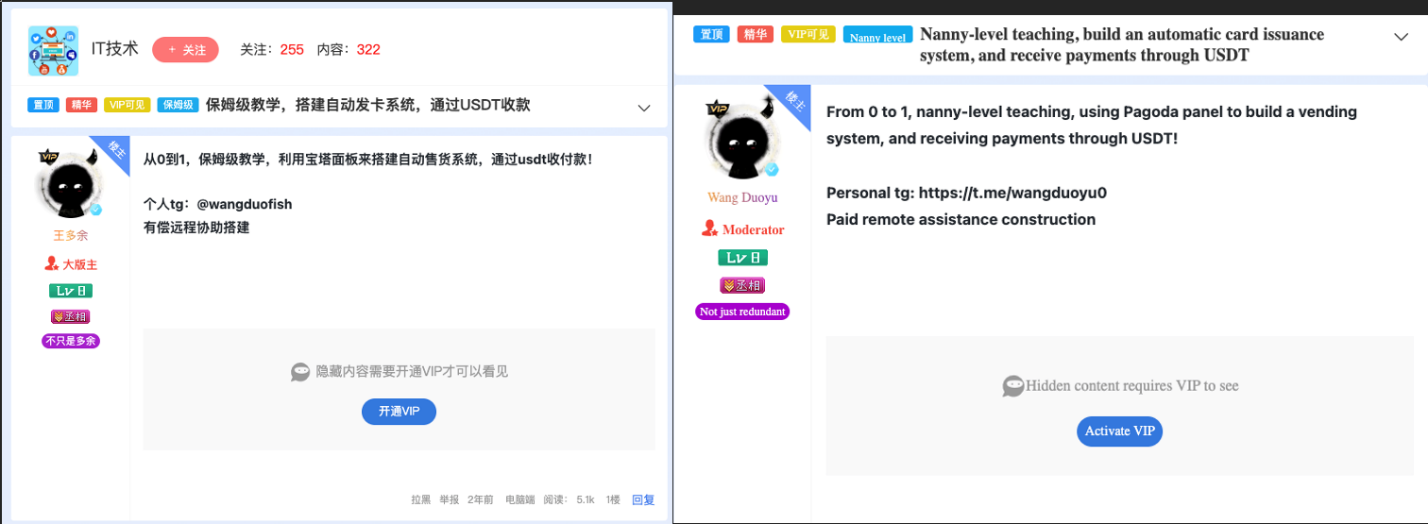
We observed that Wang Duo Yu offers the toll smishing kit source code for sale and provides services to assist in setting up the whole system. In a forum post, they stated that anyone interested can reach out to their personal Telegram account "@wangduofish". The post also includes hidden content only visible to users with VIP access.
Wang Duo Yu has crafted and designed specific smishing kits and has been selling access to these kits on their Telegram channels. The kits are available with different infrastructure options, priced at US $50 each for a full-feature development, $30 each for proxy development (when the customer has a personal domain and server), $20 each for version updates, and $20 for all other miscellaneous support. The threat actor also offers updated releases for multiple source code versions. The offers on the Telegram channel revealed that the smishing kits and source code primarily target large public-facing entities with a large end-userbase, such as toll road operators, banks and postal services.
Coverage

Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Network/Cloud Analytics (Stealthwatch/Stealthwatch Cloud) analyzes network traffic automatically and alerts users of potentially unwanted activity on every connected device.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Cisco Secure Access is a modern cloud-delivered Security Service Edge (SSE) built on Zero Trust principles. Secure Access provides seamless transparent and secure access to the internet, cloud services or private application no matter where your users work. Please contact your Cisco account representative or authorized partner if you are interested in a free trial of Cisco Secure Access.
Umbrella, Cisco’s secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them. Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Indicators of Compromise
IOCs for this threat can be found in our GitHub repository here.
