Cisco Talos recently discovered several vulnerabilities in InHand Networks’ InRouter302 that could allow an attacker to escalate their privileges on the targeted device from a non-privileged user to a privileged one. There are also multiple vulnerabilities that could allow an adversary to reach unconstrained root privileges. The router has one privileged user and several non-privileged ones.
The InRouter is an industrial LTE router that includes remote management functionalities and several security protection mechanisms, such as VPN connections and a firewall.
The router can be managed mainly in two ways: through the web interface, and through a router console accessible by telnet or, if enabled, SSH. The router does not provide access in any way to the Linux system beneath the router functionalities.
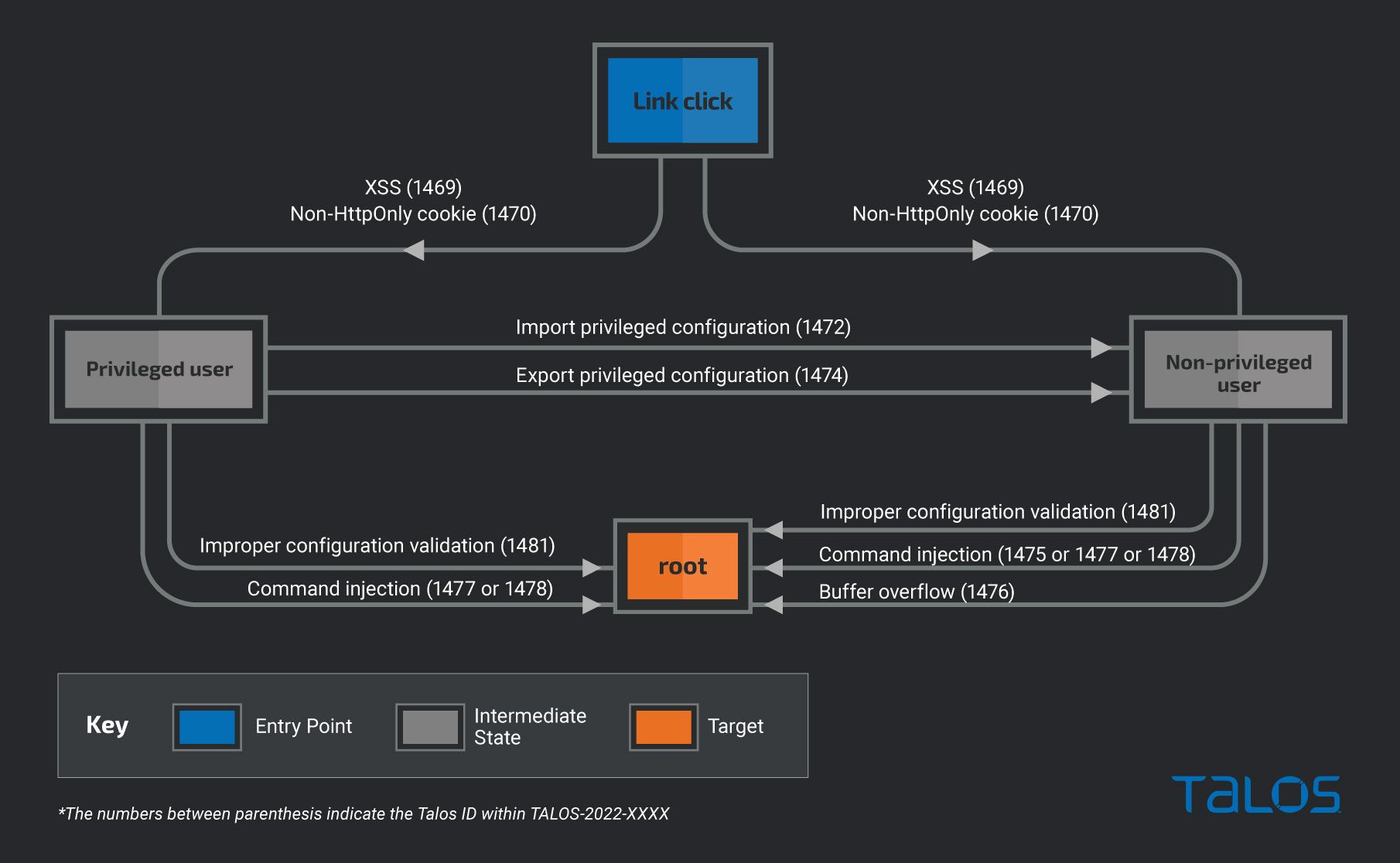
The chart below, which includes only a subset of all the discovered vulnerabilities, shows the different paths an attacker could take to obtain root access after the user clicks on an attacker-controlled link. It would be possible to chain the vulnerabilities discovered in several ways to obtain root access on the device:
Cisco Talos worked with InHand Networks to ensure that this issue is resolved and an update is available for affected customers, all in adherence to Cisco’s vulnerability disclosure policy.
To avoid the exploitation of these vulnerabilities, users are encouraged to update InHand Networks InRouter302, version 3.5.4 and 3.5.37 to version 3.5.45. Note that most vulnerabilities exist in both versions, however, several vulnerabilities are unique to 3.5.37 due to newly introduced functionality. See below for details. Talos tested and confirmed these versions are affected by these vulnerabilities. For more information on each of these issues, read their full advisories, which are linked in the blog post below.
Additionally, the following SNORTⓇ rules will detect exploitation attempts against this vulnerability: 59125, 59151, 59153, 59224-59225, 59247, 59270 – 59272, 59287, 59288, 59294, 59295 and 59414. Additional rules may be released in the future and current rules are subject to change, pending additional vulnerability information. For the most current rule information, please refer to your Cisco Secure Firewall Management Center or Snort.org.
Talos hypothesizes a scenario where the attacker would start the chain attack from a malicious link. This can be achieved through social engineering attacks, such as phishing.
If a victim clicks the malicious link their session cookie can be exfiltrated:
- TALOS-2022-1469, together with TALOS-2022-1470: The webserver uses for its web pages a template language. One of the web pages that use this template language executes one parameter set internally by the webserver as JavaScript during the handling of a request. These issues are related to the possibility to provide in the request the value of this parameter, effectively allowing to execute arbitrary JavaScript with an HTTP request. This enables an attacker to execute a cross-site scripting attack (XSS). Because no HttpOnly flag is set, the attacker could exfiltrate the session cookie, exploiting the XSS.
At this point, the attacker has either the cookie of a non-privileged user or a privileged one. In both scenarios, there are direct paths to root:
- TALOS-2022-1477: The router console, the binary users interact with when they SSH/telnet into the device, has a hidden command. When provided with a specific password, this command will spawn a root shell. The provided password is compared with a string that will be decrypted using AES, but because the AES key is in the library used, the encrypted password can be decrypted.
- TALOS-2022-1478: In the same hidden command within the router console, if a different password is provided, it will spawn a new binary. This binary is vulnerable to a command injection vulnerability, leading to the execution of OS commands as root.
- TALOS-2022-1481: It is also possible to upload a bulk router configuration. If the import is performed with this method, no check on the configuration entries value is performed. This leads to break assumptions where these values are used and can cause buffer overflows that can lead to remote code execution.
If the cookie exfiltrated is of a non-privileged user, and we do not consider that we can already obtain root from that level of privilege, the attacker can perform a privilege escalation to obtain the “privileged user” state:
- TALOS-2022-1472: The non-privileged user can upload the router configurations, change the privileged user password, and place its credential in a known state.
- TALOS-2022-1474: The non-privileged user can download the router configurations as a file. In it, there is the privileged user AES encrypted password, but because the AES password is contained in the library used by the device to encrypt and decrypt, the AES encrypted password can be decrypted by the attacker, that will obtain the privileged user credentials.
The privileged user can then perform more functionalities than the non-privileged user, but it still does not have access to the Linux system of the router. From the “privileged user” state, there are several vulnerabilities that lead to root and some, in common with the “non-privileged user” state, were discussed earlier. Still, the following ones are unique for the “privileged user”:
- TALOS-2022-1475: Inside the router console, there is a “privileged view” only accessible using the privileged user password. In this view, there is a hidden command that is vulnerable to command injection.
- TALOS-2022-1476: In the same hidden command within the router console, there is a buffer overflow vulnerability that can lead to remote code execution.
These examples show a few possible routes that these vulnerabilities could be leveraged to go from a single click to root access within the device. Once root access to the router is obtained any number of effects can be achieved including, but not limited to, injecting, dropping, or inspecting packets, DNS poisoning, or further pivoting into the network.
Additional vulnerabilities have been identified (TALOS-2022-1468, TALOS-2022-1471, TALOS-2022-1473, TALOS-2022-1495) that are not part of a chain shown:
- TALOS-2022-1468: An issue that allows an attacker to upload arbitrary files. With this capability, an attacker could perform several malicious actions. For instance, for both non-privileged and privileged users, the attacker could change the file that forces the router console to spawn when connecting to telnet or SSH, specifying instead to spawn a root shell.
- TALOS-2022-1471: This is a file-parsing issue. The functionality exposed starts the parsing of a file that is assumed to be a standard ping output. If an attacker has the ability to control the content of this file, they could trigger a buffer overflow that can lead to remote code execution. This vulnerability is reachable only by a privileged user.
- TALOS-2022-1473: If a specific web page is requested, a specific router configuration is taken and used as part of an OS command. Leading to command injection vulnerability.
- TALOS-2022-1495: The binary that manages the firmware upgrade only checks its CRC. Is possible, for both non-privileged and privileged users, to perform a firmware update with any firmware that has a valid CRC.
During our disclosure to the vendor a new firmware, version 3.5.37, was released, and we discovered TALOS-2022-1496, TALOS-2022-1499, TALOS-2022-1500, TALOS-2022-1501, in this new firmware. These problems are related to a new “privileged view” in the router console. The password for accessing it was hardcoded in the same way as TALOS-2022-1477. This view introduced new functionalities, although three of them contained command injection vulnerabilities.
TALOS-2022-1496 (CVE-2022-27172) is a vulnerability in the hard-coded password on the device, while the other three vulnerabilities all exist in different functions of the router’s software.