By Martin Zeiser.
Cisco Talos' Systems Security Research Team investigates software, operating system, IoT and ICS vulnerabilities to make sure we find vulnerabilities before the bad guys do.
We provide this information to the affected vendors so that they can create patches and protect their customers as soon as possible. We strive to improve the security of our customers with detection content, which protects them while the vendor is creating, testing, and delivering the patch. These patches ultimately remove the vulnerability in question, which increases security not only for our customers but for everyone.
After these patches become available, the Talos detection content becomes public, as well. Talos regularly releases Vulnerability Spotlights and in-depth analyses of vulnerabilities discovered by us. You can find all of the release information via the Talos vulnerability information pagehere.
Philosophy The focus of our work is to make sure our customers and their data stay safe. No matter the vulnerability we uncover, we contact and work closely with the software vendor to quickly and responsibly close any attack vectors we find. Our coordinated disclosure policy outlined below ensures the best possible approach to arrive at this goal.
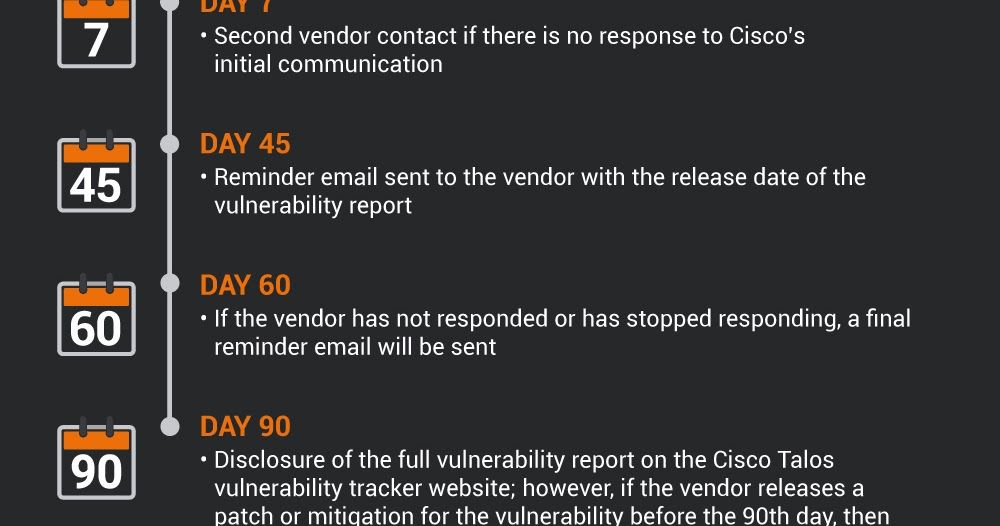
Timeline of actions to be taken by Cisco:

When it comes to closing security vulnerabilities before the bad guys exploit them, our track record proves our dedication to improving the security of our customers as well as the community. In fiscal year 2019, we published 228 advisories resulting in 237 CVEs, in a wide range of software including operating systems, internet-of-things devices, Microsoft Ofice products, PDF readers and more. This translates to almost one vulnerability discovered per working day in the last year.
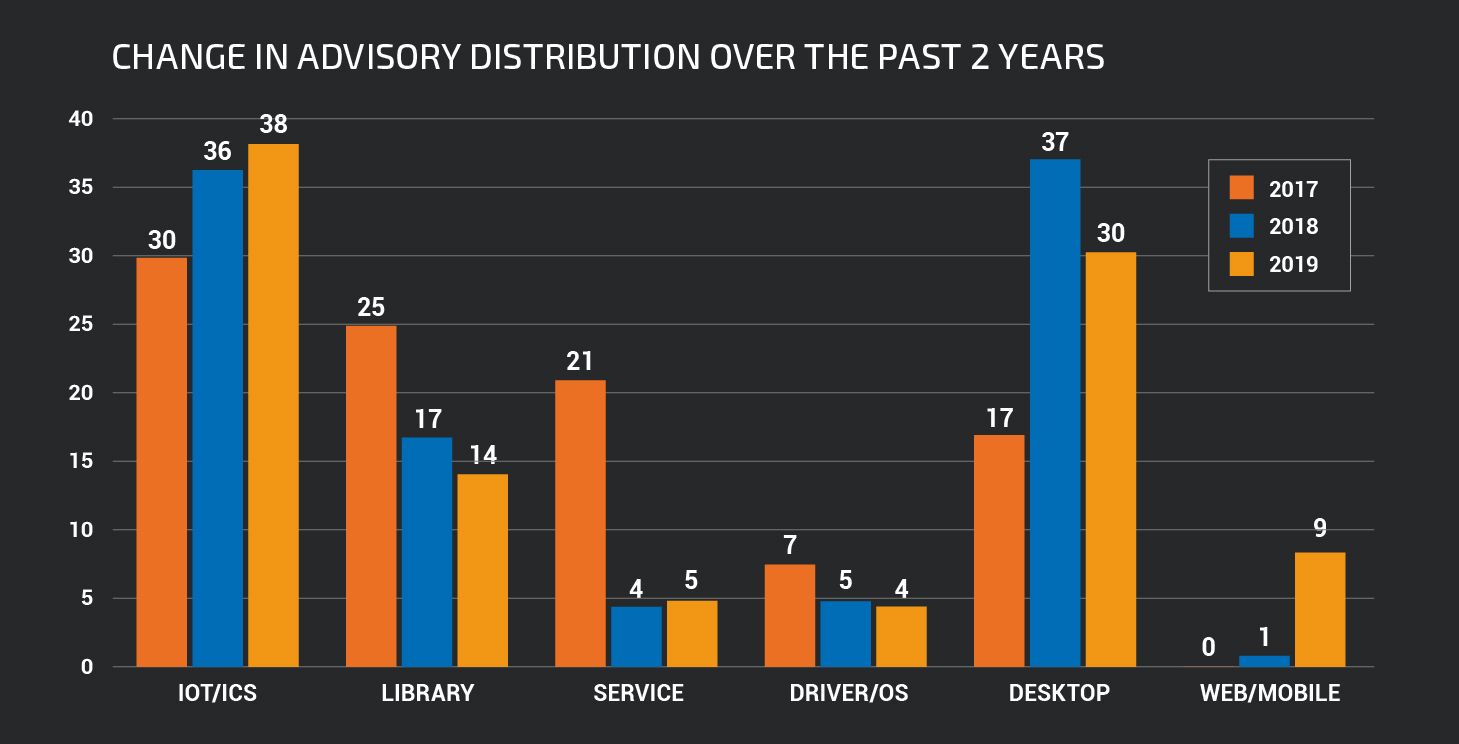
|
| Vulnerabilities discovered as percentage of total 2017, 2018, 2019 (August – July) |
While we do our best to increase coverage and thus the overall security of the Internet, bulletproof software just doesn't exist. Even vendors with large security teams make mistakes, and many don't even have those. In the end, this just means one cannot fully trust the devices on the network.
Some of our highlights from the past year:
- Multiple vulnerabilities in major PDF apps, including Adobe PDF, Foxit PDF, NitroPDF, Aspose PDF, Rainbow PDF and Google PDFium.
- Multiple vulnerabilities in each of these IoT/ICS devices: Google Nest Cam, Netgear N300 and the Nighthawk, Cujo Smart Firewalls.
- Multiple vulnerabilities in graphics drivers from Intel, Nvidia, AMD and Apple.
- More than 22 vulnerabilities in Schneider Modicon.
- Eleven vulnerabilities in Sierra Wireless 4G Gateway.
- Multiple vulnerabilities in various network routers, including from Linksys, TP-Link and Netgear.
- Various vulnerabilities in VMWare, Google V8, Windows and endpoint protection tools. Below is a breakdown of the amount of advisories we created grouped by product categories in 2019:
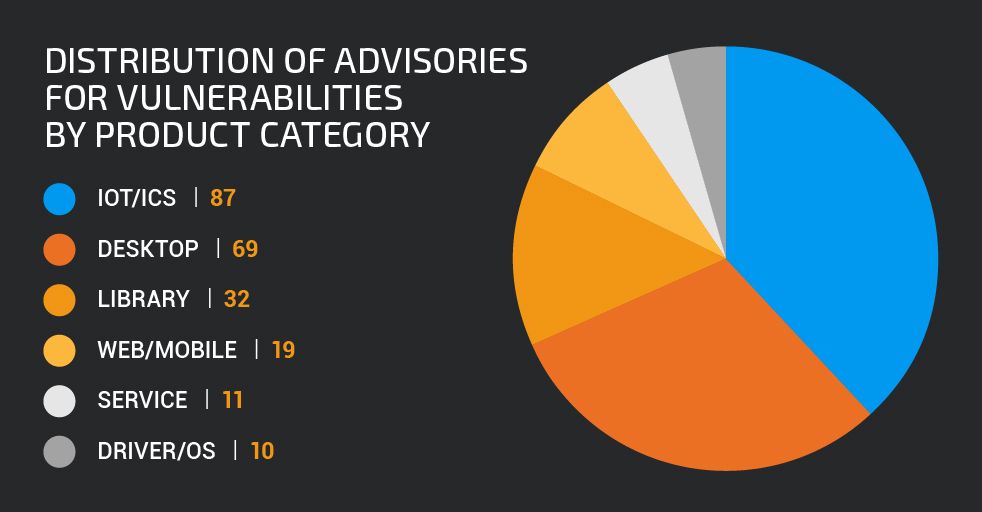
|
| Advisories by product category in 2019 |
Conclusion Talos' vulnerability research is all about closing attack vectors in software or products before malicious attackers find ways to exploit them. Working closely with vendors all over the planet, our coordinated disclosure policy ensures the best possible protection for our customers, while detection rules based on our work provide coverage where patches cannot help or have not yet been provided by a vendor. This approach has been securing networks for years now, while improving constantly, for the best possible protection and a more immune Internet.
For vulnerabilities Talos has disclosed, please refer to our Vulnerability Report Portalhere.
To review our Vulnerability Disclosure Policy, please visit this sitehere.