Discovered by Paul Rascagneres.

Overview
Cisco Talos has discovered two similar vulnerabilities in the ProtonVPN and NordVPN VPN clients. The vulnerabilities allow attackers to execute code as an administrator on Microsoft Windows operating systems from a standard user. The vulnerabilities were assigned to the CVE IDs TALOS-2018-0622 / CVE-2018-3952 (NordVPN) and TALOS-2018-0679 / CVE-2018-4010 (ProtonVPN).
The vulnerabilities are similar to a bug previously discovered by VerSprite in April 2018: CVE-2018-10169. That same month, both clients released similar patches to fix this flaw. However, we identified a way to bypass that patch. Despite the fix, it is still possible to execute code as an administrator on the system. The details section later on in this post will explain the first patch, why it was not successful, and how the editors finally fixed the problem.
Details
VPN clients' design
To understand the vulnerabilities, we first need to understand the design of the VPN clients mentioned in this article. Both clients have the same design:
- The user interface. This binary is executed with the permission of the logged-in user. The purpose of this application is to allow the user to select the VPN configuration, such as the protocol, the location of the VPN server, etc. The information is sent to a service when the user clicks on "connect" (it's, in fact, an OpenVPN configuration file).
- The service. This binary is used to receive orders from the user interface. For example, it receives the VPN configuration file from the user. The goal of the binary is to execute the OpenVPN client binary with the user configuration file (with administrator privileges).
The vulnerabilities in this article abuse the service and allow the standard user to execute arbitrary commands through OpenVPN with administrator privileges.
Initial vulnerability
The first vulnerability discovered by VerSprite is CVE-2018-10169. The author mentions he can create an OpenVPN configuration file with the following content:
plugin path\\OpenVPN_PoC.dll
This configuration file is sent to the service and will use this configuration for OpenVPN. The result is that OpenVPN_POC.dll will be loaded and executed by OpenVPN with administrator privileges.
First patch and limitation
ProtonVPN and NordVPN did the same patch. They implemented a control of the content of the OpenVPN configuration sent by the user:
if ( !text.StartsWithIgnoringCase("<tls-auth>") &&
!text.StartsWithIgnoringCase("<ca>") &&
OpenVpnConfigSecurityValidator.StartsWithName(text, "plugin") ||
OpenVpnConfigSecurityValidator.StartsWithName(text, "script-security") ||
OpenVpnConfigSecurityValidator.StartsWithName(text, "up") ||
OpenVpnConfigSecurityValidator.StartsWithName(text, "down")))
{
reason = string.Format("Invalid configuration file. Reason: {0}", text);
return false;
}
This code checks if the configuration file sent by the user contains a line starting by plugin, script-security, up or down. These are all the methods to execute code or commands through OpenVPN.
Here is the code of the check:
private static bool StartsWithName(string line, string name)
return line.StartsWithIgnoringCase(name + " ") ||
line.StartsWithIgnoringCase(name + "\t") ||
line.EqualsIgnoringCase(name);
}
The developer added additional tests to avoid tabulation or spaces before the keyword.
However, by reading the OpenVPN source code of the configuration file parser here, we can read in parse_line() function that a keyword can be between quotation marks. Therefore, we can add the following text in the configuration file:
"script-security" 2
"up" C:\\WINDOWS\\system32\\notepad.exe
It's valid for OpenVPN, and it passes the checks of the VPN services.
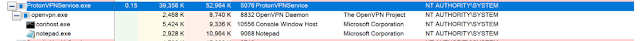
The service executes OpenVPN and it executes notepad.exe.
New patches
The new patches developed by the editors are different. For ProtonVPN, they put the OpenVPN configuration file in the installation directory, and a standard user cannot modify it. Thus, we cannot add the malicious string in it. For NordVPN, the editor decided to use an XML model to generate an OpenVPN configuration file. A standard user cannot edit the template.
More details can be found in the vulnerability reports:
- NordVPN report: TALOS-2018-0622 / CVE-2018-3952
- ProtonVPN report: TALOS-2018-0679 / CVE-2018-4010
Tested Versions:
- ProtonVPN VPN Client 1.5.1
- NordVPN 6.14.28.0
Coverage
The following Snort rules will detect exploitation attempts. Additional rules may be released at a future date, and current rules are subject to change, pending additional vulnerability information. For the most current rule information, please refer to your Firepower Management Console or Snort.org.
Snort Rules: 47035 - 47036
