Cisco Talos recently discovered multiple remote vulnerabilities in software that helps power Synology routers. The bugs exist in Synology Router Manager (SRM) — a Linux-based operating system for Synology routers — and QuickConnect, a feature inside SRM that allows users to remotely connect to their routers. An adversary could use these vulnerabilities to carry out a range of malicious actions, including executing remote code on the device, the exposure of sensitive information regarding the victim’s network and communication with other devices connected to the same network.
In accordance with our coordinated disclosure policy, Cisco Talos worked with Synology to ensure that these issues are resolved and that an update is available for affected customers. One of the vulnerabilities also affects the Qualcomm LBD service, and Qualcomm has also released an update for that.
While this post focuses on SRM which we did the research on, Synology has informed us that DSM was affected too for:
- TALOS-2020-1058 / CVE-2020-27648
- TALOS-2020-1059 / CVE-2020-27650
- TALOS-2020-1061 / CVE-2020-27652
- TALOS-2020-1071 / CVE-2020-27656
Paths to root around the world
We discovered multiple vulnerabilities that allow us to achieve unconstrained root privileges in the router. Additionally, we found that it was possible to remotely communicate with any router that was using the QuickConnect feature, and escalate our privileges to root.
As a small aside, in order to understand how the following vulnerabilities interconnect, it’s important to discuss QuickConnect. Normally if you wanted to manage your router remotely, you could make the web GUI port accessible from the WAN interface, and optionally also use a DDNS service (in case your Internet connection has a dynamic IP address) so that you could access the web GUI of the router remotely by just using your DDNS host. QuickConnect allows you to avoid all of this, and will put the router inside the QuickConnect VPN, exposing the web GUI through this tunnel and to an external URL like “http://quickconnect.to/quickconnectid”, where “quickconnectid” is chosen when the QuickConnect service is initially set up.
Back to the vulnerabilities discussion, the following schematic shows the different paths that an attacker could take to get root:
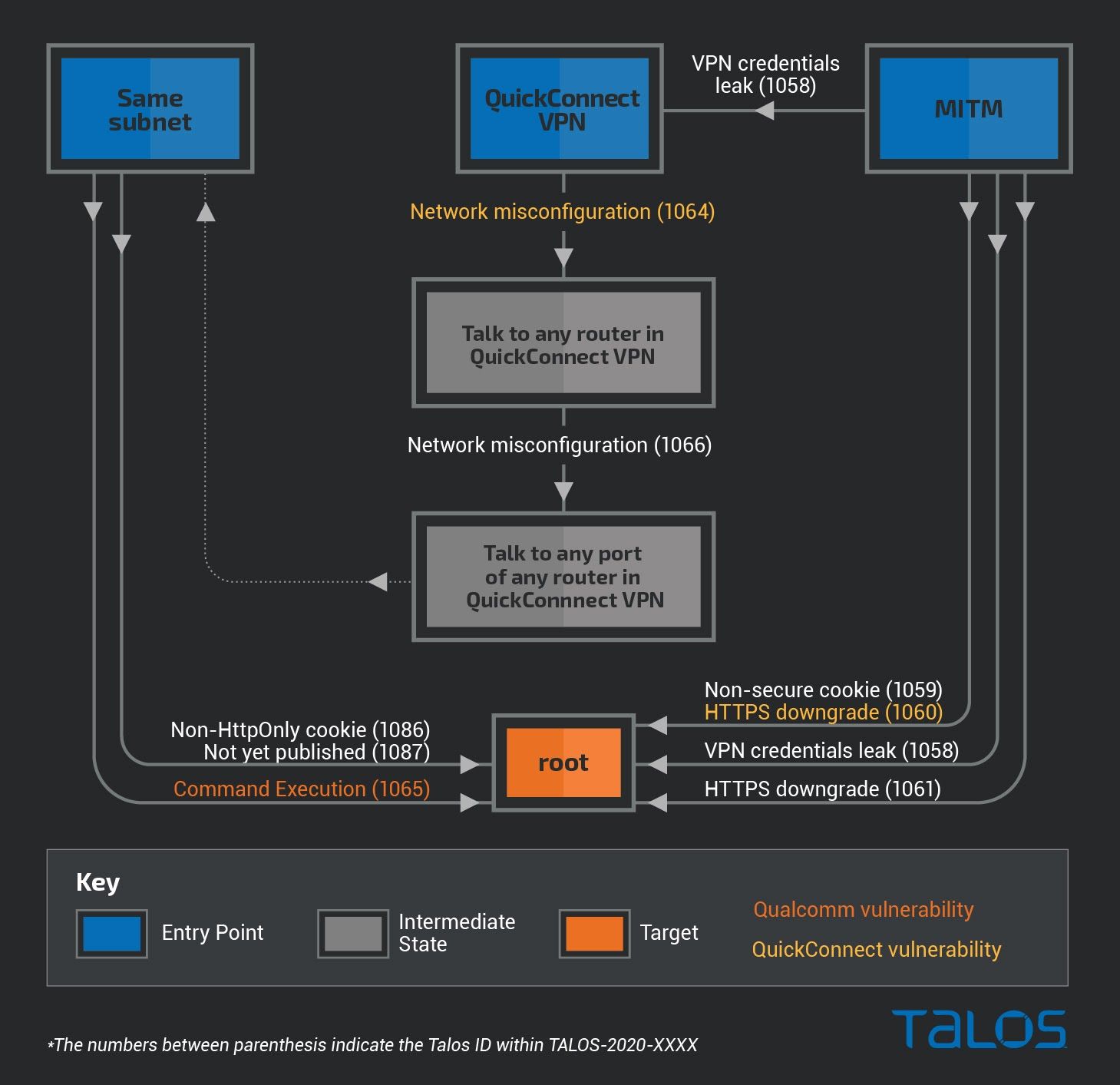
In this schematic, we hypothesize an attacker could start its attack from three different positions:
Same subnet: the attacker is in the LAN managed by the router. The attacker is “behind” the router, like in a classical home setup. In this schematic, we hypothesize an attacker could start its attack from three different positions:
- Same subnet: the attacker is in the LAN managed by the router. The attacker is “behind” the router, like in a classical home setup.
- QuickConnect VPN: the attacker is able to connect to the QuickConnect VPN. This can be done by purchasing a router and setting up a QuickConnect account. After we have a set of credentials, the router is not needed anymore and the connection can be performed by using openvpn manually.
- MITM: the attacker is able to perform a man-in-the-middle attack in the path between the router’s WAN interface and a target host on the Internet. This could be any other router in the path (e.g. an ISP), an attacker with the ability to DNS-poison, a compromised target host, etc.
Note that most of these issues allow an attacker to gain administrative privileges on the web interface. However, an administrator can enable ssh and log into the device as root, so being administrator in the web interface is equivalent to having unconstrained root privileges.
Looking at the schematic, if on the same subnet, an attacker can get root in two ways:
- TALOS-2020-1065: vulnerability in Qualcomm’s lbd, a service reachable via LAN on port 7786 and 7787, which can be used without authentication to directly execute shell commands as root.
- TALOS-2020-1086 together with TALOS-2020-1087: TALOS-2020-1086 shows that the web interface’s session cookie is missing the “httpOnly” flag, which allows for the administrator’s cookie to be read via JavaScript. TALOS-2020-1087 has not been published yet, and can be used in conjunction with TALOS-2020-1086 to obtain administrator’s access and in turn root privileges.
If the attacker is able to man-in-the-middle the WAN connection, an attacker has three ways to get root:
- TALOS-2020-1061: this vulnerability affects the router’s QuickConnect VPN connection, and can be used to force any HTTPS connection attempt to be downgraded to HTTP. This in turn allows an attacker to steal the session cookie for the web interface. The cookie will be sent in plaintext both on the router side and on the administrator’s browser side (because of the missing VPN cipher).
- TALOS-2020-1059 together with TALOS-2020-1060: these issues describe an HTTPS to HTTP downgrade that happens on the server side, while a user tries to connect to their router via QuickConnect. When connecting to QuickConnect a series of redirections happen, however one of those was forcibly happening via HTTP (even if the user started the request via HTTPS). The attacker can sniff the connection passively and steal the administrator session cookie, since there’s no “Secure” flag set.
- TALOS-2020-1058: SRM uses a modified version of openvpn to establish the QuickConnect tunnel, adding an option --syno-no-verify which allows it to connect without ssl verification. Despite the name, exploiting this issue requires several convoluted steps, so it’s best to read the advisory for details. Eventually, this can be exploited to steal VPN credentials and replicate a fake web user interface, that can be in turn used to steal administrator credentials.
As we can see from the schematic, the last vulnerability we discussed (TALOS-2020-1058) can also be used as an entry point to the QuickConnect VPN. Note that this is the entry point to a chain that allows an attacker to gain root privileges on any router connected to the QuickConnect VPN, remotely, without authentication.
In fact, since TALOS-2020-1058 allows for stealing VPN credentials, an attacker can simply use openvpn manually to connect to the VPN. Multiple routers around the world connect to the same QuickConnect VPN, but each router receives an IP in its own subnet and normally can’t speak to other subnets.
At this point, TALOS-2020-1064 demonstrates that the subnets are not logically split, in fact, an attacker, after connecting and having OpenVPN set its IP address, can change its netmask to a larger one, allowing it to talk with any other router connected to the same VPN.
Normally an attacker could also enumerate routers externally, for example by guessing QuickConnect IDs in the public URL (“http://quickconnect.to/quickconnectid”). Clearly, enumerating IPs in a smaller subnet is quicker and gives more results.
At this stage the attacker is in the “Talk to any router in QuickConnect VPN” state, and web interfaces for any router are reachable. In TALOS-2020-1066 we show that the VPN interface created by the device is unfiltered, so any service existing in the router (even those not even exposed via LAN) are exposed inside the VPN. his is equivalent to being in the same subnet as the target router, thus vulnerabilities like TALOS-2020-1065, TALOS-2020-1086 and TALOS-2020-1087 can be used to gain root privileges.
Two additional vulnerabilities have been identified (TALOS-2020-1051 and TALOS-2020-1071) that are not part of a chain, and are listed in the vulnerability list in the next paragraph.
Vulnerability details
Synology SRM DHCP monitor hostname parsing Denial of Service Vulnerability (TALOS-2020-1051/CVE-2019-11823)
An exploitable denial of service vulnerability exists in the DHCP monitor’s hostname parsing functionality of Synology SRM 1.2.3 MR2200ac 8017 and 1.2.3 RT2600ac 8017. A specially crafted network request can cause an out-of-bounds read resulting in a denial of service. An attacker can send a malicious packet to trigger this vulnerability.
Read the complete vulnerability advisory here for additional information.
Synology SRM QuickConnect authentication information disclosure vulnerability (TALOS-2020-1058/CVE-2020-27649)
A misconfiguration exists in AppArmor's synosearchagent profile of Synology DSM 6.2.3 25426 DS120j. A specially crafted kernel module can be loaded, leading to bypass of AppArmor's restrictions. An attacker can use insmod to trigger this vulnerability.
Read the complete vulnerability advisory here for additional information.
Synology DSM synoagentregisterd server finder out-of-bounds write vulnerability (TALOS-2020-1059/CVE-2020-27651)
An out-of-bounds write vulnerability exists in the synoagentregisterd server finder functionality of Synology DSM 6.2.3 25426 DS120j. A specially crafted HTTP response can lead to remote code execution. An attacker can man-in-the-middle the connection to trigger this vulnerability.
Read the complete vulnerability advisory here for additional information.
Synology QuickConnect servers HTTP redirection Information Disclosure Vulnerability (TALOS-2020-1060)
An exploitable information disclosure vulnerability exists in the HTTP redirection functionality of Synology QuickConnect servers. An attacker can impersonate the remote QuickConnect servers in order to impersonate the remote device and in turn steal the device's credentials. An attacker can perform a man-in-the-middle attack to trigger this vulnerability.
Because this vulnerability existed on Synology’s infrastructure, it was not assigned a CVE.
Read the complete vulnerability advisory here for additional information.
Synology SRM QuickConnect HTTP connection information disclosure vulnerability (TALOS-2020-1061/CVE-2020-27653)
An exploitable information disclosure vulnerability exists in the QuickConnect HTTP connection functionality of Synology SRM 1.2.3 RT2600ac 8017-5. An attacker can impersonate the remote VPN endpoint in order to downgrade the HTTPS connection to HTTP, allowing an attacker to capture the web interface communication and in turn steal the session cookies. An attacker can perform a man-in-the-middle attack to trigger this vulnerability.
Read the complete vulnerability advisory here for additional information.
Synology QuickConnect servers network misconfiguration vulnerability (TALOS-2020-1064)
An exploitable network misconfiguration vulnerability exists in the VPN servers of Synology QuickConnect. The server does not enforce proper subnetting, allowing an attacker to reach any device connected to the VPN. To abuse this vulnerability, the attacker needs to change their subnet.
Because this vulnerability existed on Synology’s infrastructure, it was not assigned a CVE.
Read the complete vulnerability advisory here for additional information.
Synology SRM lbd service command execution vulnerability (TALOS-2020-1065/CVE-2020-27654)
An exploitable command execution vulnerability exists in the lbd service functionality of Qualcomm lbd 1.1, as present in Synology SRM 1.2.3 RT2600ac 8017-5. A specially crafted debug command can overwrite arbitrary files with controllable content, resulting in remote code execution. An attacker can send an unauthenticated message to trigger this vulnerability.
Read the complete vulnerability advisory here for additional information.
Synology SRM QuickConnect iptables network misconfiguration vulnerability (TALOS-2020-1066/CVE-2020-27655)
An exploitable network misconfiguration vulnerability exists in the QuickConnect iptables functionality of Synology SRM 1.2.3 RT2600ac 8017-5. Packets originating from the QuickConnect VPN interface are not filtered, resulting in unrestricted communication with any network service running in the device.
Read the complete vulnerability advisory here for additional information.
Synology SRM dnsExit DDNS provider information disclosure vulnerability (TALOS-2020-1071/CVE-2020-27657)
An information disclosure vulnerability exists in the dnsExit DDNS provider functionality of Synology SRM 1.2.3 RT2600ac 8017-5. A specially crafted man-in-the-middle attack can steal the dnsExit credentials to take over the registered subdomain. An attacker can impersonate the remote dnsExit servers to trigger this vulnerability.
Read the complete vulnerability advisory here for additional information.
Synology SRM web interface session cookie HttpOnly flag information disclosure vulnerability (TALOS-2020-1086/CVE-2020-27658)
An exploitable information disclosure vulnerability exists in the web interface session cookie functionality of Synology SRM 1.2.3 RT2600ac 8017-5. The session cookie misses the HttpOnly flag, making it accessible via JavaScript and thus allowing an attacker to perform an XSS attack and steal the session cookie.
Read the complete vulnerability advisory here for additional information.
Versions tested
Talos tested and confirmed that TALOS-2020-1051, TALOS-2020-1158, TALOS-2020-1159,TALOS-2020-1061, TALOS-2020-1065, TALOS-2020-1066, TALOS-2020-1071 and TALOS-2020-1086 affect Synology SRM, version 1.2.3 RT2600ac 8017-5. TALOS-2020-1065 also affects Qualcomm LBD, version 1.1. TALOS-2020-1060 and TALOS-2020-1064 affect the Synology QuickConnect servers.
Synology confirmed that TALOS-2020-1058, TALOS-2020-1059, TALOS-2020-1061, TALOS-2020-1071 affect Synology DSM, version 6.2.3 25426.

Coverage
The following SNORTⓇ rules from an earlier rule release will detect exploitation attempts. Note that additional rules may be released at a future date and current rules are subject to change pending additional vulnerability information. For the most current rule information, please refer to your Firepower Management Center or Snort.org.
Snort Rules: 53755, 53756, 53839, 53840, 53959, 54009