Most users interact with the internet through the web, and many of the threat actors we write about operate on the “dark web.” Broadly speaking, the dark web is a small portion of the “deep web,” where the deep web represents most of the Web.
We know, it’s confusing — let’s walk through an example.
The surface web is what you get to see when using your favorite search engine. You can search for banks, and you will find (most likely) the website of your local bank. The results will include publicly accessible information about services they offer, their address or hours of operation.
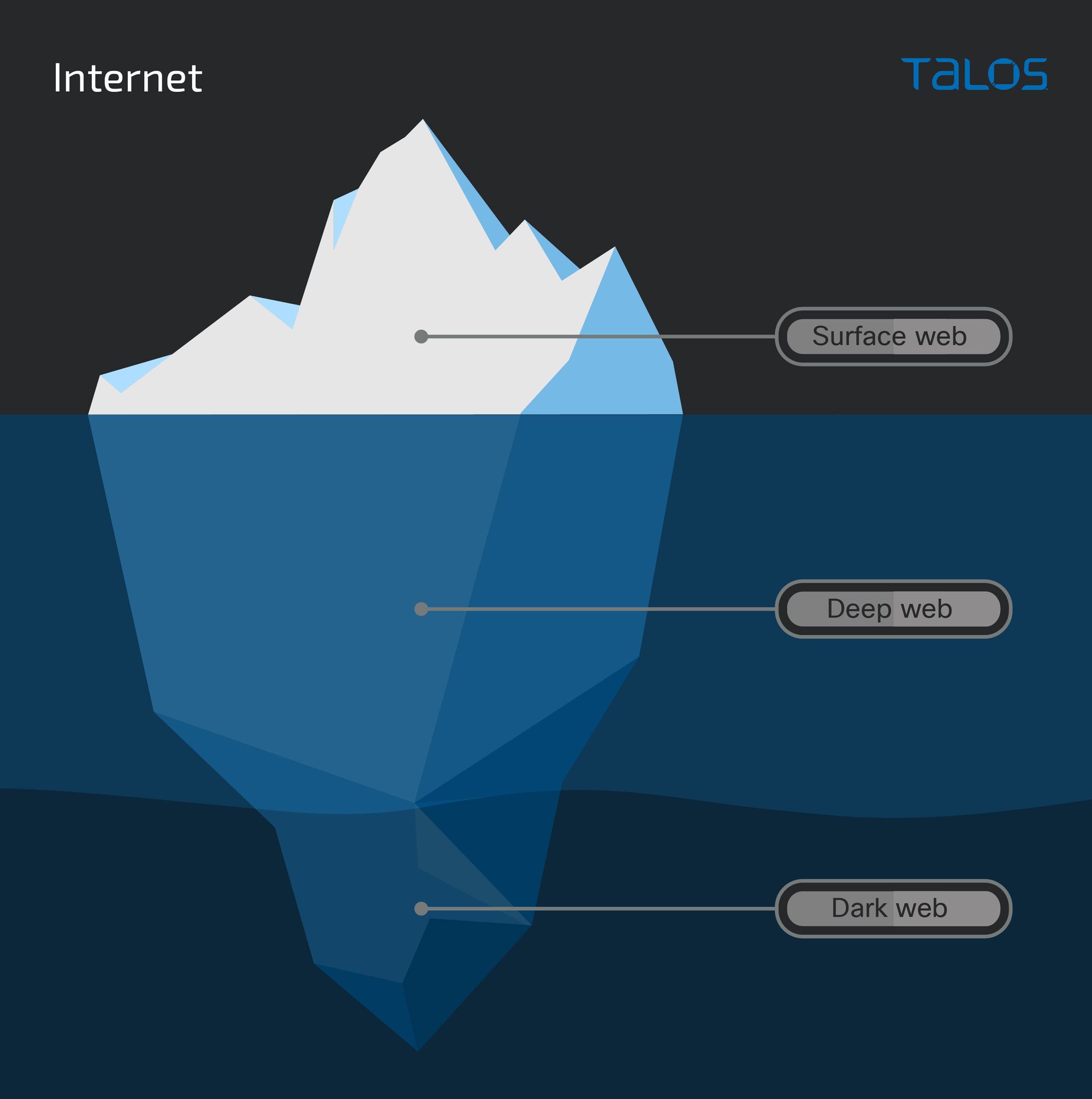
Then, there is a part of this web page you are only able to see after you log in. Your name, address, transactions and account balance. This is an example of the deep web. That is, information with restricted access (for good reason).
If a breach occurs, and this information is sold by an adversary, it will show up on the dark web. The dark web is intentionally hidden and just accessible by specific anonymizing software like Tor (The Onion Router), I2P (Invisible Internet Project), Freenet or ZeroNet. It is important to note that these technologies were/are developed for good, but criminals abuse them.
From torproject.org:
“Our mission: To advance human rights and freedoms by creating and deploying free and open-source anonymity and privacy technologies, supporting their unrestricted availability and use, and furthering their scientific and popular understanding.”
The easiest or most common way for a user to access the Tor Network is using the Tor Browser, an application based on Mozilla Firefox, but configured to route all traffic through the Tor Network, thereby enhancing users’ privacy and anonymity.
Tor works by sending traffic through three random relays in the Tor network. The last relay (exit relay) then sends the traffic out onto the public internet.
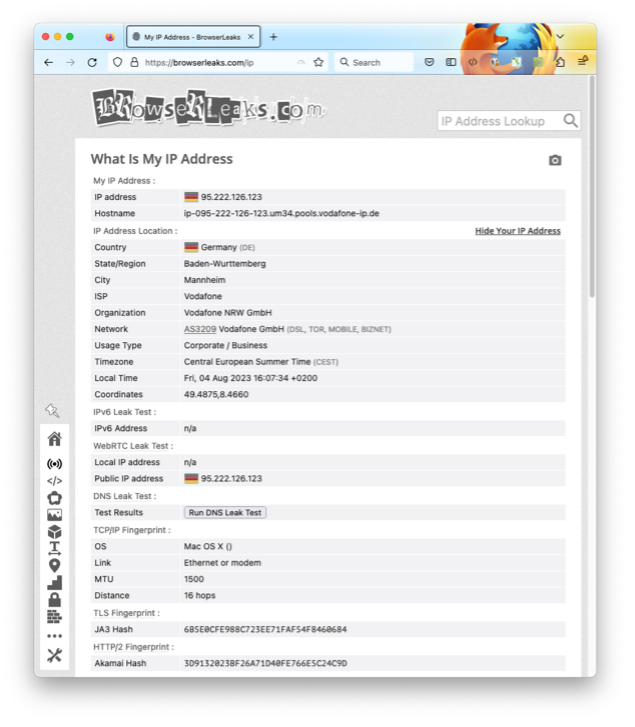
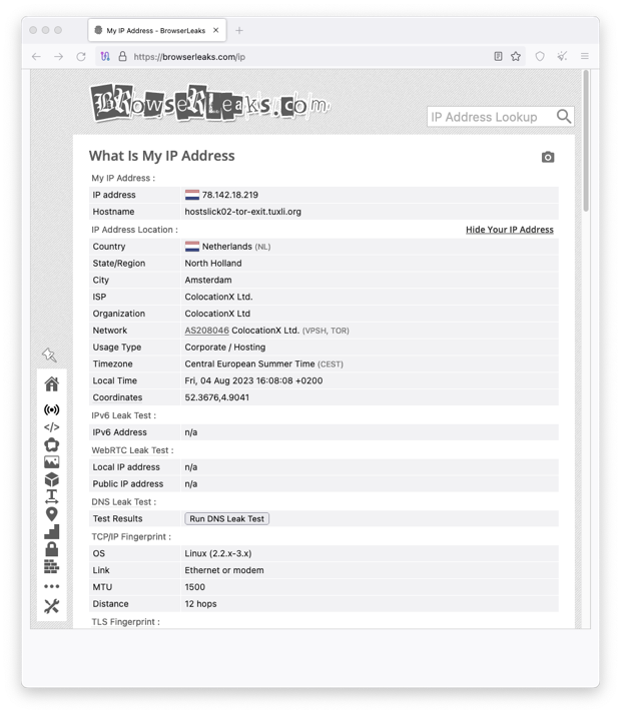
Tor also offers host services. Those webpages are then accessible by a .onion TLD, just inside the Tor network.
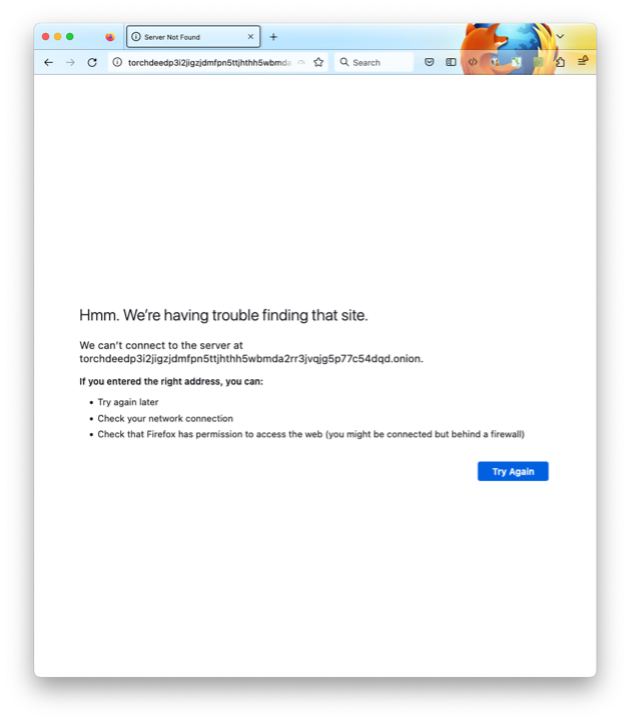

An example service is shown above. Torch is a search engine in and for the Tor network. Other examples are the BBC or New York Times, which make their pages available on Tor to thwart censorship.
The anonymity for consumers and publishers is interesting for adversaries, as it provides an additional layer of obfuscation which makes it harder for law enforcement agencies to track down transactions to a physical location. That’s why there are marketplaces and forums hosted for content such as malware, stolen credentials and alike, which are monitored by our teams.
While Tor provides a high level of anonymity and privacy, there are certain aspects of online activity that Tor does not fully protect against.
If you’d like to continue to learn more about the basics of the topics we cover on the Talos blog, read the rest of our entries in The Need to Know series.
