Summary
A recently disclosed vulnerability in F5 Networks' BIG-IP could allow an unauthenticated attacker to access the BIG-IP system to execute arbitrary system commands, create and delete files, disable services and could lead to additional malicious activity.
This vulnerability, tracked as CVE-2022-1388 is an authentication bypass vulnerability in F5's BIG-IP modules affecting the iControl REST component. BIG-IP is F5's line of appliances that organizations use as load balancers, firewalls, and for inspection and encryption of data passing in to and out of networks. The vulnerability has a CVSS score of 9.8 out of a possible 10 and is considered critical.
F5 discovered the vulnerability on May 4, 2022 and has subsequently released a security advisory and patches, along with a subsequent advisory from the U.S. Cybersecurity & Infrastructure Security Agency (CISA).
Cisco Talos is closely monitoring the recent reports of exploitation attempts against CVE-2022-1388 and strongly recommends users issue patches to affected systems as soon as possible.
Vulnerability details and ongoing exploitation
The threat stems from a faulty authentication implementation of the iControl REST, a set of web-based programming interfaces for configuring and managing BIG-IP devices. This vulnerability aims to target the iControl REST service with a path under "/mgmt" and relies on the specification of the X-F5-Auth-Token in the HTTP Connection header.
The vulnerability was assigned a CVSSv3 score of 9.8 out of 10. Cisco's Kenna Risk Score for CVE-2022-1388 is rapidly increasing jumping from 33 to 50 out of 100 in a 24-hour period and we expect the score to increase substantially as the vulnerability is exploited.
Over the last several days, proof-of-concept (PoC) exploit code has been circulating on Twitter and GitHub, underscoring the variety of ways the vulnerability can be exploited.
It is worth noting that even though most PoCs in the wild rely on the execution of commands through the "/mgmt/tm/util/bash", the vulnerability affects everything below the "/mgmt" path, which means other exploits may be developed. An adversary could also obfuscate their exploit code to avoid detection.
At the moment, Talos telemetry shows several verticals being scanned with the education sector seeing a slight increase. However, this is a developing situation and there are no indications that this activity is targeted.
Researchers are also noting that CVE-2022-1388 can be leveraged to drop web shells for prolonged backdoor access.
Guidance and mitigation
Given the severity of this vulnerability and that exploitation details have already been widely shared publicly, we strongly advise organizations to install available patches immediately and remove access to the management interface over the public internet. If organizations are unable to install updates, apply the mitigations provided by F5, which are listed below:
- Block iControl REST access through the self IP address
- Block iControl REST access through the management interface
- Modify the BIG-IP httpd configuration
Please refer to F5's security advisory for additional guidance and to determine if your product and version are known to be vulnerable. Security firm Randori has also provided a one-line bash script that BIG-IP users can use to check whether CVE-2022-1388 is exploitable on their instances.
Coverage
Ways our customers can detect and block this threat are listed below.
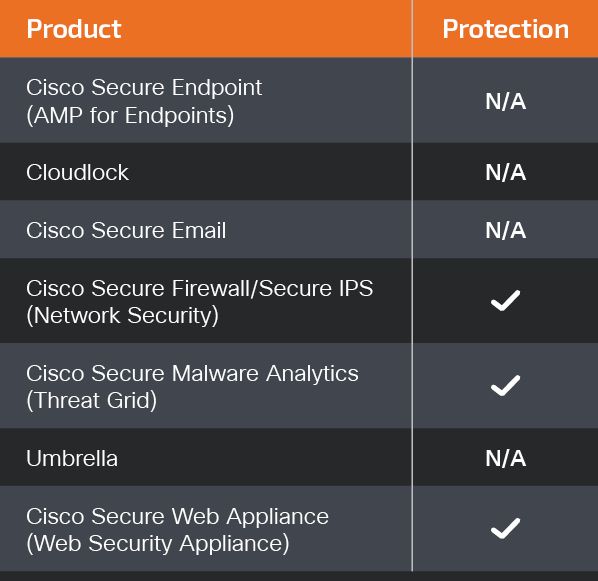
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Firepower Threat Defense (FTD), Firepower Device Manager (FDM), Threat Defense Virtual, Adaptive Security Appliance can detect malicious activity associated with this threat.
Cisco Secure Network/Cloud Analytics (Stealthwatch/Stealthwatch Cloud) analyzes network traffic automatically and alerts users of potentially unwanted activity on every connected device.
For guidance on using Cisco Secure Analytics to respond to this threat, please click here.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Secure Malware Analytics (formerly Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Talos provides the following Snort coverage for CVE-2022-1388:
- Snort 2 SIDs: 59735
- Snort 3 SIDs: 300131
IOCs
Below is a sample of attacker IPs, according to our telemetry:
5[.]189[.]191[.]107
29[.]104[.]233[.]152
41[.]79[.]198[.]18
45[.]61[.]139[.]143
45[.]79[.]171[.]157
51[.]159[.]66[.]249
52[.]74[.]130[.]60
53[.]85[.]187[.]67
58[.]213[.]200[.]67
64[.]39[.]106[.]34
64[.]39[.]108[.]98
64[.]39[.]98[.]152
64[.]39[.]98[.]159
64[.]39[.]98[.]196
64[.]39[.]98[.]227
64[.]39[.]98[.]40
66[.]254[.]159[.]252
66[.]94[.]126[.]14
68[.]183[.]202[.]236
69[.]24[.]129[.]229
72[.]166[.]5[.]40
72[.]167[.]51[.]207
79[.]18[.]33[.]4
81[.]69[.]58[.]15
82[.]80[.]33[.]200
87[.]20[.]54[.]33
88[.]226[.]109[.]164
91[.]36[.]121[.]76
94[.]177[.]118[.]79
103[.]144[.]149[.]206
103[.]144[.]149[.]49
103[.]177[.]174[.]34
104[.]208[.]85[.]237
104[.]244[.]72[.]174
107[.]189[.]29[.]64
109[.]205[.]176[.]248
113[.]23[.]27[.]104
113[.]67[.]10[.]13
119[.]140[.]78[.]118
12[.]172[.]214[.]26
120[.]170[.]212[.]254
120[.]245[.]25[.]3
121[.]196[.]223[.]32
122[.]161[.]50[.]64
122[.]75[.]182[.]121
124[.]160[.]154[.]32
128[.]199[.]16[.]44
132[.]145[.]21[.]77
137[.]184[.]236[.]99
139[.]99[.]149[.]66
141[.]11[.]28[.]89
141[.]11[.]28[.]97
144[.]202[.]124[.]151
144[.]202[.]59[.]76
144[.]76[.]251[.]214
145[.]215[.]56[.]53
149[.]28[.]147[.]208
150[.]230[.]38[.]225
156[.]146[.]34[.]98
157[.]245[.]115[.]135
157[.]245[.]200[.]184
157[.]245[.]206[.]99
159[.]89[.]182[.]71
161[.]35[.]156[.]235
161[.]35[.]158[.]59
161[.]35[.]209[.]168
161[.]35[.]232[.]12
163[.]143[.]106[.]199
163[.]32[.]193[.]116
164[.]90[.]205[.]93
167[.]172[.]83[.]249
167[.]172[.]83[.]250
167[.]172[.]83[.]251
167[.]99[.]225[.]132
172[.]104[.]15[.]189
172[.]70[.]126[.]146
172[.]70[.]131[.]167
172[.]70[.]131[.]47
172[.]70[.]222[.]71
172[.]81[.]129[.]138
174[.]138[.]22[.]187
175[.]107[.]236[.]67
178[.]62[.]228[.]64
180[.]236[.]169[.]125
181[.]214[.]206[.]31
185[.]147[.]212[.]58
185[.]212[.]61[.]84
185[.]239[.]226[.]177
186[.]80[.]52[.]118
188[.]68[.]61[.]6
189[.]37[.]76[.]246
189[.]46[.]90[.]233
193[.]29[.]15[.]143
194[.]163[.]164[.]206
194[.]163[.]185[.]138
194[.]195[.]219[.]144
194[.]195[.]86[.]50
194[.]233[.]171[.]91
194[.]233[.]77[.]245
194[.]5[.]73[.]6
196[.]65[.]108[.]171
198[.]211[.]120[.]110
198[.]252[.]101[.]110
204[.]195[.]115[.]184
206[.]189[.]200[.]122
207[.]180[.]241[.]85
208[.]71[.]210[.]1
209[.]58[.]170[.]164
210[.]92[.]18[.]153
212[.]102[.]50[.]210
217[.]252[.]7[.]13
223[.]187[.]119[.]114
223[.]72[.]39[.]119
226[.]137[.]152[.]105
250[.]100[.]25[.]148
253[.]240[.]199[.]27
103[.]85[.]25[.]79
156[.]34[.]23[.]233