Google's Threat Analysis Group published a blog Monday evening warning of an ongoing campaign attempting to compromise security researchers. Google TAG's blog outlines the attacker's motivations and various TTPs used in these attacks.
We can confirm that multiple Cisco Talos researchers received messages that appear to be linked to this campaign. As you can see below our researchers did not engage to the point where the malicious files were provided. As security researchers it is important that we follow our own best practices keeping samples and information tightly contained and isolated as much as possible.
This is not the first time Cisco and/or Talos has been targeted or used as a lure in this kind of campaign. Talos published research in 2019 detailing a campaign where fake Cisco job postings were used as a lure to point victims toward malicious web pages.
One of our researchers was contacted on Jan. 11 with the same lure as those already shared by Google and others. It is worth noting that the first thing the attacker inquired about was if the target was involved in vulnerability research.
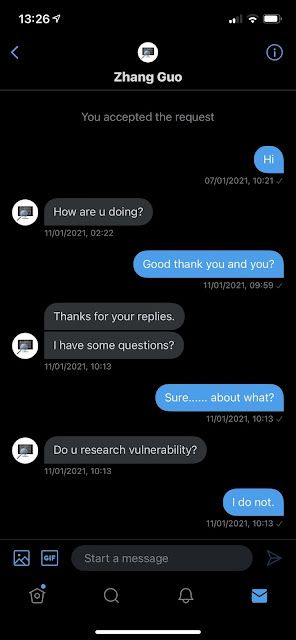
While the target affirmed that they were not involved in vulnerability research, the attacker continued their attempt to compromise them.
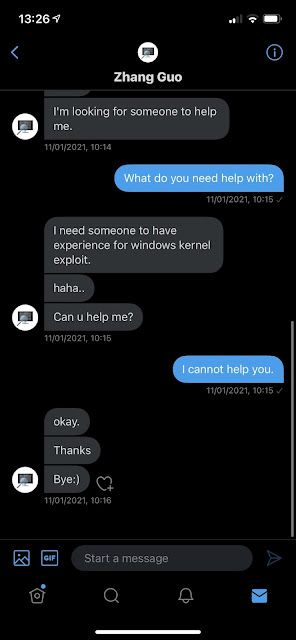
We have observed additional attempts to establish communication over other social media platforms, such as LinkedIn, but we cannot confirm with high confidence that those are related at this time. It's likely that multiple social media platforms are being used to initiate conversations with security researchers.
It is worth noting that the attacker has a good grasp of the English language and made contact within the normal working hours for the researcher based on their time zone, denoting some care regarding the quality of the lure.
There is a concept in emergency medicine called a "high index of suspicion". Some problems are hard to catch, so in order to diagnose them, you have to really be suspicious of what you see and go further than standard testing. Whether security researcher or CEO, some people have a higher than average risk of being targeted, even as compared to others in their company, so they have to have a higher index of suspicion than their peers.
This is why it is important to remain vigilant as a researcher — your work is not only read and digested by these threat actors, you can also be a potential target for state-sponsored actors that carry out these attacks. Researchers should be encouraged to follow best practices and only conduct research in safe environments. This includes isolating samples and projects from each other in the event one has been backdoored by a nefarious party. These types of campaigns are likely more popular than we realize and as defenders, we must remain vigilant.