By Nick Biasini
In the age of meme stocks, Robinhood and Elon Musk's tweets influencing the global economy, cryptocurrency mining has not seemed as fringe as it once did. Mining has been around as long as these crytocurrencies have, but only really started to gather the attention of criminals in late 2017. At the time, cryptocurrency value was surging, hitting previously unattainable values. At a time when the pre-big game hunting version of ransomware was starting to wane, malicious cryptomining was there to take up the slack, but researchers wondered if it had staying power.
The value of cryptocurrencies are extremely volatile. Bitcoin, the pseudo godfather of cryptocurrencies, experienced a 30 percent drop in its value over the course of 24 hours in May. But it also hit an all-time high value a month prior. Online adversaries are always looking for ways to make money, and cryptocurrency miners are some of the quickest ways attackers can infect a targeted machine, and sap users' computing power to mine for these virtual currencies to generate income.
So this led us to wonder: Does the volatility of cryptocurrencies influence the volume of cryptocurrency miners in the wild? It stands to reason that the more a cryptocurrency is worth, the more likely an attacker would be to want to mine for it. As we've seen the value of these currencies skyrocket recently we began to dig into the data.
The biggest facilitator to this research is the value of the currencies themselves. With more traditional payloads like RATs or banking trojans, it's tough to assign a monetary value to the payload, as a lot depends on the victim and the attacker's capabilities. Illicit cryptomining is one of the few payloads where the monetary gain is directly tied to tangible value. With this in mind, we set out to try and see if the value of virtual coins changes actors' behavior.
Process At first glance, this seems like a relatively straightforward question, but it required a bit of digging. It's simple enough to go online and look at the value of cryptocurrencies, but the bigger question is: How do you track an industry with hundreds of coins and new ones appearing almost daily? We found the answer in our breadth of research from the past several years. We've covered cryptomining extensively, including finding several large-scale campaigns generating millions of dollars and the majority favored one specific cryptocurrency, Monero.
Monero is a favorite for illicit mining for a variety of reasons, but two key points are: It's designed to run on standard, non-specialized, hardware, making it a prime candidate for installation on unsuspecting systems of users around the world, and it's privacy focused. As we've seen recently, not all cryptocurrencies have the same privacy protections and the protections afforded by Monero. Below, you'll see the value of Monero tracked since 2018. This is the starting point for our research.
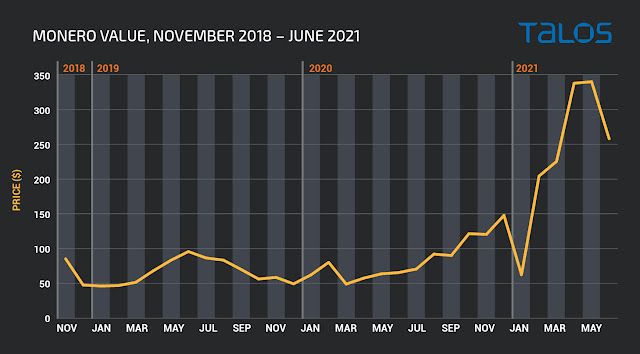
The value of Monero has fluctuated pretty significantly over the past several years, but you can see that in late 2020 and early 2021, the price really started to skyrocket, with a more recent pullback in value in June. This is one of the hallmarks of cryptocurrencies — their values can shift often and change from one extreme to the other. The previous high values associated with the initial rise in cryptomining have been dwarfed by the meteoric rise in the beginning of 2021. Note that for this graph, we averaged out the daily values so that the graph looks a little cleaner. The actual volatility is far more pronounced when you look at it on a day-to-day basis.
Next, we needed to figure out an efficient way to track the amount of cryptocurrency mining activity. After some careful consideration, we decided to rely on network-based detections. Cryptomining is typically done in the clear (non-encrypted) on the wire and, therefore, can be detected. It also ensures that the cryptominer is properly installed and functioning, since it's generating the applicable network traffic. Fortunately, our network IPS/IDS has had cryptomining detection available for years. For the purposes of tracking the mining detection, we tracked the rate that certain SNORTⓇ rules targeting cryptominers fired.
The first thing we noticed is that, no matter what, cryptomining is extremely popular. Even at its lowest point, we were seeing millions of events associated with cryptomining activity. We were also floored to see how much mining activity has risen since we first started writing about this in 2018. Today, we see more than double the volume we were observing several years ago.
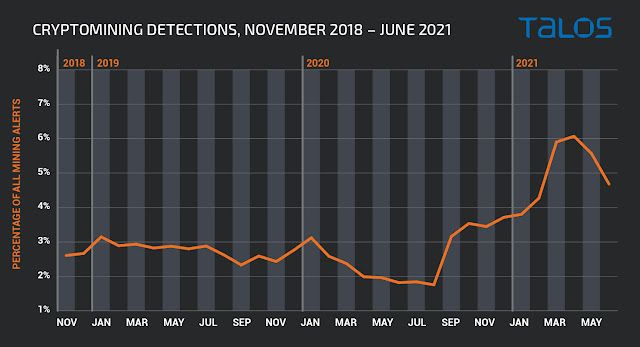
At first glance, it appears that the mining activity does have some dependence on the value of the currency. The most cryptomining activity we've ever seen has occurred in the last couple of months when Monero hit its all-time high.
Outside of the short price drop that occurred in early 2021, before the massive spike, the graph tracks almost identically to the value of the currency. This was honestly a pretty surprising correlation since it's believed that malicious actors need a significant amount of time to set up their mining operations, so it's unlikely they could flip a switch overnight and start mining as soon as values rise. This may still be true for some portion of the threat actors deploying miners, but based on the actual data, there are many others chasing the money.
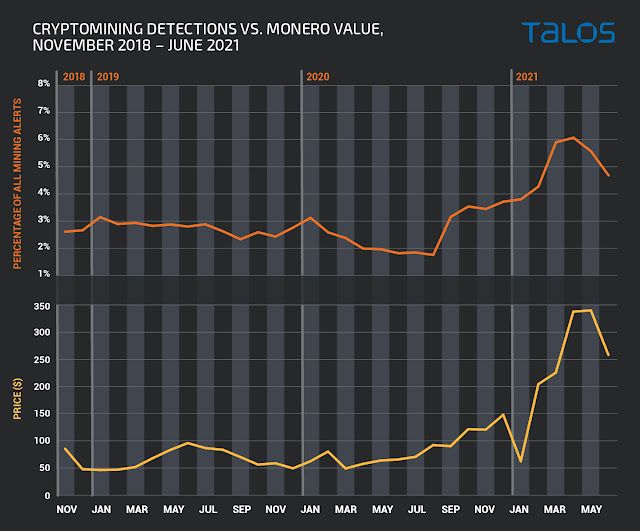
Implications This appears to be some of the clearest evidence yet that cyber criminals are opportunistic. The majority of these actors are motivated by one thing and one thing only: money. And they will follow it wherever it goes.
For example, there are the Privateers running ransomware cartels. What we've seen over the past several years is the monetary payout for these attacks has grown exponentially. Ransomware several years ago was primarily driven by drive-by downloads and malspam campaigns ransoming one system at a time. Today, it's focused around large criminal organizations ransoming multinational organizations.
There's an entire affiliate ecosystem that is feeding potential victims into this malicious cash machine. These are all logical developments — the criminals follow money, and as they see other criminals making huge monetary gains ransoming organizations, they follow suit. This is exactly what we could be seeing with cryptomining.
That being said, the TTPs associated with these actors couldn't be more different. Cryptominers are hoping to remain undetected for long periods of time, to get their miners installed on as many systems as possible without being detected. They really don't care if a system gets cleaned up, the resources are easily replaced with another victim. We have covered several of these actors over the years and their scale and effectiveness can vary widely from one campaign to the next.
Security Implications Although cryptocurrency miners don't seem that serious on the surface, it's important to remember that they have broader security implications. Unauthorized software on end systems is never a good sign. Today, it's a cryptominer, tomorrow, it could be the initial payload in an eventual ransomware attack. Cryptominers should be treated with the same level of urgency as any other security threat. There are multiple financial risks to this behavior, as well, but they are mostly related to lost productivity, hardware failures and power consumption. However, with a large enough cryptominer problem, those costs could be significant. In a world where budgets are already stretched thin, trying to account for unexpected costs could be challenging.
If you notice cryptocurrency in the headlines for its value accelerating, start paying attention to the activity on your network, it's likely to change. Likewise, if new monetization avenues open up, expect the actors to follow. If we see a huge crackdown on cryptocurrency or a cratering of the price, expect to see some major shifts on the threat landscape. We talk a lot about how adversaries pay attention to the news for effective lures. Security organizations potentially should do the same for a threat's monetary value, if it craters, the activity potentially will, as well.
Conclusion The overwhelming majority of malicious cyber actors are purely financially motivated, chasing whatever threat or scam generates the most revenue. This is something we've always known to be true, but it's a difficult thing to demonstrate more definitively. Cryptocurrency mining has given us a rare opportunity to explicitly track the value of the threat and, through data aggregation and analytics, show that as the value of the cryptocurrency increases, the amount of mining we detect does, as well.
As leaders in security organizations, the fact that you can clearly show financial gains as a driver of malicious activity may help you better defend your organization. Threats that present a clear path for attackers to make money quickly and easily are going to be the most common. In today's world, that's ransomware and cryptomining. Both provide financial gain in completely different ways. Ransomware targets enterprises specifically, is noisy, and requires actors to establish and maintain communication avenues with their victims. Cryptomining is designed to evade detection, stay active for long periods of time, and the targeting makes little to no difference other than the amount of currency they can generate.
Taking this a step further, leaders need to understand that any drastic changes in these dynamics will shift the threat landscape. If, say, governments decide to start cracking down on ransomware cartels or work more aggressively against cryptocurrencies, the threat landscape is going to react. Based on the mining data we saw here, the shift might occur relatively quickly.
Detection for cryptomining can be spread into a variety of different places including blocking mining-related domains, to enforcing limitations on the end system preventing the mining from starting and lots of network-based detection, which this research is based on. For more details on how Cisco Security products can be used to detect and prevent cryptomining, see our existing whitepaper. Regardless of the detection point, organizations should be working to prevent it.
