How do cryptocurrency drainer phishing scams work?
In recent months, a surge in cryptodrainer phishing attacks has been observed, targeting cryptocurrency holders with sophisticated schemes aimed at tricking them into divulging their valuable credentials.
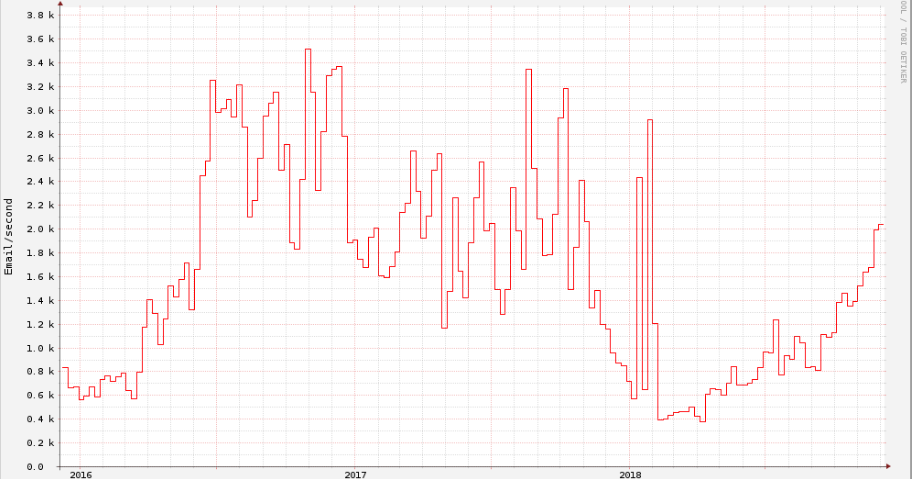
Following the Money: Comparing cryptocurrency value to illicit mining activity
By Nick Biasini In the age of meme stocks, Robinhood and Elon Musk's tweets influencing the global economy, cryptocurrency mining has not seemed as fringe as it once did. Mining has been around as long as these crytocurrencies have, but only really started to gather the att
Lemon Duck brings cryptocurrency miners back into the spotlight
By Vanja Svajcer, with contributions from Caitlin Huey. * We are used to ransomware attacks and big-game hunting making headlines, but there are still methods adversaries use to monetize their efforts in less intrusive ways. * Cisco Talos recently recorded increased activity
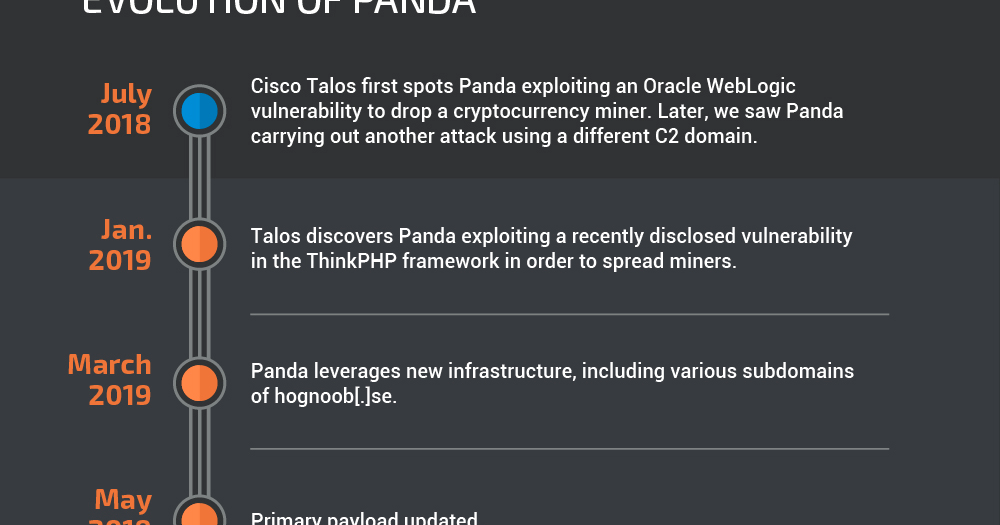
Cryptocurrency miners aren’t dead yet: Documenting the voracious but simple “Panda”
By Christopher Evans and David Liebenberg. Executive summary A new threat actor named "Panda" has generated thousands of dollars worth of the Monero cryptocurrency through the use of remote access tools (RATs) and illicit cryptocurrency-mining malware. This is far fr
Cyber Security Week in Review (March 1)
Cyber Security Week in Review (Feb. 15, 2019)
Cyber Security Week in Review (Feb. 8)
As Cryptocurrency Crash Continues, Will Mining Threat Follow?
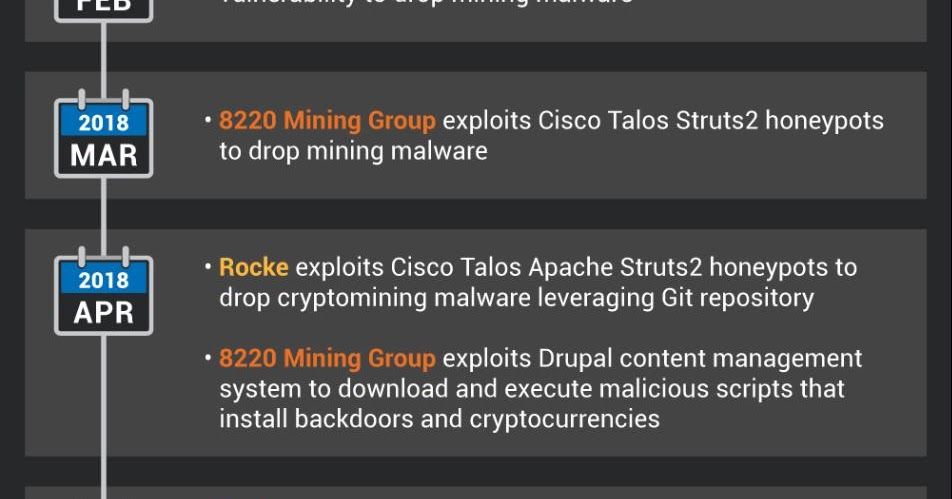
Connecting the dots between recently active cryptominers
Post authored by David Liebenberg and Andrew Williams. Executive Summary Through Cisco Talos' investigation of illicit cryptocurrency mining campaigns in the past year, we began to notice that many of these campaigns shared remarkably similar TTPs, which we at first mistak