UPDATE, APRIL 4, 2022:
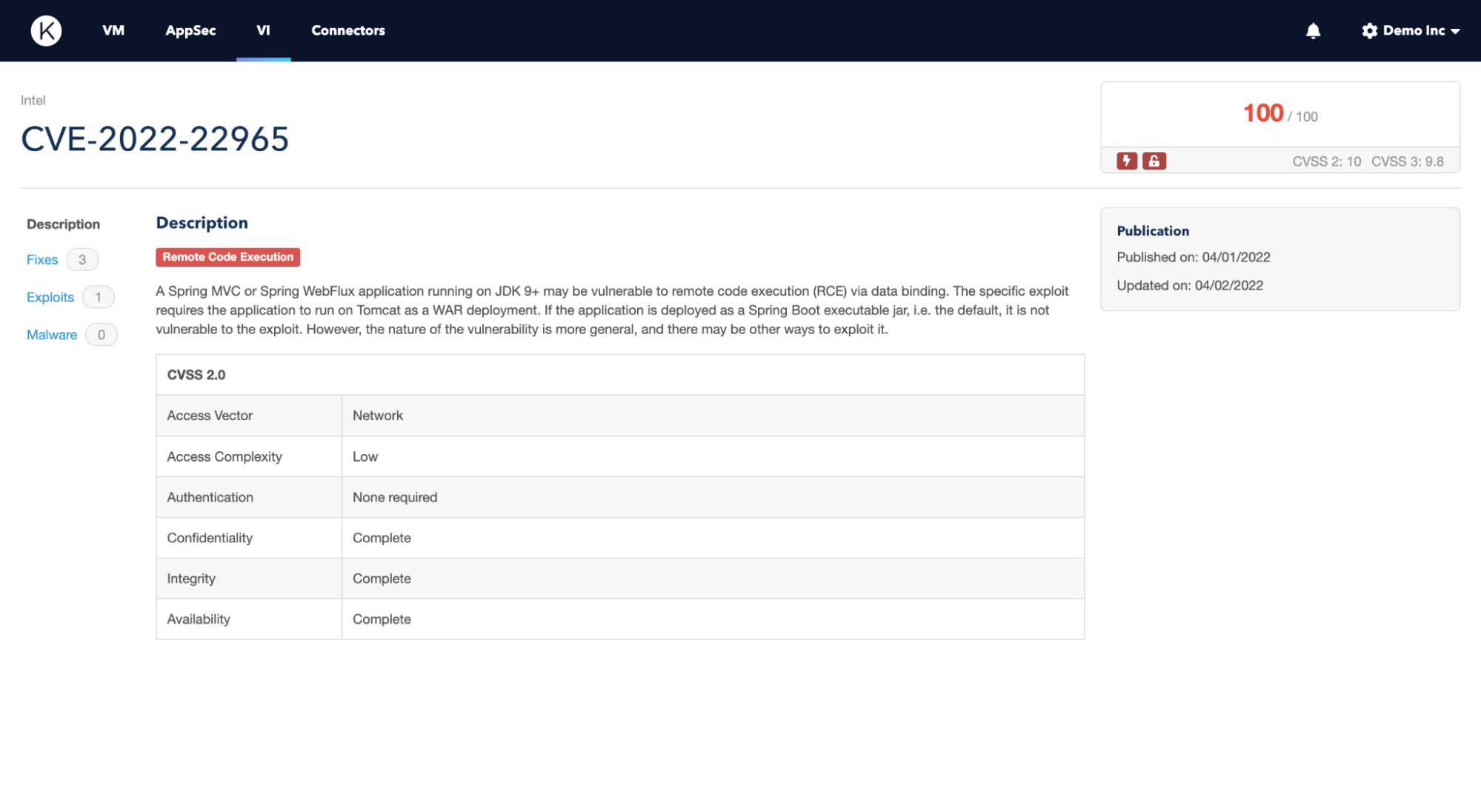
The Kenna Risk Score for CVE-2022-22965 is currently at maximum 100. This is an exceptionally rare score, of which only 415 out of 184,000 CVEs (or 0.22 percent) have achieved, reflecting the severity and potential effects of this vulnerability. To get a risk score this high means it is a widely deployed technology with a public exploit available, and we have seen proof of an ongoing active internet breach using the vulnerability.
Kenna Risk Scores are continually reevaluated and may shift over time. An outline of the current risk score is below:
Cisco Talos is releasing coverage to protect users against the exploitation of two remote code execution vulnerabilities in Spring Framework. CVE-2022-22963 is a medium-severity bug that affects Spring Cloud and CVE-2022-22965, a high-severity bug that affects Spring Core Framework. Spring is a Java-based framework commonly used by developers to create and test code. There are already reports of the vulnerabilities being leveraged in the wild and patches have been made available here, here and here.
CVE-2022-22963
CVE-2022-22963 is a vulnerability in the routing functionality in Spring Cloud Function versions 3.1.6, 3.2.2, and old unsupported versions. The vulnerability can be triggered by an attacker sending a specially crafted SpEL routing expression that could result in remote code execution. Upgrading to Spring Cloud Function 3.1.7 or 3.2.3 will resolve this issue.
CVE-2022-22965
CVE-2022-22965 or Spring4Shell is a high-severity class manipulation vulnerability that could result in remote code execution that affects two specific Spring products: Spring MVC and Spring WebFlux. This particular vulnerability appears to be a bypass of mitigations put in place for a previous vulnerability, CVE-2010-1622, and can be exploited by sending a specially crafted HTTP request that can result in code execution. Upgrading to Spring Framework 5.3.18 or 5.2.20 should resolve this issue. Alternatively, Spring has provided several workarounds that are outlined here.
As of the time of this writing, if an application was deployed using the default mechanism, as a Spring Boot executable jar, then it is not vulnerable to the exploit. However, as this is a new vulnerability this could change in the future and Cisco Talos continues to monitor.
Coverage
Snort SIDs: 30790-30793, 59388, and 59416 can detect this activity.
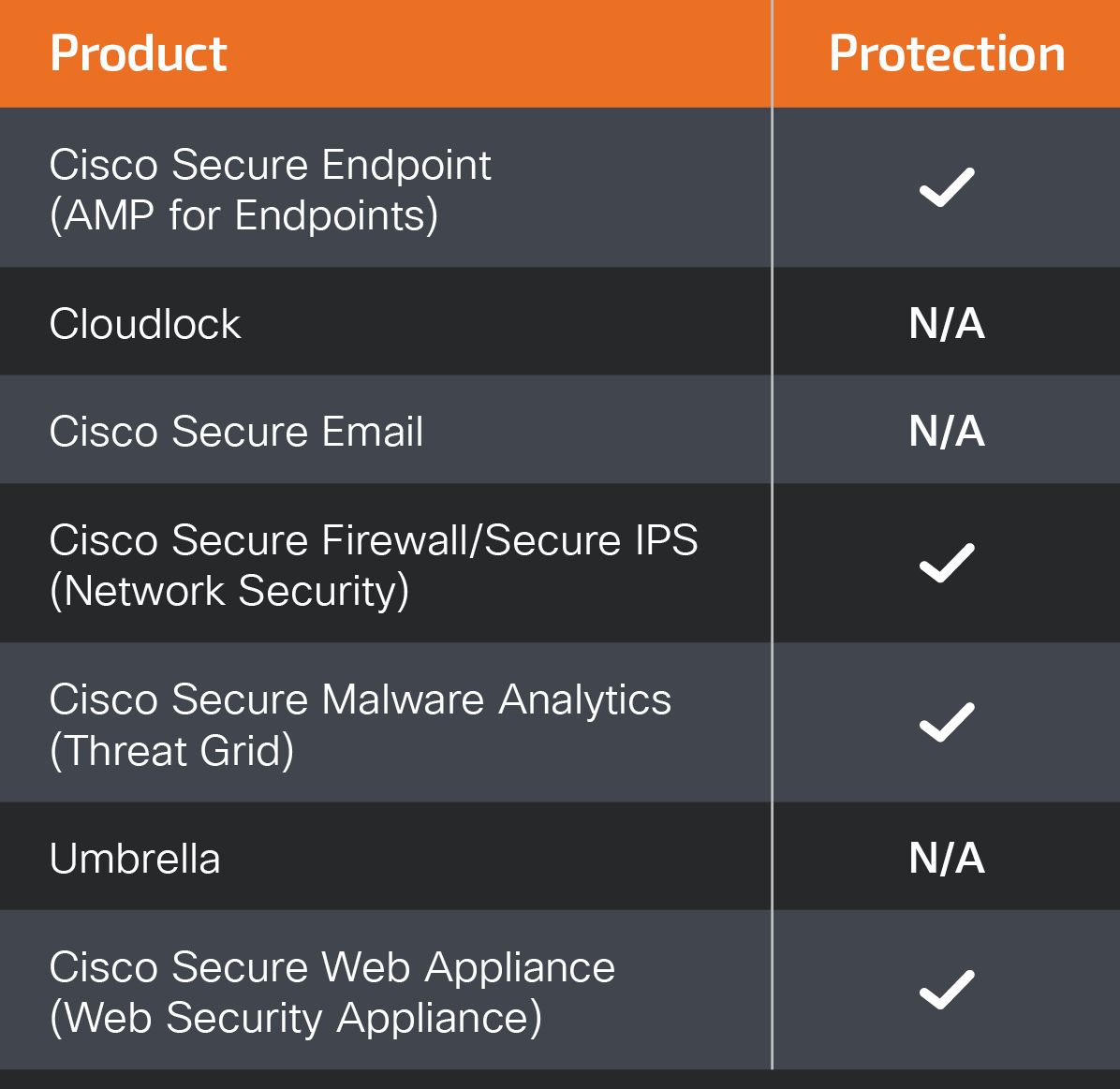
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Network/Cloud Analytics (Stealthwatch/Stealthwatch Cloud) analyzes network traffic automatically and alerts users of potentially unwanted activity on every connected device.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.