A recently discovered vulnerability in Apache HTTP Server (CVE-2021-41733) is being actively exploited in the wild.
This vulnerability is a path traversal and file disclosure vulnerability that could allow an attacker to map URLs outside of the document root. It could also result in the exposure of the source of interpreted files like CGI scripts. The exploitation of this vulnerability is of very low complexity and poses a critical threat to all users of this open-source software.
This particular vulnerability was introduced in a recent version of Apache (2.4.49). Users running older versions of Apache are not currently affected. The fix for CVE-2021-41733 in 2.4.50 was found to be insufficient, leading to a second, new vulnerability (CVE-2021-42013) that Apache is now reporting. As a result, version 2.4.51 was released to fully address the issue. Users are recommended to upgrade to 2.4.51 as soon as possible. According to data available on Shodan, only a small number of Apache installations are actually running 2.4.49 or 2.4.50, meaning less than 1 percent of the overall Apache install base could be affected.
Active Exploitation
In response to this vulnerability, Cisco Talos released coverage for Cisco Secure products, including Cisco Secure Firewall with Snort rule 58276 (Snort 3 SID 300053). Upon deploying the signature, we immediately saw exploitation activity coming from a variety of addresses. Since this is primarily a path traversal bug, the majority of the exploitation we see is focused on two specific paths: /etc/passwd and /bin/sh. These would make sense, as attackers are going to try and leverage this for access by accessing credentials or obtaining direct access to a shell. Below are a few examples of common requests we are seeing:
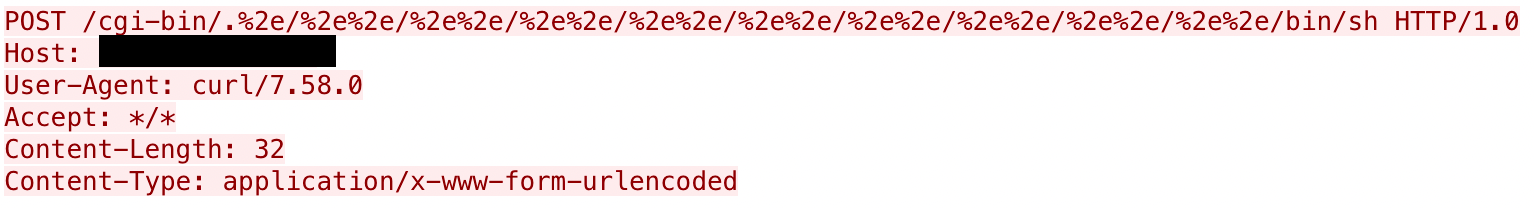
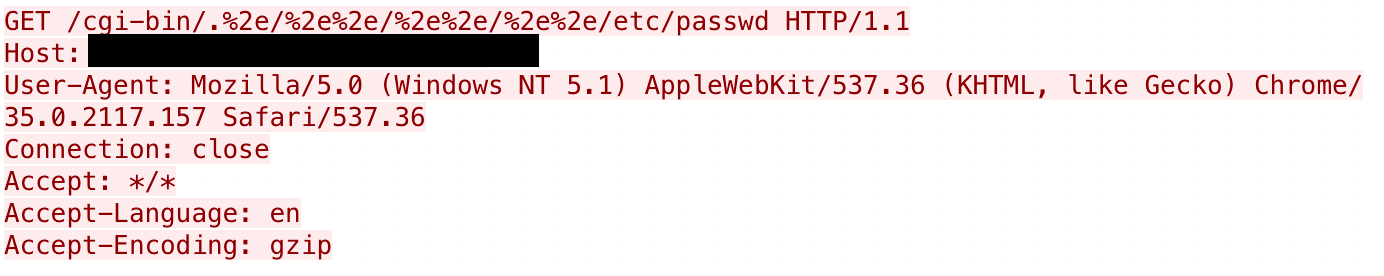
These two pcaps show the most common targets we've seen of the path traversal vulnerability and the most common approaches to user agents for the activity. The majority of the activity is using cURL as the user agent, but we have seen other activity that is focused on using various common user agents, including the one shown above.
However, this is not an exhaustive list of paths being targeted. We have seen other paths being probed by attackers including /etc/services and /etc/hosts, examples of which are shown below.


There appear to be several different groups of actors exploiting this vulnerability. Some are just scanners that appear to be scanning for potentially vulnerable hosts. Others appear to be iterating through a large list of domains with varying generic HTTP scanning leveraging this vulnerability. And there's another group operating at a much lower volume that are keenly interested in this specific vulnerability.
Conclusion
Internet-facing servers are always at increased risk of exploitation and web servers are historically a popular target. Apache is a popular web server that has a large install base. This vulnerability was only recently disclosed and the amount of exploitation in the wild points to it being a popular target for adversaries despite having a potentially small attack surface. As such, affected customers should apply the 2.4.51 patch as soon as possible to mitigate any potential issues.
The activity seems to include those that are performing wide scale scanning as well as others experimenting and working to implement mechanisms to exploit it. The low complexity of this exploit allows for automated exploitation to be easily implemented by an attacker.
Coverage
Ways our customers can detect and block this threat are listed below.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org. Snort SID 58276 (Snort 3 SID 300053) has been released to address this vulnerability.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Indicators of compromise (IoCs)
IP Addresses:
134.122.112.12
143.198.136.88
161.35.188.242
161.35.86.181
167.99.133.28
162.241.114.189
162.241.69.182
185.246.210.169
94.46.15.22
69.49.228.92
69.49.235.93
3.83.56.46
141.101.146.162
156.146.50.105
156.146.50.98
185.254.96.162
185.56.80.11
194.126.177.17
192.3.194.202
89.248.173.143
80.239.140.67
47.106.92.240
45.77.138.50
45.86.203.97
27.102.114.78
14.161.74.29
149.28.140.81
185.98.87.200
217.138.216.4
142.93.153.4
178.128.172.249
79.165.90.196
51.79.142.118
59.12.193.82
64.39.106.120
64.39.98.36
45.155.204.183
34.223.64.22
35.82.51.168
37.237.230.28
44.242.181.147
45.146.164.110
145.220.25.28
165.227.79.155
161.35.215.189
143.198.62.76
174.138.42.66
46.101.59.235
137.184.69.137
165.227.125.18