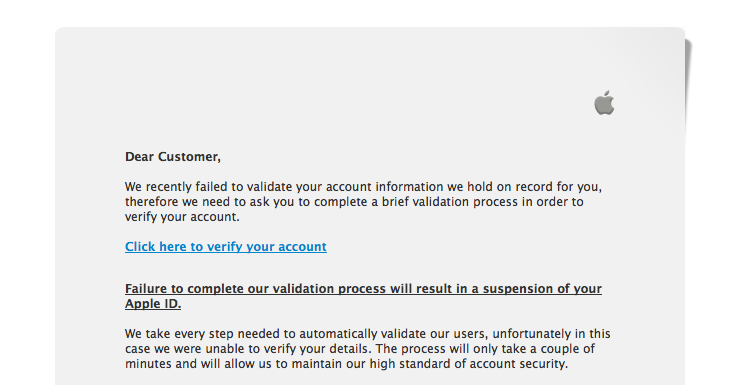
Phishing isn't new. "So, why are you writing about it?", you ask.
I received this one today and it was very well done, so I thought I'd write it up. Chances are, you've seen these before:

If you are familiar with Apple Verification emails, you'll notice the format is almost exactly what Apple uses. You'll notice that there are hardly any grammar, punctuation or capitalization errors. Usually, something as simple as the "Dear Customer" would give it away by the insertion of a space between the word "Customer" and ",". Those of you that look at phish emails all day know what I am talking about.
The domain "appleid.co.uk" that the email was "sent" from could even be legitimate. If you mouse over the "Click here to verify your account" link, the email begins to fall apart.
hxxp://appleid.apple.co.uk.cgi-bin.webobjects.myappleid.woa.verify.gb-appleid[.]net/validation_code=<long code here>/
It uses "webobjects" in the URL (an Apple Technology), and if you weren't paying attention, you will glance over the "gb-appleid[.]net" as the domain (bolded above).
In fact, when you load it in a browser, the domains the resulting webpage loads its images from is "gb-appleid[.]com".
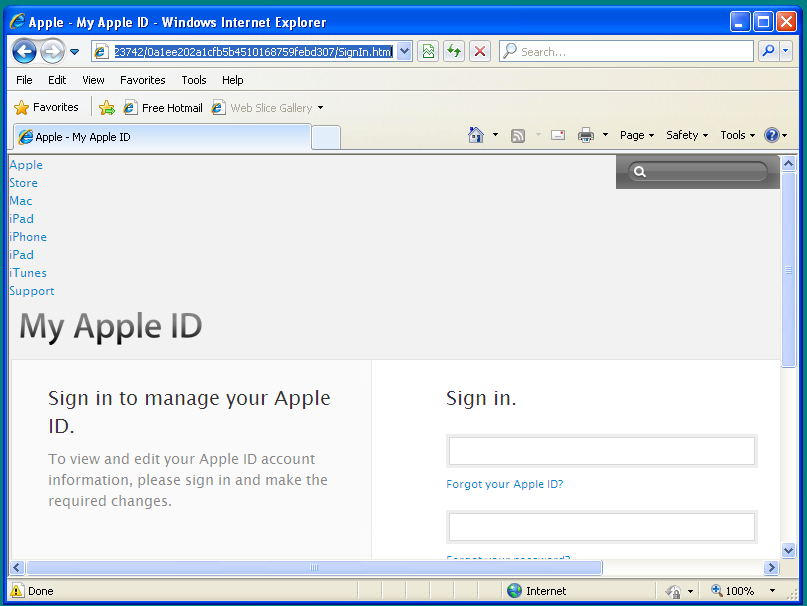
(In fact the only reason the menu (across the top of the "Apple ID Page" doesn't load correctly is because of the browser I am using in this screenshot, but the images are correct.)
Well, let's take a look at the domains whois records:
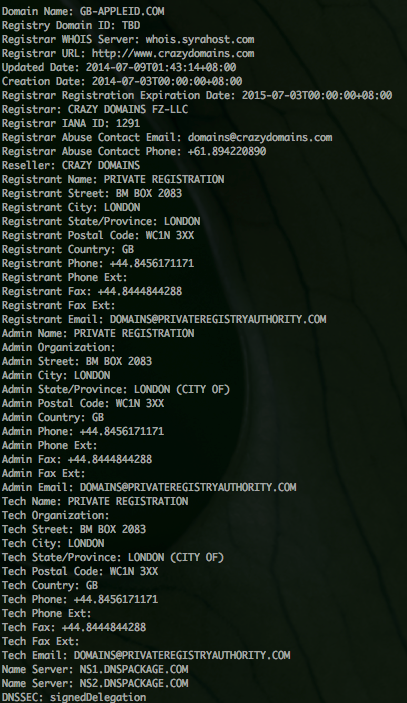
This is where the ruse falls apart. Obviously Apple runs their own DNS servers, isn't registered by "Crazy Domains, LLC", and isn't "registered" in London.
The resulting page is an attempt to get you to fill in your Apple credentials, which, of course, gives the attacker access to your entire Apple ecosystem. Email, iTunes, the works.
Phishes aren't going away. They are getting better with age.
Cisco Web and Email Security products protect customers against these sites.