CCleaner Command and Control Causes Concern
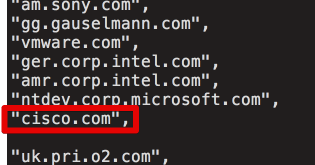
Introduction Talos recently published a technical analysis of a backdoor which was included with version 5.33 of the CCleaner application. During our investigation we were provided an archive containing files that were stored on the C2 server. Initially, we had concerns about th
CCleanup: A Vast Number of Machines at Risk
Update 9/18: CCleaner Cloud version 1.07.3191 is also reported to be affected Update 9/19: This issue was discovered and reported by both Morphisec and Cisco in separate in-field cases and reported separately to Avast. Update 9/19: There has been some confusion on how the DGA do
Cryptolocker 4 White Paper Available: The Evolution Continues
We are pleased to announce the availability of the Cryptolocker 4 white paper. Over the past year, Talos has devoted a significant amount of time to better understanding how ransomware operates, its relation to other malware, and its economic impact. This research has proven valu
Project Aspis
One of the hardest jobs on the Internet is to work the abuse desk at a hosting provider. These teams have to strike a difficult balance between protecting their customers, ensuring that their services aren’t being abused by malicious actors and delivering the service and conven
Threat Spotlight: Cisco Talos Thwarts Access to Massive International Exploit Kit Generating $60M Annually From Ransomware Alone
This post was authored by Nick Biasini with contributions from Joel Esler, Nick Hebert, Warren Mercer, Matt Olney, Melissa Taylor, and Craig Williams. Executive Summary Today, Cisco struck a blow to a group of hackers, disrupting a significant international revenue stream gener
Down the Rabbit Hole: Botnet Analysis for Non-Reverse Engineers
This post is authored by Earl Carter & Holger Unterbrink. Overview Talos is often tasked with mapping the backend network for a specific piece of malware. One approach is to first reverse engineer the sample and determine exactly how it operates. But what if there is no tim
SYNful Knock Scanner
This post was authored by William McVey. Update 2015-09-23: We updated the tool to version 1.0.1 Talos is constantly researching the ways in which threat actors are evolving to exploit systems. Recently, a piece of persistent malware coined as “SYNful Knock” was discovered on C
When Does Software Start Becoming Malware?
This post was authored by Earl Carter, Alex Chiu, Joel Esler, Geoff Serrao, and Brandon Stultz. Defining what is malware relies on determining when undesirable behavior crosses the line from benign to clearly unwanted. The lack of a single standard regarding what is and what is
Vulnerability Spotlight: Microsoft Windows CDD Font Parsing KernelMemory Corruption
Discovered by Andrea Allievi and Piotr Bania of Cisco Talos. Talos, in conjunction with Microsoft’s security advisory issued on September 8th, is disclosing the discovery of a memory corruption vulnerability within the Microsoft Windows CDD Font Parsing Kernel Driver. This vulne