Vulnerability Spotlight: Multiple remote code execution vulnerabilities in Iceni Argus PDF Content Extraction affect MarkLogic
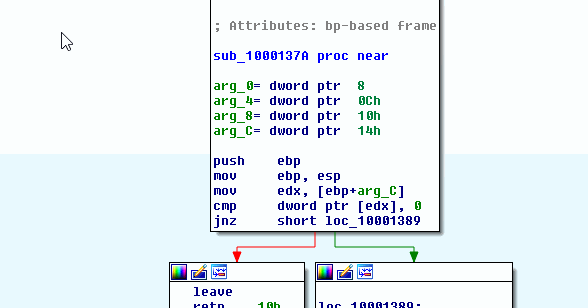
Vulnerability discovered by Marcin ’Icewall’ Noga and a member of the Talos VulnDev team. Overview Talos has discovered multiple vulnerabilities in Iceni Argus PDF content extraction product. Exploiting these vulnerabilities can allow an attacker to gain full control over the v
Project FIRST: Share Knowledge, Speed up Analysis
Crashing Stacks Without Squishing Bugs: Advanced Vulnerability Analysis
This post is authored by Marcin Noga with contributions by Holger Unterbrink Overview Crash triaging can be a long and complicated process; by using proper tools and having an optimal approach, we can make this a bit easier and less time consuming. In this post we describe a tr
Take the RIG Pill: Down the Rabbit Hole
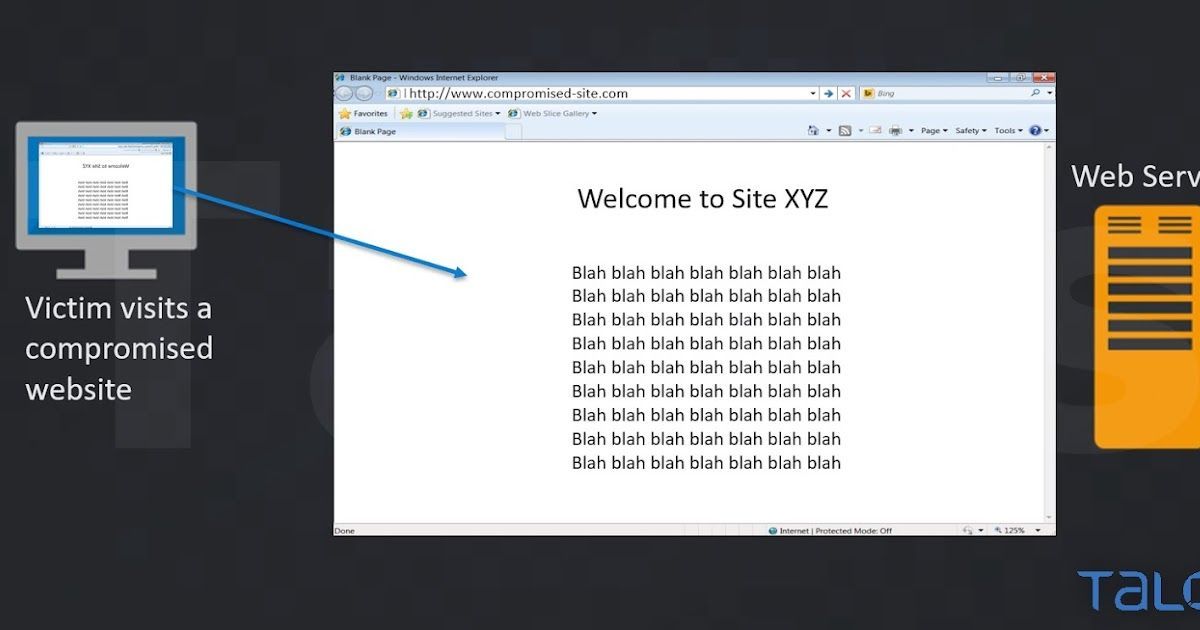
The adversaries are leveraging Gates (e.g. EITest) to redirect the users to their Landing Page. This leads to a chain of redirects, before the victim finally gets on the landing page of the exploit kit.
Vulnerability Spotlight: Kernel Information Leak & Multiple DOS Issues Within Kaspersky Internet Security Suite
A further local denial of service attack is possible through Kaspersky’s KL1 driver. A malicious user can send a specially crafted IOCTL call to the KL1 driver. Under certain conditions, this can causing the driver to read memory outside of an allocated buffer. This may provoke a
TeslaCrypt 3.0.1 - Tales From The Crypt(o)!
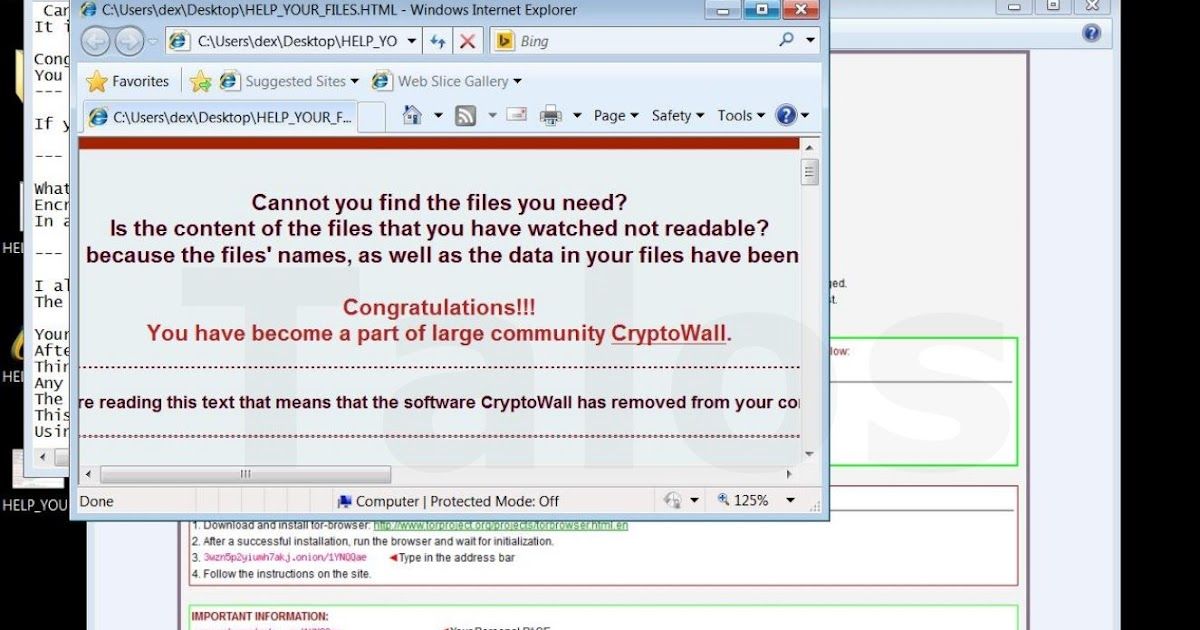
This post is authored by Andrea Allievi and Holger Unterbrink Executive Summary Ransomware is malicious software that is designed to hold users' files (such as photos, documents, and music) for ransom by encrypting their contents and demanding the user pay a fee to decryp
Threat Spotlight: CryptoWall 4 - The Evolution Continues
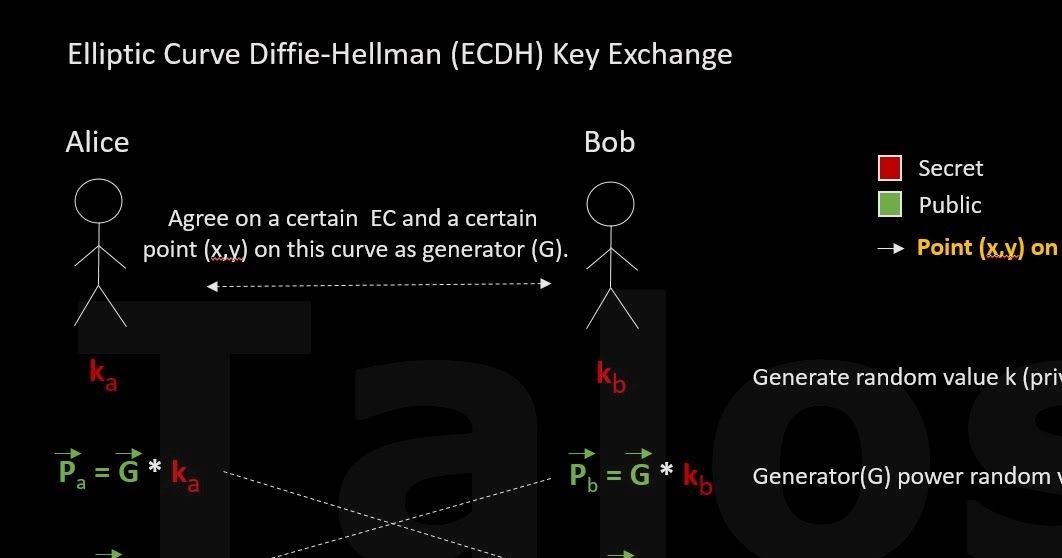
This post is authored byAndrea Allievi and Holger Unterbrink with contributions from Warren Mercer. Executive Summary Over the past year, Talos has devoted a significant amount of time to better understanding how ransomware operates, its relation to other malware, and its ec