The Rising Tides of Spam
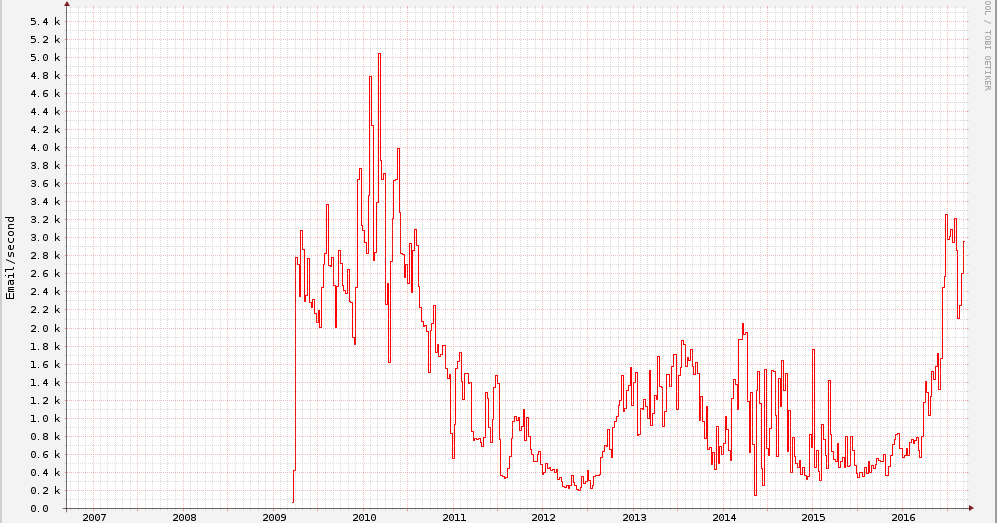
This blog post was authored by Jaeson Schultz. For the past five years we have enjoyed a relatively calm period with respect to spam volumes. Back at the turn of the decade the world was experiencing record-high volumes of spam. However, with the evolution of new anti-spam techn
Microsoft Patch Tuesday - September 2016
This post was authored by Jaeson Schultz. Well it's Microsoft Patch Tuesday, again, and that must mean we are girding our systems against another round of security vulnerabilities. This month Microsoft has released fourteen (14) bulletins covering fifty (50) security vulnera
Vulnerability Spotlight: Oracle's Outside In Technology, Turned Inside-Out
Vulnerabilities discovered by Aleksandar Nikolic. Blog post authored by Jaeson Schultz and Aleksandar Nikolic. One of the most fundamental tasks performed by many software programs involves the reading, writing, and general processing of files. In today's highly networked en
The Poisoned Archives
Vulnerabilities discovered by Marcin “Icewall” Noga. Blog post authored by Marcin Noga and Jaeson Schultz. Update 2016-08-01: Talos has produced a video demonstrating how flaws in libarchive can be exploited using Splunk 6.4.1 as an attack vector. Release 3.2.1 of Libarchive add
Multiple 7-Zip Vulnerabilities Discovered by Talos
7-Zip vulnerabilities were discovered by Marcin Noga. Update 2016-05-12: Related advisories for the 7-Zip issues covered in this blog can be found here: http://www.talosintel.com/reports/TALOS-2016-0093/ http://www.talosintel.com/reports/TALOS-2016-0094/ 7-Zip is an open-source
Oracle OIT Image Export SDK libvs_pdf XRef Index Code Execution Vulnerability
This post was authored by Aleksandar Nikolic and Jaeson Schultz. Talos has recently discovered a vulnerability in Oracle’s Outside In Technology Image Export SDK which, when exploited, allows an attacker to overflow the heap, leading to arbitrary code execution. The vulnerabil
Bypassing MiniUPnP Stack Smashing Protection
This post was authored by Aleksandar Nikolic, Warren Mercer, and Jaeson Schultz Summary MiniUPnP is commonly used to allow two devices which are behind NAT firewalls to communicate with each other by opening connections in each of the firewalls, commonly known as “hole punchin
Holiday Shopping Threat Avoidance
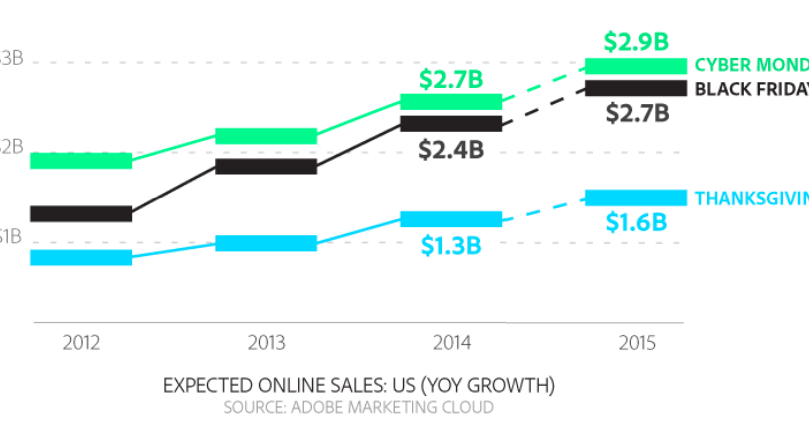
Executive Summary The holidays are upon us and the shopping season is kicking into high gear. This year, an estimated 270 million consumers will shop online and, for the first time, more than half of them will use mobile devices to check off their holiday shopping lists. With co
Domains of the Living Dead
According to the Centers for Disease Control and Prevention (CDC), “If you’re ready for a zombie apocalypse, then you’re ready for any emergency.” While events haven’t yet risen to the level of “zombie apocalypse”, computer attackers are continuing to use their voodoo to zombify