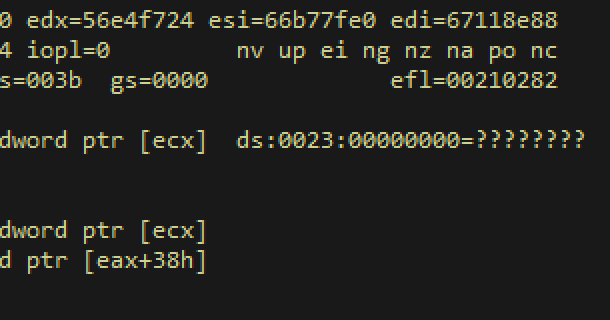
Exploitable or Not Exploitable? Using REVEN to Examine a NULL Pointer Dereference.
Authored by Aleksandar Nikolic. Executive summary It can be very time-consuming to determine if a bug is exploitable or not. In this post, we’ll show how to decide if a vulnerability is exploitable by tracing back along the path of execution that led to a crash. In this case,
Microsoft Patch Tuesday - May 2018
Today, Microsoft has released its monthly set of security advisories for vulnerabilities that have been identified and addressed in various products. This month's advisory release addresses 67 new vulnerabilities, with 21 of them rated critical, 42 of them rated important, an
Who Wasn’t Responsible for Olympic Destroyer?
Summary Absent contributions from traditional intelligence capacities, the available evidence linking the Olympic Destroyer malware to a specific threat actor group is contradictory, and does not allow for unambiguous attribution. The threat actor responsible for the attack has
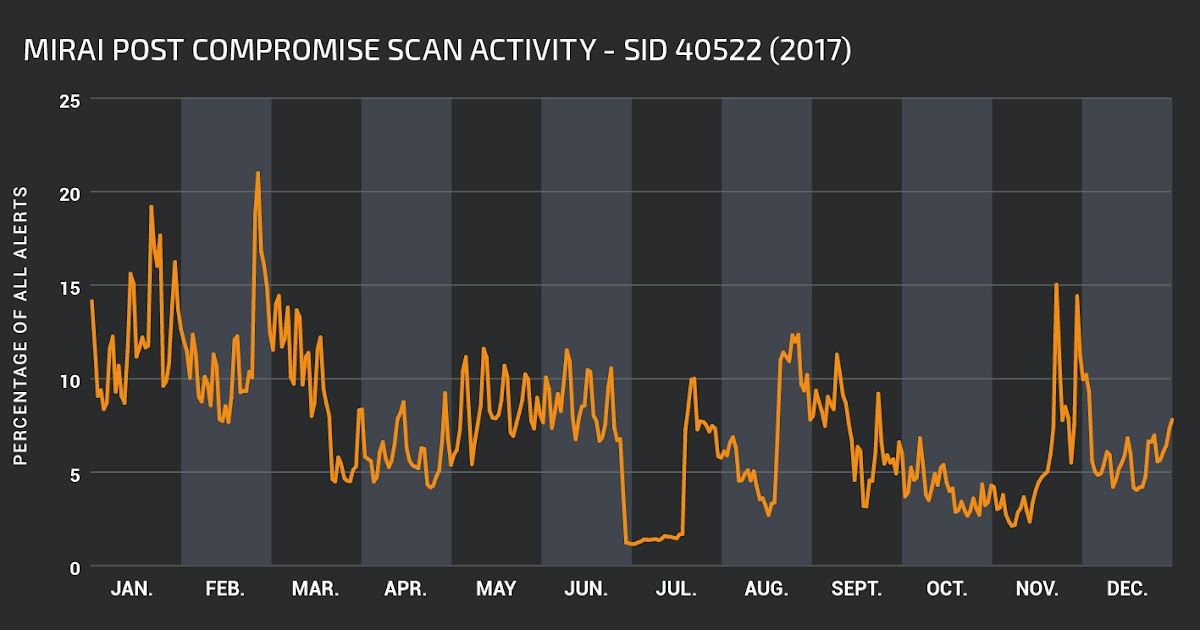
2017 in Snort Rules
This post was written by Martin Lee and Vanja Svajcer. 2017 was an eventful year for cyber security with high profile vulnerabilities that allowed self-replicating worm attacks such as WannaCry and BadRabbit to impact organizations throughout the world. In 2017, Talos researcher
This Holiday Season - Buy One IoT Device, Get Free CVEs
As the Internet of Things gains steam and continues to develop, so are adversaries and the threats affecting these systems. Companies throughout the world are busy deploying low cost Internet-connected computing devices (aka the Internet of Things) to solve business problems and
Vulnerability Spotlight: YAML Parsing Remote Code Execution Vulnerabilities in Ansible Vault and Tablib
Vulnerabilities discovered by Cory Duplantis of Talos. Talos is disclosing the presence of remote code execution vulnerabilities in the processing of Yet Another Markup Language (YAML) content in Ansible Vault and Tablib. Attackers can exploit these vulnerabilities through suppl
Vulnerability Spotlight: Code Execution Vulnerability in LabVIEW
Vulnerability discovered by Cory Duplantis of Cisco Talos. Update: 9/1/17 - National Instruments has published the following advisory Overview LabVIEW is a system design and development platform released by National Instruments. The software is widely used to create applicatio
Vulnerability Spotlight: FreeRDP Multiple Vulnerabilities
Vulnerabilities discovered by Tyler Bohan of Talos Overview Talos has discovered multiple vulnerabilities in the FreeRDP product. FreeRDP is a free implementation of the Remote Desktop Protocol (RDP) originally developed by Microsoft. RDP allows users to connect remotely to s
Vulnerability Spotlight: Dell Precision Optimizer and Invincea Vulnerabilities
Vulnerabilities discovered by Marcin ‘Icewall’ Noga of Cisco Talos. Overview Talos are releasing advisories for vulnerabilities in the Dell Precision Optimizer application service software, Invincea-X and Invincea Dell Protected Workspace. These packages are pre-installed on ce