Vulnerability Spotlight: Windows 10 Remote Denial of Service
Vulnerability discovered by Piotr Bania of Cisco Talos. Overview Talos is releasing an advisory for a remote denial of service attack vulnerability in Microsoft Windows 10 AHCACHE.SYS (TALOS-2016-0191 / CVE-2016-3369) An attacker can craft a malicious portable executable fi
Vulnerability Spotlight: Kaspersky Unhandled Windows Messages Denial of Service Vulnerability
Vulnerability discovered by Marcin 'Icewall' Noga of Cisco Talos. Overview Talos is disclosing the presence of TALOS-2016-0175 / CVE-2016-4329, a local denial of service vulnerability within Kaspersky anti-virus. A system user is able to cause a denial of service atta
Vulnerability Spotlight: Kaspersky Unhandled Windows Messages Denial of Service Vulnerability
Vulnerability discovered by Marcin ‘Icewall’ Noga of Cisco Talos. Overview Talos is disclosing the presence of TALOS-2016-0175 / CVE-2016-4329, a local denial of service vulnerability within Kaspersky anti-virus. A system user is able to cause a denial of service attack agains
Vulnerability Spotlight: Multiple Remote Code Execution Vulnerabilities Within Lexmark Perceptive Document Filters.
Vulnerabilities discovered by Tyler Bohan & Marcin Noga of Cisco Talos Talos are today releasing three new vulnerabilities discovered within the Lexmark Perceptive Document Filters library. TALOS-2016-0172, TALOS-2016-0173 and TALOS-2016-0183 allow for a remote code executio
Macro Intruders: Sneaking Past Office Defenses
This blog was written by Matthew Molyett with contributions from Martin Lee . Introduction Macros have been used since the mid 1990s to spread malware and infect systems. Increased user awareness of the need to disable the macro function within Microsoft Word during the late 90
Detecting DNS Data Exfiltration
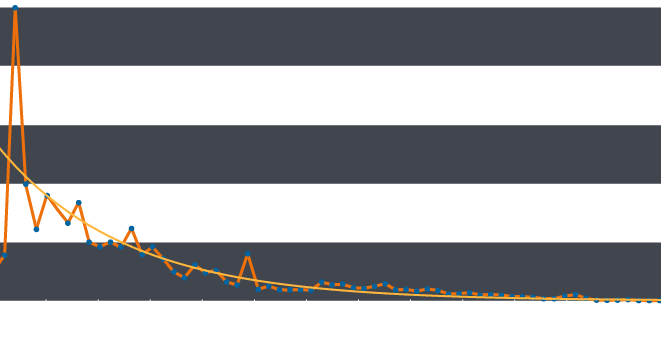
This blog was co-authored by Martin Lee and Jaeson Schultz with contributions from Warren Mercer. The recent discovery of Wekby and Point of Sale malware using DNS requests as a command and control channel highlights the need to consider DNS as a potentially malicious channel. A
Vulnerability Spotlight: LibreOffice RTF Vulnerability
Vulnerability discovered by Aleksandar Nikolic of Cisco Talos. Talos is disclosing the presence of CVE-2016-4324 / TALOS-2016-0126, a Use After Free vulnerability within the RTF parser of LibreOffice. The vulnerability lies in the parsing of documents containing both stylesheet
Vulnerability Spotlight: Further NTPD Vulnerabilities
As a member of the Linux Foundation Core Infrastructure Initiative, Cisco is contributing to the CII effort by evaluating the Network Time Protocol daemon (ntpd) for security defects. We previously identified a series of vulnerabilities in the Network Time Protocol daemon; throug
Vulnerability Spotlight: Lhasa Integer Underflow Exploit
Vulnerability discovered by Marcin Noga of Cisco Talos. Talos is disclosing the discovery of vulnerability TALOS-2016-0095 / CVE-2016-2347 in the Lhasa LZH/LHA decompression tool and library. This vulnerability is due to an integer underflow condition. The software verifies that