Talos Wins The 5th Volatility Plugin Contest With Pyrebox
Talos has won this year's 5th Volatility plugin contest with Pyrebox. Volatility is a well-known open-source framework designed to analyze operating system memory. The framework has existed since 2007. For the previous 5 years they have run a plugin contest to find the most
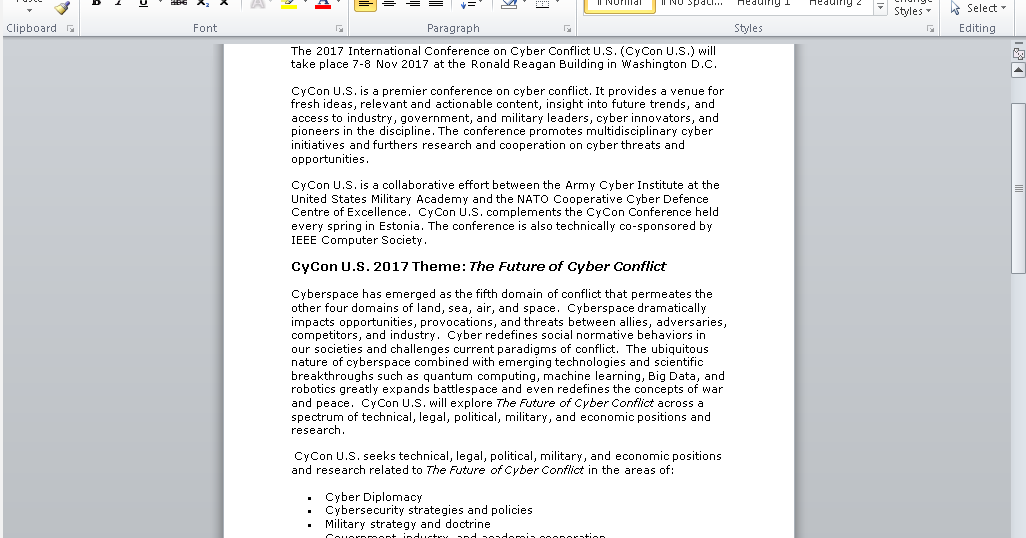
“Cyber Conflict” Decoy Document Used In Real Cyber Conflict
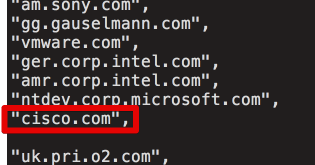
Update 10/23: CCDCOE released a statement today on their website Introduction Cisco Talos discovered a new malicious campaign from the well known actor Group 74 (aka Tsar Team, Sofacy, APT28, Fancy Bear…). Ironically the decoy document is a deceptive flyer relating to the Cyb
Disassembler and Runtime Analysis
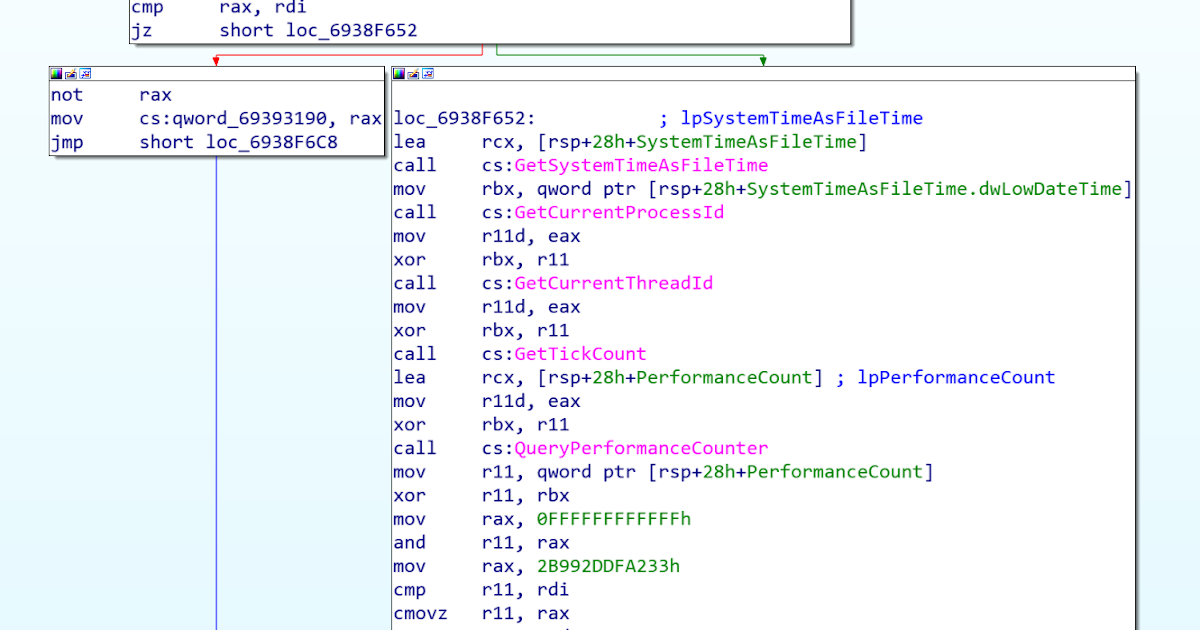
This post was authored by Paul Rascagneres. Introduction In the CCleaner 64bit stage 2 previously described in our blog, we explained that the attacker modified a legitimate executable that is part of "Symantec Endpoint". This file is named EFACli64.dll. The modificat
CCleaner Command and Control Causes Concern
Introduction Talos recently published a technical analysis of a backdoor which was included with version 5.33 of the CCleaner application. During our investigation we were provided an archive containing files that were stored on the C2 server. Initially, we had concerns about th
WinDBG and JavaScript Analysis
This blog was authored by Paul Rascagneres. Introduction JavaScript is frequently used by malware authors to execute malicious code on Windows systems because it is powerful, natively available and rarely disabled. Our previous article on .NET analysis generated much interest r
Unravelling .NET with the Help of WinDBG
This blog was authored by Paul Rascagneres and Warren Mercer. Introduction .NET is an increasingly important component of the Microsoft ecosystem providing a shared framework for interoperability between different languages and hardware platforms. Many Microsoft tools, such as
New KONNI Campaign References North Korean Missile Capabilities
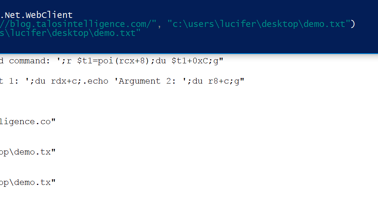
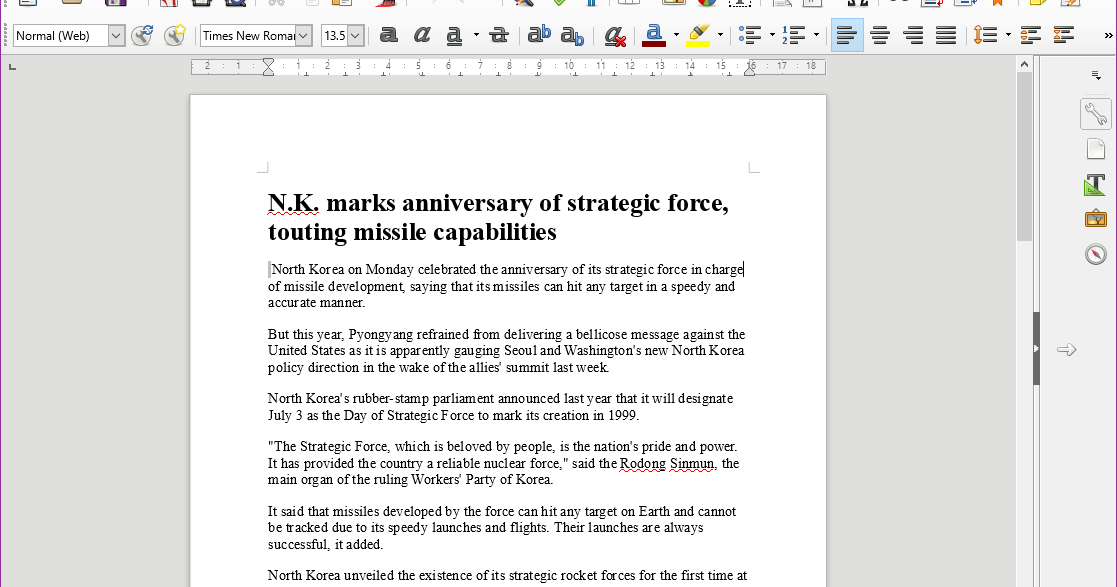
This blog was authored by Paul Rascagneres Executive Summary We recently wrote about the KONNI Remote Access Trojan (RAT) which has been distributed by a small number of campaigns over the past 3 years. We have identified a new distribution campaign which took place on 4th Jul
KONNI: A Malware Under The Radar For Years
This blog was authored by Paul Rascagneres Executive Summary Talos has discovered an unknown Remote Administration Tool that we believe has been in use for over 3 years. During this time it has managed to avoid scrutiny by the security community. The current version of the mal
Vulnerability Spotlight: Randombit Botan Library X509 Certificate Validation Bypass Vulnerability
This vulnerability was discovered by Aleksandar Nikolic of Cisco Talos. Overview Talos has discovered a vulnerability in the Randombit Botan library. A programming error exists in a way Botan library implements x500 string comparisons which could lead to certificate verificatio