Organizations across the country are on edge today after a flurry of phony bomb threats hit several public entities Thursday, such as universities, schools and news outlets, among others. The attackers distributed malicious emails claiming to have placed some type of explosive materials in the recipient's building. The emails stated the attackers would detonate these explosives unless the victim made a Bitcoin payment of several thousand dollars.
Cisco Talos discovered that this campaign is actually an evolution of sextortion and extortion attacks that we reported on in October. The claims in the emails we've seen from this actor are completely false, yet they have caused untold amounts of damage as organizations have evacuated buildings and called upon law enforcement to investigate.
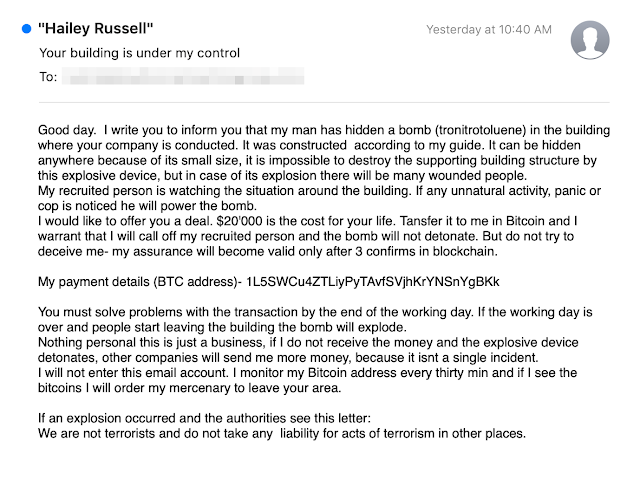
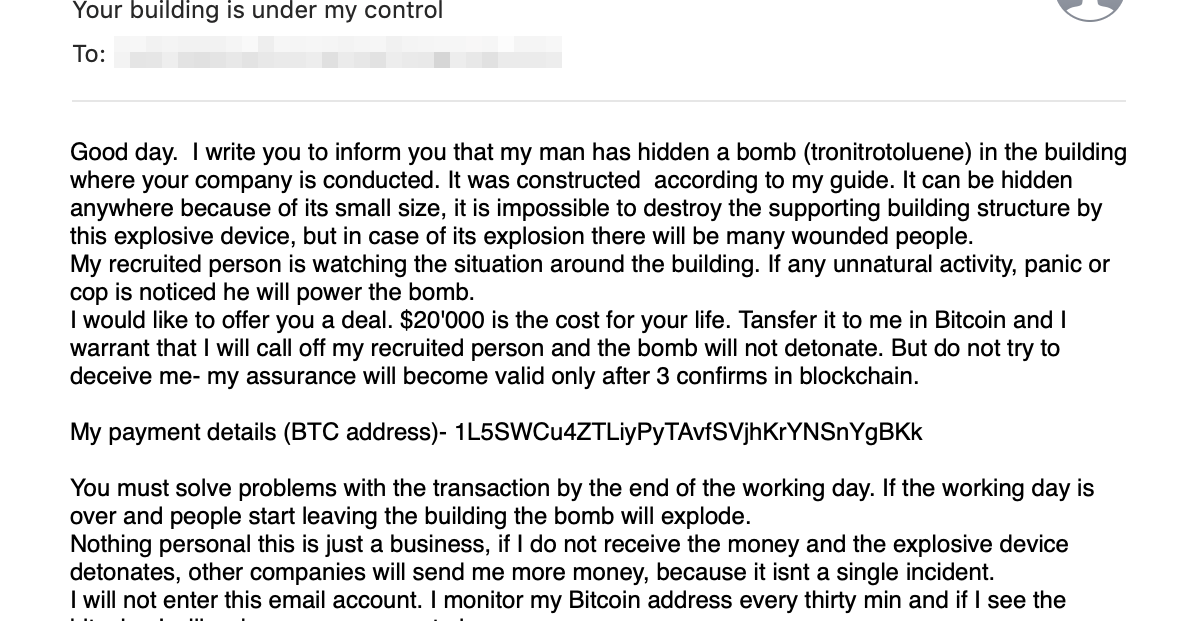
An example of the malicious, phony emails that attackers sent out to organizations across the U.S. yesterday.
What makes these particular extortion messages unique from other extortion scams we've monitored is that, previously, the attackers threatened only the individual — the attackers would threaten to expose sensitive data, or even attack the recipient physically, but there was never any threat of harm to a larger group of people, and certainly not the threat of a bomb.
Talos has discovered 17 distinct Bitcoin addresses that were used in the bomb extortion attack. Only two of the addresses have a positive balance, both from transactions received Dec. 13, the day the attacks were distributed. However, the amounts of each transaction were under $1, so it is evident the victims in this case declined to pay the $20,000 extortion payment price demanded by the attackers.
So far, all of the samples Talos has found to be associated with the bomb threat attack were sent from IP addresses belonging to the domain registrar and hosting company reg.ru, suggesting that the attackers in this case may have compromised credentials for domains that are hosted at this particular domain registrar. Multiple IPs involved in sending these bomb threats also sent various types of sextortion email that we saw in the previous campaign. In those cases, the attackers sent out emails claiming to have compromising videos of the victim and will release them to the public unless the attacker receives a Bitcoin payment.
As of late yesterday, the bomb threat email attack morphed. The attackers have returned to their empty threats of harming the individual recipient. This time, they threaten to throw acid on the victim.

An example of the newer extortion emails, claiming they will dump acid on the victim unless they receive a Bitcoin payment.
So far, none of the Bitcoin addresses associated with these new emails have received any payments. The source of the sending IP addresses changed, however. This time, the attackers are making heavy use of IP addresses at the Russian hosting company TimeWeb. As with the bomb threats, these IP addresses belong to domains that the attackers likely compromised.
The criminals conducting these extortion email attacks have demonstrated that they are willing to concoct any threat and story imaginable that they believe would fool the recipient. At this point, we have seen several different variations of these emails, and we expect these sorts of attacks to continue as long as there are victims who will believe these threats to be credible and be scared enough to send money to the attackers. Talos encourages users not to fall for these schemes and — above all — DO NOT pay extortion payments. Doing so will only confirm for the attackers that their social engineering approach is working, and victims' money goes directly toward facilitating additional attacks.
IOCs (BTC Addresses)
11B68RbmyxQys2CXXbAZxcwVXnaWCNBbw
12MET3CnEBkRc5Si5udf95fGaTZ6JwgpkK
132f8T1qF9hZj13MvPN5FbxrAhGExYZ7P3
149oyt2DL52Jgykhg5vh7Jm1QpdpfuyVqd
15F7TCqGRWE66xrBNxyt9ko1XsKaQvEh9t
15qH84uLC49CmC6jRE958Qjcf9WRZ2rMuM
1893DMwnrq9vA6JmQBdyWRKecArDAUTcGR
18UNWkvEDXgYzSAVnTmaR1X66w3T7HHsdn
1BTuxsCpAGtCzcszvFV2g4beqAZ2AUnyFh
1BfmmRBfhujpK944gai4vWvwCwGeHKbmkB
1BHasGex1jhRZeY7KyUGGKUNRtVgKedRY8
1CDs3JXUU6wNmndAF7EFcrJ6GGSYRKXd7w
1CF9VQhwjJutPxwVq5QLFA7j7baq4RDb3w
1CXrmcKL7W2o6FnrFx3ZBGn2EAsbMVZMzD
1CdD3nthrWR76RkL1WwLH7BSqCFASLjbhu
1D3ArQebDneVBVCqLort9jwvUA3AoZaNq5
1DVVQpxF4nG7rmuQFb7ZboGxu6ahKJcjf5
1Dnw2qJxGFCZdE3PzCaVioBB9zERc7SzRB
1DRXeydtqfjAmvfrLY7XiCo2A1vCq32z3a
1Ebf2rrLxVuMGKkwi2PeZtjBEEiidxrkkL
1FnTQHffH42iS15FMYNZxmNdbXtmb8WChF
1GTd6DPqcxCwX263BMsvk7FcjCQxsXhJUs
1GYAJY3GRsC5twdPgmQiEeNjdn7Kx6KSPd
1L5SWCu4ZTLiyPyTAvfSVjhKrYNSnYgBKk
1LEevM4MxKSGRrTvVrvLyjiuq3vYssdTRa
1LT4WgSuTD71Emzc7DLeHxVoZ1RjkhNcFY
1LTYBLzVSLe6GDFJ5NVVxLR2j5eQ8Wy51N
1LjxZonruwcKXEUYySrXt7gWGJLL6Pzuyx
1M9r1FpWj5QbSMECeJvXoa85TDMpoQcRaT
1MeDDtvZB5TE5tDTcwk6GiGSK3sTAP2KLA
1P3cNFy3SdfZ8PvMSdgLRcb2TtaLvxfqat
1PqX7bMnCzpJ7L1mxuGgNyaJSkJRM8SjES
Coverage