TeslaCrypt 3.0.1 - Tales From The Crypt(o)!
This post is authored by Andrea Allievi and Holger Unterbrink Executive Summary Ransomware is malicious software that is designed to hold users' files (such as photos, documents, and music) for ransom by encrypting their contents and demanding the user pay a fee to decryp
Threat Spotlight: CryptoWall 4 - The Evolution Continues
This post is authored byAndrea Allievi and Holger Unterbrink with contributions from Warren Mercer. Executive Summary Over the past year, Talos has devoted a significant amount of time to better understanding how ransomware operates, its relation to other malware, and its ec
Your Files Are Encrypted with a "Windows 10 Upgrade"
This post was authored by Nick Biasini with contributions from Craig Williams & Alex Chiu Update 8/1: To see a video of this threat in action click here Adversaries are always trying to take advantage of current events to lure users into executing their malicious payload. T
Cryptowall 3.0: Back to the Basics
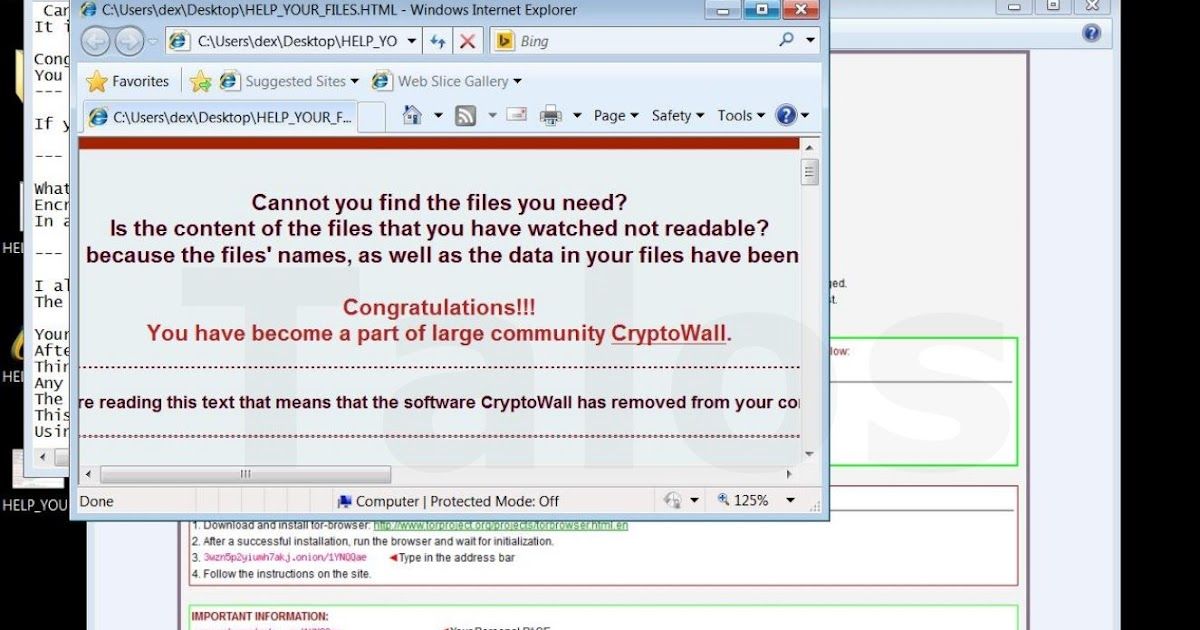
This post was authored by Andrea Allievi & Earl Carter Ransomware continues to impact a large number of organizations and the malware continues to evolve. In January, we examined Cryptowall 2.0 and highlighted new features incorporated into the dropper and Cryptowall binary
Ransomware on Steroids: Cryptowall 2.0
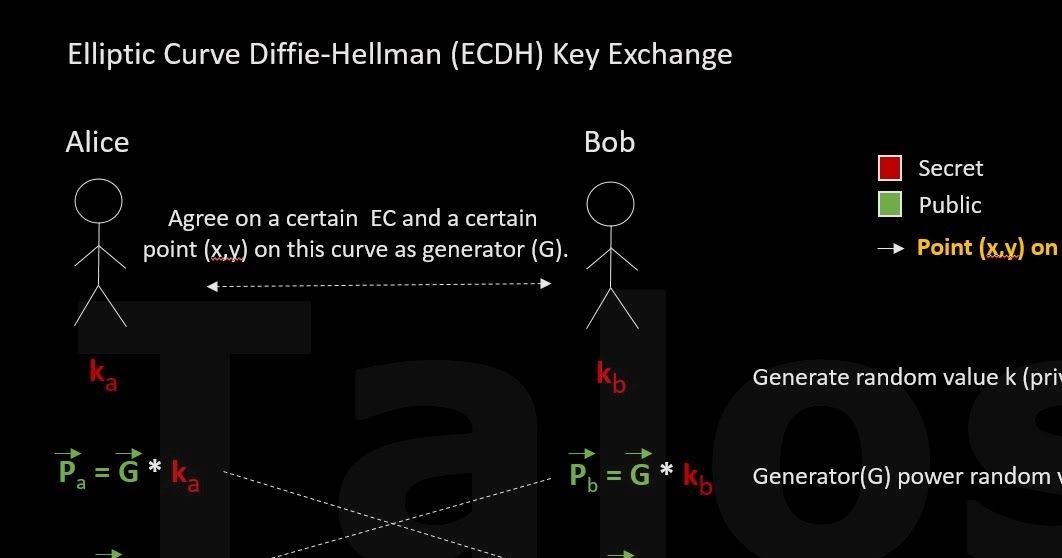
This post was authored by Andrea Allievi and Earl Carter. Ransomware holds a user’s data hostage. The latest ransomware variants encrypt the user’s data, thus making it unusable until a ransom is paid to retrieve the decryption key. The latest Cryptowall 2.0, utilizes TOR to obf