10 years of virtual dynamite: A high-level retrospective of ATM malware
ATM malware has evolved to include a number of different families and different actors behind them, ranging from criminal groups to actors affiliated with nation states.
Qakbot levels up with new obfuscation techniques
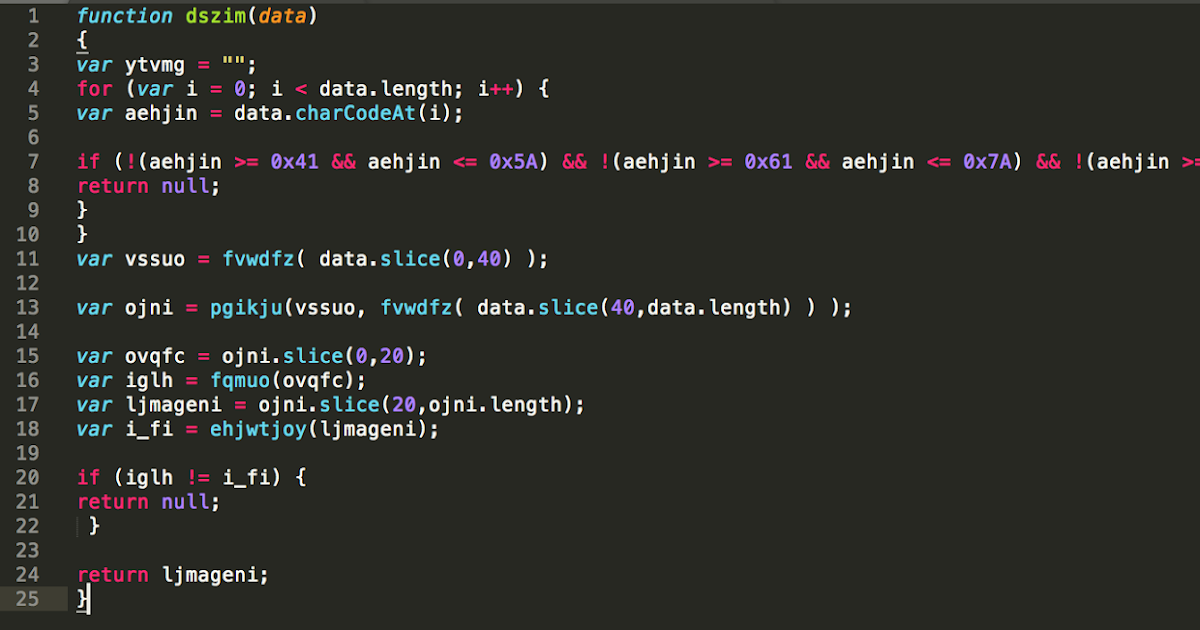
Executive summary Qakbot, also known as Qbot, is a well-documented banking trojan that has been around since 2008. Recent Qakbot campaigns, however, are utilizing an updated persistence mechanism that can make it harder for users to detect and remove the trojan. Qakbot is known
DNSpionage brings out the Karkoff
Update 4/24: The C2 section below now includes details around the XOR element of the C2 communication system. Executive summary In November 2018, Cisco Talos discovered an attack campaign, called DNSpionage, in which threat actors created a new remote administrative tool that
Sextortion profits decline despite higher volume, new techniques
Sextortion spammers continue blasting away at high volume. The success they experienced with several high-profile campaigns last year has led these attackers to continue transmitting massive amounts of sextortion email. These sextortion spammers have been doing everything they ca
Gustuff banking botnet targets Australia
EXECUTIVE SUMMARY Cisco Talos has uncovered a new Android-based campaign targeting Australian financial institutions. As the investigation progressed, Talos came to understand that this campaign was associated with the "ChristinaMorrow" text message spam scam previousl
Cisco Talos Honeypot Analysis Reveals Rise in Attacks on Elasticsearch Clusters
Christopher Evans of Cisco Talos conducted the research for this post. EXECUTIVE SUMMARY Cisco Talos warns users that they need to keep a close eye on unsecured Elasticsearch clusters. We have recently observed a spike in attacks from multiple threat actors targeting these clu
Fake Cisco Job Posting Targets Korean Candidates
Edmund Brumaghin and Paul Rascagneres authored this post, with contributions from Jungsoo An. Executive summary Cisco Talos recently observed a targeted malware campaign being leveraged in an attempt to compromise specific organizations. The infection vector associated with
Cisco AMP tracks new campaign that delivers Ursnif
Talos continues to see Ursnif in the wild. In this most recent example, we blocked it before it could do any damage to the target.
Advanced Mobile Malware Campaign in India uses Malicious MDM
Summary Cisco Talos has identified a highly targeted campaign against 13 iPhones which appears to be focused on India. The attacker deployed an open-source mobile device management (MDM) system to control enrolled devices. At this time, we don't know how the attacker managed