
- Emotet resumed spamming operations on March 7, 2023, after a months-long hiatus.
- Initially leveraging heavily padded Microsoft Word documents to attempt to evade sandbox analysis and endpoint protection, the botnets switched to distributing malicious OneNote documents on March 16.
- Since returning, Emotet has leveraged several distinct infection chains, indicating that they are modifying their approach based on their perceived success in infecting new systems.
- The initial emails delivered to victims are consistent with what has been observed from Emotet over the past several years.
Initial campaign
Following its initial return to spamming operations, Emotet was leveraging heavily padded Microsoft Word documents in an attempt to evade detection. By leveraging a large number of inconsequential bytes in their documents, they could increase the size of the documents to surpass the maximum file size restrictions that automated analysis platforms like sandboxes and anti-virus scanning engines enforce.
The initial emails were consistent with what has been commonly observed from Emotet in recent years. They typically contained an attached ZIP archive containing a Microsoft Word document. An example of one such email is shown below.
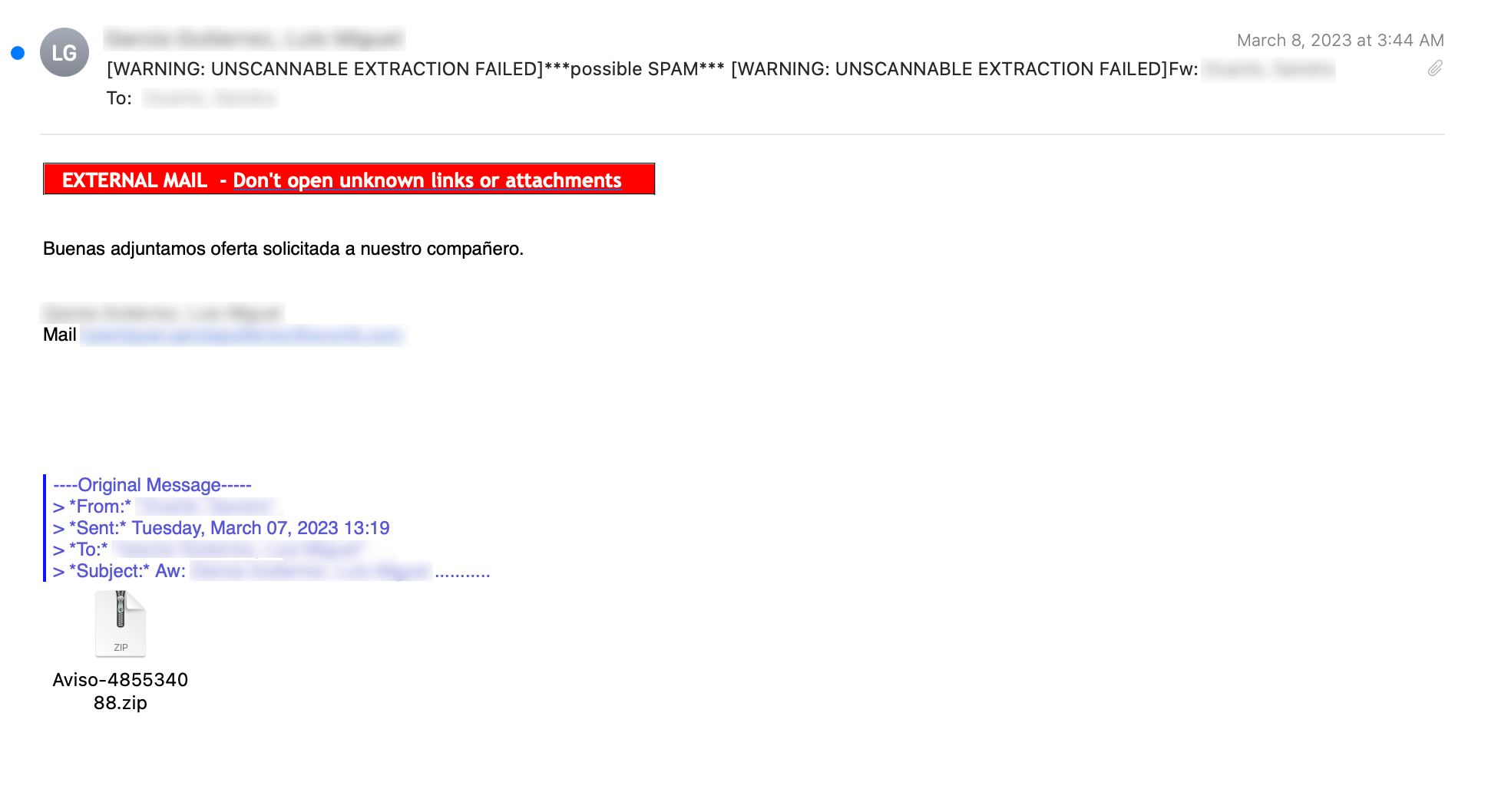
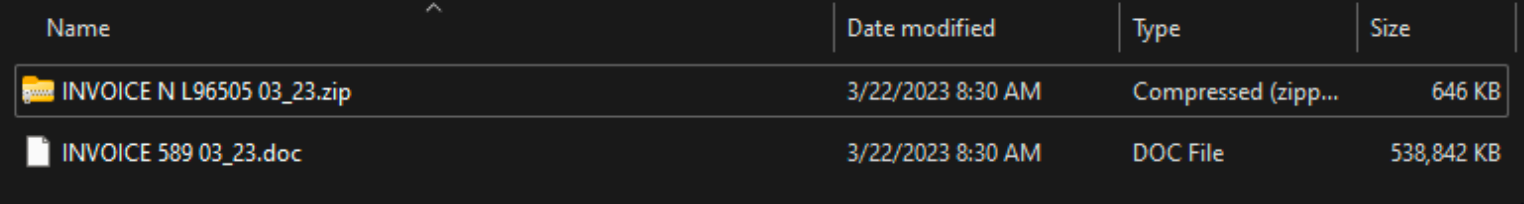
While the ZIP archives are often small, in some cases only ~646KB, the Microsoft Word document when fully extracted was ~500MB in size.
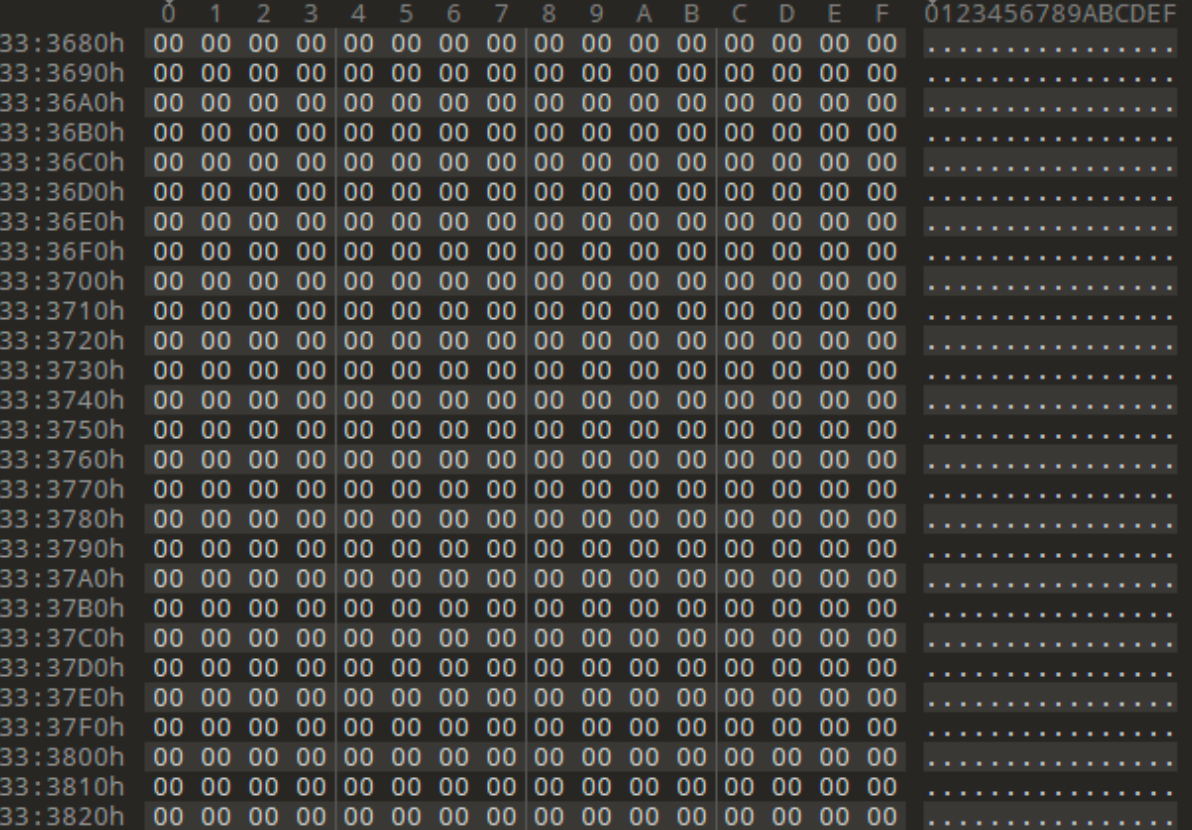
The document included a large number of 0x00 bytes, a technique commonly referred to as “padding.”
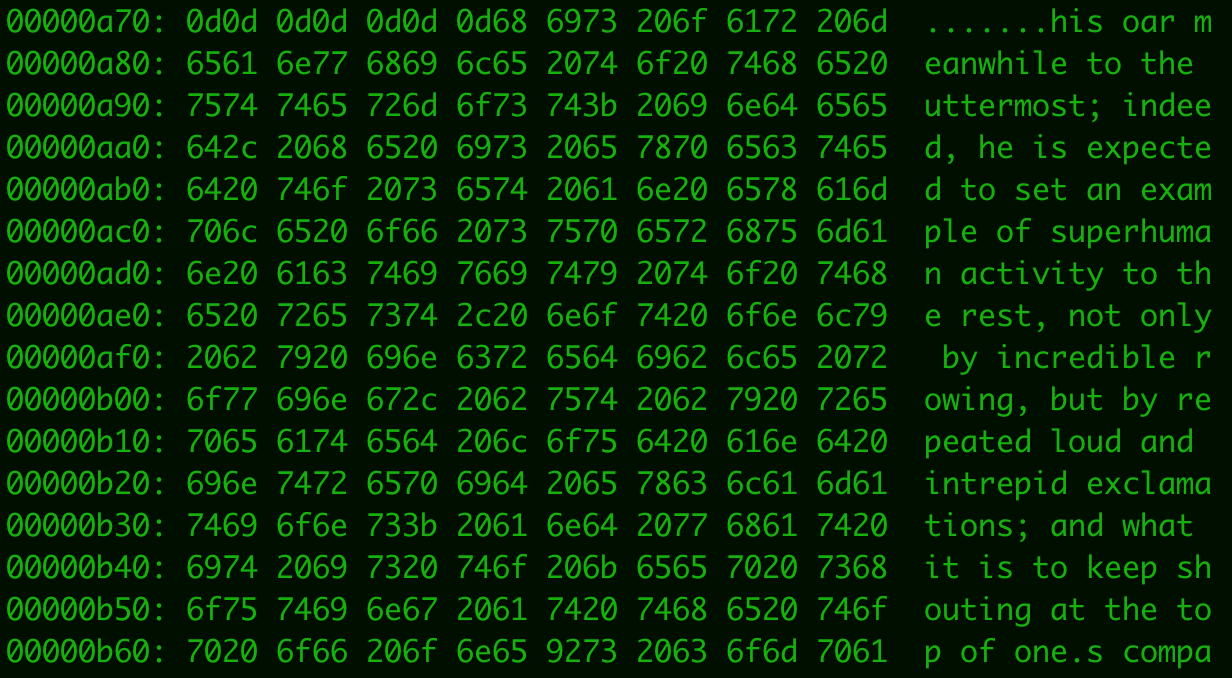
Some of the documents also featured excerpts from the classic novel “Moby Dick,” another attempt to increase the size of the documents for evasion purposes.
The Office documents featured templates consistent with those used by Emotet in the past, as shown below.
The Word documents in this campaign contained malicious VBA macros that, when executed, functioned as a malware downloader, retrieving the Emotet payload from attacker-controlled distribution servers and infecting systems, thus adding them to the Emotet botnets.
Emotet shifts to OneNote
Microsoft recently deployed new security mechanisms around protecting endpoints from macro-based malware infections, which resulted in various threat actors moving away from Office document-based malspam campaigns. In many cases, these malware distribution campaigns switched to distributing OneNote documents instead, likely as a result of decreased infections and lower success rates. Emotet is no different — shortly after their return to spamming operations on March 16, 2023, they began distributing OneNote files, as well.
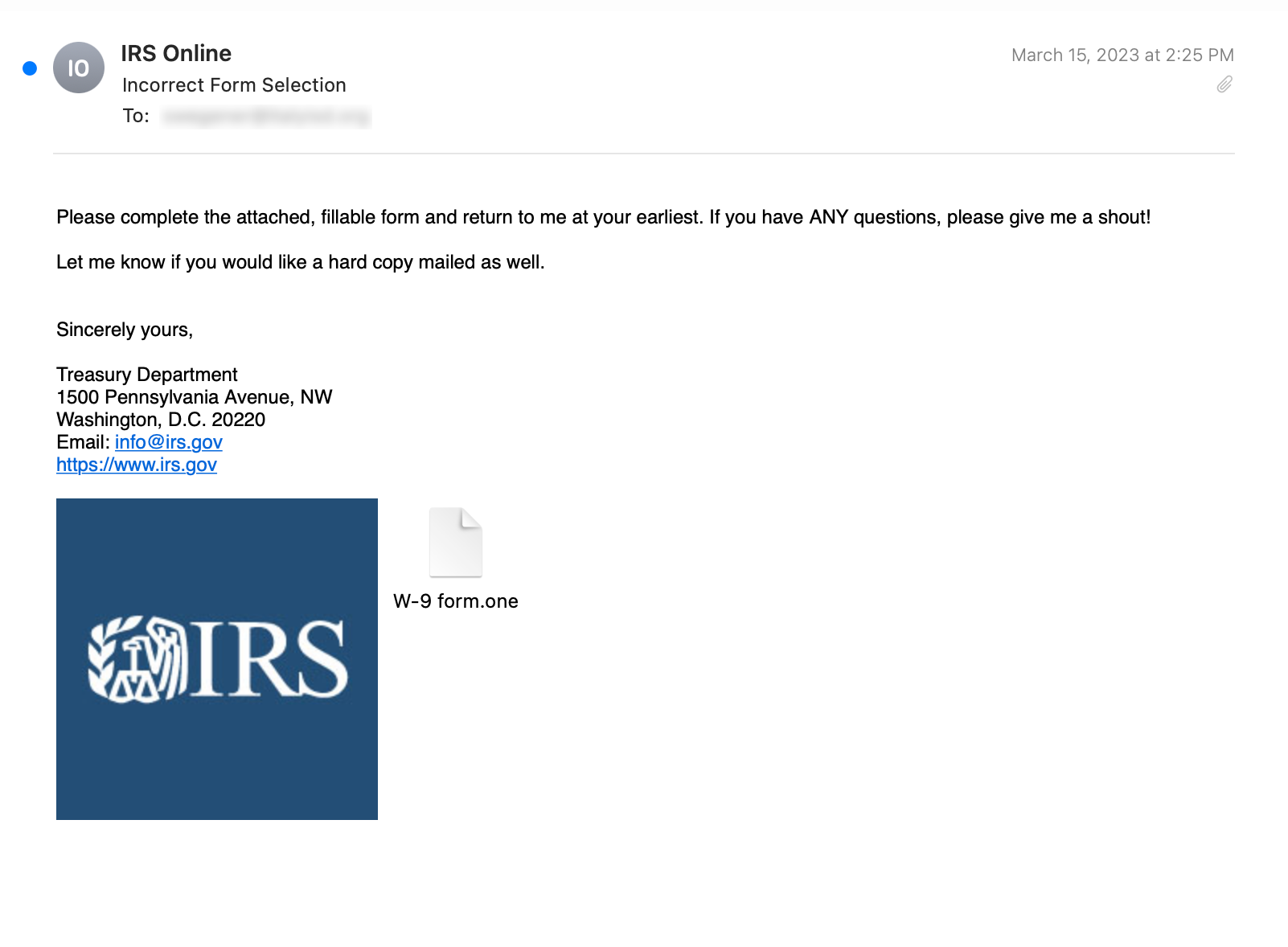
In one example, the sender purported to be from the U.S. Internal Revenue Service (IRS) and requested that the recipient complete the attached form.
The attached OneNote document featured templates similar to what has been observed in other Office document formats over the past several years, prompting the user to click inside the document to view the file.
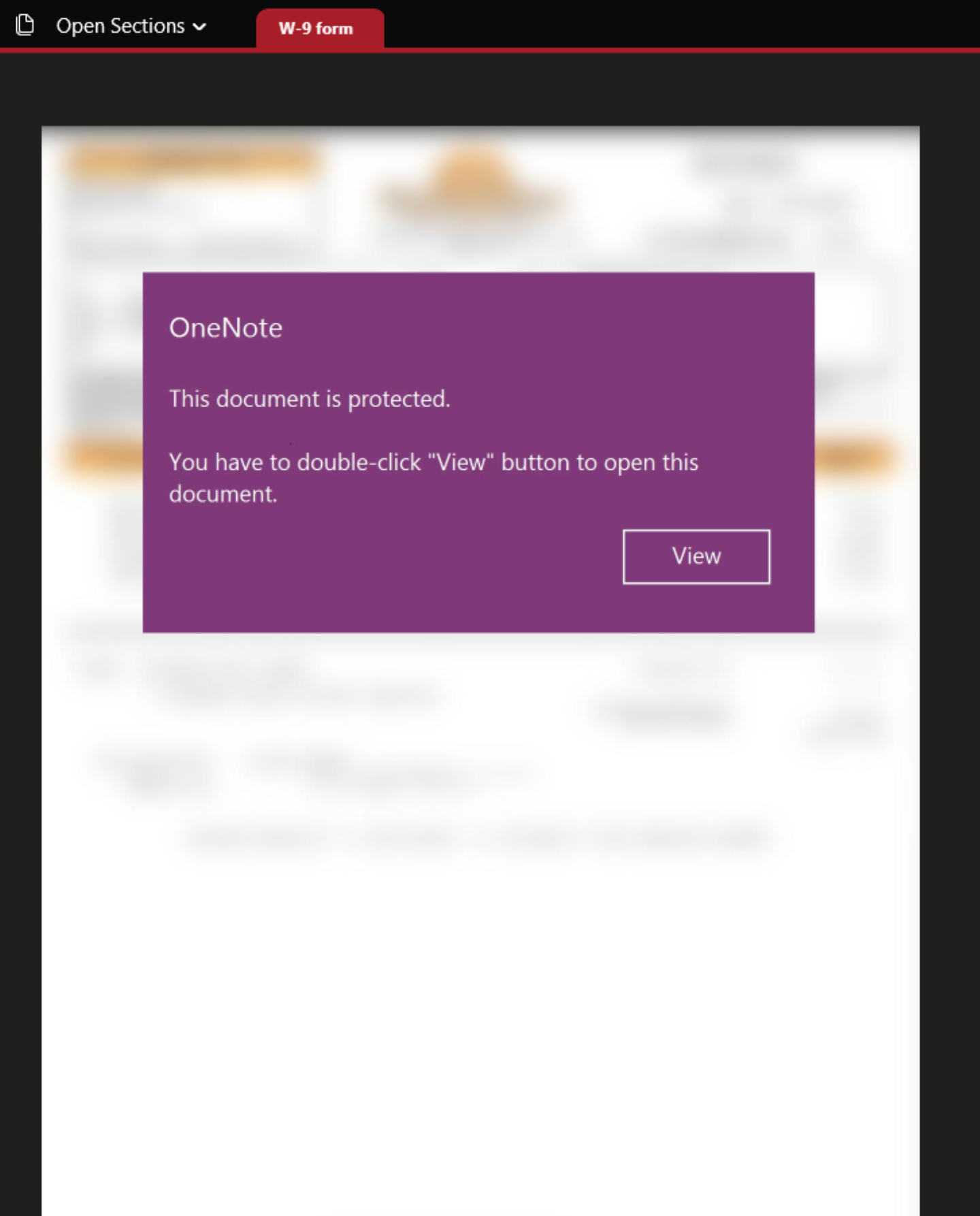
When clicked, an embedded WSF script linked behind the view button containing malicious VBScript code is executed.
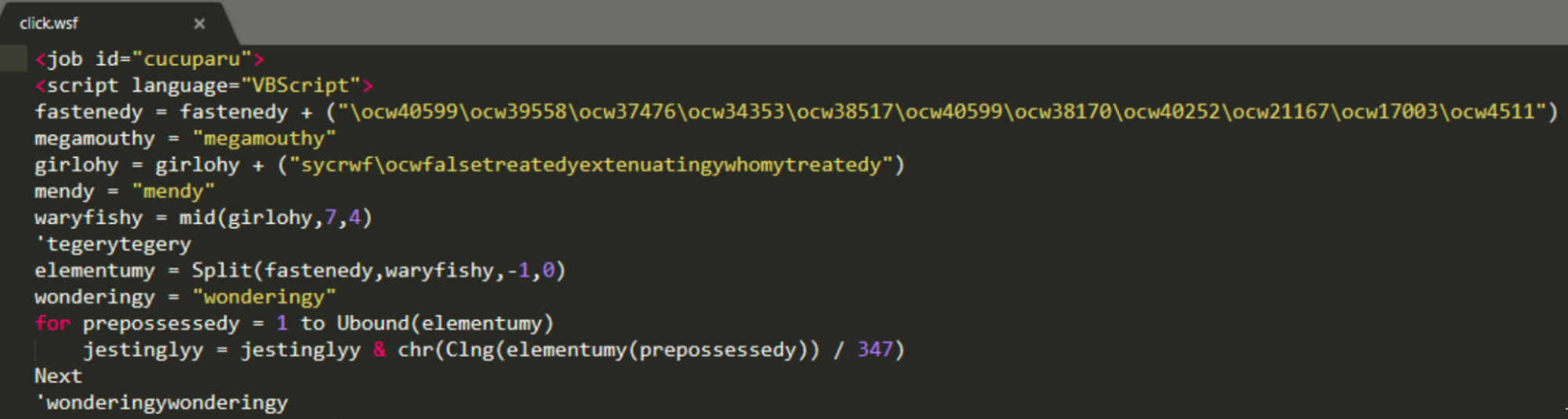
This VBScript downloader is responsible for retrieving the Emotet malware payload from an attacker-controlled server and infecting the system.

More recently, the embedded object inside of the OneNote files contained JavaScript instead of VBScript but offered the same functionality within the infection chain.
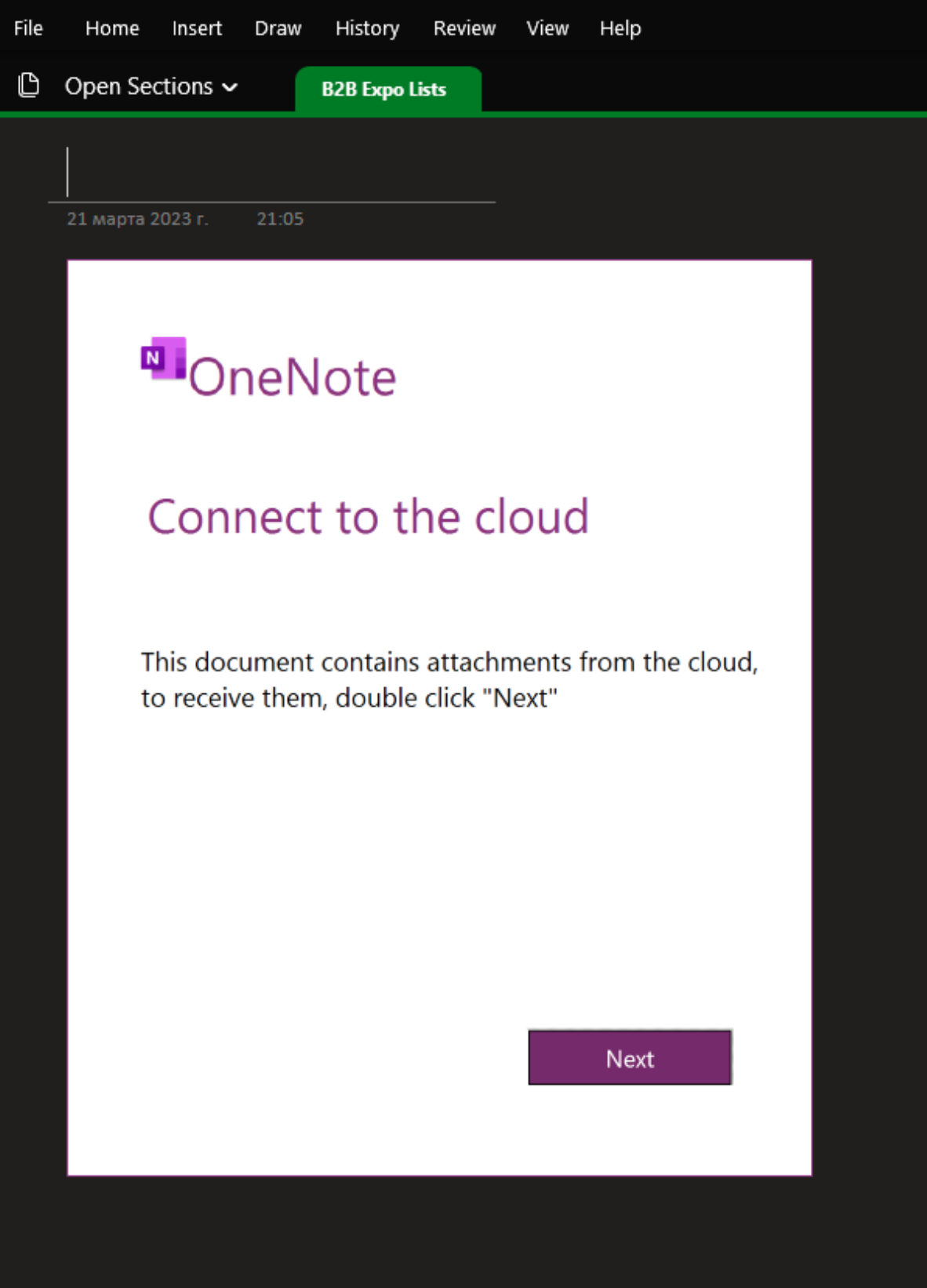
Hovering over the next button indicates that an object called “Object1.js” will execute when the button is clicked. This is because the attacker has embedded a clickable object behind the lure image as shown below.

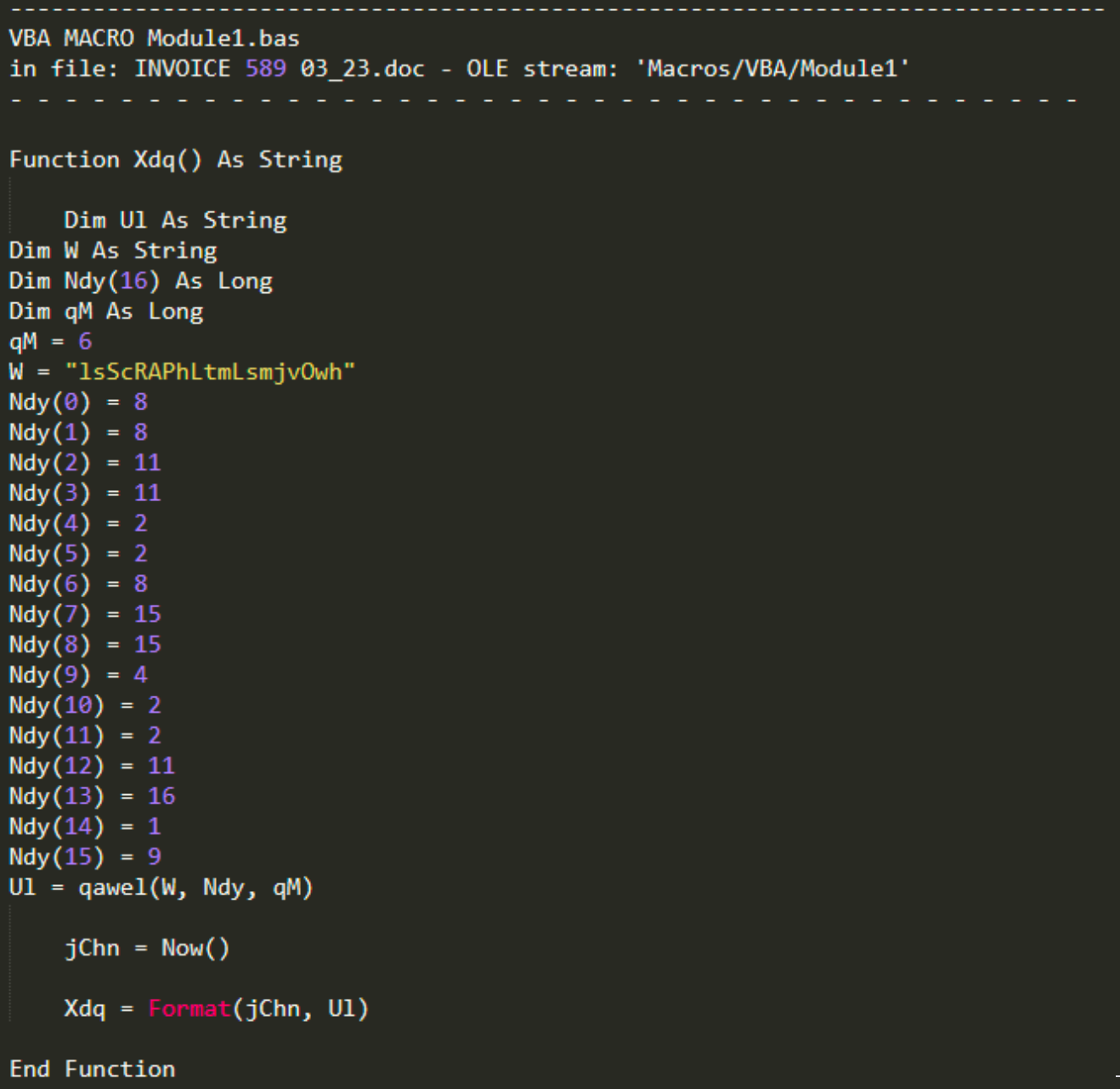
This object is a heavily obfuscated JavaScript downloader responsible for retrieving and executing the Emotet payload on the system. A snippet from the obfuscated downloader is shown below.
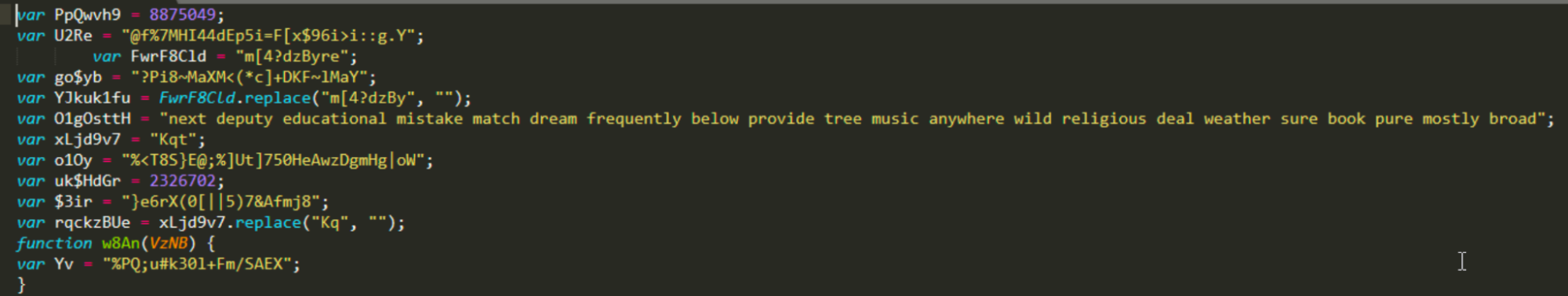
In a relatively short period, Emotet has modified its infection chain several times to maximize the likelihood of successfully infecting victims.
Indicators of Compromise
Indicators of compromise (IOCs) associated with ongoing Emotet campaigns can be found here.
Coverage
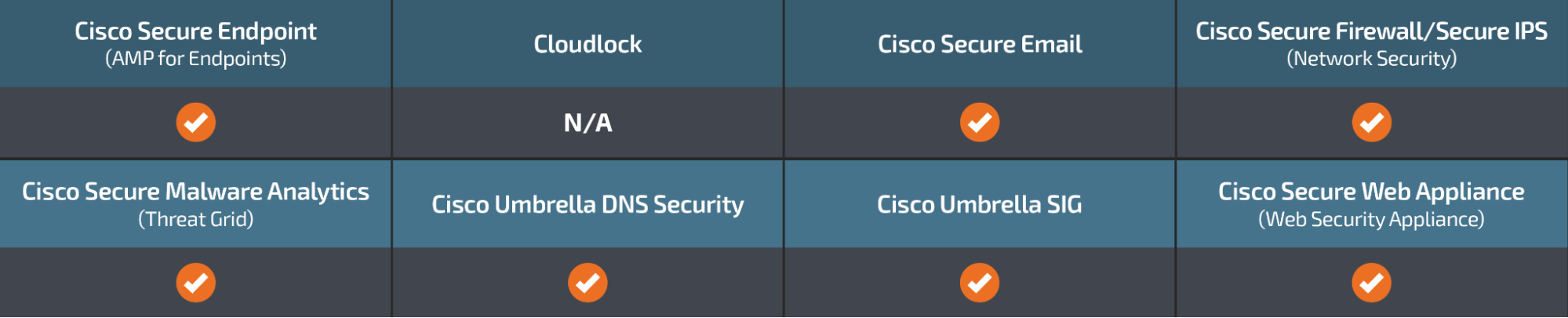
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Network/Cloud Analytics (Stealthwatch/Stealthwatch Cloud) analyzes network traffic automatically and alerts users of potentially unwanted activity on every connected device.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco’s secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Talos created the following coverage for this threat.
Snort SIDs:
51967-51971, 43890-43892, 44559, 44560, 47327, 47616, 47617, 48402, 49888, 49889, 52029, 53108, 53353-53360, 53770, 53771, 54804, 54805, 54900, 54901, 54924, 54925, 55253, 55254, 55591, 55592, 55781, 55782, 55787, 55788, 55869, 55870, 55873, 55874, 55929-55931, 56003, 56046, 56047, 56170, 56171, 56528, 56529, 56535, 56536, 56620, 56621, 56656, 56657, 56713, 56714, 56906, 56907, 56924, 56925, 56969, 56970, 56983, 56984, 57901, 58943
ClamAV Rules:
Onenote.Dropper.Emotet-9993911-1
Onenote.Dropper.CodPhish-Emotet-9993220-1
Onenote.Trojan.Agent-9987935-0